Last Updated :
11 Oct, 2024
SSH (Secure Shell) is a widely used protocol that provides secure and encrypted communication for accessing and managing remote servers. With robust encryption mechanisms, SSH allows users to connect securely over unsecured networks, run commands, transfer files, and manage services remotely.
However, users may sometimes encounter connection issues, with one common error being: «SSH: connect to host ‘hostname’ port 22: connection timed out.» Here, we will explain why this error occurs, provide troubleshooting steps, and share best practices for using SSH securely.
Primary Terminologies in SSH
The following are the primary terminologies in SSH:
- Public Key Authentication: One way to log in to the SSH server is to use two pairs of keys (public and private keys). The server uses the public key to authenticate the client and the client keeps the private key.
- SSH Client: Software that initiates the SSH connection from the user’s computer to a remote server.
- SSH Server: A program that receives the SSH connection from the user and grants access to the server’s resources.
- Port Forwarding: An SSH tool used to forward network traffic from one port to another, often used to access services behind a firewall.
- SCP(Secure Copy Policy): Ways to copy data securely between hosts via SSH.
- SFTP(Secure File Transfer Protocol): SFTP is the secure data transfer based on SSH protocol which provides secure data access, transfer, and management.
- Encryption: The process of converting data into coded form to prevent unauthorized access during transmission.
- Session: The time taken by the SSH user to connect to the server. It includes connection authentication.
What Causes «SSH: Connect to Host ‘Hostname’ Port 22: Connection Timed Out»?
The «Connection Timed Out» error occurs when the client is unable to establish a connection with the remote server on the specified port (default is port 22). This issue can arise due to several reasons, such as:
- Network connectivity problems.
- Incorrect IP address or hostname.
- Firewall or security group blocking port 22.
- SSH service not running on the server.
- Misconfigured SSH server settings.
- Server’s IP address restrictions.
Solution for SSH: Connect To Host ‘Hostname’ Port 22: Connection Timed Out
The following are the steps that guides for the solution of SSH Connection resolving the connection time out issue:
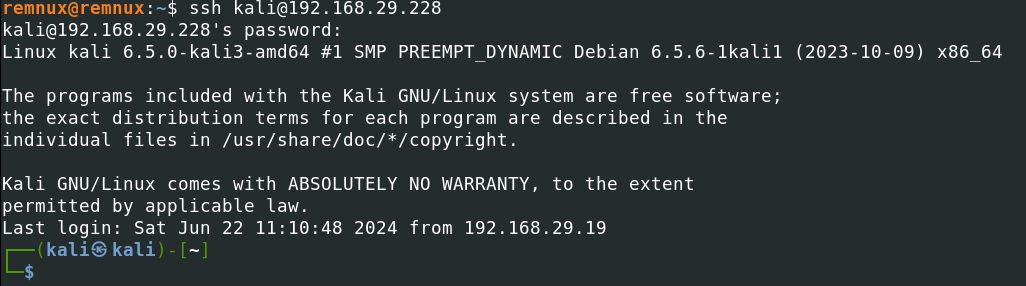
Step 1: Verify the connection using IP Address/Hostname
You can retry to connect the remote host using IP Address/Hostname.
Command
ssh kali@192.168.29.228
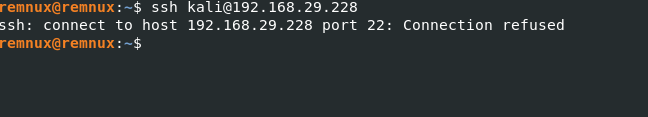
Step 2: Check the network connectivity
Ensure that the network is functional by pinging the server. If the server is reachable, you should receive responses from the remote host:
Command
ping 192.168.29.228
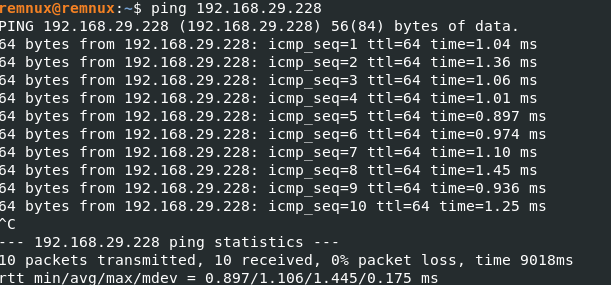
As you can see the client host can easily communicate with remote host. so there might be some other issue.
