CA, Certificate, Certificates, Free, Home Lab, Home Lab Ideas, How To, HTTPS, i12bretro, Microsoft, PKI, Private Key Infrastructure, Public Key Infrastructure, Remote Management, Self-Signed HTTPS, Self-Signed PKI, Self-Signed SSL, Server Administration, SSL, SSL Certificates, System Administration, Tutorial, WAC, Web Based Tools, Web Based Utilities, Windows, Windows Admin Center, X Certificate Key Manager, XCA
2 Minutes
View interactive steps on GitHub
Prerequisites
- A XCA PKI database https://youtu.be/ezzj3x207lQ
Create Your SSL Certificate
- Launch XCA
- Open the PKI database if it is not already (File > Open DataBase), enter password
- Click on the Certificates tab, right click on your Intermediate CA certificate
- Select New
- On the Source tab, make sure Use this Certificate for signing is selected
- Verify your Intermediate CA certificate is selected from the drop down
- Click the Subject tab
- Complete the Distinguished Name section
internalName: i12bretrodc.i12bretro.local
countryName: US
stateOrProvinceName: Virginia
localityName: Northern
organizationName: i12bretro
organizationUnitName: i12bretro Certificate Authority
commonName: i12bretrodc.i12bretro.local - Click the Generate a New Key button
- Enter a name and set the key size to at least 2048
- Click Create
- Click on the Extensions tab
- Select End Entity from the type list
- Click Edit next to Subject Alternative Name
- Add any DNS or IP addresses that the certificate will identify
- Update the validity dates to fit your needs
- Click the Key Usage tab
- Under Key Usage select Digital Signature, Key Encipherment
- Under Extended Key Usage select Web Server and Web Client Authentication
- Click the Netscape tab
- Select SSL Server
- Click OK to create the certificate
Exporting the Certificate
- In XCA, click on the Certificates tab
- Right click the SSL certificate > Export > File
- Set the file name with a .p12 extension and verify the export format is PKCS #12 (*.p12)
- Enter a password to protect the .p12 export
Importing Certificate Into Windows Certificate Store
- Right click the Start Button > Run
- Type mmc.exe, press enter
- Click File > Add/Remove Snap-in…
- Click Certificates
- Click Add
- Select Computer account
- Click Next
- Select Local computer
- Click Finish
- Click OK
- Expand Certificates
- Right click the Personal folder > All Tasks > Import….
- Click Next
- Click Browse > Select the exported SSL .p12 file > Click Next
- Enter the password created for the .p12 export
- Verify Include all extended properties is checked
- Click Next
- Click Next
- Click Finish
- Double click the newly imported certificate
- Select the Details tab > Scrool to the bottom of the details pane
- Click the thumbprint line item
- Copy the thumbprint value in the lower pane to the clipboard
- Download Windows Admin Center Download
- Run the downloaded .msi
- If WAC is already installed, click the change button
- Select the Use an SSL certificate installed on this computer option
- Paste in the thumbprint copied from the imported certificate
- Click Change to apply the changes
Published

This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
Prerequisites:
- Some linux based environment
Links that might be useful in this case:
- Setting up WSL2 (Windows Subsytem for Linux) on Windows 10
Anyone who has been using the Windows Admin Center for longer than 60 days will probably run into a certificate problem. The latest browser from Microsft, called Edge, will then no longer allow access to the WAC portal at all.
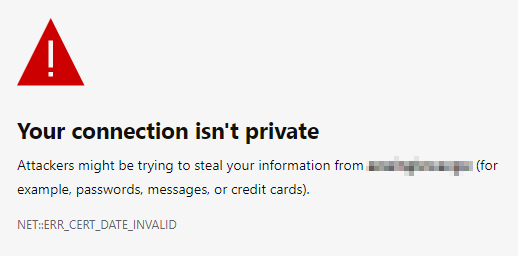
1) Scenario 1 — Local WAC Installation
The easiest way to get a new certificate is to initiate a repair installation. Enclosed are the necessary steps, if you have a local WAC — installation.
