| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1 Windows 2016 and 10 Windows Server 2019 and 2022 Windows Server 2025 |
|
Category • Subcategory |
Logon/Logoff • Logon |
| Type | Success |
|
Corresponding events in Windows 2003 and before |
528 , 540
|
4624: An account was successfully logged on
On this page
- Description of this event
- Field level details
- Examples
This is a highly valuable event since it documents each and every successful attempt to logon to the local computer regardless of logon type, location of the user or type of account. You can tie this event to logoff events 4634 and 4647 using Logon ID.
Win2012 adds the Impersonation Level field as shown in the example.
Win2016/10 add further fields explained below.
Free Security Log Resources by Randy
- Free Security Log Quick Reference Chart
- Windows Event Collection: Supercharger Free Edtion
- Free Active Directory Change Auditing Solution
- Free Course: Security Log Secrets
Description Fields in
4624
Subject:
Identifies the account that requested the logon — NOT the user who just logged on. Subject is usually Null or one of the Service principals and not usually useful information. See New Logon for who just logged on to the sytem.
- Security ID
- Account Name
- Account Domain
- Logon ID
Logon Information:
- Logon Type: See below
Remaining logon information fields are new to Windows 10/2016
- Restricted Admin Mode: Normally «-«.»Yes» for incoming Remote Desktop Connections where the client specified /restrictedAdmin on the command line. Restricted admin mode is an important way to limit the spread of admin credentials in ways they can be harvested by malware using pass-the-hash and related techniques. You should only see with for logon type 10. When you remote desktop into a server with /restrictedAdmin you get full authority on that server but it doesn’t carry with you if you access other systems from within that RDP session. This field allows you to detect RDP sessions that fail to use restricted admin mode.
- Virtual Account: Normally «No». This will be Yes in the case of services configured to logon with a «Virtual Account». Virtual Accounts only come up in Service logon types (type 5), when Windows starts a logon session in connection with a service starting up. You can configure services to run as a virtual account which is what Microsoft calls a «managed local account». They’re «domain» is «NT Service» as in an instance of MS SQL Server named Supercharger running as NT SERVICE\MSSQL$SUPERCHARGER.
- Elevated Token: Yes or No. It will be Yes if the user is a member of Administrators — kind of… The «kind of» applies to interactive logons, when you are an admin and you have User Account Control (UAC) enabled. Then when you logon you actually get 2 logon sessions. One without the Administrators SID and related privileges in your security token and another session with all that authority. Everything you do happens under the unprivileged logon session until you attempt to run something requiring admin authority. After you approve the UAC dialog box, Windows runs that one operation under the other logon sesson. So in the log you will see 2 of these events, one where this field is Yes and other No. The 2 logon sessions are connected by the Linked Logon ID described below.
Remaining logon information fields are new to Windows 2025
- Remote Credential Guard: Normally «-«.
Logon Type:
This is a valuable piece of information as it tells you HOW the user just logged on:
|
Logon Type |
Description |
| 2 | Interactive (logon at keyboard and screen of system) |
| 3 | Network (i.e. connection to shared folder on this computer from elsewhere on network) |
| 4 | Batch (i.e. scheduled task) |
| 5 | Service (Service startup) |
| 7 | Unlock (i.e. unnattended workstation with password protected screen saver) |
| 8 | NetworkCleartext (Logon with credentials sent in the clear text. Most often indicates a logon to IIS with «basic authentication») See this article for more information. |
| 9 | NewCredentials such as with RunAs or mapping a network drive with alternate credentials. This logon type does not seem to show up in any events. If you want to track users attempting to logon with alternate credentials see 4648. MS says «A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity, but uses different credentials for other network connections.» |
| 10 | RemoteInteractive (Terminal Services, Remote Desktop or Remote Assistance) |
| 11 | CachedInteractive (logon with cached domain credentials such as when logging on to a laptop when away from the network) |
Impersonation Level: (Win2012 and later)
From MSDN
| Anonymous | Anonymous COM impersonation level that hides the identity of the caller. Calls to WMI may fail with this impersonation level. |
| Default | Default impersonation. |
| Delegate | Delegate-level COM impersonation level that allows objects to permit other objects to use the credentials of the caller. This level, which will work with WMI calls but may constitute an unnecessary security risk, is supported only under Windows 2000. |
| Identify | Identify-level COM impersonation level that allows objects to query the credentials of the caller. Calls to WMI may fail with this impersonation level. |
| Impersonate | Impersonate-level COM impersonation level that allows objects to use the credentials of the caller. This is the recommended impersonation level for WMI calls. |
New Logon:
The user who just logged on is identified by the Account Name and Account Domain. You can determine whether the account is local or domain by comparing the Account Domain to the computer name. If they match, the account is a local account on that system, otherwise a domain account.
