SNMPWalk
SNMPWalk is a powerful network management tool that allows users to quickly and easily access and monitor information from network devices such as routers, switches, and servers. It allows users to view the SNMP tree of managed devices and then walk through the MIBs to retrieve detailed information about the device.
SnmpWalk allows for convenient and efficient retrieval of multiple pieces of data from SNMP-enabled devices.
Features:
• Support for SNMPv1/v2c/v3: SNMPWalk is compatible with all versions of SNMP and allows users to easily access and monitor information from network devices.
• Comprehensive MIB Viewer: SNMPWalk provides a comprehensive view of all MIBs on the network, making it easy to find the information needed.
• Advanced Filtering: SNMPWalk supports advanced filtering options, which allow users to easily filter out unnecessary information when walking the MIBs.
• Intelligent MIB Navigation: SNMPWalk provides an intelligent navigation system, which allows users to quickly and easily traverse the MIBs and find the desired information.
• Graphical Representation: SNMPWalk provides a graphical representation of the MIBs, which allows users to easily visualize the data and quickly identify relationships between different elements of the network.
• Automated Monitoring: SNMPWalk allows users to automate the monitoring process, so the user can set up periodic scans of the network for any changes or anomalies.
• Flexible Configuration: SNMPWalk provides a flexible configuration system, which allows users to customize the way the tool works to fit their network and their needs.
• Support for Multiple Platforms: SNMPWalk is compatible with multiple platforms and operating systems, such as Windows, Linux, and Mac OS X.
• Easy-to-Use Interface: SNMPWalk has an easy-to-use interface, which allows users to quickly and easily access all the features of the tool.
• Comprehensive Reporting: SNMPWalk provides comprehensive reports on the status of the network, making it easy to identify any issues and take action.
• Scalable Solution: SNMPWalk is a scalable solution, which allows users to easily increase or decrease the number of devices monitored.
• Security: SNMPWalk provides secure access to the network, so users can be sure their data and information is kept safe.
Conclusion
SNMPWalk is a powerful network management tool that allows users to quickly and easily access and monitor information from network devices. It provides a comprehensive view of all MIBs on the network, advanced filtering options, an intelligent navigation system, graphical representations of the MIBs, automated monitoring, flexible configuration, support for multiple platforms, an easy-to-use interface, comprehensive reports, and secure access. SNMPWalk is a scalable solution, which allows users to easily increase or decrease the number of devices monitored.
1. A computer with an operating system that supports SNMP
2. SNMP protocol support and access to an SNMP-enabled device
3. An SNMP-compliant management application
4. An SNMP agent that supports the SNMP protocol and is installed on the device being monitored
5. An SNMP manager with the ability to walk the SNMP MIB tree
6. A network connection between the device and the manager
7. The correct SNMP community string for the device
8. A compatible version of the SNMP protocol
Скриншот программы:

Детали программы:
Версия: 1.02
Дата загрузки: 15 Apr 15
Тип распространения: Бесплатная
Популярность: 1643
Размер: 178 Kb
- Currently 4.25/5
- 1
- 2
- 3
- 4
- 5
Rating: 4.3/5 (Total Votes: 4)
SnmpWalk позволяет обнаружить набор переменных, которые доступны для чтения на определенном устройстве. Вы можете получить полный список или только часть. Анализируя результаты сканирования сетевого устройства, полученного с SnmpWalk вы можете составить список поддерживаемых баз MIB и таким образом, получить полные описания переменных и их возможных значений. Кроме того, документы MIB содержит информацию о SNMP переменных, которые доступны только для записи. После анализа данные, полученные с SnmpWalk от аппаратных или программное обеспечение SNMP источников, вы можете использовать SNMPSET и SnmpGet инструменты, чтобы изменить и получить значения.
15 Apr 15
Поддерживаемые операционные системы
Другие программы разработчика SnmpSoft
Комментарии к SnmpWalk
Популярные программы
SnmpWalk
(Shell Tool) 1.02
SnmpWalk allows you to detect a set of variables that are available for reading on an individual device. You can obtain a full or partial list.
SNMP is a unified protocol for network monitoring and network device management. All active network devices support SNMP.
SnmpWalk needs to be run in the Command Prompt or Powershell. As always, you should do so as Administrator or Elevated.
SnmpWalk allows you to detect a set of variables that are available for reading on an individual device. You can obtain a full list or just part. By analyzing the results of a network device scan obtained with SnmpWalk, you can develop a list of supported MIBs and, in this way, obtain full descriptions of variables and possible values. Besides that, MIB documents contain information about SNMP variables that are available only for writing. After analyzing information retrieved with SnmpWalk from hardware or software SNMP sources, you can use SnmpSet and SnmpGet tools to change and obtain values.
Features:
All available switches are listed in that archive as ReadMe.txt.
Screenshot for SnmpWalk
Top Downloads In Networking
Simple Port Forwarding works with webpages and not directly with your router making it a safe program to use. Supports 52 Languages and 2600+ routers. Portable version also available.
Network Inventory Advisor compiles detailed information about all the computers on your network.
Advanced IP Scanner is a fast, robust, and easy-to-use free IP scanner for Windows.
Wireshark 4.4.6 [ 2025-04-16 15:33:16 | 59-84 MB | Freeware | 11|10|8|7|macOS | 5 ]
Wireshark was designed for quickly capturing then analyzing network packets and displaying detailed information about them.
Look@LAN 2.50 Build 35 [ 2016-10-16 09:26:05 | 2.1 MB | Freeware | Win 10 / 8 / 7 / Vista / XP | 5 ]
Look@Lan is an advanced network monitor that allows you to monitor your net in few clicks.
Tactical Briefings
Comment Rules & Etiquette — We welcome all comments from our readers, but any comment section requires some moderation. Some posts are auto-moderated to reduce spam, including links and swear words. When you make a post, and it does not appear, it went into moderation. We are emailed when posts are marked as spam and respond ASAP. Some posts might be deleted to reduce clutter. Examples include religion, politics, and comments about listing errors (after we fix the problem and upvote your comment). Finally, be nice. Thank you for choosing MajorGeeks.
© 2000-2025 MajorGeeks.com
(because I can never find them…)
I’m not sure exactly why, but the net-snmp folks don’t release the win32 versions of their tools except as source packages. (Update: not sure if this is still true, this page was started years ago.) Since I’m sick of hunting them down, I’ve placed my copy here. So, if you are looking for net-snmp tools (snmpwalk, snmpget, etc) for Windows, you’ve found them below.
Most recent binaries were build from net-snmp-5.9.1 as downloaded on January 1, 2023.
I haven’t been able to get openssl support to build into this version, sorry. Unresolved external when linking. The error I get is:
link.exe netsnmp.lib netsnmpagent.lib netsnmpmibs.lib netsnmptrapd.lib advapi32.lib ws2_32.lib kernel32.lib user32.lib /nologo /subsystem:console /pdb:"../bin/.\release/snmptrapd.pdb" /out:"..\bin\.\release/snmptrapd.exe" /libpath:"../lib/.\release" /libpath:c:/openssl-win32/lib/vc /MANIFEST:EMBED ".\release\snmptrapd.obj" ".\release\winservice.obj" ".\release\winservice.res" netsnmpagent.lib(snmp_vars.obj) : error LNK2019: unresolved external symbol _netsnmp_certs_agent_init referenced in function _init_agent ..\bin\.\release\snmptrapd.exe : fatal error LNK1120: 1 unresolved externals NMAKE : fatal error U1077: '"C:\Program Files (x86)\Microsoft Visual Studio\2019\Community\VC\Tools\MSVC\14.28.29333\bin\HostX86\x86\link.exe"' : return code '0x460' Stop. NMAKE : fatal error U1077: '"C:\Program Files (x86)\Microsoft Visual Studio\2019\Community\VC\Tools\MSVC\14.28.29333\bin\HostX86\x86\nmake.EXE"' : return code '0x2' Stop.
If you can fix that for me let me know. I don’t have a lot of time to throw at it.
If they release a new version at some point and put my versions out of date, remind me via email and I may update them for you.
As required, here is the license.
A note from someone who had a little trouble with the MIB files:
«I just found out where the problem was. When I tried running snmpget I got a message that said it could not find the module. I had to create an environment variable called MIBDIRS = «c:\snmp\mibs» in my case. Thanks for posting the tools.»
