| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1 Windows 2016 and 10 Windows Server 2019 and 2022 Windows Server 2025 |
|
Category • Subcategory |
Logon/Logoff • Logon |
| Type | Success |
|
Corresponding events in Windows 2003 and before |
528 , 540
|
4624: An account was successfully logged on
On this page
- Description of this event
- Field level details
- Examples
This is a highly valuable event since it documents each and every successful attempt to logon to the local computer regardless of logon type, location of the user or type of account. You can tie this event to logoff events 4634 and 4647 using Logon ID.
Win2012 adds the Impersonation Level field as shown in the example.
Win2016/10 add further fields explained below.
Free Security Log Resources by Randy
- Free Security Log Quick Reference Chart
- Windows Event Collection: Supercharger Free Edtion
- Free Active Directory Change Auditing Solution
- Free Course: Security Log Secrets
Description Fields in
4624
Subject:
Identifies the account that requested the logon — NOT the user who just logged on. Subject is usually Null or one of the Service principals and not usually useful information. See New Logon for who just logged on to the sytem.
- Security ID
- Account Name
- Account Domain
- Logon ID
Logon Information:
- Logon Type: See below
Remaining logon information fields are new to Windows 10/2016
- Restricted Admin Mode: Normally «-«.»Yes» for incoming Remote Desktop Connections where the client specified /restrictedAdmin on the command line. Restricted admin mode is an important way to limit the spread of admin credentials in ways they can be harvested by malware using pass-the-hash and related techniques. You should only see with for logon type 10. When you remote desktop into a server with /restrictedAdmin you get full authority on that server but it doesn’t carry with you if you access other systems from within that RDP session. This field allows you to detect RDP sessions that fail to use restricted admin mode.
- Virtual Account: Normally «No». This will be Yes in the case of services configured to logon with a «Virtual Account». Virtual Accounts only come up in Service logon types (type 5), when Windows starts a logon session in connection with a service starting up. You can configure services to run as a virtual account which is what Microsoft calls a «managed local account». They’re «domain» is «NT Service» as in an instance of MS SQL Server named Supercharger running as NT SERVICE\MSSQL$SUPERCHARGER.
- Elevated Token: Yes or No. It will be Yes if the user is a member of Administrators — kind of… The «kind of» applies to interactive logons, when you are an admin and you have User Account Control (UAC) enabled. Then when you logon you actually get 2 logon sessions. One without the Administrators SID and related privileges in your security token and another session with all that authority. Everything you do happens under the unprivileged logon session until you attempt to run something requiring admin authority. After you approve the UAC dialog box, Windows runs that one operation under the other logon sesson. So in the log you will see 2 of these events, one where this field is Yes and other No. The 2 logon sessions are connected by the Linked Logon ID described below.
Remaining logon information fields are new to Windows 2025
- Remote Credential Guard: Normally «-«.
Logon Type:
This is a valuable piece of information as it tells you HOW the user just logged on:
|
Logon Type |
Description |
| 2 | Interactive (logon at keyboard and screen of system) |
| 3 | Network (i.e. connection to shared folder on this computer from elsewhere on network) |
| 4 | Batch (i.e. scheduled task) |
| 5 | Service (Service startup) |
| 7 | Unlock (i.e. unnattended workstation with password protected screen saver) |
| 8 | NetworkCleartext (Logon with credentials sent in the clear text. Most often indicates a logon to IIS with «basic authentication») See this article for more information. |
| 9 | NewCredentials such as with RunAs or mapping a network drive with alternate credentials. This logon type does not seem to show up in any events. If you want to track users attempting to logon with alternate credentials see 4648. MS says «A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity, but uses different credentials for other network connections.» |
| 10 | RemoteInteractive (Terminal Services, Remote Desktop or Remote Assistance) |
| 11 | CachedInteractive (logon with cached domain credentials such as when logging on to a laptop when away from the network) |
Impersonation Level: (Win2012 and later)
From MSDN
| Anonymous | Anonymous COM impersonation level that hides the identity of the caller. Calls to WMI may fail with this impersonation level. |
| Default | Default impersonation. |
| Delegate | Delegate-level COM impersonation level that allows objects to permit other objects to use the credentials of the caller. This level, which will work with WMI calls but may constitute an unnecessary security risk, is supported only under Windows 2000. |
| Identify | Identify-level COM impersonation level that allows objects to query the credentials of the caller. Calls to WMI may fail with this impersonation level. |
| Impersonate | Impersonate-level COM impersonation level that allows objects to use the credentials of the caller. This is the recommended impersonation level for WMI calls. |
New Logon:
The user who just logged on is identified by the Account Name and Account Domain. You can determine whether the account is local or domain by comparing the Account Domain to the computer name. If they match, the account is a local account on that system, otherwise a domain account.
- Security ID: the SID of the account
- Account Name: Logon name of the account
- Account Domain: Domain name of the account in either the DNS name (can be upper or lowercase) or pre-Win2k NETBIOS domain name. In the case of special subjects (well known security principals) like SYSTEM, LOCAL SERVICE, NETWORK SERVICE, ANONYMOUS LOGON this field will be «NT AUTHORITY». It can also be «NT Service» as in the case of virtual accounts for services. See above. Finally, if the account is a local account, this field will be the name of the computer.
- Logon ID: a semi-unique (unique between reboots) number that identifies the logon session just initiated. Any events logged subsequently during this logon session will report the same Logon ID through to the logoff event 4647 or 4634.
- Linked Login ID: (Win2016/10) This is relevant to User Account Control and interactive logons. When an admin logs on interactively to a system with UAC enabled, Windows actually creates 2 logon sessions — one with and one without privilege. This is called a split token and this fields links the 2 sessions to each other. See Elevated Token above.
- Network Account Name: (Win2016/10) This will be «-» unless the logon type is NewCredentials aka 9, then it will be the user name that is used for outbound network connections.