- Security ID: the SID of the account
- Account Name: Logon name of the account
- Account Domain: Domain name of the account in either the DNS name (can be upper or lowercase) or pre-Win2k NETBIOS domain name. In the case of special subjects (well known security principals) like SYSTEM, LOCAL SERVICE, NETWORK SERVICE, ANONYMOUS LOGON this field will be «NT AUTHORITY». It can also be «NT Service» as in the case of virtual accounts for services. See above. Finally, if the account is a local account, this field will be the name of the computer.
- Logon ID: a semi-unique (unique between reboots) number that identifies the logon session just initiated. Any events logged subsequently during this logon session will report the same Logon ID through to the logoff event 4647 or 4634.
- Linked Login ID: (Win2016/10) This is relevant to User Account Control and interactive logons. When an admin logs on interactively to a system with UAC enabled, Windows actually creates 2 logon sessions — one with and one without privilege. This is called a split token and this fields links the 2 sessions to each other. See Elevated Token above.
- Network Account Name: (Win2016/10) This will be «-» unless the logon type is NewCredentials aka 9, then it will be the user name that is used for outbound network connections.
- Network Account Domain: (Win2016/10) see above
- Logon GUID: Supposedly you should be able to correlate logon events on this computer with corresonding authentication events on the domain controller using this GUID. Such as linking 4624 on the member computer to 4769 on the DC. But the GUIDs do not match between logon events on member computers and the authentication events on the domain controller.
Process Information:
- Process ID is the process ID specified when the executable started as logged in 4688.
- Process Name: identifies the program executable that processed the logon. This is one of the trusted logon processes identified by 4611.
Network Information:
This section identifies WHERE the user was when he logged on. Of course if logon is initiated from the same computer this information will either be blank or reflect the same local computers.
- Workstation Name: the computer name of the computer where the user is physically present in most cases unless this logon was intitiated by a server application acting on behalf of the user. Workstation may also not be filled in for some Kerberos logons since the Kerberos protocol doesn’t really care about the computer account in the case of user logons and therefore lacks any field for carrying workstation name in the ticket request message.
- Source Network Address: the IP address of the computer where the user is physically present in most cases unless this logon was intitiated by a server application acting on behalf of the user. If this logon is initiated locally the IP address will sometimes be 127.0.0.1 instead of the local computer’s actual IP address. This field is also blank sometimes because Microsoft says «Not every code path in Windows Server 2003 is instrumented for IP address, so it’s not always filled out.»
- Source Port: identifies the source TCP port of the logon request which seems useless since with most protocols source ports are random.
Detailed Authentication Information:
- Logon Process: (see 4611) CredPro indicates a logon initiated by User Account Control
- Authentication Package: (see 4610 or 4622)
- Transited Services: This has to do with server applications that need to accept some other type of authentication from the client and then transition to Kerberos for accessing other resources on behalf of the client. See http://msdn.microsoft.com/msdnmag/issues/03/04/SecurityBriefs/. MS says: Transmitted services are populated if the logon was a result of a S4U (Service For User) logon process. S4U is a Microsoft extension to the Kerberos Protocol to allow an application service to obtain a Kerberos service ticket on behalf of a user – most commonly done by a front-end website to access an internal resource on behalf of a user. For more information about S4U, see https://msdn.microsoft.com/en-us/library/cc246072.aspx
- Package name: If this logon was authenticated via the NTLM protocol (instead of Kerberos for instance) this field tells you which version of NTLM was used. See security option «Network security: LAN Manager authentication level». This field only populated if Authentication Package = NTLM. Possible values: “NTLM V1”, “NTLM V2”, “LM”
- Key Length: Length of key protecting the «secure channel». See security option «Domain Member: Require strong (Windows 2000 or later) session key». If value is 0 this would indicate security option «Domain Member: Digitally encrypt secure channel data (when possible)» failed. MS says the length of NTLM Session Security key. Typically it has 128 bit or 56 bit length. This parameter is always 0 if “Authentication Package” = “Kerberos”, because it is not applicable for Kerberos protocol. This field will also have “0” value if Kerberos was negotiated using Negotiate authentication package.
Supercharger Free Edition
Centrally manage WEC subscriptions.
Free.
Examples of 4624
Windows 11 and 2025
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: DESKTOP-LLHJ389$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon Information:
Logon Type: 7
Restricted Admin Mode: —
Remote Credential Guard: —
Virtual Account: No
Elevated Token: No
Impersonation Level: Impersonation
New Logon:
Security ID: AzureAD\RandyFranklinSmith
Account Name: rsmith@montereytechgroup.com
Account Domain: AzureAD
Logon ID: 0xFD5113F
Linked Logon ID: 0xFD5112A
Network Account Name: —
Network Account Domain: —
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x30c
Process Name: C:\Windows\System32\lsass.exe
Network Information:
Workstation Name: DESKTOP-LLHJ389
Source Network Address: —
Source Port: —
Detailed Authentication Information:
Logon Process: Negotiat
Authentication Package: Negotiate
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
Windows 10 and 2016/2019/2022
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: DESKTOP-LLHJ389$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon Information:
Logon Type: 7
Restricted Admin Mode: —
Remote Credential Guard: —
Virtual Account: No
Elevated Token: No
Impersonation Level: Impersonation
New Logon:
Security ID: AzureAD\RandyFranklinSmith
Account Name: rsmith@montereytechgroup.com
Account Domain: AzureAD
Logon ID: 0xFD5113F
Linked Logon ID: 0xFD5112A
Network Account Name: —
Network Account Domain: —
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x30c
Process Name: C:\Windows\System32\lsass.exe
Network Information:
Workstation Name: DESKTOP-LLHJ389
Source Network Address: —
Source Port: —
Detailed Authentication Information:
Logon Process: Negotiat
Authentication Package: Negotiate
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
Win2012
An account was successfully logged on.
