In this guide, I share my Windows Defender Firewall Best Practices and tips.
Most of these best practices are geared towards enterprise networks that use group policy or Intune.
These are the settings I’ve used in the real world. They took careful planning, lots of testing, and approval. No two networks or organizations are the same, so these settings may not work for you. I recommend you test and get approval before making changes to production systems.
List of Firewall Best Practices:
- Centrally Manage The Firewall with Group Policy
- Create a Baseline Firewall Policy
- Create Separate GPOs for Specific Rules
- Leave Default Inbound & Outbound Rules
- Enable All Firewall Profiles
- Disable Rule Merging
- Enable Logs
- Limit the Scope of Firewall Rules
- Enable the Firewall
- Firewall Rule Naming Convention
- Document Settings & Use GPO Comments
Do I Really Need the Windows Firewall?
The Windows firewall can help protect your computer from unwanted traffic. It is considered an Active Directory security best practice by Microsoft and other security professionals. Disabling and leaving the firewall off can make your computer more vulnerable to viruses, ransomware, and other malicious attacks. Even if you have a network-based firewall on the perimeter of your network it is still recommended to have a host-based firewall enabled. The more layers of security you have the better you will be protected.
Many security organizations such as the Center for Internet Security recommend enabling the Windows firewall. Here is a screenshot from the CIS Security Controls regarding firewalls.
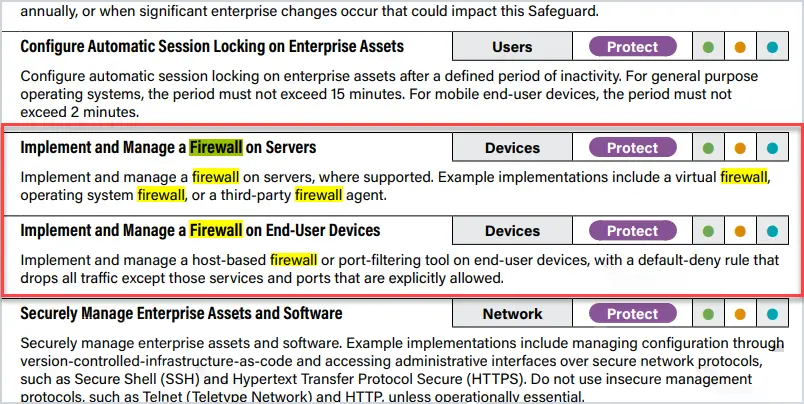
How Do I Check my Firewall Status?
There are a few ways to check if the Windows Firewall is on.
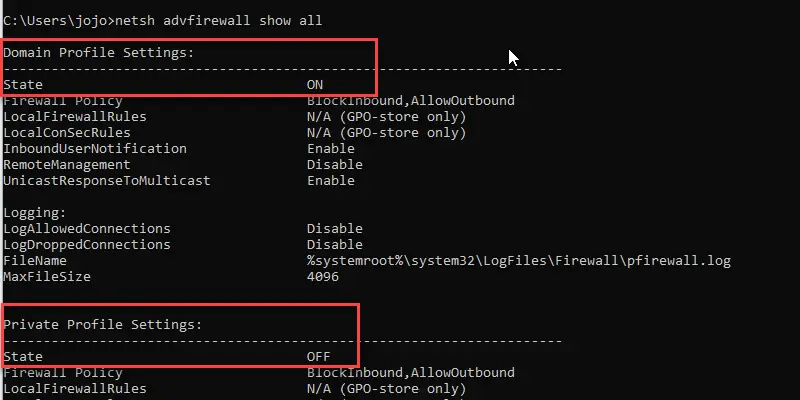
The below command will show the firewall status for all three profiles:
netsh advfirewall show all
Another way to check the firewall status is to click the windows start button and type firewall then select “check firewall status”
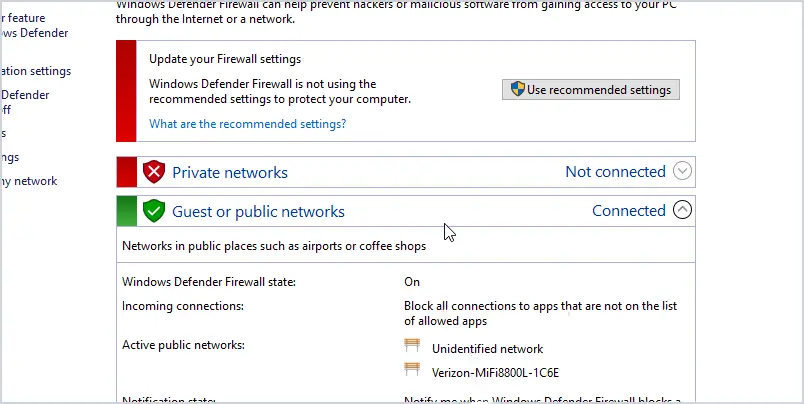
In the picture above you can see the firewall is on for the public network but not for the private networks.
1. Centrally Manage the Firewall with Group Policy
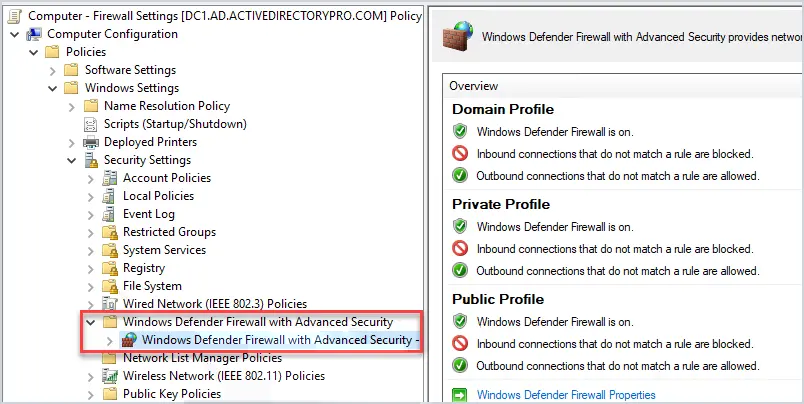
If you have an Active Directory environment or Azure with domain joined computers you should centrally manage the firewall settings. You do not want users to have the ability to manage rules or worse, disable the Firewall. I see too often the firewall popup and say something was blocked, then users just click to add the rule. This could be a disaster and weaken your endpoint security.
Centrally managing the Firewall helps to ensure you have consistent Firewall rules across all systems.
2. Create a Baseline Firewall Policy
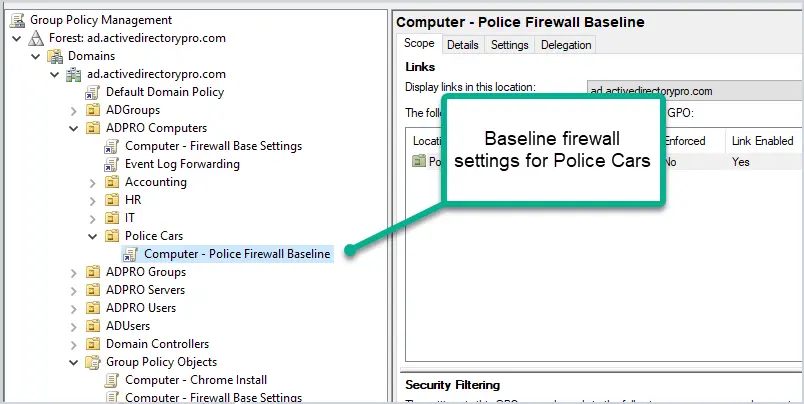
I like to create a baseline firewall policy that can be applied to all computers or a large set of computers. This would include common programs that most computers would have installed. These would be things like Microsoft Teams, Outlook, Java, Office apps, Adobe, and so on.
I create a separate baseline policy for servers and other special use computers that would require more strict rules. For example, mobile computers in police cars would get a separate baseline policy.
When creating the baseline, I only allow what is needed. Again, I’m looking for just the common programs that are used by most users. Specific things like FTP, or allowing SMTP will go into a separate GPO which I’ll go over in tip #4.
3. Create Seperate GPOs for Specific Rules
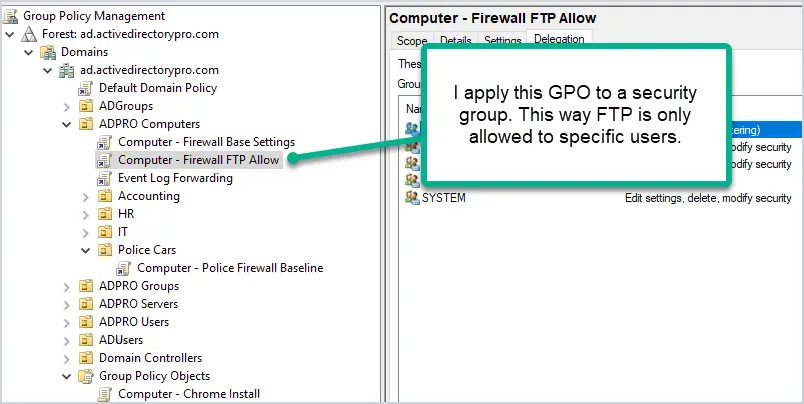
Let’s say you rolled out a baseline firewall GPO and then someone needs FTP unblocked, what do you do? Do you add it to the baseline? NO WAY. This would unblock FTP for a large group of users and weaken your security.
What I do, and also has worked out great, is create a new GPO that unblocks FTP (or whatever is needed) and only apply it to a security group. This works great for two reasons. First, it only unblocks FTP for a small group of users and keeps it blocked for all other users. Second, by using a security group you can easily see which users or computers have specific rules open.
How do you apply a GPO to a security group?
Use the Delegation tab on the GPO to change the permissions and only allow it for a group. You will need to change Authenticated Users to Deny for Apply group policy. Then add your new group and give it Read and Apply group policy allow permissions. Be sure to test this before rolling it out.
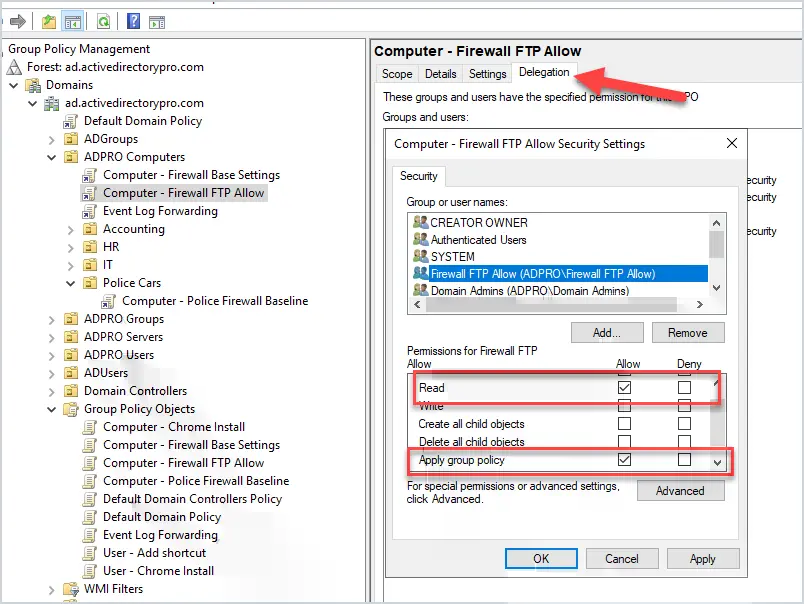
This helps to minimize GPOs needed and to allow the firewall to be 100% managed by GPO.
