Время на прочтение9 мин
Количество просмотров174K

Некоторое время поработав с Zabbix, я подумал, почему бы не попробовать использовать его в качестве решения для мониторинга событий информационной безопасности. Как известно, в ИТ инфраструктуре предприятия множество самых разных систем, генерирующих такой поток событий информационной безопасности, что просмотреть их все просто невозможно. Сейчас в нашей корпоративной системе мониторинга сотни сервисов, которые мы наблюдаем с большой степенью детализации. В данной статье, я рассматриваю особенности использования Zabbix в качестве решения по мониторингу событий ИБ.
Что же позволяет Zabbix для решения нашей задачи? Примерно следующее:
- Максимальная автоматизация процессов инвентаризации ресурсов, управления уязвимостями, контроля соответствия политикам безопасности и изменений.
- Постоянная защита корпоративных ресурсов с помощью автоматического мониторинга информационной безопасности.
- Возможность получать максимально достоверную картину защищенности сети.
- Анализ широкого спектра сложных систем: сетевое оборудование, такое как Cisco, Juniper, платформы Windows, Linux, Unix, СУБД MSQL, Oracle, MySQL и т.д., сетевые приложения и веб-службы.
- Минимизация затрат на аудит и контроль защищенности.
В статье я не буду рассматривать всё выше перечисленное, затронем только наиболее распространённые и простые вопросы.
Подготовка
Итак, для начала я установил сервер мониторинга Zabbix. В качестве платформы мы будем использовать ОС FreeBSD. Думаю, что рассказывать в деталях о процессе установки и настройки нет необходимости, довольно подробная документация на русском языке есть на сайте разработчика, начиная от процесса установки до описания всех возможностей системы.
Мы будем считать что сервер установлен, настроен, а так же настроен web-frontend для работы с ним. На момент написания статьи система работает под управлением ОС FreeBSD 9.1, Zabbix 2.2.1.
Мониторинг событий безопасности MS Windows Server
С помощью системы мониторинга Zabbix можно собирать любую имеющуюся информацию из системных журналов Windows с произвольной степенью детализации. Это означает, что если Windows записывает какое-либо событие в журнал, Zabbix «видит» его, например по Event ID, текстовой, либо бинарной маске. Кроме того, используя Zabbix, мы можем видеть и собирать колоссальное количество интересных для мониторинга безопасности событий, например: запущенные процессы, открытые соединения, загруженные в ядро драйверы, используемые dll, залогиненных через консоль или удалённый доступ пользователей и многое другое.
Всё, что остаётся – определить события возникающие при реализации ожидаемых нами угроз.
Устанавливая решение по мониторингу событий ИБ в ИТ инфраструктуре следует учитывать необходимость выбора баланса между желанием отслеживать всё подряд, и возможностями по обработке огромного количества информации по событиям ИБ. Здесь Zabbix открывает большие возможности для выбора. Ключевые модули Zabbix написаны на C/C++, скорость записи из сети и обработки отслеживаемых событий составляет 10 тысяч новых значений в секунду на более менее обычном сервере с правильно настроенной СУБД.
Всё это даёт нам возможность отслеживать наиболее важные события безопасности на наблюдаемом узле сети под управлением ОС Windows.
Итак, для начала рассмотрим таблицу с Event ID, которые, на мой взгляд, очевидно, можно использовать для мониторинга событий ИБ:
События ИБ MS Windows Server Security Log
Я уделяю внимание локальным группам безопасности, но в более сложных схемах AD необходимо учитывать так же общие и глобальные группы.
Дабы не дублировать информацию, подробнее о критически важных событиях можно почитать в статье:
http://habrahabr.ru/company/netwrix/blog/148501/
Способы мониторинга событий ИБ MS Windows Server
Рассмотрим практическое применение данной задачи.
Для сбора данных необходимо создать новый элемент данных:
Ключ: eventlog[Security,,,,1102|4624|4625|4720|4724|4725|4726|4731|4732|4733|4734|4735|4738|4781]
Тип элемента данных: Zabbix агент (активный)
Тип информации: Журнал (лог)
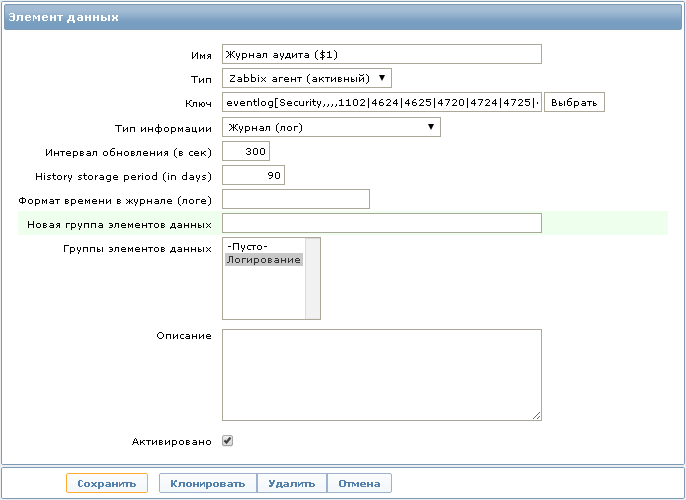
При желании для каждого Event ID можно создать по отдельному элементу данных, но я использую в одном ключе сразу несколько Event ID, чтобы хранить все полученные записи в одном месте, что позволяет быстрее производить поиск необходимой информации, не переключаясь между разными элементами данных.
Хочу заметить что в данном ключе в качестве имени мы используем журнал событий Security.
Теперь, когда элемент данных мы получили, следует настроить триггер. Триггер – это механизм Zabbix, позволяющий сигнализировать о том, что наступило какое-либо из отслеживаемых событий. В нашем случае – это событие из журнала сервера или рабочей станции MS Windows.
Теперь все что будет фиксировать журнал аудита с указанными Event ID будет передано на сервер мониторинга. Указание конкретных Event ID полезно тем, что мы получаем только необходимую информацию, и ничего лишнего.
Вот одно из выражений триггера:
{Template Windows - Eventlog 2008:eventlog[Security,,,,1102|4624|4625|4720|4724|4725|4726|4731|4732|4733|4734|4735|4738|4781].logeventid(4624)}=1&{Template Windows - Eventlog 2008:eventlog[Security,,,,1102|4624|4625|4720|4724|4725|4726|4731|4732|4733|4734|4735|4738|4781].nodata(5m)}=0

Данное выражение позволит отображать на Dashboard информацию о том что «Вход с учётной записью выполнен успешно», что соответствует Event ID 4624 для MS Windows Server 2008. Событие исчезнет спустя 5 минут, если в течение этого времени не был произведен повторный вход.
Если же необходимо отслеживать определенного пользователя, например “Администратор”, можно добавить к выражению триггера проверку по regexp:
&{Template Windows - Eventlog 2008:eventlog[Security,,,,1102|4624|4625|4720|4724|4725|4726|4731|4732|4733|4734|4735|4738|4781,,skip].regexp(Администратор)}=1
Тогда триггер сработает только в том случае если будет осуществлён вход в систему именно под учетной записью с именем “Администратор”.
P.S.
Мы рассматривали простейший пример, но так же можно использовать более сложные конструкции. Например с использованием типов входа в систему, кодов ошибок, регулярных выражений и других параметров.
Таким образом тонны сообщений, генерируемых системами Windows будет проверять Zabbix, а не наши глаза. Нам остаётся только смотреть на панель Zabbix Dashboard.
Дополнительно, у меня настроена отправка уведомлений на e-mail. Это позволяет оперативно реагировать на события, и не пропустить события произошедшие например в нерабочее время.
Мониторинг событий безопасности Unix систем
Система мониторинга Zabbix так же позволяет собирать информацию из лог-файлов ОС семейства Unix.
События ИБ в Unix системах, подходящие для всех
Такими проблемами безопасности систем семейства Unix являются всё те же попытки подбора паролей к учётным записям, а так же поиск уязвимостей в средствах аутентификации, например, таких как SSH, FTP и прочих.
Некоторые критически важные события в Unix системах
Исходя из вышеуказанного следует, что нам необходимо отслеживать действия, связанные с добавлением, изменением и удалением учётных записей пользователей в системе.
Так же немаловажным фактом будет отслеживание попыток входа в систему. Изменения ключевых файлов типа sudoers, passwd, etc/rc.conf, содержимое каталогов /usr/local/etc/rc.d наличие запущенных процессов и т.п.
Способы мониторинга ИБ в Unix системах
Рассмотрим следующий пример. Нужно отслеживать входы в систему, неудачные попытки входа, попытки подбора паролей в системе FreeBSD по протоколу SSH.
Вся информация об этом, содержится в лог-файле /var/log/auth.log.