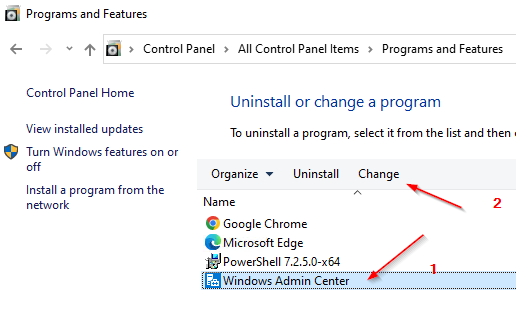
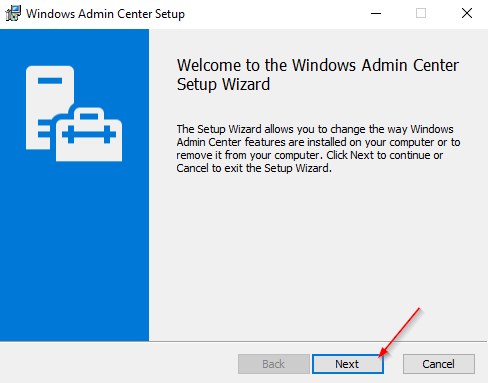
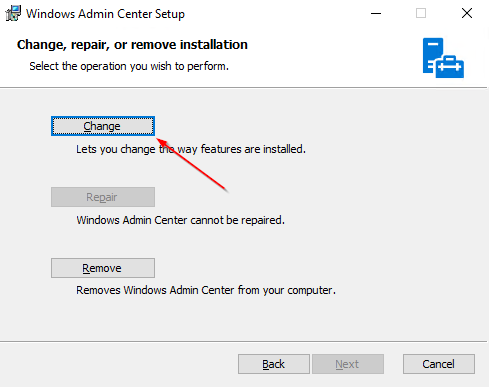
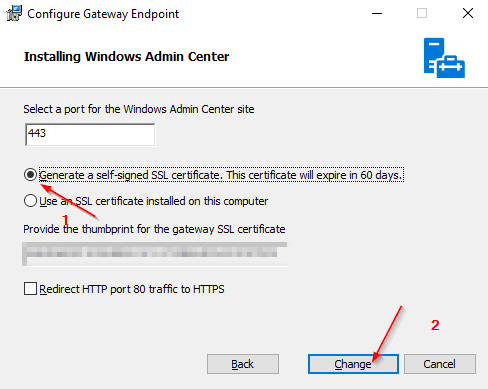
You could also use a separately created certificate at this point by providing its Thumprint ID to perform the necessary reassignment.
2) Scenario 2 — WAC — Gateway Installation
In order to avoid getting an expired certificate again in 60 days, I create myself a certificate which is valid for 10 years.
For this I switch to my Linux environment. In my case a WSL installation based on Ubuntu.
# Creating a cert - folder
mkdir certs# Changing Directory
cd certs
# Generating the Cert
openssl req -x509 -newkey rsa:4096 -sha256 -days 3650 -nodes \
-keyout cert.key -out cert.crt -extensions san -config \
<(echo "[req]";
echo distinguished_name=req;
echo "[san]";
echo subjectAltName=DNS:<fqdn>
) \
-subj "/CN=<fqdn>"
# Looking for the new generated certs
ls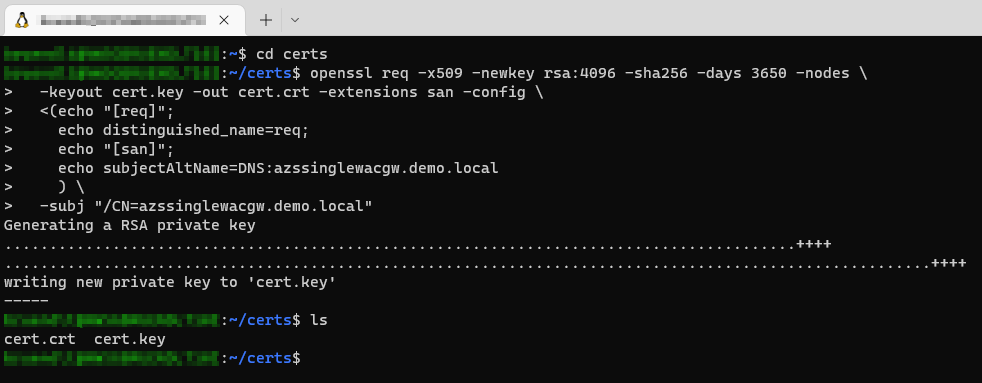
# Certificate conversion - CRT+Key = PFX
openssl pkcs12 -export -in cert.crt -inkey cert.key -out wac.pfx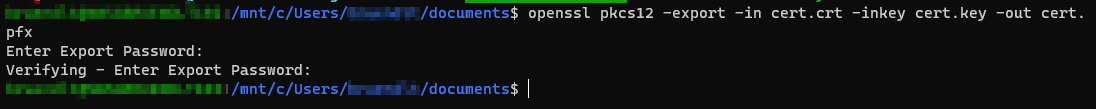
# Obtaining the certificates via Windows Explorer
\\wsl$\Ubuntu\home\bruendlt\certs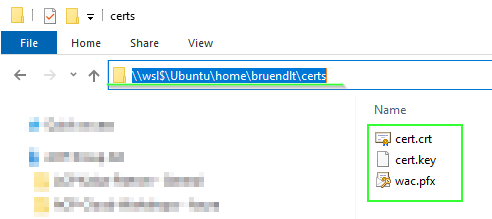
The changeover process:
# var
$GatewayServerName="<Hostname WAC - Gateway>"
# session
$Session=New-PSSession -ComputerName $GatewayServerName
# copy
Copy-Item -Path "$env:USERPROFILE\Downloads\wac.pfx" -Destination "$env:USERPROFILE\Downloads\wac.pfx" -ToSession $Session
# cert import
Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Import-PfxCertificate -FilePath "$env:USERPROFILE\Downloads\wac.pfx" -CertStoreLocation Cert:LocalMachine\My -Exportable -Password (ConvertTo-SecureString -String '<PFX - File Password>' -AsPlainText -Force)}
# extract appId
$pattern = '(?<=\{).+?(?=\})'
