Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Intrusion detection software for Windows checks for changes that are made by all sorts of unwanted programs that could be injected into your system by cyber criminals.
These tools study the data packets, both incoming and outgoing, to check what kind of data transfers are at hand. It will alert you if they find any suspicious activity on the system or in the network.
Intrusion detection software exists as an answer to the increasing frequency of attacks made on systems.
Such tools usually inspect the host configuration for risky settings, password files, and more areas. Then, they detect all kinds of violations that could prove dangerous for the network.
IDS also set in place various ways for the network to record any suspicious activities and potential attack methods and to report them to the admin.
In other words, an IDS is quite similar to the Windows firewall but more than guarding against attacks from outside the network, an IDS is also able to identify suspicious activity from within the network.
Some IDS software is also able to respond to potential intrusion. This is Host Intrusion Prevention System software (HIPS) or just IPS (Intrusion Prevention System).
Generally speaking, Intrusion Detection Software for Windows shows what is happening. The IPS solutions also act upon the known threats.
There are some products which combine these two features, and we’ll present to you the best on the market.
What are the types of IDS?
An intrusion detection system (IDS) is a tool created to test the vulnerability exploits against a target system or computer. There are four main types of intrusion detection systems:
- Network intrusion detection system – an independent platform that monitors network traffic, probes hosts, and identifies intruders.
- Host-based intrusion detection system – an agent installed directly on the host and filters malicious traffic that goes through allocation logs, system calls, and file system modifications.
- Perimeter intrusion detection system – creates “perimeter fences” around main system infrastructures to detect and locate intrusion attempts there.
- VM-based intrusion detection system – similar to any of the three above, is deployed remotely via a virtual machine.
Best intrusion detection systems to install on PC
ESET HOME Security Essential – Most comprehensive security features
ESET HOME Security Essential will actively protect your PC from any kind of threat. The software will ensure that your sensitive data, banking transactions, passwords, login credentials, and webcam are safe.
ESET uses advanced AI and machine learning to create proactive protection which will stop known malware and emerging ones from entering and infecting your device.
Since it is cross-platform, the antivirus is ready to secure all kinds of devices, such as Android phones, iPhones, Linux and Windows computers, or MACs.
Here is a list of its core features:
- Privacy protection
- Anti-theft measurements
- Lightweight software with minimal power usage
- Secure active scanning and malware removal
ESET HOME Security Essential
It utilizes advanced AI to scan your computer for harmful software and keep your system safe.
Total AV – Best browsing security and system maintenance
If you want complete antivirus protection, TotalAV is the right choice for you. With features to protect your system from any online or offline threats, it’s one of the few antiviruses that offers you a series of tune-up tools to maintain peak performance.
With TotalAV and WebShield, you are completely protected while browsing. Malicious websites and links are automatically blocked, and downloaded files and executables are verified before you even click on them.
Besides full virus protection, it provides a Total Adblocker to reduce all unwanted pop-ups and notifications and load all pages faster.
Some of TotalAV’s key features include:
- Data breach monitoring and alerts
- Blocking of tracking cookies
- Tune-up tools for system maintenance
- PUA protection and zero-day cloud scanning
Total AV
A great intrusion detection software that will protect every aspect of your computer.
Bitdefender Internet Security – Most advanced virus protection and prevention
Bitdefender is a self-proclaimed global leader in cyber security, protecting millions of users around the world from online threats.
The software is equipped with multilayered protection to ensure nothing gets past its real-time scanning. In addition, the program is lightweight and doesn’t consume resources from your computer.
Bitdefender Internet Security will perform periodic scans, and it will actively take care of your online data and privacy, prohibiting any intruding software from stealing it.
Let’s have a look at the software’s key features:
- Multiplatform protection
- Privacy firewall
- Parental control is perfect for keeping children safe
- Multilayered antivirus, malware, ransomware, adware protection
Bitdefender Internet Security
Bitdefender Internet Security is an award-winning antivirus with unbeatable virus protection.
Malwarebytes Endpoint Protection – Best malware protection
According to Malwarebytes, the industry-leading security software manufacturer, there is no better protection strategy than proactive prevention and we couldn’t agree more.
Malwarebytes Endpoint Protection is an advanced IDS solution for endpoints that uses a layered approach packed with multiple detection techniques to identify and keep malware and other cyber threats away from your systems.
It delivers best-in-class protection against both known and unknown malware, ransomware, and zero-hour threats within one unified solution meant to reduce costs and simplify the deployment process.
Let’s quickly look at its key features:
- Web protection (against malicious websites and ad networks)
- Application hardening (reduces vulnerability exploit surface)
- Application behavior protection (prevents apps’ leveraging and endpoint infection)
- Mitigation (blocks ransomware and attempts to execute code on the endpoint from any distance)
- Machine learning-based anomaly detection
- Pre and post-execution layered detection techniques
- Centralized cloud-console (for easy cloud-enabled deployment and management)
Malwarebytes Endpoint Protection
The best protection strategy is prevention. Keep your endpoints safe with Malwarebytes!
Avast Free Antivirus– Great basic free protection
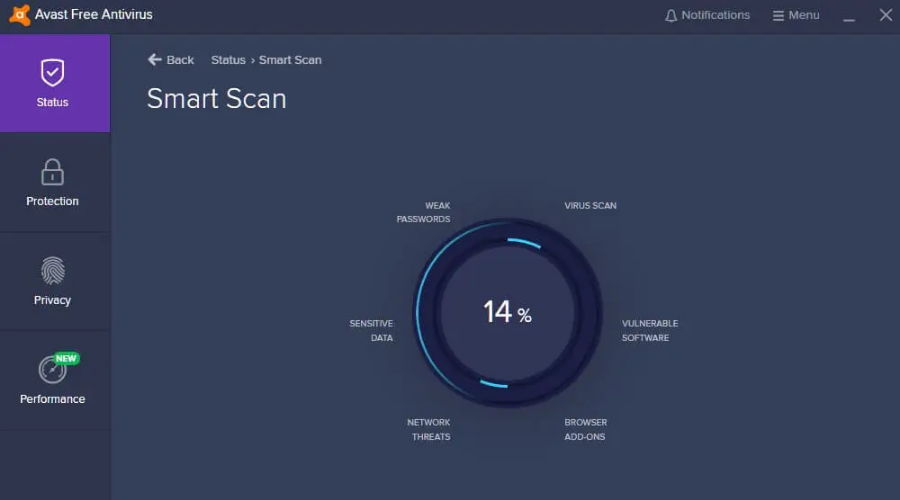
One other great malware detection software is Avast Free Antivirus. The program also uses advanced AI to optimize its scans and find all harmful software and viruses on your PC.
The free version of this program comes with the malware scanner and removal tool which is more than enough for those who want to keep their data secured.
If you choose to upgrade to the premium version, you’ll benefit from these key features:
- Premium malware scanner and removal
- PC cleaner and optimizer
- Customer support and remote control
- Wi-fi inspector
Avast Free Antivirus
Avast gives you more than any other competitors, providing excellent antivirus protection for free.
Malware Defender – Great for advanced users