Step 3: Test the port connectivity
Try to check port 22 is open in remote server using telnet command or not.
Command
telnet 192.168.29.228 22

If you receive a message indicating that the connection is refused or fails, it suggests that port 22 is either closed or blocked by a firewall.
Step 4: Verify the status of SSH on remote host
Cross check the status of SSH service and re-enable it.
Command
sudo systemctl start ssh
Step 5: Enable the SSH service
Make sure the SSH service is enabled to start automatically on boot.
Command
sudo systemctl enable ssh
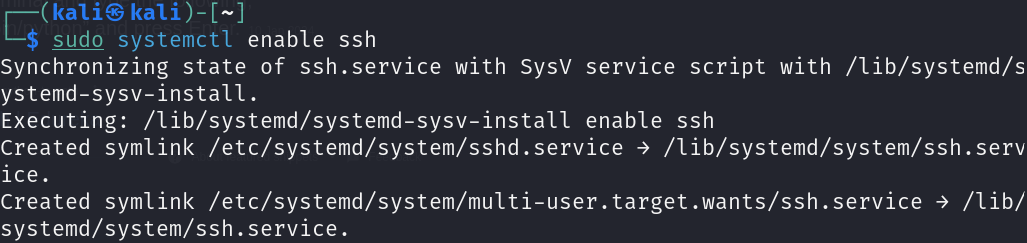
Step 6: Re-check the SSH Service Status
Verify that the SSH service is running correctly:
Command
sudo systemctl status ssh
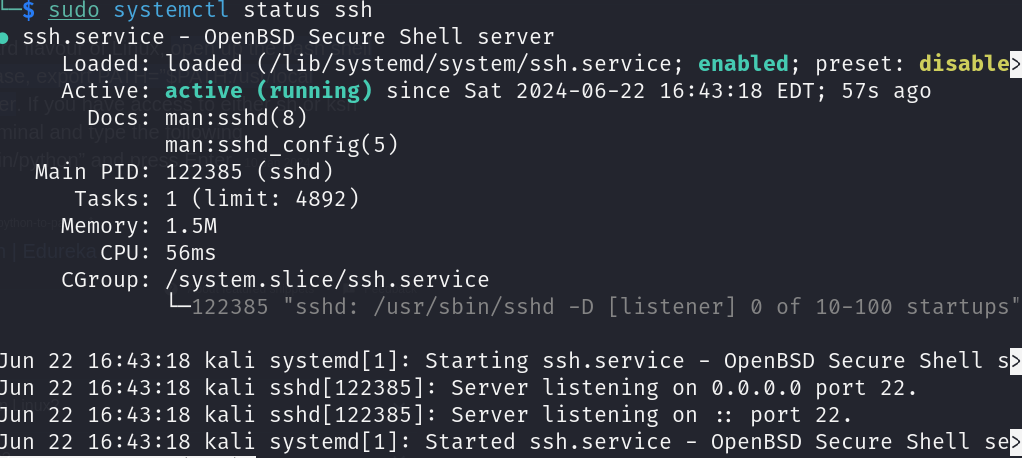
Step 7: Test the SSH Connection
Again try to connect the remote host after configuration changes.
Command
ssh kali@192.168.29.228
Troubleshooting issues of SSH Connection
The folowing are the some of the troubleshooting issues and best practices of SSH Connection:
- Refusing Connection: It generally occurs when server not running or firewall blocks port.
- Authentication Failure: It generally occurs when incorrect credentials or keys don’t match
- Permission Issue: It generally occurs when user doesn’t have permission on the server
- Host Key Verification Failed: It generally occurs when server’s host key changed (could be a security issue).
Conclusion
In conclusion, this error arises due to network connectivity, configuration issue, service issue etc. The solution provided here may resolve this issue. Remember to keep your SSH settings updated and adopt security measures to protect your server from potential threats.
