| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1 Windows 2016 and 10 Windows Server 2019 and 2022 Windows Server 2025 |
|
Category • Subcategory |
Account Logon • Kerberos Authentication Service |
| Type |
Success
Failure |
|
Corresponding events in Windows 2003 and before |
672 , 676
|
4768: A Kerberos authentication ticket (TGT) was requested
On this page
- Description of this event
- Field level details
- Examples
This event is logged on domain controllers only and both success and failure instances of this event are logged.
At the beginning of the day when a user sits down at his or her workstation and enters his domain username and password, the workstation contacts a local DC and requests a TGT. If the username and password are correct and the user account passes status and restriction checks, the DC grants the TGT and logs event ID 4768 (authentication ticket granted).
If the ticket request fails Windows will either log this event, 4768 or 4771 with failure as the type.
The User field for this event (and all other events in the Audit account logon event category) doesn’t help you determine who the user was; the field always reads N/A. Rather look at the Account Information: fields, which identify the user who logged on and the user account’s DNS suffix. The User ID field provides the SID of the account.
Windows logs other instances of event ID 4768 when a computer in the domain needs to authenticate to the DC typically when a workstation boots up or a server restarts. In these instances, you’ll find a computer name in the User Name and fields. Computer generated kerberos events are always identifiable by the $ after the computer account’s name.
Microsoft’s Comments:
This event records that a Kerberos TGT was granted, actual access will not occur until a service ticket is granted, which is audited by Event 673. If the PATYPE is PKINIT, the logon was a smart card logon.
Result codes:
| Result code | Kerberos RFC description | Notes on common failure codes |
| 0x1 | Client’s entry in database has expired | |
| 0x2 | Server’s entry in database has expired | |
| 0x3 | Requested protocol version # not supported | |
| 0x4 | Client’s key encrypted in old master key | |
| 0x5 | Server’s key encrypted in old master key | |
| 0x6 | Client not found in Kerberos database | Bad user name, or new computer/user account has not replicated to DC yet |
| 0x7 | Server not found in Kerberos database | New computer account has not replicated yet or computer is pre-w2k |
| 0x8 | Multiple principal entries in database | |
| 0x9 | The client or server has a null key | administrator should reset the password on the account |
| 0xA | Ticket not eligible for postdating | |
| 0xB | Requested start time is later than end time | |
| 0xC | KDC policy rejects request | Workstation restriction, or Authentication Policy Silo (look for event ID 4820) |
| 0xD | KDC cannot accommodate requested option | |
| 0xE | KDC has no support for encryption type | |
| 0xF | KDC has no support for checksum type | |
| 0x10 | KDC has no support for padata type | |
| 0x11 | KDC has no support for transited type | |
| 0x12 | Clients credentials have been revoked | Account disabled, expired, locked out, logon hours. |
| 0x13 | Credentials for server have been revoked | |
| 0x14 | TGT has been revoked | |
| 0x15 | Client not yet valid — try again later | |
| 0x16 | Server not yet valid — try again later | |
| 0x17 | Password has expired | The user’s password has expired. |
| 0x18 | Pre-authentication information was invalid | Usually means bad password |
| 0x19 | Additional pre-authentication required* | |
| 0x1F | Integrity check on decrypted field failed | |
| 0x20 | Ticket expired | Frequently logged by computer accounts |
| 0x21 | Ticket not yet valid | |
| 0x21 | Ticket not yet valid | |
| 0x22 | Request is a replay | |
| 0x23 | The ticket isn’t for us | |
| 0x24 | Ticket and authenticator don’t match | |
| 0x25 | Clock skew too great | Workstation’s clock too far out of sync with the DC’s |
| 0x26 | Incorrect net address | IP address change? |
| 0x27 | Protocol version mismatch | |
| 0x28 | Invalid msg type | |
| 0x29 | Message stream modified | |
| 0x2A | Message out of order | |
| 0x2C | Specified version of key is not available | |
| 0x2D | Service key not available | |
| 0x2E | Mutual authentication failed | may be a memory allocation failure |
| 0x2F | Incorrect message direction | |
| 0x30 | Alternative authentication method required* | |
| 0x31 | Incorrect sequence number in message | |
| 0x32 | Inappropriate type of checksum in message | |
| 0x3C | Generic error (description in e-text) | |
| 0x3D | Field is too long for this implementation |
Free Security Log Resources by Randy
- Free Security Log Quick Reference Chart
- Windows Event Collection: Supercharger Free Edtion
- Free Active Directory Change Auditing Solution
- Free Course: Security Log Secrets
Description Fields in
4768
Account Information:
- Account Name: logon name of the account that just authenticated
- Supplied Realm Name: domain name of the account
- User ID: SID of the account
- MSDS-SupportedEncryptionTypes:
- Available Keys:
Service Information:
- Service Name: always «krbtgt»
- Service ID:
- MSDS-SupportedEncryptionTypes:
- Available Keys:
Domain Controller Information:
- MSDS-SupportedEncryptionTypes:
- Available Keys:
Network Information:
- Client Address: IP address where user is present
- Client Port: source port
- Advertized Etypes:
Additional Information:
- Ticket Options: unknown. Please start a discussion if you have information to share on this field.