- Network Account Domain: (Win2016/10) see above
- Logon GUID: Supposedly you should be able to correlate logon events on this computer with corresonding authentication events on the domain controller using this GUID. Such as linking 4624 on the member computer to 4769 on the DC. But the GUIDs do not match between logon events on member computers and the authentication events on the domain controller.
Process Information:
- Process ID is the process ID specified when the executable started as logged in 4688.
- Process Name: identifies the program executable that processed the logon. This is one of the trusted logon processes identified by 4611.
Network Information:
This section identifies WHERE the user was when he logged on. Of course if logon is initiated from the same computer this information will either be blank or reflect the same local computers.
- Workstation Name: the computer name of the computer where the user is physically present in most cases unless this logon was intitiated by a server application acting on behalf of the user. Workstation may also not be filled in for some Kerberos logons since the Kerberos protocol doesn’t really care about the computer account in the case of user logons and therefore lacks any field for carrying workstation name in the ticket request message.
- Source Network Address: the IP address of the computer where the user is physically present in most cases unless this logon was intitiated by a server application acting on behalf of the user. If this logon is initiated locally the IP address will sometimes be 127.0.0.1 instead of the local computer’s actual IP address. This field is also blank sometimes because Microsoft says «Not every code path in Windows Server 2003 is instrumented for IP address, so it’s not always filled out.»
- Source Port: identifies the source TCP port of the logon request which seems useless since with most protocols source ports are random.
Detailed Authentication Information:
- Logon Process: (see 4611) CredPro indicates a logon initiated by User Account Control
- Authentication Package: (see 4610 or 4622)
- Transited Services: This has to do with server applications that need to accept some other type of authentication from the client and then transition to Kerberos for accessing other resources on behalf of the client. See http://msdn.microsoft.com/msdnmag/issues/03/04/SecurityBriefs/. MS says: Transmitted services are populated if the logon was a result of a S4U (Service For User) logon process. S4U is a Microsoft extension to the Kerberos Protocol to allow an application service to obtain a Kerberos service ticket on behalf of a user – most commonly done by a front-end website to access an internal resource on behalf of a user. For more information about S4U, see https://msdn.microsoft.com/en-us/library/cc246072.aspx
- Package name: If this logon was authenticated via the NTLM protocol (instead of Kerberos for instance) this field tells you which version of NTLM was used. See security option «Network security: LAN Manager authentication level». This field only populated if Authentication Package = NTLM. Possible values: “NTLM V1”, “NTLM V2”, “LM”
- Key Length: Length of key protecting the «secure channel». See security option «Domain Member: Require strong (Windows 2000 or later) session key». If value is 0 this would indicate security option «Domain Member: Digitally encrypt secure channel data (when possible)» failed. MS says the length of NTLM Session Security key. Typically it has 128 bit or 56 bit length. This parameter is always 0 if “Authentication Package” = “Kerberos”, because it is not applicable for Kerberos protocol. This field will also have “0” value if Kerberos was negotiated using Negotiate authentication package.
Supercharger Enterprise
Load Balancing for Windows Event Collection
Examples of 4624
Windows 11 and 2025
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: DESKTOP-LLHJ389$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon Information:
Logon Type: 7
Restricted Admin Mode: —
Remote Credential Guard: —
Virtual Account: No
Elevated Token: No
Impersonation Level: Impersonation
New Logon:
Security ID: AzureAD\RandyFranklinSmith
Account Name: rsmith@montereytechgroup.com
Account Domain: AzureAD
Logon ID: 0xFD5113F
Linked Logon ID: 0xFD5112A
Network Account Name: —
Network Account Domain: —
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x30c
Process Name: C:\Windows\System32\lsass.exe
Network Information:
Workstation Name: DESKTOP-LLHJ389
Source Network Address: —
Source Port: —
Detailed Authentication Information:
Logon Process: Negotiat
Authentication Package: Negotiate
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
Windows 10 and 2016/2019/2022
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: DESKTOP-LLHJ389$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon Information:
Logon Type: 7
Restricted Admin Mode: —
Remote Credential Guard: —
Virtual Account: No
Elevated Token: No
Impersonation Level: Impersonation
New Logon:
Security ID: AzureAD\RandyFranklinSmith
Account Name: rsmith@montereytechgroup.com
Account Domain: AzureAD
Logon ID: 0xFD5113F
Linked Logon ID: 0xFD5112A
Network Account Name: —
Network Account Domain: —
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x30c
Process Name: C:\Windows\System32\lsass.exe
Network Information:
Workstation Name: DESKTOP-LLHJ389
Source Network Address: —
Source Port: —
Detailed Authentication Information:
Logon Process: Negotiat
Authentication Package: Negotiate
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
Win2012
An account was successfully logged on.
Subject:
Security ID: NULL SID
Account Name: —
Account Domain: —
Logon ID: 0x0
Logon Type: 3
Impersonation Level: Impersonation
New Logon:
Security ID: LB\DEV1$
Account Name: DEV1$
Account Domain: LB
Logon ID: 0x894B5E95
Logon GUID: {f09e5f81-9f19-5f11-29b8-8750c7c02be3}
Process Information:
Process ID: 0x0
Process Name: —
Network Information:
Workstation Name:
Source Network Address: 10.42.1.161
Source Port: 59752
Detailed Authentication Information:
Logon Process: Kerberos
Authentication Package: Kerberos
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
Win2008
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: WIN-R9H529RIO4Y$
Account Domain: WORKGROUP
Logon ID: 0x3e7
Logon Type:10
New Logon:
Security ID: WIN-R9H529RIO4Y\Administrator
Account Name: Administrator
Account Domain: WIN-R9H529RIO4Y
Logon ID: 0x19f4c
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x4c0
Process Name: C:\Windows\System32\winlogon.exe
Network Information:
Workstation Name: WIN-R9H529RIO4Y
Source Network Address: 10.42.42.211
Source Port: 1181
Detailed Authentication Information:
Logon Process: User32
Authentication Package: Negotiate
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection
- The Changing Landscape of Authentication and Logon Tracking in Hybrid Environments of Entra and AD
При расследовании различных инцидентов администратору необходимо получить информацию кто и когда заходил на определенный компьютер Windows. Историю входов пользователя в доменной сети можно получить из журналов контроллеров домена. Но иногда проще получить информацию непосредсвенно из логов компьютера. В этой статье мы покажем, как получить и проанализировать историю входа пользователей на компьютер/сервер Windows. Такая статистика поможет вам ответить на вопрос “Как в Windows проверить кто и когда использовал этот компьютере”.