4. Leave Default Inbound & Outbound Rules
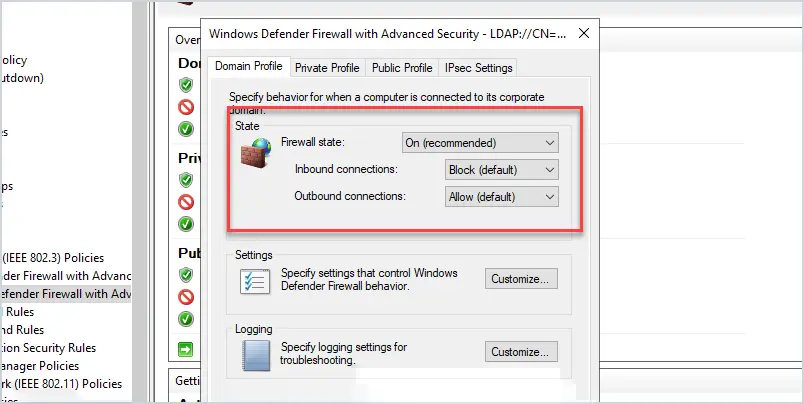
Microsoft says “These settings have been designed to secure your device for use in most network scenarios”.
I agree as this blocks unwanted inbound connections by default. What I mean by unwanted, is connections that your computer did not initiate. For example, if someone tried to admin share (c$) or RDP to your computer it would be blocked. This will also block lateral movement from hacking tools and viruses. Huge Win!
This still allows your computer to make outbound connections that your computer initiates. For example, when you open chrome or firefox this would be allowed with these default rules. These default rules make it easy to implement a secure configuration with less disruption to the users.
If you have strict requirements and need to control all inbound and outbound traffic then don’t use the defaults allow outbound rule. For example, if you just want to allow port 443 outbound to a specific address then do not use these defaults.
It’s possible you could end up with a mix of GPOs that use the defaults and others that do not. Maybe your baseline is default but then have specific computers that block everything by default. Every organization is different and there is no one size fits all for firewall rules.
5. Enable All Firewall Profiles
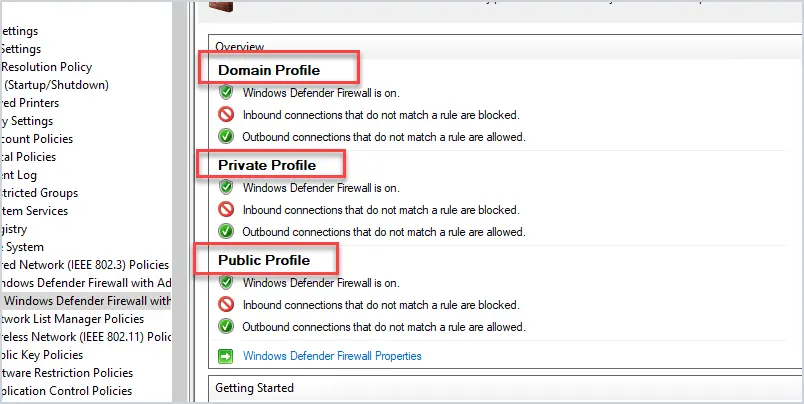
The Windows Firewall has three profiles, domain, private and public.
Domain profile: This profile applies to networks where the computer can authenticate to a domain controller.
Private profile: This profile is a user assigned profile and is used for private and home networks.
Public profile: This is used when connected to public networks such as public wifi.
The best practice is to enable all three profiles. When creating new firewall rules you can then set the rule to the group that best applies (sometimes it will be all three).
For example, if you are creating a rule to allow access to an internal FTP server then there is no need to apply this to the public profile. If you don’t apply very strict rules and applied this to the public profile then you just opened inbound FTP connections from the internet (when connected to a public network).
6. Disable Rule Merging
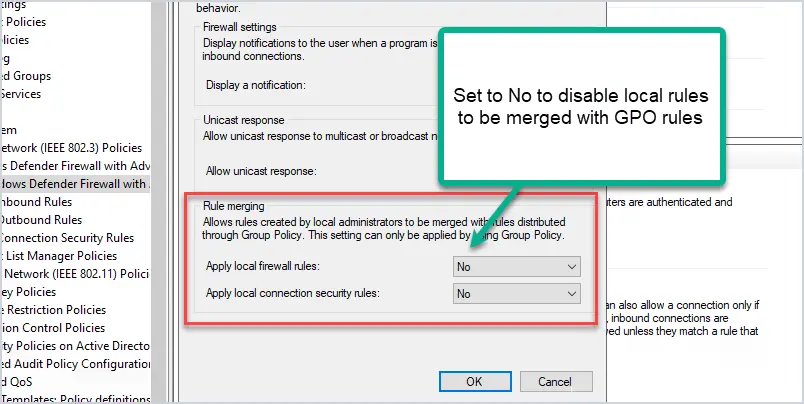
Disable rule merging means local firewall rules are ignored. The endpoint Firewall settings will be 100% managed by group policy. This is my preference.
If it’s not 100% centrally managed then how can you maintain a security posture? I don’t want apps or users to create their own Firewall rules, that is just going to shoot holes in the firewall.
If you added firewall rules locally on the computer and set this to “No” the local rules will no longer apply.
7. Log Settings
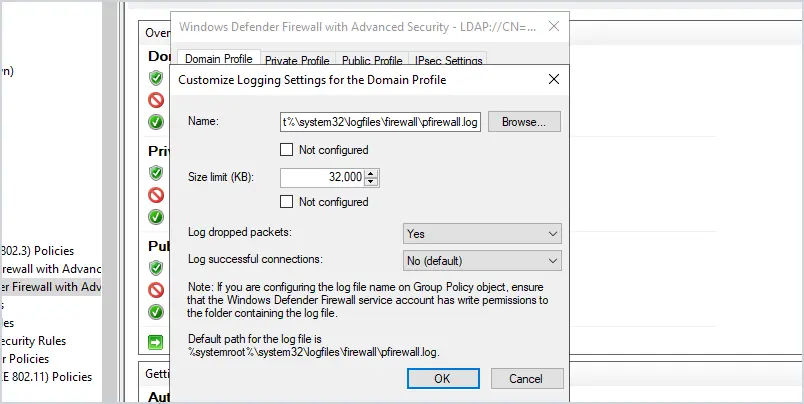
I recommend enabling logging of dropped packets and increasing the size of the log file. There will be times when the firewall is blocking a legit program and you or someone else will need to troubleshoot it. Logging the blocked connections makes it super easy to identify when the firewall is causing a connection issue.
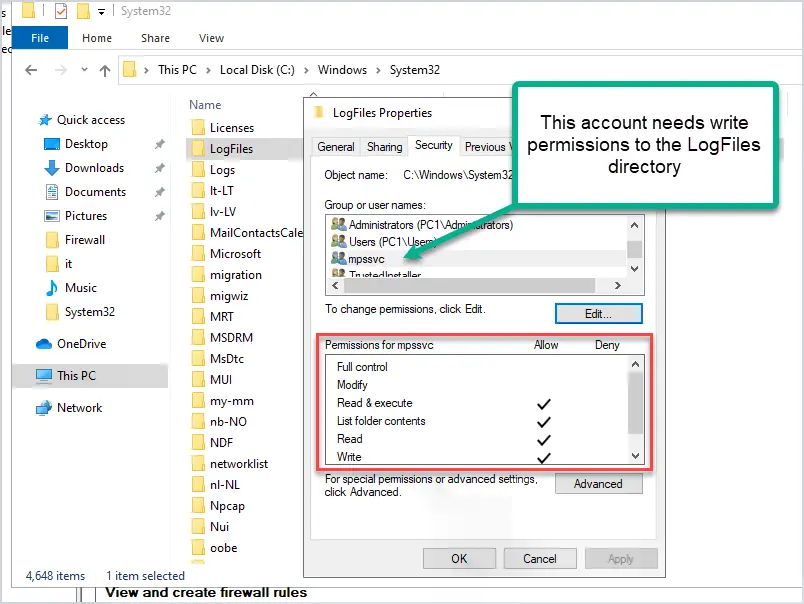
Firewall No Log File Issue
A lot of times the default log file location is missing the permissions to write the log file. I guess this is a Microsoft bug because it happens a lot. To fix this the computer will need to have the mpssvc service account have write permissions to the c:\windows\system32\logfiles directory.
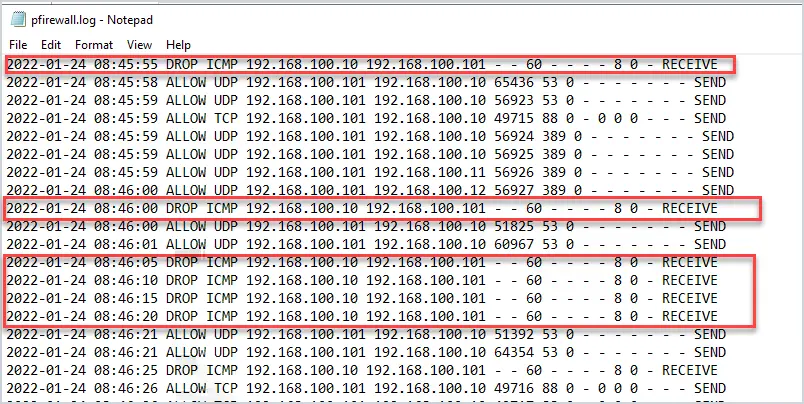
Here is an example of the log file.
8. Limit the Scope of Firewall Rules
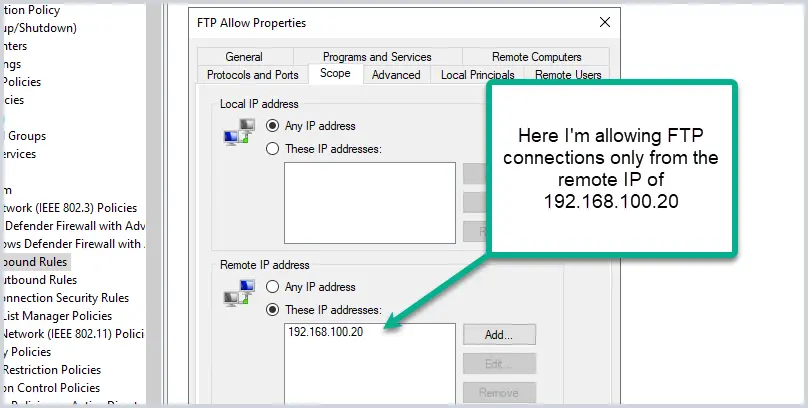
When unblocking a program or service, limit access to remote IP addresses, or authorized computers. For example, if you allow Jim’s computer to allow FTP connections, don’t just allow FTP from any IP address. You can limit the scope, for example, I will just allow Jim’s computer to accept FTP connections from 192.168.100.20.