- Result Code: error if any — see above table
- Ticket Encryption Type: unknown. Please start a discussion if you have information to share on this field.
- Session Encryption Type:
- Pre-Authentication Type: unknown. Please start a discussion if you have information to share on this field.
- Pre-Authentication EncryptionType:
Certificate Information:
This information is only filled in if logging on with a smart card.
- Certificate Issuer Name:
- Certificate Serial Number:
- Certificate Thumbprint:
Ticket Information:
- Response ticket hash: Unique identifier of the ticket issuedy by the domain controller which can be either a ticket granting ticket (event id 4768) or a ticket granting service (event id 4769 and 4770)
Supercharger Enterprise
Load Balancing for Windows Event Collection
Examples of 4768
Success
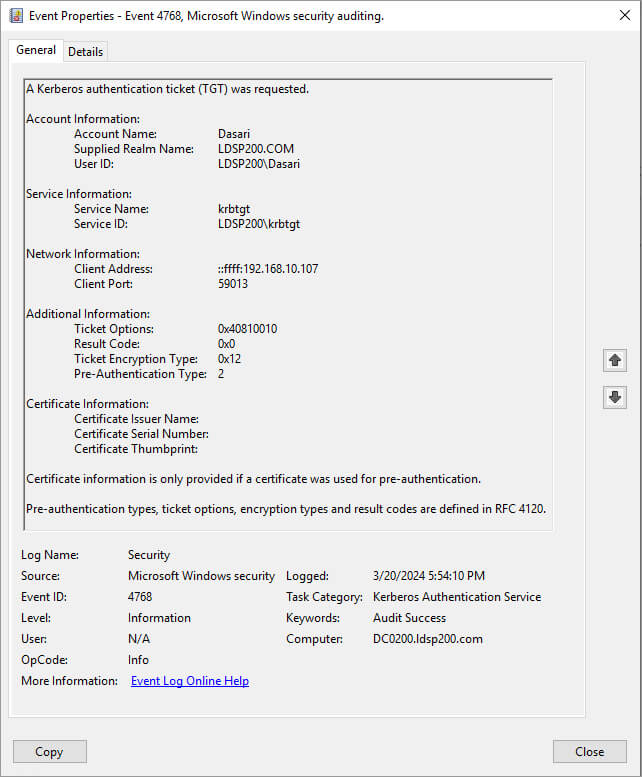
A Kerberos authentication ticket (TGT) was requested.
Account Information:
Account Name: Administrator
Supplied Realm Name: acme-fr
User ID: ACME-FR\administrator
MSDS-SupportedEncryptionTypes:
Available Keys:
Service Information:
Service Name: krbtgt
Service ID: ACME-FR\krbtgt
MSDS-SupportedEncryptionTypes:
Available Keys:
Domain Controller Information:
MSDS-SupportedEncryptionTypes:
Available Keys:
Network Information:
Client Address: ::1
Client Port: 0
Advertized Etypes:
Additional Information:
Ticket Options: 0x40810010
Result Code: 0x0
Ticket Encryption Type: 0x12
Session Encryption Type:
Pre-Authentication Type: 2
Pre-Authentication EncryptionType:
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Ticket Information:
Response Ticket Hash:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120.
Failure
A Kerberos authentication ticket (TGT) was requested.
Account Information:
Account Name: nebuchadnezzar
Supplied Realm Name: acme-fr
User ID: NULL SID
MSDS-SupportedEncryptionTypes:
Available Keys:
Service Information:
Service Name: krbtgt/acme-fr
Service ID: NULL SID
MSDS-SupportedEncryptionTypes:
Available Keys:
Domain Controller Information:
MSDS-SupportedEncryptionTypes:
Available Keys:
Network Information:
Client Address: ::1
Client Port: 0
Advertized Etypes:
Additional Information:
Ticket Options: 0x40810010
Result Code: 0x12
Ticket Encryption Type: 0xffffffff
Session Encryption Type:
Pre-Authentication Type: —
Pre-Authentication EncryptionType:
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Ticket Information:
Response Ticket Hash:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120. EditMore Resources
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection
- The Changing Landscape of Authentication and Logon Tracking in Hybrid Environments of Entra and AD
|
Время на прочтение4 мин
Количество просмотров309K

Рэнди Франклин Смит (CISA, SSCP, Security MVP) имеет в своем арсенале очень полезный документ, рассказывающий о том, какие события (event IDs) обязательно должны отслеживаться в рамках обеспечения информационной безопасности Windows. В этом документе изложена крайне полезная информация, которая позволит Вам “выжать” максимум из штатной системы аудита. Мы подготовили перевод этого материала. Заинтересованных приглашаем под кат.