3 min read
Encountering the message «SSH: Connect to Host ‘Hostname’ Port 22: Connection Timed Out» can be frustrating, especially when you need to access a remote server quickly. This error typically indicates that your SSH client cannot establish a connection to the server on port 22, which is the default port for SSH. Let’s explore effective solutions to troubleshoot and resolve this issue.
Common Causes of Connection Timeout
Before diving into solutions, it’s essential to understand the potential causes of this timeout error:
-
Network Issues: Problems with your local internet connection or the server’s network.
-
Firewall Restrictions: Firewalls on your local machine, network, or server blocking SSH traffic.
-
Server Configuration: SSH service may not be running on the server or may be configured incorrectly.
-
Incorrect Hostname or IP Address: Mistyped hostname or IP address can lead to connection issues.
Step-by-Step Solutions
1. Check Your Internet Connection
Ensure that your local internet connection is stable and functioning correctly. You can verify this by trying to access other websites or services.
- Test Connectivity: Open your terminal and ping a reliable server (like Google):
ping google.com
2. Verify SSH Service on the Server
If you have access to the server, check if the SSH service is running.
- Connect Locally: If you can access the server physically or via another method, run the following command:
sudo systemctl status ssh
- Start SSH Service: If the service is not running, start it with:
sudo systemctl start ssh
3. Check Firewall Settings
Firewalls can often block port 22, preventing SSH connections. Depending on the operating system, follow these steps:
For Linux (UFW)
- Check the status of UFW (Uncomplicated Firewall):
sudo ufw status
- If SSH is not allowed, enable it:
sudo ufw allow 22
For Linux (iptables)
- List current iptables rules:
sudo iptables -L -n
- Ensure there’s a rule permitting traffic on port 22. If not, add one:
sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT
For Windows Firewall
-
Open Windows Firewall settings.
-
Ensure that the inbound rules allow traffic on port 22.
4. Test From a Different Network
If possible, try connecting from a different network or location. This can help determine if the issue lies with your current network configuration.
5. Use the Correct Hostname or IP Address
Double-check the hostname or IP address you are using to connect. A simple typo can lead to a connection timeout.
6. Check Server Configuration
Review the SSH configuration file on the server (/etc/ssh/sshd_config) for any misconfigurations:
- Access the config file:
sudo nano /etc/ssh/sshd_config
-
Verify Port and ListenAddress:
-
Ensure that
Port 22is set correctly. -
Check that
ListenAddressis either commented out or set to the correct IP address.
7. Restart the SSH Service
After making any changes, restart the SSH service to apply them:
sudo systemctl restart ssh
8. Use Verbose Mode for More Details
When trying to connect via SSH, you can use the verbose mode to get more detailed output about the connection process:
ssh -vvv username@hostname
This command will provide insights into where the connection process might be failing.
Conclusion
Dealing with the “SSH: Connect to Host ‘Hostname’ Port 22: Connection Timed Out” error can be a hassle, but by following the steps outlined above, you can effectively troubleshoot and resolve the issue. Always start with basic checks like your internet connection and firewall settings, then move on to server-specific configurations.
If you continue to experience issues, consider reaching out to your server administrator or hosting provider for further assistance. Happy troubleshooting!
Related Articles
CDN 2025: Edge-Cached WASM Modules for Sub-50ms Global Latency
Learn how edge-cached WebAssembly modules on CDNs deliver sub-50ms global latency, improving performance and user experience across applications.
WebAssembly 4.0 for Games: Porting C++ Engines to the Browser
Learn how to port C++ game engines to browsers with WebAssembly 4.0. This guide covers performance optimization, memory management, and cross-platform compatibility.
CDN 2025: Reducing Global Latency with Edge-Cached WASM Modules
Learn how edge-cached WebAssembly modules are transforming CDNs in 2025, cutting global latency by up to 63% while improving reliability and developer control.
How to Build a Web3 Twitter Clone Using Farcaster Protocol: Step-by-Step Guide
Learn how to build a decentralized Twitter clone with Farcaster protocol, featuring user authentication, cast creation, and feed management. No Web3 experience needed!
