SSH-Agent and OpenSSH are tools in Windows that can be used to authenticate to remote Git repositories, such as GitLab, GitHub, Azure DevOps, etc. Once set up as a service that stores your various SSH keys, this can facilitate authentication without entering a password each time, removing the irritation of entering a password every time you wish to push/pull/etc. from a Git repository.
Prerequisites
- The OpenSSH Client optional service must be enabled on your machine, and OpenSSH must be added to your PATH environment variable. You can read how to do that here.
- A remote Git repository that you wish to access. We will use a GitLab repository for this article; however, the process will be similar for other Git management providers.
- Git must be installed on your machine.
How to Install the SSH-Agent Service in Windows
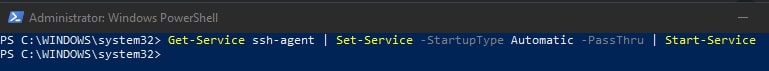
Using an elevated PowerShell window (run as admin), execute the following command to install the SSH-Agent service and configure it to start automatically when you log into your machine:
Get-Service ssh-agent | Set-Service -StartupType Automatic -PassThru | Start-Service
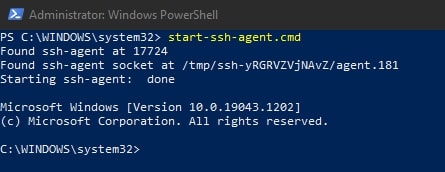
To avoid needing to restart your system to get the service running for the first time, execute this command:
start-ssh-agent.cmd
Setting up an SSH Key Pair to Access a Git Remote Provider
Using a command line tool such as Bash or PowerShell, you should be able to follow these steps to create a local SSH key pair. For our example, we will create an ED25519 key, but you can create other keys such as an RSA.
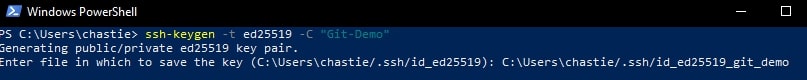
Create a new SSH ED25519 key, giving it a useful comment:
ssh-keygen -t ed25519 -C "Git-Demo"
By default, the file will be stored in your local user’s SSH repository in Windows. You can choose another storage location if you wish or rename the file by entering a new file path to save the key. Leave it blank to stick with the default.
In our example, we rename the file from the default id_ed25519 to id_ed25519_git_demo:
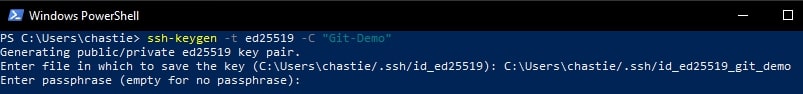
You can also add a password if you like or leave this blank:
You will then be shown the key’s randomart image to confirm creation:
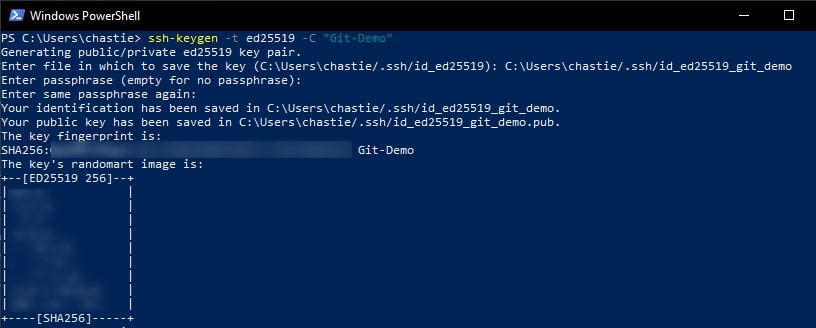
Copy the contents of the public key to your clipboard. You can read this key with the following command:
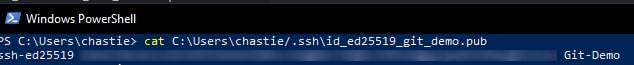
cat path\to\ssh\key.pub
For example, our code is likely:
cat C:\Users\chastie/.ssh\id_ed25519_git_demo.pub
Note: We access the public key with the .pub suffix.