This is a free Windows-compatible IPS software that provides network protection for its advanced users.
The software will successfully handle intrusion prevention and also malware detection. It is very well-suited for home use even if its instructional material is a bit too complex for average users.
Acting as a host intrusion prevention system, the tool monitors a single host for any kind of suspicious activity.
Malware Defender was initially a commercial program, but its excellent features changed its ownership a while ago, and then a new version was released that was freeware.
Let’s quickly look at its key features:
- Default installation into learning mode to reduce the number of initial alerts to a minimum
- Files, registry, application modules, and network protection
- Connection Monitor (the perfect companion to Windows native firewall, with more detailed control)
The software is an excellent performer, but its only minus would be the fact that its complexities make it unsuitable for the average user.
On the other hand, all mistakes can be rectified by changing rule permission from the log entries.
Although if you have already denied a vital system function you won’t be able to do much more to get things back the way they were before, so you should pay attention.
⇒ Get Malware Defender
Snort for Windows – Open-source network IDS

Snort for Windows is an open-source network intrusion software that delivers real-time traffic analysis and packet logging on IP networks.
The software is able to perform protocol analysis, and content searching/matching can be used to detect a variety of attacks and probes, such as buffer overflows.
It will also analyze stealth port scans, CGI attacks, SMB probes, OS fingerprinting attempts, and much more.
The program is straightforward to deploy, and it has a vast number of open-source developers. The Snort community supports the software, but it also provides the core rule sets for some commercial IDS/IPS products.
Protect your home network with the firewall devices on this thorough list and never worry about malware again.
Let’s quickly look at its key features:
- Returns everything that it sees including detailed packet decodes
- Easy configuration to only present alerts from its set of rules
- Robust tools for gathering and for analyzing network traffic.
- Deployment across very large network infrastructures is also possible
Due to its ability to be quickly deployed, its very comprehensive capabilities, and its great open-source community support, Snort is usually everyone’s favorite.
There is also the commercial version which is available as an appliance from Sourcefire, and it’s guided by Snort’s developer as its CEO.
Roesch managed to blend perfectly the best parts of the open-source and the commercial worlds into the Sourcefire offerings.
⇒ Get Snort for Windows
The Bro Network Security Monitor / Zeek – Good framework analysis

This is a powerful network analysis framework that is very different from the typical IDS you may have known until now. Bro’s domain-specific scripting language will enable site-specific monitoring policies.
The program comes packed with analyzers for lots of protocols, and it enables high-level semantic analysis in the application layer. It also keeps a great application-layer state about the network that it monitors.
Let’s quickly look at its key features:
- No traditional signatures (interfaces with other applications for real-time exchange of information)
- Comprehensive logs archive
- Targets especially high-performance networks
If you are looking for the best free and paid Windows 10 FTP clients, check out this awesome list with the best products on the market and decide for yourself.
While the program focuses on network security monitoring, it will also provide users with a comprehensive platform for more general network traffic analysis.
It is well-grounded in more than 15 years of research the software managed to successfully bridge the traditional gap between academics and operations from its very beginning.
The user community of Bro includes some major universities, supercomputing centers, research labs, and also lots of open-science communities.
NOTE
Update: The Bro has undertaken a rebranding process and it is now known as Zeek.
⇒ Try The Bro Network security monitor
OSSEC Free IDS for Businesses – Good multi-purpose IDS