О том, как настроить аудит, мы уже обстоятельно писали в одном из наших постов. Но из всех event id, которые встречаются в журналах событий, необходимо остановить свое внимание на нескольких критических важных. На каких именно – решать каждому. Однако Рэнди Франклин Смит предлагает сосредоточить внимание на 10 важных событиях безопасности в Windows.
Контроллеры доменов
Event ID — (Категория) — Описание
1) 675 или 4771
(Аудит событий входа в систему)
Событие 675/4771 на контроллере домена указывает на неудачную попытку войти через Kerberos на рабочей станции с доменной учетной записью. Обычно причиной этого является несоответствующий пароль, но код ошибки указывает, почему именно аутентификация была неудачной. Таблица кодов ошибок Kerberos приведена ниже.
2) 676, или Failed 672 или 4768
(Аудит событий входа в систему)
Событие 676/4768 логгируется для других типов неудачной аутентификации. Таблица кодов Kerberos приведена ниже.
ВНИМАНИЕ: В Windows 2003 Server событие отказа записывается как 672 вместо 676.
3) 681 или Failed 680 или 4776
(Аудит событий входа в систему)
Событие 681/4776 на контроллере домена указывает на неудачную попытку входа в систему через
NTLM с доменной учетной записью. Код ошибки указывает, почему именно аутентификация была неудачной.
Коды ошибок NTLM приведены ниже.
ВНИМАНИЕ: В Windows 2003 Server событие отказа записывается как 680 вместо 681.
4) 642 или 4738
(Аудит управления учетными записями)
Событие 642/4738 указывает на изменения в указанной учетной записи, такие как сброс пароля или активация деактивированной до этого учетной записи. Описание события уточняется в соответствие с типом изменения.
5) 632 или 4728; 636 или 4732; 660 или 4756
(Аудит управления учетными записями)
Все три события указывают на то, что указанный пользователь был добавлен в определенную группу. Обозначены Глобальная (Global), Локальная (Local) и Общая (Universal) соответственно для каждого ID.
6) 624 или 4720
(Аудит управления учетными записями)
Была создана новая учетная запись пользователя
7) 644 или 4740
(Аудит управления учетными записями)
Учетная запись указанного пользователя была заблокирована после нескольких попыток входа

(Аудит системных событий)
Указанный пользователь очистил журнал безопасности
Вход и выход из системы (Logon/Logoff)
Event Id — Описание
528 или 4624 — Успешный вход в систему
529 или 4625 — Отказ входа в систему – Неизвестное имя пользователя или неверный пароль
530 или 4625 Отказ входа в систему – Вход в систему не был осуществлен в течение обозначенного периода времени
531 или 4625 — Отказ входа в систему – Учетная запись временно деактивирована
532 или 4625 — Отказ входа в систему – Срок использования указанной учетной записи истек
533 или 4625 — Отказ входа в систему – Пользователю не разрешается осуществлять вход в систему на данном компьютере
534 или 4625 или 5461 — Отказ входа в систему – Пользователь не был разрешен запрашиваемый тип входа на данном компьютере
535 или 4625 — Отказ входа в систему – Срок действия пароля указанной учетной записи истек
539 или 4625 — Отказ входа в систему – Учетная запись заблокирована
540 или 4624 — Успешный сетевой вход в систему (Только Windows 2000, XP, 2003)
Типы входов в систему (Logon Types)
Тип входа в систему — Описание
2 — Интерактивный (вход с клавиатуры или экрана системы)
3 — Сетевой (например, подключение к общей папке на этом компьютере из любого места в сети или IIS вход — Никогда не заходил 528 на Windows Server 2000 и выше. См. событие 540)
4 — Пакет (batch) (например, запланированная задача)
5 — Служба (Запуск службы)
7 — Разблокировка (например, необслуживаемая рабочая станция с защищенным паролем скринсейвером)
8 — NetworkCleartext (Вход с полномочиями (credentials), отправленными в виде простого текст. Часто обозначает вход в IIS с “базовой аутентификацией”)
9 — NewCredentials
10 — RemoteInteractive (Терминальные службы, Удаленный рабочий стол или удаленный помощник)
11 — CachedInteractive (вход с кешированными доменными полномочиями, например, вход на рабочую станцию, которая находится не в сети)
Коды отказов Kerberos
Код ошибки — Причина
6 — Имя пользователя не существует
12 — Ограничение рабочей машины; ограничение времени входа в систему
18 — Учетная запись деактивирована, заблокирована или истек срок ее действия
23 — Истек срок действия пароля пользователя