Download Directories:
- Version 5.8, 5.9.1 and later on download.elifulkerson.com
- Older versions (no signatures provided)
Direct Download:
net-snmp 5.9.1 statically linked, no openssl
Listing directory https://download.elifulkerson.com/files/net-snmp-compiled-win32/netsnmp-5.9.1-nossl-static:encode_keychange.exe January 01 2023 15:00:56 51200 PE32 executable (console) Intel 80386, for MS Windows encode_keychange.exe.asc January 02 2023 22:33:20 801 GnuPG signature
encode_keychange.exe.asc January 02 2023 22:33:20 801 GnuPG signature encode_keychange.exe.md5 January 02 2023 22:33:20 55 MD5 checksum
encode_keychange.exe.md5 January 02 2023 22:33:20 55 MD5 checksum encode_keychange.exe.sha1 January 02 2023 22:33:20 63 SHA1 checksum
encode_keychange.exe.sha1 January 02 2023 22:33:20 63 SHA1 checksum encode_keychange.exe.sha256 January 02 2023 22:33:20 87 SHA256 checksum
encode_keychange.exe.sha256 January 02 2023 22:33:20 87 SHA256 checksum encode_keychange.exe.sha512 January 02 2023 22:33:20 151 SHA512 checksum
encode_keychange.exe.sha512 January 02 2023 22:33:20 151 SHA512 checksum mib2c January 01 2023 15:01:30 45136 Perl script text executable
mib2c January 01 2023 15:01:30 45136 Perl script text executable mib2c.asc January 02 2023 22:33:34 801 GnuPG signature
mib2c.asc January 02 2023 22:33:34 801 GnuPG signature mib2c.md5 January 02 2023 22:33:34 40 MD5 checksum
mib2c.md5 January 02 2023 22:33:34 40 MD5 checksum mib2c.sha1 January 02 2023 22:33:34 48 SHA1 checksum
mib2c.sha1 January 02 2023 22:33:34 48 SHA1 checksum mib2c.sha256 January 02 2023 22:33:34 72 SHA256 checksum
mib2c.sha256 January 02 2023 22:33:34 72 SHA256 checksum mib2c.sha512 January 02 2023 22:33:34 136 SHA512 checksum
mib2c.sha512 January 02 2023 22:33:34 136 SHA512 checksum snmpbulkget.exe January 01 2023 15:00:58 355840 PE32 executable (console) Intel 80386, for MS Windows
snmpbulkget.exe January 01 2023 15:00:58 355840 PE32 executable (console) Intel 80386, for MS Windows snmpbulkget.exe.asc January 02 2023 22:33:52 801 GnuPG signature
snmpbulkget.exe.asc January 02 2023 22:33:52 801 GnuPG signature snmpbulkget.exe.md5 January 02 2023 22:33:52 50 MD5 checksum
snmpbulkget.exe.md5 January 02 2023 22:33:52 50 MD5 checksum snmpbulkget.exe.sha1 January 02 2023 22:33:52 58 SHA1 checksum
snmpbulkget.exe.sha1 January 02 2023 22:33:52 58 SHA1 checksum snmpbulkget.exe.sha256 January 02 2023 22:33:52 82 SHA256 checksum
snmpbulkget.exe.sha256 January 02 2023 22:33:52 82 SHA256 checksum snmpbulkget.exe.sha512 January 02 2023 22:33:52 146 SHA512 checksum
snmpbulkget.exe.sha512 January 02 2023 22:33:52 146 SHA512 checksum snmpbulkwalk.exe January 01 2023 15:00:58 356864 PE32 executable (console) Intel 80386, for MS Windows
snmpbulkwalk.exe January 01 2023 15:00:58 356864 PE32 executable (console) Intel 80386, for MS Windows snmpbulkwalk.exe.asc January 02 2023 22:34:16 801 GnuPG signature
snmpbulkwalk.exe.asc January 02 2023 22:34:16 801 GnuPG signature snmpbulkwalk.exe.md5 January 02 2023 22:34:16 51 MD5 checksum
snmpbulkwalk.exe.md5 January 02 2023 22:34:16 51 MD5 checksum snmpbulkwalk.exe.sha1 January 02 2023 22:34:16 59 SHA1 checksum
snmpbulkwalk.exe.sha1 January 02 2023 22:34:16 59 SHA1 checksum snmpbulkwalk.exe.sha256 January 02 2023 22:34:16 83 SHA256 checksum
snmpbulkwalk.exe.sha256 January 02 2023 22:34:16 83 SHA256 checksum snmpbulkwalk.exe.sha512 January 02 2023 22:34:16 147 SHA512 checksum
snmpbulkwalk.exe.sha512 January 02 2023 22:34:16 147 SHA512 checksum snmpconf January 01 2023 15:01:30 26989 Perl script text executable
snmpconf January 01 2023 15:01:30 26989 Perl script text executable snmpconf.asc January 02 2023 22:34:32 801 GnuPG signature
snmpconf.asc January 02 2023 22:34:32 801 GnuPG signature snmpconf.md5 January 02 2023 22:34:32 43 MD5 checksum
snmpconf.md5 January 02 2023 22:34:32 43 MD5 checksum snmpconf.sha1 January 02 2023 22:34:32 51 SHA1 checksum
snmpconf.sha1 January 02 2023 22:34:32 51 SHA1 checksum snmpconf.sha256 January 02 2023 22:34:32 75 SHA256 checksum
snmpconf.sha256 January 02 2023 22:34:32 75 SHA256 checksum snmpconf.sha512 January 02 2023 22:34:32 139 SHA512 checksum
snmpconf.sha512 January 02 2023 22:34:32 139 SHA512 checksum snmpd.exe January 01 2023 15:01:30 939008 PE32 executable (console) Intel 80386, for MS Windows
snmpd.exe January 01 2023 15:01:30 939008 PE32 executable (console) Intel 80386, for MS Windows snmpd.exe.asc January 02 2023 22:34:40 801 GnuPG signature
snmpd.exe.asc January 02 2023 22:34:40 801 GnuPG signature snmpd.exe.md5 January 02 2023 22:34:40 44 MD5 checksum
snmpd.exe.md5 January 02 2023 22:34:40 44 MD5 checksum snmpd.exe.sha1 January 02 2023 22:34:40 52 SHA1 checksum
snmpd.exe.sha1 January 02 2023 22:34:40 52 SHA1 checksum snmpd.exe.sha256 January 02 2023 22:34:40 76 SHA256 checksum
snmpd.exe.sha256 January 02 2023 22:34:40 76 SHA256 checksum snmpd.exe.sha512 January 02 2023 22:34:40 140 SHA512 checksum
snmpd.exe.sha512 January 02 2023 22:34:40 140 SHA512 checksum snmpdelta.exe January 01 2023 15:01:00 360960 PE32 executable (console) Intel 80386, for MS Windows
snmpdelta.exe January 01 2023 15:01:00 360960 PE32 executable (console) Intel 80386, for MS Windows snmpdelta.exe.asc January 02 2023 22:33:24 801 GnuPG signature
snmpdelta.exe.asc January 02 2023 22:33:24 801 GnuPG signature snmpdelta.exe.md5 January 02 2023 22:33:24 48 MD5 checksum
snmpdelta.exe.md5 January 02 2023 22:33:24 48 MD5 checksum snmpdelta.exe.sha1 January 02 2023 22:33:24 56 SHA1 checksum
snmpdelta.exe.sha1 January 02 2023 22:33:24 56 SHA1 checksum snmpdelta.exe.sha256 January 02 2023 22:33:24 80 SHA256 checksum
snmpdelta.exe.sha256 January 02 2023 22:33:24 80 SHA256 checksum snmpdelta.exe.sha512 January 02 2023 22:33:24 144 SHA512 checksum
snmpdelta.exe.sha512 January 02 2023 22:33:24 144 SHA512 checksum snmpdf.exe January 01 2023 15:01:00 358400 PE32 executable (console) Intel 80386, for MS Windows
snmpdf.exe January 01 2023 15:01:00 358400 PE32 executable (console) Intel 80386, for MS Windows snmpdf.exe.asc January 02 2023 22:33:38 801 GnuPG signature
snmpdf.exe.asc January 02 2023 22:33:38 801 GnuPG signature snmpdf.exe.md5 January 02 2023 22:33:38 45 MD5 checksum
snmpdf.exe.md5 January 02 2023 22:33:38 45 MD5 checksum snmpdf.exe.sha1 January 02 2023 22:33:38 53 SHA1 checksum
snmpdf.exe.sha1 January 02 2023 22:33:38 53 SHA1 checksum snmpdf.exe.sha256 January 02 2023 22:33:38 77 SHA256 checksum
snmpdf.exe.sha256 January 02 2023 22:33:38 77 SHA256 checksum snmpdf.exe.sha512 January 02 2023 22:33:38 141 SHA512 checksum
snmpdf.exe.sha512 January 02 2023 22:33:38 141 SHA512 checksum snmpget.exe January 01 2023 15:01:00 355840 PE32 executable (console) Intel 80386, for MS Windows
snmpget.exe January 01 2023 15:01:00 355840 PE32 executable (console) Intel 80386, for MS Windows snmpget.exe.asc January 02 2023 22:34:04 801 GnuPG signature
snmpget.exe.asc January 02 2023 22:34:04 801 GnuPG signature snmpget.exe.md5 January 02 2023 22:34:04 46 MD5 checksum
snmpget.exe.md5 January 02 2023 22:34:04 46 MD5 checksum snmpget.exe.sha1 January 02 2023 22:34:04 54 SHA1 checksum
snmpget.exe.sha1 January 02 2023 22:34:04 54 SHA1 checksum snmpget.exe.sha256 January 02 2023 22:34:04 78 SHA256 checksum
snmpget.exe.sha256 January 02 2023 22:34:04 78 SHA256 checksum snmpget.exe.sha512 January 02 2023 22:34:04 142 SHA512 checksum
snmpget.exe.sha512 January 02 2023 22:34:04 142 SHA512 checksum snmpgetnext.exe January 01 2023 15:01:02 355840 PE32 executable (console) Intel 80386, for MS Windows
snmpgetnext.exe January 01 2023 15:01:02 355840 PE32 executable (console) Intel 80386, for MS Windows snmpgetnext.exe.asc January 02 2023 22:34:20 801 GnuPG signature
snmpgetnext.exe.asc January 02 2023 22:34:20 801 GnuPG signature snmpgetnext.exe.md5 January 02 2023 22:34:20 50 MD5 checksum
snmpgetnext.exe.md5 January 02 2023 22:34:20 50 MD5 checksum snmpgetnext.exe.sha1 January 02 2023 22:34:20 58 SHA1 checksum
snmpgetnext.exe.sha1 January 02 2023 22:34:20 58 SHA1 checksum snmpgetnext.exe.sha256 January 02 2023 22:34:20 82 SHA256 checksum