По умолчанию права на данный файл — 600, и его можно просматривать только с привилегиями root. Придется немного пожертвовать локальной политикой безопасности, и разрешить читать данный файл группе пользователей zabbix:
Меняем права на файл:
chgrp zabbix /var/log/auth.log
chmod 640 /var/log/auth.log
Нам понадобится новый элемент данных со следующим ключом:
log[/var/log/auth.log,sshd,,,skip]
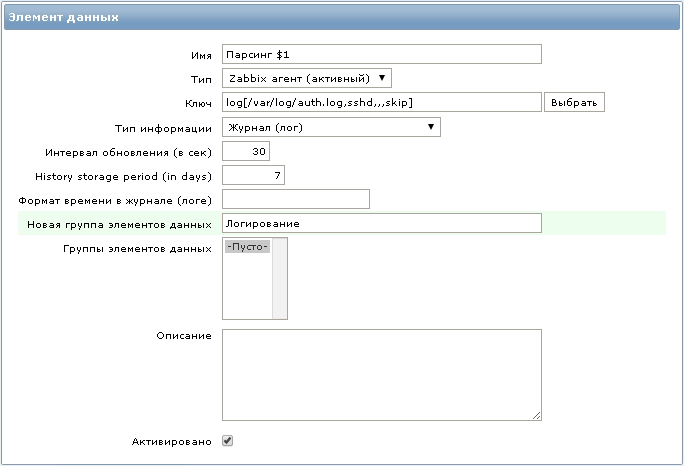
Все строки в файле /var/log/auth.log содержащие слово ”sshd” будут переданы агентом на сервер мониторинга.
Далее можно настроить триггер со следующим выражением:
{Template FreeBSD - SSH:log[/var/log/auth.log,sshd,,,skip].regexp(error:)}|{Template FreeBSD - SSH:log[/var/log/auth.log,sshd,,,skip].regexp(Wrong passwordr:)}&{Template FreeBSD - SSH:log[/var/log/auth.log,sshd,,,skip].nodata(3m)}=0
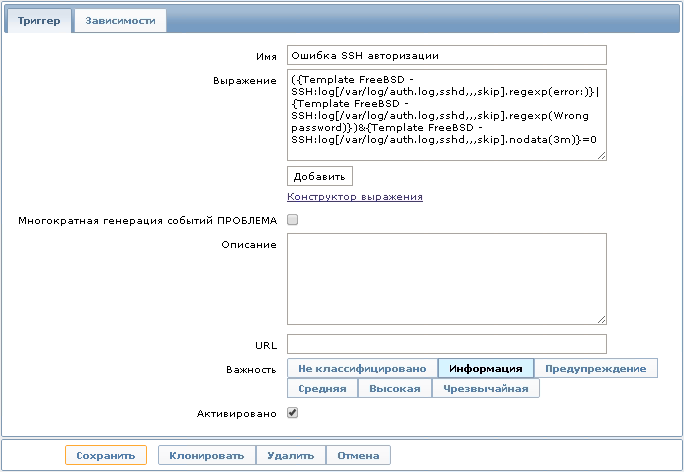
Это выражение определяется как проблема, когда в лог-файле появляются записи, отобранные по регулярному выражению “error:”. Открыв историю полученных данных, мы увидим ошибки, которые возникали при авторизации по протоколу SSH.
Вот пример последнего значения элемента данных, по которому срабатывает данный триггер:

Рассмотрим ещё один пример мониторинга безопасности в ОС FreeBSD:
С помощью агента Zabbix мы можем осуществлять проверку контрольной суммы файла /etc/passwd.
Ключ в данном случае будет следующий:
vfs.file.cksum[/etc/passwd]
Это позволяет контролировать изменения учётных записей, включая смену пароля, добавление или удаление пользователей. В данном случае мы не узнаем, какая конкретная операция была произведена, но если к серверу кроме Вас доступ никто не имеет, то это повод для быстрого реагирования. Если необходимо более детально вести политику то можно использовать другие ключи, например пользовательские параметры.
Например, если мы хотим получать список пользователей, которые на данный момент заведены в системе, можно использовать такой пользовательский параметр:
UserParameter=system.users.list, /bin/cat /etc/passwd | grep -v "#" | awk -F\: '{print $$1}'
И, например, настроить триггер на изменение в получаемом списке.
Или же можно использовать такой простой параметр:
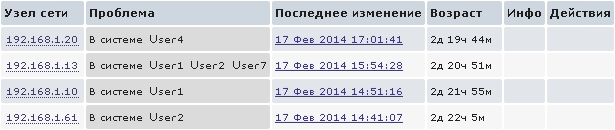
UserParameter=system.users.online, /usr/bin/users
Так мы увидим на Dashboard, кто на данный момент находится в системе:
Мониторинг событий ИБ на сетевых устройствах
С помощью Zabbix можно так же очень эффективно отслеживать события ИБ на сетевых устройствах Cisco и Juniper, используя протокол SNMP. Передача данных с устройств осуществляется с помощью так называемых трапов (SNMP Trap).
С точки зрения ИБ можно выделить следующие события, которые необходимо отслеживать — изменения конфигураций оборудования, выполнение команд на коммутаторе/маршрутизаторе, успешную авторизацию, неудачные попытки входа и многое другое.
Способы мониторинга
Рассмотрим опять же пример с авторизацией:
В качестве стенда я буду использовать эмулятор GNS3 с маршрутизатором Cisco 3745. Думаю многим знакома данная схема.
Для начала нам необходимо настроить отправку SNMP трапов с маршрутизатора на сервер мониторинга. В моём случае это будет выглядеть так:
login block-for 30 attempts 3 within 60
login on-failure log
login on-success log
login delay 5
logging history 5
snmp-server enable traps syslog
snmp-server enable traps snmp authentication
snmp-server host 192.168.1.1 public
Будем отправлять события из Syslog и трапы аутентификации. Замечу, что удачные и неудачные попытки авторизации пишутся именно в Syslog.
Далее необходимо настроить прием нужных нам SNMP трапов на сервере мониторинга.
Добавляем следующие строки в snmptt.conf:
EVENT clogMessageGenerated .1.3.6.1.4.1.9.9.41.2.0.1 "Status Events" Normal
FORMAT ZBXTRAP $ar $N $*
SDESC
EDESC
В нашем примере будем ловить трапы Syslog.
Теперь необходимо настроить элемент данных для сбора статистики со следующим ключом:
snmptrap[“Status”]

Если трап не настроен на сервере мониторинга, то в логе сервера будут примерно такие записи:
unmatched trap received from [192.168.1.14]:...
В результате в полученном логе будет отражаться информация о попытках входа с детализированной информацией (user, source, localport и reason в случае неудачи):

Ну и можно настроить триггер для отображения события на Dashboard:
{192.168.1.14:snmptrap["Status"].regexp(LOGIN_FAILED)}&{192.168.1.14:snmptrap["Status"].nodata(3m)}=0
В сочетании с предыдущим пунктом у нас на Dashboard будет информация вот такого плана:

Аналогично вышеописанному примеру можно осуществлять мониторинг большого количества событий, происходящих на маршрутизаторах Cisco, для описания которых одной статьей явно не обойтись.
Хочу заметить что приведённый пример не будет работать на продуктах Cisco ASA и PIX, так как там несколько иначе организована работа с логированием авторизации.
Juniper и Syslog
Ещё одним примером мы разберем мониторинг авторизации в JunOS 12.1 для устройств Juniper.
Тут мы не сможем воспользоваться трапами SNMP, потому как нет поддержки отправки трапов из Syslog сообщений. Нам понадобится Syslog сервер на базе Unix, в нашем случае им будет тот же сервер мониторинга.
На маршрутизаторе нам необходимо настроить отправку Syslog на сервер хранения:
system syslog host 192.168.1.1 authorization info
Теперь все сообщения об авторизации будут отправляться на Syslog сервер, можно конечно отправлять все сообщения (any any), но переизбыток информации нам не нужен, отправляем только необходимое.
Далее переходим к Syslog серверу
Смотрим tcpdump, приходят ли сообщения:
tcpdump -n -i em0 host 192.168.1.112 and port 514
12:22:27.437735 IP 192.168.1.112.514 > 192.168.1.1.514: SYSLOG auth.info, length: 106
По умолчанию в настройках syslog.conf все что приходит с auth.info должно записываться в /var/log/auth.log. Далее делаем все аналогично примеру с мониторингом входов в Unix.
Вот пример строки из лога:

Остается только настроить триггер на данное событие так же как это было рассмотрено в примере с авторизацией на Unix сервере.
P.S.
Таким способом можно отслеживать множество событий, среди которых такие как: сохранение конфигурации устройства (commit), вход и выход из режима редактирования конфигурации (edit).
Так же хочу заметить, что аналогичным способом можно осуществлять мониторинг и на устройствах Cisco, но способ с SNMP трапами мне кажется более быстрым и удобным, и исключается необходимость в промежуточном Syslog сервере.
Заключение
В заключении хочу отметить, что я с удовольствием приму замечания и дополнения к данной статье, а так же интересные предложения по использованию мониторинга событий информационной безопасности при помощи Zabbix.
Спасибо за внимание. 
Here are some security-related Windows events. You can use the event IDs in this list to search for suspicious activities.