24 — Предварительная аутентификация не удалась; обычно причиной является неверный пароль
32 — Истек срок действия заявки. Это нормальное событие, которое логгируется учетными записями компьютеров
37 — Время на рабочей машины давно не синхронизировалось со временем на контроллере домена
Коды ошибок NTLM
Код ошибки (десятичная система) — Код ошибки (16-ричная система) — Описание
3221225572 — C0000064 — Такого имени пользователя не существует
3221225578 — C000006A — Верное имя пользователя, но неверный пароль
3221226036 — C0000234 — Учетная запись пользователя заблокирована
3221225586 — C0000072 — Учетная запись деактивирована
3221225583 — C000006F — Пользователь пытается войти в систему вне обозначенного периода времени (рабочего времени)
3221225584 — C0000070 — Ограничение рабочей станции
3221225875 — C0000193 — Истек срок действия учетной записи
3221225585 — C0000071 — Истек срок действия пароля
3221226020 — C0000224 — Пользователь должен поменять пароль при следующем входе в систему
Еще раз продублируем ссылку на скачивание документа на сайте Рэнди Франклина Смита www.ultimatewindowssecurity.com/securitylog/quickref/Default.aspx. Нужно будет заполнить небольшую форму, чтобы получить к нему доступ.
P.S. Хотите полностью автоматизировать работу с журналами событий? Попробуйте новую версию NetWrix Event Log Manager 4.0, которая осуществляет сбор и архивирование журналов событий, строит отчеты и генерирует оповещения в режиме реального времени. Программа собирает данные с многочисленных компьютеров сети, предупреждает Вас о критических событиях и централизованно хранит данные обо всех событиях в сжатом формате для удобства анализа архивных данных журналов. Доступна бесплатная версия программы для 10 контроллеров доменов и 100 компьютеров.
Last Updated on December 24, 2024 by Deepanshu Sharma

Have you ever pondered over the intricacies of digital security in a world where data breaches lurk around every digital corner? Picture this: you’re safeguarding your organization’s network, but are you certain that every user accessing it is who they claim to be? Enter Kerberos, the guardian angel of network authentication. But here’s the catch: how do you ensure Kerberos itself isn’t compromised? The answer lies within Event ID 4768, the gateway to deciphering Kerberos authentication tickets.
Event ID 4768 Components
Account Information
Account Name: Specifies the name of the account for which a Ticket Granting Ticket (TGT) was requested. Notably, computer account names end with a $ symbol.
Supplied Realm Name: Identifies the Kerberos Realm to which the Account Name belongs.
User ID: Represents the Security Identifier (SID) of the account that requested a TGT. If the SID cannot be resolved, the source data appears in the event.
Service Information
Service Name: Indicates the name of the service in the Kerberos Realm to which the TGT request was sent.
Service ID: Denotes the SID of the service account in the Kerberos Realm to which the TGT request was sent.
Network Information
Client Address: Specifies the IP address of the computer from which the TGT request was received.
Client Port: Indicates the source port number of the client network connection. It’s typically “0” for local (localhost) requests.
Additional Information
Ticket Options: Represents a set of different ticket flags in hexadecimal format, including values like Forwardable, Renewable, Canonicalize, and Renewable-ok.
Result Code: Displays a set of different failure codes in hexadecimal format, providing insights into the outcome of the authentication attempt. Possible causes are varied, including issues like expired passwords, invalid credentials, or unsupported encryption types.
Ticket Encryption Type: Specifies the cryptographic suite used for issuing the TGT, such as DES, AES, or RC4.
Pre-Authentication Type: Indicates the code number of the pre-authentication type used for the TGT request, offering details about the authentication method employed.
Certificate Issuer Name: Identifies the name of the Certificate Authority (CA) that issued the smart card certificate.
Certificate Serial Number: Represents the serial number of the smart card certificate used during logon.
Certificate Thumbprint: Denotes the thumbprint of the smart card certificate, providing a unique identifier for authentication purposes.