The golden rule with firewalls is to only allow what is needed. Allowing Jim’s computer to accept FTP connections from any remote address is a security risk. There are multiple ways to do this. I would also recommend locking the rule down to an application, the port number, and the remote address.
This may not always be possible but when you can, lock it down as much as possible.
9. Enable the Firewall
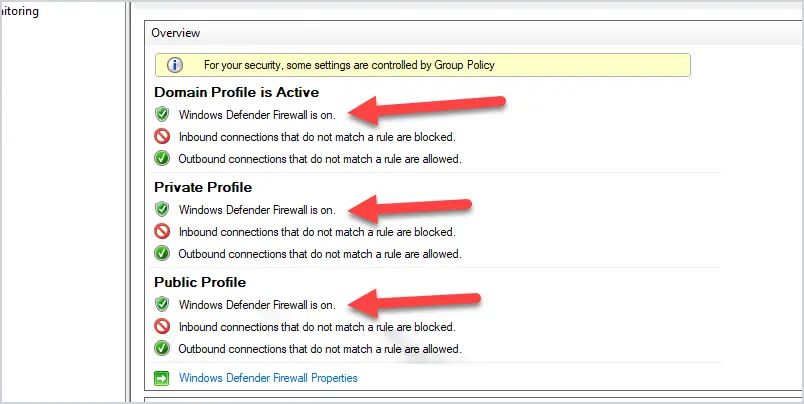
I’m shocked at how many organizations still disable the Windows Firewall or have it poorly configured.
The Windows Firewall provides many security benefits including:
- Control inbound and outbound connections
- Block viruses and ransomware from spreading on your network
- Block users from sharing folders and printers on their computers
- Reduce network threats
- Encrypt network communication on your network
- Slow down attackers from moving latterly on your network
- Block insecure ports by default
Most security organizations such as sans CIS and CISA recommend using a host based firewall to mitigate malicious network activity.
When first released, the Windows Firewall with XP was so bad everyone disabled it. It had limited features and was difficult to configure. Due to all the complaints, Microsoft made major improvements, and it’s been a good enterprise firewall ever since.
Unfortunately, it’s still widely disabled. This is a huge mistake.
Most organizations have a network based firewall and think they don’t need the Windows firewall. This is false and bad practice. Security is all about layers, the more layers you have the better you will be protected. You need a Network firewall at the parameter of your network and the firewall enabled on all endpoints.
10. Firewall Rule Naming Convention
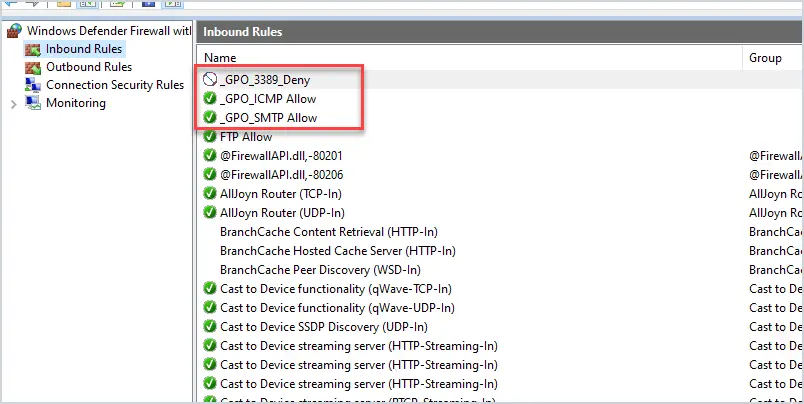
The endpoints will most likely have all the default rules in place unless you applied a policy to clear them. The local firewall rules will not be working but will still show up. This can be confusing and make it difficult to find rules you push out with group policy.
I like to start the GPO rule name with an underscore or a three letter appreciation. This makes it easy to find my GPO Firewall rules on the local endpoint.
For example, in the picture above I started them with _GPO_, now when I open the local firewall all of my GPO rules are at the top and easy to find.
Again when you disable rule merge (tip#7) all of the local firewall rules will not be applied. It’s not as big of an issue as you think when using tip#5.
11. Document Settings & Use GPO Comments
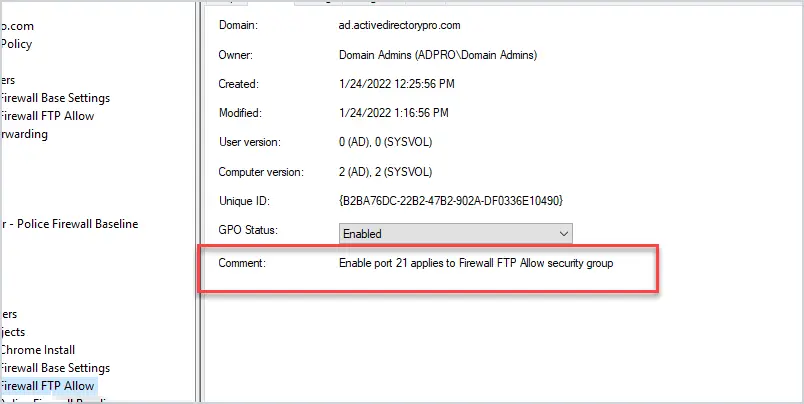
Document the firewall GPO settings and share them with your staff. The firewall is often blamed for everything so it helps when your staff knows what the GPO rules are doing. Even when they do know they will still often blame the firewall. When this happens this is when you show them the firewall logs and prove the firewall is not blocking anything.
The comment section in the GPO is helpful and provides administrators with a quick way to know what the GPO is used for.
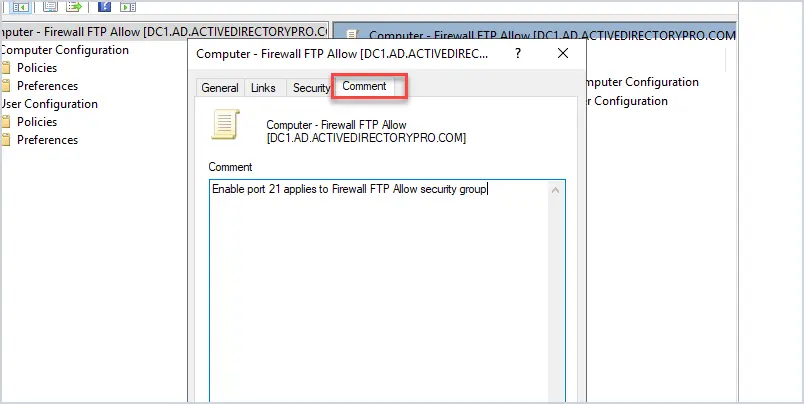
You can access the comment by right clicking the GPO > properties then click on the comment tab.
Now click the comment tab.
Summary
Host based firewalls are essential to an organization’s security strategy. To have good security you must have many layers of defense and the Windows Firewall adds another layer. Plus it’s free.
One huge benefit that is not often talked about is how host based firewalls can block lateral movement in your network. This is a common tactic hackers and viruses use to compromise systems and the entire network. Implementing these best practices will block this lateral movement and many other unwanted connections.
If you currently disable the firewall or do not centrally manage it then I recommend you start looking into changing that.
Sources
- Best practices for configuring Windows Defender Firewall
- Basic Firewall Policy Design Example
- Implemented these rules in small to large production networks
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
With increasing concerns for privacy and security, it has become essential to understand and implement the best settings on your device for safety. Though Windows 11 has a robust firewall, you need to optimize the settings to maximize the first line of defense. In this guide, we will discuss some of the best practices for the Windows 11 firewall. Read on!
What are the Windows 11 Firewall best practices?
1. Always keep the Windows Firewall enabled
- Press Windows + I to open the Settings app.
- Go to Privacy & security, then select Windows Security.
- On the Windows Security app, locate and click Firewall & network protection.
- You will see a Domain network, a Private network, and a Public network. Check if all three say the Firewall is on.
- If you see the Firewall is off message under any of them, click Turn on.
- Click Yes on the UAC prompt and locate Microsoft Defender Firewall, and toggle on the switch to enable it.
The most fundamental thing is to keep the Windows Firewall enabled at all times, as a disabled firewall risks exposing your device to various threat actors.
2. Block the unused ports
- Press the Windows key, type windows security in the search box, and click Open.
- Go to Firewall & network protection.
- Click the Advanced settings option to access the Windows Defender Firewall with the Advanced Security window.
- Click Inbound Rules or Outbound Rules from the left pane, and click New Rule from the right.
- Select Port and click Next.
- Now, select TCP or UDP, enter the specific port number to block and click Next.
- Select Block the connection and click Next.
- Place a checkmark next to all the network profiles (Domain, Private, and Public), then click Next.
- Name the rule and click Finish.
Reduce the number of entry points for unauthorized access to maintain system security and minimize the attack surface.
3. Enable security notifications
- Press the Windows key, type control panel in the search box, and click Open.
- Select Category for View by and click System and security.
- Click Security and Maintenance.
- Click Change Security and Maintenance settings.
- Under Turn messages on or off, make sure Network Firewall is selected, and click OK to save the changes.
Enabling the notifications will help you get alerts whenever the firewall blocks apps or connection attempts, allowing you to identify and respond to unauthorized access requests.
4. Create outbound or inbound rules
- Press the Windows key, type Windows security in the search box, and click Open.
- Go to Firewall & network protection.
- Click the Advanced settings option to access the Windows Defender Firewall with the Advanced Security window.
- Click Inbound Rules or Outbound Rules from the left pane, and click New Rule from the right.
- Follow the on-screen instructions and create rules, such as Allowing only trusted applications and services and restricting unwanted outbound connections to reduce exposure to threats.
Creating inbound and outbound rules can help you manage network security, protect sensitive information, and ensure that only authorized apps communicate with the network.
- Mail and Calendar app now stops syncing your Outlook/Hotmail account in Windows 11
- Windows 11 Start menu panel for Phone Link allows easy access to Android, iPhone
- WSUS blocks downloading Windows 11 24H2 update on 23H2 & 22H2 devices, leaving 0x80240069 error
- Microsoft updates Copilot app with guided tour for new users
- Recent Windows 11 update lets you disable profanity filter in voice typing
5. Enable Log settings
- Press the Windows key, type windows security in the search box, and click Open.
- Go to Firewall & network protection.
- Click the Advanced settings option to access the Windows Defender Firewall with the Advanced Security window.
- Select Windows Defender Firewall with Advanced Security on Local Computer, and click Properties from the right pane.
- Go to the Domain Profile tab, locate Logging, and click Customize.
- Look for the Size limit option and increase the log file size.