Subject:
Security ID: NULL SID
Account Name: —
Account Domain: —
Logon ID: 0x0
Logon Type: 3
Impersonation Level: Impersonation
New Logon:
Security ID: LB\DEV1$
Account Name: DEV1$
Account Domain: LB
Logon ID: 0x894B5E95
Logon GUID: {f09e5f81-9f19-5f11-29b8-8750c7c02be3}
Process Information:
Process ID: 0x0
Process Name: —
Network Information:
Workstation Name:
Source Network Address: 10.42.1.161
Source Port: 59752
Detailed Authentication Information:
Logon Process: Kerberos
Authentication Package: Kerberos
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
Win2008
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: WIN-R9H529RIO4Y$
Account Domain: WORKGROUP
Logon ID: 0x3e7
Logon Type:10
New Logon:
Security ID: WIN-R9H529RIO4Y\Administrator
Account Name: Administrator
Account Domain: WIN-R9H529RIO4Y
Logon ID: 0x19f4c
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x4c0
Process Name: C:\Windows\System32\winlogon.exe
Network Information:
Workstation Name: WIN-R9H529RIO4Y
Source Network Address: 10.42.42.211
Source Port: 1181
Detailed Authentication Information:
Logon Process: User32
Authentication Package: Negotiate
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection
- The Changing Landscape of Authentication and Logon Tracking in Hybrid Environments of Entra and AD
|
Инструкция по отключению сбора и отправки в Microsoft диагностических данных и статистики использования Windows 11.
Что такое телеметрия Windows. Зачем отключать
Данные телеметрии нужны Microsoft для улучшения Windows. Телеметрия интегрирована в операционную систему. Автоматически собирает статистику и отправляет в Microsoft. Основные собираемых данных:
- использование ОС;
- работа с программами;
- посещение сайтов.
Заботитесь о конфиденциальности и не желаете ни с кем делиться сведениями об использовании ноутбука или настольного ПК — дезактивируйте сбор и отправку данных. Телеметрию также отключают для снижения нагрузки на сетевое соединение. Постоянная передача данных повышает использование интернет-трафика. Пользователей все чаще беспокоит чрезмерный и интерес к данным, которые человек вполне может считать личными. Зачем кому-то постороннему знать, за какую команду вы болеете. Ранее рассказывал в «Блоге системного администратора» способы отключить слежку Google:
Отключите телеметрию в редакторе локальных групповых политик
Редактор локальных групповых политик (Group Policy Editor) встроен в версии Windows Pro и Корпоративной. Недоступен в Домашней Windows Home.
Нажмите на клавиатуре Win + R, чтобы открыть окно «Выполнить». Введите gpedit.msc в поле справа от надписи «Открыть:». Нажмите «ОК» в нижней части окна.