This is an open-source host-based IDS that performs file integrity checking, log analysis, policy monitoring, rootkit detection, real-time alerting, and active responses and it runs on almost all platforms including Windows.
The software watches it all, and it actively monitors all aspects of the system’s activity. With this program, you will not be in the dark regarding what is happening to your valuable computer assets anymore.
Let’s quickly look at its key features:
- Real-time analytics and insights into your network security events (via alert logs and email alerts)
- Full host-based intrusion detection across multiple platforms
- Fully open-source, and free to use
- Fully customizable (extensive configuration options, add your very own customized alert rules and writing scripts, modify the source code and add new capabilities)
- Detect and alert unauthorized file system modifications and malicious behavior based on entries in the log files
⇒ Get OSSEC Free IDS
Securing your enterprise these days doesn’t have to be a nightmare and a back-breaking ordeal. All the solutions that we mentioned above will provide you with industrial-strength protection against all intrusion attempts.
All these tools combine the most popular open-source security software into one unified solution stack that will be easy enough to install and use. So feel free to pick your favorite one according to your needs.
Radu Tyrsina
Radu Tyrsina has been a Windows fan ever since he got his first PC, a Pentium III (a monster at that time).
For most of the kids of his age, the Internet was an amazing way to play and communicate with others, but he was deeply impressed by the flow of information and how easily you can find anything on the web.
Prior to founding Windows Report, this particular curiosity about digital content enabled him to grow a number of sites that helped hundreds of millions reach faster the answer they’re looking for.
The best free intrusion detection software for Windows detects cyber attacks, malware, DoS and port scan attacks. It tracks network traffic and detects malicious activity by analyzing suspicious patterns in incoming packets.
It can report suspicious activity to the administrator or collect it using a security information and event management (SIEM) system.
Top 5 Free Intrusion Detection Software For Windows
-
Malwarebytes Endpoint Protection —
Complete web protection
-
OSSEC —
Multiplatform solution
-
Snort —
With great signature blocking
-
Zeek —
Comprehensive logs archive
-
Suricata —
Multi-threaded function
Such programs can be quite pricey, but there are some free alternatives that you can use. On this list, you will find the top tools that will cope with this task. Check out this review and choose an option that suits you more.
1. Malwarebytes Endpoint Protection — Our Choice
- Application hardening feature
- Machine learning-based anomaly detection
- Centralized cloud-console
- GUI is very intuitive an easy to use
- No notification process to inform
Verdict: Malwarebytes Endpoint Protects free web protection for Windows is a common and reliable way to protect your computer from the things that are lurking around the Internet, waiting to infiltrate your machine and ruin it.
It is computer anti spyware software designed to infiltrate your personal computer and do some damage without your permission or knowledge. This sort of behavior is considered bad in the eyes of the law and can cause you to be held financially liable for something that you didn’t create.
2. OSSEC
- Runs on any operating system
- Supports tcl/tk
- Can receive alerts from other tools
- Open source HIDS
- Primarily a wireless security solution
Verdict: When using OSSEC you will get some of the same features that you would from the Internet security suite. You will be able to automatically update your virus database, have dedicated IP address space, firewalls and even dedicated monitoring capabilities.
One feature that OSSEC offers that is often not found in other products is web filtering. This feature will allow you to restrict certain web pages from being able to access your network and can help to reduce the amount of web intrusions that occur on your network.
3. Snort
With great signature blocking
- Real time updates
- Keeps your network visibility high
- IPS detection and blocking
- Can be behind in updates
Verdict: The best web security for Windows that you can get for free is an application called Snort. If you want to be protected from the most serious types of web threats, then this program is what you should be using on your PC. This web security tool works by installing a program known as «XoftSpySE» onto your system and then working to make sure that it has the most up to date anti virus protection on your PC.
4. Zeek
Comprehensive logs archive
- Supports cybersecurity knowledge management
- Can help analysts identify threats
- Flexibility
- No traditional signatures
Verdict: Zeek has been making quality products for over 10 years and one of the best products they have come out with is their Zeek Free Intrusion Detection Software for Windows XP Home Edition. They have kept that same powerful software but added in so many features. One of the best things about this software is that it is free and you can find it at the link below. I am sure once you download this free antivirus software you will see the many benefits it can give you.
The main reason why I like this product so much is because it not only detects intrusions but also many other web threats as well. They have a web protection scanner that will check your computer for any intrusions such as spyware, adware, Trojans, worms, and viruses.
5. Suricata
- Built in hardware acceleration
- File extraction
- Cross-platform support
- System and network resource intensive
Verdict: Suricata can protect your PC from the threats posed by the likes of spam, phishing, malicious software and other online threats. Internet security has been growing over the years as more people rely on the internet for their day to day needs and to help keep them safe there are many security programs that can be downloaded from the internet.
However, many of these free programs aren’t as effective as the anti-spyware programs that can be purchased and are prone to having a number of false alarms, which means that your computer could be vulnerable to further attacks. It’s important to have the best protection possible, and so we’ve put together this guide to helping you identify the best free intrusions detection software for Windows XP Home Edition to help ensure you get the protection you need.
Eva Williams
Writer & Gear Reviewer
Eva Williams is a talented family photographer and software expert who is in charge of mobile software and apps testing and overviewing in the FixThePhoto team. Eva earned her Bachelor’s degree in Visual Arts from NYU and work 5+ years assisting some of the city’s popular wedding photographers. She doesn’t trust Google search results and always tests everything herself, especially, much-hyped programs and apps.
Read Eva’s full bio
Tetiana Kostylieva
Photo & Video Insights Blogger
Tetiana Kostylieva is the content creator, who takes photos and videos for almost all FixThePhoto blog articles. Her career started in 2013 as a caricature artist at events. Now, she leads our editorial team, testing new ideas and ensuring the content is helpful and engaging. She likes vintage cameras and, in all articles, she always compares them with modern ones showing that it isn’t obligatory to invest in brand-new equipment to produce amazing results.
Read Tetiana’s full bio
Межсетевые экраны — один из первых эшелонов защиты интернет-сервисов с довольно широким функционалом по безопасности. В их состав обычно входит класс решений IDPS, который позволяет с высокой точностью определять нелегитимные запросы и блокировать их.
В этом материале рассказываю, что такое системы IDPS и какие они бывают. А также показываю, как их разворачивать на виртуальных серверах и настраивать сигнатуры для блокирования вредоносного трафика. Все инструкции — на примере Snort и Suricata. Подробности под катом.
Знакомство с IDPS
Intrusion Detection and Prevention System, IDPS — это системы обнаружения и предотвращения вторжения. По сути, IDPS мониторит транзитный и локальный трафик на попытки сканирования и атак, соотнося их с имеющимися сигнатурами. Если трафик «зловредный» — он блокируется.
Классификация IDPS и популярные решения
IDPS можно разделить на два класса — NIDS (Network Intrusion Detection System) и HIDS (Host-based Intrusion Detection). Первые — мониторят сетевой трафик, в то время как вторые — анализируют события хоста, в том числе приходящий и уходящий трафик внутри систем.
Как видно из названия, NIDS необходимо ставить на хосты, управляющие трафиком, а HIDS больше подходят для endpoint-хостов с локальными сервисами. Более подробно о классификации и особенностях IDPS-систем можно почитать в Академии Selectel.
В рамках статьи покажем, как начать работать с двумя представителями систем IDPS:
- Suricata (как инстанс в Ubuntu 20.04) — это высокопроизводительный софт для анализа трафика и поиска угроз;
- Snort (как пакет в pfSense 2.6.0) — это один из самых популярных IDPS с открытым исходным кодом.
Между этими решениями есть одно важное отличие. Snort работает только в однопоточном режиме, в то время как Suricata может запускаться в многопоточных сценариях и позволяет обрабатывать больше трафика одномоментно.
Сетевая схема на базе Suricata
В рамках статьи рассмотрим схемы включения IDPS в «разрыв».
Сетевая схема на базе Suricata
В данной схеме между целевым веб-сервером и интернетом установлена IDPS. То есть маршрутизацию и проброс портов обеспечивает именно хост с IDPS. Таким образом, правильно настроив систему, можно блокировать трафик при срабатывании сигнатур.
Настройка хоста
Для начала развернем виртуальный сервер с Ubuntu — хост для IDPS. Это можно сделать за несколько кликов: регистрируемся и входим в панель управления, переходим в раздел Облачная платформа, выбираем Серверы и настраиваем конфигурации.