Event 4768 Result Codes
0x16Server not yet valid – try again later
0x18Pre-authentication information was invalidUsually means bad password0x1FIntegrity check on decrypted field failed
0x21Ticket not yet valid
0x23The ticket isn’t for us
| Result code | Kerberos RFC description | Notes on common failure codes |
|---|---|---|
| 0x1 | Client’s entry in database has expired | |
| 0x2 | Server’s entry in database has expired | |
| 0x3 | Requested protocol version # not supported | |
| 0x4 | Client’s key encrypted in old master key | |
| 0x5 | Server’s key encrypted in old master key | |
| 0x6 | Client not found in Kerberos database | Bad user name, or new computer/user account has not replicated to DC yet |
| 0x7 | Server not found in Kerberos database | New computer account has not replicated yet or computer is pre-w2k |
| 0x8 | Multiple principal entries in database | |
| 0x9 | The client or server has a null key | Administrator should reset the password on the account |
| 0xA | Ticket not eligible for postdating | |
| 0xB | Requested start time is later than end time | |
| 0xC | KDC policy rejects request | Workstation restriction, or Authentication Policy Silo (look for event ID 4820) |
| 0xD | KDC cannot accommodate requested option | |
| 0xE | KDC has no support for encryption type | |
| 0xF | KDC has no support for checksum type | |
| 0x10 | KDC has no support for padata type | |
| 0x11 | KDC has no support for transited type | |
| 0x12 | Clients credentials have been revoked | Account disabled, expired, locked out, logon hours. |
| 0x13 | Credentials for server have been revoked | |
| 0x14 | TGT has been revoked | |
| 0x15 | Client not yet valid – try again later | |
| 0x17 | Password has expired | The user’s password has expired. |
| 0x19 | Additional pre-authentication required* | |
| 0x20 | Ticket expired | Frequently logged by computer accounts |
| 0x22 | Request is a replay | |
| 0x24 | Ticket and authenticator don’t match | |
| 0x25 | Clock skew too great | Workstation’s clock too far out of sync with the DC’s |
| 0x26 | Incorrect net address | IP address change? |
| 0x27 | Protocol version mismatch | |
| 0x28/td> | Invalid msg type | |
| 0x29 | Message stream modified | |
| 0x2A | Message out of order | |
| 0x2C | Specified version of key is not available | |
| 0x2D | Service key not available | |
| 0x2E | Mutual authentication failed | May be a memory allocation failure |
| 0x2F | Incorrect message direction | |
| 0x30 | Alternative authentication method required* | |
| 0x31 | Incorrect sequence number in message | |
| 0x32 | Inappropriate type of checksum in message | |
| 0x3C | Generic error (description in e-text) | |
| 0x3D | Field is too long for this implementation |
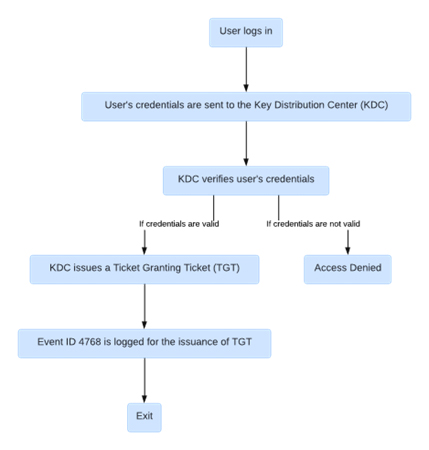
How Does Kerberos Authentication Align with Event ID 4768?
Within the intricate maze of network security, Kerberos emerges as a steadfast guardian, meticulously validating the identities of users as they navigate the digital landscape. Fundamentally, Kerberos functions as a robust network authentication protocol, meticulously crafted to facilitate secure communication over inherently non-secure networks. Yet, amid the tumultuous skirmishes of the digital realm, one event shines with unparalleled importance – Event ID 4768. Like a beacon piercing through the darkness, Event ID 4768 serves as a guiding light, illuminating the intricate path of Kerberos authentication and unraveling its mysteries within the labyrinth of network security.
As organizations strive to fortify their digital perimeters against ever-evolving cyber threats, understanding the nuances of Kerberos authentication and the role of Event ID 4768 becomes paramount. This introductory event marks the initiation of a complex authentication process, where users seek access to network resources through the procurement of Ticket Granting Tickets (TGTs) from the Key Distribution Center (KDC). However, beyond its surface significance lies a deeper layer of complexity. While Event ID 4768 heralds the commencement of the authentication exchange, it often conceals crucial details vital for effective security monitoring, such as the identity of the user initiating the request. Thus, amidst the intricate dance of network security, Event ID 4768 emerges as a focal point, compelling organizations to delve deeper into its implications and decipher its role in safeguarding digital assets against the relentless tide of cyber threats.