- Locate Log dropped packets and select Yes from the drop-down menu.
- Now go to the Public and Private profiles and do the same.
- Click OK, then OK to save the changes.
Enabling the logging of dropped packers and increasing the size of the log file will help you identify blocked connections when the Firewall is causing connection issues.
6. Customize network profiles
- Press the Windows key, type windows security in the search box, and click Open.
- Go to Firewall & network protection.
- You will see three network profiles: Domain, Private, and Public
- Click Domain network, and under Incoming connections, select Blocks all incoming connections, including those in the list of allowed apps.
- Click Yes on the UAC prompt. Then, use the arrow on the left side to return to the previous page.
- Go to the private and public networks and make the same changes under these profiles.
Customizing network profiles in Windows 11 Firewall is essential for adapting security measures to different environments.
7. Setup connection rules
- Press Windows + R to open the Run window.
- Type wf.msc and click OK to open the Windows Defender Firewall with the Advanced Security window.
- Click Connection Security Rules and select New Rule from the right pane.
- Choose Isolation, Server-to-Server, or Tunnel per your preferences and click Next.
- Now, follow the on-screen prompts to specify the connection type, authentication method, and the computer or network profile included.
- Once you have configured it, name the rule and click Finish.
Setting up connection security rules in the Windows 11 Firewall protects data and maintains a strong security posture. If Windows Defender Firewall prevents connections on your device, you can check this guide for solutions.
8. Use the monitoring tools
You can use monitoring tools to track network activity, monitor apps accessing the network, and analyze firewall events. To do that, you can open the Windows Defender Firewall with the Advanced Security window, go to Monitoring, and use options like Firewall, Connection Security Rules, and Security Association.
Moreover, you can right-click Windows Defender Firewall properties, click Logging, and enable logging for dropped packets and successful locations.
In addition to all these, keep reviewing, adding, and removing rules regularly according to your network environment.
If you’re wondering how to check if your Firewall blocks a website, then you should check these settings; read this guide to learn more.
In case the Windows Firewall has blocked some features of an app; it could be due to malware; check out this guide to know more.
If you think there are more tips that you can follow, feel free to share them with our readers in the comments section below. We will add them to the list.
Srishti Sisodia
Windows Software Expert
Srishti Sisodia is an electronics engineer and writer with a passion for technology. She has extensive experience exploring the latest technological advancements and sharing her insights through informative blogs.
Her diverse interests bring a unique perspective to her work, and she approaches everything with commitment, enthusiasm, and a willingness to learn. That’s why she’s part of Windows Report’s Reviewers team, always willing to share the real-life experience with any software or hardware product. She’s also specialized in Azure, cloud computing, and AI.
Table of Contents
- Struggling with Open Ports? Discover the Powerful Way to Manage Windows Firewall Rules with Group Policy
- Why Use Firewall Group Policy?
- Step-by-Step Solution: Configuring Firewall Port Exceptions via Group Policy
- Step 1: Open Group Policy Management Console
- Step 2: Select the Target OU or Domain
- Step 3: Name Your Policy Clearly
- Step 4: Edit the New Group Policy Object
- Step 5: Navigate to the Firewall Settings
- Step 6: Enable and Configure the Policy
- Step 7: Add Your Port Exception
- Step 8: Apply and Close
- Step 9: Force Group Policy Update
- Step 10: Verify the Rule on Target Machines
- Firewall Port Exception Syntax Explained
- Key Benefits of Using Group Policy for Firewall Management
Struggling with Open Ports? Discover the Powerful Way to Manage Windows Firewall Rules with Group Policy
Effectively managing which ports are open on your Windows machines is crucial for network security and operational efficiency. Disabling the Windows Firewall is never recommended-instead, you can use Group Policy to centrally control firewall rules, ensuring only the necessary ports are open for your applications and servers.
Below is a clear, concise, and professional guide to configuring Windows Firewall port exceptions using Group Policy, with a focus on best practices for security and scalability.
- Centralized Management: Easily configure and enforce firewall rules across multiple machines from a single location.
- Enhanced Security: Only necessary ports are opened, reducing your attack surface.
- Scalability: Apply policies to specific Organizational Units (OUs) for targeted control.
- Auditability: Clearly see which rules are applied and why, supporting compliance and troubleshooting.
Step-by-Step Solution: Configuring Firewall Port Exceptions via Group Policy
Step 1: Open Group Policy Management Console
On a domain controller or a client with Remote Administration Tools, press Windows Key + R, type gpmc.msc, and press Enter.
Step 2: Select the Target OU or Domain
- In the console, select the Organizational Unit (OU) containing the computers you want to manage.
- Right-click the OU or domain, then choose Create a GPO in this domain, and Link it here…
Step 3: Name Your Policy Clearly
Use a descriptive name (e.g., “Open TCP Port 9503 for McAfee Move Servers”) for easy identification later.
Step 4: Edit the New Group Policy Object
Right-click your newly created GPO and select Edit.
Step 5: Navigate to the Firewall Settings
Go to: Computer Configuration > Policies > Administrative Templates > Network > Network Connections > Windows Firewall > Domain Profile > Windows Firewall: Define inbound port exceptions
Step 6: Enable and Configure the Policy
- Double-click Windows Firewall: Define inbound port exceptions.
- Set the policy to Enabled, then click Show to add new entries.
Step 7: Add Your Port Exception
Use the following syntax for each exception: <Port>:<Transport>:<Scope>:<Name>
Example for opening TCP port 9503 from any source:
9503:TCP:*:McAfee Move
You can add multiple entries as needed.
Step 8: Apply and Close
Click OK, then Apply, and close the Group Policy Management Editor.
Step 9: Force Group Policy Update
To apply changes immediately, run gpupdate /force on the target machines, or wait for the next policy refresh cycle.
Step 10: Verify the Rule on Target Machines
- Press Windows Key + R, type WF.msc, and press Enter.
- Go to Inbound Rules and confirm your new rule appears.
- Double-click the rule to verify it was applied via Group Policy and that the correct port and settings are in place.
Firewall Port Exception Syntax Explained
- Port: Enter the port number (e.g., 9503).
- Transport: Specify TCP or UDP.
- Scope: Define the allowed source (e.g., 192.168.1.0/24 for a subnet, * for any).
- Name: Add a clear name for easy identification.
Example Entry:
9503:TCP:*:McAfee Move
Key Benefits of Using Group Policy for Firewall Management
- Consistency: Ensures all targeted machines have identical firewall configurations.
- Reduced Human Error: Centralized management minimizes misconfigurations.
- Quick Rollback: Easily remove or modify rules by editing the GPO.
- Audit Trail: Group Policy provides visibility into applied settings for compliance.
By following these steps, you can confidently manage Windows Firewall rules across your organization, ensuring both security and operational effectiveness. This proactive approach not only protects your network but also streamlines IT administration-giving you peace of mind and more time to focus on other priorities.
Уровень сложностиСложный
Время на прочтение33 мин
Количество просмотров125K

Windows 10 очень любит Интернет. Обновления, синхронизации, телеметрия и ещё куча разной другой очень нужной ЕЙ информации постоянно гуляет через наши сетевые соединения. В «стандартном» сценарии использования, когда Windows 10 управляет домашним или рабочим компьютером, это, в общем-то, терпимо, хотя и не очень приятно.
Однако жизнь сложная штука и не ограничивается только стандартными вариантами. Существуют ситуации, когда подобная сетевая активность операционной системы (ОС) нежелательна и даже вредна. За примерами далеко ходить не надо. Попробуйте подключить к Интернету давно не используемый резервный компьютер, собранный на старом железе. Пока софт на нём не обновится, использовать его будет практически невозможно, всё будет дико тормозить и еле шевелиться. А если вам в этот момент нужно срочно что-то сделать?
Для того чтобы подобного не происходило, необходимо «заткнуть рот Windows», то есть сделать так, чтобы она самостоятельно перестала «стучаться» в Интернет, устанавливать обновления и заниматься прочими непотребствами. Вот именно этим мы с вами и займёмся.
Если бы операционная система (ОС) разрабатывалась для удовлетворения нужд потребителей, то эту статью писать бы не пришлось. В ОС были бы стандартные механизмы настройки, с помощью которых можно было бы отключить весь ненужный функционал, но, к сожалению, это не так.
Проблема в том, что компьютер, управляемый Windows 10, нам не принадлежит. ОС содержит неудаляемые приложения, она может самостоятельно отменять действия пользователя, удалять или инсталлировать программы, а также делать другие вещи, идущие вразрез с мнением пользователя, будь он даже администратор системы.
Интеграция с облачными сервисами в Windows 10 реализована так жёстко, что безболезненно отключить её просто невозможно. При любой попытке деактивации хотя бы части этого функционала в ОС обязательно что-нибудь да сломается. Поэтому дальнейший материал, так сказать, для профессионального использования. Не рекомендуется применять его на ваших компьютерах без предварительного тестирования и отладки.
Знай своего врага в лицо
Первым шагом в нашей войне с «паразитной» сетевой активностью ОС будет исследование этой самой активности. Для этого мы соберём простейший лабораторный стенд, состоящий из двух виртуальных машин (ВМ).

Здесь Windows 10 будет выходить в Интернет через промежуточный Linux-шлюз, который будет оказывать ей услуги NAT и DNS-сервера.
Исследовать «паразитный» сетевой трафик будем как на Linux-шлюзе, так и на самой Windows 10. На шлюзе это будем делать с помощью сниффера tcpdump и логов DNS-сервера, а на Windows 10 мы воспользуемся утилитой Process Monitor из пакета Sysinternals.
Настройку Linux-шлюза опустим из-за банальности, а про Process Monitor скажем пару слов. Для наших целей сделаем следующие шаги:
- Отключим захват всех событий, кроме тех, что связаны с сетью. Для этого главный тулбар настроим следующим образом:
- Настроим сброс отфильтрованных событий, чтобы не было переполнения памяти.
Для этого в Menu > Filter и активируем опцию «Drop filtered events». - Настроим главный экран, что бы он отображал только то, что нам нужно.
Открываем Options > Select columns и ставим галки только напротив пунктов: «Process name», «Command Line» и «Path»
В результате всех этих экзерциций при анализе сетевого трафика мы сможем увидеть процесс, инициирующий соединение, сетевой адрес назначения, и имена сетевых служб, запускаемых через специализированный процесс svchost.exe.

Первый замер
Наш первый замер будет самый простой. Мы дождёмся чуда, когда Windows перестанет передавать что-либо в Интернет, после чего пробежимся по стандартным настройкам ОС и посмотрим, какой трафик при этом будет генерироваться.

Смотрите, как здорово. В Интернет передаётся информация практически о каждом нашем клике. Приватность? Не, не слышал… Что ж, мы научились детектировать «паразитный» трафик. Теперь будем разбираться, как его блокировать.