A sample is shown here. You can then select this and copy it with a right-click of your mouse:
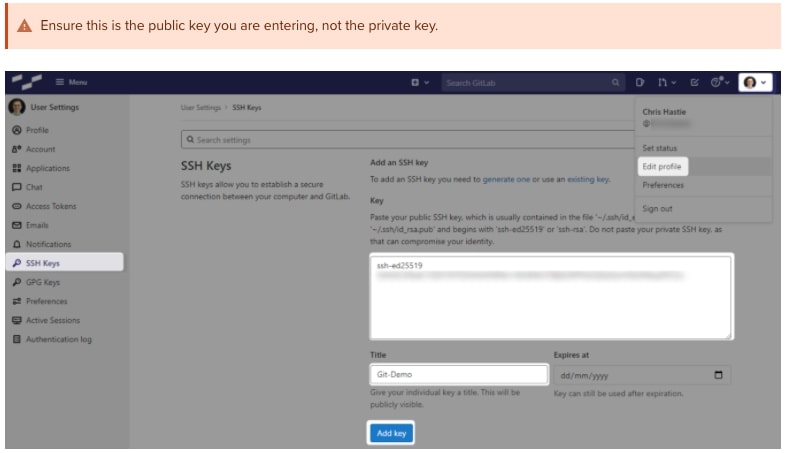
In GitLab (or the appropriate location of your Git remote repository), you can now add this public key to your user profile. In GitLab, you can do this by adding it under the SSH Keys section of your user settings:
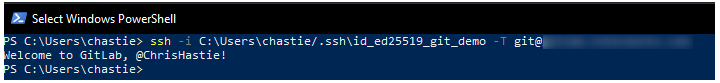
Test that you can connect to the repository when using the SSH private key directly with this command:
ssh -i path/to/ssh/private/key -T git@host
For example, our command could be:
ssh -i C:\Users\chastie/.ssh\id_ed25519_git_demo -T git@gitlab.mycompany.com or ssh -i C:\Users\chastie/.ssh\id_ed25519_git_demo -T git@github.com
We have now established an SSH key pair that can authenticate to our Git remote provider. It remains to set this up in the SSH-Agent service to automatically provide access. We can demonstrate the issue by attempting the same connection, but without specifically naming the SSH key, with the command below:
ssh -T git@host
As we can see, if we execute this command without specifying an SSH key, we are prompted for a password:
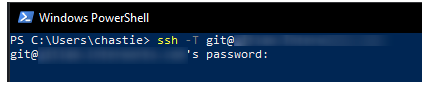
Adding the SSH Key to the SSH-Agent Service
Our goal is to be able to connect to a Git repository without entering a password. At this stage, we have a working SSH key pair and the SSH-Agent service installed and running.
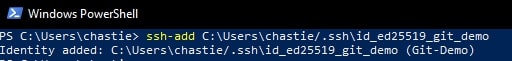
Execute the following command to add your SSH key to your SSH-Agent service:
ssh-add path/to/ssh/private/key
For our example, our command could be:
ssh-add C:\Users\chastie/.ssh\id_ed25519_git_demo
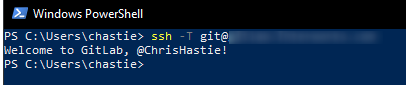
We can now test our connection to our Git remote provider without specifying a key and connect successfully:
ssh -T git@host
Configuring Git to Leverage the Windows SSH-Agent
In an elevated console (run as admin), execute the following command to modify your existing Git configuration to leverage the windows OpenSSH service as the core SSH command:
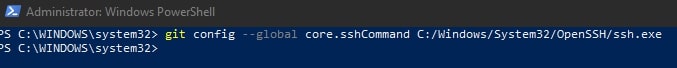
git config --global core.sshCommand C:/Windows/System32/OpenSSH/ssh.exe
Congratulations! You have now set up your environment to automatically authenticate to your Git remote provider through an SSH key pair, without using passwords. If you wish to facilitate access to any other Git remote providers, simply follow the same steps to generate a key pair ( as outlined above) and add it to your existing SSH-Agent service.
In this article I’m going to show you can use SSH on Windows machines. We’ll go over the installation of OpenSS, basic SSH configuration, as well as connecting to and from a Windows and Linux machine.
The Secure Shell (SSH) Protocol is a network protocol that allows secure access to interact with remote network resources over port 22. SSH is commonly used for remote login and command-line execution for administrative purposes. Microsoft Windows uses an implementation of OpenSSH to implement the SSH protocol and actively maintains this software project on GitHub under the openssh-portable repository.
Did you know that you can even use SSH to mount a filesystem with SSHFS, create a transparent proxy with SSHuttle, and copy files back and forth between systems using SCP? There are many amazing uses that includes the SSH protocol! If you’re curious about more implementations of the SSH protocol you can learn more here.
Installation
In order to use OpenSSH we need to first install the Microsoft.OpenSSH.Beta package using Microsoft Package Manager (winget). For those unfamiliar with the Windows Package Manager, I wrote a blog post on winget.
Searching For the OpenSSH Package
In order to find the OpenSSH package to install we are going to use the Windows Package Manager through a PowerShell terminal to search for available packages.

winget search openssh
Once we have the name of the package, Microsoft.OpenSSH.Beta we can verify this package by showing package details using winget.
Is OpenSSH Already Installed?
We can check if OpenSSH is installed or not using the winget list command.
winget list Microsoft.OpenSSH.Beta

winget list Microsoft.OpenSSH.Beta
If OpenSSH is already installed we can skip the installation process.