Выведем доступные сетевые интерфейсы. Один из них будет вести в интернет, а второй — в локальную сеть, ему необходимо назначить свободный адрес.
eth1: inet 192.168.1.254/24 brd 192.168.1.255 scope global eth1
Теперь настроим для локальной сети выход в интернет и заранее «опубликуем» веб-сервер наружу:
$ sudo echo 1 > /proc/sys/net/ipv4/ip_forward
$ sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
$ sudo iptables -t nat -A PREROUTING -p tcp -i eth0 --dport 80 -j DNAT --to-destination 192.168.1.2:80
$ sudo iptables -A FORWARD -p tcp -d 192.168.1.2 --dport 80 -m state --state NEW,ESTABLISHED,RELATED -j ACCEPT
$ sudo iptables-save > /etc/iptables/rules.v4
Вторым этапом развернем хост для веб-сервера, на который поставим Nginx и проверим доступность снаружи:
$ sudo apt install nginx -y
$ curl http://45.145.64.243
Что должен вернуть cURL запрос к Nginx ↓
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
<h1>Welcome to nginx!</h1>
If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.
For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.
<em>Thank you for using nginx.</em>
</body>
</html>
Отлично — страница отвечает, в логах Nginx можно увидеть подобные обращения:
$ tail -f /var/log/nginx/access.log
- - [25/Jun/2023:10:05:15 +0000] "PROPFIND / HTTP/1.1" 400 166 "-" "-"
- - [25/Jun/2023:10:05:15 +0000] "TRACE / HTTP/1.0" 405 166 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:httpoptions: TRACE)"
- - [25/Jun/2023:10:05:15 +0000] "TRACE / HTTP/1.0" 405 166 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:httpoptions: TRACE)"
- - [25/Jun/2023:10:05:15 +0000] "TRACK / HTTP/1.0" 405 166 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:httpoptions: TRACK)"
- - [25/Jun/2023:10:05:15 +0000] "TRACK / HTTP/1.0" 405 166 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:httpoptions: TRACK)"
- - [25/Jun/2023:10:05:15 +0000] "GET /TiVoConnect?Command=QueryServer HTTP/1.1" 404 162 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:000001)"
- - [25/Jun/2023:10:05:15 +0000] "GET /TiVoConnect?Command=QueryContainer&Container=/&Recurse=Yes HTTP/1.1" 404 162 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:000002)"
- - [25/Jun/2023:10:05:15 +0000] "GET /cfappman/index.cfm HTTP/1.1" 404 162 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:000013)"
- - [25/Jun/2023:10:05:15 +0000] "GET /cfdocs/examples/cvbeans/beaninfo.cfm HTTP/1.1" 404 162 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:000014)"
- - [25/Jun/2023:10:05:15 +0000] "GET /cfdocs/examples/parks/detail.cfm HTTP/1.1" 404 162 "-" "Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:000015)"
Сервер начали сканировать — надо поспешить настроить IDPS. Система позволит отслеживать и блокировать обращения, которые будут совпадать с сигнатурами атак. Давайте поставим решение Suricata на хост.
Установка Suricata
Для начала скачаем необходимые зависимости.
$ sudo apt install libpcre3 libpcre3-dbg libpcre3-dev build-essential libpcap-dev libnet1-dev libyaml-0-2 libyaml-dev pkg-config zlib1g zlib1g-dev libcap-ng-dev libcap-ng0 make libmagic-dev libjansson-dev libnss3-dev libgeoip-dev liblua5.1-dev libhiredis-dev libevent-dev python-yaml rustc cargo
Теперь у нас есть два способа, как установить систему Suricata на хост:
1. Сборка из исходников
Первый способ довольно простой: достаточно просто скачать архив и распаковать из него Suricata.
$ wget https://www.openinfosecfoundation.org/download/suricata-6.0.13.tar.gz
$ ls
suricata-6.0.13.tar.gz
$ tar xzvf suricata-6.0.13.tar.gz
$ cd suricata-6.0.13
$ sudo ./configure --prefix=/usr/ --sysconfdir=/etc/ --localstatedir=/var/
$ sudo make
$ sudo make install
2. Установка из PPA
Второй способ — установить Suricata из Personal Package Archive, PPA. Это специальный репозиторий с open source-проектами разных компаний, в том числе разработчиков Suricata (OSIF).
$ sudo add-apt-repository ppa:oisf/suricata-stable
$ sudo apt-get update
$ sudo apt-get install suricata
Супер! Suricata установлена на хосте. Это можно проверить, введя suricata -V — специальную команду, которая возвращает версию установленной системы.
Обновление
После установки Suricata важно обновить правила (сигнатуры) и их источники:
root@suricata:~/suricata-6.0.12# suricata-update
</source lang="bash">
<spoiler title="Результат корректного обновления правил ↓">
<source lang="bash">
25/6/2023 -- 11:54:49 - <Info> -- Using data-directory /var/lib/suricata.
25/6/2023 -- 11:54:49 - <Info> -- Using Suricata configuration /etc/suricata/suricata.yaml
25/6/2023 -- 11:54:49 - <Info> -- Using /usr/share/suricata/rules for Suricata provided rules.
25/6/2023 -- 11:54:49 - <Info> -- Found Suricata version 6.0.13 at /usr/bin/suricata.
25/6/2023 -- 11:54:49 - <Info> -- Loading /etc/suricata/suricata.yaml
25/6/2023 -- 11:54:49 - <Info> -- Disabling rules for protocol http2
25/6/2023 -- 11:54:49 - <Info> -- Disabling rules for protocol modbus
25/6/2023 -- 11:54:49 - <Info> -- Disabling rules for protocol dnp3
25/6/2023 -- 11:54:49 - <Info> -- Disabling rules for protocol enip
25/6/2023 -- 11:54:49 - <Info> -- No sources configured, will use Emerging Threats Open
25/6/2023 -- 11:54:49 - <Info> -- Fetching https://rules.emergingthreats.net/open/suricata-6.0.13/emerging.rules.tar.gz.
100% - 3949155/3949155
25/6/2023 -- 11:54:50 - <Info> -- Done.
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/app-layer-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/decoder-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/dhcp-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/dnp3-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/dns-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/files.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/http-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/ipsec-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/kerberos-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/modbus-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/nfs-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/ntp-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/smb-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/smtp-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/stream-events.rules
25/6/2023 -- 11:54:50 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/tls-events.rules
