This blog post is a step by step guide on how to install Routing and Remote Access Service on Windows Server 2019.
Overview:
The Remote Access server role provides three network access technologies in Windows Server 2019. These technologies are the role services of the Remote Access server role.
- DirectAccess
- Routing and Remote Access
- Web Application Proxy
By using RRAS, you can deploy DirectAccess and VPN connections to provide end-users with remote access to your organization’s network. You can also create a site-to-site VPN connection between two servers at different locations.
- PART-1 How to Install Remote Access Service on Windows Server 2019
- PART-2 How to Install and Configure VPN in Windows Server 2019
- PART-3 Configure Network Policy Server (NPS) for VPN in Windows Server 2019
- PART-4 Configure Port Forwarding and Test VPN Connection on Windows 10
Understanding Test Lab:
- WS2K19-DC01: Domain Controller and DNS server.
- WS2K19-VPN01: Member Server.
- WS10-CLI01: Windows 10 PC.
Install Remote Access service on Windows Server 2019:
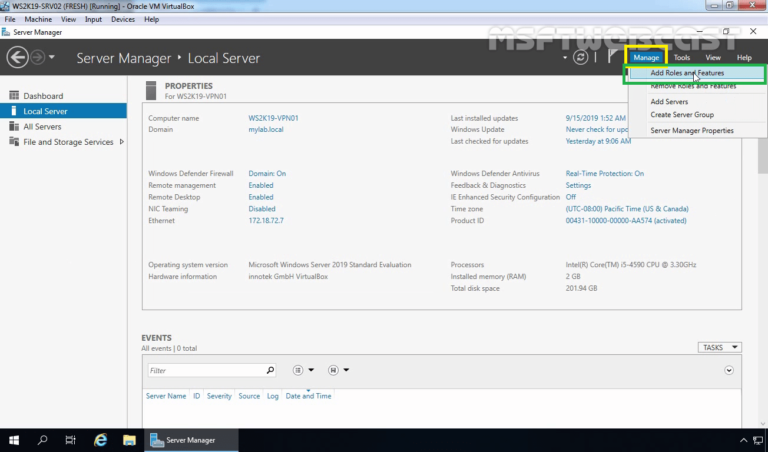