Monitor windows security events and send alerts, protect your windows domain, create insights and reports on active directory audit events with one single tool. Protect windows servers and monitor security risks
Download XpoLog for Windows Server and Active Directory monitoring – out-of-the-box.
| Event ID | What it means |
| 4624 | Successful account log on |
| 4625 | Failed account log on |
| 4634 | An account logged off |
| 4648 | A logon attempt was made with explicit credentials |
| 4719 | System audit policy was changed. |
| 4964 | A special group has been assigned to a new log on |
| 1102 | Audit log was cleared. This can relate to a potential attack |
| 4720 | A user account was created |
| 4722 | A user account was enabled |
| 4723 | An attempt was made to change the password of an account |
| 4725 | A user account was disabled |
| 4728 | A user was added to a privileged global group |
| 4732 | A user was added to a privileged local group |
| 4756 | A user was added to a privileged universal group |
| 4738 | A user account was changed |
| 4740 | A user account was locked out |
| 4767 | A user account was unlocked |
| 4735 | A privileged local group was modified |
| 4737 | A privileged global group was modified |
| 4755 | A privileged universal group was modified |
| 4772 | A Kerberos authentication ticket request failed |
| 4777 | The domain controller failed to validate the credentials of an account. |
| 4782 | Password hash an account was accessed |
| 4616 | System time was changed |
| 4657 | A registry value was changed |
| 4697 | An attempt was made to install a service |
| 4698, 4699, 4700, 4701, 4702 | Events related to Windows scheduled tasks being created, modified, deleted, enabled or disabled |
| 4946 | A rule was added to the Windows Firewall exception list |
| 4947 | A rule was modified in the Windows Firewall exception list |
| 4950 | A setting was changed in Windows Firewall |
| 4954 | Group Policy settings for Windows Firewall has changed |
| 5025 | The Windows Firewall service has been stopped |
| 5031 | Windows Firewall blocked an application from accepting incoming traffic |
| 5152, 5153 | A network packet was blocked by Windows Filtering Platform |
| 5155 | Windows Filtering Platform blocked an application or service from listening on a port |
| 5157 | Windows Filtering Platform blocked a connection |
| 5447 | A Windows Filtering Platform filter was changed |
* If you haven’t read our power guide: “How to Look for Suspicious Activities in Windows Servers”? we recommend you to do so.
To learn more about XpoLog go to our feature tour.
Analyze & monitor Windows logs for security, performance, health and more – automatically with XpoLog fully automated log manager
Join The Community Experts
Learn how to make the best out of your log parsing
“Probably the best log analysis tool”
“This is the best one in the market as of now”
“I can truly recommend their technology and personnel”
| Windows |
1100 |
The event logging service has shut down |
| Windows |
1101 |
Audit events have been dropped by the transport. |
| Windows |
1102 |
The audit log was cleared |
| Windows |
1104 |
The security Log is now full |
| Windows |
1105 |
Event log automatic backup |
| Windows |
1108 |
The event logging service encountered an error |
| Windows |
4608 |
Windows is starting up |
| Windows |
4609 |
Windows is shutting down |
| Windows |
4610 |
An authentication package has been loaded by the Local Security Authority |
| Windows |
4611 |
A trusted logon process has been registered with the Local Security Authority |
| Windows |
4612 |
Internal resources allocated for the queuing of audit messages have been exhausted, leading to the loss of some audits. |
| Windows |
4614 |
A notification package has been loaded by the Security Account Manager. |
| Windows |
4615 |
Invalid use of LPC port |
| Windows |
4616 |
The system time was changed. |
| Windows |
4618 |
A monitored security event pattern has occurred |
| Windows |
4621 |
Administrator recovered system from CrashOnAuditFail |
| Windows |
4622 |
A security package has been loaded by the Local Security Authority. |
| Windows |
4624 |
An account was successfully logged on |
| Windows |
4625 |
An account failed to log on |
| Windows |
4626 |
User/Device claims information |
| Windows |
4627 |
Group membership information. |
| Windows |
4634 |
An account was logged off |
| Windows |
4646 |
IKE DoS-prevention mode started |
| Windows |
4647 |
User initiated logoff |
| Windows |
4648 |
A logon was attempted using explicit credentials |
| Windows |
4649 |
A replay attack was detected |
| Windows |
4650 |
An IPsec Main Mode security association was established |
| Windows |
4651 |
An IPsec Main Mode security association was established |
| Windows |
4652 |
An IPsec Main Mode negotiation failed |
| Windows |
4653 |
An IPsec Main Mode negotiation failed |
| Windows |
4654 |
An IPsec Quick Mode negotiation failed |
| Windows |
4655 |
An IPsec Main Mode security association ended |
| Windows |
4656 |
A handle to an object was requested |
| Windows |
4657 |
A registry value was modified |
| Windows |
4658 |
The handle to an object was closed |
| Windows |
4659 |
A handle to an object was requested with intent to delete |
| Windows |
4660 |
An object was deleted |
| Windows |
4661 |
A handle to an object was requested |
| Windows |
4662 |
An operation was performed on an object |
| Windows |
4663 |
An attempt was made to access an object |
| Windows |
4664 |
An attempt was made to create a hard link |
| Windows |
4665 |
An attempt was made to create an application client context. |
| Windows |
4666 |
An application attempted an operation |
| Windows |
4667 |
An application client context was deleted |
| Windows |
4668 |
An application was initialized |
| Windows |
4670 |
Permissions on an object were changed |
| Windows |
4671 |
An application attempted to access a blocked ordinal through the TBS |
| Windows |
4672 |
Special privileges assigned to new logon |
| Windows |
4673 |
A privileged service was called |
| Windows |
4674 |
An operation was attempted on a privileged object |
| Windows |
4675 |
SIDs were filtered |
| Windows |
4688 |
A new process has been created |
| Windows |
4689 |
A process has exited |
| Windows |
4690 |
An attempt was made to duplicate a handle to an object |
| Windows |
4691 |
Indirect access to an object was requested |
| Windows |
4692 |
Backup of data protection master key was attempted |
| Windows |
4693 |
Recovery of data protection master key was attempted |
| Windows |
4694 |
Protection of auditable protected data was attempted |
| Windows |
4695 |
Unprotection of auditable protected data was attempted |
| Windows |
4696 |
A primary token was assigned to process |
| Windows |
4697 |
A service was installed in the system |
| Windows |
4698 |
A scheduled task was created |
| Windows |
4699 |
A scheduled task was deleted |
| Windows |
4700 |
A scheduled task was enabled |
| Windows |
4701 |
A scheduled task was disabled |
| Windows |
4702 |
A scheduled task was updated |
| Windows |
4703 |
A token right was adjusted |
| Windows |
4704 |
A user right was assigned |
| Windows |
4705 |
A user right was removed |
| Windows |
4706 |
A new trust was created to a domain |
| Windows |
4707 |
A trust to a domain was removed |
| Windows |
4709 |
IPsec Services was started |
| Windows |
4710 |
IPsec Services was disabled |
| Windows |
4711 |
PAStore Engine (1%) |
| Windows |
4712 |
IPsec Services encountered a potentially serious failure |
| Windows |
4713 |
Kerberos policy was changed |
| Windows |
4714 |
Encrypted data recovery policy was changed |
| Windows |
4715 |
The audit policy (SACL) on an object was changed |
| Windows |
4716 |
Trusted domain information was modified |
| Windows |
4717 |
System security access was granted to an account |
| Windows |
4718 |
System security access was removed from an account |
| Windows |
4719 |
System audit policy was changed |
| Windows |
4720 |
A user account was created |
| Windows |
4722 |
A user account was enabled |
| Windows |
4723 |
An attempt was made to change an account’s password |
| Windows |
4724 |
An attempt was made to reset an accounts password |
| Windows |
4725 |
A user account was disabled |
| Windows |
4726 |
A user account was deleted |
| Windows |
4727 |
A security-enabled global group was created |
| Windows |
4728 |
A member was added to a security-enabled global group |
| Windows |
4729 |
A member was removed from a security-enabled global group |
| Windows |
4730 |
A security-enabled global group was deleted |
| Windows |
4731 |
A security-enabled local group was created |
| Windows |
4732 |
A member was added to a security-enabled local group |
| Windows |
4733 |
A member was removed from a security-enabled local group |
| Windows |
4734 |
A security-enabled local group was deleted |
| Windows |
4735 |
A security-enabled local group was changed |
| Windows |
4737 |
A security-enabled global group was changed |
| Windows |
4738 |
A user account was changed |
| Windows |
4739 |
Domain Policy was changed |
| Windows |
4740 |
A user account was locked out |
| Windows |
4741 |
A computer account was created |
| Windows |
4742 |
A computer account was changed |
| Windows |
4743 |
A computer account was deleted |
| Windows |
4744 |
A security-disabled local group was created |
| Windows |
4745 |
A security-disabled local group was changed |
| Windows |
4746 |
A member was added to a security-disabled local group |
| Windows |
4747 |
A member was removed from a security-disabled local group |
| Windows |
4748 |
A security-disabled local group was deleted |
| Windows |
4749 |
A security-disabled global group was created |
| Windows |
4750 |
A security-disabled global group was changed |
| Windows |
4751 |
A member was added to a security-disabled global group |
| Windows |
4752 |