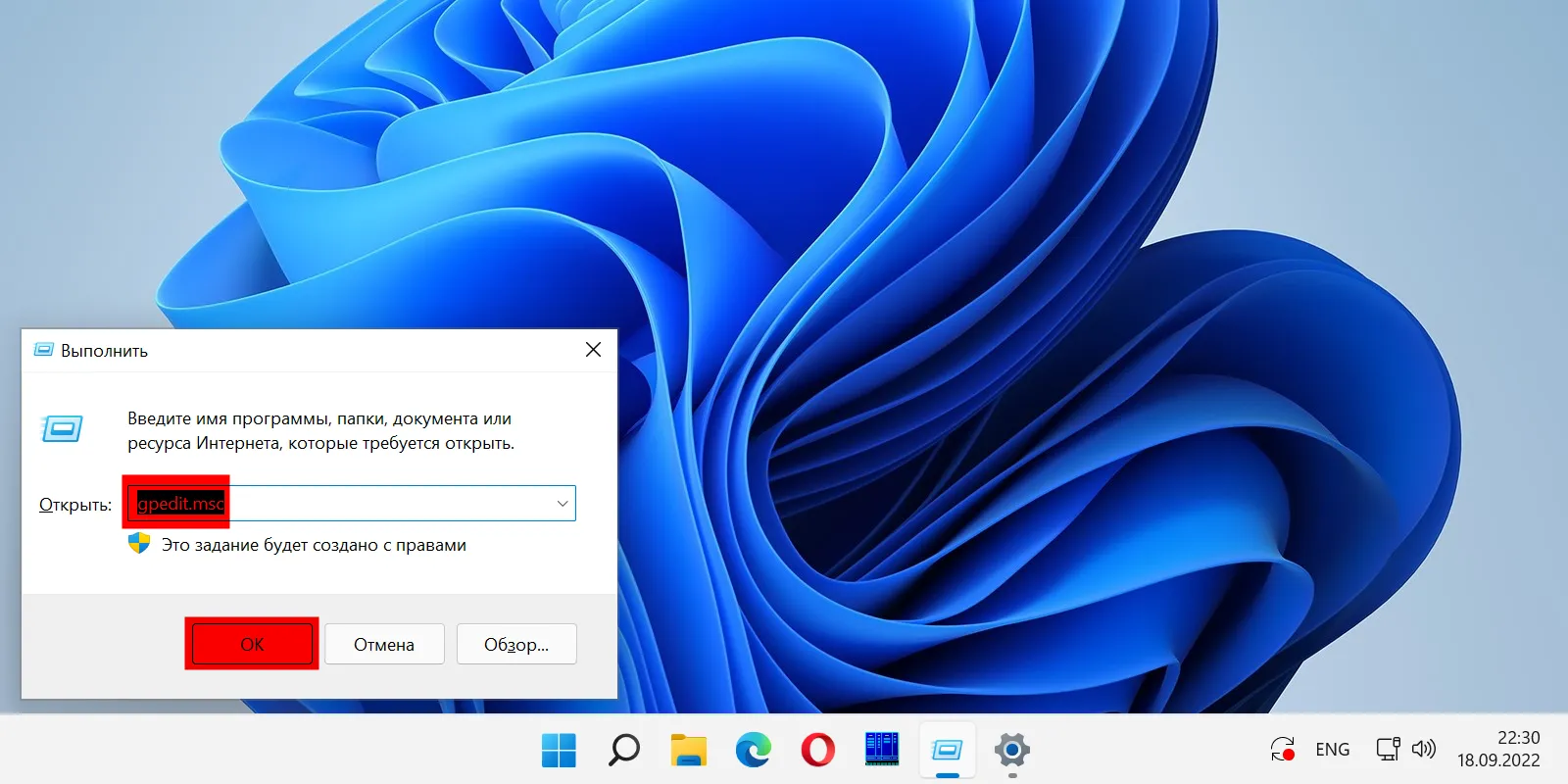
В левой панели окна редактора перейдите по следующему пути:
Конфигурация компьютера > Административные шаблоны > Компоненты Windows
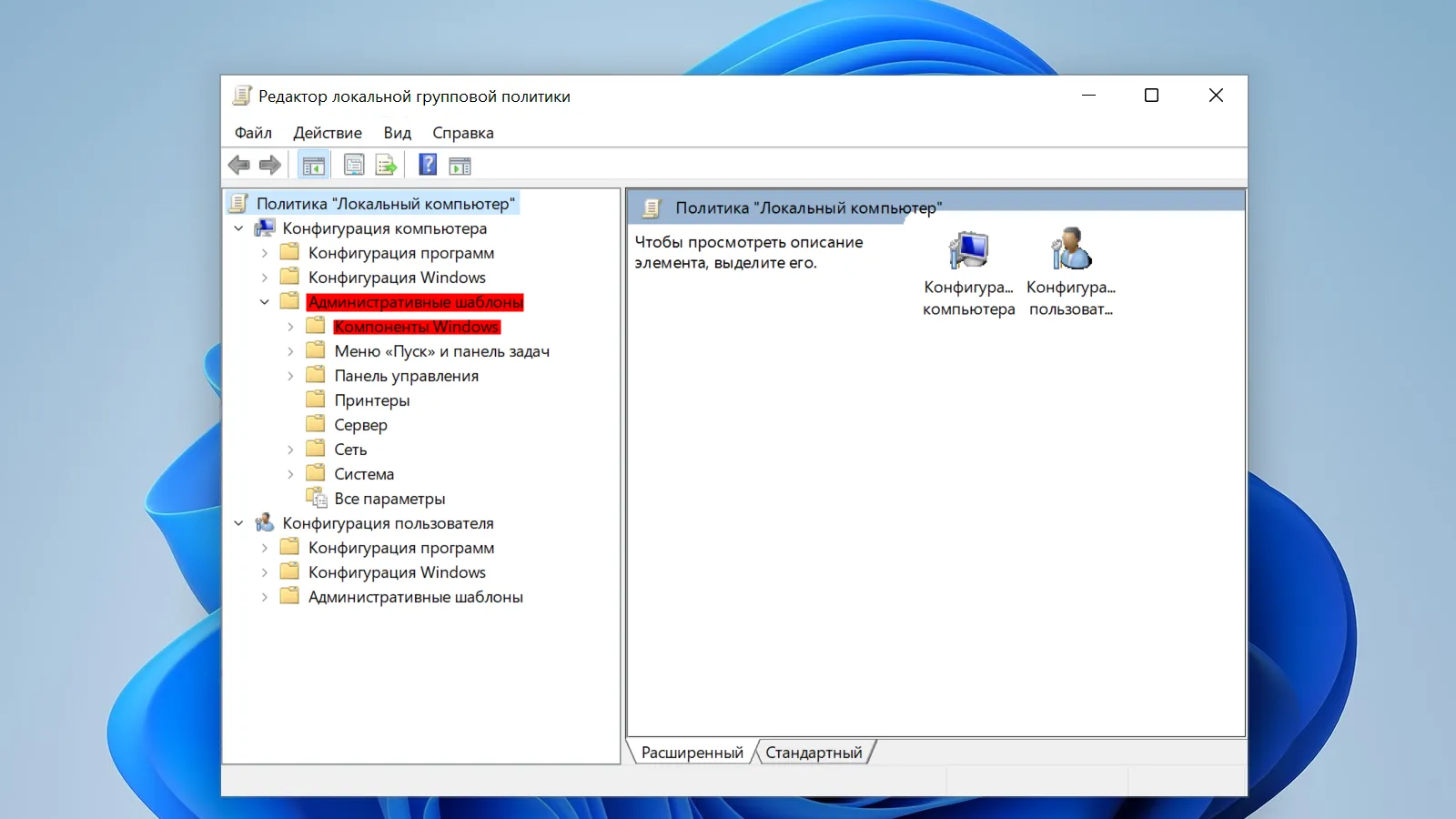