1. Open Server Manager Console.
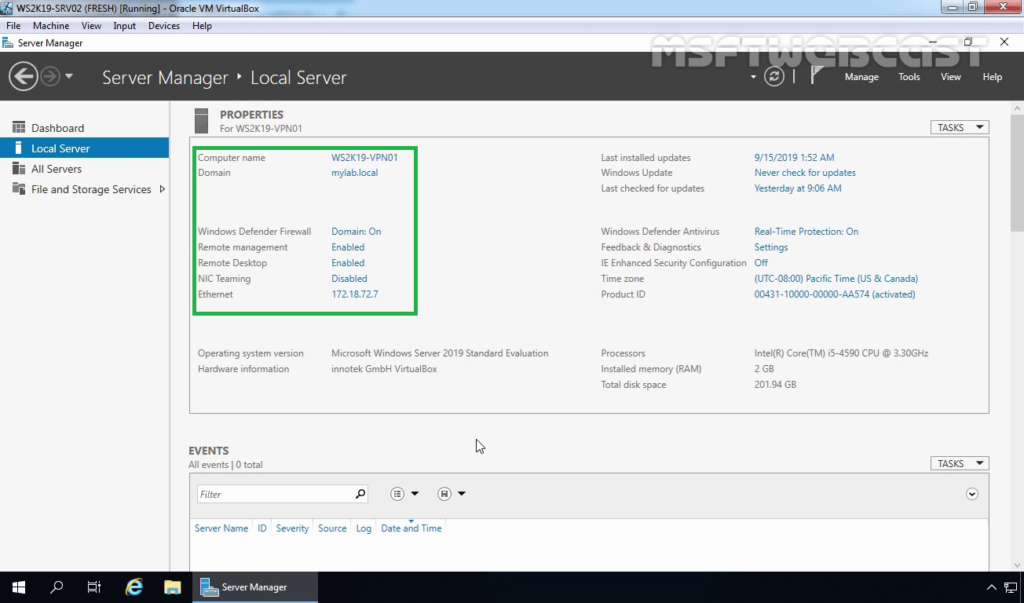
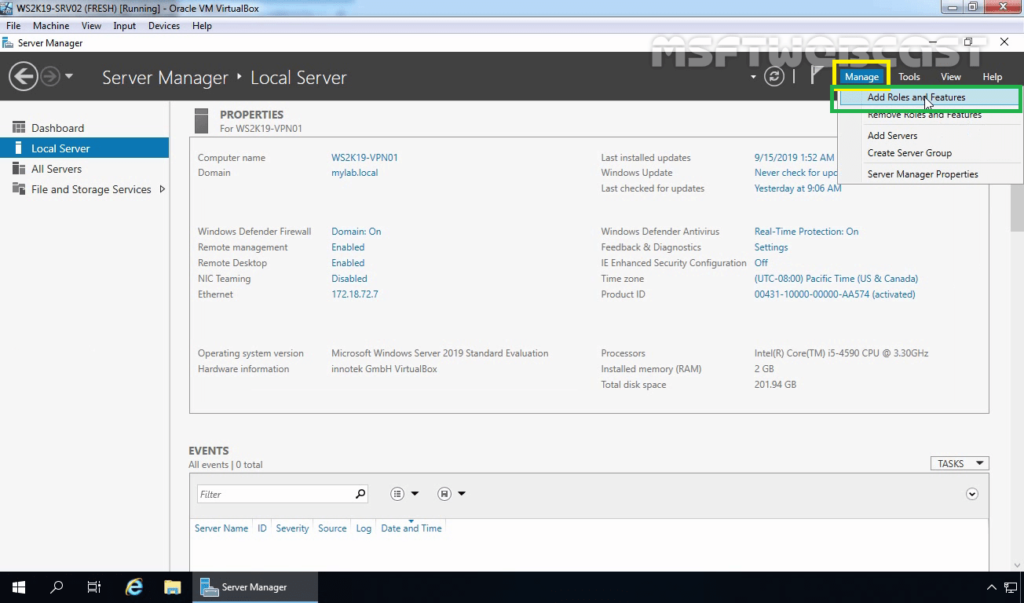
2. At the top of the Server Manager, click on Manage and select Add Roles and Features.
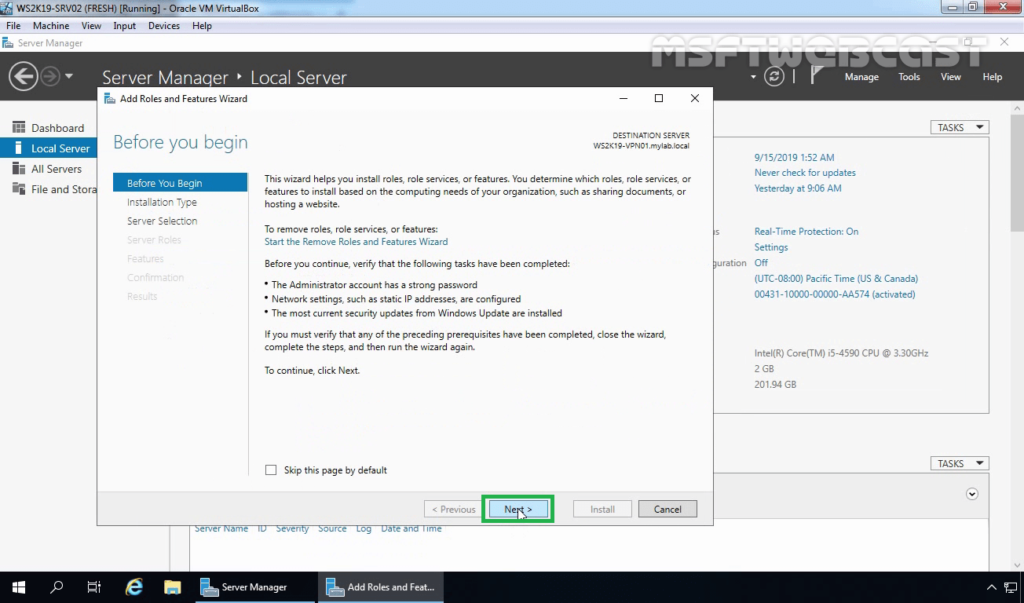
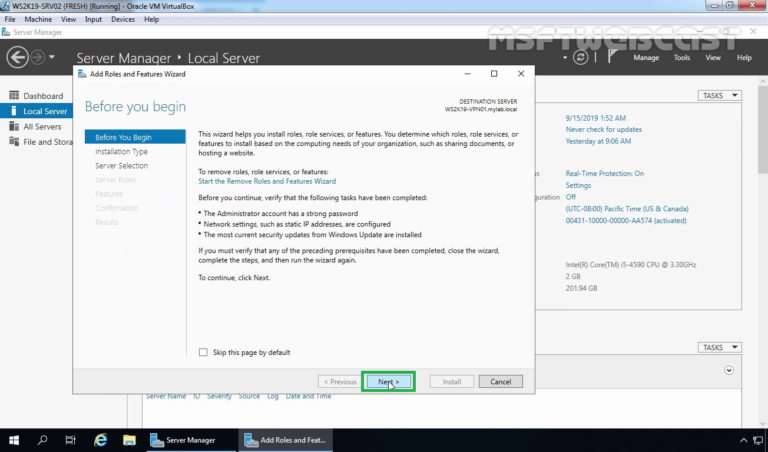
3. On the Before you begin page, click Next.
4. Select Role-based or feature-based installation and then click Next.
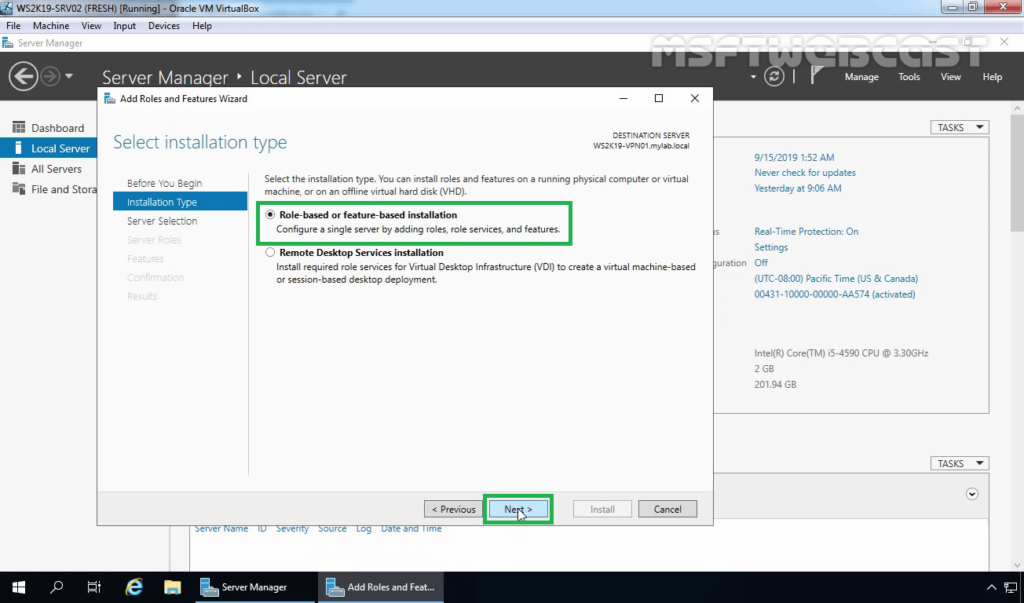
5. Select a server from the server pool on which you want to install the Remote Access Service, click Next.
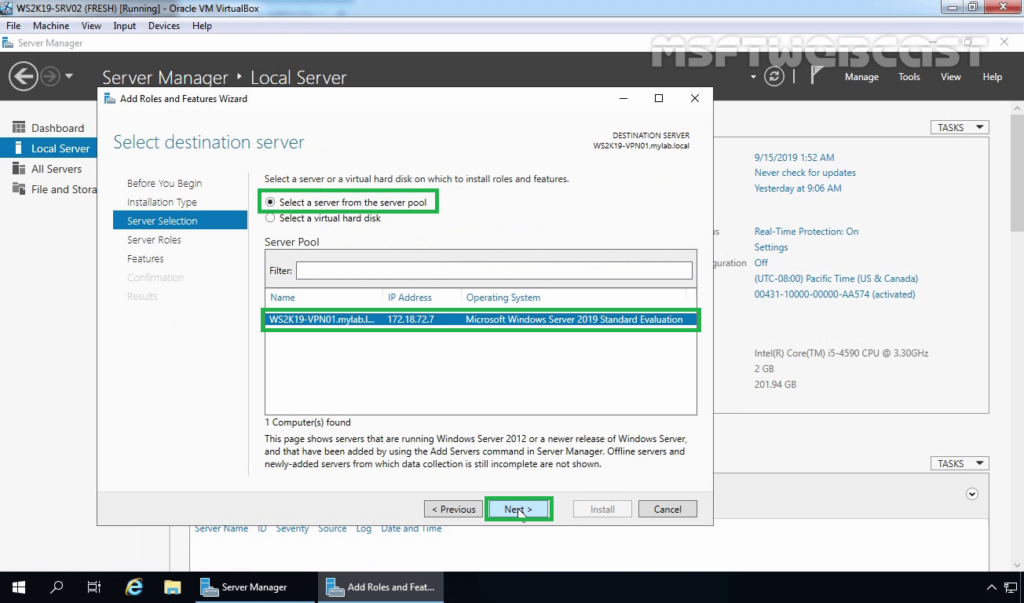
6. On select server roles page, select Remote Access Service. Click Next.
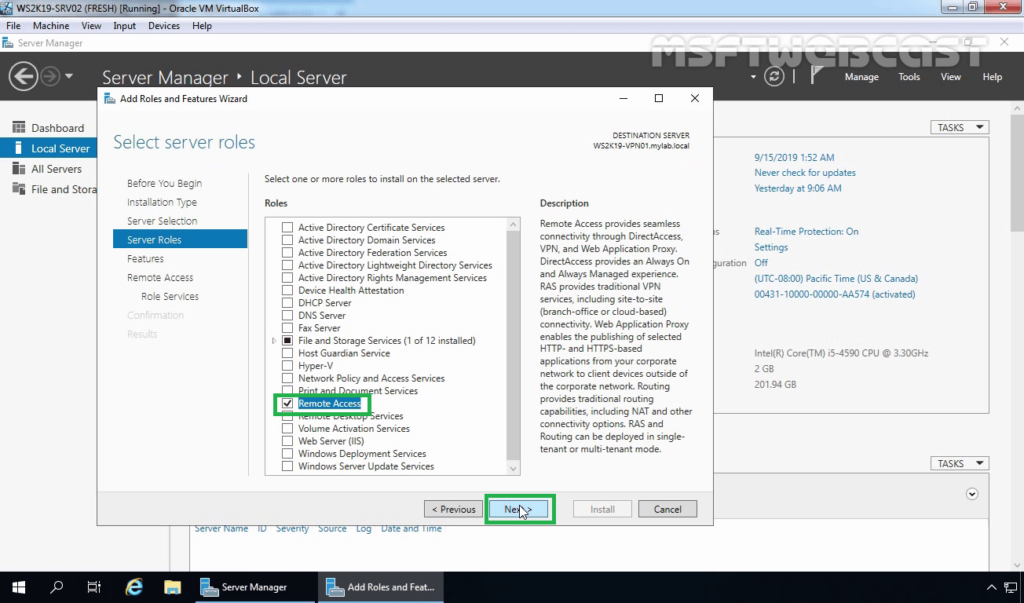
7. On select features page, click Next.
8. On the Remote Access page, read a brief overview of the Routing and Remote Access Service. Click Next.
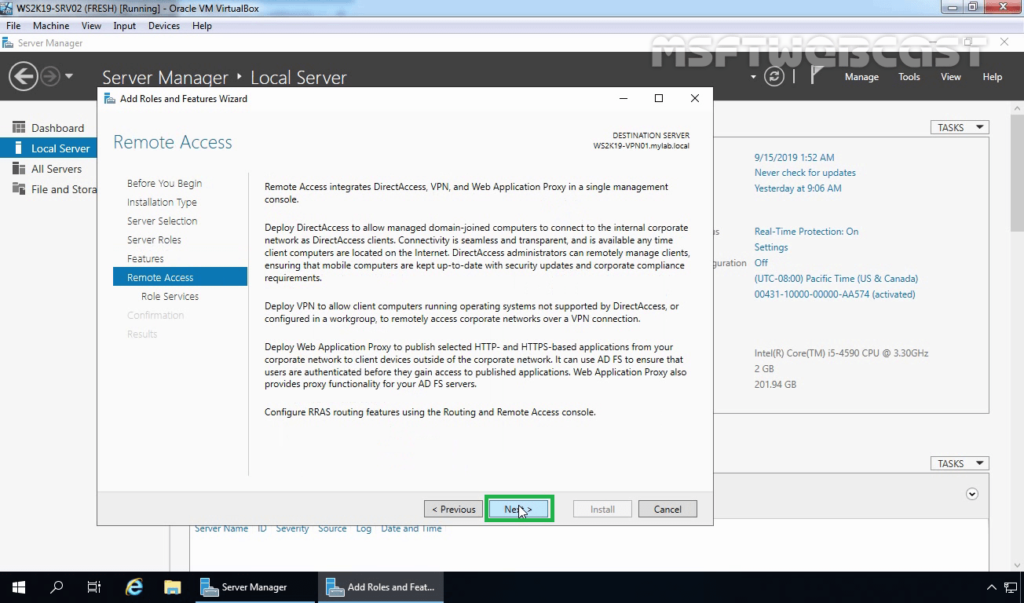
9. On select role services page, select DirectAccess and VPN (RAS) service.
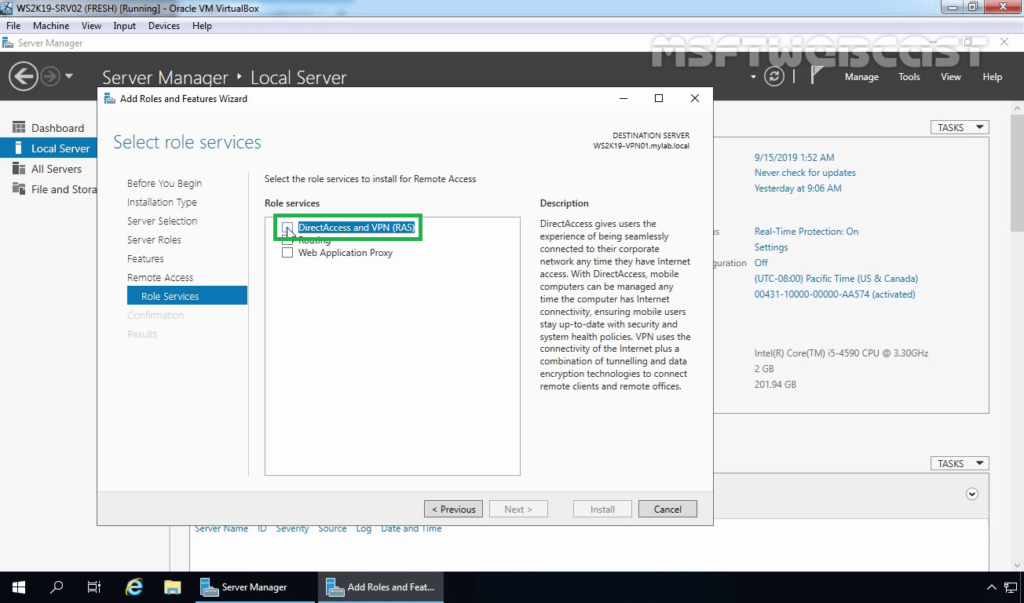
10. A new window will pop up, click on Add Features to include required features and management tools for DirectAccess and VPN.