Содержание:
- Настройка политики аудита входа пользователей в Windows
- Поиск событий входа пользователей в журнале событий Windows
- Анализ событий входа пользователей в Windows с помощью PowerShell
Настройка политики аудита входа пользователей в Windows
Сначала нужно включить политик аудита входа пользователей. На отдельностоящем компьютере для настройки параметров локальной групповой политики используется оснастка gpedit.msc. Если вы хотите включить политику для компьютеров в домене Active Directorty, нужно использовать редактор доменных GPO (
gpmc.msc
).
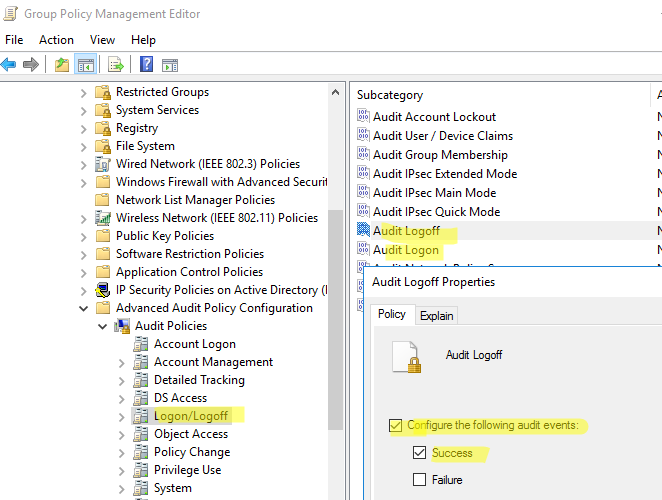
- Запустите консоль GPMC, создайте новую GPO и назначьте ее на Organizational Units (OU) с компьютерами и / или серверами, для которых вы хотите включить политику аудита событий входа;
- Откройте объект GPO и перейдите в раздел Computer Configuration -> Policies -> Windows Settings -> Security Settings –> Advanced Audit Policy Configuration -> Audit Policies -> Logon/Logoff;
- Включите две политики аудита Audit Logon и Audit Logoff. Это позволит отслеживать как события входа, так и события выхода пользователей. Если вы хотите отслеживать только успешные события входа, включите в настройках политик только опцию Success;
- Закройте редактор GPO и обновите настройки политик на клиентах.
Поиск событий входа пользователей в журнале событий Windows
После того как вы включили политики аудита входа, при каждом входе пользователя в Windows в журнале Event Viewer будет появляться запись о входе. Посмотрим, как она выглядит.
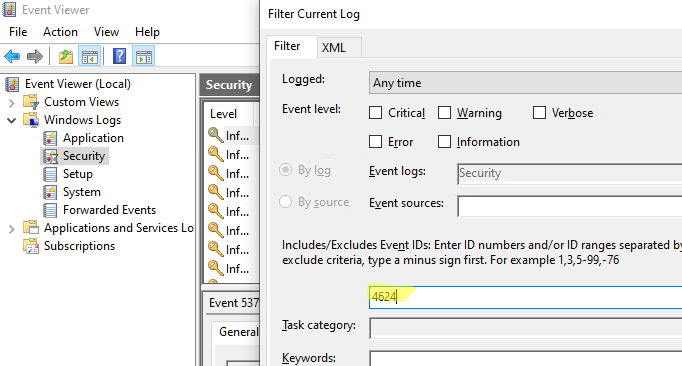
- Откройте оснастку Event Viewer (
eventvwr.msc
); - Разверните секцию Windows Logs и выберите журнал Security;
- Щелкните по нему правой клавишей и выберите пункт Filter Current Log;
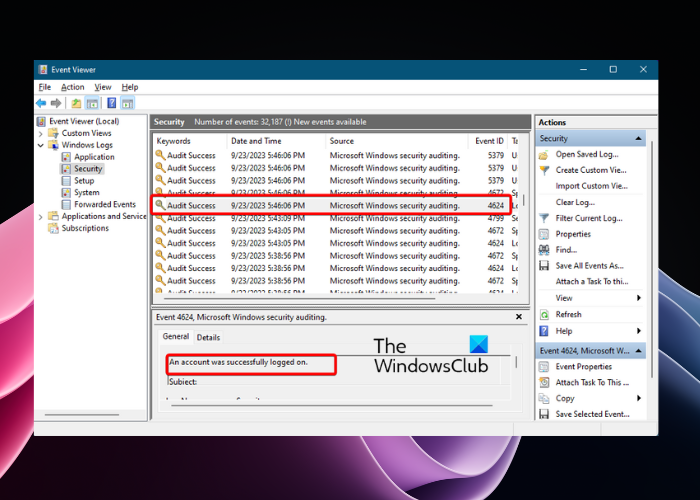
- В поле укажите ID события 4624 и нажмите OK;
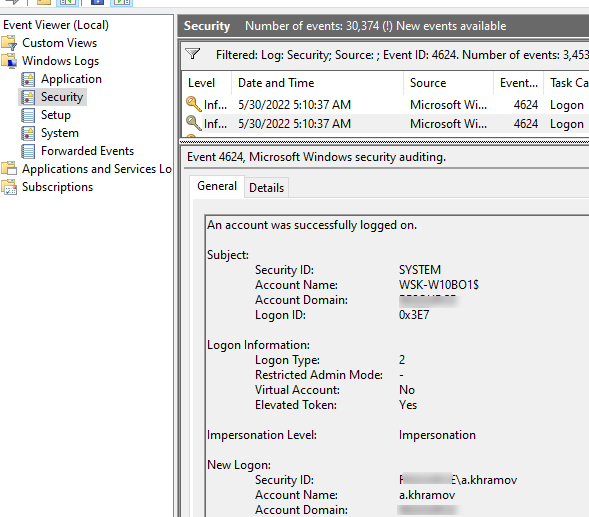
- В окне события останутся только события входа пользователей, системных служб с описанием
An account was successfully logged on
; - В описании события указано имя и домен пользователя, вошедшего в систему:
New Logon: Security ID: WINITPRO\a.khramov Account Name: a.khramov Account Domain: WINITPRO
Ниже перечислены другие полезные EventID:
| Event ID | Описание |
| 4624 | A successful account logon event |
| 4625 | An account failed to log on |
| 4648 | A logon was attempted using explicit credentials |
| 4634 | An account was logged off |
| 4647 | User initiated logoff |
Если полистать журнал событий, можно заметить, что в нем присутствуют не только события входа пользователей на компьютер. Здесь также будут события сетевого доступа к этому компьютеру (при открытии по сети общих файлов или печати на сетевых принтерах), запуске различных служб и заданий планировщика и т.д. Т.е. очень много лишний событий, которые не относятся ко входу локального пользователя. Чтобы выбрать только события интерактивного входа пользователя на консоль компьютера, нужно дополнительно сделать выборку по значению параметра Logon Type. В таблице ниже перечислены коды Logon Type.
| Код Logon Type | Описание |
|---|---|
| 0 | System |
| 2 | Interactive |