OpenSSH Package Metadata
When searching for applications and packages using Microsoft winget it’s a good idea to show the package metadata before installing, especially if this package is not something you’re familiar with.
winget show Microsoft.OpenSSH.Beta

winget show Microsoft.OpenSSH.Beta
Using the show command allows us to see critical information regarding this package including: publisher, source, release notes, and security fixes. Keeping up with package security is essential!
Installing the OpenSSH Package
Once we’ve found and verified the OpenSSH package we can move on to installing the package using winget. During the installation we can verify the Installer Url is indeed the URL we saw from the previous show command. The Windows Package Manager will also verify the hash for us!
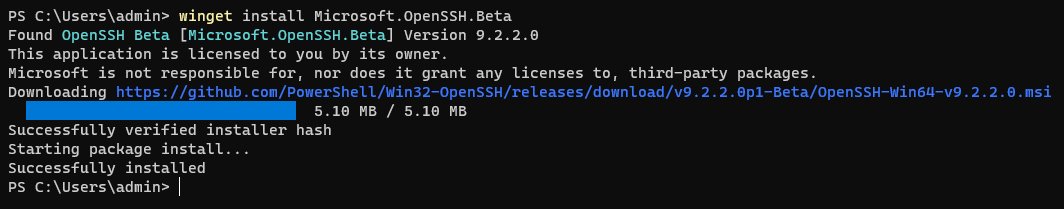
winget install Microsoft.OpenSSH.Beta
Enabling the ssh-agent Service
Once installed we can ensure that the ssh-agent service is enabled and started on our Windows machine using a powershell terminal. It’s important to note that this must be done through an Administrator terminal.
Elevate Terminal
I suggest using gsudo to elevate the current terminal. The tool gsudo is the Windows equivalent of the Linux sudo command. If you don’t have gsudo already installed you can use this guide to setup gsudo.
If gsudo is already installed we can elevate the current terminal window with the following command.
Enable ssh-agent Service
Once the current terminal is elevated with Administrator privileges we can run use the Set-Service command to enable the ssh-agent service to be a persistent service which starts up automatically.
Set-Service ssh-agent -StartupType Automatic
Start ssh-agent Service
Once we have our ssh-agent enabled as a persistent service we can start this service directly with the Start-Service command.
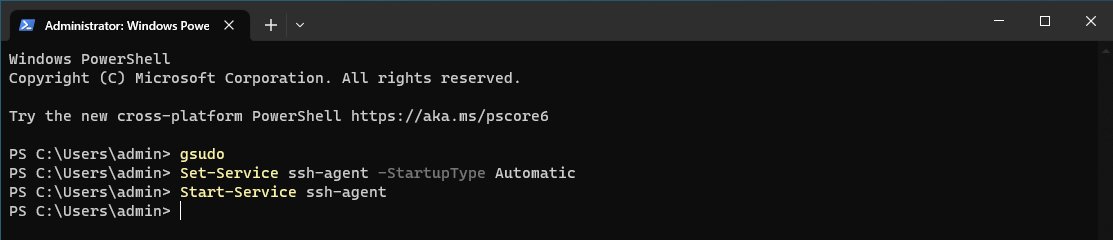
Sequence of commands to enable & start ssh-agent service
Generate SSH Keys
After we have enabled and started the ssh-agent service we can move onto generating an ssh keypair. This can be accomplished using the ssh-keygen command. In our terminal run the following command.
This command will generate a new ssh key-pair for us and will ask us to provide the file to save the key as. Additionally, we will be asked to provide a key password, we can hit enter twice to use a passwordless key.
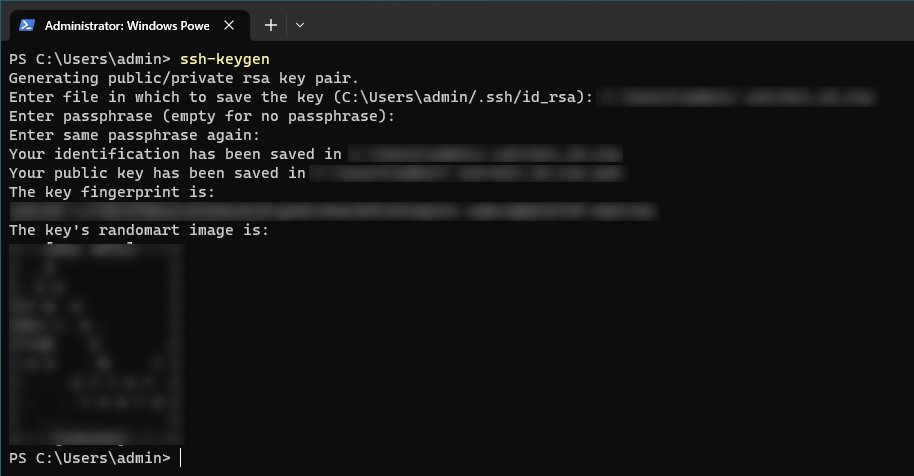
Generating a new ssh key-pair using the ssh-keygen command
Adding the SSH Key to the Authentication Agent
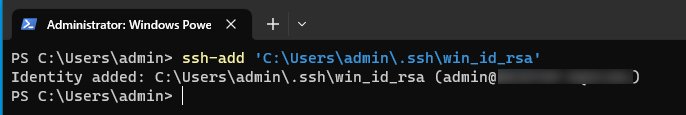
Once our ssh key-pair has been generated we can move onto adding our private key to the ssh agent using the ssh-add command. This important step adds our key to the authentication agent which we need in order to authenticate with our key-pair.