Вариант блокировки № 1 – Windows Firewall
Наиболее логичным вариантом блокировки выглядит использование штатного межсетевого экрана — Windows Firewall. По логике вещей мы должны каким-то образом идентифицировать паразитный трафик и затем его заблокировать. Сделать это можно двумя способами:
- Оставить разрешённым весь исходящий трафик и при этом блокировать только тот, что мы сочтём паразитным.
- Запретить весь исходящий трафик, а затем разрешить только тот, что сочтём нужным (не паразитным).
Но поскольку мы работаем в недоверенной системе, то нам нужно убедиться, что Windows Firewall в принципе на это способен. В частности, нам нужно удостовериться, что:
- Windows Firewall может разрешать или запрещать системный траффик ОС.
- Windows Firewall может разрешать или запрещать траффик с гранулярностью до системных служб.
- Windows Firewall самостоятельно не отменит сделанные нами правила или другим образом не проявит излишнюю самостоятельность.
▍ Тест для Windows Firewall № 1. Может ли он блокировать системный трафик?
Идея эксперимента очень проста. Мы запретим любую сетевую активность и посмотрим, какой трафик будет проходить через этот запрет. Для этого в настройках Windows Firewall установим по умолчанию блокировку всего исходящего и входящего трафика, после чего удалим все правила исключения. Данные со шлюза говорят о том, что «паразитный» Интернет-трафик отсутствует, и фиксируются только ARP-запросы.

Получается, Windows Firewall может действительно заблокировать весь Интернет-трафик. Звучит обнадёживающе.
▍ Тест для Windows Firewall № 2. Может ли он управлять трафиком конкретной сетевой службы?
В этом эксперименте мы должны убедиться, что Windows Firewall может управлять трафиком с гранулярностью до сервиса. Для этого попробуем разрешить трафик для системного DNS-клиента (имя этой службы – Dnscache). С помощью мастера настройки создадим исходящее правило, разрешающее весь трафик, и укажем, чтобы оно применялось к данной службе.

Смотрим, что там на шлюзе.

Словно человек, изнывающий от жажды при виде бутылки чистой воды, Windows 10 после разрешения работы DNS-клиента сразу же бросилась пытаться что-нибудь передать или получить из Интернета, ведь она не была в онлайне уже несколько минут. Мало ли что там могло произойти!
Windows Firewall прошёл и это испытание. Остался последний шаг.
▍ Тест для Windows Firewall № 3. Будет ли Windows Firewall самостоятельно исправлять правила, созданные пользователем?
Одним из генераторов «паразитного» трафика является встроенный антивирус Windows Defender. Он качает обновления баз, а также передаёт в облачный сервис (который судя по групповым политикам, называется SpyNet) принадлежащие вам файлы. В качестве теста попробуем заблокировать эту сетевую активность.
Для схемы с разрешённым по умолчанию исходящим трафиком создадим правило блокировки Windows Defender. Для этого в правиле блокировки укажем путь к блокируемой программе: «C:\Program Files\Windows Defender\MpCmdRun.exe»

В момент записи правила сразу же срабатывает Windows Defender с обнаружением угрозы (WDBlockFirewallRule) и удаляет сделанное нами правило.

Таким образом, последний тест Windows Firewall провалил. Конечно, правила удалил не Windows Firewall, а другой компонент ОС, тем не менее мы в очередной раз убедились, что наш компьютер нам не принадлежит.
▍ Итог по Windows Firewall
Несмотря на все выкрутасы, использование Windows Firewall для блокировки паразитного трафика возможно. Единственной доступной в данном случае схемой будет блокировка по умолчанию всего исходящего трафика с созданием разрешающих правил для трафика, который мы сочтём нужным. Тем не менее осадочек остался, и использовать Windows Firewall дальше мы не будем.
Вариант блокировки № 2 – рекомендации Microsoft
Корпорацию Microsoft наверно так задолбали с наездами по поводу не в меру ретивой сетевой активности Windows, что она выпустила гайд «Manage connections from Windows 10 and Windows 11 operating system components to Microsoft services» о том, как немного притормозить её пыл. В гайде приведены инструкции, как с помощью групповых политик или манипуляций с реестром отключить часть сетевых возможностей ОС. Также Microsoft предлагает удалить некоторые встроенные приложения. Реализация гайда приведена под спойлерами ниже.
REG-файл уровня пользователя user.reg
Windows Registry Editor Version 5.00
; 8. Internet Explorer. Turn off the home page
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Internet Explorer\Main]
"Start Page"="about:blank"
; 8. Internet Explorer. Turn off the home page
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Internet Explorer\Control Panel]
"HomePage"=dword:1
; 8. Internet Explorer. Disable first run wizard
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Internet Explorer\Main]
"DisableFirstRunCustomize"=dword:1
; 8. Internet Explorer. Set about:blank in new tab
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Internet Explorer\TabbedBrowsing]
"NewTabPageShow"=dword:0
; 8.1 ActiveX control blocking. Disable periodocally download a list of out-of-date ActiveX controls
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\VersionManager]
"DownloadVersionList"=dword:0
; 18.1 General. Disable websites access to my language list
[HKEY_CURRENT_USER\Control Panel\International\User Profile]
"HttpAcceptLanguageOptOut"=dword:00000001
; 18.1 General. Disable track app launches
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced]
"Start_TrackProgs"=dword:00000000
; 18.1 General. Turn off SmartScreen check of URLs what Microsoft Store apps use:
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\AppHost]
"EnableWebContentEvaluation"=dword:00000000
; 18.6 Speech. Prevent sending your voice input to Microsoft Speech services:
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Settings\OnlineSpeechPrivacy]
"HasAccepted"=dword:00000000
; 18.16 Feedback & diagnostics. Turn off tailored experiences
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\CloudContent]
"DisableTailoredExperiencesWithDiagnosticData"=dword:1
; 18.21 Inking & Typing. Turn off Inking & Typing data collection
[HKEY_CURRENT_USER\Software\Policies\Microsoft\InputPersonalization]
"RestrictImplicitTextCollection"=dword:0
; 18.21 Inking & Typing. Turn off Inking & Typing data collection
[HKEY_CURRENT_USER\Software\Policies\Microsoft\InputPersonalization]
"RestrictImplicitInkCollection"=dword:0
; 18.21 Inking & Typing. Turn off Inking & Typing data collection
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\InputPersonalization]
"RestrictImplicitInkCollection"=dword:00000001
; 18.21 Inking & Typing. Turn off Inking & Typing data collection
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\InputPersonalization]
"RestrictImplicitTextCollection"=dword:00000001
; 21. Sync your settings
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Messaging]
"CloudServiceSyncEnabled"=dword:00000000
; 25. Personalized Experiences. Disable feature
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\CloudContent]
"DisableWindowsSpotlightFeatures"=dword:1
; !!! This must be done within 15 minutes after Windows 10 or Windows 11 is installed.
; 25. Personalized Experiences. Disable feature
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\CloudContent]
"DisableCloudOptimizedContent"=dword:00000001
; 29. Windows Update. Turn off
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\WindowsUpdate]
"DisableWindowsUpdateAccess"=dword:1
; 29. Windows Update. Turn off
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\WindowsUpdate]
"DisableWindowsUpdateAccessMode"=dword:0
REG-файл уровня компьютер comp.reg
Windows Registry Editor Version 5.00
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\AuthRoot]
"DisableRootAutoUpdate"=dword:1
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\ChainEngine\Config]
"ChainUrlRetrievalTimeoutMilliseconds"=dword:15000
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\ChainEngine\Config]
"ChainRevAccumulativeUrlRetrievalTimeoutMilliseconds"=dword:20000
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\ChainEngine\Config]
"Options"=dword:0
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\ChainEngine\Config]
"CrossCertDownloadIntervalHours"=dword:168
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\DPNGRA\Certificates]
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\DPNGRA\CRLs]
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\DPNGRA\CTLs]
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\FVE\Certificates]
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\FVE\CRLs]
; 1. Automatic Root Certificates Update. Disable auto update
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\FVE\CTLs]
; 2.1 Cortana and Search Group Policies. Turn off Cortana
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Windows Search]
"AllowCortana"=dword:0
; 2.1 Cortana and Search Group Policies. Block access to location information for Cortana
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Windows Search]
"AllowSearchToUseLocation"=dword:0
; 2.1 Cortana and Search Group Policies. Remove the option to search the Internet from Cortana
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Windows Search]
"DisableWebSearch"=dword:1
; 2.1 Cortana and Search Group Policies. Stop web queries and results from showing in Search
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Windows Search]
"ConnectedSearchUseWeb"=dword:0
; 2.1 Cortana and Search Group Policies. Firewall block rule
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsFirewall\FirewallRules]
"{0DE40C8E-C126-4A27-9371-A27DAB1039F7}"="v2.25|Action=Block|Active=TRUE|Dir=Out|Protocol=6|App=%windir%\\SystemApps\\Microsoft.Windows.Cortana_cw5n1h2txyewy\\searchUI.exe|Name=Block outbound Cortana|"
; !!!!!!!!!
; 3. Date & Time. Disable NTP
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Parameters]
"Type"="NoSync"
; !!!!!!!!!
; 3. Date & Time. Disable NTP
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\W32time\TimeProviders\NtpClient]
"Enabled"=dword:0
; 4. Device metadata retrieval. Prevent
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Device Metadata]
"PreventDeviceMetadataFromNetwork"=dword:1
; 5. Find My Device. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\FindMyDevice]
"AllowFindMyDevice"=dword:0
; 6. Font streaming. Disable download on demand
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"EnableFontProviders"=dword:0
; 7. Insider Preview builds. Turn off Insider Preview builds
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PreviewBuilds]
"AllowBuildPreview"=dword:0
; 7. Insider Preview builds. Turn off Insider Preview builds
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"ManagePreviewBuildsPolicyValue"=dword:1
; 7. Insider Preview builds. Turn off Insider Preview builds
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"BranchReadinessLevel"=-
; 8. Internet Explorer. Disable suggested Sites
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Internet Explorer\Suggested Sites]
"Enabled"=dword:0
; 8. Internet Explorer. Disable enhanced suggestion in Address Bar
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Internet Explorer]
"AllowServicePoweredQSA"=dword:0
; !!!!!!!!!