| 3 | Network |
| 4 | Batch |
| 5 | Service |
| 6 | Proxy |
| 7 | Unlock |
| 8 | NetworkCleartext |
| 9 | NewCredentials |
| 10 | RemoteInteractive |
| 11 | CachedInteractive |
| 12 | CachedRemoteInteractive |
| 13 | CachedUnlock |
При удаленном подключении к рабочему столу компьютера по RDP, в журнале событий появится записи с Logon Type 10 или 3. Подробнее об анализе RDP логов в Windows.
В соответствии с этой таблицей событие локального входа пользователя на компьютер должно содержать Logon Type: 2.
Для фильтрации события входа по содержать Logon Type лучше использовать PowerShell.
Анализ событий входа пользователей в Windows с помощью PowerShell
Допустим, наша задача получить информацию о том, какие пользователи входили на этот компьютер за последнее время. Нам интересует именно события интерактивного входа (через консоль) с
LogonType =2
. Для выбора события из журналов Event Viewer мы воспользуемся командлетом Get-WinEvent.
Следующий PowerShell скрипт выведет история входа пользователей на текущий компьютер и представит ее в виде графической таблицы Out-GridView.
$query = @'
<QueryList>
<Query Id='0' Path='Security'>
<Select Path='Security'>
*[System[EventID='4624']
and(
EventData[Data[@Name='VirtualAccount']='%%1843']
and
EventData[Data[@Name='LogonType']='2']
)
]
</Select>
</Query>
</QueryList>
'@
$properties = @(
@{n='User';e={$_.Properties[5].Value}},
@{n='Domain';e={$_.Properties[6].Value}},
@{n='TimeStamp';e={$_.TimeCreated}}
@{n='LogonType';e={$_.Properties[8].Value}}
)
Get-WinEvent -FilterXml $query | Select-Object $properties|Out-GridView
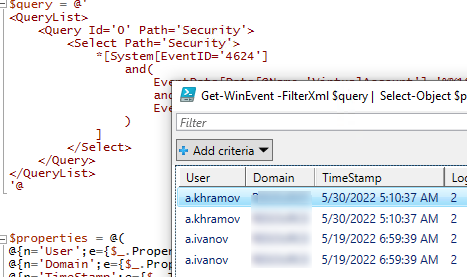
Если нужно выбрать события входа за последние несколько дней, можно добавить pipe с таким условием:
|Where-Object {$_.TimeStamp -gt '5/10/22'}
Командлет Get-WinEvent позволяет получить информацию с удаленных компьютеров. Например, чтобы получить историю входов с двух компьютеров, выполните следующий скрипт:
'msk-comp1', 'msk-comp2' |
ForEach-Object {
Get-WinEvent -ComputerName $_ -FilterXml $query | Select-Object $properties
}
Если протокол RPC закрыт между компьютерами, вы можете получить данные с удаленных компьютеров с помощью PowerShell Remoting командлета Invoke-Command:
Invoke-Command -ComputerName 'msk-comp1', 'msk-comp2' {Get-WinEvent -FilterXml $query | Select-Object $properties}
Время на прочтение4 мин
Количество просмотров309K

Рэнди Франклин Смит (CISA, SSCP, Security MVP) имеет в своем арсенале очень полезный документ, рассказывающий о том, какие события (event IDs) обязательно должны отслеживаться в рамках обеспечения информационной безопасности Windows. В этом документе изложена крайне полезная информация, которая позволит Вам “выжать” максимум из штатной системы аудита. Мы подготовили перевод этого материала. Заинтересованных приглашаем под кат.
О том, как настроить аудит, мы уже обстоятельно писали в одном из наших постов. Но из всех event id, которые встречаются в журналах событий, необходимо остановить свое внимание на нескольких критических важных. На каких именно – решать каждому. Однако Рэнди Франклин Смит предлагает сосредоточить внимание на 10 важных событиях безопасности в Windows.