ssh-add 'C:\Users\admin\.ssh\win_id_rsa'
Connecting to Windows From Linux
After we’ve successfully added our ssh key to the authentication agent with ssh-add we are ready to test ssh authentication using our .pub public key.
In this example I’m going to connect to my Windows machine from my Linux machine. First we need to ensure that the public key we just generated is on the machine we want connect from. Since I’m using virtual machines I’ll simply move my key over using a shared folder from my host.
The Windows public ssh key located on my Linux machine
We also need to know the IP address of our Windows machine, we can find this information out easily with PowerShell with the Get-NetIPAddress command.
Get-NetIPAddress -AddressFamily IPv4 | Format-Table
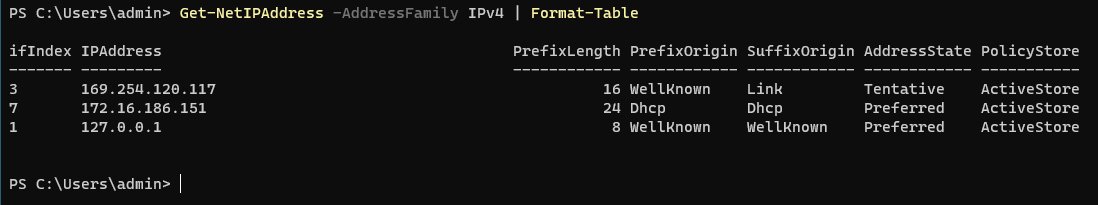
Get-NetIPAddress command output
Once we have our public key on our Linux machine and the IP address of our Windows machine we are ready ssh to our Windows machine.
To confirm we are on a Linux machine we can use the uname -a command.
Running the uname -a command
To ssh to our Windows machine we can run the following command providing our username, IP address, as well as public key.
ssh admin@172.16.186.151 -i win_id_rsa.pub
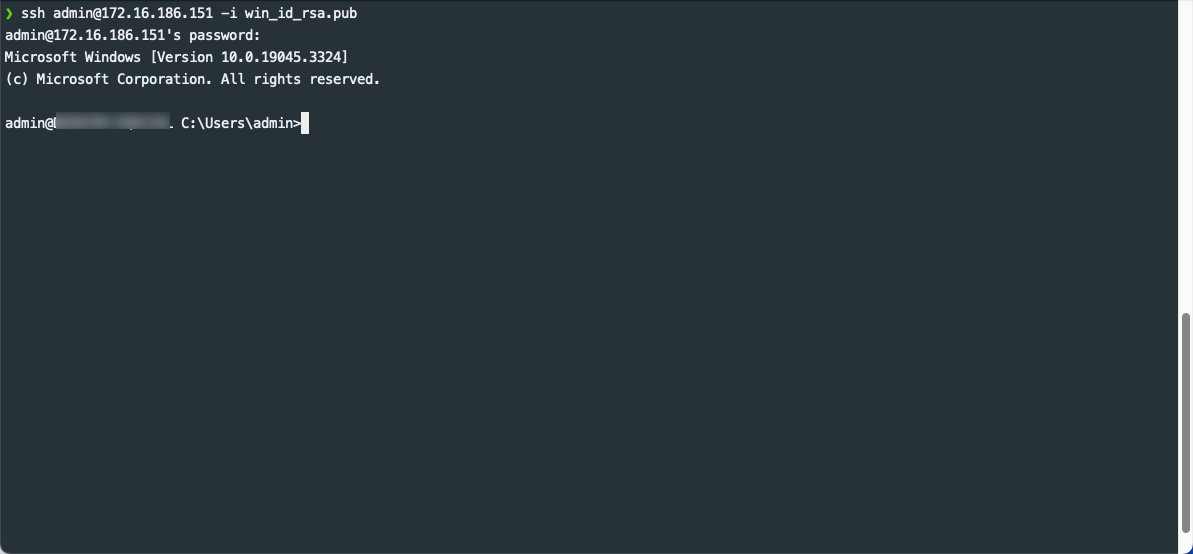
Running the SSH command to connect to Windows from Linux
If successful you’ll see a Microsoft Windows command-line terminal from your Linux.