snmpgetnext.exe.sha256 January 02 2023 22:34:20 82 SHA256 checksum snmpgetnext.exe.sha512 January 02 2023 22:34:20 146 SHA512 checksum
snmpgetnext.exe.sha512 January 02 2023 22:34:20 146 SHA512 checksum snmpnetstat.exe January 01 2023 15:01:08 389632 PE32 executable (console) Intel 80386, for MS Windows
snmpnetstat.exe January 01 2023 15:01:08 389632 PE32 executable (console) Intel 80386, for MS Windows snmpnetstat.exe.asc January 02 2023 22:34:34 801 GnuPG signature
snmpnetstat.exe.asc January 02 2023 22:34:34 801 GnuPG signature snmpnetstat.exe.md5 January 02 2023 22:34:34 50 MD5 checksum
snmpnetstat.exe.md5 January 02 2023 22:34:34 50 MD5 checksum snmpnetstat.exe.sha1 January 02 2023 22:34:34 58 SHA1 checksum
snmpnetstat.exe.sha1 January 02 2023 22:34:34 58 SHA1 checksum snmpnetstat.exe.sha256 January 02 2023 22:34:34 82 SHA256 checksum
snmpnetstat.exe.sha256 January 02 2023 22:34:34 82 SHA256 checksum snmpnetstat.exe.sha512 January 02 2023 22:34:34 146 SHA512 checksum
snmpnetstat.exe.sha512 January 02 2023 22:34:34 146 SHA512 checksum snmpset.exe January 01 2023 15:01:10 360448 PE32 executable (console) Intel 80386, for MS Windows
snmpset.exe January 01 2023 15:01:10 360448 PE32 executable (console) Intel 80386, for MS Windows snmpset.exe.asc January 02 2023 22:34:44 801 GnuPG signature
snmpset.exe.asc January 02 2023 22:34:44 801 GnuPG signature snmpset.exe.md5 January 02 2023 22:34:44 46 MD5 checksum
snmpset.exe.md5 January 02 2023 22:34:44 46 MD5 checksum snmpset.exe.sha1 January 02 2023 22:34:44 54 SHA1 checksum
snmpset.exe.sha1 January 02 2023 22:34:44 54 SHA1 checksum snmpset.exe.sha256 January 02 2023 22:34:44 78 SHA256 checksum
snmpset.exe.sha256 January 02 2023 22:34:44 78 SHA256 checksum snmpset.exe.sha512 January 02 2023 22:34:44 142 SHA512 checksum
snmpset.exe.sha512 January 02 2023 22:34:44 142 SHA512 checksum snmpstatus.exe January 01 2023 15:01:12 350208 PE32 executable (console) Intel 80386, for MS Windows
snmpstatus.exe January 01 2023 15:01:12 350208 PE32 executable (console) Intel 80386, for MS Windows snmpstatus.exe.asc January 02 2023 22:33:26 801 GnuPG signature
snmpstatus.exe.asc January 02 2023 22:33:26 801 GnuPG signature snmpstatus.exe.md5 January 02 2023 22:33:26 49 MD5 checksum
snmpstatus.exe.md5 January 02 2023 22:33:26 49 MD5 checksum snmpstatus.exe.sha1 January 02 2023 22:33:26 57 SHA1 checksum
snmpstatus.exe.sha1 January 02 2023 22:33:26 57 SHA1 checksum snmpstatus.exe.sha256 January 02 2023 22:33:26 81 SHA256 checksum
snmpstatus.exe.sha256 January 02 2023 22:33:26 81 SHA256 checksum snmpstatus.exe.sha512 January 02 2023 22:33:26 145 SHA512 checksum
snmpstatus.exe.sha512 January 02 2023 22:33:26 145 SHA512 checksum snmptable.exe January 01 2023 15:01:16 364544 PE32 executable (console) Intel 80386, for MS Windows
snmptable.exe January 01 2023 15:01:16 364544 PE32 executable (console) Intel 80386, for MS Windows snmptable.exe.asc January 02 2023 22:33:42 801 GnuPG signature
snmptable.exe.asc January 02 2023 22:33:42 801 GnuPG signature snmptable.exe.md5 January 02 2023 22:33:42 48 MD5 checksum
snmptable.exe.md5 January 02 2023 22:33:42 48 MD5 checksum snmptable.exe.sha1 January 02 2023 22:33:42 56 SHA1 checksum
snmptable.exe.sha1 January 02 2023 22:33:42 56 SHA1 checksum snmptable.exe.sha256 January 02 2023 22:33:42 80 SHA256 checksum
snmptable.exe.sha256 January 02 2023 22:33:42 80 SHA256 checksum snmptable.exe.sha512 January 02 2023 22:33:42 144 SHA512 checksum
snmptable.exe.sha512 January 02 2023 22:33:42 144 SHA512 checksum snmptest.exe January 01 2023 15:01:16 358912 PE32 executable (console) Intel 80386, for MS Windows
snmptest.exe January 01 2023 15:01:16 358912 PE32 executable (console) Intel 80386, for MS Windows snmptest.exe.asc January 02 2023 22:34:08 801 GnuPG signature
snmptest.exe.asc January 02 2023 22:34:08 801 GnuPG signature snmptest.exe.md5 January 02 2023 22:34:08 47 MD5 checksum
snmptest.exe.md5 January 02 2023 22:34:08 47 MD5 checksum snmptest.exe.sha1 January 02 2023 22:34:08 55 SHA1 checksum
snmptest.exe.sha1 January 02 2023 22:34:08 55 SHA1 checksum snmptest.exe.sha256 January 02 2023 22:34:08 79 SHA256 checksum
snmptest.exe.sha256 January 02 2023 22:34:08 79 SHA256 checksum snmptest.exe.sha512 January 02 2023 22:34:08 143 SHA512 checksum
snmptest.exe.sha512 January 02 2023 22:34:08 143 SHA512 checksum snmptranslate.exe January 01 2023 15:01:16 346624 PE32 executable (console) Intel 80386, for MS Windows
snmptranslate.exe January 01 2023 15:01:16 346624 PE32 executable (console) Intel 80386, for MS Windows snmptranslate.exe.asc January 02 2023 22:34:24 801 GnuPG signature
snmptranslate.exe.asc January 02 2023 22:34:24 801 GnuPG signature snmptranslate.exe.md5 January 02 2023 22:34:24 52 MD5 checksum
snmptranslate.exe.md5 January 02 2023 22:34:24 52 MD5 checksum snmptranslate.exe.sha1 January 02 2023 22:34:24 60 SHA1 checksum
snmptranslate.exe.sha1 January 02 2023 22:34:24 60 SHA1 checksum snmptranslate.exe.sha256 January 02 2023 22:34:24 84 SHA256 checksum
snmptranslate.exe.sha256 January 02 2023 22:34:24 84 SHA256 checksum snmptranslate.exe.sha512 January 02 2023 22:34:24 148 SHA512 checksum
snmptranslate.exe.sha512 January 02 2023 22:34:24 148 SHA512 checksum snmptrap.exe January 01 2023 15:01:18 369152 PE32 executable (console) Intel 80386, for MS Windows
snmptrap.exe January 01 2023 15:01:18 369152 PE32 executable (console) Intel 80386, for MS Windows snmptrap.exe.asc January 02 2023 22:34:38 801 GnuPG signature
snmptrap.exe.asc January 02 2023 22:34:38 801 GnuPG signature snmptrap.exe.md5 January 02 2023 22:34:38 47 MD5 checksum
snmptrap.exe.md5 January 02 2023 22:34:38 47 MD5 checksum snmptrap.exe.sha1 January 02 2023 22:34:38 55 SHA1 checksum
snmptrap.exe.sha1 January 02 2023 22:34:38 55 SHA1 checksum snmptrap.exe.sha256 January 02 2023 22:34:38 79 SHA256 checksum
snmptrap.exe.sha256 January 02 2023 22:34:38 79 SHA256 checksum snmptrap.exe.sha512 January 02 2023 22:34:38 143 SHA512 checksum
snmptrap.exe.sha512 January 02 2023 22:34:38 143 SHA512 checksum snmptrapd.exe January 01 2023 15:01:26 644096 PE32 executable (console) Intel 80386, for MS Windows
snmptrapd.exe January 01 2023 15:01:26 644096 PE32 executable (console) Intel 80386, for MS Windows snmptrapd.exe.asc January 02 2023 22:34:56 801 GnuPG signature
snmptrapd.exe.asc January 02 2023 22:34:56 801 GnuPG signature snmptrapd.exe.md5 January 02 2023 22:34:56 48 MD5 checksum
snmptrapd.exe.md5 January 02 2023 22:34:56 48 MD5 checksum snmptrapd.exe.sha1 January 02 2023 22:34:56 56 SHA1 checksum
snmptrapd.exe.sha1 January 02 2023 22:34:56 56 SHA1 checksum snmptrapd.exe.sha256 January 02 2023 22:34:56 80 SHA256 checksum
snmptrapd.exe.sha256 January 02 2023 22:34:56 80 SHA256 checksum snmptrapd.exe.sha512 January 02 2023 22:34:56 144 SHA512 checksum
snmptrapd.exe.sha512 January 02 2023 22:34:56 144 SHA512 checksum snmpusm.exe January 01 2023 15:01:20 361984 PE32 executable (console) Intel 80386, for MS Windows
snmpusm.exe January 01 2023 15:01:20 361984 PE32 executable (console) Intel 80386, for MS Windows snmpusm.exe.asc January 02 2023 22:33:30 801 GnuPG signature
snmpusm.exe.asc January 02 2023 22:33:30 801 GnuPG signature snmpusm.exe.md5 January 02 2023 22:33:30 46 MD5 checksum
snmpusm.exe.md5 January 02 2023 22:33:30 46 MD5 checksum snmpusm.exe.sha1 January 02 2023 22:33:30 54 SHA1 checksum
snmpusm.exe.sha1 January 02 2023 22:33:30 54 SHA1 checksum snmpusm.exe.sha256 January 02 2023 22:33:30 78 SHA256 checksum
snmpusm.exe.sha256 January 02 2023 22:33:30 78 SHA256 checksum snmpusm.exe.sha512 January 02 2023 22:33:30 142 SHA512 checksum
snmpusm.exe.sha512 January 02 2023 22:33:30 142 SHA512 checksum snmpvacm.exe January 01 2023 15:01:22 366592 PE32 executable (console) Intel 80386, for MS Windows
snmpvacm.exe January 01 2023 15:01:22 366592 PE32 executable (console) Intel 80386, for MS Windows snmpvacm.exe.asc January 02 2023 22:33:46 801 GnuPG signature