$appId=[regex]::Matches((Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {netsh http show sslcert})[8], $pattern).Value
# thumprint
$Thumbprint = (Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Get-ChildItem -Path Cert:\LocalMachine\MY | Where-Object {$_.Subject -Match "$GatewayServerName"} | Select-Object FriendlyName, Thumbprint, Subject, NotBefore, NotAfter| Sort-Object -Property NotAfter -Descending | Select-Object -first 1}).Thumbprint
# delete old binding
Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {netsh http delete sslcert ipport=0.0.0.0:443}
# add new binding
$NetshArgumentList = "http add sslcert ipport=0.0.0.0:443 certhash="+$Thumbprint+" appid=`'{"+$appId+"}`'"
Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Invoke-Expression "netsh $using:NetshArgumentList"}
# restart
Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Restart-Service ServerManagementGateway}
#add certificate to trusted root certs
$Subject = (Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Get-ChildItem -Path Cert:\LocalMachine\MY | Where-Object {$_.Subject -Match "$GatewayServerName"} | Select-Object FriendlyName, Thumbprint, Subject, NotBefore, NotAfter| Sort-Object -Property NotAfter -Descending | Select-Object -first 1}).Subject
start-sleep 10
$cert = Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Get-ChildItem Cert:\LocalMachine\My\ |where subject -eq "$using:Subject"}
$cert | Export-Certificate -FilePath $env:TEMP\WACCert.cer
Import-Certificate -FilePath $env:TEMP\WACCert.cer -CertStoreLocation Cert:\LocalMachine\Root\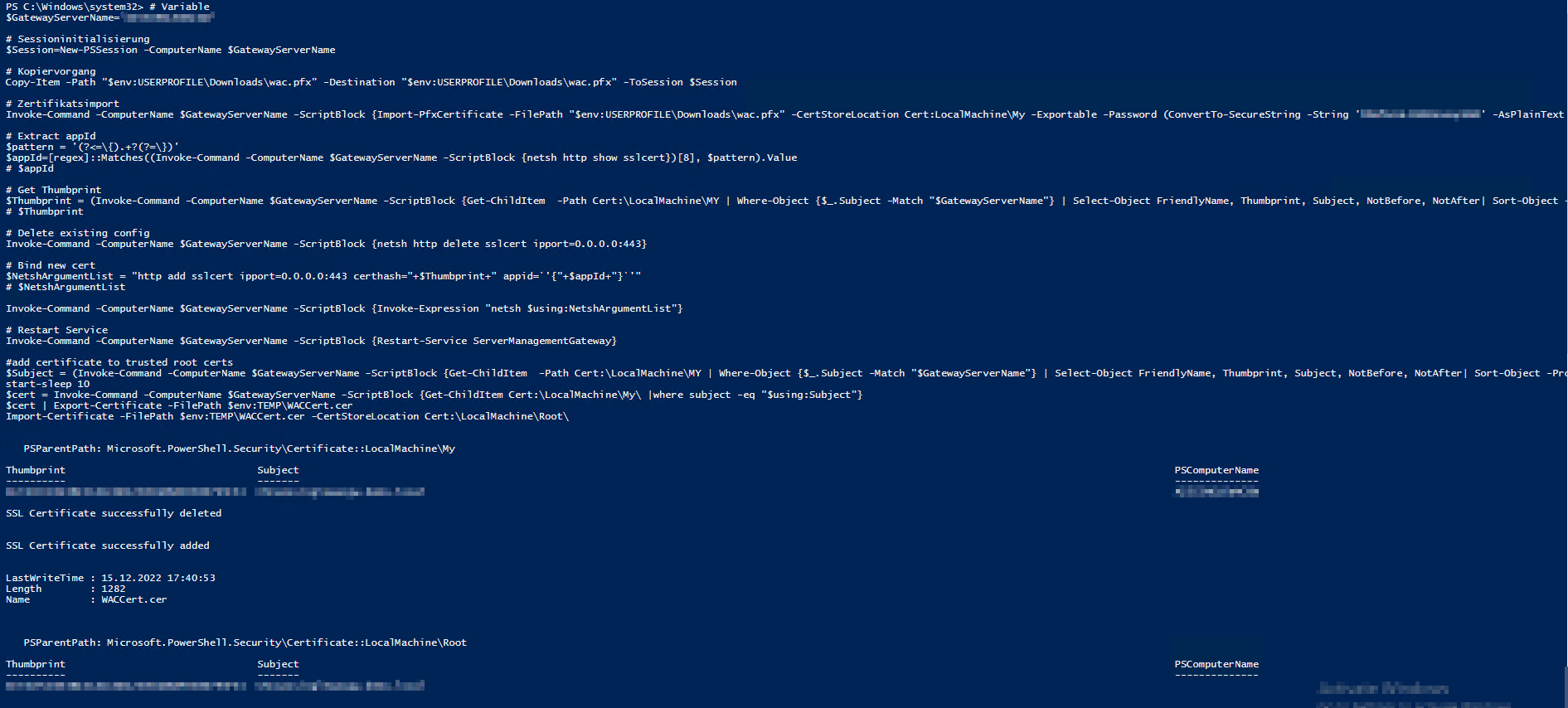
References:
Install Windows Admin Center
How to install Windows Admin Center on a Windows PC or on a server so that multiple users can access Windows Admin Center using a web browser.