Connecting to Linux From Windows
If we would like to connect to our Linux machine from our Windows machine we can perform the opposite steps. Similar to the above we need to do the following (if you already have a key-pair for your Linux machine setup feel free to skip the “Ensuring SSH Is Installed on Linux” section).
Ensuring SSH Is Installed on Linux
In this section I will use an Ubuntu Desktop as my Linux machine. We need to perform some administrative tasks to ensure that we are able to connect to our Linux machine from Windows
Install SSH
If SSH is not already installed we can install using apt install.
Running the sudo apt install -y ssh
Start & Enable the SSH Service
Once the ssh package as well as dependant packages are installed we can start the ssh service using the following the systemctl command.
You can also ensure that the ssh starts in a persistent manner when the Ubuntu machine boots.
sudo systemctl enable ssh
Generate SSH keys
Similar to how we generated a key-pair on Windows, we can use the same command on Linux to generate a new SSH key-pair. We can do so with the ssh-keygen command.
Like when we did with Windows we’ll be required to give the output location of our key-pair as well as provide an optional password.
Running the ssh-keygen command
Adding the SSH Key with ssh-add
Once we’ve generated the ssh key we can proceed to add the private key to the ssh authentication agent using ssh-add command by running.
ssh-add /home/gothburz/.ssh/ubuntu_id_rsa
Running the ssh-add command
Copy SSH Public Key to Windows Machine
Once we have ensured that ssh is properly up and running including adding our key-pair to the ssh authentication agent we need to ensure we copied our public key over to our Windows machine
Since I’m using virtual machines I’ll simply move my key over using a shared folder from my host.
Verifying the Linux SSH public key with the ls command
Connecting to Linux from Windows Machine
Once we have ensured that our Linux machine is properly configured with SSH and that our public ssh key is on our Windows machine we can go ahead and initiate an SSH connection.
We can use the ssh command to initiate the connection from Windows to Linux using powershell.
Be sure to change your username@host as well as the path to the public key.
ssh gothburz@172.16.186.163 -i .\ubuntu_id_rsa.pub

Connecting to our Linux machine from Windows with the ssh command
Depending on your configuration you might be asked for a password as well. Once you’ve ran the ssh command and entered the correct password you should enter a new Linux terminal from Windows. Congrats!
Learn More About SSH
If you’d like to add a definitive guide to SSH to your library then I highly recommend the following book. Written for a wide audience, this book covers the Secure Shell (SSH) in great detail by providing a comprehensive guide for a plethora of use cases, features, and even contains in-depth case studies on large, sensitive computer networks.
Conclusion
In this blog post we looked at how to use the SSH protocol on Microsoft Windows using OpenSSH. We went through the following:
-
The OpenSSH installation process with the Windows Package Manager (WinGet)
-
The SSH configuration process
-
How to connect to Windows from Linux
-
How to connect to Linux from Windows
I hope you found this post insightful and useful in your day-to-day operations.
Let me know if you have any questions regarding SSH and happy connecting! 
В Windows 10 и Windows Server 2019 появился встроенный SSH клиент, который вы можете использовать для подключения к *Nix серверам, ESXi хостам и другим устройствам по защищенному протоколу, вместо Putty, MTPuTTY или других сторонних SSH клиентов. Встроенный SSH клиент Windows основан на порте OpenSSH и предустановлен в ОС, начиная с Windows 10 1809.
Содержание:
- Установка клиента OpenSSH в Windows 10
- Как использовать SSH клиенте в Windows 10?
- SCP: копирование файлов из/в Windows через SSH
Установка клиента OpenSSH в Windows 10
Клиент OpenSSH входит в состав Features on Demand Windows 10 (как и RSAT). Клиент SSH установлен по умолчанию в Windows Server 2019 и Windows 10 1809 и более новых билдах.
Проверьте, что SSH клиент установлен:
Get-WindowsCapability -Online | ? Name -like 'OpenSSH.Client*'
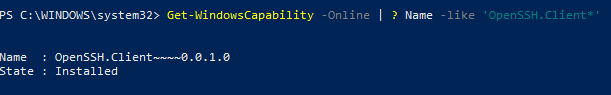
В нашем примере клиент OpenSSH установлен (статус: State: Installed).
Если SSH клиент отсутствует (State: Not Present), его можно установить:
- С помощью команды PowerShell:
Add-WindowsCapability -Online -Name OpenSSH.Client* - С помощью DISM:
dism /Online /Add-Capability /CapabilityName:OpenSSH.Client~~~~0.0.1.0 - Через Параметры -> Приложения -> Дополнительные возможности -> Добавить компонент. Найдите в списке Клиент OpenSSH и нажмите кнопку Установить.