A member was removed from a security-disabled global group |
| Windows |
4753 |
A security-disabled global group was deleted |
| Windows |
4754 |
A security-enabled universal group was created |
| Windows |
4755 |
A security-enabled universal group was changed |
| Windows |
4756 |
A member was added to a security-enabled universal group |
| Windows |
4757 |
A member was removed from a security-enabled universal group |
| Windows |
4758 |
A security-enabled universal group was deleted |
| Windows |
4759 |
A security-disabled universal group was created |
| Windows |
4760 |
A security-disabled universal group was changed |
| Windows |
4761 |
A member was added to a security-disabled universal group |
| Windows |
4762 |
A member was removed from a security-disabled universal group |
| Windows |
4763 |
A security-disabled universal group was deleted |
| Windows |
4764 |
A groups type was changed |
| Windows |
4765 |
SID History was added to an account |
| Windows |
4766 |
An attempt to add SID History to an account failed |
| Windows |
4767 |
A user account was unlocked |
| Windows |
4768 |
A Kerberos authentication ticket (TGT) was requested |
| Windows |
4769 |
A Kerberos service ticket was requested |
| Windows |
4770 |
A Kerberos service ticket was renewed |
| Windows |
4771 |
Kerberos pre-authentication failed |
| Windows |
4772 |
A Kerberos authentication ticket request failed |
| Windows |
4773 |
A Kerberos service ticket request failed |
| Windows |
4774 |
An account was mapped for logon |
| Windows |
4775 |
An account could not be mapped for logon |
| Windows |
4776 |
The domain controller attempted to validate the credentials for an account |
| Windows |
4777 |
The domain controller failed to validate the credentials for an account |
| Windows |
4778 |
A session was reconnected to a Window Station |
| Windows |
4779 |
A session was disconnected from a Window Station |
| Windows |
4780 |
The ACL was set on accounts which are members of administrators groups |
| Windows |
4781 |
The name of an account was changed |
| Windows |
4782 |
The password hash an account was accessed |
| Windows |
4783 |
A basic application group was created |
| Windows |
4784 |
A basic application group was changed |
| Windows |
4785 |
A member was added to a basic application group |
| Windows |
4786 |
A member was removed from a basic application group |
| Windows |
4787 |
A non-member was added to a basic application group |
| Windows |
4788 |
A non-member was removed from a basic application group.. |
| Windows |
4789 |
A basic application group was deleted |
| Windows |
4790 |
An LDAP query group was created |
| Windows |
4791 |
A basic application group was changed |
| Windows |
4792 |
An LDAP query group was deleted |
| Windows |
4793 |
The Password Policy Checking API was called |
| Windows |
4794 |
An attempt was made to set the Directory Services Restore Mode administrator password |
| Windows |
4797 |
An attempt was made to query the existence of a blank password for an account |
| Windows |
4798 |
A user’s local group membership was enumerated. |
| Windows |
4799 |
A security-enabled local group membership was enumerated |
| Windows |
4800 |
The workstation was locked |
| Windows |
4801 |
The workstation was unlocked |
| Windows |
4802 |
The screen saver was invoked |
| Windows |
4803 |
The screen saver was dismissed |
| Windows |
4816 |
RPC detected an integrity violation while decrypting an incoming message |
| Windows |
4817 |
Auditing settings on object were changed. |
| Windows |
4818 |
Proposed Central Access Policy does not grant the same access permissions as the current Central Access Policy |
| Windows |
4819 |
Central Access Policies on the machine have been changed |
| Windows |
4820 |
A Kerberos Ticket-granting-ticket (TGT) was denied because the device does not meet the access control restrictions |
| Windows |
4821 |
A Kerberos service ticket was denied because the user, device, or both does not meet the access control restrictions |
| Windows |
4822 |
NTLM authentication failed because the account was a member of the Protected User group |
| Windows |
4823 |
NTLM authentication failed because access control restrictions are required |
| Windows |
4824 |
Kerberos preauthentication by using DES or RC4 failed because the account was a member of the Protected User group |
| Windows |
4825 |
A user was denied the access to Remote Desktop. By default, users are allowed to connect only if they are members of the Remote Desktop Users group or Administrators group |
| Windows |
4826 |
Boot Configuration Data loaded |
| Windows |
4830 |
SID History was removed from an account |
| Windows |
4864 |
A namespace collision was detected |
| Windows |
4865 |
A trusted forest information entry was added |
| Windows |
4866 |
A trusted forest information entry was removed |
| Windows |
4867 |
A trusted forest information entry was modified |
| Windows |
4868 |
The certificate manager denied a pending certificate request |
| Windows |
4869 |
Certificate Services received a resubmitted certificate request |
| Windows |
4870 |
Certificate Services revoked a certificate |
| Windows |
4871 |
Certificate Services received a request to publish the certificate revocation list (CRL) |
| Windows |
4872 |
Certificate Services published the certificate revocation list (CRL) |
| Windows |
4873 |
A certificate request extension changed |
| Windows |
4874 |
One or more certificate request attributes changed. |
| Windows |
4875 |
Certificate Services received a request to shut down |
| Windows |
4876 |
Certificate Services backup started |
| Windows |
4877 |
Certificate Services backup completed |
| Windows |
4878 |
Certificate Services restore started |
| Windows |
4879 |
Certificate Services restore completed |
| Windows |
4880 |
Certificate Services started |
| Windows |
4881 |
Certificate Services stopped |
| Windows |
4882 |
The security permissions for Certificate Services changed |
| Windows |
4883 |
Certificate Services retrieved an archived key |
| Windows |
4884 |
Certificate Services imported a certificate into its database |
| Windows |
4885 |
The audit filter for Certificate Services changed |
| Windows |
4886 |
Certificate Services received a certificate request |
| Windows |
4887 |
Certificate Services approved a certificate request and issued a certificate |
| Windows |
4888 |
Certificate Services denied a certificate request |
| Windows |
4889 |
Certificate Services set the status of a certificate request to pending |
| Windows |
4890 |
The certificate manager settings for Certificate Services changed. |
| Windows |
4891 |
A configuration entry changed in Certificate Services |
| Windows |
4892 |
A property of Certificate Services changed |
| Windows |
4893 |
Certificate Services archived a key |
| Windows |
4894 |
Certificate Services imported and archived a key |
| Windows |
4895 |
Certificate Services published the CA certificate to Active Directory Domain Services |
| Windows |
4896 |
One or more rows have been deleted from the certificate database |
| Windows |
4897 |
Role separation enabled |
| Windows |
4898 |
Certificate Services loaded a template |
| Windows |
4899 |
A Certificate Services template was updated |
| Windows |
4900 |
Certificate Services template security was updated |
| Windows |
4902 |
The Per-user audit policy table was created |
| Windows |
4904 |
An attempt was made to register a security event source |
| Windows |
4905 |
An attempt was made to unregister a security event source |
| Windows |
4906 |
The CrashOnAuditFail value has changed |
| Windows |
4907 |
Auditing settings on object were changed |
| Windows |
4908 |
Special Groups Logon table modified |
| Windows |
4909 |
The local policy settings for the TBS were changed |
| Windows |
4910 |
The group policy settings for the TBS were changed |
| Windows |
4911 |
Resource attributes of the object were changed |
| Windows |
4912 |
Per User Audit Policy was changed |
| Windows |
4913 |
Central Access Policy on the object was changed |
| Windows |
4928 |
An Active Directory replica source naming context was established |
| Windows |
4929 |
An Active Directory replica source naming context was removed |
| Windows |
4930 |
An Active Directory replica source naming context was modified |
| Windows |
4931 |
An Active Directory replica destination naming context was modified |
| Windows |
4932 |
Synchronization of a replica of an Active Directory naming context has begun |
| Windows |
4933 |
Synchronization of a replica of an Active Directory naming context has ended |
| Windows |
4934 |
Attributes of an Active Directory object were replicated |
| Windows |
4935 |
Replication failure begins |
| Windows |
4936 |
Replication failure ends |
| Windows |
4937 |
A lingering object was removed from a replica |
| Windows |
4944 |
The following policy was active when the Windows Firewall started |
| Windows |
4945 |
A rule was listed when the Windows Firewall started |
| Windows |
4946 |
A change has been made to Windows Firewall exception list. A rule was added |
| Windows |
4947 |
A change has been made to Windows Firewall exception list. A rule was modified |
| Windows |
4948 |
A change has been made to Windows Firewall exception list. A rule was deleted |
| Windows |
4949 |
Windows Firewall settings were restored to the default values |
| Windows |
4950 |
A Windows Firewall setting has changed |
| Windows |
4951 |
A rule has been ignored because its major version number was not recognized by Windows Firewall |
| Windows |
4952 |
Parts of a rule have been ignored because its minor version number was not recognized by Windows Firewall |
| Windows |
4953 |
A rule has been ignored by Windows Firewall because it could not parse the rule |
| Windows |
4954 |
Windows Firewall Group Policy settings has changed. The new settings have been applied |
| Windows |
4956 |
Windows Firewall has changed the active profile |