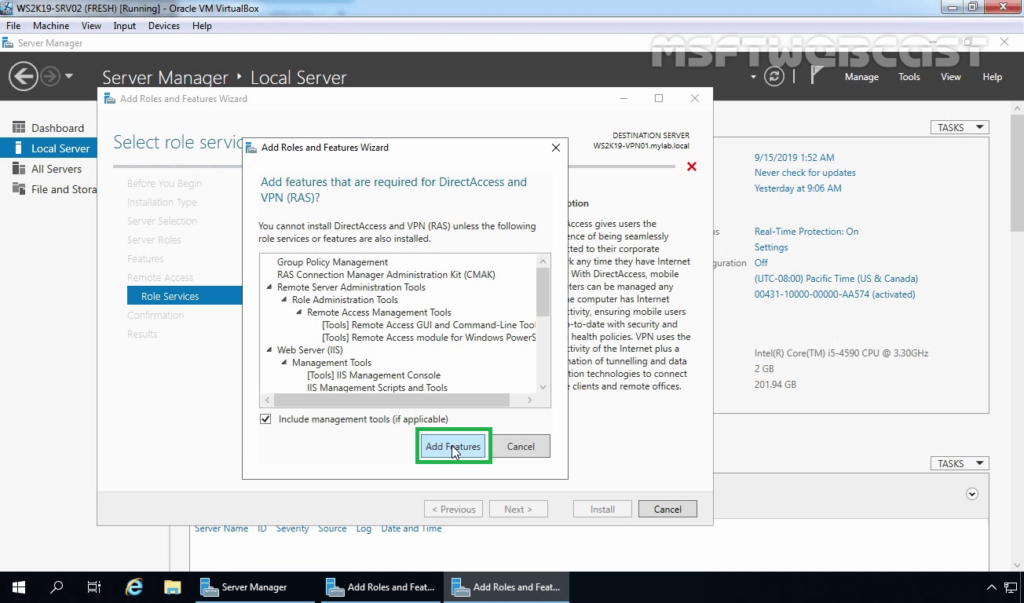
11. Make sure that DirectAccess and VPN role service is selected.
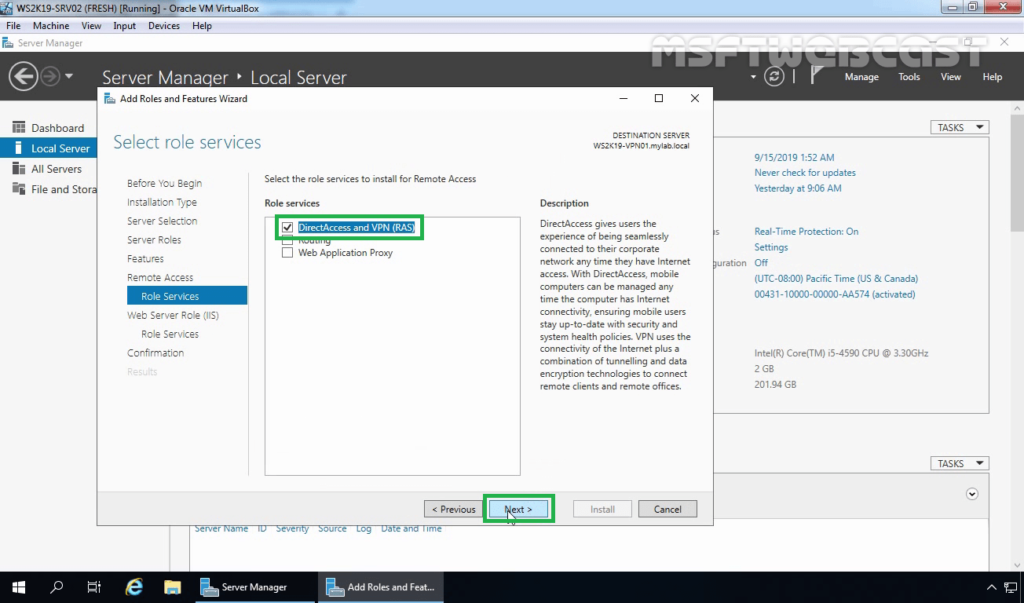
12. On the Web Server Role (IIS) page, read a brief overview of the IIS Service. Click Next.
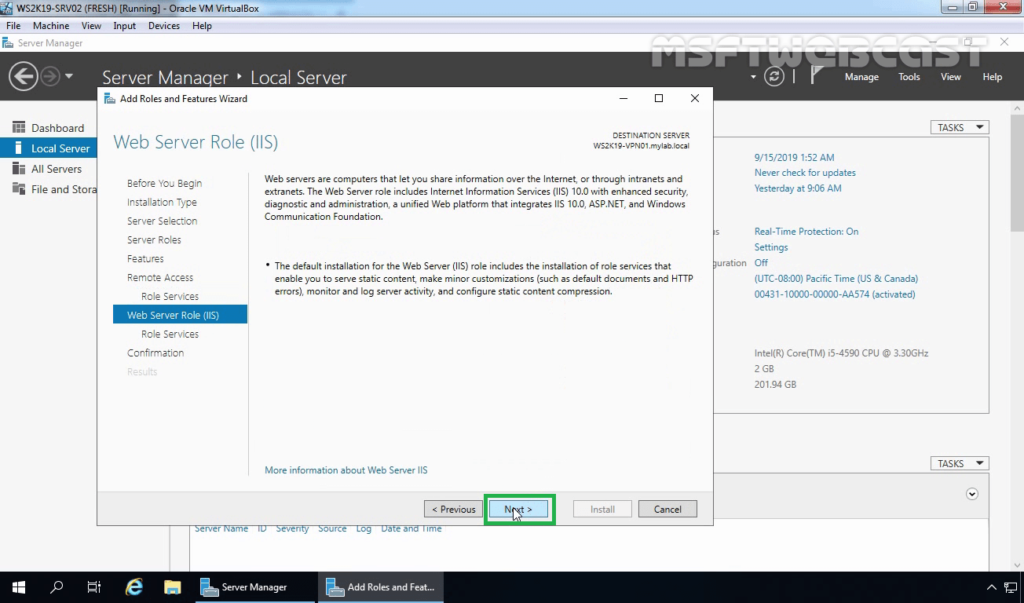
13. All required IIS role services are already selected. Click Next to continue.
14. Click on the Install button to start the installation of Remote Access Service on Windows Server 2019.
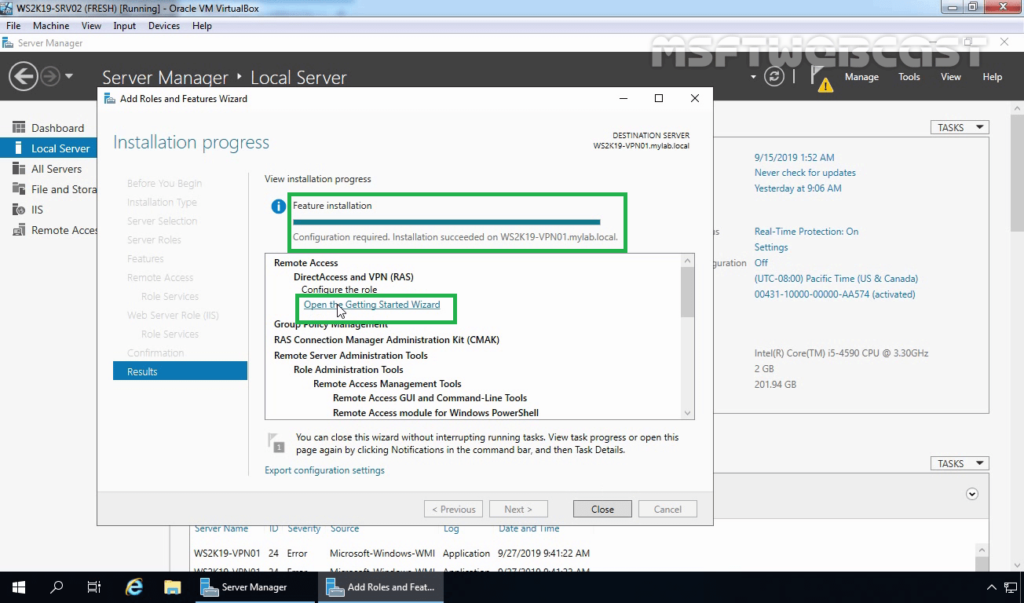