Контроллеры доменов
Event ID — (Категория) — Описание
1) 675 или 4771
(Аудит событий входа в систему)
Событие 675/4771 на контроллере домена указывает на неудачную попытку войти через Kerberos на рабочей станции с доменной учетной записью. Обычно причиной этого является несоответствующий пароль, но код ошибки указывает, почему именно аутентификация была неудачной. Таблица кодов ошибок Kerberos приведена ниже.
2) 676, или Failed 672 или 4768
(Аудит событий входа в систему)
Событие 676/4768 логгируется для других типов неудачной аутентификации. Таблица кодов Kerberos приведена ниже.
ВНИМАНИЕ: В Windows 2003 Server событие отказа записывается как 672 вместо 676.
3) 681 или Failed 680 или 4776
(Аудит событий входа в систему)
Событие 681/4776 на контроллере домена указывает на неудачную попытку входа в систему через
NTLM с доменной учетной записью. Код ошибки указывает, почему именно аутентификация была неудачной.
Коды ошибок NTLM приведены ниже.
ВНИМАНИЕ: В Windows 2003 Server событие отказа записывается как 680 вместо 681.
4) 642 или 4738
(Аудит управления учетными записями)
Событие 642/4738 указывает на изменения в указанной учетной записи, такие как сброс пароля или активация деактивированной до этого учетной записи. Описание события уточняется в соответствие с типом изменения.
5) 632 или 4728; 636 или 4732; 660 или 4756
(Аудит управления учетными записями)
Все три события указывают на то, что указанный пользователь был добавлен в определенную группу. Обозначены Глобальная (Global), Локальная (Local) и Общая (Universal) соответственно для каждого ID.
6) 624 или 4720
(Аудит управления учетными записями)
Была создана новая учетная запись пользователя
7) 644 или 4740
(Аудит управления учетными записями)
Учетная запись указанного пользователя была заблокирована после нескольких попыток входа

(Аудит системных событий)
Указанный пользователь очистил журнал безопасности
Вход и выход из системы (Logon/Logoff)
Event Id — Описание
528 или 4624 — Успешный вход в систему
529 или 4625 — Отказ входа в систему – Неизвестное имя пользователя или неверный пароль
530 или 4625 Отказ входа в систему – Вход в систему не был осуществлен в течение обозначенного периода времени
531 или 4625 — Отказ входа в систему – Учетная запись временно деактивирована
532 или 4625 — Отказ входа в систему – Срок использования указанной учетной записи истек
533 или 4625 — Отказ входа в систему – Пользователю не разрешается осуществлять вход в систему на данном компьютере
534 или 4625 или 5461 — Отказ входа в систему – Пользователь не был разрешен запрашиваемый тип входа на данном компьютере
535 или 4625 — Отказ входа в систему – Срок действия пароля указанной учетной записи истек
539 или 4625 — Отказ входа в систему – Учетная запись заблокирована
540 или 4624 — Успешный сетевой вход в систему (Только Windows 2000, XP, 2003)
Типы входов в систему (Logon Types)
Тип входа в систему — Описание
2 — Интерактивный (вход с клавиатуры или экрана системы)
3 — Сетевой (например, подключение к общей папке на этом компьютере из любого места в сети или IIS вход — Никогда не заходил 528 на Windows Server 2000 и выше. См. событие 540)
4 — Пакет (batch) (например, запланированная задача)
5 — Служба (Запуск службы)
7 — Разблокировка (например, необслуживаемая рабочая станция с защищенным паролем скринсейвером)
8 — NetworkCleartext (Вход с полномочиями (credentials), отправленными в виде простого текст. Часто обозначает вход в IIS с “базовой аутентификацией”)
9 — NewCredentials
10 — RemoteInteractive (Терминальные службы, Удаленный рабочий стол или удаленный помощник)
11 — CachedInteractive (вход с кешированными доменными полномочиями, например, вход на рабочую станцию, которая находится не в сети)
Коды отказов Kerberos
Код ошибки — Причина
6 — Имя пользователя не существует
12 — Ограничение рабочей машины; ограничение времени входа в систему
18 — Учетная запись деактивирована, заблокирована или истек срок ее действия
23 — Истек срок действия пароля пользователя
24 — Предварительная аутентификация не удалась; обычно причиной является неверный пароль
32 — Истек срок действия заявки. Это нормальное событие, которое логгируется учетными записями компьютеров
37 — Время на рабочей машины давно не синхронизировалось со временем на контроллере домена
Коды ошибок NTLM
Код ошибки (десятичная система) — Код ошибки (16-ричная система) — Описание
3221225572 — C0000064 — Такого имени пользователя не существует
3221225578 — C000006A — Верное имя пользователя, но неверный пароль
3221226036 — C0000234 — Учетная запись пользователя заблокирована
3221225586 — C0000072 — Учетная запись деактивирована
3221225583 — C000006F — Пользователь пытается войти в систему вне обозначенного периода времени (рабочего времени)
3221225584 — C0000070 — Ограничение рабочей станции
3221225875 — C0000193 — Истек срок действия учетной записи
3221225585 — C0000071 — Истек срок действия пароля
3221226020 — C0000224 — Пользователь должен поменять пароль при следующем входе в систему
Еще раз продублируем ссылку на скачивание документа на сайте Рэнди Франклина Смита www.ultimatewindowssecurity.com/securitylog/quickref/Default.aspx. Нужно будет заполнить небольшую форму, чтобы получить к нему доступ.
P.S. Хотите полностью автоматизировать работу с журналами событий? Попробуйте новую версию NetWrix Event Log Manager 4.0, которая осуществляет сбор и архивирование журналов событий, строит отчеты и генерирует оповещения в режиме реального времени. Программа собирает данные с многочисленных компьютеров сети, предупреждает Вас о критических событиях и централизованно хранит данные обо всех событиях в сжатом формате для удобства анализа архивных данных журналов. Доступна бесплатная версия программы для 10 контроллеров доменов и 100 компьютеров.