В «папке» «Компоненты Windows» находим «Сборки для сбора данных и предварительные сборки». В правой панели редактора дважды кликните по
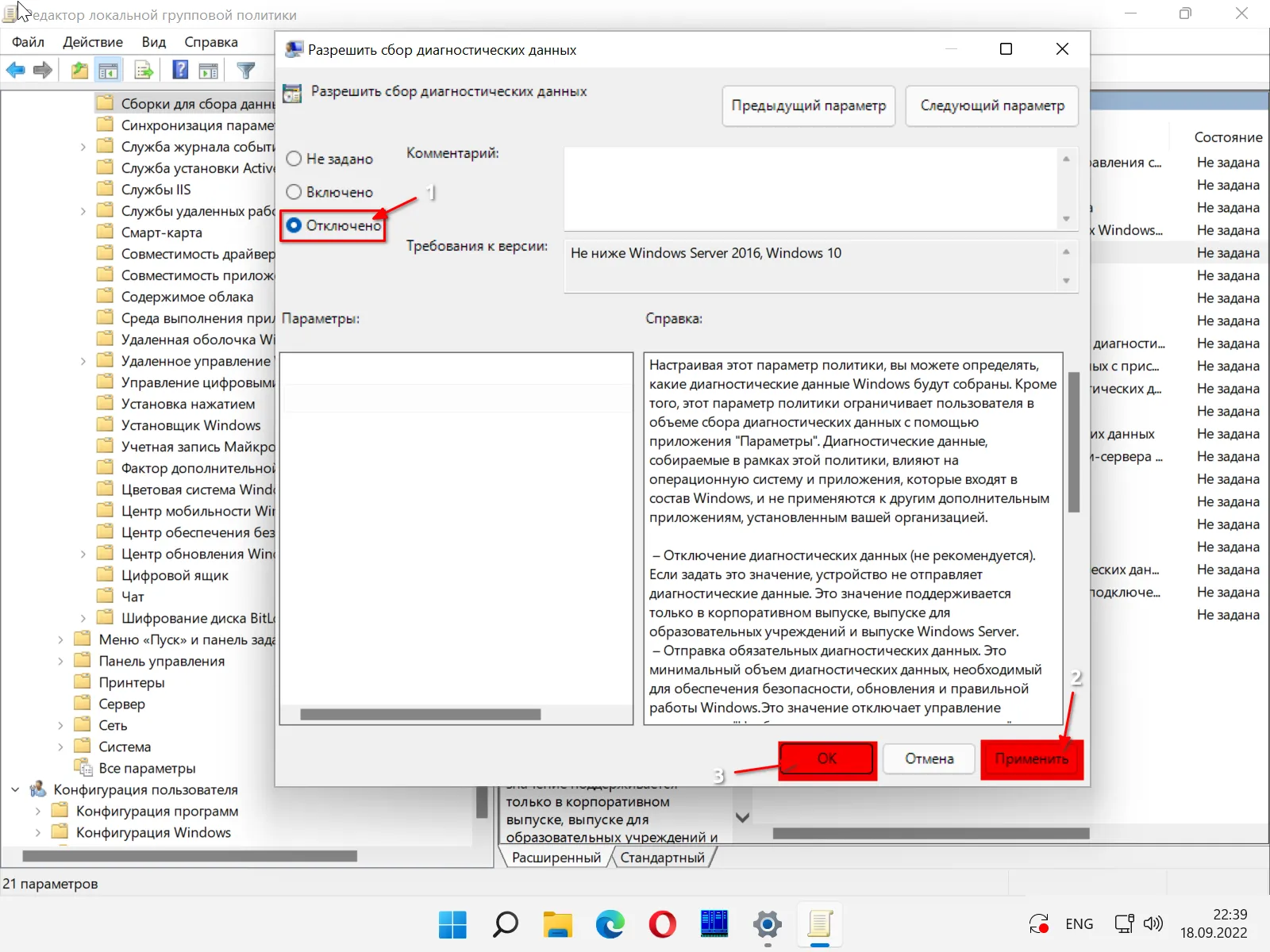
«Разрешить сборку диагностических данных».