15. After installing the Remote Access service on windows server 2019, the next step is to configure the Remote Access server.
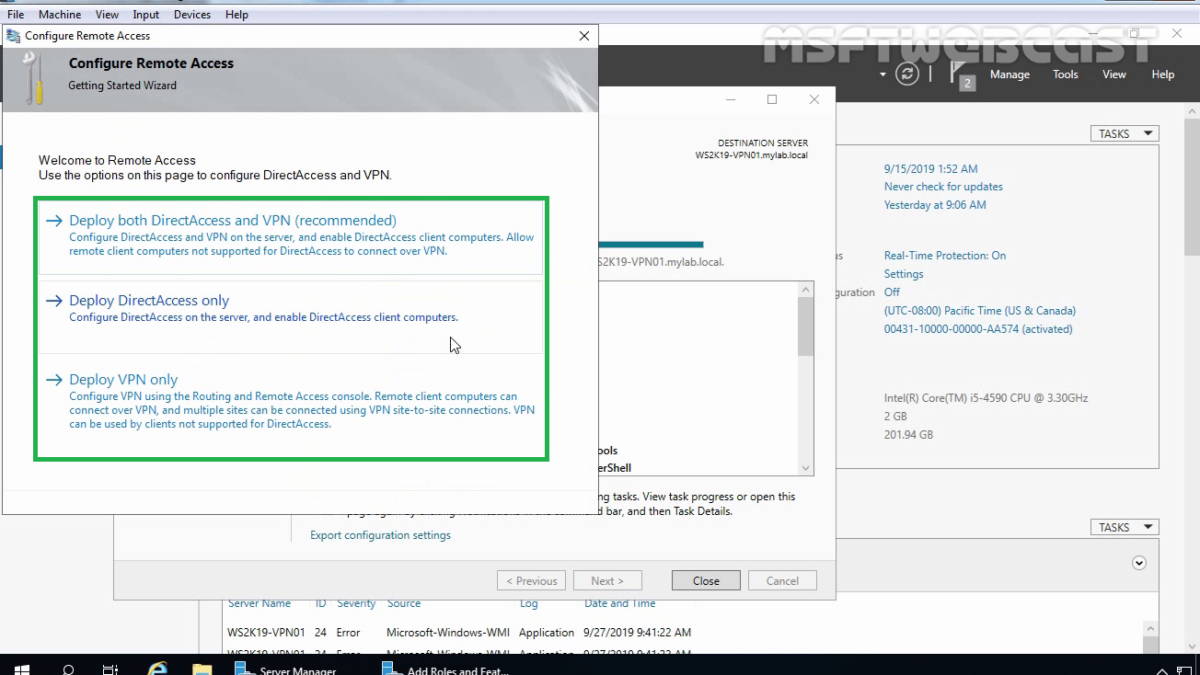
16. Click on the Open the Getting Started Wizard link to start the wizard to configure DirectAccess and VPN on Windows Server 2019 Remote Access Server.
17. From this console, we can configure VPN on Windows Server 2019. In the next post on How to Configure VPN using Remote Access Service on Windows Server 2019.
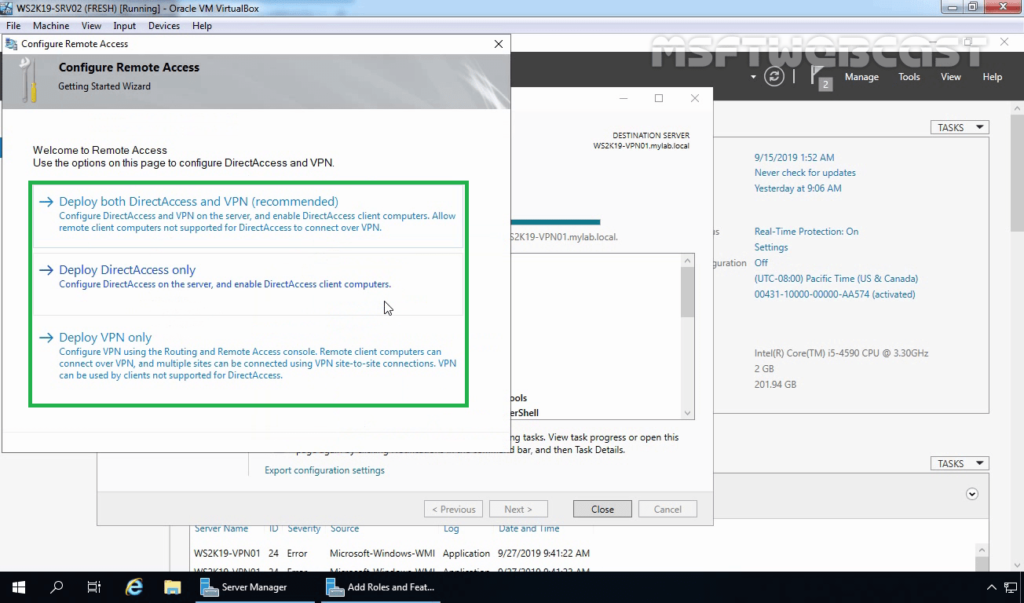
After installing the Remote Access Service, next steps will be configure it.
Thank you for reading.