Microsoft Learn

https://it-infrastructure.solutions/windows-admin-center-hybrid-hub-to-the-cloud-azure-part-2/
Setting up WSL2 (Windows Subsytem for Linux) on Windows 10
Generating self-signed certificate files (Linux — Debian)
How to Access Your Linux (WSL) Files in Windows 10
Windows 10’s May 2019 Update introduced an easy, safe, and officially supported way to access and work with your Linux files from within File Explorer and other applications. Here’s how to get at your Windows Subsystem for Linux (WSL) files.
Chris HoffmanHow-To Geek

How do I create a new certificate for Windows Admin Center??
I just now observed that our internal WAC certificate was only two months old and it’s already expired. Can I simply create and use our own self-signed certificate and use it?? Do I install it like normal certificates within the Certificates MMC and WAC will automagically use it?? Thank you, Tom
TECHCOMMUNITY.MICROSOFT.COM

Cloud and Virtualization Architect. Florent is specializing in public, hybrid, and private cloud technologies. He is a Microsoft MVP in Cloud and Datacenter Management and an MCSE in Private Cloud.
Cloud and Virtualization Architect. Florent is specializing in public, hybrid, and private cloud technologies. He is a Microsoft MVP in Cloud and Datacenter Management and an MCSE in Private Cloud.
Today, I connected to my Windows Admin Center, and I had the following error message that says that my certificate is expired:
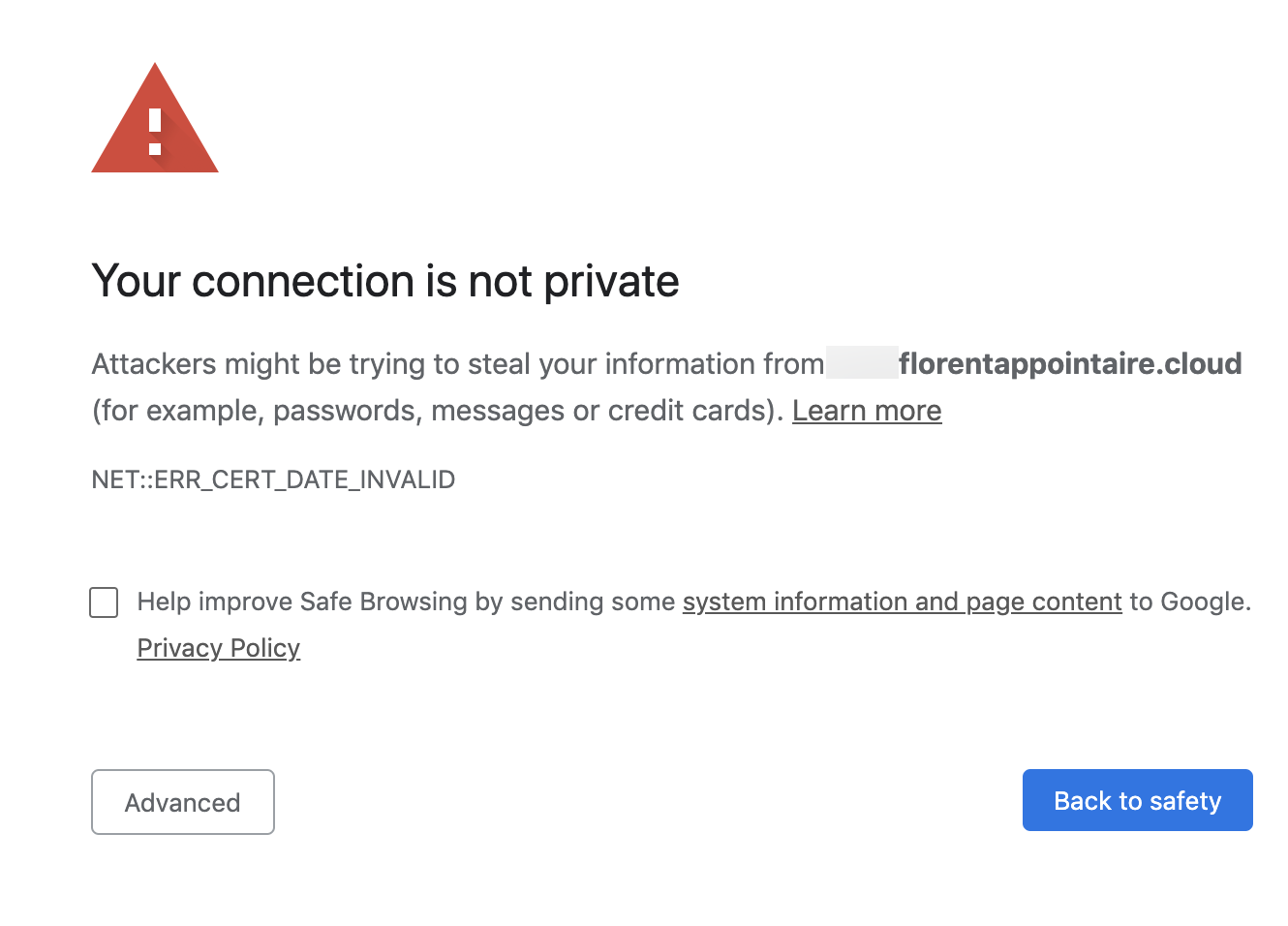
I renewed my certificate, and to change it in the WAC, you just need to import the new certificate on the server, and get his thumbprint:
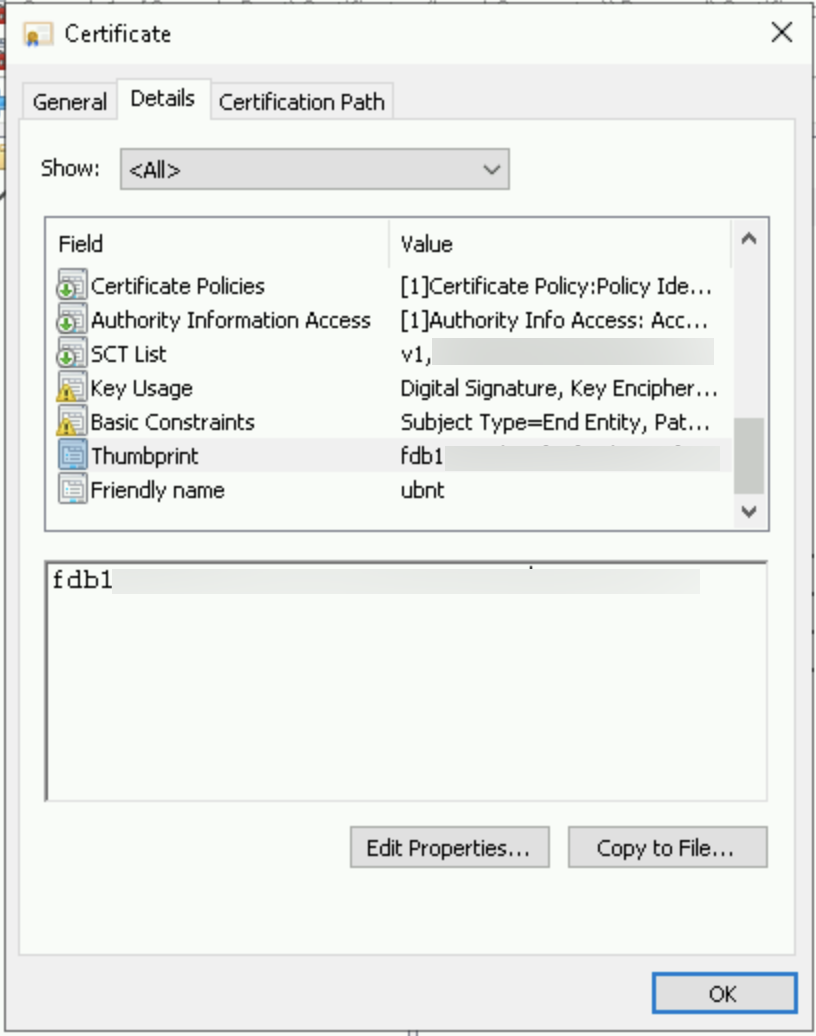
When you’ve this key, just go in the configuration panel, and search Windows Admin Center. Click on Change:
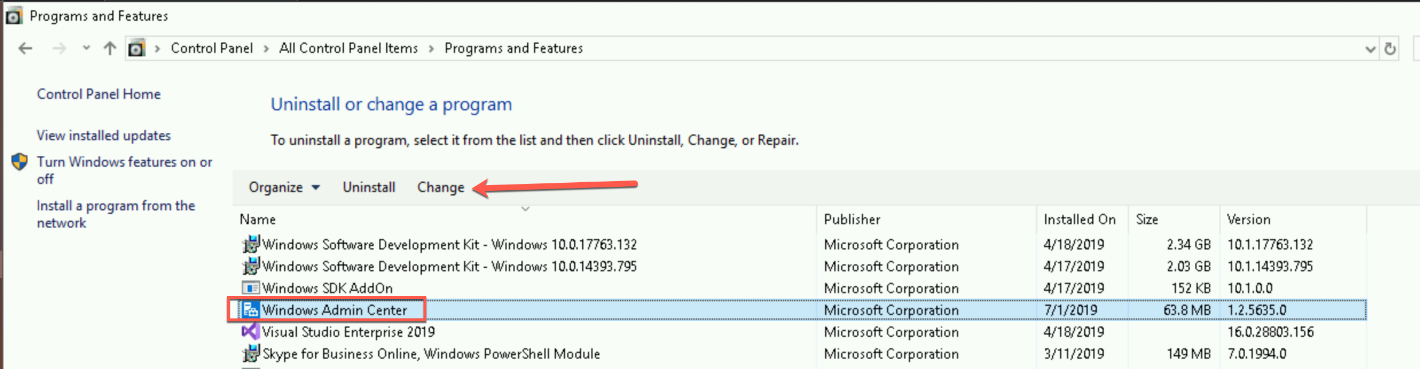
Choose to modify the WAC:
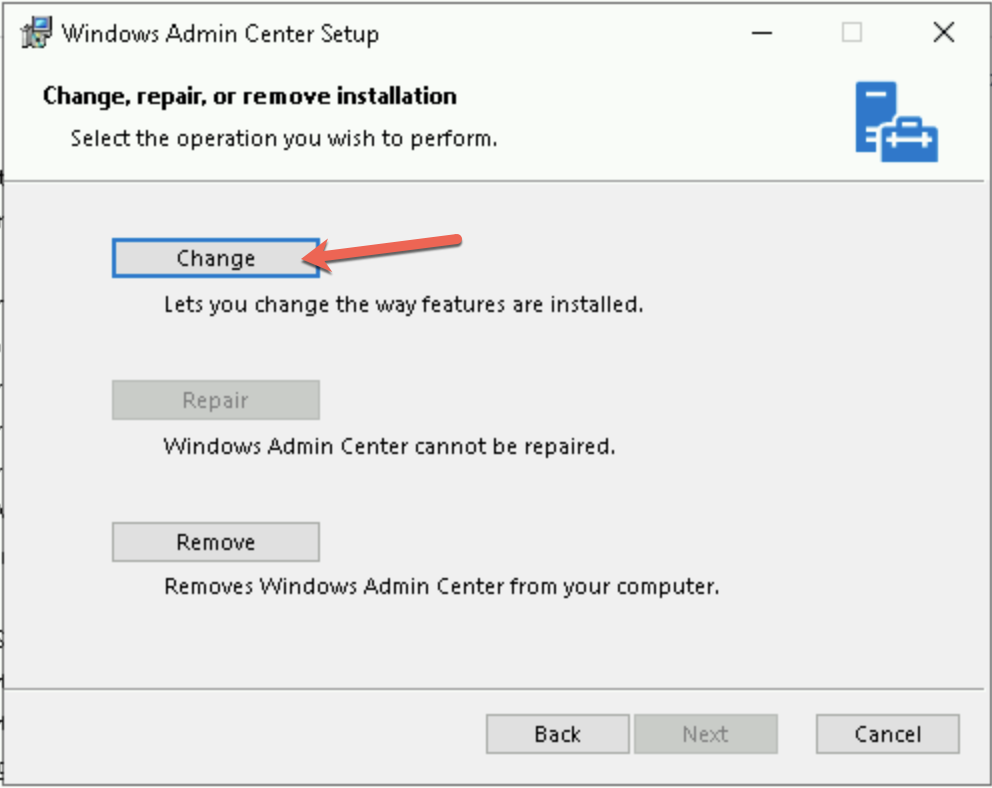
Replace the thumbprint by the new certificate that you copied previously and click on Change:
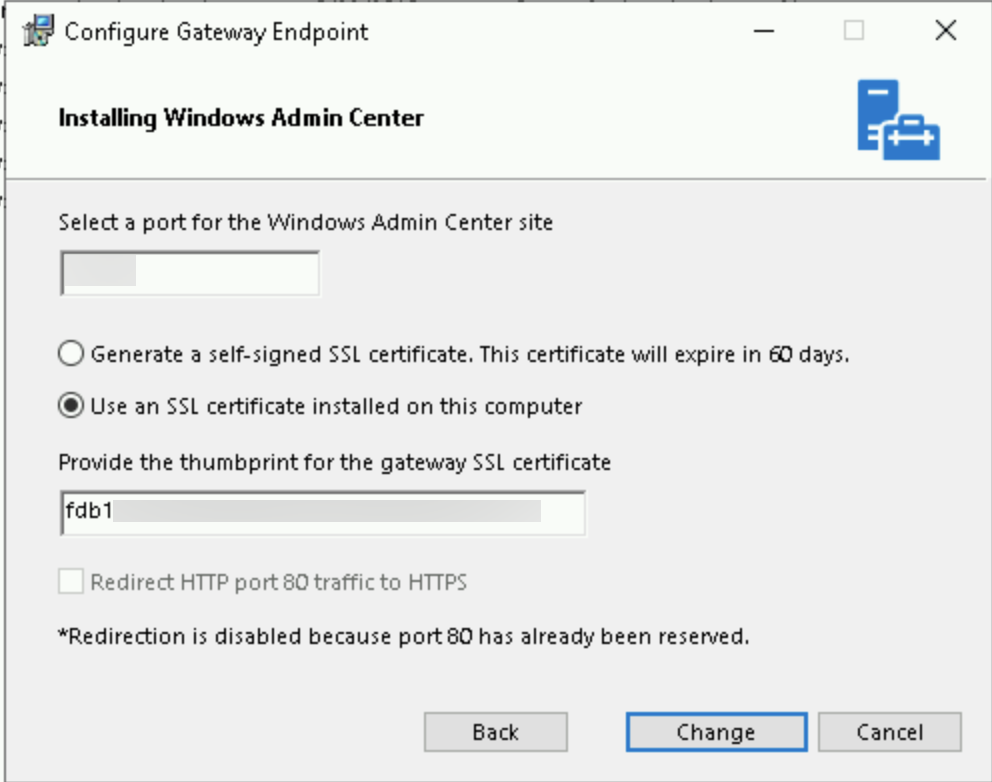