snmpvacm.exe.asc January 02 2023 22:33:46 801 GnuPG signature snmpvacm.exe.md5 January 02 2023 22:33:46 47 MD5 checksum
snmpvacm.exe.md5 January 02 2023 22:33:46 47 MD5 checksum snmpvacm.exe.sha1 January 02 2023 22:33:46 55 SHA1 checksum
snmpvacm.exe.sha1 January 02 2023 22:33:46 55 SHA1 checksum snmpvacm.exe.sha256 January 02 2023 22:33:46 79 SHA256 checksum
snmpvacm.exe.sha256 January 02 2023 22:33:46 79 SHA256 checksum snmpvacm.exe.sha512 January 02 2023 22:33:46 143 SHA512 checksum
snmpvacm.exe.sha512 January 02 2023 22:33:46 143 SHA512 checksum snmpwalk.exe January 01 2023 15:01:24 357376 PE32 executable (console) Intel 80386, for MS Windows
snmpwalk.exe January 01 2023 15:01:24 357376 PE32 executable (console) Intel 80386, for MS Windows snmpwalk.exe.asc January 02 2023 22:34:12 801 GnuPG signature
snmpwalk.exe.asc January 02 2023 22:34:12 801 GnuPG signature snmpwalk.exe.md5 January 02 2023 22:34:12 47 MD5 checksum
snmpwalk.exe.md5 January 02 2023 22:34:12 47 MD5 checksum snmpwalk.exe.sha1 January 02 2023 22:34:12 55 SHA1 checksum
snmpwalk.exe.sha1 January 02 2023 22:34:12 55 SHA1 checksum snmpwalk.exe.sha256 January 02 2023 22:34:12 79 SHA256 checksum
snmpwalk.exe.sha256 January 02 2023 22:34:12 79 SHA256 checksum snmpwalk.exe.sha512 January 02 2023 22:34:12 143 SHA512 checksum
snmpwalk.exe.sha512 January 02 2023 22:34:12 143 SHA512 checksum traptoemail January 01 2023 15:01:30 2277 Perl script text executable
traptoemail January 01 2023 15:01:30 2277 Perl script text executable traptoemail.asc January 02 2023 22:34:28 801 GnuPG signature
traptoemail.asc January 02 2023 22:34:28 801 GnuPG signature traptoemail.md5 January 02 2023 22:34:28 46 MD5 checksum
traptoemail.md5 January 02 2023 22:34:28 46 MD5 checksum traptoemail.sha1 January 02 2023 22:34:28 54 SHA1 checksum
traptoemail.sha1 January 02 2023 22:34:28 54 SHA1 checksum traptoemail.sha256 January 02 2023 22:34:28 78 SHA256 checksum
traptoemail.sha256 January 02 2023 22:34:28 78 SHA256 checksum traptoemail.sha512 January 02 2023 22:34:28 142 SHA512 checksum ↩ Browse the download server
traptoemail.sha512 January 02 2023 22:34:28 142 SHA512 checksum ↩ Browse the download server
net-snmp 5.9.1 dynamically linked, no openssl
Listing directory https://download.elifulkerson.com/files/net-snmp-compiled-win32/netsnmp-5.9.1-nossl-dynamic:encode_keychange.exe January 02 2023 20:34:00 17920 PE32 executable (console) Intel 80386, for MS Windows encode_keychange.exe.asc January 02 2023 22:35:20 801 GnuPG signature
encode_keychange.exe.asc January 02 2023 22:35:20 801 GnuPG signature encode_keychange.exe.md5 January 02 2023 22:35:20 55 MD5 checksum
encode_keychange.exe.md5 January 02 2023 22:35:20 55 MD5 checksum encode_keychange.exe.sha1 January 02 2023 22:35:20 63 SHA1 checksum
encode_keychange.exe.sha1 January 02 2023 22:35:20 63 SHA1 checksum encode_keychange.exe.sha256 January 02 2023 22:35:20 87 SHA256 checksum
encode_keychange.exe.sha256 January 02 2023 22:35:20 87 SHA256 checksum encode_keychange.exe.sha512 January 02 2023 22:35:20 151 SHA512 checksum
encode_keychange.exe.sha512 January 02 2023 22:35:20 151 SHA512 checksum mib2c January 02 2023 20:34:22 45136 Perl script text executable
mib2c January 02 2023 20:34:22 45136 Perl script text executable mib2c.asc January 02 2023 22:35:30 801 GnuPG signature
mib2c.asc January 02 2023 22:35:30 801 GnuPG signature mib2c.md5 January 02 2023 22:35:30 40 MD5 checksum
mib2c.md5 January 02 2023 22:35:30 40 MD5 checksum mib2c.sha1 January 02 2023 22:35:30 48 SHA1 checksum
mib2c.sha1 January 02 2023 22:35:30 48 SHA1 checksum mib2c.sha256 January 02 2023 22:35:30 72 SHA256 checksum
mib2c.sha256 January 02 2023 22:35:30 72 SHA256 checksum mib2c.sha512 January 02 2023 22:35:30 136 SHA512 checksum
mib2c.sha512 January 02 2023 22:35:30 136 SHA512 checksum netsnmp.dll January 02 2023 20:33:28 474624 PE32 executable (DLL) (console) Intel 80386, for MS Windows
netsnmp.dll January 02 2023 20:33:28 474624 PE32 executable (DLL) (console) Intel 80386, for MS Windows netsnmp.dll.asc January 02 2023 22:35:44 801 GnuPG signature
netsnmp.dll.asc January 02 2023 22:35:44 801 GnuPG signature netsnmp.dll.md5 January 02 2023 22:35:44 46 MD5 checksum
netsnmp.dll.md5 January 02 2023 22:35:44 46 MD5 checksum netsnmp.dll.sha1 January 02 2023 22:35:44 54 SHA1 checksum
netsnmp.dll.sha1 January 02 2023 22:35:44 54 SHA1 checksum netsnmp.dll.sha256 January 02 2023 22:35:44 78 SHA256 checksum
netsnmp.dll.sha256 January 02 2023 22:35:44 78 SHA256 checksum netsnmp.dll.sha512 January 02 2023 22:35:44 142 SHA512 checksum
netsnmp.dll.sha512 January 02 2023 22:35:44 142 SHA512 checksum snmpbulkget.exe January 02 2023 20:34:00 11264 PE32 executable (console) Intel 80386, for MS Windows
snmpbulkget.exe January 02 2023 20:34:00 11264 PE32 executable (console) Intel 80386, for MS Windows snmpbulkget.exe.asc January 02 2023 22:36:06 801 GnuPG signature
snmpbulkget.exe.asc January 02 2023 22:36:06 801 GnuPG signature snmpbulkget.exe.md5 January 02 2023 22:36:06 50 MD5 checksum
snmpbulkget.exe.md5 January 02 2023 22:36:06 50 MD5 checksum snmpbulkget.exe.sha1 January 02 2023 22:36:06 58 SHA1 checksum
snmpbulkget.exe.sha1 January 02 2023 22:36:06 58 SHA1 checksum snmpbulkget.exe.sha256 January 02 2023 22:36:06 82 SHA256 checksum
snmpbulkget.exe.sha256 January 02 2023 22:36:06 82 SHA256 checksum snmpbulkget.exe.sha512 January 02 2023 22:36:06 146 SHA512 checksum
snmpbulkget.exe.sha512 January 02 2023 22:36:06 146 SHA512 checksum snmpbulkwalk.exe January 02 2023 20:34:02 12288 PE32 executable (console) Intel 80386, for MS Windows
snmpbulkwalk.exe January 02 2023 20:34:02 12288 PE32 executable (console) Intel 80386, for MS Windows snmpbulkwalk.exe.asc January 02 2023 22:36:20 801 GnuPG signature
snmpbulkwalk.exe.asc January 02 2023 22:36:20 801 GnuPG signature snmpbulkwalk.exe.md5 January 02 2023 22:36:20 51 MD5 checksum
snmpbulkwalk.exe.md5 January 02 2023 22:36:20 51 MD5 checksum snmpbulkwalk.exe.sha1 January 02 2023 22:36:20 59 SHA1 checksum
snmpbulkwalk.exe.sha1 January 02 2023 22:36:20 59 SHA1 checksum snmpbulkwalk.exe.sha256 January 02 2023 22:36:22 83 SHA256 checksum
snmpbulkwalk.exe.sha256 January 02 2023 22:36:22 83 SHA256 checksum snmpbulkwalk.exe.sha512 January 02 2023 22:36:22 147 SHA512 checksum
snmpbulkwalk.exe.sha512 January 02 2023 22:36:22 147 SHA512 checksum snmpconf January 02 2023 20:34:22 26989 Perl script text executable
snmpconf January 02 2023 20:34:22 26989 Perl script text executable snmpconf.asc January 02 2023 22:36:34 801 GnuPG signature
snmpconf.asc January 02 2023 22:36:34 801 GnuPG signature snmpconf.md5 January 02 2023 22:36:34 43 MD5 checksum
snmpconf.md5 January 02 2023 22:36:34 43 MD5 checksum snmpconf.sha1 January 02 2023 22:36:34 51 SHA1 checksum
snmpconf.sha1 January 02 2023 22:36:34 51 SHA1 checksum snmpconf.sha256 January 02 2023 22:36:34 75 SHA256 checksum
snmpconf.sha256 January 02 2023 22:36:34 75 SHA256 checksum snmpconf.sha512 January 02 2023 22:36:34 139 SHA512 checksum
snmpconf.sha512 January 02 2023 22:36:34 139 SHA512 checksum snmpd.exe January 02 2023 20:34:22 555520 PE32 executable (console) Intel 80386, for MS Windows
snmpd.exe January 02 2023 20:34:22 555520 PE32 executable (console) Intel 80386, for MS Windows snmpd.exe.asc January 02 2023 22:35:22 801 GnuPG signature
snmpd.exe.asc January 02 2023 22:35:22 801 GnuPG signature snmpd.exe.md5 January 02 2023 22:35:22 44 MD5 checksum
snmpd.exe.md5 January 02 2023 22:35:22 44 MD5 checksum snmpd.exe.sha1 January 02 2023 22:35:22 52 SHA1 checksum
snmpd.exe.sha1 January 02 2023 22:35:22 52 SHA1 checksum snmpd.exe.sha256 January 02 2023 22:35:22 76 SHA256 checksum
snmpd.exe.sha256 January 02 2023 22:35:22 76 SHA256 checksum snmpd.exe.sha512 January 02 2023 22:35:22 140 SHA512 checksum
snmpd.exe.sha512 January 02 2023 22:35:22 140 SHA512 checksum snmpdelta.exe January 02 2023 20:34:02 17920 PE32 executable (console) Intel 80386, for MS Windows