Post Views: 4,487
Home » Windows 2019 SSTP Server with only ONE NIC – Quick Guide
In this short guide we deploy a Windows-based SSTP server for clients. For details about the protocol and the way to deploy a linux-based implementation of the server that has auto-renewing SSL certificates, visit my guide HERE.
Our test VM has only one network card to simulate a low-budget real-life scenario. That means we’ll configure a separate subnet for connected clients and use NAT to give then network access. If the server has multiple NICs, clients can be relayed to use the local DHCP service to get unique IP addresses. Further on that later.
Before You Start
We start with a fresh install of Windows Server 2019, and join it to the alwayshotcafe.com domain.
The server is publicly accessible as vpn.alwayshotcafe.com.
As a side note: if security is a concern, only port 443/tcp needs to be allowed/forwarded to the VPN server for SSTP.
1. Install the RRAS role on the server
We need the RRAS role on the VPN server, also the NPS (Network Policy Services) role to control who is allowed to connect and when to the service.
Via PowerShell:
To install the RRAS role (VPN and Routing services) we use the following PowerShell cmdlet
PS C:\> Install-WindowsFeature RemoteAccess, DirectAccess-VPN, Routing, RSAT-RemoteAccess-PowerShell, RSAT-RemoteAccess-Mgmt, RSAT-NPAS
Alternatively, use the GUI:
1. If you prefer the GUI, open the Server Manager, and select the «Add Roles and Features» option
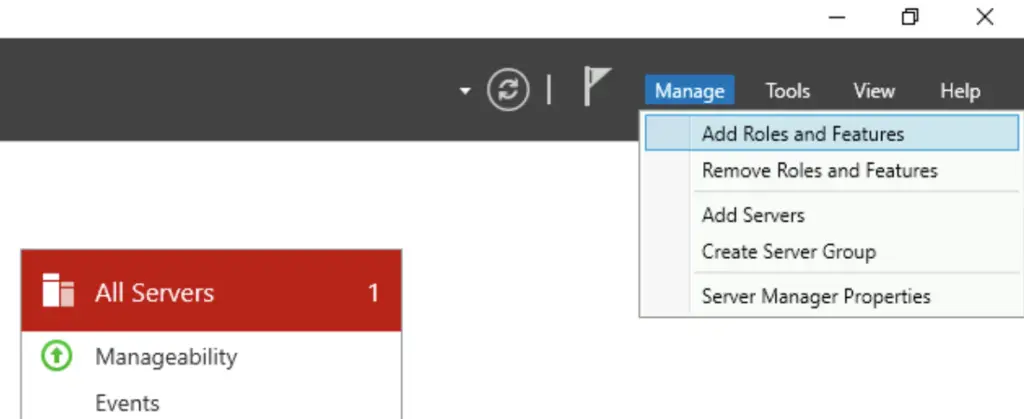
2. Check the «Remote Access» role, hit Next
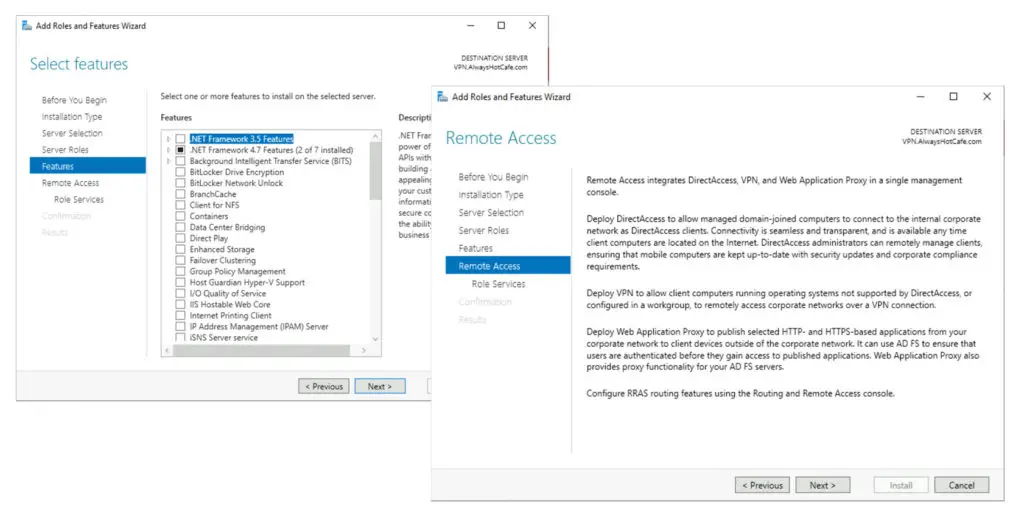
3. Pass the next two pages
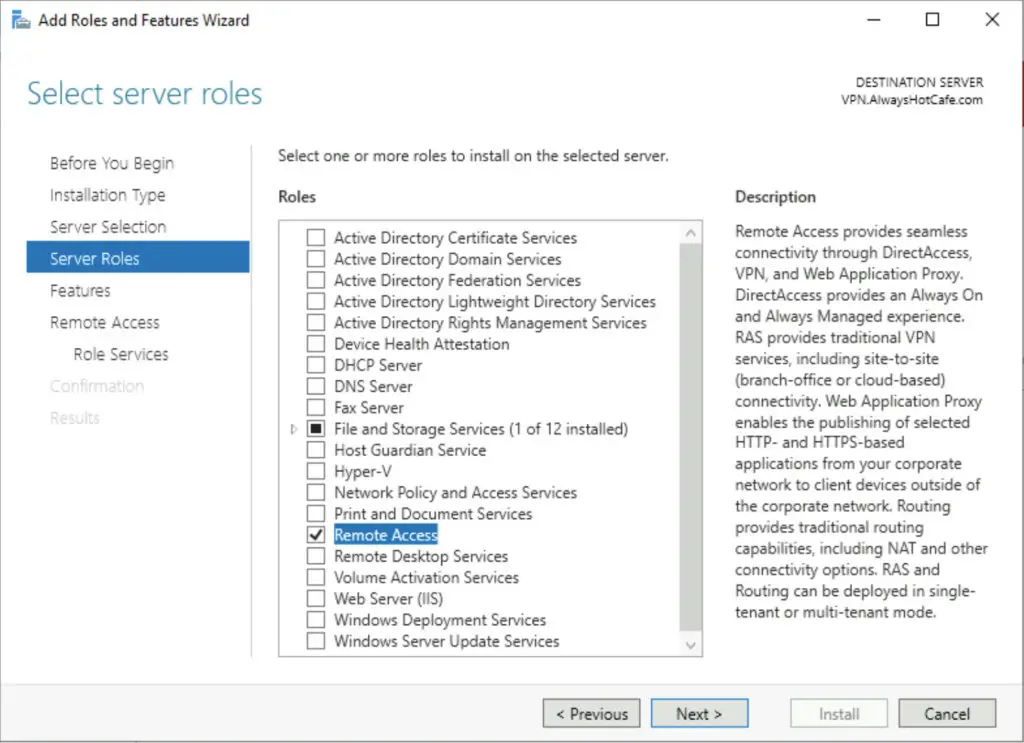
4. Select the RAS role service, also the Routing option that will be handy if NAT-ing is needed (to conserver IP addresses in your current subnet, a separate one is created for VPN clients). It is a necessity on a server with only one NIC.