Understanding Event ID 4768
A. Ticket Granting Ticket (TGT)
At the core of Kerberos authentication lies the Ticket Granting Ticket (TGT), a digital key granting access to the network’s inner sanctum. Far beyond a mere credential, the TGT acts as the cornerstone of secure traversal across the digital landscape. It encapsulates the user’s authenticated identity, enabling seamless interaction with network resources while maintaining robust security protocols.
B. The Ritual of TGT Procurement
Event ID 4768 serves as the herald, signaling the commencement of the TGT procurement process. When a user seeks access to network resources, they embark on a journey orchestrated by the Key Distribution Center (KDC). This journey entails a series of cryptographic exchanges, culminating in the issuance of the coveted TGT. Event ID 4768 captures the essence of this ritual, offering insights into the intricate mechanisms governing user authentication within the Kerberos framework.
C. Unveiling the Veil of Secrecy
Despite its significance, Event ID 4768 operates within the confines of certain limitations. Notably, the event fails to disclose critical details, such as the identity of the user requesting the TGT. This omission poses challenges for security administrators, who must navigate the digital landscape armed with incomplete information. However, despite its limitations, Event ID 4768 remains a valuable tool in the arsenal of security professionals, offering glimpses into the inner workings of Kerberos authentication and guiding organizations towards enhanced network security practices.
In essence, understanding Event ID 4768 transcends mere technical proficiency; it necessitates a comprehensive grasp of the symbiotic relationship between Kerberos authentication and network security. By navigating the intricate nuances of this event, organizations can bolster their defenses against potential threats and navigate the digital landscape with confidence and resilience.
Why Monitor Event ID 4768?
In today’s dynamic cybersecurity landscape, vigilant monitoring of Event ID 4768 is essential for safeguarding digital environments. This event holds significant importance due to its various security benefits and compliance imperatives.
Security benefits associated with Event ID 4768 include the detection of potential privilege abuse. Monitoring helps identify unauthorized attempts to exploit elevated privileges, preventing potential breaches. It also aids in identifying suspicious activity, such as the Pass-the-Ticket technique, enabling prompt response measures. Additionally, organizations gain valuable insights into user interactions, aiding auditing processes and detecting anomalous behaviors indicating security risks.
Monitoring Event ID 4768 is crucial for meeting compliance requirements. Regulatory mandates necessitate Kerberos authentication event monitoring, including Event ID 4768, as a foundational element of compliance frameworks. Compliance obligations often demand specific security controls to protect sensitive data and ensure IT system integrity, with Event ID 4768 monitoring playing a vital role in demonstrating compliance. Compliance with industry standards builds trust among stakeholders, highlighting the strategic importance of monitoring Event ID 4768 in the ongoing fight against cyber threats.
Conclusion
In the ever-evolving landscape of digital security, Event ID 4768 emerges as a beacon, guiding the vigilant towards a realm of heightened awareness. By deciphering the cryptic messages embedded within this event, organizations can fortify their defenses against the machinations of digital adversaries. So, the next time Event ID 4768 graces your security logs, seize the opportunity to unveil its secrets and fortify the bastions of network security.
By understanding the nuances of Kerberos authentication and the significance of Event ID 4768, IT professionals can wield this knowledge as a potent weapon in the ongoing battle for digital sovereignty. So, as you traverse the digital frontier, remember – vigilance is the watchword, and Event ID 4768 is your compass guiding towards secure horizons.
- Event IDWindows
Event ID 4768 is an important security event logged by Windows operating systems when a Kerberos authentication ticket (TGT – Ticket Granting Ticket) is requested. This event is a normal part of the Kerberos authentication process which is integral to authenticating and authorizing users and services in a network. Understanding how to fix issues related to this event is crucial for maintaining a secure and efficient network. In this article, we will delve deep into the implications of Event ID 4768, what it indicates, and how to address any associated problems effectively.
Understanding Event ID 4768
The Kerberos authentication protocol is essential for secure identity verification in Windows environments, especially within Active Directory (AD) networks. When a user logs into a Windows domain, their credentials are verified against AD, which issues a Kerberos ticket if authentication is successful.
Event ID 4768 specifically indicates that a Kerberos TGT was requested. This request can be triggered by various actions:
- Users logging into their accounts.
- Service accounts starting, which may request their tickets.
- Applications that require tickets to access resources on the network.
The Event ID 4768 will generally look something like this in the Windows Security Event Log:
A Kerberos authentication ticket (TGT) was requested.
Subject:
Security ID: [Security ID of the requester]
Account Name: [Account Name of the requester]
Account Domain: [Domain or Source of the account]
Logon ID: [Unique Logon ID]
Service Information:
Service ID: [Service ID]
Service Name: [Service's SID]
Ticket Information:
Ticket Options: [...]
Ticket Encrypt Type: [...]