You may often come across the Event ID 4624, An account was successfully logged on message in the Event Viewer during your routine audit. However, there’s nothing to worry about since this is a regular Windows security log generated whenever you successfully log into the computer. So, if at any time you need to check the user login history, you need to look for the Event ID 4624.
However, it can be a concern if an account does not appear familiar to you or if you suspect that your account may have been hacked. In such a case, you need to review the Windows Security Log in the Event Viewer properly to identify any threats and eliminate them accordingly.
Having said that, we have a detailed guide to help you understand everything about Windows Event ID 4624 and how to detect any problems.
What is the 4624 Event ID?
Event ID 4624 in the Windows Event Log indicates every successful login session on the destination computer. This audit setting generates on the machine you accessed and where you created the session. So, if anyone is snooping around on your computer, this is the Event ID you need to look for.
Besides, this is a piece of highly valuable information that tells you exactly who (user) logged on and from which account. For this, you can check the New Logon field that shows the following details:
- Security ID
- Account Name
- Account Domain
- Login ID
However, we will also explain the other properties related to Event ID 4624 below.
Note – You can configure this audit setting in the Local Security Policy or Group Policy Editor (gpedit.msc). Then, you can alter the auditing options to observe successful login attempts for security purposes. However, these settings can only record events on the local computer and not on the domain controller.
Windows Event ID 4624 properties
You can find the properties of an Event ID under the General tab. Here, you will find the below fields:
1] Subject
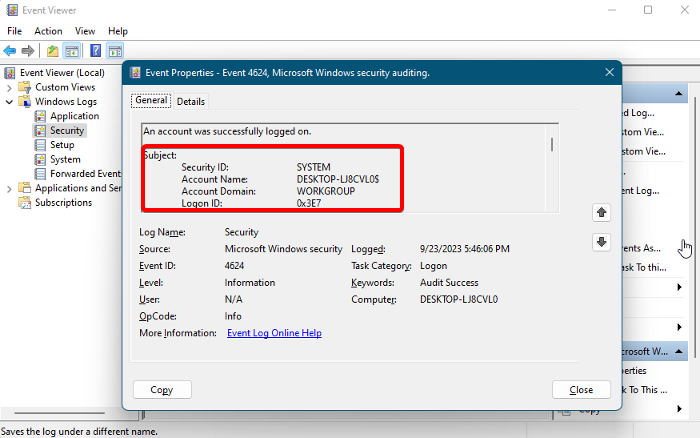
Security ID (SID):
It denotes that there was a successful login.
Account name
Name of the account that recorded a successful login. This helps you to identify if it’s a legitimate account.
Account Domain
The domain of the account/the computer name that recorded the event is useful for troubleshooting.
Logon ID
Denotes a hexadecimal value that can be helpful to associate this event with any of the recent events that may have the same Logon ID. Moreover, it also helps you identify any issues with the events and troubleshoot accordingly.
Read: How to disable Windows Event Log
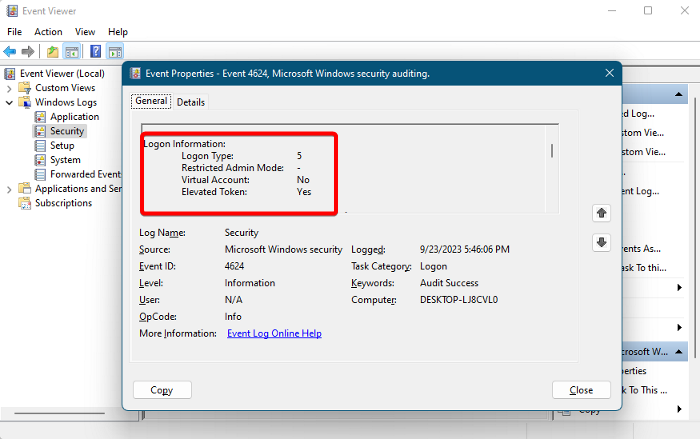
2] Logon Information
This property includes the following:
Logon Type
| Logon Type | Logon Title | Description |
|---|---|---|
| 0 | System | Used solely by the System account, such as, during the system startup. |
| 2 | Interactive | A user logged on to this computer. |
| 3 | Network | A user or computer logged on to the current workstation from the network. |
| 4 | Batch | Used by batch servers, where processes may be running on behalf of a user without their direct involvement. |
| 5 | Service | A service was started by the Service Control Manager. |
| 7 | Unlock | This computer was unlocked. |
| 8 | NetworkCleartext | A user logged on to this computer from the network. The user’s password was then passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials do not traverse the network in plaintext (also called cleartext). |
| 9 | NewCredentials | A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity but uses different credentials for other network connections. |
| 10 | RemoteInteractive | A user logged on to this computer remotely using Terminal Services or Remote Desktop. |
| 11 | CachedInteractive | A user logged on to this computer with network credentials that were stored locally on the computer. The domain controller was not contacted to verify the credentials. |
| 12 | CachedRemoteInteractive | Same as RemoteInteractive. This is used for internal auditing. |
| 13 | CachedUnlock | Workstation logon. |
*Data courtesy – Microsoft
Restricted Admin Mode
You only see this when a user successfully logs on remotely via the Terminal Services or Remote Desktop. The value of Restricted Admin Mode is a boolean, that is, Yes or No.
Virtual Account
Again, the value of a Virtual Account is either a Yes or No. This indicates whether the account that documented the successful logon is a virtual account or not. For example, Managed Service Account.
Elevated Token
This is again a Yes or No field, denoting whether the account that initiated the successful logon (event ID 4624) is an admin account or not.