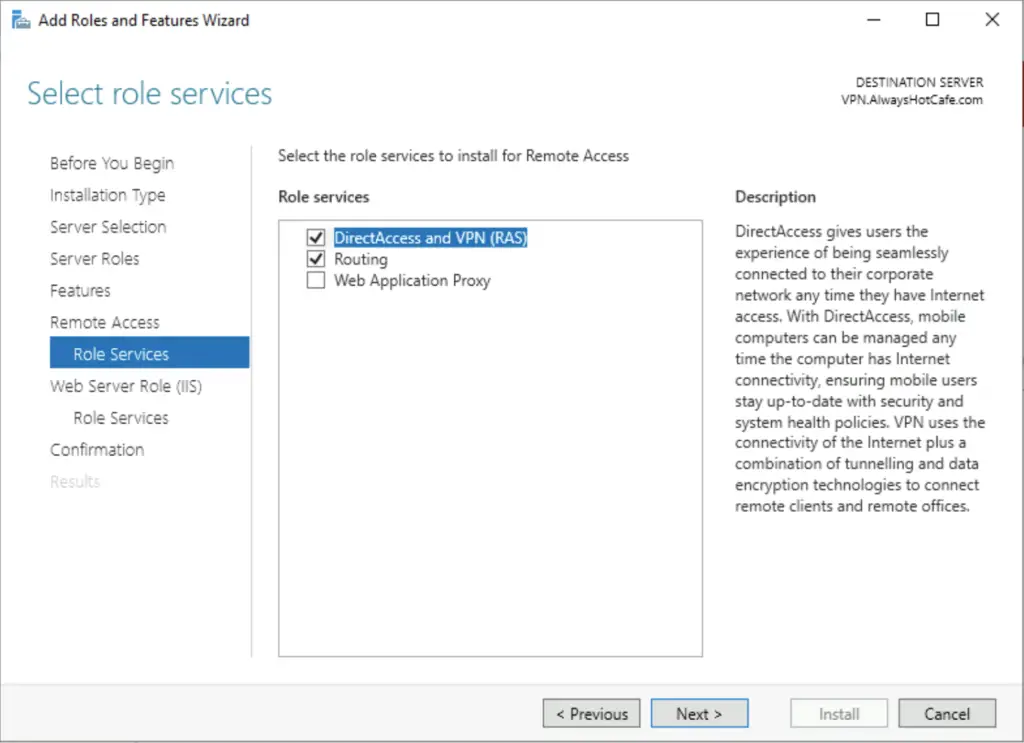
5. Accepting the defaults on the following pages, finally click on Install
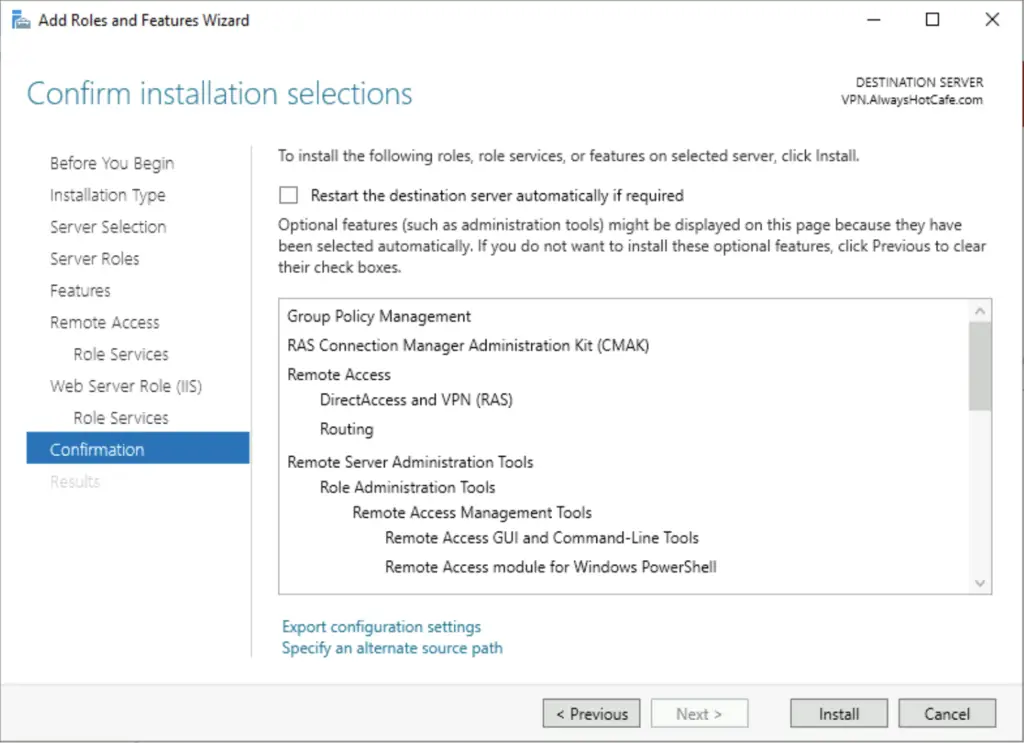
Configure the RRAS service
1. Open the RRAS console by running rrasmgmt.msc, or open it in the Administrative Tools folder.
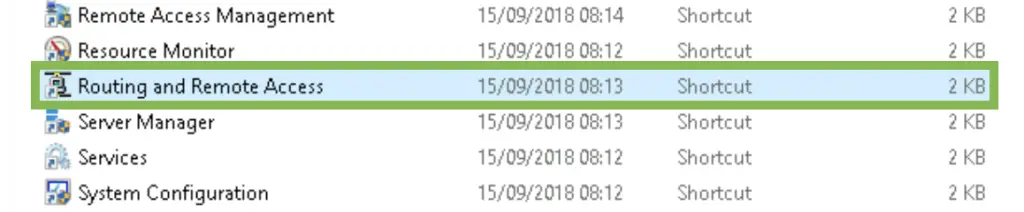
2. Right-click on the local server name (here VPN), then select the «Configure and Enable Routing and Remote Access» option
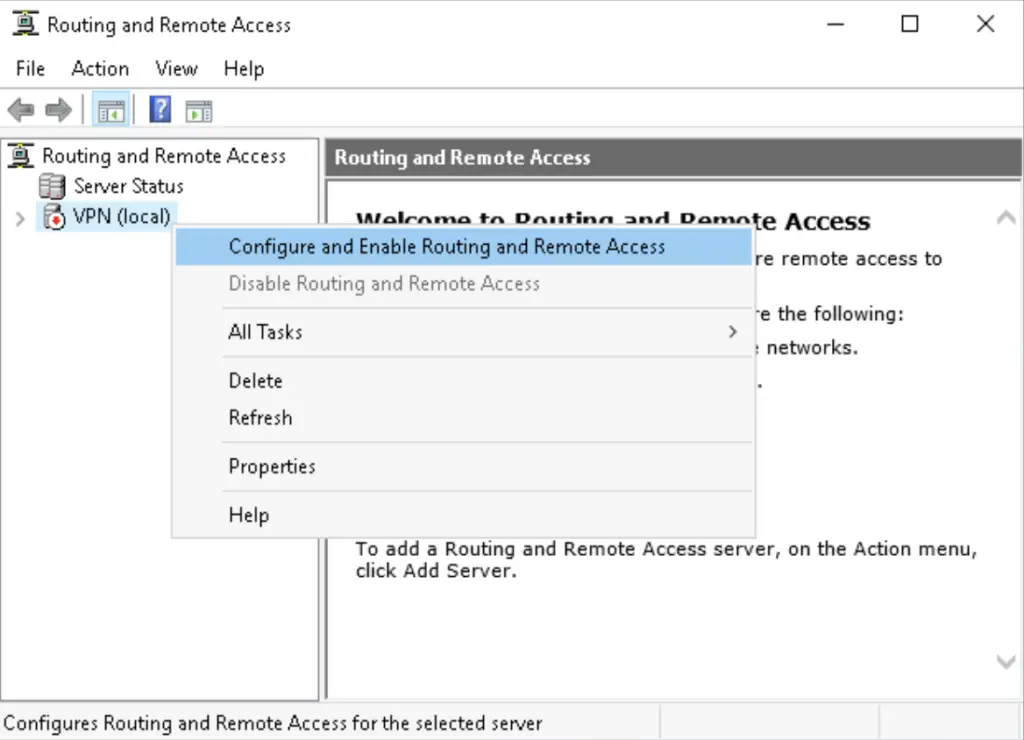
3. Choose the Custom option. If your server has only one NIC, this is the only option you have anyway, all the other will throw you errors as by default Windows RRAS servers are expected to have multiple network interfaces.