; 8. Internet Explorer. Disable auto complete
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CurrentVersion\Explorer\AutoComplete]
"AutoSuggest"="no"
; 8. Internet Explorer. Disable geolocation
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Internet Explorer\Geolocation]
"PolicyDisableGeolocation"=dword:1
; 8. Internet Explorer. Prevent managing Microsoft Defender SmartScreen
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Internet Explorer\PhishingFilter]
"EnabledV9"=dword:0
; 8. Internet Explorer. Turn off Compatibility View
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Internet Explorer\BrowserEmulation]
"DisableSiteListEditing"=dword:1
; 8. Internet Explorer. Turn off the flip ahead with page prediction feature
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Internet Explorer\FlipAhead]
"Enabled"=dword:0
; 8. Internet Explorer. Turn off background synchronization for feeds and Web Slices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Internet Explorer\Feeds]
"BackgroundSyncStatus"=dword:0
; 8. Internet Explorer. Disallow Online Tips
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"AllowOnlineTips"=dword:0
; 9. License Manager. Turn off related traffic
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LicenseManager]
"Start"=dword:00000004
; 10. Live Tiles. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CurrentVersion\PushNotifications]
"NoCloudApplicationNotification"=dword:1
; 11. Mail synchronization. Turn off the Windows Mail app
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Mail]
"ManualLaunchAllowed"=dword:00000000
; 12. Microsoft Account. Disable Microsoft Account Sign-In Assistant:
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\wlidsvc]
"Start"=dword:00000004
13.1 Microsoft Edge Group Policies. Disable Address Bar drop-down list suggestions
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\ServiceUI]
"ShowOneBox"=dword:0
13.1 Microsoft Edge Group Policies. Disable configuration updates for the Books Library
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\BooksLibrary]
"AllowConfigurationUpdateForBooksLibrary"=dword:0
13.1 Microsoft Edge Group Policies. Turn off autofill
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\Main]
"Use FormSuggest"="no"
13.1 Microsoft Edge Group Policies. Don't send "Do Not Track"
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\Main]
"DoNotTrack"=dword:1
13.1 Microsoft Edge Group Policies. Disable password manager
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\Main]
"FormSuggest Passwords"="no"
13.1 Microsoft Edge Group Policies. Turn off search suggestion in address bar
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\SearchScopes]
"ShowSearchSuggestionsGlobal"=dword:0
13.1 Microsoft Edge Group Policies. Turn off SmartScreen
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\PhishingFilter]
"EnabledV9"=dword:0
13.1 Microsoft Edge Group Policies. Open blank new tab
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\ServiceUI]
"AllowWebContentOnNewTabPage"=dword:0
13.1 Microsoft Edge Group Policies. Set blank homepage
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\Internet Settings]
"ProvisionedHomePages"="<<about:blank>>"
13.1 Microsoft Edge Group Policies. Prevent the First Run webpage from opening
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\Main]
"PreventFirstRunPage"=dword:1
13.1 Microsoft Edge Group Policies. Disable compatibility mode
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MicrosoftEdge\BrowserEmulation]
"MSCompatibilityMode"=dword:0
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"SearchSuggestEnabled"=dword:00000000
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"AutofillAddressEnabled"=dword:00000000
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"AutofillCreditCardEnabled"=dword:00000000
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"ConfigureDoNotTrack"=dword:00000001
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"PasswordManagerEnabled"=dword:00000000
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"DefaultSearchProviderEnabled"=dword:00000000
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"HideFirstRunExperience"=dword:00000001
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"SmartScreenEnabled"=dword:00000000
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"NewTabPageLocation"="about:blank"
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"RestoreOnStartup"=dword:00000005
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge\RestoreOnStartupURLs]
"1"="about:blank"
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge\EdgeUpdate]
"UpdateDefault"=dword:00000000
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge\EdgeUpdate]
"AutoUpdateCheckPeriodMinutes"=dword:00000000
; 13.2 Microsoft Edge Enterprise.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge\EdgeUpdate]
"ExperimentationAndConfigurationServiceControl"=dword:00000000
; 14. Network Connection Status Indicator. Turn off active probe
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\NetworkConnectivityStatusIndicator]
"NoActiveProbe"=dword:1
; 15. Offline maps. Disable download and update offline maps
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Maps]
"AutoDownloadAndUpdateMapData"=dword:0
; 15. Offline maps. Disable download and update offline maps
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Maps]
"AllowUntriggeredNetworkTrafficOnSettingsPage"=dword:0
; 16. OneDrive. Prevent the usage of OneDrive for file storage
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\OneDrive]
"DisableFileSyncNGSC"=dword:1
; 16. OneDrive. Prevent OneDrive from generating network traffic until the user signs in to OneDrive
[HKEY_LOCAL_MACHINE\Software\Microsoft\OneDrive]
"PreventNetworkTrafficPreUserSignIn"=dword:1
; 18.1 General. Turn off advertising ID
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\AdvertisingInfo]
"Enabled"=dword:00000000
; 18.1 General. Turn off advertising ID
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AdvertisingInfo]
"DisabledByGroupPolicy"=dword:1
; 18.1 General. Disable continue experiences
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"EnableCdp"=dword:0
; 18.2 Location. Prevent apps from accessing the location
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\LocationAndSensors]
"DisableLocation"=dword:1
; 18.2 Location. Prevent apps from accessing the location
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessLocation"=dword:2
; 18.2 Location. Prevent apps from accessing the location
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessLocation_UserInControlOfTheseApps"=hex(7):00,00
; 18.2 Location. Prevent apps from accessing the location
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessLocation_ForceAllowTheseApps"=hex(7):00,00
; 18.2 Location. Prevent apps from accessing the location
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessLocation_ForceDenyTheseApps"=hex(7):00,00
; 18.3 Camera. Prevent apps from accessing the camera
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCamera"=dword:2
; 18.3 Camera. Prevent apps from accessing the camera
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCamera_UserInControlOfTheseApps"=hex(7):00,00
; 18.3 Camera. Prevent apps from accessing the camera
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCamera_ForceAllowTheseApps"=hex(7):00,00
; 18.3 Camera. Prevent apps from accessing the camera
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCamera_ForceDenyTheseApps"=hex(7):00,00
; 18.4 Microphone. Prevent apps from accessing the microphone
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMicrophone"=dword:2
; 18.4 Microphone. Prevent apps from accessing the microphone
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMicrophone_UserInControlOfTheseApps"=hex(7):00,00
; 18.4 Microphone. Prevent apps from accessing the microphone
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMicrophone_ForceAllowTheseApps"=hex(7):00,00
; 18.4 Microphone. Prevent apps from accessing the microphone
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMicrophone_ForceDenyTheseApps"=hex(7):00,00
; 18.5 Notifications. Turn off cloud notifications notifications
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CurrentVersion\PushNotifications]
"NoCloudApplicationNotification"=dword:1
; 18.5 Notifications. Prevent apps from accessing my notifications
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessNotifications"=dword:2
; 18.5 Notifications. Prevent apps from accessing my notifications
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessNotifications_UserInControlOfTheseApps"=hex(7):00,00
; 18.5 Notifications. Prevent apps from accessing my notifications
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessNotifications_ForceAllowTheseApps"=hex(7):00,00
; 18.5 Notifications. Prevent apps from accessing my notifications
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessNotifications_ForceDenyTheseApps"=hex(7):00,00
; 18.6 Speech. Turn off updates to the speech recognition and speech synthesis models
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Speech]
"AllowSpeechModelUpdate"=dword:0
; 18.6 Speech. Turn off updates to the speech recognition and speech synthesis models
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\InputPersonalization]
"AllowInputPersonalization"=dword:0
; 18.7 Account info. Prevent apps from accessing account info
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessAccountInfo"=dword:2
; 18.7 Account info. Prevent apps from accessing account info
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessAccountInfo_UserInControlOfTheseApps"=hex(7):00,00
; 18.7 Account info. Prevent apps from accessing account info
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessAccountInfo_ForceAllowTheseApps"=hex(7):00,00
; 18.7 Account info. Prevent apps from accessing account info
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessAccountInfo_ForceDenyTheseApps"=hex(7):00,00
; 18.8 Contacts. Prevent apps from accessing contacts
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessContacts"=dword:2
; 18.8 Contacts. Prevent apps from accessing contacts
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessContacts_UserInControlOfTheseApps"=hex(7):00,00
; 18.8 Contacts. Prevent apps from accessing contacts
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessContacts_ForceAllowTheseApps"=hex(7):00,00
; 18.8 Contacts. Prevent apps from accessing contacts
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessContacts_ForceDenyTheseApps"=hex(7):00,00
; 18.9 Calendar. Prevent apps from accessing calendar
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCalendar"=dword:2
; 18.9 Calendar. Prevent apps from accessing calendar
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCalendar_UserInControlOfTheseApps"=hex(7):00,00
; 18.9 Calendar. Prevent apps from accessing calendar
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCalendar_ForceAllowTheseApps"=hex(7):00,00
; 18.9 Calendar. Prevent apps from accessing calendar
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCalendar_ForceDenyTheseApps"=hex(7):00,00
; 18.10 Call history. Prevent apps from accessing call history
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCallHistory"=dword:2
; 18.10 Call history. Prevent apps from accessing call history
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCallHistory_UserInControlOfTheseApps"=hex(7):00,00
; 18.10 Call history. Prevent apps from accessing call history
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCallHistory_ForceAllowTheseApps"=hex(7):00,00
; 18.10 Call history. Prevent apps from accessing call history
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessCallHistory_ForceDenyTheseApps"=hex(7):00,00
; 18.11 Email. Prevent apps from accessing emails
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessEmail"=dword:2
; 18.11 Email. Prevent apps from accessing emails
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessEmail_UserInControlOfTheseApps"=hex(7):00,00
; 18.11 Email. Prevent apps from accessing emails
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessEmail_ForceAllowTheseApps"=hex(7):00,00
; 18.11 Email. Prevent apps from accessing emails
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessEmail_ForceDenyTheseApps"=hex(7):00,00
; 18.12 Messaging. Prevent apps from accessing messages
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMessaging"=dword:2
; 18.12 Messaging. Prevent apps from accessing messages
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMessaging_UserInControlOfTheseApps"=hex(7):00,00
; 18.12 Messaging. Prevent apps from accessing messages
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMessaging_ForceAllowTheseApps"=hex(7):00,00
; 18.12 Messaging. Prevent apps from accessing messages
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMessaging_ForceDenyTheseApps"=hex(7):00,00
; 18.12 Messaging. Turn off Message Sync
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Messaging]
"AllowMessageSync"=dword:0
; 18.13 Phone calls. Prevent apps from accessing phone calls
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessPhone"=dword:2
; 18.13 Phone calls. Prevent apps from accessing phone calls
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessPhone_UserInControlOfTheseApps"=hex(7):00,00
; 18.13 Phone calls. Prevent apps from accessing phone calls
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessPhone_ForceAllowTheseApps"=hex(7):00,00
; 18.13 Phone calls. Prevent apps from accessing phone calls
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessPhone_ForceDenyTheseApps"=hex(7):00,00
; 18.14 Radios. Prevent apps from accessing radio