3] Impersonation Level
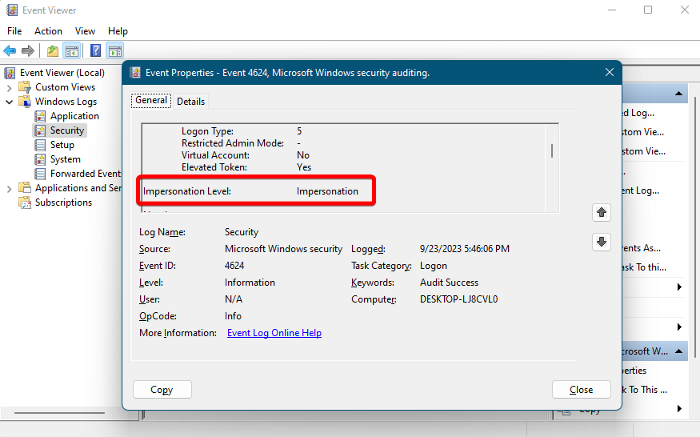
This field indicates how much a process in the login session impersonates (simulates). It’s the level of authority permitted by the server to mimic a client on his behalf. The 4 different levels are Anonymous, Identification, Impersonation, and Delegation.
Read: The security log is now full (Event ID 1104)
4] New Logon
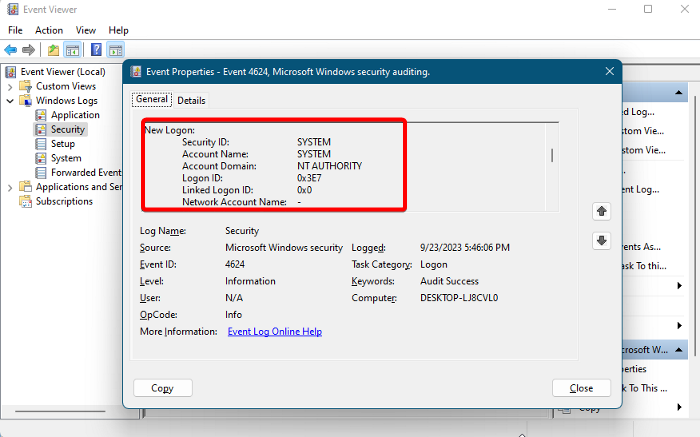
This is the account that actually logged on and for which the logon session was created. You can compare the computer name with the account domain to identify if it’s local or domain. If it matches, it’s local; if not, then it’s the domain account.
Furthermore, it’s divided into two categories: Account and Network Information:
Account Information
- Security ID – SID that recorded the successful logon of the Windows Security Event ID 4624.
- Account Name – Carries out the successful logon.
- Account Domain – The domain name could be in either of the following formats: NeTBIOS name of the domain, in lowercase, or in uppercase formats. But if the Account Domain shows NT AUTHORITY, it means that the logon account is a LOCAL SERVICE or ANONYMOUS LOGON.
- Logon ID – It displays a hexadecimal value that’s useful for troubleshooting.
- Linked Logon ID – Again a hexadecimal value relative to the Logon session. If there are no related logon events, the value is 0x0.
- GUID – Allows you to link two events one of which is the Event ID 4624 and the other with the same GUID, thus, helping you to identify a potential threat.
Network Information
- Network Account Name – Only relevant to the NewCredentials logon type, however, if the logon type is something else, then the Network Account Name is documented as “–“.
- Network Account Domain – Only applicable to the NewCredentials logon type. If the user wants to create a network connection, they will need to use the domain name as specified in this field. But if the logon type is something else, it would be recorded as “–“.
5] Process Information
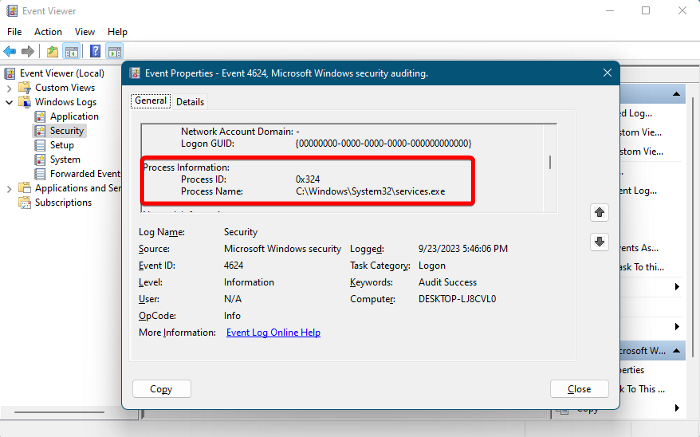
This field provides details regarding the process that documented the successful logon event.
- Process ID – It displays a hexadecimal value that Windows and other OS use to identify a process exclusively. To view the Process ID of all processes that are currently running on your Windows PC, launch PowerShell, run the Get-Process command and hit Enter. Now, change the hexadecimal value of the Process ID into decimal in the event ID 4624. This helps you to compare the process ID to one of the IDs generated by the Get-Process PowerShell command.
- Process Name – Documents the successful logon.
Read: Event ID 1101, Audit events have been dropped by the transport. 0
6] Network Information
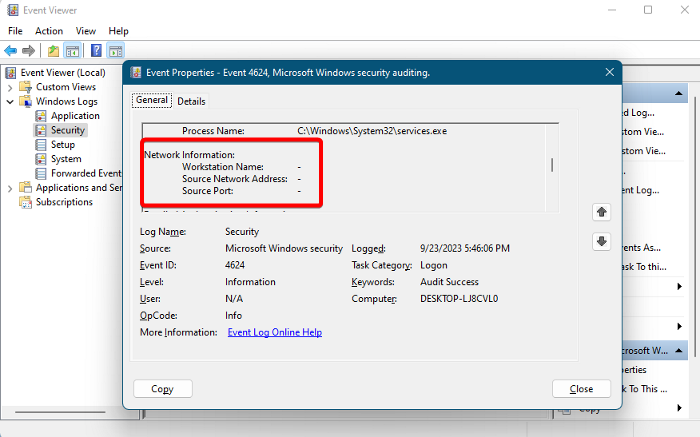
This section offers you important information related to troubleshooting purposes. For example, which computer the user logged in from, the IP address of the PC and the port used.