| Windows |
4957 |
Windows Firewall did not apply the following rule |
| Windows |
4958 |
Windows Firewall did not apply the following rule because the rule referred to items not configured on this computer |
| Windows |
4960 |
IPsec dropped an inbound packet that failed an integrity check |
| Windows |
4961 |
IPsec dropped an inbound packet that failed a replay check |
| Windows |
4962 |
IPsec dropped an inbound packet that failed a replay check |
| Windows |
4963 |
IPsec dropped an inbound clear text packet that should have been secured |
| Windows |
4964 |
Special groups have been assigned to a new logon |
| Windows |
4965 |
IPsec received a packet from a remote computer with an incorrect Security Parameter Index (SPI). |
| Windows |
4976 |
During Main Mode negotiation, IPsec received an invalid negotiation packet. |
| Windows |
4977 |
During Quick Mode negotiation, IPsec received an invalid negotiation packet. |
| Windows |
4978 |
During Extended Mode negotiation, IPsec received an invalid negotiation packet. |
| Windows |
4979 |
IPsec Main Mode and Extended Mode security associations were established. |
| Windows |
4980 |
IPsec Main Mode and Extended Mode security associations were established |
| Windows |
4981 |
IPsec Main Mode and Extended Mode security associations were established |
| Windows |
4982 |
IPsec Main Mode and Extended Mode security associations were established |
| Windows |
4983 |
An IPsec Extended Mode negotiation failed |
| Windows |
4984 |
An IPsec Extended Mode negotiation failed |
| Windows |
4985 |
The state of a transaction has changed |
| Windows |
5024 |
The Windows Firewall Service has started successfully |
| Windows |
5025 |
The Windows Firewall Service has been stopped |
| Windows |
5027 |
The Windows Firewall Service was unable to retrieve the security policy from the local storage |
| Windows |
5028 |
The Windows Firewall Service was unable to parse the new security policy. |
| Windows |
5029 |
The Windows Firewall Service failed to initialize the driver |
| Windows |
5030 |
The Windows Firewall Service failed to start |
| Windows |
5031 |
The Windows Firewall Service blocked an application from accepting incoming connections on the network. |
| Windows |
5032 |
Windows Firewall was unable to notify the user that it blocked an application from accepting incoming connections on the network |
| Windows |
5033 |
The Windows Firewall Driver has started successfully |
| Windows |
5034 |
The Windows Firewall Driver has been stopped |
| Windows |
5035 |
The Windows Firewall Driver failed to start |
| Windows |
5037 |
The Windows Firewall Driver detected critical runtime error. Terminating |
| Windows |
5038 |
Code integrity determined that the image hash of a file is not valid |
| Windows |
5039 |
A registry key was virtualized. |
| Windows |
5040 |
A change has been made to IPsec settings. An Authentication Set was added. |
| Windows |
5041 |
A change has been made to IPsec settings. An Authentication Set was modified |
| Windows |
5042 |
A change has been made to IPsec settings. An Authentication Set was deleted |
| Windows |
5043 |
A change has been made to IPsec settings. A Connection Security Rule was added |
| Windows |
5044 |
A change has been made to IPsec settings. A Connection Security Rule was modified |
| Windows |
5045 |
A change has been made to IPsec settings. A Connection Security Rule was deleted |
| Windows |
5046 |
A change has been made to IPsec settings. A Crypto Set was added |
| Windows |
5047 |
A change has been made to IPsec settings. A Crypto Set was modified |
| Windows |
5048 |
A change has been made to IPsec settings. A Crypto Set was deleted |
| Windows |
5049 |
An IPsec Security Association was deleted |
| Windows |
5050 |
An attempt to programmatically disable the Windows Firewall using a call to INetFwProfile.FirewallEnabled(FALSE |
| Windows |
5051 |
A file was virtualized |
| Windows |
5056 |
A cryptographic self test was performed |
| Windows |
5057 |
A cryptographic primitive operation failed |
| Windows |
5058 |
Key file operation |
| Windows |
5059 |
Key migration operation |
| Windows |
5060 |
Verification operation failed |
| Windows |
5061 |
Cryptographic operation |
| Windows |
5062 |
A kernel-mode cryptographic self test was performed |
| Windows |
5063 |
A cryptographic provider operation was attempted |
| Windows |
5064 |
A cryptographic context operation was attempted |
| Windows |
5065 |
A cryptographic context modification was attempted |
| Windows |
5066 |
A cryptographic function operation was attempted |
| Windows |
5067 |
A cryptographic function modification was attempted |
| Windows |
5068 |
A cryptographic function provider operation was attempted |
| Windows |
5069 |
A cryptographic function property operation was attempted |
| Windows |
5070 |
A cryptographic function property operation was attempted |
| Windows |
5071 |
Key access denied by Microsoft key distribution service |
| Windows |
5120 |
OCSP Responder Service Started |
| Windows |
5121 |
OCSP Responder Service Stopped |
| Windows |
5122 |
A Configuration entry changed in the OCSP Responder Service |
| Windows |
5123 |
A configuration entry changed in the OCSP Responder Service |
| Windows |
5124 |
A security setting was updated on OCSP Responder Service |
| Windows |
5125 |
A request was submitted to OCSP Responder Service |
| Windows |
5126 |
Signing Certificate was automatically updated by the OCSP Responder Service |
| Windows |
5127 |
The OCSP Revocation Provider successfully updated the revocation information |
| Windows |
5136 |
A directory service object was modified |
| Windows |
5137 |
A directory service object was created |
| Windows |
5138 |
A directory service object was undeleted |
| Windows |
5139 |
A directory service object was moved |
| Windows |
5140 |
A network share object was accessed |
| Windows |
5141 |
A directory service object was deleted |
| Windows |
5142 |
A network share object was added. |
| Windows |
5143 |
A network share object was modified |
| Windows |
5144 |
A network share object was deleted. |
| Windows |
5145 |
A network share object was checked to see whether client can be granted desired access |
| Windows |
5146 |
The Windows Filtering Platform has blocked a packet |
| Windows |
5147 |
A more restrictive Windows Filtering Platform filter has blocked a packet |
| Windows |
5148 |
The Windows Filtering Platform has detected a DoS attack and entered a defensive mode; packets associated with this attack will be discarded. |
| Windows |
5149 |
The DoS attack has subsided and normal processing is being resumed. |
| Windows |
5150 |
The Windows Filtering Platform has blocked a packet. |
| Windows |
5151 |
A more restrictive Windows Filtering Platform filter has blocked a packet. |
| Windows |
5152 |
The Windows Filtering Platform blocked a packet |
| Windows |
5153 |
A more restrictive Windows Filtering Platform filter has blocked a packet |
| Windows |
5154 |
The Windows Filtering Platform has permitted an application or service to listen on a port for incoming connections |
| Windows |
5155 |
The Windows Filtering Platform has blocked an application or service from listening on a port for incoming connections |
| Windows |
5156 |
The Windows Filtering Platform has allowed a connection |
| Windows |
5157 |
The Windows Filtering Platform has blocked a connection |
| Windows |
5158 |
The Windows Filtering Platform has permitted a bind to a local port |
| Windows |
5159 |
The Windows Filtering Platform has blocked a bind to a local port |
| Windows |
5168 |
Spn check for SMB/SMB2 fails. |
| Windows |
5169 |
A directory service object was modified |
| Windows |
5170 |
A directory service object was modified during a background cleanup task |
| Windows |
5376 |
Credential Manager credentials were backed up |
| Windows |
5377 |
Credential Manager credentials were restored from a backup |
| Windows |
5378 |
The requested credentials delegation was disallowed by policy |
| Windows |
5379 |
Credential Manager credentials were read |
| Windows |
5380 |
Vault Find Credential |
| Windows |
5381 |
Vault credentials were read |
| Windows |
5382 |
Vault credentials were read |
| Windows |
5440 |
The following callout was present when the Windows Filtering Platform Base Filtering Engine started |
| Windows |
5441 |
The following filter was present when the Windows Filtering Platform Base Filtering Engine started |
| Windows |
5442 |
The following provider was present when the Windows Filtering Platform Base Filtering Engine started |
| Windows |
5443 |
The following provider context was present when the Windows Filtering Platform Base Filtering Engine started |
| Windows |
5444 |
The following sub-layer was present when the Windows Filtering Platform Base Filtering Engine started |
| Windows |
5446 |
A Windows Filtering Platform callout has been changed |
| Windows |
5447 |
A Windows Filtering Platform filter has been changed |
| Windows |
5448 |
A Windows Filtering Platform provider has been changed |
| Windows |
5449 |
A Windows Filtering Platform provider context has been changed |
| Windows |
5450 |
A Windows Filtering Platform sub-layer has been changed |
| Windows |
5451 |
An IPsec Quick Mode security association was established |
| Windows |
5452 |
An IPsec Quick Mode security association ended |
| Windows |
5453 |
An IPsec negotiation with a remote computer failed because the IKE and AuthIP IPsec Keying Modules (IKEEXT) service is not started |
| Windows |
5456 |
PAStore Engine applied Active Directory storage IPsec policy on the computer |
| Windows |
5457 |
PAStore Engine failed to apply Active Directory storage IPsec policy on the computer |
| Windows |
5458 |
PAStore Engine applied locally cached copy of Active Directory storage IPsec policy on the computer |
| Windows |
5459 |