SvelteKit 4.0: Blazing-Fast SEO with Hybrid Rendering
Learn how SvelteKit 4.0’s hybrid rendering delivers lightning-fast page loads and superior SEO performance for modern web applications.
Edge AI in Browser: Run PyTorch Models with WebGPU and ONNX
Learn how to run PyTorch models directly in your browser using WebGPU and ONNX Runtime for faster, private AI applications without server dependencies.
Is HTMX the Future of Web Dev? A React vs. HTMX Benchmark
Compare HTMX vs React performance in this hands-on benchmark. Discover which technology delivers faster load times and better UX for your next web project.
Mastering WebAssembly 2.0: Rust + WASI for Cross-Platform Apps
Learn how to build high-performance cross-platform applications using Rust, WebAssembly 2.0, and WASI. Practical guide with code examples and setup instructions.
Enhance Web App Performance with These Testing Tips
I’ll share practical tips for efficient web application performance testing, allowing you to ensure your app meets the highest standards.
What is Web Performance? Boost Your Website’s Speed
Discover what web performance is and why it’s essential for your website. Learn key metrics and tips to enhance your site’s speed and user experience.

If you’ve attempted to establish an SSH connection to a remote server and received a “Connection Timed Out” error message, don’t worry! This is a common issue…
Here’s a step-by-step guide for easily fixing the SSH Connection Timed Out error. 😃
By the way, What does SSH "connection timed out" mean?
This error happens when the computer tries to connect with a server through SSH and it waits for a response on the other end. If, in a certain amount of time, SSH doesn't connect, it says, "Connection Timed Out." That really only tells you that your computer couldn't communicate with the server, but it's not sure exactly why.
Quick Summary of Fixes
- Check if the Server is Running
- Verify the SSH Port
- Check Firewall Settings (on Your PC and the Server)
- Self-Assessment of Your End Issues
- Increase Connection Timeout
- Check Server Logs for Errors
- Advanced Troubleshooting (Optional)
- Get Your Windows VPS Server Today
Solutions
Check if the Server is Running
Make sure the server is up and running. You can verify this by pinging the server or by contacting the server administrator for its status.
To ping the server, use the following command: replace the IP of your server with the IP of your machine.
ping <ip_address>If you get a response like “Request Timed Out” or “Destination Host Unreachable,” the server might be down.

Verify the SSH Port
SSH uses port 22 by default, but the server might use a different port. If your server uses a custom port, you’ll need to specify it in the command. You can use the SSH connecting command like the below:
ssh -p 2222 [email protected]Remember to replace the username, server IP address, and SSH port with the correct values as of your server.
Check Firewall Settings (on Your PC and the Server)
If a firewall is blocking your SSH connection, you must adjust its settings.
On your local machine, make sure the firewall allows outgoing SSH connections on port 22, or whichever custom port is utilized.
On your server side, check whether SSH connections are allowed if you have access to the server by any means.
sudo ufw allow sshOr, if SSH runs on a different port:
sudo ufw allow <port number>If you’re not using the UFW firewall, adjust these settings by referring to the blog: https://www.veeble.org/kb/how-to-open-a-specific-port-on-linux/
Self-Assessment of Your End Issues
- Open up any other site on your browser to make sure you are online and the Internet is working without issues.
- Check the Internet speed also via visiting the speed testing websites available in your search engine, such as SpeedTest by Ookla.
- Double-check the IP address of the server and make sure you’re using the correct one.
Increase Connection Timeout
You can increase the SSH timeout value to give the server more time to respond. Sometimes the server might be slow to respond, and the default timeout period might be too short. So to alter it and connect to the server, use the following command format:
ssh -o ConnectTimeout=30 user@server_ip_addressIn this example, 30 represents the number of seconds before timing out.
Check Server Logs for Errors
If you have access to the server logs, check them for any signs of SSH-related issues. You can usually find the logs in /var/log/auth.log or /var/log/secure, depending on your system.
cat /var/log/auth.logOR
cat /var/log/secureAdvanced Troubleshooting (Optional)
If you are still facing issues connecting to SSH, it is recommended to check any blocks for your IP in your server’s firewall as well as the below blog SSH access regaining solutions:
The “Connection Timed Out” error in SSH can be frustrating, but with this guide, you can troubleshoot and fix the issue easily. Most of the time, the problem is with either a firewall, the wrong SSH port, or a network connection. By following these simple steps, you’ll be able to connect to your server in no time!