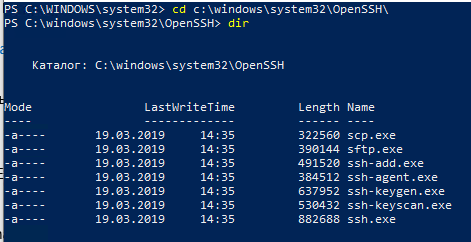
]Бинарные файлы OpenSSH находятся в каталоге c:\windows\system32\OpenSSH\.
- ssh.exe – это исполняемый файл клиента SSH;
- scp.exe – утилита для копирования файлов в SSH сессии;
- ssh-keygen.exe – утилита для генерации ключей аутентификации;
- ssh-agent.exe – используется для управления ключами;
- ssh-add.exe – добавление ключа в базу ssh-агента.
Вы можете установить OpenSSH и в предыдущих версиях Windows – просто скачайте и установите Win32-OpenSSH с GitHub (есть пример в статье “Настройка SSH FTP в Windows”).
Как использовать SSH клиенте в Windows 10?
Чтобы запустить SSH клиент, запустите командную строку
PowerShell
или
cmd.exe
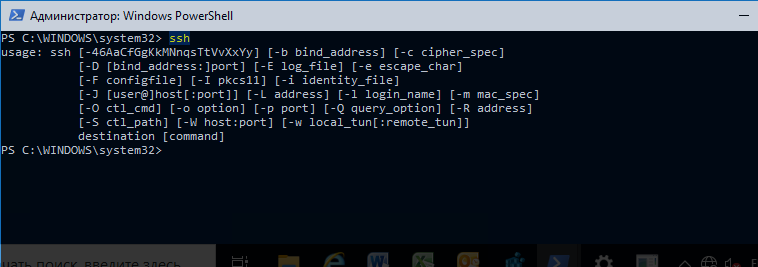
. Выведите доступные параметры и синтаксис утилиты ssh.exe, набрав команду:
ssh
usage: ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-b bind_address] [-c cipher_spec]
[-D [bind_address:]port] [-E log_file] [-e escape_char]
[-F configfile] [-I pkcs11] [-i identity_file]
[-J [user@]host[:port]] [-L address] [-l login_name] [-m mac_spec]
[-O ctl_cmd] [-o option] [-p port] [-Q query_option] [-R address]
[-S ctl_path] [-W host:port] [-w local_tun[:remote_tun]]
destination [command]
Для подключения к удаленному серверу по SSH используется команда:
ssh username@host
Если SSH сервер запущен на нестандартном порту, отличном от TCP/22, можно указать номер порта:
ssh username@host -p port
Например, чтобы подключиться к Linux хосту с IP адресом 192.168.1.202 под root, выполните:
ssh [email protected]
При первом подключении появится запрос на добавление ключа хоста в доверенные, наберите yes -> Enter (при этом отпечаток ключа хоста добавляется в файл C:\Users\username\.ssh\known_hosts).
Затем появится запрос пароля указанной учетной записи, укажите пароль root, после чего должна открытся консоль удаленного Linux сервера (в моем примере на удаленном сервере установлен CentOS 8).
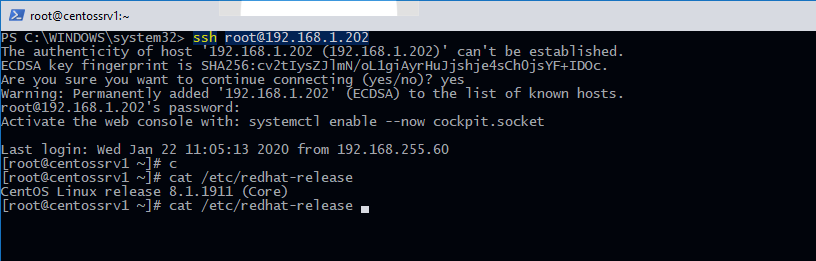
С помощью SSH вы можете подключаться не только к *Nix подобным ОС, но и к Windows. В одной из предыдущих статей мы показали, как настроить OpenSSH сервер на Windows 10 и подключиться к нему с другого компьютера Windows с помощью SSH клиента.
Если вы используете SSH аутентификацию по RSA ключам (см. пример с настройкой SSH аутентификации по ключам в Windows), вы можете указать путь к файлу с закрытым ключом в клиенте SSH так:
ssh [email protected] -i "C:\Users\username\.ssh\id_rsa"
Также вы можете добавить ваш закрытый ключ в SSH-Agent. Сначала нужно включить службу ssh-agent и настроить ее автозапуск:
set-service ssh-agent StartupType ‘Automatic’
Start-Service ssh-agent
Добавим ваш закрытый ключ в базу ssh-agent:
ssh-add "C:\Users\username\.ssh\id_rsa"
Теперь вы можете подключиться к серверу по SSH без указания пути к RSA ключу, он будет использоваться автоматически. Пароль для подключения не запрашивается (если только вы не защитили ваш RSA ключ отдельным паролем):
ssh [email protected]
Еще несколько полезных аргументов SSH:
-
-C
– сжимать трафик между клиентом и сервером (полезно на медленных и нестабильных подключениях); -
-v
– вывод подробной информации обо всех действия клиента ssh; -
-R
/
-L
– можно использовать для проброса портов через SSH туннель.