PAStore Engine failed to apply locally cached copy of Active Directory storage IPsec policy on the computer |
| Windows |
5460 |
PAStore Engine applied local registry storage IPsec policy on the computer |
| Windows |
5461 |
PAStore Engine failed to apply local registry storage IPsec policy on the computer |
| Windows |
5462 |
PAStore Engine failed to apply some rules of the active IPsec policy on the computer |
| Windows |
5463 |
PAStore Engine polled for changes to the active IPsec policy and detected no changes |
| Windows |
5464 |
PAStore Engine polled for changes to the active IPsec policy, detected changes, and applied them to IPsec Services |
| Windows |
5465 |
PAStore Engine received a control for forced reloading of IPsec policy and processed the control successfully |
| Windows |
5466 |
PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory cannot be reached, and will use the cached copy of the Active Directory IPsec policy instead |
| Windows |
5467 |
PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory can be reached, and found no changes to the policy |
| Windows |
5468 |
PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory can be reached, found changes to the policy, and applied those changes |
| Windows |
5471 |
PAStore Engine loaded local storage IPsec policy on the computer |
| Windows |
5472 |
PAStore Engine failed to load local storage IPsec policy on the computer |
| Windows |
5473 |
PAStore Engine loaded directory storage IPsec policy on the computer |
| Windows |
5474 |
PAStore Engine failed to load directory storage IPsec policy on the computer |
| Windows |
5477 |
PAStore Engine failed to add quick mode filter |
| Windows |
5478 |
IPsec Services has started successfully |
| Windows |
5479 |
IPsec Services has been shut down successfully |
| Windows |
5480 |
IPsec Services failed to get the complete list of network interfaces on the computer |
| Windows |
5483 |
IPsec Services failed to initialize RPC server. IPsec Services could not be started |
| Windows |
5484 |
IPsec Services has experienced a critical failure and has been shut down |
| Windows |
5485 |
IPsec Services failed to process some IPsec filters on a plug-and-play event for network interfaces |
| Windows |
5632 |
A request was made to authenticate to a wireless network |
| Windows |
5633 |
A request was made to authenticate to a wired network |
| Windows |
5712 |
A Remote Procedure Call (RPC) was attempted |
| Windows |
5888 |
An object in the COM+ Catalog was modified |
| Windows |
5889 |
An object was deleted from the COM+ Catalog |
| Windows |
5890 |
An object was added to the COM+ Catalog |
| Windows |
6144 |
Security policy in the group policy objects has been applied successfully |
| Windows |
6145 |
One or more errors occured while processing security policy in the group policy objects |
| Windows |
6272 |
Network Policy Server granted access to a user |
| Windows |
6273 |
Network Policy Server denied access to a user |
| Windows |
6274 |
Network Policy Server discarded the request for a user |
| Windows |
6275 |
Network Policy Server discarded the accounting request for a user |
| Windows |
6276 |
Network Policy Server quarantined a user |
| Windows |
6277 |
Network Policy Server granted access to a user but put it on probation because the host did not meet the defined health policy |
| Windows |
6278 |
Network Policy Server granted full access to a user because the host met the defined health policy |
| Windows |
6279 |
Network Policy Server locked the user account due to repeated failed authentication attempts |
| Windows |
6280 |
Network Policy Server unlocked the user account |
| Windows |
6281 |
Code Integrity determined that the page hashes of an image file are not valid… |
| Windows |
6400 |
BranchCache: Received an incorrectly formatted response while discovering availability of content. |
| Windows |
6401 |
BranchCache: Received invalid data from a peer. Data discarded. |
| Windows |
6402 |
BranchCache: The message to the hosted cache offering it data is incorrectly formatted. |
| Windows |
6403 |
BranchCache: The hosted cache sent an incorrectly formatted response to the client’s message to offer it data. |
| Windows |
6404 |
BranchCache: Hosted cache could not be authenticated using the provisioned SSL certificate. |
| Windows |
6405 |
BranchCache: %2 instance(s) of event id %1 occurred. |
| Windows |
6406 |
%1 registered to Windows Firewall to control filtering for the following: |
| Windows |
6407 |
%1 |
| Windows |
6408 |
Registered product %1 failed and Windows Firewall is now controlling the filtering for %2. |
| Windows |
6409 |
BranchCache: A service connection point object could not be parsed |
| Windows |
6410 |
Code integrity determined that a file does not meet the security requirements to load into a process. This could be due to the use of shared sections or other issues |
| Windows |
6416 |
A new external device was recognized by the system. |
| Windows |
6417 |
The FIPS mode crypto selftests succeeded |
| Windows |
6418 |
The FIPS mode crypto selftests failed |
| Windows |
6419 |
A request was made to disable a device |
| Windows |
6420 |
A device was disabled |
| Windows |
6421 |
A request was made to enable a device |
| Windows |
6422 |
A device was enabled |
| Windows |
6423 |
The installation of this device is forbidden by system policy |
| Windows |
6424 |
The installation of this device was allowed, after having previously been forbidden by policy |
| Windows |
8191 |
Highest System-Defined Audit Message Value |
This article serves as a quick reference for Windows Security Log event IDs.
Windows Security Log Reference
To Open the security log run
Then in the console tree, expand Windows Logs, and then click Security. The results pane lists individual security events.
User Account Changes
| Event ID | Description |
|---|---|
| 4720 | Created |
| 4722 | Enabled |
| 4723 | User changed own password |
| 4724 | Privileged User changed this user’s password |
| 4725 | Disabled |
| 4726 | Deleted |
| 4738 | Changed |
| 4740 | Locked out |
| 4767 | Unlocked |
| 4781 | Name change |
Domain Controller Authentication Events
| Event ID | Description |
|---|---|
| 4768 | A Kerberos authentication ticket (TGT) was requested |
| 4771 | Kerberos pre-authentication failed |
| 4820 | A Kerberos TGT was denied because the device does not meet the access control restrictions |
Logon Session Events (Correlate by Logon ID)
| Event ID | Description |
|---|---|
| 4624 | Successful logon |
| 4647 | User initiated logoff |
| 4625 | Logon failure {See Logon Failure Codes) |
| 4778 | Remote desktop session reconnected |
| 4779 | Remote desktop session disconnected |
| 4800 | Workstation locked |
| 4801 | Workstation unlocked |
| 4802 | Screen saver invoked |
| 4803 | Screen saver dismissed |
Logon Types
| Type ID | Description |
|---|---|
| 2 | Interactive |
| 3 | Network (i.e. mapped drive) |
| 4 | Batch |
| 5 | Service (service startup) |
| 7 | Unlock |
| 8 | Network Cleartext |
| 10 | Remote Desktop |
| 11 | Logon with cached credentials |
Security Group Changes
| Action | Local | Global | Universal |
|---|---|---|---|
| Created | 4731 | 4727 | 4754 |
| Changed | 4735 | 4737 | 4755 |
| Deleted | 4734 | 4730 | 4758 |
| Member Added | 4732 | 4728 | 4756 |
| Member Removed | 4733 | 4729 | 4757 |
Distribution Group Changes
| Action | Local | Global | Universal |
|---|---|---|---|
| Created | 4744 | 4749 | 4759 |
| Changed | 4745 | 4750 | 4760 |
| Deleted | 4748 | 4753 | 4763 |
| Member Added | 4746 | 4751 | 4761 |
| Member Removed | 4747 | 4752 | 4762 |
In Microsoft Windows, the Security Log is a log that records login/logout activity as well as other security-related events as defined by the system’s audit policy. Administrators can set up Windows to record operating system activity in the Security Log by using auditing.
Following are the security event ids with the activities.
Event ID
Event Log
1100
The event logging service has shut down
1101
Audit events have been dropped by the transport.
1102
The audit log was cleared
1104
The security Log is now full
1105
Event log automatic backup
1108
The event logging service encountered an error
4608
Windows is starting up
4609
Windows is shutting down
4610
An authentication package has been loaded by the Local Security Authority
4611
A trusted logon process has been registered with the Local Security Authority
4612
Internal resources allocated for the queuing of audit messages have been exhausted, leading to the loss of some audits.
4614
A notification package has been loaded by the Security Account Manager.
4615
Invalid use of LPC port
4616
The system time was changed.
4618
A monitored security event pattern has occurred
4621
Administrator recovered system from CrashOnAuditFail
4622
A security package has been loaded by the Local Security Authority.
4624
An account was successfully logged on
4625
An account failed to log on
4626
User/Device claims information
4627
Group membership information.
4634
An account was logged off
4646
IKE DoS-prevention mode started
4647
User initiated logoff
4648
A logon was attempted using explicit credentials
4649
A replay attack was detected
4650
An IPsec Main Mode security association was established
4651
An IPsec Main Mode security association was established
4652
An IPsec Main Mode negotiation failed
4653
An IPsec Main Mode negotiation failed
4654
An IPsec Quick Mode negotiation failed
4655
An IPsec Main Mode security association ended
4656
A handle to an object was requested
4657
A registry value was modified
4658
The handle to an object was closed
4659
A handle to an object was requested with intent to delete
4660
An object was deleted
4661
A handle to an object was requested
4662
An operation was performed on an object
4663
An attempt was made to access an object
4664
An attempt was made to create a hard link
4665
An attempt was made to create an application client context.