Get Your Windows VPS Server Today
Deploy your Windows applications and websites with ease. Our reliable infrastructure ensures your online presence is always available.
Get Your VPS Now
25 мая, 2017 11:40 дп
93 893 views
| Комментариев нет
Linux, SSH
В первой статье этой серии вы узнали о том, как и в каких ситуациях вы можете попробовать исправить ошибки SSH. Остальные статьи расскажут, как определить и устранить ошибки:
- Ошибки протокола: в этой статье вы узнаете, что делать, если сбрасываются клиентские соединения, клиент жалуется на шифрование или возникают проблемы с неизвестным или измененным удаленным хостом.
- Ошибки аутентификации: поможет устранить проблемы с парольной аутентификацией или сбросом SSH-ключей.
- Ошибки оболочки: это руководство поможет исправить ошибки ветвления процессов, валидации оболочки и доступа к домашнему каталогу.
Для взаимодействия SSH-клиента с SSH-сервером необходимо установить базовое сетевое подключение. Это руководство поможет определить некоторые общие ошибки подключения, исправить их и предотвратить их возникновение в будущем.
Требования
- Убедитесь, что можете подключиться к виртуальному серверу через консоль.
- Проверьте панель на предмет текущих проблем, влияющих на работу и состояние сервера и гипервизора.
Основные ошибки
Разрешение имени хоста
Большинство ошибок подключения возникает тогда, когда ссылка на хост SSH не может быть сопоставлена с сетевым адресом. Это почти всегда связано с DNS, но первопричина часто бывает не связана с DNS.
На клиенте OpenSSH эта команда:
ssh user@example.com
может выдать ошибку:
ssh: Could not resolve hostname example.com: Name or service not known
В PuTTY может появиться такая ошибка:
Unable to open connection to example.com Host does not exist
Чтобы устранить эту ошибку, можно попробовать следующее:
- Проверьте правильность написания имени хоста.
- Убедитесь, что вы можете разрешить имя хоста на клиентской машине с помощью команды ping. Обратитесь к сторонним сайтам (WhatsMyDns.net, например), чтобы подтвердить результаты.
Если у вас возникают проблемы с разрешением DNS на любом уровне, в качестве промежуточного решения можно использовать IP-адрес сервера, например:
ssh user@111.111.111.111
# вместо
ssh user@example.com.
Истечение времени соединения
Эта ошибка значит, что клиент попытался установить соединение с SSH-сервером, но сервер не смог ответить в течение заданного периода ожидания.
На клиенте OpenSSH следующая команда:
ssh user@111.111.111.111
выдаст такую ошибку:
ssh: connect to host 111.111.111.111 port 22: Connection timed out
В PuTTY ошибка выглядит так:
Network error: Connection timed out
Чтобы исправить ошибку:
- Убедитесь, что IP-адрес хоста указан правильно.
- Убедитесь, что сеть поддерживает подключение через используемый порт SSH. Некоторые публичные сети могут блокировать порт 22 или пользовательские SSH-порты. Чтобы проверить работу порта, можно, например, попробовать подключиться к другим хостам через этот же порт. Это поможет вам определить, не связана ли проблема с самим сервером.
- Проверьте правила брандмауэра. Убедитесь, что политика по умолчанию – не DROP.
Отказ в соединении
Эта ошибка означает, что запрос передается на хост SSH, но хост не может успешно принять запрос.
На клиенте OpenSSH следующая команда выдаст ошибку:
ssh user@111.111.111.111
ssh: connect to host 111.111.111.111 port 22: Connection refused
В PuTTY ошибка появится в диалоговом окне:
Network error: Connection refused
Эта ошибка имеет общие с ошибкой Connection Timeout причины. Чтобы исправить её, можно сделать следующее:
- Убедиться, что IP-адрес хоста указан правильно.