The WAC service will restart. When it’s done, the certificate on your WAC has been changed:
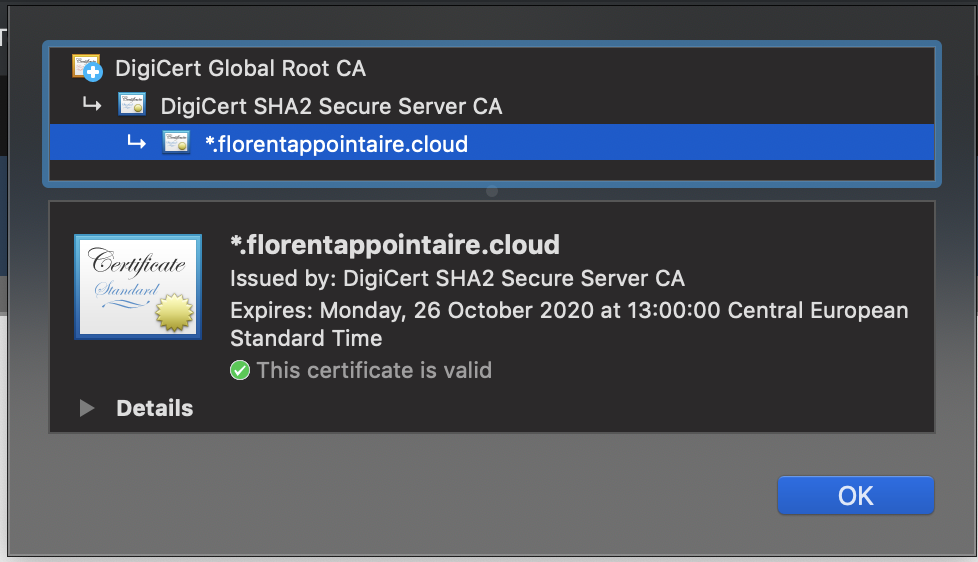
- Top 5 New Features in Windows Server 2019
- Enable Azure Monitor from Windows Admin Center
https://techcommunity.microsoft.com/t5/windows-admin-center/how-do-i-create-a-new-certificate-for-windows-admin-center/m-p/3274246/highlight/true#M1636
The certificate must be in the computer’s certificate store. I requested a certificate from my AD CS server with these steps [link to previous post].
Open PowerShell and run ls cert:\LocalMachine\my.
[server2]: PS C:\Users\da-chris\Documents> ls cert:\LocalMachine\my PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\my
Thumbprint Subject
---------- -------
FCC75611ABF84E20C948BFE023C4024DDE14D370 CN=Windows Admin Center
F9F6D219F129D3422863CF62134BE67F680D7EF4 CN=Windows Admin Center Root CA
20E1FE01174A1953A8F1E36B9F06427C92D9B433 CN=server2.ad.mydomain.com
The certificate’s thumbprint will be needed for the next configuration steps. I want to use the third certificate, so I can store that in a variable with the command $thumbprint = (ls cert:\LocalMachine\my).Thumbprint[2].
Next, run netsh http show sslcert and make note of the Application ID.
[server2]: PS C:\Users\da-chris\Documents> netsh http show sslcertSSL Certificate bindings:
-------------------------
IP:port : 0.0.0.0:443
Certificate Hash : fcc75611abf84e20c948bfe023c4024dde14d370
Application ID : {efa5e219-ee8b-435e-99d3-f6df1a58ca58}
[other irrelevant information has been removed]
I stored it in a variable using $appid = "{efa5e219-ee8b-435e-99d3-f6df1a58ca58}".
Delete the binding with netsh http delete sslcert ipport=0.0.0.0:443.
[server2]: PS C:\Users\da-chris\Documents> netsh http delete sslcert ipport=0.0.0.0:443SSL Certificate successfully deleted
Now create the binding with the new certificate thumbprint and previous Application ID. If you didn’t assign the hash/thumbprint or application ID variables, copy/paste the respective values into the command. Then run netsh http show sslcert again to confirm the settings.