snmpdelta.exe January 02 2023 20:34:02 17920 PE32 executable (console) Intel 80386, for MS Windows snmpdelta.exe.asc January 02 2023 22:35:32 801 GnuPG signature
snmpdelta.exe.asc January 02 2023 22:35:32 801 GnuPG signature snmpdelta.exe.md5 January 02 2023 22:35:32 48 MD5 checksum
snmpdelta.exe.md5 January 02 2023 22:35:32 48 MD5 checksum snmpdelta.exe.sha1 January 02 2023 22:35:32 56 SHA1 checksum
snmpdelta.exe.sha1 January 02 2023 22:35:32 56 SHA1 checksum snmpdelta.exe.sha256 January 02 2023 22:35:32 80 SHA256 checksum
snmpdelta.exe.sha256 January 02 2023 22:35:32 80 SHA256 checksum snmpdelta.exe.sha512 January 02 2023 22:35:32 144 SHA512 checksum
snmpdelta.exe.sha512 January 02 2023 22:35:32 144 SHA512 checksum snmpdf.exe January 02 2023 20:34:04 16384 PE32 executable (console) Intel 80386, for MS Windows
snmpdf.exe January 02 2023 20:34:04 16384 PE32 executable (console) Intel 80386, for MS Windows snmpdf.exe.asc January 02 2023 22:35:48 801 GnuPG signature
snmpdf.exe.asc January 02 2023 22:35:48 801 GnuPG signature snmpdf.exe.md5 January 02 2023 22:35:48 45 MD5 checksum
snmpdf.exe.md5 January 02 2023 22:35:48 45 MD5 checksum snmpdf.exe.sha1 January 02 2023 22:35:48 53 SHA1 checksum
snmpdf.exe.sha1 January 02 2023 22:35:48 53 SHA1 checksum snmpdf.exe.sha256 January 02 2023 22:35:48 77 SHA256 checksum
snmpdf.exe.sha256 January 02 2023 22:35:48 77 SHA256 checksum snmpdf.exe.sha512 January 02 2023 22:35:48 141 SHA512 checksum
snmpdf.exe.sha512 January 02 2023 22:35:48 141 SHA512 checksum snmpget.exe January 02 2023 20:34:04 11264 PE32 executable (console) Intel 80386, for MS Windows
snmpget.exe January 02 2023 20:34:04 11264 PE32 executable (console) Intel 80386, for MS Windows snmpget.exe.asc January 02 2023 22:36:10 801 GnuPG signature
snmpget.exe.asc January 02 2023 22:36:10 801 GnuPG signature snmpget.exe.md5 January 02 2023 22:36:10 46 MD5 checksum
snmpget.exe.md5 January 02 2023 22:36:10 46 MD5 checksum snmpget.exe.sha1 January 02 2023 22:36:10 54 SHA1 checksum
snmpget.exe.sha1 January 02 2023 22:36:10 54 SHA1 checksum snmpget.exe.sha256 January 02 2023 22:36:10 78 SHA256 checksum
snmpget.exe.sha256 January 02 2023 22:36:10 78 SHA256 checksum snmpget.exe.sha512 January 02 2023 22:36:10 142 SHA512 checksum
snmpget.exe.sha512 January 02 2023 22:36:10 142 SHA512 checksum snmpgetnext.exe January 02 2023 20:34:06 11264 PE32 executable (console) Intel 80386, for MS Windows
snmpgetnext.exe January 02 2023 20:34:06 11264 PE32 executable (console) Intel 80386, for MS Windows snmpgetnext.exe.asc January 02 2023 22:36:24 801 GnuPG signature
snmpgetnext.exe.asc January 02 2023 22:36:24 801 GnuPG signature snmpgetnext.exe.md5 January 02 2023 22:36:24 50 MD5 checksum
snmpgetnext.exe.md5 January 02 2023 22:36:24 50 MD5 checksum snmpgetnext.exe.sha1 January 02 2023 22:36:24 58 SHA1 checksum
snmpgetnext.exe.sha1 January 02 2023 22:36:24 58 SHA1 checksum snmpgetnext.exe.sha256 January 02 2023 22:36:24 82 SHA256 checksum
snmpgetnext.exe.sha256 January 02 2023 22:36:24 82 SHA256 checksum snmpgetnext.exe.sha512 January 02 2023 22:36:24 146 SHA512 checksum
snmpgetnext.exe.sha512 January 02 2023 22:36:24 146 SHA512 checksum snmpnetstat.exe January 02 2023 20:34:10 56832 PE32 executable (console) Intel 80386, for MS Windows
snmpnetstat.exe January 02 2023 20:34:10 56832 PE32 executable (console) Intel 80386, for MS Windows snmpnetstat.exe.asc January 02 2023 22:36:36 801 GnuPG signature
snmpnetstat.exe.asc January 02 2023 22:36:36 801 GnuPG signature snmpnetstat.exe.md5 January 02 2023 22:36:36 50 MD5 checksum
snmpnetstat.exe.md5 January 02 2023 22:36:36 50 MD5 checksum snmpnetstat.exe.sha1 January 02 2023 22:36:36 58 SHA1 checksum
snmpnetstat.exe.sha1 January 02 2023 22:36:36 58 SHA1 checksum snmpnetstat.exe.sha256 January 02 2023 22:36:36 82 SHA256 checksum
snmpnetstat.exe.sha256 January 02 2023 22:36:36 82 SHA256 checksum snmpnetstat.exe.sha512 January 02 2023 22:36:36 146 SHA512 checksum
snmpnetstat.exe.sha512 January 02 2023 22:36:36 146 SHA512 checksum snmpset.exe January 02 2023 20:34:12 12288 PE32 executable (console) Intel 80386, for MS Windows
snmpset.exe January 02 2023 20:34:12 12288 PE32 executable (console) Intel 80386, for MS Windows snmpset.exe.asc January 02 2023 22:35:24 801 GnuPG signature
snmpset.exe.asc January 02 2023 22:35:24 801 GnuPG signature snmpset.exe.md5 January 02 2023 22:35:24 46 MD5 checksum
snmpset.exe.md5 January 02 2023 22:35:24 46 MD5 checksum snmpset.exe.sha1 January 02 2023 22:35:24 54 SHA1 checksum
snmpset.exe.sha1 January 02 2023 22:35:24 54 SHA1 checksum snmpset.exe.sha256 January 02 2023 22:35:24 78 SHA256 checksum
snmpset.exe.sha256 January 02 2023 22:35:24 78 SHA256 checksum snmpset.exe.sha512 January 02 2023 22:35:24 142 SHA512 checksum
snmpset.exe.sha512 January 02 2023 22:35:24 142 SHA512 checksum snmpstatus.exe January 02 2023 20:34:14 12800 PE32 executable (console) Intel 80386, for MS Windows
snmpstatus.exe January 02 2023 20:34:14 12800 PE32 executable (console) Intel 80386, for MS Windows snmpstatus.exe.asc January 02 2023 22:35:36 801 GnuPG signature
snmpstatus.exe.asc January 02 2023 22:35:36 801 GnuPG signature snmpstatus.exe.md5 January 02 2023 22:35:36 49 MD5 checksum
snmpstatus.exe.md5 January 02 2023 22:35:36 49 MD5 checksum snmpstatus.exe.sha1 January 02 2023 22:35:36 57 SHA1 checksum
snmpstatus.exe.sha1 January 02 2023 22:35:36 57 SHA1 checksum snmpstatus.exe.sha256 January 02 2023 22:35:36 81 SHA256 checksum
snmpstatus.exe.sha256 January 02 2023 22:35:36 81 SHA256 checksum snmpstatus.exe.sha512 January 02 2023 22:35:36 145 SHA512 checksum
snmpstatus.exe.sha512 January 02 2023 22:35:36 145 SHA512 checksum snmptable.exe January 02 2023 20:34:14 19968 PE32 executable (console) Intel 80386, for MS Windows
snmptable.exe January 02 2023 20:34:14 19968 PE32 executable (console) Intel 80386, for MS Windows snmptable.exe.asc January 02 2023 22:35:56 801 GnuPG signature
snmptable.exe.asc January 02 2023 22:35:56 801 GnuPG signature snmptable.exe.md5 January 02 2023 22:35:56 48 MD5 checksum
snmptable.exe.md5 January 02 2023 22:35:56 48 MD5 checksum snmptable.exe.sha1 January 02 2023 22:35:56 56 SHA1 checksum
snmptable.exe.sha1 January 02 2023 22:35:56 56 SHA1 checksum snmptable.exe.sha256 January 02 2023 22:35:56 80 SHA256 checksum
snmptable.exe.sha256 January 02 2023 22:35:56 80 SHA256 checksum snmptable.exe.sha512 January 02 2023 22:35:56 144 SHA512 checksum
snmptable.exe.sha512 January 02 2023 22:35:56 144 SHA512 checksum snmptest.exe January 02 2023 20:34:14 15872 PE32 executable (console) Intel 80386, for MS Windows
snmptest.exe January 02 2023 20:34:14 15872 PE32 executable (console) Intel 80386, for MS Windows snmptest.exe.asc January 02 2023 22:36:14 801 GnuPG signature
snmptest.exe.asc January 02 2023 22:36:14 801 GnuPG signature snmptest.exe.md5 January 02 2023 22:36:14 47 MD5 checksum
snmptest.exe.md5 January 02 2023 22:36:14 47 MD5 checksum snmptest.exe.sha1 January 02 2023 22:36:14 55 SHA1 checksum
snmptest.exe.sha1 January 02 2023 22:36:14 55 SHA1 checksum snmptest.exe.sha256 January 02 2023 22:36:14 79 SHA256 checksum
snmptest.exe.sha256 January 02 2023 22:36:14 79 SHA256 checksum snmptest.exe.sha512 January 02 2023 22:36:14 143 SHA512 checksum
snmptest.exe.sha512 January 02 2023 22:36:14 143 SHA512 checksum snmptranslate.exe January 02 2023 20:34:16 15360 PE32 executable (console) Intel 80386, for MS Windows
snmptranslate.exe January 02 2023 20:34:16 15360 PE32 executable (console) Intel 80386, for MS Windows snmptranslate.exe.asc January 02 2023 22:36:26 801 GnuPG signature
snmptranslate.exe.asc January 02 2023 22:36:26 801 GnuPG signature snmptranslate.exe.md5 January 02 2023 22:36:26 52 MD5 checksum
snmptranslate.exe.md5 January 02 2023 22:36:26 52 MD5 checksum snmptranslate.exe.sha1 January 02 2023 22:36:26 60 SHA1 checksum
snmptranslate.exe.sha1 January 02 2023 22:36:26 60 SHA1 checksum snmptranslate.exe.sha256 January 02 2023 22:36:26 84 SHA256 checksum
snmptranslate.exe.sha256 January 02 2023 22:36:26 84 SHA256 checksum snmptranslate.exe.sha512 January 02 2023 22:36:26 148 SHA512 checksum