Ticket Lifetime: [...]
Client Address: [IP address]
Client Port: [Port number]The Significance of this Event
While Event ID 4768 itself does not indicate a problem, it can serve as a marker for issues related to authentication failures, improperly configured services, and even potential security breaches. Recognizing the patterns associated with this ID can help network administrators maintain the integrity of their services and address any security risks proactively.
Common Issues Associated with Event ID 4768
Despite being a part of a normal authentication process, several issues may arise in conjunction with Event ID 4768, particularly under the following circumstances:
1. Multiple Failed Logon Attempts
If you notice numerous 4768 events in quick succession, it could indicate users or services are repeatedly failing to authenticate. This could alert you to:
- Password issues (e.g., expired passwords).
- Accounts that are locked out or disabled.
- Misconfigured application identities, such as incorrect service principals.
2. Unusual Ticket Requests
Requests for Kerberos tickets from unusual or unexpected accounts may signal unauthorized access attempts, particularly if you observe requests from unknown IP addresses or applications.
3. Time Synchronization Issues
Kerberos relies heavily on time synchronization between the client and server. If there are discrepancies, it can lead to authentication failures that, while not directly logged as Event ID 4768, are reflected in event log failures that can stem from improper time settings.
4. Service Account Misconfiguration
Service accounts may request tickets as they authenticate to other services. If these accounts are misconfigured, you may see an abnormal number of requests alongside frequent failures.
Troubleshooting Steps
To effectively manage issues related to Event ID 4768, the following troubleshooting steps can be undertaken:
Step 1: Review the Event Logs
Begin by closely examining the Windows Event Viewer logs. Look at the Security logs, focusing on the timestamp and details surrounding Event ID 4768. Evaluate the Logon ID and the source accounts involved.
Step 2: Look for Related Events
Often, Event ID 4768 will be accompanied by other events such as:
- Event ID 4771 – Kerberos pre-authentication failed.
- Event ID 4740 – A user account was locked out.
Identifying patterns and correlating these events can offer insights into potential issues.
Step 3: Analyze Authentication Failures
Should any authentication failures be recorded, check the accounts involved to determine if they are locked out or if their passwords have expired. If issues are identified, follow the necessary protocols to reset passwords or unlock accounts.
Step 4: Check for Time Synchronization Issues
Ensure that all devices within the domain are synchronized with a reliable time service. Kerberos operates using timestamps, making accurate timekeeping vital. You can do this by verifying the time settings both on the client and the domain controllers. Use the following command to check the time settings:
w32tm /query /statusStep 5: Validate Service Account Credentials
If service accounts are involved, verify that:
- They have the correct permissions.
- Their passwords are not expired.
- They are configured properly within services.
Step 6: Implement Monitoring
Implement continuous monitoring solutions that can alert administrators to multiple ticket requests or failed authentications automatically. Such monitoring aids in the rapid identification of unusual patterns.
Step 7: Review Security Policies
Examine the Active Directory security policies to ensure they align with best practices for authentication. Incorporating policies around password expiry, account lockout thresholds, and Kerberos ticket lifetimes can enhance your AD’s resilience.
Common Resolutions to Problems
Once you’ve identified the issues contributing to the Event ID 4768 occurrences, addressing them may include the following remedies:
1. Resetting Passwords
For locked-out or expired accounts, reset the user passwords and verify their access to resources subsequently.
2. Configuring Time Synchronization
Use NTP (Network Time Protocol) to ensure all devices are time-synchronized:
- Configure the primary domain controller to an external NTP server.
- Update additional domain controllers and member servers to use the primary domain controller as their time source.
3. Updating Service Account Settings
Review any associated service accounts and ensure they are properly set up with valid credentials.
4. Adjusting Security Settings
Consider revising Active Directory security policies to better manage how authentication and access are governed. This may involve:
- Implementing stricter account lockout policies.
- Adjusting password policies to require complexity and regular updates.
5. Enabling Auditing Features
Increase the level of security auditing for user logon events. This can help trace back the source of the problem should similar issues arise in the future.
Conclusion
Understanding and troubleshooting Event ID 4768 is critical for maintaining a secure Windows environment. While the event itself may not indicate a fault, it serves as a reminder to review and verify an organization’s security posture regularly. The knowledge gained from analyzing authentication ticket requests can play a pivotal role in building a solid defense against unauthorized access and maintaining the integrity of network operations.
Taking proactive measures, monitoring account activities, validating configurations, and ensuring time synchronization are essential steps that contribute towards the efficient management of Kerberos authentication in Windows domains. Implementing these practices not only helps in rectifying issues related to Event ID 4768 but also strengthens the network’s overall security landscape.