[server2]: PS C:\Users\da-chris\Documents> netsh http add sslcert ipport=0.0.0.0:443 certhash=$thumbprint appid=$appidSSL Certificate successfully added
[server2]: PS C:\Users\da-chris\Documents> netsh http show sslcert
SSL Certificate bindings:
-------------------------
IP:port : 0.0.0.0:443
Certificate Hash : 20e1fe01174a1953a8f1e36b9f06427c92d9b433
Application ID : {efa5e219-ee8b-435e-99d3-f6df1a58ca58}
The final step is to restart Windows Admin Center.
[server2]: PS C:\Users\da-chris\Documents> net stop ServerManagementGateway; net start ServerManagementGateway
The Windows Admin Center Service service is stopping.
The Windows Admin Center Service service was stopped successfully.The Windows Admin Center Service service is starting.
The Windows Admin Center Service service was started successfully.
Refresh WAC in your browser and it should be using the new certificate.
Intro
Today I am going to show you how to renew your Windows Admin Center certificate, as well as how to distribute that certificate with Group Policy. For those that do not know, Windows Admin center is an awesome tool that allows you to manage, configure and troubleshoot Windows servers and PCs. The best part, in my opinion, is that not only is it completely free, but you can run it in a browser window on any PC.
Problem Statement
The issue we are trying to solve today is that while Windows Admin Center works great on our gateway server that we stood up, but any other endpoint accessing this gateway gets a cert error.
.png)
Certificate working correctly on local host
.png)
Certificate error when connecting to the WAC on another server
Why is this happening?
This is happening because of the way we set up Windows Admin Center. When installing the application we have the option to select an SSL certificate that we (the administrator) provide. This would be the ideal way to configure Windows Admin Center, but it would require us to use a certificate from either a public certificate authority or create one in an internal certificate authority. Now in my lab environment, I don’t want to pay for a public SSL certificate, and I don’t have an internal CA. But I can still solve this problem by using a self-signed certificate and then distributing it to our endpoints with Group Policy.
Self-signed Certificate
First thing we have to do is verify that we have a valid Windows Admin Center self-signed certificate. Now, it would be pretty obvious if we didn’t, as we would be getting a cert error even on our Windows Admin Center gateway. But let’s check our certificate and verify its validity period.
.png)
Confirm the certificate is valid
.png)
Check certlm.msc for the published Windows Admin Center certificate
Renewing Windows Admin Center Self-signed Certificate
If we do need to renew the certificate, it is super simple. We just need to launch the Windows Admin Center installer and select Change. This will give us the option to change out the certificate or create a new one.
.png)
In the installer options, you can create a new certificate or view the thumbprint of the current one
Exporting our Self-signed Certificate
Now that we have verified our certificate is valid, we need to export it so that we can distribute it to our other endpoints that will be using the Windows Admin Center on our gateway server.
.png)
Right-click the WAC certificate, under All Tasks, choose Export
On the next screen, choose to export the private key, leave the default format options checked, set a password, and then select a file name/location to export it. Once exported, move it to your domain controller where we will be creating the GPO.
The exported certificate
Creating the Group Policy Object to Distribute the Certificate
Now we need to create the GPO that will push our certificate to our endpoints. First we will connect to one of our domain controllers and open up the Group Policy Management Editor.
Verify our Certificate has been Distributed to our Clients
Now that our GPO is created, we need to verify it has made it to our endpoints. First thing we can do is perform a manual Group Policy update on our client to save some time waiting for a sync. We can then open view our Trust Root Certificate store on the client to verify the Windows Admin Center certificate exists. Lastly, we will launch the Windows Admin Center in the browser and confirm we don’t have any errors.
.png)
Right click the OU that will house your GPO and select Create a GPO. I named mine “Client Certificates”
.png)
.png)
Right-click, choose Import, and browse to your exported WAC certificate Note: You may need to change the file type filter to All Files
.png)
Type in the password you chose earlier. Leave everything else as the defaults
.png)
Make sure the Trust Root Certificate store is selected
That is it. Click Finish and you will see the certificate show up in the policy you created.
Now to verify what we have done, go to a machine that is in the OU where you applied the GPO. Run GPUpdate /Force to kick off a group policy scan (this is done automatically at a variable time period, but kicking it off manually will save some time). Once the group policy update completes, launch certlm.msc and verify the Windows Admin Center certificate is now showing in the Trusted Root Certificate store.
.png)
Open certlm.msc and verifiy the certificate is now there
Lastly, open a web browser on the machine and navigate to your WAC URL. Instead of the certificate warning we got previously, you should get a log-in prompt. Enter your credentials and look at our secure connection!
.png)
Look, a padlock instead of a certificate error!
Missed a step? I have a full video on this process linked below.
References:
Microsoft — Updating WAC certificate
Microsoft — Distribute Certificates with Group Policy
Video for the visual learners: Updating and distributing your Windows Admin Center Certificate