Note: it is understandable as RRAS servers should have their public interface in a DMZ subnet and the internal should be used to assign users local IP addresses to follow best practices
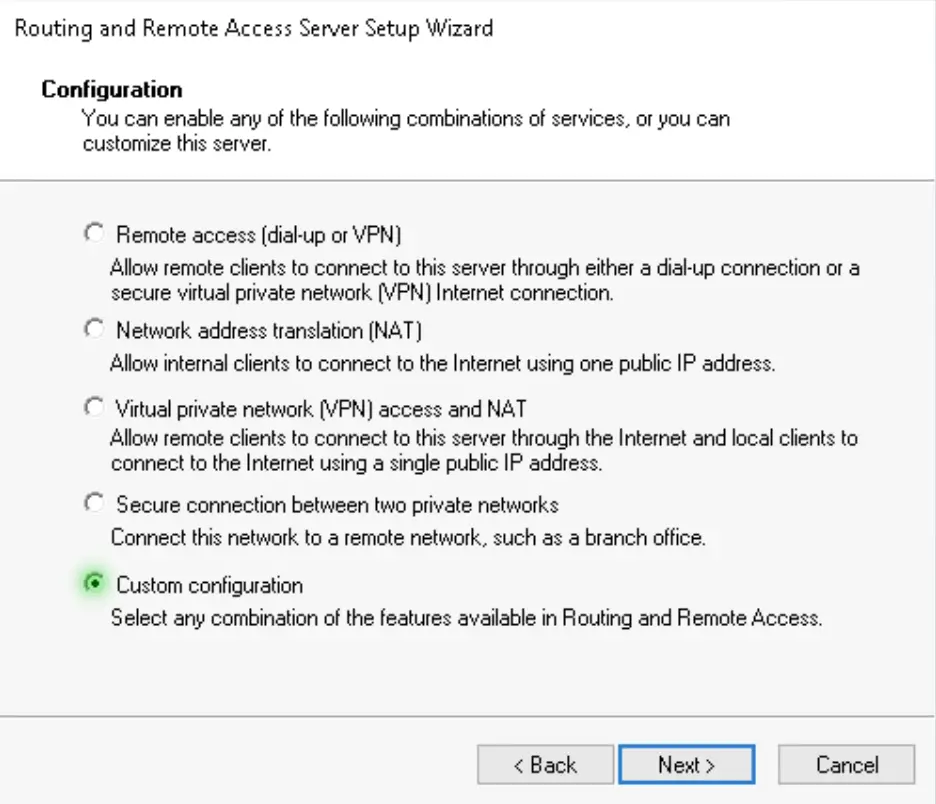
4. We need the VPN access, NAT and LAN routing services to be added to the server
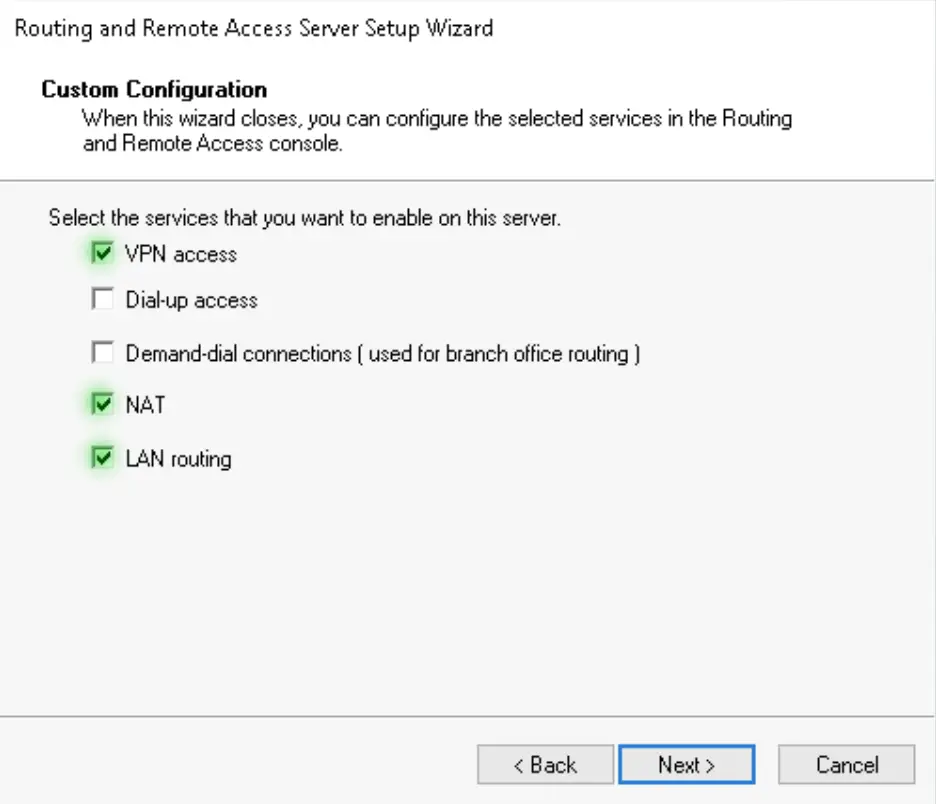
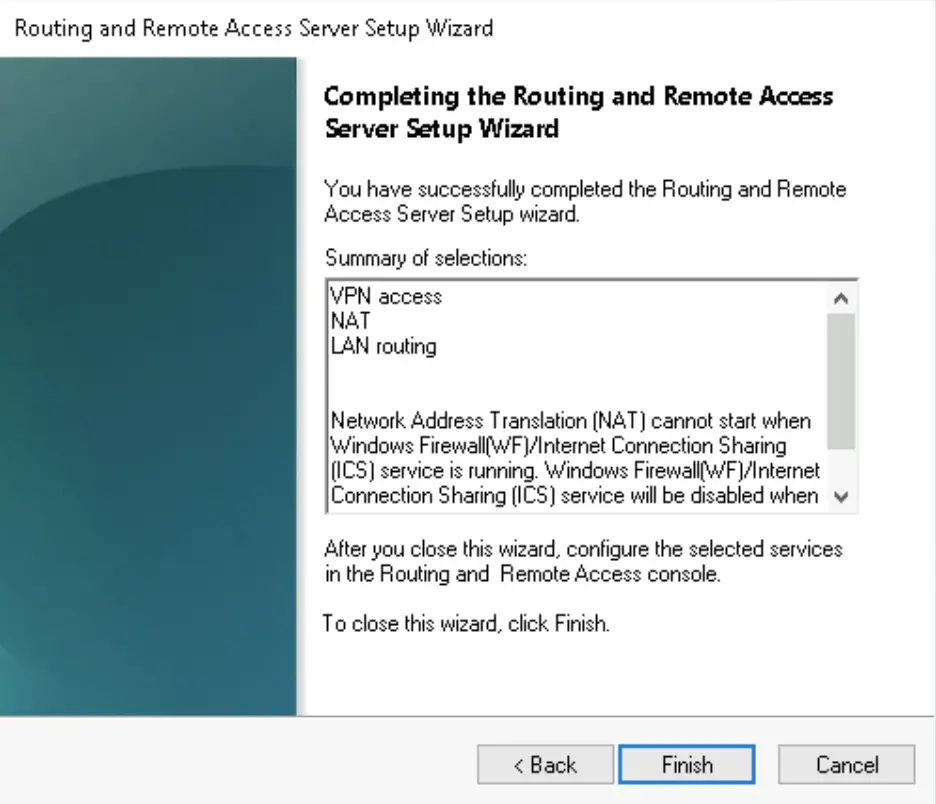
Enable SSTP
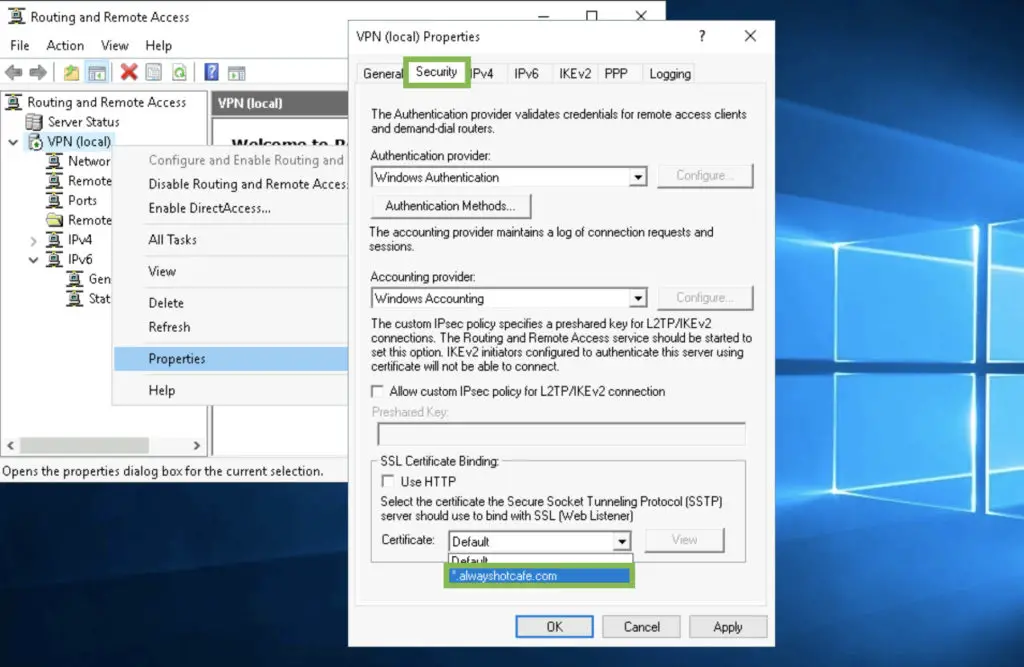
To enable SSTP we need a valid SSL certificate with the subject (alternative) name which matches the FQDN of the VPN server. The client will use this FQDN to make the VPN connection. Here it is vpn.alwayshotcafe.com, and we use our wildcard certificate that covers our requirements. For a guide on how to generate an SSL certificate for Windows, click here.