- Убедиться, что сеть поддерживает подключение через используемый порт SSH. Некоторые публичные сети могут блокировать порт 22 или пользовательские SSH-порты. Чтобы проверить работу порта, можно, например, попробовать подключиться к другим хостам через этот же порт.
- Проверить правила брандмауэра. Убедитесь, что политика по умолчанию – не DROP, и что брандмауэр не блокирует этот порт.
- Убедиться, что сервис запущен и привязан к требуемому порту.
Рекомендации по исправлению ошибок подключения
Брандмауэр
Иногда проблемы с подключением возникают из-за брандмауэра. Он может блокировать отдельные порты или сервисы.
Читайте также: Что такое брандмауэр и как он работает?
В разных дистрибутивах используются разные брандмауэры. Вы должны научиться изменять правила и политики своего брандмауэра. В Ubuntu обычно используется UFW, в CentOS – FirewallD. Брандмауэр iptables используется независимо от системы.
Читайте также:
- Основы UFW: общие правила и команды фаервола
- Настройка брандмауэра FirewallD в CentOS 7
- Основы Iptables: общие правила и команды брандмауэра
Чтобы настроить брандмауэр, нужно знать порт сервиса SSH. По умолчанию это порт 22.
Чтобы запросить список правил iptables, введите:
iptables -nL
Такой вывод сообщает, что правил, блокирующих SSH, нет:
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Если в выводе вы видите правило или политику по умолчанию REJECT или DROP, убедитесь, что цепочка INPUT разрешает доступ к порту SSH.
Чтобы запросить список правил FirewallD, введите:
firewall-cmd --list-services
Список, появившийся на экране, содержит все сервисы, которые поддерживаются брандмауэром. В списке должно быть правило:
dhcpv6-client http ssh
Если вы настроили пользовательский порт SSH, используйте опцию –list-ports. Если вы создали пользовательское определение сервиса, добавьте опцию –list-services, чтобы найти SSH.
Чтобы проверить состояние UFW, введите:
ufw status
Команда вернёт доступные порты:
Status: active
To Action From
-- ------ ----
22 LIMIT Anywhere
443 ALLOW Anywhere
80 ALLOW Anywhere
Anywhere ALLOW 192.168.0.0
22 (v6) LIMIT Anywhere (v6)
443 (v6) ALLOW Anywhere (v6)
80 (v6) ALLOW Anywhere (v6)
В списке должен быть порт SSH.
Проверка состояния сервиса SSH
Если вы не можете подключиться к серверу по SSH, убедитесь, что сервис SSH запущен. Способ сделать это зависит от операционной системы сервера. В более старых версиях дистрибутивов (Ubuntu 14.04, CentOS 6, Debian 
Метод проверки состояния сервиса может варьироваться от системы к системе. В более старых версиях (Ubuntu 14 и ниже, CentOS 6, Debian 6) используется команда service, поддерживаемая системой инициализации Upstart, а в более современных дистрибутивах для управления сервисом используется команда systemctl.
Примечание: В дистрибутивах Red Hat (CentOS и Fedora) сервис называется sshd, а в Debian и Ubuntu – ssh.
В более старых версия используйте команду:
service ssh status
Если процесс работает должным образом, вы увидите вывод, который содержит PID:
ssh start/running, process 1262
Если сервис не работает, вы увидите:
ssh stop/waiting
В системах на основе SystemD используйте:
systemctl status sshd
В выводе должна быть строка active:
sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled)
Active: active (running) since Mon 2017-03-20 11:00:22 EDT; 1 months 1 days ago
Process: 899 ExecStartPre=/usr/sbin/sshd-keygen (code=exited, status=0/SUCCESS)
Main PID: 906 (sshd)
CGroup: /system.slice/sshd.service
├─ 906 /usr/sbin/sshd -D
├─26941 sshd: [accepted]
└─26942 sshd: [net]
Если сервис не работает, вы увидите в выводе inactive:
sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled)
Active: inactive (dead) since Fri 2017-04-21 08:36:13 EDT; 2s ago
Process: 906 ExecStart=/usr/sbin/sshd -D $OPTIONS (code=exited, status=0/SUCCESS)
Process: 899 ExecStartPre=/usr/sbin/sshd-keygen (code=exited, status=0/SUCCESS)
Main PID: 906 (code=exited, status=0/SUCCESS)
Чтобы перезапустить сервис, введите соответственно:
service ssh start
systemctl start sshd
Проверка порта SSH
Существует два основных способа проверить порт SSH: проверить конфигурационный файл SSH или просмотреть запущенный процесс.