Откроется новое окно, в котором нужно активировать опцию «Выключено». В нижней части окна «Разрешить сборку диагностических данных» нажмите кнопку «Применить», затем — «ОК» в нижней части малого окна.
Закройте редактор локальной групповой политики. Операционная система прекратит сбор диагностических данных. Используете Windows 7 или Vista и планируете перейти на Windows 11 или 10 — может не получиться скачать оригинальный ISO у Microsoft. Подсказал обходные методы загрузки образа операционной системы из России:
Отключаете ли вы телеметрию Windows? Напишите в комментариях.
5
3
голоса
Рейтинг статьи
Last Updated on May 9, 2025 by Satyendra

IT administrators need to have visibility over who and when computers were logged into for security and compliance reasons.
Event ID 4624 is an important event as it records all successful attempts to logon to the local computer regardless of logon type, user location or account type. This event can be linked to logoff events 4634 and 4647 using the Logon ID.
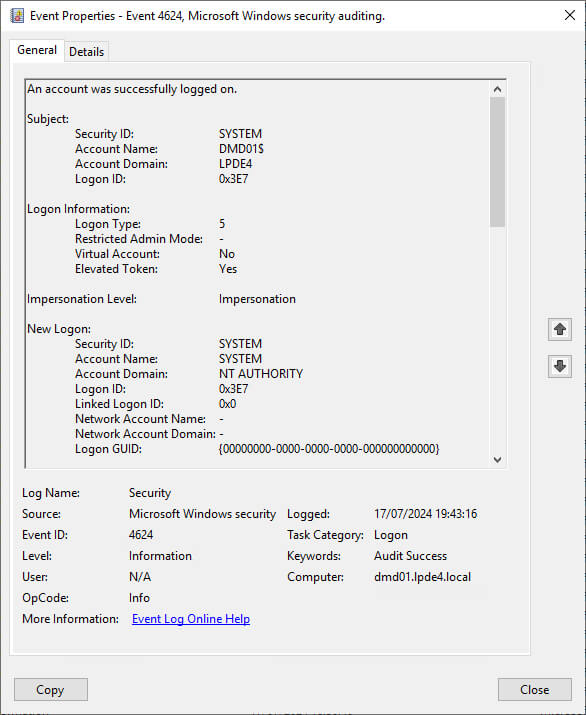
Event Fields Description
The key information that can be derived from Event 4624 includes:
Logon Type: This field reveals the kind of logon that occurred. There are a total of nine different types of logons, the most common logon types are: logon type 2 (interactive) and logon type 3 (network) and 5 (service startup). Any other logon type is a red flag.
New Logon: This section reveals the Account Name of the user for whom the new logon was created and the Logon ID, a hexadecimal value that helps correlate this event with other events.
10 Best Practices for Keeping Active Directory SecureFollow the 10 steps in this whitepaper and you will be in a far better position to keep your AD secure.
Download Whitepaper
| Logon Type | Description |
|---|---|
| 2 | -Interactive logon Occurs when a user logs on using a computer’s local keyboard and screen. |
| 3 | +Network logon |
| 4 | +Batch logon |
| 5 | +Service logon |
| 7 | +Unlock logon |
| 8 | +NetworkClearText logon |
| 9 | +NewCredentials logon |
| 10 | +RemoteInteractive logon |
| 11 | +CachedInteractive logon |
Other information that can be obtained from Event 4624 is as follows:
- The Subject section reveals the account on the local system (not the user) that requested the logon.
- The Impersonation Level section reveals the extent to which a process in the logon session can impersonate a client. Impersonation Levels determine the operations a server can perform in the client’s context.
- The Process Information section reveals details surrounding the process that attempted the logon.
- The Network Information section reveals where the user was when they logged on. If the logon was initiated from the same computer, this information will either be blank or reflect the local computer’s workstation name and source network address.
- The Authentication Information reveals information about the authentication package used for logon.