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessRadios"=dword:2
; 18.14 Radios. Prevent apps from accessing radio
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessRadios_UserInControlOfTheseApps"=hex(7):00,00
; 18.14 Radios. Prevent apps from accessing radio
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessRadios_ForceAllowTheseApps"=hex(7):00,00
; 18.14 Radios. Prevent apps from accessing radio
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessRadios_ForceDenyTheseApps"=hex(7):00,00
; 18.15 Other devices. Prevent communications with unpaired devices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsSyncWithDevices"=dword:2
; 18.15 Other devices. Prevent communications with unpaired devices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsSyncWithDevices_UserInControlOfTheseApps"=hex(7):00,00
; 18.15 Other devices. Prevent communications with unpaired devices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsSyncWithDevices_ForceAllowTheseApps"=hex(7):00,00
; 18.15 Other devices. Prevent communications with unpaired devices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsSyncWithDevices_ForceDenyTheseApps"=hex(7):00,00
; 18.15 Other devices. Prevent communications with tursted devices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessTrustedDevices"=dword:2
; 18.15 Other devices. Prevent communications with tursted devices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessTrustedDevices_UserInControlOfTheseApps"=hex(7):00,00
; 18.15 Other devices. Prevent communications with tursted devices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessTrustedDevices_ForceAllowTheseApps"=hex(7):00,00
; 18.15 Other devices. Prevent communications with tursted devices
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessTrustedDevices_ForceDenyTheseApps"=hex(7):00,00
; 18.16 Feedback & diagnostics. Turn off Feedback notifications
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\DataCollection]
"DoNotShowFeedbackNotifications"=dword:1
; 18.16 Feedback & diagnostics. Disable telemetry
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\DataCollection]
"AllowTelemetry"=dword:0
; 18.16 Feedback & diagnostics. Turn off tailored experiences
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CloudContent]
"DisableWindowsConsumerFeatures"=dword:1
; 18.17 Background apps. Turn off background app
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsRunInBackground"=dword:2
; 18.17 Background apps. Turn off background app
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsRunInBackground_UserInControlOfTheseApps"=hex(7):00,00
; 18.17 Background apps. Turn off background app
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsRunInBackground_ForceAllowTheseApps"=hex(7):00,00
; 18.17 Background apps. Turn off background app
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsRunInBackground_ForceDenyTheseApps"=hex(7):00,00
; 18.18 Motion. Prevent apps from accessing motion data
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMotion"=dword:2
; 18.18 Motion. Prevent apps from accessing motion data
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMotion_UserInControlOfTheseApps"=hex(7):00,00
; 18.18 Motion. Prevent apps from accessing motion data
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMotion_ForceAllowTheseApps"=hex(7):00,00
; 18.18 Motion. Prevent apps from accessing motion data
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessMotion_ForceDenyTheseApps"=hex(7):00,00
; 18.19 Tasks. Prevent apps from accessing tasks
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessTasks"=dword:2
; 18.19 Tasks. Prevent apps from accessing tasks
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessTasks_UserInControlOfTheseApps"=hex(7):00,00
; 18.19 Tasks. Prevent apps from accessing tasks
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessTasks_ForceAllowTheseApps"=hex(7):00,00
; 18.19 Tasks. Prevent apps from accessing tasks
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsAccessTasks_ForceDenyTheseApps"=hex(7):00,00
; 18.20 App Diagnostics. Prevent apps from accessing diagnostic information
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsGetDiagnosticInfo"=dword:2
; 18.20 App Diagnostics. Prevent apps from accessing diagnostic information
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsGetDiagnosticInfo_UserInControlOfTheseApps"=hex(7):00,00
; 18.20 App Diagnostics. Prevent apps from accessing diagnostic information
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsGetDiagnosticInfo_ForceAllowTheseApps"=hex(7):00,00
; 18.20 App Diagnostics. Prevent apps from accessing diagnostic information
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsGetDiagnosticInfo_ForceDenyTheseApps"=hex(7):00,00
; 18.21 Inking & Typing. Turn off Inking & Typing data collection
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\TextInput]
"AllowLinguisticDataCollection"=dword:0
; 18.22 Activity History. Turn off tracking of your Activity History
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"EnableActivityFeed"=dword:0
; 18.22 Activity History. Turn off tracking of your Activity History
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"PublishUserActivities"=dword:0
; 18.22 Activity History. Turn off tracking of your Activity History
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"UploadUserActivities"=dword:0
; 18.23 Voice Activation. Turn Off apps ability to listen for a Voice keyword
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsActivateWithVoice"=dword:2
; 18.23 Voice Activation. Turn Off apps ability to listen for a Voice keyword
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\AppPrivacy]
"LetAppsActivateWithVoiceAboveLock"=dword:2
; 18.24 News and interests. Disable Windows Feeds
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Windows Feeds]
"EnableFeeds"=dword:00000000
; 19. Software Protection Platform. Turn off sending KMS client activation data to Microsoft
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\CurrentVersion\Software Protection Platform]
"NoGenTicket"=dword:1
; 20. Storage health. Turn off downloading updates to the Disk Failure Prediction Model
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\StorageHealth]
"AllowDiskHealthModelUpdates"=dword:0
; 21. Sync your settings. Turn off settings sync
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SettingSync]
"DisableSettingSync"=dword:2
; 21. Sync your settings. Turn off settings sync
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SettingSync]
"DisableSettingSyncUserOverride"=dword:1
; 22. Teredo. Disable Teredo
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\TCPIP\v6Transition]
"Teredo_State"="Disabled"
; 23. Wi-Fi Sense. Turn off the feature
[HKEY_LOCAL_MACHINE\Software\Microsoft\wcmsvc\wifinetworkmanager\config]
"AutoConnectAllowedOEM"=dword:0
; 24. Microsoft Defender Antivirus. Disconnect from the Microsoft Antimalware Protection Service
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows Defender\Spynet]
"SpynetReporting"=dword:0
; 24. Microsoft Defender Antivirus. Stop sending file samples back to Microsoft
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows Defender\Spynet]
"SubmitSamplesConsent"=dword:2
; 24. Microsoft Defender Antivirus. Stop downloading Definition Updates
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows Defender\Signature Updates]
"FallbackOrder"="FileShares"
; 24. Microsoft Defender Antivirus. Stop downloading Definition Updates
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows Defender\Signature Updates]
"DefinitionUpdateFileSharesSources"="Nothing"
; 24. Microsoft Defender Antivirus. Turn off Malicious Software Reporting Tool (MSRT) diagnostic data:
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\MRT]
"DontReportInfectionInformation"=dword:00000001
; 24. Microsoft Defender Antivirus. Turn off Enhanced Notifications
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows Defender\Reporting]
"DisableEnhancedNotifications"=dword:1
; 24.1 Microsoft Defender SmartScreen. Disable feature
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"EnableSmartScreen"=dword:0
; 24.1 Microsoft Defender SmartScreen. Disable feature
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows Defender\SmartScreen]
"ConfigureAppInstallControlEnabled"=dword:1
; 24.1 Microsoft Defender SmartScreen. Disable feature
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows Defender\SmartScreen]
"ConfigureAppInstallControl"="Anywhere"
; 24.1 Microsoft Defender SmartScreen. Disable feature
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"ShellSmartScreenLevel"=-
; 25. Personalized Experiences. Disable feature
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CloudContent]
"DisableCloudOptimizedContent"=dword:1
; 26. Microsoft Store. Disable all apps from Microsoft Store
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\WindowsStore]
"DisableStoreApps"=dword:1
; 26. Microsoft Store. Turn off Automatic Download and Install of updates.
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\WindowsStore]
"AutoDownload"=dword:2
; 27. Apps for websites. Turn off apps for websites
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"EnableAppUriHandlers"=dword:0
; 28.3. Delivery Optimization. (simple mode) prevent P2P traffic
; Value is Hex 63 = 99 decimal
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\DeliveryOptimization]
"DODownloadMode"=dword:63
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"DoNotConnectToWindowsUpdateInternetLocations"=dword:1
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"DisableWindowsUpdateAccess"=dword:1
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"WUServer"=" "
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"WUStatusServer"=" "
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"UpdateServiceUrlAlternate"=" "
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU]
"UseWUServer"=dword:1
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"FillEmptyContentUrls"=-
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"DoNotEnforceEnterpriseTLSCertPinningForUpdateDetection"=-
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate]
"SetProxyBehaviorForUpdateDetection"=dword:0
; 29. Windows Update. Turn off
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsStore\WindowsUpdate]
"AutoDownload"=dword:00000005
; 30. Cloud Clipboard
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System]
"AllowCrossDeviceClipboard"=dword:0
; 31. Services Configuration. Turn off
[HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\DataCollection]
"DisableOneSettingsDownloads"=dword:00000001
PowerShell-скрипт, удаляющий ВСЕ встроенные приложения
get-AppxPackage | Remove-AppxPackage
$packs = Get-AppxProvisionedPackage -online | Select-Object PackageName
foreach ($pack in $packs) {Remove-AppxProvisionedPackage -online -PackageName $pack.PackageName}
get-AppxPackage -allusers | Remove-AppxPackage
'Uninstalling OneDrive...'
taskkill.exe /F /IM "OneDrive.exe"
& "$env:systemroot\SysWOW64\OneDriveSetup.exe" /uninstall
'... waiting until OneDrive will be uninstalled ....'
while (Test-Path $env:LOCALAPPDATA\Microsoft\OneDrive\OneDrive.exe) { Start-Sleep 1 }
'... OneDrive Uninstalling complete!'
Применим все эти файлы, перезагрузимся и посмотрим, что станет с трафиком.
Важно! Перед применением REG-файлов необходимо отключить самозащиту Windows Defender (Tamper protection). О том, как это сделать, будет в конце статьи.

«Паразитный» трафик уменьшился в разы, но, ожидаемо, не пропал полностью. Анализ фонового трафика находящейся в простое ВМ выявил следующих «болтунов»:
- MS Edge;
- Сервис Delivery Optimization (DoSvc);
- Сервис AppX Deployment Service (AppXSVC);
- Сервис Windows Update (wuauserv).
С большей частью болтунов можно разобраться, указав в свойствах сетевого подключения, что оно лимитированное (mettered). Для проводных (Ethernet) соединений сделать это можно с помощью скрипта под спойлером.
PowerShell-скрипт, устанавливающий признак лимитированного соединения
<#
.SYNOPSIS : PowerShell script to set Ethernet connection as metered or not metered
.AUTHOR : Michael Pietroforte
.SITE : https://4sysops.com
#>
#We need a Win32 class to take ownership of the Registry key
$definition = @"
using System;
using System.Runtime.InteropServices;
namespace Win32Api
{
public class NtDll
{
[DllImport("ntdll.dll", EntryPoint="RtlAdjustPrivilege")]
public static extern int RtlAdjustPrivilege(ulong Privilege, bool Enable, bool CurrentThread, ref bool Enabled);
}
}
"@
Add-Type -TypeDefinition $definition -PassThru | Out-Null
[Win32Api.NtDll]::RtlAdjustPrivilege(9, $true, $false, [ref]$false) | Out-Null
#Setting ownership to Administrators
$key = [Microsoft.Win32.Registry]::LocalMachine.OpenSubKey("SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\DefaultMediaCost",[Microsoft.Win32.RegistryKeyPermissionCheck]::ReadWriteSubTree,[System.Security.AccessControl.RegistryRights]::takeownership)
$acl = $key.GetAccessControl()
$acl.SetOwner([System.Security.Principal.NTAccount]"Administrators")
$key.SetAccessControl($acl)
#Giving Administrators full control to the key
$rule = New-Object System.Security.AccessControl.RegistryAccessRule ([System.Security.Principal.NTAccount]"Administrators","FullControl","Allow")
$acl.SetAccessRule($rule)
$key.SetAccessControl($acl)
#Setting Ethernet as metered or not metered
$path = "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\DefaultMediaCost"
$name = "Ethernet"
$metered = Get-ItemProperty -Path $path | Select-Object -ExpandProperty $name
New-ItemProperty -Path $path -Name $name -Value "2" -PropertyType DWORD -Force | Out-Null
Write-Host "Ethernet is now set to metered."