snmptranslate.exe.sha512 January 02 2023 22:36:26 148 SHA512 checksum snmptrap.exe January 02 2023 20:34:16 13824 PE32 executable (console) Intel 80386, for MS Windows
snmptrap.exe January 02 2023 20:34:16 13824 PE32 executable (console) Intel 80386, for MS Windows snmptrap.exe.asc January 02 2023 22:36:40 801 GnuPG signature
snmptrap.exe.asc January 02 2023 22:36:40 801 GnuPG signature snmptrap.exe.md5 January 02 2023 22:36:40 47 MD5 checksum
snmptrap.exe.md5 January 02 2023 22:36:40 47 MD5 checksum snmptrap.exe.sha1 January 02 2023 22:36:40 55 SHA1 checksum
snmptrap.exe.sha1 January 02 2023 22:36:40 55 SHA1 checksum snmptrap.exe.sha256 January 02 2023 22:36:40 79 SHA256 checksum
snmptrap.exe.sha256 January 02 2023 22:36:40 79 SHA256 checksum snmptrap.exe.sha512 January 02 2023 22:36:40 143 SHA512 checksum
snmptrap.exe.sha512 January 02 2023 22:36:40 143 SHA512 checksum snmptrapd.exe January 02 2023 20:34:20 257536 PE32 executable (console) Intel 80386, for MS Windows
snmptrapd.exe January 02 2023 20:34:20 257536 PE32 executable (console) Intel 80386, for MS Windows snmptrapd.exe.asc January 02 2023 22:35:28 801 GnuPG signature
snmptrapd.exe.asc January 02 2023 22:35:28 801 GnuPG signature snmptrapd.exe.md5 January 02 2023 22:35:28 48 MD5 checksum
snmptrapd.exe.md5 January 02 2023 22:35:28 48 MD5 checksum snmptrapd.exe.sha1 January 02 2023 22:35:28 56 SHA1 checksum
snmptrapd.exe.sha1 January 02 2023 22:35:28 56 SHA1 checksum snmptrapd.exe.sha256 January 02 2023 22:35:28 80 SHA256 checksum
snmptrapd.exe.sha256 January 02 2023 22:35:28 80 SHA256 checksum snmptrapd.exe.sha512 January 02 2023 22:35:28 144 SHA512 checksum
snmptrapd.exe.sha512 January 02 2023 22:35:28 144 SHA512 checksum snmpusm.exe January 02 2023 20:34:18 24576 PE32 executable (console) Intel 80386, for MS Windows
snmpusm.exe January 02 2023 20:34:18 24576 PE32 executable (console) Intel 80386, for MS Windows snmpusm.exe.asc January 02 2023 22:35:40 801 GnuPG signature
snmpusm.exe.asc January 02 2023 22:35:40 801 GnuPG signature snmpusm.exe.md5 January 02 2023 22:35:40 46 MD5 checksum
snmpusm.exe.md5 January 02 2023 22:35:40 46 MD5 checksum snmpusm.exe.sha1 January 02 2023 22:35:40 54 SHA1 checksum
snmpusm.exe.sha1 January 02 2023 22:35:40 54 SHA1 checksum snmpusm.exe.sha256 January 02 2023 22:35:40 78 SHA256 checksum
snmpusm.exe.sha256 January 02 2023 22:35:40 78 SHA256 checksum snmpusm.exe.sha512 January 02 2023 22:35:40 142 SHA512 checksum
snmpusm.exe.sha512 January 02 2023 22:35:40 142 SHA512 checksum snmpvacm.exe January 02 2023 20:34:18 23552 PE32 executable (console) Intel 80386, for MS Windows
snmpvacm.exe January 02 2023 20:34:18 23552 PE32 executable (console) Intel 80386, for MS Windows snmpvacm.exe.asc January 02 2023 22:36:00 801 GnuPG signature
snmpvacm.exe.asc January 02 2023 22:36:00 801 GnuPG signature snmpvacm.exe.md5 January 02 2023 22:36:00 47 MD5 checksum
snmpvacm.exe.md5 January 02 2023 22:36:00 47 MD5 checksum snmpvacm.exe.sha1 January 02 2023 22:36:00 55 SHA1 checksum
snmpvacm.exe.sha1 January 02 2023 22:36:00 55 SHA1 checksum snmpvacm.exe.sha256 January 02 2023 22:36:00 79 SHA256 checksum
snmpvacm.exe.sha256 January 02 2023 22:36:00 79 SHA256 checksum snmpvacm.exe.sha512 January 02 2023 22:36:00 143 SHA512 checksum
snmpvacm.exe.sha512 January 02 2023 22:36:00 143 SHA512 checksum snmpwalk.exe January 02 2023 20:34:18 13312 PE32 executable (console) Intel 80386, for MS Windows
snmpwalk.exe January 02 2023 20:34:18 13312 PE32 executable (console) Intel 80386, for MS Windows snmpwalk.exe.asc January 02 2023 22:36:16 801 GnuPG signature
snmpwalk.exe.asc January 02 2023 22:36:16 801 GnuPG signature snmpwalk.exe.md5 January 02 2023 22:36:16 47 MD5 checksum
snmpwalk.exe.md5 January 02 2023 22:36:16 47 MD5 checksum snmpwalk.exe.sha1 January 02 2023 22:36:16 55 SHA1 checksum
snmpwalk.exe.sha1 January 02 2023 22:36:16 55 SHA1 checksum snmpwalk.exe.sha256 January 02 2023 22:36:16 79 SHA256 checksum
snmpwalk.exe.sha256 January 02 2023 22:36:16 79 SHA256 checksum snmpwalk.exe.sha512 January 02 2023 22:36:16 143 SHA512 checksum
snmpwalk.exe.sha512 January 02 2023 22:36:16 143 SHA512 checksum traptoemail January 02 2023 20:34:22 2277 Perl script text executable
traptoemail January 02 2023 20:34:22 2277 Perl script text executable traptoemail.asc January 02 2023 22:36:30 801 GnuPG signature
traptoemail.asc January 02 2023 22:36:30 801 GnuPG signature traptoemail.md5 January 02 2023 22:36:30 46 MD5 checksum
traptoemail.md5 January 02 2023 22:36:30 46 MD5 checksum traptoemail.sha1 January 02 2023 22:36:30 54 SHA1 checksum
traptoemail.sha1 January 02 2023 22:36:30 54 SHA1 checksum traptoemail.sha256 January 02 2023 22:36:30 78 SHA256 checksum
traptoemail.sha256 January 02 2023 22:36:30 78 SHA256 checksum traptoemail.sha512 January 02 2023 22:36:30 142 SHA512 checksum ↩ Browse the download server
traptoemail.sha512 January 02 2023 22:36:30 142 SHA512 checksum ↩ Browse the download server
What is SNMP?
SNMP also known as “Simple Network Management Protocol” is an application-layer protocol used to measure and monitor the performance of the devices within a network. It helps the system administrator to ensure that networks stay up and running. Today, SNMP is one of the most popular networking protocols in the world. All modern manufacturers create SNMP-enabled devices that enterprises can use to obtain performance data from the devices.
How SNMP Works?
SNMP uses the device’s Management Information Database (MIB) to collect the performance data. The MIB is a database that records information about the hardware and contains MIB files. The MIB resides within the SNMP manager designed to collect information and organize it into a hierarchical format. SNMP uses this information from the MIB to interpret messages before sending them onwards to the end-user.
There are different types of queries managers used to poll the information from the SNMP agent including, GET or GET-NEXT commands. The GET command uses the agent’s hostname and Object Identifiers (OID) to obtain the information from the MIB. The GET-NEXT command obtains the data from the next OID.
What is SNMPWALK?
SNMPWALK is a command-line utility used to collect the information from remote SNMP-enabled devices including, routers and switches. It allows you to see all the OID variables available on remote devices. It sends multiple GET-NEXT commands to OIDs then the manager collects the data from all OIDs. SNMPWALK is a command-line utility that can be installed on Linux and Windows operating systems.
In this guide, we will show you how to install SNMPWALK on Windows and Linux. We will also explain how to use it to get the information from the remote devices.
Install SNMP and SNMPWALK on Linux
In this section, we will show you how to install SNMP and SNMPWALK on Debian and RPM-based Linux operating systems.
For RPM-based operating system including, RHEL/CentOS/Fedora, install the SNMP and SNMPWALK using the following command:
yum install net-snmp net-snmp-libs net-snmp-utils -y
For Debian based operating system including, Debian/Ubuntu, install the SNMP and SNMPWALK using the following command:
apt-get install snmpd snmp libsnmp-dev -y
Once the installation has been finished, start the SNMP service and enable it to start at system reboot with the following command:
systemctl start snmpd
systemctl enable snmpd
You can check the status of the SNMP with the following command:
systemctl status snmpd
You should get the following output:
● snmpd.service - Simple Network Management Protocol (SNMP) Daemon.
Loaded: loaded (/lib/systemd/system/snmpd.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2021-05-14 06:36:48 UTC; 3min 22s ago
Main PID: 36724 (snmpd)
Tasks: 1 (limit: 4691)
Memory: 8.7M
CGroup: /system.slice/snmpd.service
└─36724 /usr/sbin/snmpd -LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid
May 14 06:36:48 ubuntu2004 systemd[1]: Starting Simple Network Management Protocol (SNMP) Daemon....