Why Monitor Successful Logons
There are a number of reasons why successful logins need to be monitored and these are explained below:
1. Security Strategy – Auditing successful logons in Active Directory is a key element of identity security and robust data security strategy. To prevent privilege abuse, organizations need to be vigilant about the actions which privileged users are performing and this starts with logons. This can help to detect abnormal and potentially malicious activity. Examples include a logon from an inactive or restricted account, users logging on outside of normal working hours, and concurrent logons to many resources.
2. Operational Needs – Monitoring logons helps to track user activity like user attendance, peak logon times, and so on.
3. Compliance Regulations – Compliance regulations may mandate that successful logon information is recorded.
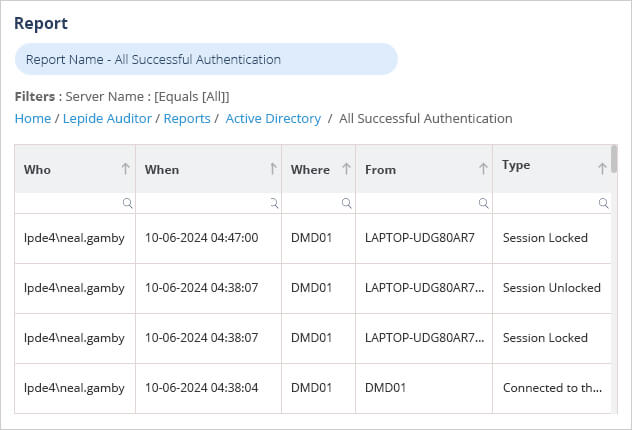
How Lepide Change Reporter (Free Tool) Helps
A more straightforward approach to monitoring successful logons it to use the Lepide Change Reporter. The Lepide Solution overcomes the limitations of native auditing and provides a simple but comprehensive way to track all the logon/logoff activities of Active Directory users.
The report below is the All Successful Authentications Report, one of the many reports included with the Lepide Change Reporter and shows all successful authentications for a specified time period:
Related Articles:
- Account Lockout Event ID 4740
- Windows Event ID 4774 – An Account was Mapped for Logon
- Windows Event ID 4773 – Kerberos Authentication
- Windows Event ID 4660 – An Object Was Deleted
- Active DirectoryEvent IDWindows

User account login failed? User account login success ? looks like the user has forgotten his password! Closing the incident as false-positive, Oh bad! stop doing this, We need to get some more insights on the events and understand much more about the user behaviors. Event ID 4625 will represent the user who has failed logins and the same user logged with correct credentials Event ID 4624 is logged.
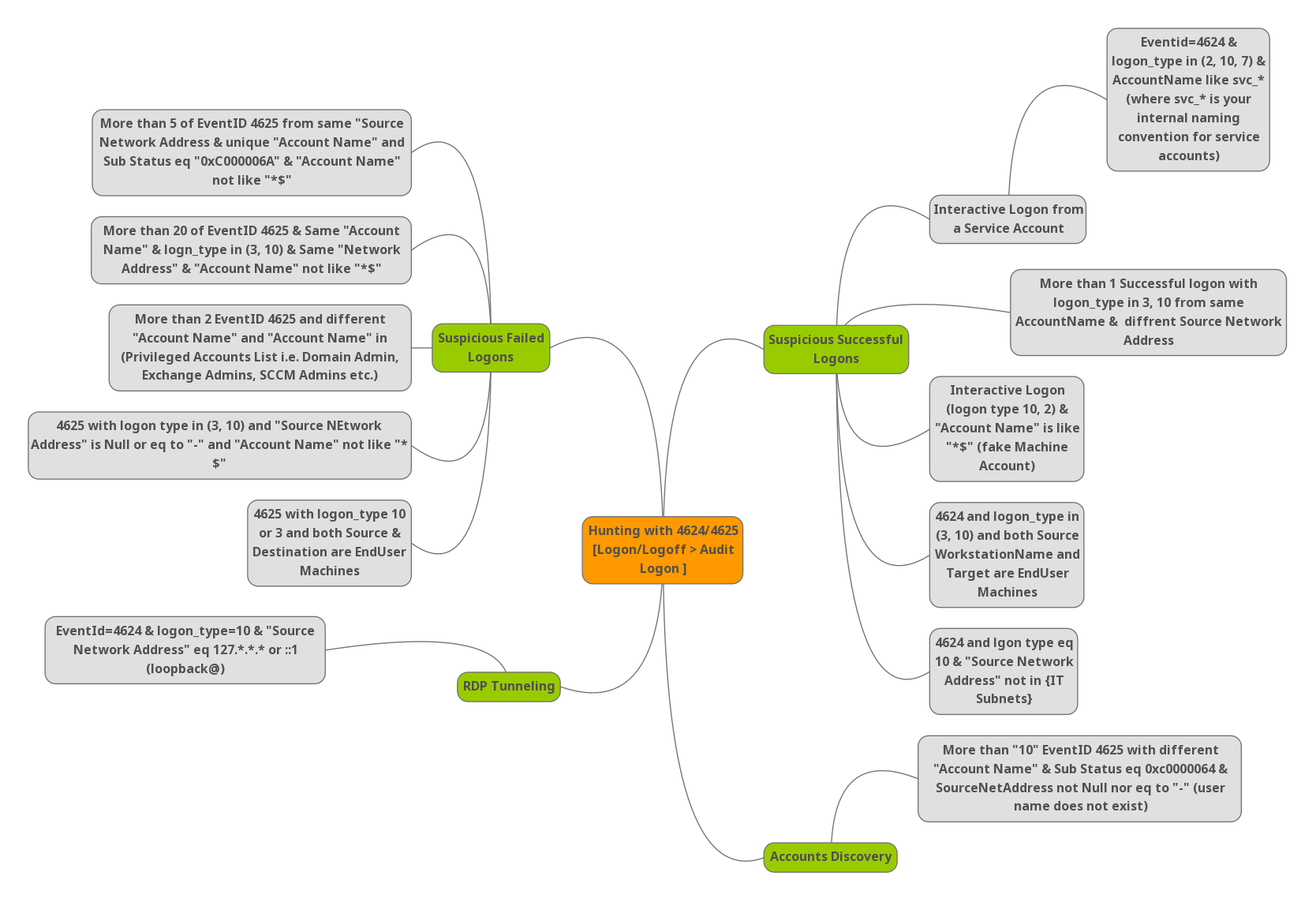
Dealing with such events will take much dwell time to analyze. Knowing and correlating the right logon types will save you hunt time. In this blog, we will see the mindmap of handling the will know events IDs ( 4625 & 4624 ) which is very normal with legitimate users also.
How to avoid those normal users’ noise in logs and hunt only the attacker’s activities. Please find the below cheatsheet.
Also Read : Threat Hunting using Sysmon – Advanced Log Analysis for Windows
Windows Logon Types :
| Logon Type | Logon Title | Description |
|---|---|---|
| 2 | Interactive | A user logged on to this computer. |
| 3 | Network | A user or computer logged on to this computer from the network. |
| 4 | Batch | Batch logon type is used by batch servers, where processes may be executing on behalf of a user without their direct intervention. |
| 5 | Service | Service was started by the Service Control Manager. |