Event ID 4768 is logged only in domain controller for both success and failure instances. If the username and password are correct and the DC grants the TGT and logs the Event ID 4768 (authentication ticket granted). If the ticket request fails Windows will either log the event 4768 with failure as the type or 4771. In this article, I am going to explain about how to enable or configure Event ID 4768 through Default Domain Controller Policy GPO and Auditpol.exe, and how to disable Event ID 4768.
Summary:
- Event ID 4768 Source
- Enable Event 4768 through Group Policy
- Enable Event 4768 via Auditpol
- Stop Event 4768 via GPO and Auditpol
Event ID 4768 Source
Log Name: Security Source: Microsoft-Windows-Security-Auditing Date: 5/5/2014 3:43:20 PM Event ID: 4768 Task Category: Kerberos Authentication Service Level: Information Keywords: Audit Success User: N/A Computer: Work2008R2.TestDomain.local Description: A Kerberos authentication ticket (TGT) was requested. Account Information: Account Name: LTest Supplied Realm Name: TESTDOMAIN User ID: TESTDOMAINLTest Service Information: Service Name: krbtgt Service ID: TESTDOMAINkrbtgt Network Information: Client Address: 192.78.2.145 Client Port: 0 Additional Information: Ticket Options: 0x40810010 Result Code: 0x0 Ticket Encryption Type: 0x12 Pre-Authentication Type: 2 Certificate Information: Certificate Issuer Name: Certificate Serial Number: Certificate Thumbprint: Certificate information is only provided if a certificate was used for pre-authentication. Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120.
Enable AD Logon Audit Event 4768 via Group Policy
To enable event id 4768 in every Domain Controller, We need to configure audit settings in Default Domain Controllers Policy, or you can create new GPO and links it to the Domain Controllers OU via GPMC console, or else you can configure the corresponding policies on Local Security Policy of each and every Domain Controller..
Follow the below steps to enable Active Directory Kerberos Logon Audit event 4768 via Default Domain Controllers Policy.
1. Press the key ‘Window’ + ‘R’
2. Type the command gpmc.msc, and click OK.
Note: Skip the above steps by clicking Start –>Administrative Tools –>Group Policy Management.
3. Expand the domain node and Domain Controllers OU, right–click on the Default Domain Controllers Policy, then click Edit. – refer the below image.
4. Expand Computer Configuration node and Security Settings and navigate to the node Audit Policy (Computer Configuration->Policies->Windows Settings->Security Settings-> Advanced Audit Policy Configuration -> Audit Policies->Account Logon).
5. In right-side pane, double-click on Audit account logon events and set Success and Failure setting to enable kerberos logon event 4768.
Note: In Windows 2008 R2 and later versions, you can also control this event by subcategory-level setting via Advanced Audit Policy Configuration.
Expand Computer Configuration and Security Settings and navigate to the node Account Logon (Computer Configuration->Policies->Windows Settings->Security Settings-> Advanced Audit Policy Configuration -> Audit Policies->Account Logon) and set the setting Audit Kerberos Authentication Service as Success and Failure
6. Run the command gpupdate /force from command prompt to update Group Policy settings.
Enable/Configure Event ID 4768 via Auditpol
Auditpol.exe is the command line utility tool to change Audit Security settings as category and sub-category level. It is available by default Windows 2008 R2 and later versions/Windows 7 and later versions. By using Auditpol, we can get/set Audit Security settings per user level and computer level.
Note: You should run Auditpol command with elevated privilege (Run As Administrator);
You can enable Event 4768 through Kerberos Authentication Service subcategory by using the following command
Success Audit:
auditpol /set /subcategory:"Kerberos Authentication Service" /success:enable

Failure Audit:
auditpol /set /subcategory:"Kerberos Authentication Service" /Failure:enable
To update or refresh GPO settings, run the command gpupdate/force
Disable/Stop Event ID 4768
You can disable or stop the audit Event 4768 by removing success and failure audit of Kerberos Authentication Service subcategory by using the following command.
auditpol /set /subcategory:"Kerberos Authentication Service" /success:disable
You can also stop this event by removing the success and failure setting from the Default Domain Controller Policy’s category level setting path (Computer Configuration->Policies->Windows Settings->Security Settings-> Advanced Audit Policy Configuration -> Audit Policies->Account Logon->Audit account logon events)
or by subcategory level setting (Computer Configuration->Policies->Windows Settings->Security Settings-> Advanced Audit Policy Configuration -> Audit Policies->Account Logon->Audit Kerberos Authentication Service)
Note: This article is applies to only Windows Server 2008 R2, Windows Server 2012, Windows 7 and Windows 8
Thanks,
Morgan
Software Developer