May 14 06:36:48 ubuntu2004 systemd[1]: Started Simple Network Management Protocol (SNMP) Daemon..By default, SNMP does not allow retrieving all available SNMP information. So you will need to edit the SNMP default configuration file and make some changes so we can retrieve all information using the SNMPWALK command.
nano /etc/snmp/snmpd.conf
Find the following lines:
rocommunity public default -V systemonly
rocommunity6 public default -V systemonly
And, replace them with the following lines:
rocommunity public default
rocommunity6 public default
Save and close the file then restart the SNMP service to apply the changes:
systemctl restart snmpd
Now, open your command-line interface and print help information of SNMPWALK command as shown below:
snmpwalk -h
You should get the following output:
USAGE: snmpwalk [OPTIONS] AGENT [OID]
Version: 5.8
Web: http://www.net-snmp.org/
Email: net-snmp-coders@lists.sourceforge.net
OPTIONS:
-h, --help display this help message
-H display configuration file directives understood
-v 1|2c|3 specifies SNMP version to use
-V, --version display package version number
SNMP Version 1 or 2c specific
-c COMMUNITY set the community string
SNMP Version 3 specific
-a PROTOCOL set authentication protocol (MD5|SHA|SHA-224|SHA-256|SHA-384|SHA-512)
-A PASSPHRASE set authentication protocol pass phrase
-e ENGINE-ID set security engine ID (e.g. 800000020109840301)
-E ENGINE-ID set context engine ID (e.g. 800000020109840301)
-l LEVEL set security level (noAuthNoPriv|authNoPriv|authPriv)
-n CONTEXT set context name (e.g. bridge1)
-u USER-NAME set security name (e.g. bert)
-x PROTOCOL set privacy protocol (DES|AES)
-X PASSPHRASE set privacy protocol pass phrase
-Z BOOTS,TIME set destination engine boots/time
General communication options
-r RETRIES set the number of retries
-t TIMEOUT set the request timeout (in seconds)
Debugging
-d dump input/output packets in hexadecimal
-D[TOKEN[,...]] turn on debugging output for the specified TOKENs
(ALL gives extremely verbose debugging output)
Install SNMP and SNMPWALK on Windows 10 Windows Server 2016 and Windows Server 2019
In this section, we will show you how to install SNMP and SNMPWALK on the Windows operating system.
Follow the below steps to install SNMP on Windows:
Step 1 – Open the Control Panel as shown below:
Step 2 – Click on the Programs and Features you should see in the page below:
Step 3 – Click on the Turn Windows features on or off.
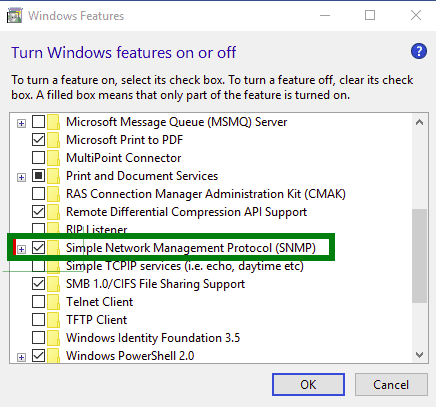
Step 4 – On Windows 10, select Simple Network Management Protocol (SNMP) and install it.
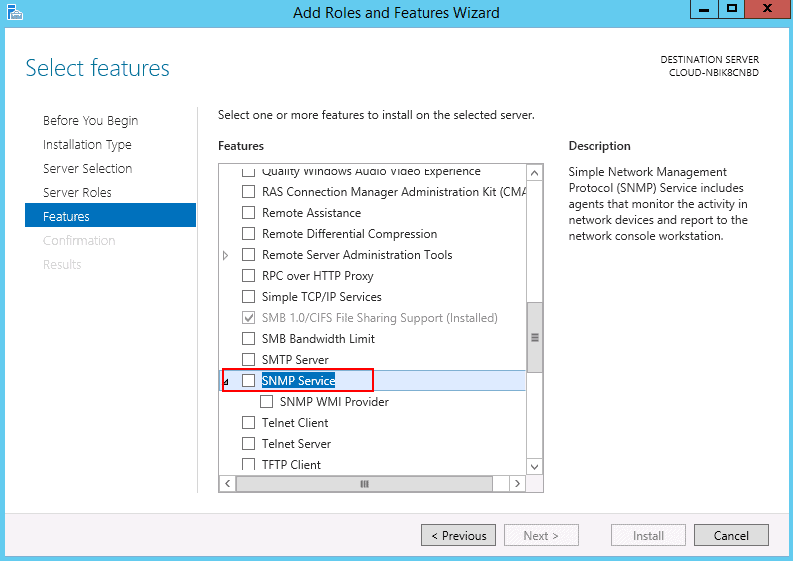
Step 5 – On Windows Server 2016 and 2019, click on the Add Roles and Features Wizard until you reach the Features section then select SNMP service.
Step 6 – Install SNMP Service.
This will automatically install the SNMP service on your Windows system.
After installing SNMP, you will need to configure it.
Follow the below steps to configure the SNMP service:
Step 1 – Press Windows + R and type services.msc as shown below:
Step 2 – Press OK to open the Windows service configuration wizard.
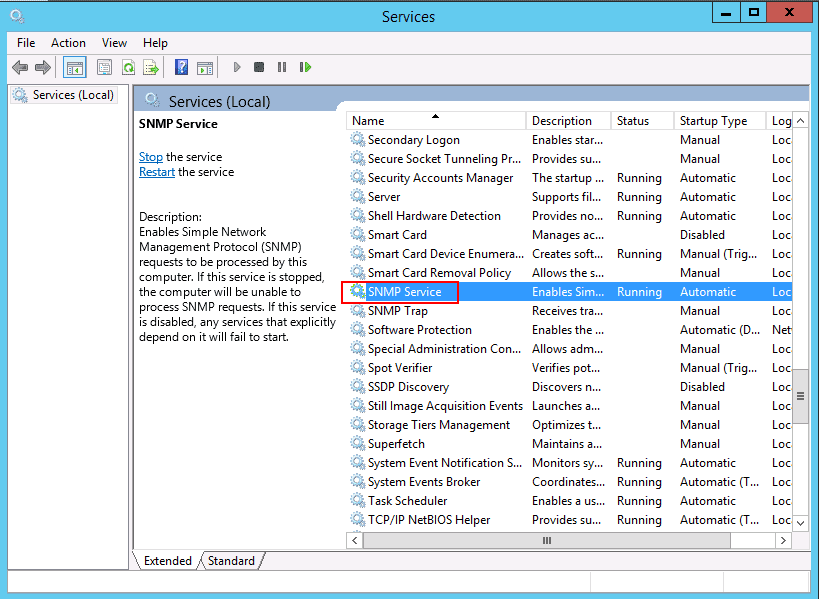
Step 3 – Select the SNMP service, right-click and click on the properties as shown below:
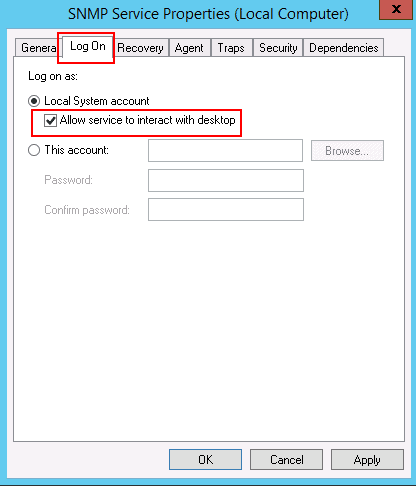
Step 4 – In the Log On tab, select “Allow service to interact with desktop”. Then click on the Agent tab as shown below:
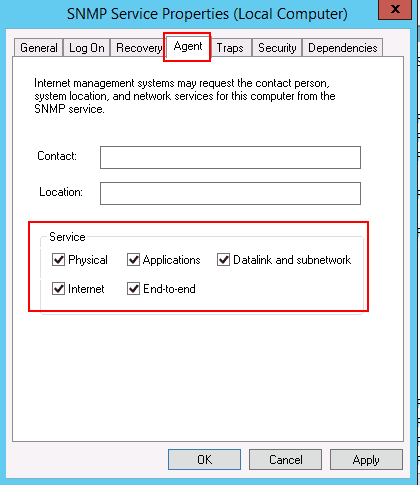
Step 5 – Select all services and click on the Security tab as shown below:
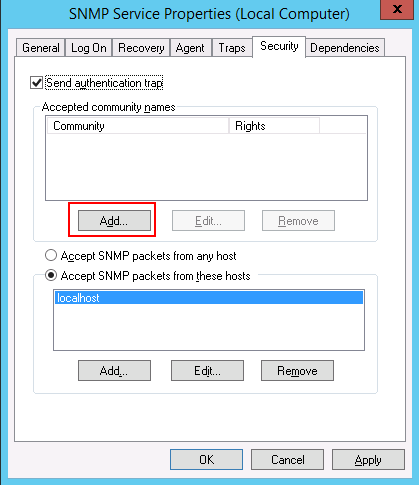
Step 6 – Click on the Add button. You should see the following screen:
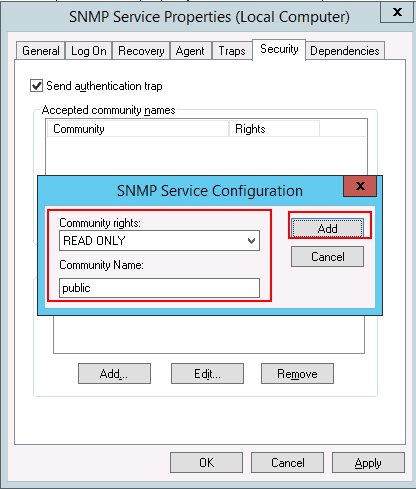
Step 7 – Provide community rights and community name then click on the Add button. You should see the following page:
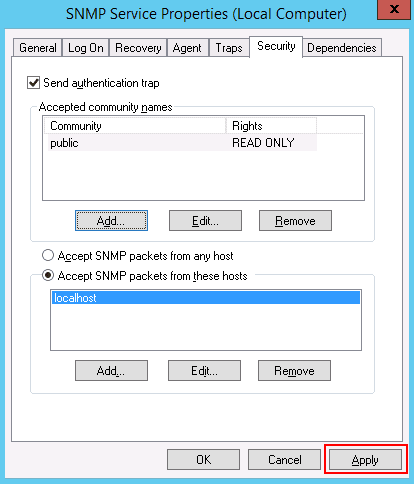
Step 8 – Click on the Apply button to apply the changes.
For full SNMP functionality, you will need to download the SolarWinds MIB Walk module from their Engineer’s Toolset to your windows system. However, you can download the free snmpwalk files from the SourceForge website and follow along with this post.
Once SNMPWALK is downloaded, extract it to the download folder. You can now use snmpwalk.exe to launch and use the SNMPWALK.