- Workstation Name – Documents the PC name from which the user logged in.
- Source Network Address – Registers the IP address of the PC from which the user logged in.
- Source Port – Records the original TCP port of the remote machine which was used to log in.
7] Detailed Authentication Information
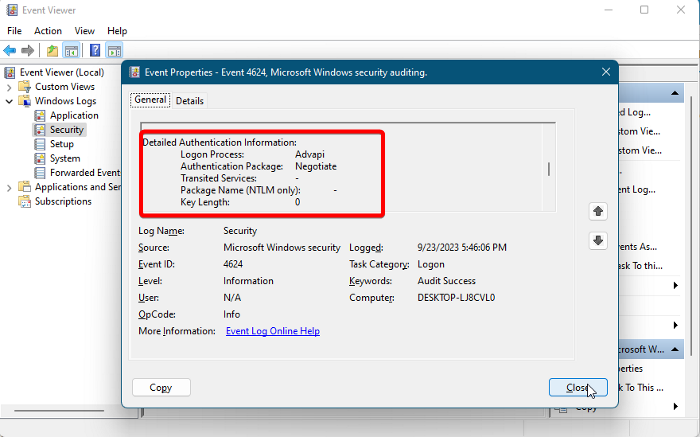
This field represents how the authentication process is initiated. It maintains a record of the process in which the authentication and the package was used. It also shows other details like Transited Services, Package Name, and Key Length.
- Logon Process – It displays the name of the authenticated logon process the user used to logon when the system recorded the Windows Event ID 4624.
- Authentication Package – Registers the authentication package type that was used to logon to this computer.
- Transited Services – Shows only transmitted services (for only Kerberos).
- Package Name – It documents the NTLM version if the logon request was authenticated by the NTLM protocol.
- Key Length – Only applicable for NTLM authentication Protocol. For others, the field returns 0.
In addition, for Event ID 4624, Microsoft has some additional recommendations for the type of monitoring required based on the situation.
What is Event ID 4625?
Event ID 4625 registers whenever the user fails to log in to a local computer. This event is populated on the device from where the user tried to log in. Moreover, to identify failed logons, you can create a PowerShell script that can help you find the Windows Event logs with the Event ID 4625.
What is Event ID 4634?
Event ID 4634 indicates that an account was logged off. This means that whenever a logon session is ended (logged out), Event 4634 is generated. However, this differs from the Event ID 4647, which denotes that a user started the logoff. In this case, it simply registered that a session is no longer running and has ended.
Event ID 4624 is a critical event in Windows security auditing and monitoring, signaling a successful account logon. This event is generated on the machine where the logon session was created, typically a user’s workstation or a server acting as a destination of a remote logon request (e.g., RDP, network share access). Analyzing these events is essential for security operations to track user activities, detect unauthorized access, and ensure compliance with security policies.
Key Details of Event ID 4624
-
Log Location: Security log.
-
%SYSTEM ROOT%\System32\winevt\logs\Security.evtx
-
Event ID 4624 is logged whenever an account successfully logs on to a system. This includes various scenarios such as:
-
A user logs on to their workstation.
-
A user accesses another computer over the network.
-
A service starts with a specific user account.
-
Scheduled tasks initiate using a user’s credentials.
Information Contained in the Log
An Event ID 4624 log contains several pieces of crucial information:
-
: Indicates the logon method (interactive, network, remote desktop, batch, service, etc.). Each logon type has a specific number associated with it, which helps in understanding the context of the logon.
-
Subject: Information about the account that requested the logon (not always applicable).
-
Security ID: The SID of the account.
-
Account Name: The name of the account.
-
Account Domain: The domain of the account.
-
Logon ID: A value that identifies the logon session. This can be useful for correlating to other events related to the same session.
-
-
Logon Information: Details about the user and session.
-
User Name and Domain: The name and domain of the user who logged on.
-
Logon ID: Uniquely identifies the logon session.
-
Logon GUID: A GUID that identifies the logon session.
-
Authentication Package: The name of the authentication package that processed the logon request.
-
-
Network Information: Details about network logons.
-
Workstation Name: The name of the workstation from which the logon request originated.
-
Source Network Address and Port: Indicates the source IP address and port number for the logon request (mainly applicable for remote logons).
-
-
Detailed Authentication Information: Provides details about the authentication process.
-
Logon Process: The process that managed the logon.
-
Authentication Package: The package that was used to authenticate the user.
-
Transited Services: Lists the services that participated in the logon request.
-
Package Name (NTLM only): Shows the NTLM package name if NTLM was used for authentication.
-
-
Impersonation Level: Indicates the level of impersonation (e.g., impersonation, delegation).
Analyzing Event ID 4624 entries is crucial for several reasons:
-
Access Tracking and User Activity Monitoring: Helps in understanding user behavior by tracking when and how users log on to systems.
-
Unauthorized Access Detection: By analyzing logon patterns and types, it’s possible to detect unusual or unauthorized access attempts.
-
Forensic Analysis: In the event of a security incident, these logs provide invaluable insights into the actions taken by users or attackers.
-
Compliance: Many regulatory frameworks require detailed logging of user activities, including successful logon attempts.
Tools and Strategies for Analysis
-
Windows Event Viewer: Allows for manual inspection and filtering of event logs.
-
PowerShell: Scripts can automate the extraction and analysis of 4624 events for patterns or anomalies.
-
SIEM Systems: Aggregate 4624 events from across the environment to provide centralized monitoring and alerting on suspicious activities.
-
Alerting Mechanisms: Configuring alerts for anomalous logon patterns (e.g., logons at unusual hours, logon types that are uncommon for a user) can help in quickly detecting potential security issues.