25/6/2023 -- 11:54:51 - <Info> -- Ignoring file rules/emerging-deleted.rules
25/6/2023 -- 11:54:53 - <Info> -- Loaded 43346 rules.
25/6/2023 -- 11:54:53 - <Info> -- Disabled 14 rules.
25/6/2023 -- 11:54:53 - <Info> -- Enabled 0 rules.
25/6/2023 -- 11:54:53 - <Info> -- Modified 0 rules.
25/6/2023 -- 11:54:53 - <Info> -- Dropped 0 rules.
25/6/2023 -- 11:54:54 - <Info> -- Enabled 131 rules for flowbit dependencies.
25/6/2023 -- 11:54:54 - <Info> -- Backing up current rules.
25/6/2023 -- 11:54:57 - <Info> -- Writing rules to /var/lib/suricata/rules/suricata.rules: total: 43346; enabled: 34518; added: 0; removed 0; modified: 14
25/6/2023 -- 11:54:57 - <Info> -- Writing /var/lib/suricata/rules/classification.config
25/6/2023 -- 11:54:57 - <Info> -- Testing with suricata -T.
25/6/2023 -- 11:55:23 - <Info> -- Done.
root@suricata:~/suricata-6.0.12# suricata-update update-sources
25/6/2023 -- 11:56:27 - <Info> -- Using data-directory /var/lib/suricata.
25/6/2023 -- 11:56:27 - <Info> -- Using Suricata configuration /etc/suricata/suricata.yaml
25/6/2023 -- 11:56:27 - <Info> -- Using /usr/share/suricata/rules for Suricata provided rules.
25/6/2023 -- 11:56:27 - <Info> -- Found Suricata version 6.0.13 at /usr/bin/suricata.
25/6/2023 -- 11:56:27 - <Info> -- Downloading https://www.openinfosecfoundation.org/rules/index.yaml
25/6/2023 -- 11:56:28 - <Info> -- Adding all sources
25/6/2023 -- 11:56:28 - <Info> -- Saved /var/lib/suricata/update/cache/index.yaml
Далее в файле /etc/default/suricata сверим значение параметра IFACE с именем внешнего интерфейса хоста:
$ cat /etc/default/suricata | grep IFACE
IFACE=eth0
$ ip a
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether fa:16:3e:29:e3:e3 brd ff:ff:ff:ff:ff:ff
inet 45.145.64.243/29 brd 45.145.64.247 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::f816:3eff:fe29:e3e3/64 scope link
valid_lft forever preferred_lft forever
Обратите внимание на строку IFACE=eth0 и 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP>.
Названия интерфейсов совпадают, идем дальше. Проверим, чтобы это же значение стояло в файле /etc/suricata/suricata.yaml в блоках pcap, pfring и af-packet. По умолчанию там установлено eth0 — совпадает с именем внешнего интерфейса.
Конфигурирование
Основным конфигурационным файлом suricata является /etc/suricata/suricata.yaml — откроем его и поправим настройки. В блоке outputs включим вывод данных:
outputs:
# a line based alerts log similar to Snort's fast.log
- fast:
enabled: yes
filename: fast.log
append: yes
- eve-log:
enabled: yes
filetype: regular #regular|syslog|unix_dgram|unix_stream|redis
filename: eve.json
types:
- alert:
payload: yes # enable dumping payload in Base64
# payload-buffer-size: 4kb # max size of payload buffer to output in eve-log
# payload-printable: yes # enable dumping payload in printable (lossy) format
# packet: yes # enable dumping of packet (without stream segments)
# metadata: no # enable inclusion of app layer metadata with alert. Default yes
http-body: yes # Requires metadata; enable dumping of HTTP body in Base64
- http-log:
enabled: yes
filename: http.log
append: yes
Проверить валидность файла конфигураций можно с помощью команды suricata -T -c /etc/suricata/suricata.yaml -v.
Результат проверки конфигурации ↓
25/6/2023 -- 12:26:54 - <Info> - Running suricata under test mode
25/6/2023 -- 12:26:54 - <Notice> - This is Suricata version 6.0.13 RELEASE running in SYSTEM mode
25/6/2023 -- 12:26:54 - <Info> - CPUs/cores online: 2
25/6/2023 -- 12:26:54 - <Info> - Setting engine mode to IDS mode by default
25/6/2023 -- 12:26:54 - <Info> - fast output device (regular) initialized: fast.log
25/6/2023 -- 12:26:54 - <Info> - eve-log output device (regular) initialized: eve.json
25/6/2023 -- 12:26:54 - <Info> - http-log output device (regular) initialized: http.log
25/6/2023 -- 12:26:54 - <Info> - alert-debug output device (regular) initialized: alert-debug.log
25/6/2023 -- 12:26:54 - <Info> - stats output device (regular) initialized: stats.log
25/6/2023 -- 12:27:05 - <Info> - 2 rule files processed. 34519 rules successfully loaded, 0 rules failed
25/6/2023 -- 12:27:05 - <Info> - Threshold config parsed: 0 rule(s) found
25/6/2023 -- 12:27:06 - <Info> - 34522 signatures processed. 1280 are IP-only rules, 5229 are inspecting packet payload, 27806 inspect application layer, 108 are decoder event only
25/6/2023 -- 12:27:20 - <Notice> - Configuration provided was successfully loaded. Exiting.
25/6/2023 -- 12:27:20 - <Info> - cleaning up signature grouping structure... complete
Если открыть лог-файлы, вы увидите обращения к веб-серверу, которые фиксирует Suricata. Это связано с тем, что в большинстве правил этой IDPS-системы указано действие alert. Чтобы Suricata не просто логировала подозрительный трафик, но и блокировала его, нужно добавить действие drop в сигнатурах, которые находятся по адресу /var/lib/suricata/rules. В этом же каталоге можно создавать файлы со своими правилами.
$ tail -f /var/log/suricata/http.log
06/25/2023-12:33:15.638309 45.145.64.243[**]/[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:Port Check)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:15.763447 45.145.64.243[**]/[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:getinfo)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:15.799758 45.145.64.243[**]/[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:15.836635 45.145.64.243[**]/dpyyI9SK.link[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:15.873426 45.145.64.243[**]/dpyyI9SK.de[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:15.909272 45.145.64.243[**]/dpyyI9SK.nlm[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:15.945103 45.145.64.243[**]/dpyyI9SK.var[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:15.980823 45.145.64.243[**]/dpyyI9SK.pm[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:16.016680 45.145.64.243[**]/dpyyI9SK.config[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:16.053655 45.145.64.243[**]/dpyyI9SK.jsp[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
06/25/2023-12:33:16.089380 45.145.64.243[**]/dpyyI9SK.pwd[**]Mozilla/5.00 (Nikto/2.1.5) (Evasions:None) (Test:map_codes)[**]109.207.173.75:51566 -> 45.145.64.243:80
Логи подозрительных обращений к веб-серверу, которые записала Suricata.
Сетевая схема на базе Snort