SCP: копирование файлов из/в Windows через SSH
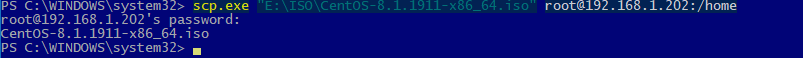
С помощью утилиты scp.exe, которая входит в состав пакета клиента SSH, вы можете скопировать файл с вашего компьютера на SSH сервер:
scp.exe "E:\ISO\CentOS-8.1.1911-x86_64.iso" [email protected]:/home
Можно рекурсивно скопировать все содержимое каталога:
scp -r E:\ISO\ [email protected]:/home
И наоборот, вы можете скопировать файл с удаленного сервера на ваш компьютер:
scp.exe [email protected]:/home/CentOS-8.1.1911-x86_64.iso e:\tmp
Если вы настроите аутентификацию по RSA ключам, то при копировании файлов не будет появляться запрос на ввод пароля для подключения к SSH серверу. Это удобно, когда вам нужно настроить автоматическое копирование файлов по расписанию.
Итак, теперь вы можете прямо из Windows 10 подключаться к SSH серверам, копировать файлы с помощью scp без установки сторонних приложений и утилит.
The latest builds of Windows 10 and Windows 11 include a build-in SSH server and client that are based on OpenSSH.
This means now you can remotely connect to Windows 10/11 or Windows Server 2019 using any SSH client, like Linux distros.
Let’s see how to configure OpenSSH on Windows 10 and Windows 11, and connect to it using Putty or any other SSH client.
OpenSSH is an open-source, cross-platform version of Secure Shell (SSH) that is used by Linux users for a long time.
This project is currently ported to Windows and can be used as an SSH server on almost any version of Windows.
In the latest versions of Windows Server 2022/2019 and Windows 11, OpenSSH is built-in to the operating system image.
How to install SSH Server on Windows 10?
Make sure our build of Windows 10 is 1809 or newer. The easiest way to do this is by running the command:
Note. If you have an older Windows 10 build installed, you can update it through Windows Update or using an ISO image with a newer version of Windows 10 (you can create an image using the Media Creation Tool). If you don’t want to update your Windows 10 build, you can manually install the Win32-OpenSSH port for Windows with GitHub.
Enable feature
We can enable OpenSSH server in Windows 10 through the graphical Settings panel:
-
Go to the
Settings>Apps>Apps and features>Optional features(or run thecommand ms-settings:appsfeatures) -
Click Add a feature, select
OpenSSH Server(OpenSSH-based secure shell (SSH) server, for secure key management and access from remote machines), and clickInstall
Install using PowerShell
We can also install sshd server using PowerShell:
Add-WindowsCapability -Online -Name OpenSSH.Server*
Install using DISM
Or we can also install sshd server using DISM:
dism /Online /Add-Capability /CapabilityName:OpenSSH.Server~~~~0.0.1.0
If you want to make sure the OpenSSH server is installed, run the following PS command:
Get-WindowsCapability -Online | ? Name -like 'OpenSSH.Server*'
How to uninstall SSH Server?
Use the following PowerShell command to uninstall the SSH server:
Remove-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0
How to Install SSH Server on Windows 11?
Also, you can add the OpenSSH Server on Windows 11.
- Go to Settings > Apps > Optional features;
- Click View Features;
Select OpenSSH Server from the list and click Next > Install;
Wait for the installation to complete.
The OpenSSH binaries are located in the C:\Windows\System32\OpenSSH\ folder.
Configuring SSH Service on Windows 10 and 11
Check the status of ssh-agent and sshd services using the PowerShell command Get-Service:
As we can see, both services are in a Stopped state and not added to the automatic startup list. To start services and configure autostart for them, run the following commands:
Start-Service sshd Set-Service -Name sshd -StartupType 'Automatic' Start-Service 'ssh-agent' Set-Service -Name 'ssh-agent' -StartupType 'Automatic'
We also need to allow incoming connections to TCP port 22 in the Windows Defender Firewall. We can open the port using netsh:
netsh advfirewall firewall add rule name=”SSHD service” dir=in action=allow protocol=TCP localport=22
Or we can add a firewall rule to allow SSH traffic using PowerShell:
New-NetFirewallRule -Name sshd -DisplayName 'OpenSSH Server (sshd)' -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22
Now we can connect to Windows 10 using any SSH client. To connect from Linux, use the command:
ssh -p 22 admin@192.168.1.90
Here, the admin is a local Windows user under which we want to connect. 192.168.1.90 is an IP address of your Windows 10 computer.