Как правило, конфигурационный файл SSH хранится в /etc/ssh/sshd_config. Стандартный порт 22 может переопределяться любой строкой в этом файле, определяющей директиву Port.
Запустите поиск по файлу с помощью команды:
grep Port /etc/ssh/sshd_config
Читайте также: Использование Grep и регулярных выражений для поиска текстовых шаблонов в Linux
Команда вернёт:
Port 22
Если вы уже убедились, что сервис работает, теперь вы можете узнать, работает ли он на требуемом порте. Для этого используйте команду ss. Команда netstat –plnt выдаст аналогичный результат, но команду ss рекомендуется использовать для запроса информации сокета из ядра.
ss -plnt
В выводе должно быть указано имя программы и порт, который она прослушивает. Например, следующий вывод сообщает, что сервис SSH прослушивает все интерфейсы и порт 22.
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:* users:(("sshd",pid=1493,fd=3))
LISTEN 0 128 :::22 :::* users:(("sshd",pid=1493,fd=4))
Символ * и 0.0.0.0 указывает, что все интерфейсы сервера прослушиваются. Строка 127.0.0.1 значит, что сервис не является общедоступным. В sshd_config директива ListenAddress должна быть закомментирована, чтобы прослушивать все интерфейсы, или должна содержать внешний IP-адрес сервера.
Если у вас не получается самостоятельно настроить соединение SSH, вы можете обратиться за помощью к службе поддержки своего хостинг-провайдера.
Tags: firewalld, Iptables, OpenSSH, PuTTY, SSH, UFW
A connection timeout means that the client attempted to establish a network socket to the SSH server, but the server failed to respond within the timeout period.
ssh: connect to host 203.0.113.0 port 22: Connection timed out
In PuTTY, you might see an error window with text like this:
Network error: Connection timed out
Get Your Free Linux training!
Join our free Linux training and discover the power of open-source technology. Enhance your skills and boost your career!
Start Learning Linux today — Free!
In this article, we will dive into this issue and see how to troubleshoot this error:
Table of Contents
Check SSH command syntax
The syntax for the SSH command is as follows:
ssh [options] [user@]hostname [command]
Here is a brief explanation of each part of the syntax:
- ssh – This is the command to initiate the SSH connection.
- [options] – This is an optional parameter that allows you to specify additional options to configure the SSH connection. For example, you can use the -p option to specify a non-standard SSH port.
- [user@]hostname – This is the remote host that you want to connect to. You can optionally specify a username to use for the SSH connection. If you omit the username, the default username for your current session will be used.
- [command] – This is an optional parameter that allows you to specify a command to run on the remote host after the SSH connection is established. If you omit this parameter, you will be dropped into an interactive shell on the remote host.
Here is an example of how to use the SSH command to connect to a remote host:
ssh [email protected]
This will initiate an SSH connection to the host example.com using the username username.
If you have already set up SSH keys, you will be logged in without being prompted for a password. If not, you will be prompted to enter your password.
Enable verbose output in SSH command
The ssh -vvv command is used to establish an SSH connection to a remote server with verbose output enabled. The -v flag stands for “verbose,” and it can be used up to three times in a row (i.e., -v, -vv, -vvv) to increase the level of detail in the output. Here’s what each level of verbosity provides:
- -v: Verbose mode, displays debug messages about the authentication process and other connection details.
- -vv: Provides additional debug information and more details about the connection process.
- -vvv: Provides the most detailed output, including debugging information about the SSH handshake and messages exchanged during the connection process.
Using the -vvv flag is helpful when troubleshooting SSH connection issues, as it provides a wealth of information that can help pinpoint the problem.
However, keep in mind that the output can be quite verbose and overwhelming, so it’s usually best to start with the -v or -vv flags and work your way up to -vvv if needed.