Сетевая схема с промежуточным маршрутизатором
В данной схеме, как и в первой, есть промежуточный маршрутизатор pfSense, на котором настроен NAT для выхода веб-сервера в интернет. А также port-forwarding для доступа к службе веб-сервера снаружи.
Внутри репозиториев pfSense есть пакет snort, который мы установим и настроим в режиме мониторинга. Таким образом, мы сможет наблюдать срабатывания IDS, но трафик до сервера блокироваться не будет.
В качестве IDS для второй схемы рассмотрим Snort — вероятно, самый популярный open source-IDPS. Давайте соберем целевую схему и посмотрим, как работать с этой системой.
Запуск хоста с веб-сервером
Разворачиваем хост для IDPS. Создаем сервер и настраиваем произвольную конфигурацию. Оптимальный вариант — 2 ядра vCPU, 4 ГБ ОЗУ, универсальный SSD-диск и Ubuntu в качестве операционной системы.

Далее подключаемся к виртуальной машине из консоли панели управления и меняем адрес шлюза по умолчанию на 192.168.0.254. Это будущий LAN-адрес хоста с Snort.
# ip route replace default via 192.168.0.254 dev eth0
После переключения трафика сервера на pfSense обновим локальную копию списка пакетов в репозиториях и поставим Nginx. А после — проверим доступность веб-сервера снаружи с помощью cURL-запроса.
# apt update && apt install nginx -y
$ curl http://45.145.64.242/
Запуск второго хоста
Теперь развернем второй хост, но уже с системой Snort. В качестве него может выступить, например, Linux-сервер, виртуальная машина с pfSense или межсетевой экран Selectel.
В рамках теста развернем виртуальную машину с pfSense 2.6 — ее также можно создать через панель управления. Сначала скачаем образ pfsense с официального сайта, а после — загрузим в хранилище образов.