| 7 | Unlock | This workstation was unlocked. |
| 8 | NetworkCleartext | A user logged on to this computer from the network. The user’s password was passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials do not traverse the network in plaintext (also called cleartext). |
| 9 | NewCredentials | A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity but uses different credentials for other network connections. |
| 10 | RemoteInteractive | A user logged on to this computer remotely using Terminal Services or Remote Desktop. |
| 11 | CachedInteractive | A user logged on to this computer with network credentials that were stored locally on the computer. The domain controller was not contacted to verify the credentials. |
Also Read: Threat Hunting using Firewall Logs – Soc Incident Response Procedure
Suspicious Failed Logons:
- Event ID 4625 is observed for 5 or more times with the sub status 0xC0000064 , Status code ( 0xC000006A ) says user name is correct but the password is wrong and account name not has the value $ , $ says ( Any username that ends with $ is a computer account. ) , In this case we are ignoring the computer account.
- More than 20 events seen for 4625 and the account types are ( 3 & 10 ) and traffic from same network address and account name not has the value $ , In this case our hunting case includes Type 3 ( A user or computer logged on to this computer from the network ) and Type 10 ( A user logged on to this computer remotely using Terminal Services or Remote Desktop )
- More than 2 Events for 4625 and the account names are different and it is privileged account list i.e, Exhange Admin etc.
- Event ID 4625 with logon type ( 3 , 10 ) and source Network address is null or “-” and account name not has the value $
- Event ID 4625 with logon types 3 or 10 , Both source and destination are end users machines.
- More than “10” EventID 4625 with different “Account Name” and Sub status 0xc0000064 , Status code 0xc0000064 says user name does not exist and source network address is not equal to “null” or “-” , Possible accounts discovery.
Also Read: Splunk Architecture: Forwarder, Indexer, And Search Head
Suspicious Successful Logons:
- Event ID 4624 with Logon type 10 ( RemoteInteractive logins ) and source network address is loopback ( 127.*.*.* or ::1 ) , mostly RDP tunneling.
- Event ID 4624 and logon type 10 ( Remote Interactive ) and source network is not in your organization Subnet.
- Event ID 4624 and logon type ( 3, 10 ) and both source work station names and destination are end user machines.
- Event Id 4624 with logon types ( 10 ,2 ) , Type 2 ( A user logged on to this computer ) and account name has ends with $ , Example: ItSupport$ , Possible fake machine account.
- Event Id 4624 with more than 1 successful logon with logon type in 3, 10 from same account name and different source network address.
- Event ID 4624 and logon types ( 2,10,7 ) and account name like svc_* or internal service accounts , Possible interactive logon from a service account.
Happy Hunting!