Confirm that the server is correct
To confirm that the server’s IP address is correct, you can use ping command and follow these steps:
Identify the server that you want to connect to. This could be a domain name, a hostname, or an IP address.
Open a command prompt or terminal window on your local machine.
Type the following command, replacing server_address with the domain name, hostname, or IP address of the server:
ping server_address
This will send a small packet of data to the server and wait for a response. If the hostname is resolvable, you should see a series of responses.
Look at the IP address displayed in the ping results to confirm that it matches the expected IP address for the server.
If the hostname is not resolvable, you will see a message indicating that the hostname could not be resolved.
In this case, you may need to check your DNS settings or use a different hostname or IP address to connect to the server.
Check that the network allows SSH traffic over the port being used.
Some public networks may block port 22 or custom SSH ports.To check if the network allows SSH traffic over the port being used, you can follow these steps:
Identify the port number being used for SSH on the server. The default port number for SSH is 22, but some servers may use a custom port number.
Open a command prompt or terminal window on your local machine.
Type the following command, replacing port_number with the port number being used for SSH:
telnet server_address port_number
This will attempt to establish a connection to the server using the Telnet protocol on the specified port. If the network allows SSH traffic on this port, you should see a message indicating that the connection was successful.
If the network does not allow SSH traffic on this port, you will see a message indicating that the connection could not be established.
If the network is blocking SSH traffic on the port being used, you may need to use a different port number for SSH, or configure the network to allow SSH traffic on the current port.
For example, to check if the SSH port (port 22) is open on a remote server with the IP address 192.168.1.1, you can use the following command:
telnet 192.168.1.1 22
If the port is open, you will see something like this:
Trying 192.168.1.1...
Connected to 192.168.1.1.
Escape character is '^]'.
Press CTRL + ] and then type quit to exit.
If the port is not open, you will see an error message like this:
Trying 192.168.1.1...
telnet: Unable to connect to remote host: Connection refused
Verify the firewall rules on both the client and server
Identify the firewall software that is running on both the client and server machines. Common firewall software includes iptables on Linux and Windows Firewall on Windows.
Check the firewall rules on both the client and server to ensure that they are not set to DROP traffic by default. If the default policy is set to DROP, incoming traffic will be blocked by default and will need to be explicitly allowed.
Check that the SSH port is permitted for incoming connections. By default, SSH uses port 22, but some servers may use a custom port number.
On Linux machines with iptables, you can use the following command to list the current firewall rules:
sudo iptables -L
On Windows machines, you can use the Windows Firewall with Advanced Security console to view and manage firewall rules.
Look for a rule that allows incoming traffic on the SSH port. If such a rule exists, the SSH port is permitted for incoming connections. If there is no such rule, you may need to create a new rule to allow incoming traffic on the SSH port.
On Linux machines with iptables, you can use the following command to add a new rule to allow incoming traffic on the SSH port:
sudo iptables -A INPUT -p tcp --dport ssh -j ACCEPT
This command adds a new rule to the INPUT chain of the iptables firewall to accept incoming traffic on the SSH port. The -p tcp option specifies that the rule applies to TCP traffic, and the –dport ssh option specifies the destination port as the SSH port (port 22 by default). Finally, the -j ACCEPT option tells iptables to accept incoming traffic that matches the specified rule.
Note that this command only adds the new rule temporarily and will be lost when the system is rebooted. To make the rule persistent, you will need to save the iptables configuration. This can be done using the following command:
sudo iptables-save > /etc/sysconfig/iptables
This command saves the current iptables configuration to the /etc/sysconfig/iptables file, which is read at boot time to restore the firewall rules.
Increase the timeout value for the SSH command
To increase the timeout value for the SSH command, you can use the -o option with the ServerAliveInterval parameter. This option sets the time interval (in seconds) between sending packets to the server to request a response and keep the connection alive.
For example, to set the timeout value to 120 seconds (2 minutes), you can use the following command:
ssh -o ServerAliveInterval=120 username@hostname
This will send a packet every 120 seconds to the server to keep the connection alive. If the server does not respond to any of these packets within the specified interval, the connection will be closed and the SSH command will time out.