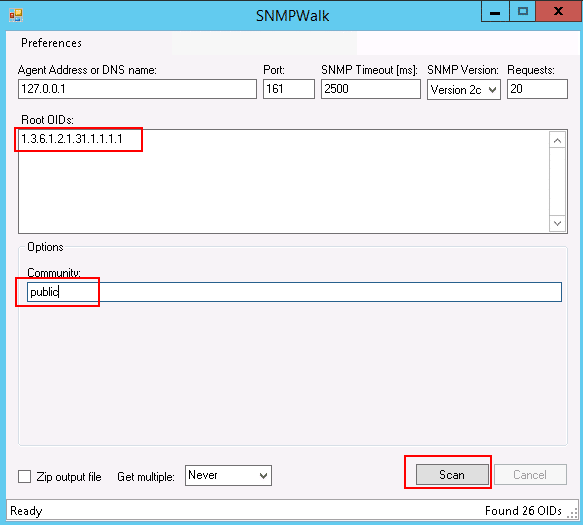
Provide your agent address, OID, community, and click the Scan button. This will generate a complete system information report based on the OID.
How to Use SNMPWALK to Retrieve the System Information
In this section, we will show you how to use the SNMPWALK command in Linux to retrieve the system information.
You can use the following options with the SNMPWALK command to retrieve the system information:
- -v: Specify the SNMP version.
- -c: Specify the community string which you have configured on the SNMP.
- hostname: Specify the hostname or IP address of the system where the SNMP agent is installed.
- OID: Specify the OID to return all SNMP objects.
Now, open your command-line interface and run the following command to list all existing OIDs on the network..
snmpwalk -v 2c -c public localhost
You should get the following output:
iso.3.6.1.2.1.1.1.0 = STRING: "Linux ubuntu2004 5.4.0-29-generic #33-Ubuntu SMP Wed Apr 29 14:32:27 UTC 2020 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (19907) 0:03:19.07
iso.3.6.1.2.1.1.4.0 = STRING: "Me <me@example.org>"
iso.3.6.1.2.1.1.5.0 = STRING: "ubuntu2004"
iso.3.6.1.2.1.1.6.0 = STRING: "Sitting on the Dock of the Bay"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.2.1 = OID: iso.3.6.1.6.3.10.3.1.1
iso.3.6.1.2.1.1.9.1.2.2 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.2.1.1.9.1.2.3 = OID: iso.3.6.1.6.3.15.2.1.1
iso.3.6.1.2.1.1.9.1.2.4 = OID: iso.3.6.1.6.3.1
iso.3.6.1.2.1.1.9.1.2.5 = OID: iso.3.6.1.6.3.16.2.2.1
iso.3.6.1.2.1.1.9.1.2.6 = OID: iso.3.6.1.2.1.49
iso.3.6.1.2.1.1.9.1.2.7 = OID: iso.3.6.1.2.1.4
iso.3.6.1.2.1.1.9.1.2.8 = OID: iso.3.6.1.2.1.50
iso.3.6.1.2.1.1.9.1.2.9 = OID: iso.3.6.1.6.3.13.3.1.3
iso.3.6.1.2.1.1.9.1.2.10 = OID: iso.3.6.1.2.1.92
iso.3.6.1.2.1.1.9.1.3.1 = STRING: "The SNMP Management Architecture MIB."
iso.3.6.1.2.1.1.9.1.3.2 = STRING: "The MIB for Message Processing and Dispatching."
iso.3.6.1.2.1.1.9.1.3.3 = STRING: "The management information definitions for the SNMP User-based Security Model."
iso.3.6.1.2.1.1.9.1.3.4 = STRING: "The MIB module for SNMPv2 entities"
iso.3.6.1.2.1.1.9.1.3.5 = STRING: "View-based Access Control Model for SNMP."
iso.3.6.1.2.1.1.9.1.3.6 = STRING: "The MIB module for managing TCP implementations"
iso.3.6.1.2.1.1.9.1.3.7 = STRING: "The MIB module for managing IP and ICMP implementations"
iso.3.6.1.2.1.1.9.1.3.8 = STRING: "The MIB module for managing UDP implementations"
iso.3.6.1.2.1.1.9.1.3.9 = STRING: "The MIB modules for managing SNMP Notification, plus filtering."
iso.3.6.1.2.1.1.9.1.3.10 = STRING: "The MIB module for logging SNMP Notifications."
You can see the different OIDs in the above output. The typical format of an OID is shown below:
1.3.6.1.4.1.2021.10.1
A brief explanation of the most commonly used OIDs are shown below:
- 1 – ISO – International Organization for Standardization (ISO)
- 3 – org – Organizations according to ISO/IEC 6523-2
- 6 – dod – US Department of Defense (DOD)
- 1 – Internet protocol
- 4 – Private – Device manufactured by a private company
- 2021 – It is the particular device manufacturer number.
To get the hostname of the system, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.1.5
You should get the following output:
iso.3.6.1.2.1.1.5.0 = STRING: "ubuntu2004"
To get the hostname and kernel information, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.1.1
You should get the following output:
iso.3.6.1.2.1.1.1.0 = STRING: "Linux ubuntu2004 5.4.0-29-generic #33-Ubuntu SMP Wed Apr 29 14:32:27 UTC 2020 x86_64"
To get the network interface information, run the following command:
snmpwalk -v 2c 127.0.0.1 -c public .1.3.6.1.2.1.2.2.1.1
You should get the following output:
iso.3.6.1.2.1.2.2.1.1.1 = INTEGER: 1
iso.3.6.1.2.1.2.2.1.1.2 = INTEGER: 2
iso.3.6.1.2.1.2.2.1.1.3 = INTEGER: 3
To get the MAC address information, run the following command:
snmpwalk -v 2c 127.0.0.1 -c public .1.3.6.1.2.1.2.2.1.6
You should get the following output:
iso.3.6.1.2.1.2.2.1.6.1 = ""
iso.3.6.1.2.1.2.2.1.6.2 = Hex-STRING: 00 00 2D 3A 26 A4
iso.3.6.1.2.1.2.2.1.6.3 = Hex-STRING: 00 00 0A 3A 26 A4
To get a list of all network interface, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.31.1.1.1.1
You should get the following output:
iso.3.6.1.2.1.31.1.1.1.1.1 = STRING: "lo"
iso.3.6.1.2.1.31.1.1.1.1.2 = STRING: "eth0"
iso.3.6.1.2.1.31.1.1.1.1.3 = STRING: "eth1"
To get an IP address of the system, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.4.20.1.1
You should get the following output:
iso.3.6.1.2.1.4.20.1.1.45.58.38.164 = IpAddress: 45.58.38.164
iso.3.6.1.2.1.4.20.1.1.127.0.0.1 = IpAddress: 127.0.0.1
To get the Subnet Mask of the system, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.4.20.1.3
You should get the following output:
iso.3.6.1.2.1.4.20.1.3.45.58.38.164 = IpAddress: 255.255.255.0
iso.3.6.1.2.1.4.20.1.3.127.0.0.1 = IpAddress: 255.0.0.0
To get the CPU information, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.25.3.2.1.3 |grep -i cpu
You should get the following output:
iso.3.6.1.2.1.25.3.2.1.3.196608 = STRING: "GenuineIntel: QEMU Virtual CPU version 2.5+"
iso.3.6.1.2.1.25.3.2.1.3.196609 = STRING: "GenuineIntel: QEMU Virtual CPU version 2.5+"
To get the system load information, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.4.1.2021.10.1
You should get the following output:
iso.3.6.1.4.1.2021.10.1.1.1 = INTEGER: 1
iso.3.6.1.4.1.2021.10.1.1.2 = INTEGER: 2
iso.3.6.1.4.1.2021.10.1.1.3 = INTEGER: 3
iso.3.6.1.4.1.2021.10.1.2.1 = STRING: "Load-1"
iso.3.6.1.4.1.2021.10.1.2.2 = STRING: "Load-5"
iso.3.6.1.4.1.2021.10.1.2.3 = STRING: "Load-15"
iso.3.6.1.4.1.2021.10.1.3.1 = STRING: "0.00"
iso.3.6.1.4.1.2021.10.1.3.2 = STRING: "0.01"
iso.3.6.1.4.1.2021.10.1.3.3 = STRING: "0.00"
iso.3.6.1.4.1.2021.10.1.4.1 = STRING: "12.00"
iso.3.6.1.4.1.2021.10.1.4.2 = STRING: "12.00"
iso.3.6.1.4.1.2021.10.1.4.3 = STRING: "12.00"
iso.3.6.1.4.1.2021.10.1.5.1 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.5.2 = INTEGER: 1
iso.3.6.1.4.1.2021.10.1.5.3 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.6.1 = Opaque: Float: 0.000000
iso.3.6.1.4.1.2021.10.1.6.2 = Opaque: Float: 0.010000
iso.3.6.1.4.1.2021.10.1.6.3 = Opaque: Float: 0.000000
iso.3.6.1.4.1.2021.10.1.100.1 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.100.2 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.100.3 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.101.1 = ""
iso.3.6.1.4.1.2021.10.1.101.2 = ""
iso.3.6.1.4.1.2021.10.1.101.3 = ""
To get the system uptime information, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.1.3.0
You should get the following output:
iso.3.6.1.2.1.1.3.0 = Timeticks: (66282) 0:11:02.82
Conclusion
In the above post, you learned how to install and use SNMP and SNMPWALK on Windows and Linux to get the system information across the connected devices. I hope this will help you to monitor the network devices.
SNMPWALK FAQs
What is a snmpwalk tool?
SNMPWALK is a process of exploring the Management Information Base (MIB) structure of an SNMP report. The MIB has a tree structure that is denoted by a dot-notation number and the “walk” crawls through these numbers, recreating the tree. An SNMPWALK tool can construct a MIB tree by mapping the relationship between the values in a MIB. Each number that identifies a node on the MIB tree will have a label and a value. The OID (Object ID) is a reference code for the label.
Is SNMP v3 TCP or UDP?
All versions of SNMP use the same ports – there are two and they are both UDP. Regular SNMP transactions involve the SNMP Manager sending out a broadcasted request, to which the SNMP device agents reply with a MIB. This communication occurs on UDP port 161. The SNMP agent can send out a warning message without waiting for a request. This is called a Trap and it goes to UDP port 162.
What is OID in Linux?
OID is short for Object ID. It is the level code that identifies a node in a tree structure that is used for reporting in SNMP. An SNMP report is called a Management Information Base (MIB). It has a set number of fields that are identified by OIDs. The OID uses a dot-notation format to indicate the inheritance of a node on the tree.