Во время настройки конфигурации нужно выбрать загруженный образ в разделе Источник. Далее все стандартно: для сервера с pfSense будет достаточно 4 ядер vCPU, 8 ГБ ОЗУ и универсального SSD на 50 ГБ.

После включения хоста назначаем адресацию, как указано на целевой схеме выше.


Супер! Теперь нужно провести первичную инициализацию pfSense, изменить пароль администратора — и pfSense готов к работе:

Наиболее подробно мы рассказали о настройке pfSense в отдельной статье.
Настроим проброс порта 80/TCP с Nginx в интернет. Это можно сделать в разделе Port Forward внутри панели pfSense.

Установка и настройка Snort
Хост подготовлен к установке Snort. Это можно сделать через менеджер пакетов в pfSense. На данный момент, в репозиториях доступна версия Snort 2.9.20.



Отлично! Теперь идем в раздел конфигурирования Snort и настраиваем обновления сигнатур в разделе Global Settings:

В Snort есть несколько категорий сигнатур — community, registered и subscription. Подробнее о каждой можно узнать на официальном сайте.
Все архивы с сигнатурами Snort подтягивает из следующих репозиториев: SNORT_ENFORCING_RULES, ET_BASE_DNLD_URL, SNORT_GPLV2_DNLD, SNORT_OPENAPPID_DNLD_URL, SNORT_OPENAPPID_RULES, SNORT_ENFORCING_RULES, FEODOTRACKER.
Сигнатуры Snort можно использовать в качестве правил для Suricata. Также их можно конвертировать в сигнатуры для других IDPS-систем — например, с помощью fortios-ips-snort ретранслировать правила из Snort для Fortigate.
Далее необходимо установить параметры детектирования трафика в разделе Snort Interface.
- Pattern Match — алгоритм обнаружения подозрительных запросов.
- Blocking Mode — способ блокирования. По умолчанию можно установить на DISABLED.

В логах Snort (раздел Alerts) будет информация о выявленном вредоносном трафике, приходящим на наш опубликованный веб-сервер:

В описании алертов можно найти краткую информацию о найденных атаках. Также на сайте Snort есть более подробное описание — например, WEBROOT DIRECTORY TRAVERSAL и UNESCAPED SPACE IN HTTP URI.
Snort, как и Suricata, умеет блокировать IP-адрес источника атаки — это можно настроить в разделе Snort Interfaces/Block Settings:

А что насчет отправки логов, например, в собственную SIEM? Тут схема такая: Snort умеет отправлять данные в System Log, а pfSense — пересылать логи на удаленный syslog-сервер. Настраивается это довольно просто.
1. Настраиваем логирование в Snort:

2. Включаем отправку логов на внешний syslog-сервер:

Настройка IDPS и применение сигнатур — не самая сложная задача, но крайне полезная, если вы заботитесь о безопасности своих сервисов. Важно понимать, что это не панацея от взлома, но важный элемент эшелонированной защиты инфраструктуры.
В следующей части разберем, как работает IDPS на отечественных NGFW. Интересно? Тогда следите за обновлениями на Хабре и в Академии Selectel. Увидимся!
Возможно, эти тексты тоже вас заинтересуют:
→ Open source, собственные серверы и экспертиза: доступный межсетевой экран для инфраструктуры в Selectel
→ Укрепление Nginx с помощью Fail2ban: тестируем и оцениваем «профит»
→ Проблемы безопасности SNMP на практике: имитация атак и меры профилактики
Cybercriminals are working hard these days to gain access to your business and home networks and it, therefore, becomes imperative that you take all possible steps to secure your Windows system. If you have an Intrusion Detection Software (IDS) or an Intrusion Prevention Software (IPS) installed on your computers, servers or nodes, it will an additional layer of security to your computer.
An intrusion detection software basically checks for changes made by unwanted programs that could be injected into your systems by cybercriminals. All of them study the data packets—incoming and outgoing—to see what kind of data is being transferred and alert you in case they find any suspicious activities on the computer or network.
There is a wide range of intrusion detection software available on the market. The functioning of different software depends upon how it is coded, but most of it checks data packet signatures, changes made to the computer registry or other areas of interest such as startup programs, the format of data packets, etc., so that it can trace possible intrusions on behalf of cybercriminals.
Intrusion detection software are of two types. One is the Host-based intrusion detection system and the other is Network-based intrusion detection system. The network-based intrusion detection system relies on data packets traveling on the network to make sure everything is alright. It works by comparing data packets by known types of attacks and by finding out irregularities in data packets traveling on the network. Examples of anomalies could be missing signatures, improper type of data packet etc.
The host-based intrusion system relies more on system settings to determine whether there has been a compromise or if software is trying to force changes on your computer or computer network.
In short, an IDS monitors data packets traveling over the network and alerts you when an attack is suspected or when a policy violation occurs. It will inform you that someone is trying to get into your computer and explain what happened during the cyber attack, whereas an IPS will attempt to stop it and prevent access. An IDS detects unauthorized activity, whereas an IPS will block unauthorized packets that match a particular malicious signature.
Intrusion Detection & Prevention Software
Here is the list of 3 free intrusion detection software for your Windows system – Snort, OSSEC for Enterprise use, and WinPatrol. Snort and OSSEC are network intrusion detection systems while WinPatrol is Host-based Intrusion detection.
OSSEC Free IDS for Businesses
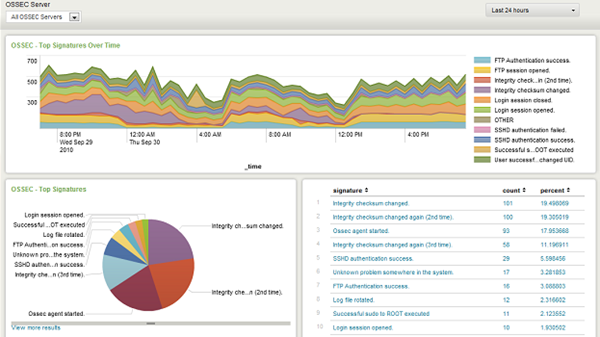
OSSEC is an Open Source Host-based Intrusion Detection System that performs log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerting and active response and runs on almost all platforms like Windows, Linux, Polaris and Mac. This open-source tool keeps an eye on data traveling on your network and alerts you in case of irregularities. It also keeps a log that provides you with details of what happened so that you can zero in on decisions.
OSSEC will check for policy violations, file integrity, log analysis and offers real-time alerts and active responses. As such, it is good for small businesses and also for home networks. The configuration is a little tough for those who do not have much knowledge of networks but it does its work pretty well and hence is recommended. Documentation is available, so most users who are not well versed with networks can refer to the documentation in case of doubts and questions.
Open-Source Snort Intrusion Detection and Prevention Software
Snort is an open-source network intrusion prevention and detection system (IDS/IPS) developed by Sourcefire, which combines the benefits of signature, protocol, and anomaly-based inspection. It has plenty of options that help you customize it to your company’s needs. It is good for both business and home use. It can be run on servers with multiple nodes or on a standalone system.
This tool available at sourceforge.net checks the different aspects of packets and logs all irregularities so that you can check them if you feel something suspicious happens. It alerts you if any such irregularities are detected and help you dig into it by providing you the logs. It checks packet signatures, packet format, network IDs and more before allowing a packet to enter your network.
The commercial version of Snort has plenty more features, but if your business needs are small, the free version of the open-source Snort is good enough to take care of any possible intrusions.
WinPatrol for home computers
Both Snort and OSSEC are good for business networks. You can use WinPatrol in addition to the above or as a standalone package on standalone computers. I will not recommend it for networks where chances of anomalies are high, but for those who need a simple intrusion detection system that they can run on their home computers, WinPatrol, as a simple intrusion detection software, is the best as it is easy to use.
One just needs to install it and it takes care of everything on the computer. Other than network packets, it also checks for registry changes and some other things that make it a perfect tool for moderate computer users. It offers real-time protection against changes made to the registry, startup programs, Internet options, and more. There are both paid and free versions of the software. The paid version offers more details about a possible intrusion, but for most of home computers, the free version is sufficient.
However this freeware is no longer being updated.
Does Windows have intrusion detection?
Windows 11 and Windows 10 are much better in terms of security than Windows 7 or older versions. Although they come with advanced security protection and shield, you might need to take additional measures in order to protect your PC from intrusion. Having said that, you can rely on Windows Security but up to a point.
What is the best intrusion prevention system?
Multiple intrusion prevention systems are available for Windows 11 and Windows 10. For example, you can use OSSEC Free IDS for Businesses, which is an open-source tool compatible with Windows 11/10. You can also use Snort, which is probably the best on the market.
HitmanPro.Alert is a free browser integrity & intrusion detection tool you may want to also check out! This Anti-Hacker software can make your Windows computer hacker-proof.
Everyone has their own favorite freeware. Let us know if you have any suggestions or observations to make.