4666
An application attempted an operation
4667
An application client context was deleted
4668
An application was initialized
4670
Permissions on an object were changed
4671
An application attempted to access a blocked ordinal through the TBS
4672
Special privileges assigned to new logon
4673
A privileged service was called
4674
An operation was attempted on a privileged object
4675
SIDs were filtered
4688
A new process has been created
4689
A process has exited
4690
An attempt was made to duplicate a handle to an object
4691
Indirect access to an object was requested
4692
Backup of data protection master key was attempted
4693
Recovery of data protection master key was attempted
4694
Protection of auditable protected data was attempted
4695
Unprotection of auditable protected data was attempted
4696
A primary token was assigned to process
4697
A service was installed in the system
4698
A scheduled task was created
4699
A scheduled task was deleted
4700
A scheduled task was enabled
4701
A scheduled task was disabled
4702
A scheduled task was updated
4703
A token right was adjusted
4704
A user right was assigned
4705
A user right was removed
4706
A new trust was created to a domain
4707
A trust to a domain was removed
4709
IPsec Services was started
4710
IPsec Services was disabled
4711
PAStore Engine (1%)
4712
IPsec Services encountered a potentially serious failure
4713
Kerberos policy was changed
4714
Encrypted data recovery policy was changed
4715
The audit policy (SACL) on an object was changed
4716
Trusted domain information was modified
4717
System security access was granted to an account
4718
System security access was removed from an account
4719
System audit policy was changed
4720
A user account was created
4722
A user account was enabled
4723
An attempt was made to change an account’s password
4724
An attempt was made to reset an accounts password
4725
A user account was disabled
4726
A user account was deleted
4727
A security-enabled global group was created
4728
A member was added to a security-enabled global group
4729
A member was removed from a security-enabled global group
4730
A security-enabled global group was deleted
4731
A security-enabled local group was created
4732
A member was added to a security-enabled local group
4733
A member was removed from a security-enabled local group
4734
A security-enabled local group was deleted
4735
A security-enabled local group was changed
4737
A security-enabled global group was changed
4738
A user account was changed
4739
Domain Policy was changed
4740
A user account was locked out
4741
A computer account was created
4742
A computer account was changed
4743
A computer account was deleted
4744
A security-disabled local group was created
4745
A security-disabled local group was changed
4746
A member was added to a security-disabled local group
4747
A member was removed from a security-disabled local group
4748
A security-disabled local group was deleted
4749
A security-disabled global group was created
4750
A security-disabled global group was changed
4751
A member was added to a security-disabled global group
4752
A member was removed from a security-disabled global group
4753
A security-disabled global group was deleted
4754
A security-enabled universal group was created
4755
A security-enabled universal group was changed
4756
A member was added to a security-enabled universal group
4757
A member was removed from a security-enabled universal group
4758
A security-enabled universal group was deleted
4759
A security-disabled universal group was created
4760
A security-disabled universal group was changed
4761
A member was added to a security-disabled universal group
4762
A member was removed from a security-disabled universal group
4763
A security-disabled universal group was deleted
4764
A groups type was changed
4765
SID History was added to an account
4766
An attempt to add SID History to an account failed
4767
A user account was unlocked
4768
A Kerberos authentication ticket (TGT) was requested
4769
A Kerberos service ticket was requested
4770
A Kerberos service ticket was renewed
4771
Kerberos pre-authentication failed
4772
A Kerberos authentication ticket request failed
4773
A Kerberos service ticket request failed
4774
An account was mapped for logon
4775
An account could not be mapped for logon
4776
The domain controller attempted to validate the credentials for an account
4777
The domain controller failed to validate the credentials for an account
4778
A session was reconnected to a Window Station
4779
A session was disconnected from a Window Station
4780
The ACL was set on accounts which are members of administrators groups
4781
The name of an account was changed
4782
The password hash an account was accessed
4783
A basic application group was created
4784
A basic application group was changed
4785
A member was added to a basic application group
4786
A member was removed from a basic application group
4787
A non-member was added to a basic application group
4788
A non-member was removed from a basic application group..
4789
A basic application group was deleted
4790
An LDAP query group was created
4791
A basic application group was changed
4792
An LDAP query group was deleted
4793
The Password Policy Checking API was called
4794
An attempt was made to set the Directory Services Restore Mode administrator password
4797
An attempt was made to query the existence of a blank password for an account
4798
A user’s local group membership was enumerated.
4799
A security-enabled local group membership was enumerated
4800
The workstation was locked
4801
The workstation was unlocked
4802
The screen saver was invoked
4803
The screen saver was dismissed
4816
RPC detected an integrity violation while decrypting an incoming message
4817
Auditing settings on object were changed.
4818
Proposed Central Access Policy does not grant the same access permissions as the current Central Access Policy
4819
Central Access Policies on the machine have been changed
4820
A Kerberos Ticket-granting-ticket (TGT) was denied because the device does not meet the access control restrictions
4821
A Kerberos service ticket was denied because the user, device, or both does not meet the access control restrictions
4822
NTLM authentication failed because the account was a member of the Protected User group
4823
NTLM authentication failed because access control restrictions are required
4824
Kerberos preauthentication by using DES or RC4 failed because the account was a member of the Protected User group
4825
A user was denied the access to Remote Desktop. By default, users are allowed to connect only if they are members of the Remote Desktop Users group or Administrators group
4826
Boot Configuration Data loaded
4830
SID History was removed from an account
4864
A namespace collision was detected
4865
A trusted forest information entry was added
4866
A trusted forest information entry was removed
4867
A trusted forest information entry was modified
4868
The certificate manager denied a pending certificate request
4869
Certificate Services received a resubmitted certificate request
4870
Certificate Services revoked a certificate
4871
Certificate Services received a request to publish the certificate revocation list (CRL)
4872
Certificate Services published the certificate revocation list (CRL)
4873
A certificate request extension changed
4874
One or more certificate request attributes changed.
4875
Certificate Services received a request to shut down
4876
Certificate Services backup started
4877
Certificate Services backup completed
4878
Certificate Services restore started
4879
Certificate Services restore completed
4880
Certificate Services started
4881
Certificate Services stopped
4882
The security permissions for Certificate Services changed
4883
Certificate Services retrieved an archived key
4884
Certificate Services imported a certificate into its database
4885
The audit filter for Certificate Services changed
4886
Certificate Services received a certificate request
4887
Certificate Services approved a certificate request and issued a certificate
4888
Certificate Services denied a certificate request
4889
Certificate Services set the status of a certificate request to pending
4890
The certificate manager settings for Certificate Services changed.
4891
A configuration entry changed in Certificate Services
4892
A property of Certificate Services changed
4893
Certificate Services archived a key
4894
Certificate Services imported and archived a key
4895
Certificate Services published the CA certificate to Active Directory Domain Services
4896
One or more rows have been deleted from the certificate database
4897
Role separation enabled
4898
Certificate Services loaded a template
4899
A Certificate Services template was updated
4900
Certificate Services template security was updated
4902
The Per-user audit policy table was created
4904
An attempt was made to register a security event source
4905
An attempt was made to unregister a security event source
4906
The CrashOnAuditFail value has changed
4907
Auditing settings on object were changed
4908
Special Groups Logon table modified
4909
The local policy settings for the TBS were changed
4910
The group policy settings for the TBS were changed
4911
Resource attributes of the object were changed
4912
Per User Audit Policy was changed
4913
Central Access Policy on the object was changed
4928
An Active Directory replica source naming context was established
4929
An Active Directory replica source naming context was removed
4930
An Active Directory replica source naming context was modified
4931
An Active Directory replica destination naming context was modified
4932
Synchronization of a replica of an Active Directory naming context has begun
4933
Synchronization of a replica of an Active Directory naming context has ended
4934
Attributes of an Active Directory object were replicated
4935
Replication failure begins
4936
Replication failure ends
4937
A lingering object was removed from a replica
4944
The following policy was active when the Windows Firewall started
4945
A rule was listed when the Windows Firewall started
4946
A change has been made to Windows Firewall exception list. A rule was added
4947
A change has been made to Windows Firewall exception list. A rule was modified
4948
A change has been made to Windows Firewall exception list. A rule was deleted
4949
Windows Firewall settings were restored to the default values
4950
A Windows Firewall setting has changed
4951
A rule has been ignored because its major version number was not recognized by Windows Firewall
4952
Parts of a rule have been ignored because its minor version number was not recognized by Windows Firewall
4953
A rule has been ignored by Windows Firewall because it could not parse the rule
4954
Windows Firewall Group Policy settings has changed. The new settings have been applied
4956
Windows Firewall has changed the active profile
4957
Windows Firewall did not apply the following rule
4958
Windows Firewall did not apply the following rule because the rule referred to items not configured on this computer
4960
IPsec dropped an inbound packet that failed an integrity check
4961
IPsec dropped an inbound packet that failed a replay check
4962
IPsec dropped an inbound packet that failed a replay check
4963
IPsec dropped an inbound clear text packet that should have been secured
4964
Special groups have been assigned to a new logon
4965
IPsec received a packet from a remote computer with an incorrect Security Parameter Index (SPI).
4976
During Main Mode negotiation, IPsec received an invalid negotiation packet.
4977
During Quick Mode negotiation, IPsec received an invalid negotiation packet.
4978
During Extended Mode negotiation, IPsec received an invalid negotiation packet.
4979
IPsec Main Mode and Extended Mode security associations were established.
4980
IPsec Main Mode and Extended Mode security associations were established
4981
IPsec Main Mode and Extended Mode security associations were established
4982
IPsec Main Mode and Extended Mode security associations were established
4983
An IPsec Extended Mode negotiation failed
4984
An IPsec Extended Mode negotiation failed
4985
The state of a transaction has changed
5024
The Windows Firewall Service has started successfully
5025
The Windows Firewall Service has been stopped
5027
The Windows Firewall Service was unable to retrieve the security policy from the local storage
5028
The Windows Firewall Service was unable to parse the new security policy.
5029
The Windows Firewall Service failed to initialize the driver
5030
The Windows Firewall Service failed to start
5031
The Windows Firewall Service blocked an application from accepting incoming connections on the network.