After that, a new Windows command prompt window will open in SSH session.
Hint. To run the PowerShell.exe cli instead of cmd.exe shell when logging in via SSH on Windows 10, we need to run the following command in Windows 10 (under admin account):
New-ItemProperty -Path "HKLM:\SOFTWARE\OpenSSH" -Name DefaultShell -Value "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -PropertyType String -Force
Now, we change the default OpenSSH shell. From here, when connecting to Windows via SSH, you will immediately see PowerShell prompt instead of cmd.exe.
If you want to use key-based ssh authentication instead of password authentication, you need to generate a key using ssh-keygen on your client.
Then, the contents of the id_rsa.pub file must be copied to the c:\users\admin\.ssh\authorized_keys file in Windows 10.
After that, you can connect from your Linux client to Windows 10 without a password. Use the command:
ssh -l admin@192.168.1.90
Configuration
We can configure various OpenSSH server settings in Windows using the %programdata%\ssh\sshd_config configuration file.
For example, we can disable password authentication and leave only key-based auth with:
PubkeyAuthentication yes PasswordAuthentication no
Here we can also specify a new TCP port (instead of the default TCP 22 port) on which the SSHD will accept connections. For example:
Using the directives AllowGroups, AllowUsers, DenyGroups, DenyUsers, you can specify users and groups who are allowed or denied to connect to Windows via SSH:
DenyUsers theitbros\jbrown@192.168.1.15— blocks connections to username jbrown from 192.168.1.15 hostsжDenyUsers theitbros\*— prevent all users from theitbros domain to connect host using sshжAllowGroups theitbros\ssh_allow— only allow users from theitbtos\ssh_allow connect hostю- The allow and deny rules of sshd are processed in the following order:
DenyUsers,AllowUsers,DenyGroups, andAllowGroups.
After making changes to the sshd_config file, you need to restart the sshd service:
Get-Service sshd | Restart-Service –force
In previous versions of OpenSSH on Windows, all sshd service logs were written to the text file C:\ProgramData\ssh\logs\sshd.log by default.
On Windows 11, SSH logs can be viewed using the Event Viewer console (eventvwr.msc). All SSH events are available in a separate section Application and Services Logs > OpenSSH > Operational.
For example, the screenshot shows an example of an event with a successful connection to the computer via SSH. You can see the ssh client’s IP address (hostname) and the username used to connect.
sshd: Accepted password for jbrown from 192.168.14.14. port 49833 ssh2
I needed to run git natively in windows (no wsl) for a recent project. I use ssh certificates with passphrases to authenticate with my git provider.
Ssh requires the certificate passphrase every time you use a connection. It’s annoying typing this passphrase in to terminal when using a git command.
The Problem
On most *nix systems there is an ssh-agent installed that will store your pass phrases so you don’t have to enter them when using Git with ssh.
Ssh-agent is harder to configure on windows because some of the default settings and paths are different to *nix systems.
I didn’t want to use Git for Windows because it uses GitBash. I couldn’t use WSL because I wanted git to work on any terminal in windows.
These are the steps I had to research to use Git on Windows with the built in Windows ssh-agent.
Note: You must be an administrator to perform the required actions.
Open ssl on Windows
If you use Windows 10 or higher there is a built-in openssl instance. You can turn it on in the Optional Features settings pane.
Microsoft provide more instructions here: https://learn.microsoft.com/en-us/windows-server/administration/openssh/openssh_install_firstuse?tabs=gui
Follow the instructions to install it if you don’t have it.
A note on certificates
I’ll assume that you have ssh certificates available and any ssh aliases are set in the config file
The default location for the config file on windows is
$HOME\.ssh\config
You should create that file if you need ssh aliases. You can read more about this in my article on ssh for git accounts — /2021/05/04/configure-multiple-github-accounts-one-computer/
Enabling Ssh agent
Open a powershell terminal as administrator and run the following to have ssh-agent available.
# Have ssh agent start automatically
Get-Service ssh-agent | Set-Service -StartupType Automatic
# Start ssh agent now
Start-Service ssh-agent
# Should work successfully
Get-Service ssh-agent
Configure git to use Windows ssh
# tell git to use ssh.exe
git config --global core.sshCommand "'C:\Windows\System32\OpenSSH\ssh.exe'"
Load keys into ssh agent
Copy your keys into a folder that ssh-agent can access. Anywhere in the $HOME/.ssh should be ok.
Then add the key to ssh-agent. You will be prompted for a password and ssh agent will remember it for you.
ssh-add "C:\Users\darragh\.ssh\authorized_keys\darraghPersonalGithub"