После применения этого скрипта объём передаваемого трафика снизится ещё больше (~1Mb/час), а единственным болтуном останется MS Edge. Если вы планируете использовать этот браузер в дальнейшем, то на этом можно и успокоиться. Для тех же, кто хочет полной приватности, необходимо победить финального босса — MS Edge.
Чтобы прикрыть ему рот, необходимо с помощью штатных средств (Menu > Settings) настроить браузер таким образом, чтобы он использовал облачные службы, синхронизировался и выполнял прочую сетевую активность по минимуму. Если требуется настроить несколько машин, то можно только на одной настроить пользовательский профиль в браузере, а потом копировать его на все другие машины. Профиль хранится в «%LOCALAPPDATA%\Microsoft\Edge\User Data».
После настройки браузера необходимо отключить службы Edge, отвечающие за обновления, и удалить задания из системного планировщика. Сделать всё это можно следующим скриптом:
PowerShell-скрипт, отключающий службы обновления MS Edge
'Killing MS Edge processes...'
C:\Windows\System32\taskkill.exe /F /IM "msedge.exe"
'Stroping MS Edge update related services...'
C:\Windows\System32\net.exe stop MicrosoftEdgeElevationService
C:\Windows\System32\net.exe stop edgeupdate
C:\Windows\System32\net.exe stop edgeupdatem
'Disabling MS Edge update related services...'
C:\Windows\System32\sc.exe config MicrosoftEdgeElevationService obj= .\Guest start= disabled
C:\Windows\System32\sc.exe config edgeupdate obj= .\Guest start= disabled
C:\Windows\System32\sc.exe config edgeupdatem obj= .\Guest start= disabled
'Removing MS Edge update related Scheduler Tasks...'
Get-ScheduledTask -TaskName "*EdgeUpdate*" | Unregister-ScheduledTask -Confirm:$false
После всех этих манипуляций с MS Edge система полностью прекратит генерировать фоновый Интернет-трафик (при измерении в режиме простоя). Важно отметить, что любой неосторожный запуск MS Edge приведёт к тому, что он снова будет втихаря стучаться в Интернет. Так что будьте осторожны.
▍ Отключение Windows Defender
Данный шаг является опциональным, поскольку болтливость встроенного антивируса существенно ограничится REG-файлами, приведёнными выше. Однако, в условиях, когда антивирус не обновляется, он теряет всякую актуальность и жрёт ресурсы впустую. Чтобы его отключить, нужно сделать следующее:
- Руками, с помощью GUI в настройках антивируса необходимо отключить опцию «Tamper protection» (Settings > Update & Security > Windows Security > Virus & Threat protection > Virus & Threat protection settings > Tamper protection off).
- Затем следует применить следующий REG-файл.
REG-файл, отключающий Windows Defender
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender] "DisableAntiSpyware"=dword:00000001
▍ Краткая инструкция применения данного способа блокировки
- Загрузить REG-файлы уровня пользователя user.reg и уровня компьютера comp.reg.
- Запустить скрипт, удаляющий встроенные приложения.
- Запустить скрипт, устанавливающий признак лимитированного соединения.
- Провести настройку браузера MS Edge.
- Запустить скрипт, отключающий механизмы обновления MS Edge.
▍ Послевкусие и стратегия использования
Как уже отмечалось выше, любые попытки отключения сетевых возможностей ОС Windows 10 приводят к проблемам. Данный способ не исключение.
Практика показала, что после проведения всех этих манипуляций некоторые программы, например, Mozilla Firefox, отказываются инсталлироваться. Тем не менее ранее установленные программы, тот же Firefox, продолжают работать. Всё это говорит о том, что стратегия «затыкания рта Windows» должна быть такой:
- Полностью обновить ОС.
- Инсталляция и настройка требуемых сторонних программ.
- Отключение «паразитного» сетевого трафика.
Помоги спутнику бороться с космическим мусором в нашей новой игре! 🛸

Configuring Windows Firewall settings is one of the most fundamental security precautions. It is a built-in security feature that comes with all versions of Windows, acting as a barrier between your computer and the internet while blocking any unauthorized access to your system. It monitors inbound and outbound traffic and prevents malicious software from accessing your computer.
This article will look at configuring Windows Firewall settings for better security.
Understanding Windows Firewall
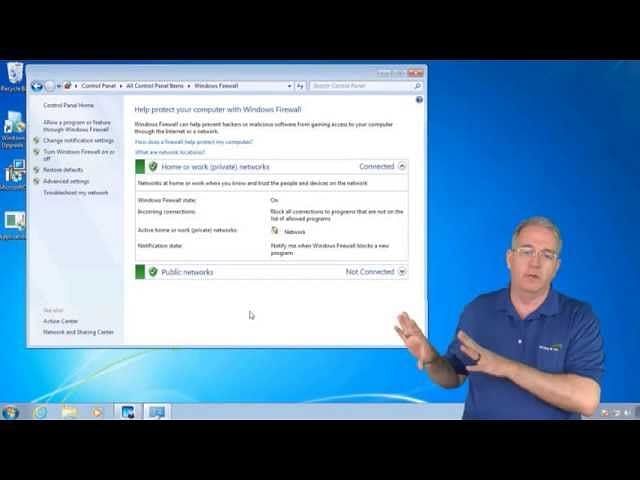
Before customizing the Windows Firewall settings, it is important to understand how it works. Windows Firewall applies a set of rules to determine which traffic is permitted and which is denied. Windows Firewall, by default, blocks all incoming traffic while allowing all outbound traffic.
Windows Firewall has three types of profiles: domain, private, and public. The Domain profile is applied when a computer is associated with a domain. When a computer is connected to a private network, the Private profile is applied. For a computer connected to a public network, such as a coffee shop or airport, a Public profile is applied.
Configuring Windows Firewall settings

The first step to customizing Windows Firewall settings is to turn it on. Windows Firewall is enabled by default in all versions of Windows, but it is important to double-check that it is activated.
To see if the Windows Firewall is enabled, go to the Control Panel and select «System and Security.» Select «Windows Firewall» and ensure that the «Windows Firewall On or Off» option is set to «On.»
Once you have confirmed that Windows Firewall is enabled, you can start customizing its settings. Custom rules may be created in the firewall to restrict or allow traffic depending on certain criteria. You can set rules that allow traffic from specified IP addresses while blocking access to specific ports.
To create a new rule in Windows Firewall, follow these steps:
1) Navigate to the Control Panel and select «System and Security.»
2) Select «Windows Firewall» and then «Advanced Settings.»
3) In the left pane, select «Inbound Rules» or «Outbound Rules,» depending on whether you wish to prevent or allow traffic.
4) Click the «New Rule» button in the right pane.
5) Create your rule by using the on-screen instructions.
You can also modify the existing rules by right-clicking on the rule and selecting «Properties.» From there, you can change the criteria for the rule or disable it altogether.
Creating exceptions in Windows Firewall
In a few cases, you can make exceptions in Windows Firewall that allow programs or services to communicate over the firewall that would otherwise be restricted.
To create an exception in Windows Firewall, follow these steps:
1) Go to the Control Panel and click «System and Security.»
2) Click on «Windows Firewall» and then click on «Advanced Settings.»
3) In the left pane, click on «Inbound Rules» or «Outbound Rules,» depending on the type of traffic you want to allow.
4) Click on «New Rule» in the right pane.
5) Select «Program» as the rule type and follow the on-screen instructions to select the program you want to allow.
Read how exceptions work and how Windows Firewall blocks Diablo 4.
Managing notifications and logging in Windows Firewall
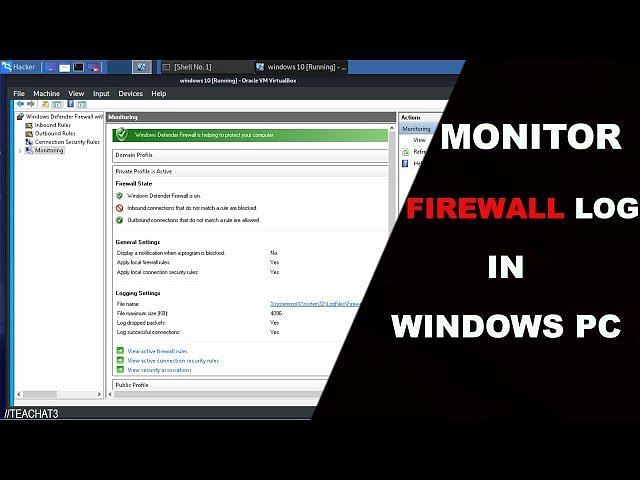
Windows Firewall can be configured to notify you when it blocks an incoming or outgoing connection. This can be helpful in identifying potential threats and responding to them appropriately.
To manage notifications in Windows Firewall, follow these steps:
1) Navigate to the Control Panel and select «System and Security.»
2) Select «Windows Firewall» and then «Advanced Settings.»
3) In the left pane, double-click «Windows Firewall Properties.»
4) Under «Logging,» select «Customise» to specify the connections you wish to log.
5) Under «Notifications,» choose the option that best meets your requirements.
Best practices for configuring Windows Firewall settings
While configuring Windows Firewall settings is an important step in computer security, several practices must be followed to ensure maximum protection. Here are a few crucial points to keep in mind:
1) Keep Windows Firewall updated.
2) Use multiple layers of protection.
3) Regularly review and update Windows Firewall rules.
4) Block unnecessary traffic.
5) Disable unnecessary services and programs.
Conclusion
Setting up your Windows Firewall is essential in protecting your computer and personal data. You may customize your Windows Firewall settings to restrict unauthorized access and prevent malware from attacking your PC by following the methods suggested in this article.
To maintain optimum security, review and update your Windows Firewall rules frequently, keep Windows Firewall updated, and use several levels of protection. With these suggestions in mind, you can use your computer knowing your sensitive information is safe.
-
Clickbait / Misleading
-
Factually Incorrect
-
Hateful or Abusive
-
Baseless Opinion
-
Too Many Ads
-
Other
Submit
Was this article helpful?
Thank You for feedback
About the author
Orvill Samanta is an analyst and journalist on Gaming Tech at Sportskeeda. When he isn’t exploring the latest tech trends, he’s immersing himself in captivating anime worlds, valorent, indulging his passion for all things anime.
Know More
Edited by Dinesh Renthlei


