5032
Windows Firewall was unable to notify the user that it blocked an application from accepting incoming connections on the network
5033
The Windows Firewall Driver has started successfully
5034
The Windows Firewall Driver has been stopped
5035
The Windows Firewall Driver failed to start
5037
The Windows Firewall Driver detected critical runtime error. Terminating
5038
Code integrity determined that the image hash of a file is not valid
5039
A registry key was virtualized.
5040
A change has been made to IPsec settings. An Authentication Set was added.
5041
A change has been made to IPsec settings. An Authentication Set was modified
5042
A change has been made to IPsec settings. An Authentication Set was deleted
5043
A change has been made to IPsec settings. A Connection Security Rule was added
5044
A change has been made to IPsec settings. A Connection Security Rule was modified
5045
A change has been made to IPsec settings. A Connection Security Rule was deleted
5046
A change has been made to IPsec settings. A Crypto Set was added
5047
A change has been made to IPsec settings. A Crypto Set was modified
5048
A change has been made to IPsec settings. A Crypto Set was deleted
5049
An IPsec Security Association was deleted
5050
An attempt to programmatically disable the Windows Firewall using a call to INetFwProfile.FirewallEnabled(FALSE
5051
A file was virtualized
5056
A cryptographic self test was performed
5057
A cryptographic primitive operation failed
5058
Key file operation
5059
Key migration operation
5060
Verification operation failed
5061
Cryptographic operation
5062
A kernel-mode cryptographic self test was performed
5063
A cryptographic provider operation was attempted
5064
A cryptographic context operation was attempted
5065
A cryptographic context modification was attempted
5066
A cryptographic function operation was attempted
5067
A cryptographic function modification was attempted
5068
A cryptographic function provider operation was attempted
5069
A cryptographic function property operation was attempted
5070
A cryptographic function property operation was attempted
5071
Key access denied by Microsoft key distribution service
5120
OCSP Responder Service Started
5121
OCSP Responder Service Stopped
5122
A Configuration entry changed in the OCSP Responder Service
5123
A configuration entry changed in the OCSP Responder Service
5124
A security setting was updated on OCSP Responder Service
5125
A request was submitted to OCSP Responder Service
5126
Signing Certificate was automatically updated by the OCSP Responder Service
5127
The OCSP Revocation Provider successfully updated the revocation information
5136
A directory service object was modified
5137
A directory service object was created
5138
A directory service object was undeleted
5139
A directory service object was moved
5140
A network share object was accessed
5141
A directory service object was deleted
5142
A network share object was added.
5143
A network share object was modified
5144
A network share object was deleted.
5145
A network share object was checked to see whether client can be granted desired access
5146
The Windows Filtering Platform has blocked a packet
5147
A more restrictive Windows Filtering Platform filter has blocked a packet
5148
The Windows Filtering Platform has detected a DoS attack and entered a defensive mode; packets associated with this attack will be discarded.
5149
The DoS attack has subsided and normal processing is being resumed.
5150
The Windows Filtering Platform has blocked a packet.
5151
A more restrictive Windows Filtering Platform filter has blocked a packet.
5152
The Windows Filtering Platform blocked a packet
5153
A more restrictive Windows Filtering Platform filter has blocked a packet
5154
The Windows Filtering Platform has permitted an application or service to listen on a port for incoming connections
5155
The Windows Filtering Platform has blocked an application or service from listening on a port for incoming connections
5156
The Windows Filtering Platform has allowed a connection
5157
The Windows Filtering Platform has blocked a connection
5158
The Windows Filtering Platform has permitted a bind to a local port
5159
The Windows Filtering Platform has blocked a bind to a local port
5168
Spn check for SMB/SMB2 fails.
5169
A directory service object was modified
5170
A directory service object was modified during a background cleanup task
5376
Credential Manager credentials were backed up
5377
Credential Manager credentials were restored from a backup
5378
The requested credentials delegation was disallowed by policy
5379
Credential Manager credentials were read
5380
Vault Find Credential
5381
Vault credentials were read
5382
Vault credentials were read
5440
The following callout was present when the Windows Filtering Platform Base Filtering Engine started
5441
The following filter was present when the Windows Filtering Platform Base Filtering Engine started
5442
The following provider was present when the Windows Filtering Platform Base Filtering Engine started
5443
The following provider context was present when the Windows Filtering Platform Base Filtering Engine started
5444
The following sub-layer was present when the Windows Filtering Platform Base Filtering Engine started
5446
A Windows Filtering Platform callout has been changed
5447
A Windows Filtering Platform filter has been changed
5448
A Windows Filtering Platform provider has been changed
5449
A Windows Filtering Platform provider context has been changed
5450
A Windows Filtering Platform sub-layer has been changed
5451
An IPsec Quick Mode security association was established
5452
An IPsec Quick Mode security association ended
5453
An IPsec negotiation with a remote computer failed because the IKE and AuthIP IPsec Keying Modules (IKEEXT) service is not started
5456
PAStore Engine applied Active Directory storage IPsec policy on the computer
5457
PAStore Engine failed to apply Active Directory storage IPsec policy on the computer
5458
PAStore Engine applied locally cached copy of Active Directory storage IPsec policy on the computer
5459
PAStore Engine failed to apply locally cached copy of Active Directory storage IPsec policy on the computer
5460
PAStore Engine applied local registry storage IPsec policy on the computer
5461
PAStore Engine failed to apply local registry storage IPsec policy on the computer
5462
PAStore Engine failed to apply some rules of the active IPsec policy on the computer
5463
PAStore Engine polled for changes to the active IPsec policy and detected no changes
5464
PAStore Engine polled for changes to the active IPsec policy, detected changes, and applied them to IPsec Services
5465
PAStore Engine received a control for forced reloading of IPsec policy and processed the control successfully
5466
PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory cannot be reached, and will use the cached copy of the Active Directory IPsec policy instead
5467
PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory can be reached, and found no changes to the policy
5468
PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory can be reached, found changes to the policy, and applied those changes
5471
PAStore Engine loaded local storage IPsec policy on the computer
5472
PAStore Engine failed to load local storage IPsec policy on the computer
5473
PAStore Engine loaded directory storage IPsec policy on the computer
5474
PAStore Engine failed to load directory storage IPsec policy on the computer
5477
PAStore Engine failed to add quick mode filter
5478
IPsec Services has started successfully
5479
IPsec Services has been shut down successfully
5480
IPsec Services failed to get the complete list of network interfaces on the computer
5483
IPsec Services failed to initialize RPC server. IPsec Services could not be started
5484
IPsec Services has experienced a critical failure and has been shut down
5485
IPsec Services failed to process some IPsec filters on a plug-and-play event for network interfaces
5632
A request was made to authenticate to a wireless network
5633
A request was made to authenticate to a wired network
5712
A Remote Procedure Call (RPC) was attempted
5888
An object in the COM+ Catalog was modified
5889
An object was deleted from the COM+ Catalog
5890
An object was added to the COM+ Catalog
6144
Security policy in the group policy objects has been applied successfully
6145
One or more errors occured while processing security policy in the group policy objects
6272
Network Policy Server granted access to a user
6273
Network Policy Server denied access to a user
6274
Network Policy Server discarded the request for a user
6275
Network Policy Server discarded the accounting request for a user
6276
Network Policy Server quarantined a user
6277
Network Policy Server granted access to a user but put it on probation because the host did not meet the defined health policy
6278
Network Policy Server granted full access to a user because the host met the defined health policy
6279
Network Policy Server locked the user account due to repeated failed authentication attempts
6280
Network Policy Server unlocked the user account
6281
Code Integrity determined that the page hashes of an image file are not valid…
6400
BranchCache: Received an incorrectly formatted response while discovering availability of content.
6401
BranchCache: Received invalid data from a peer. Data discarded.
6402
BranchCache: The message to the hosted cache offering it data is incorrectly formatted.
6403
BranchCache: The hosted cache sent an incorrectly formatted response to the client’s message to offer it data.
6404
BranchCache: Hosted cache could not be authenticated using the provisioned SSL certificate.
6405
BranchCache: %2 instance(s) of event id %1 occurred.
6406
%1 registered to Windows Firewall to control filtering for the following:
6407
1%
6408
Registered product %1 failed and Windows Firewall is now controlling the filtering for %2.
6409
BranchCache: A service connection point object could not be parsed
6410
Code integrity determined that a file does not meet the security requirements to load into a process. This could be due to the use of shared sections or other issues
6416
A new external device was recognized by the system.
6417
The FIPS mode crypto selftests succeeded
6418
The FIPS mode crypto selftests failed
6419
A request was made to disable a device
6420
A device was disabled
6421
A request was made to enable a device
6422
A device was enabled
6423
The installation of this device is forbidden by system policy
6424
The installation of this device was allowed, after having previously been forbidden by policy
8191
Highest System-Defined Audit Message Value
We can see all the events in Windows Event Viewer. To open Event Viewer simply go to start and search for Event Viewer. There will be four events in an Event Viewer.
In this article, we have covered Security Event which is most important for Audit. Security Event logs will be generated if some process is violated or something is changed which is not recommended in the system and cause some breach of policy in the windows system. These checks are regularly updated in your security event logs.
A security event is a change in how a network or information technology service is used on a regular basis that may indicate that a security policy has been broken or a security measure has failed.