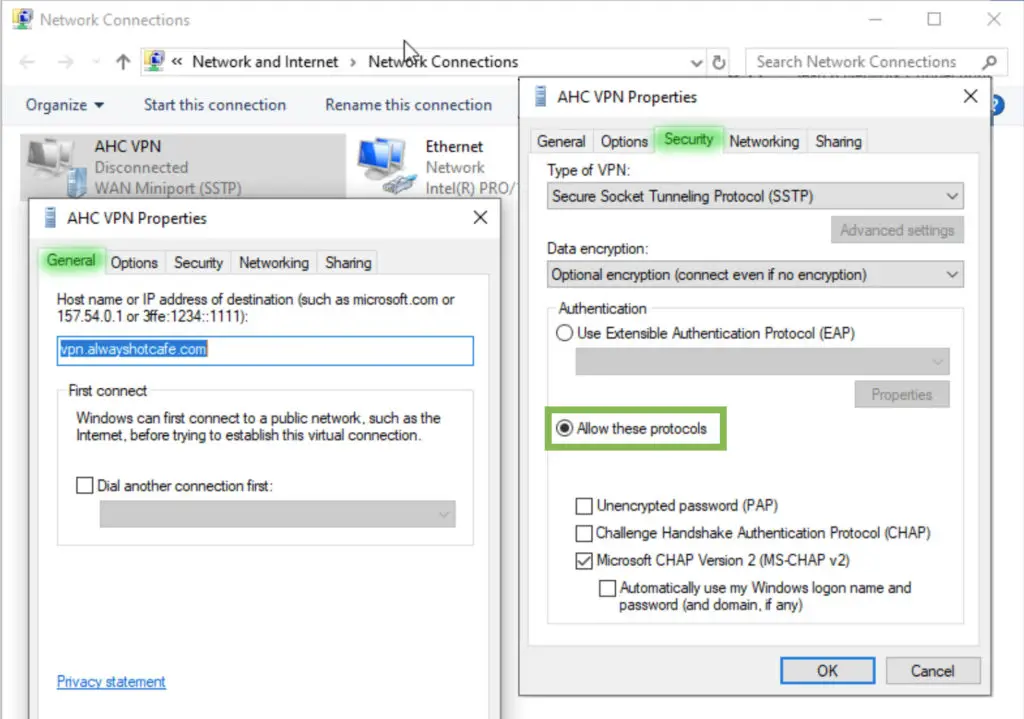
1. Right-click on the server name (VPN) in the RRAS console. Switch to the Security tab and select the correct certificate from the drop-down list.
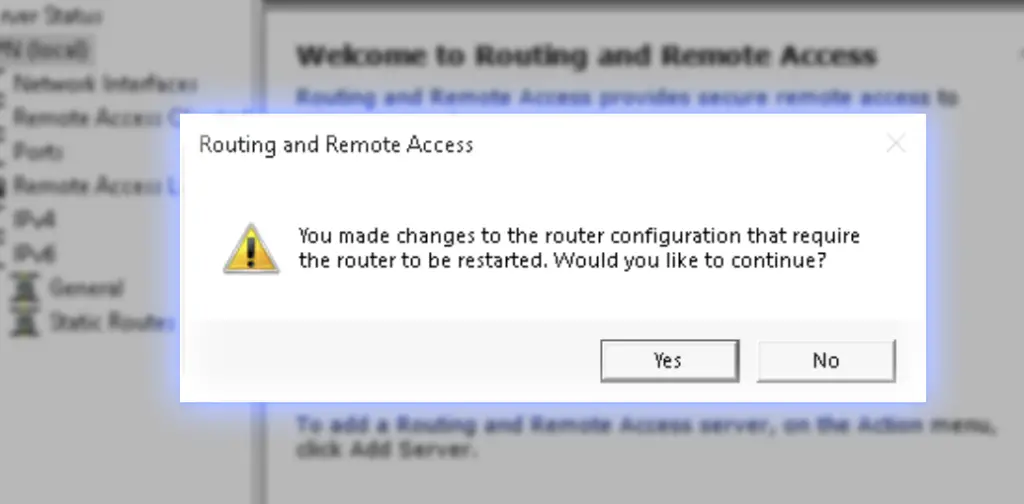
2. Then restart the service
Set up NAT for connected clients
Clients can now connect, but they are not able to communicate with any other devices yet. The 10.255.255.0/24 is a new subnet the rest of the network isn’t aware of. We use NAT to effectively masquerade client requests as if they were originating from the VPN server itself, that the rest of our network know.
It’s great for flexibility, as we can expand the client IP pool as large as we want. The downside is this way it’s trickier if we want to initiate connections to a client from our network and not the other way around.
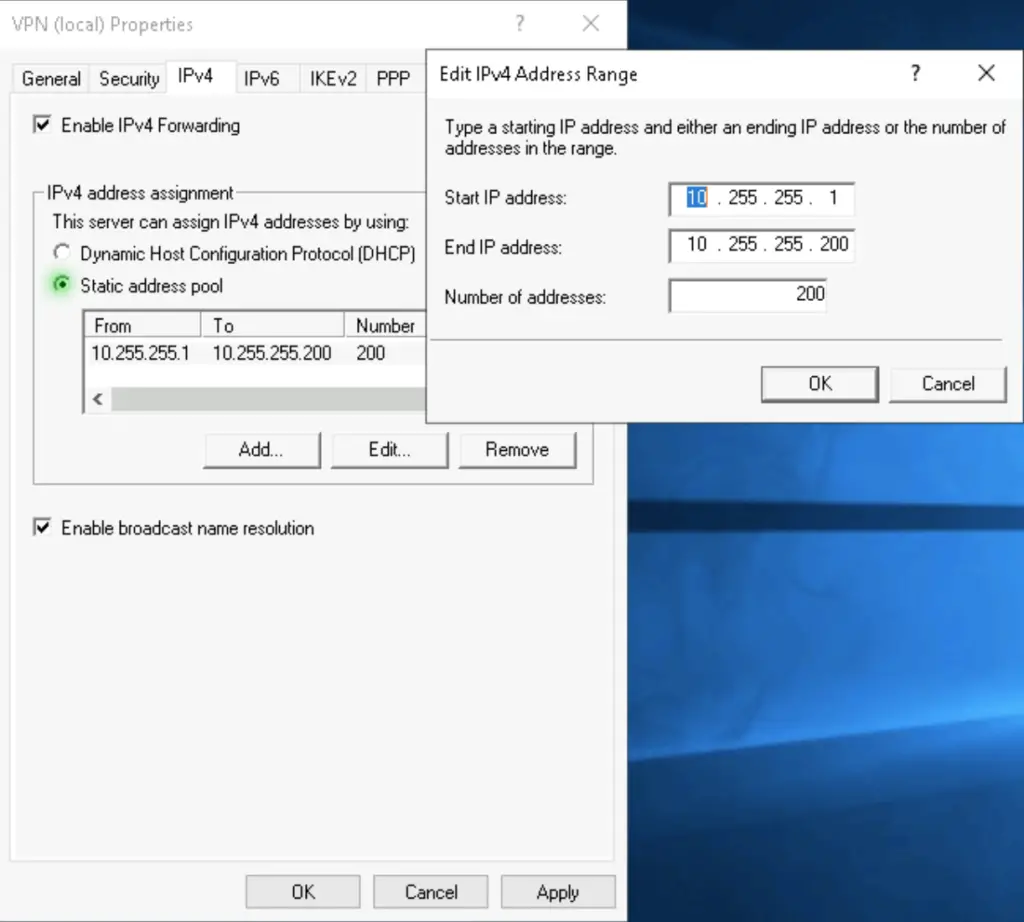
1. Open the Properties of our VPN server again. Under the IPv4 settings create a static address pool for connecting clients. In our example, the pool spans from 10.255.255.1 to 10.255.255.200, making it available for 200 clients to connect to the server at the same time.
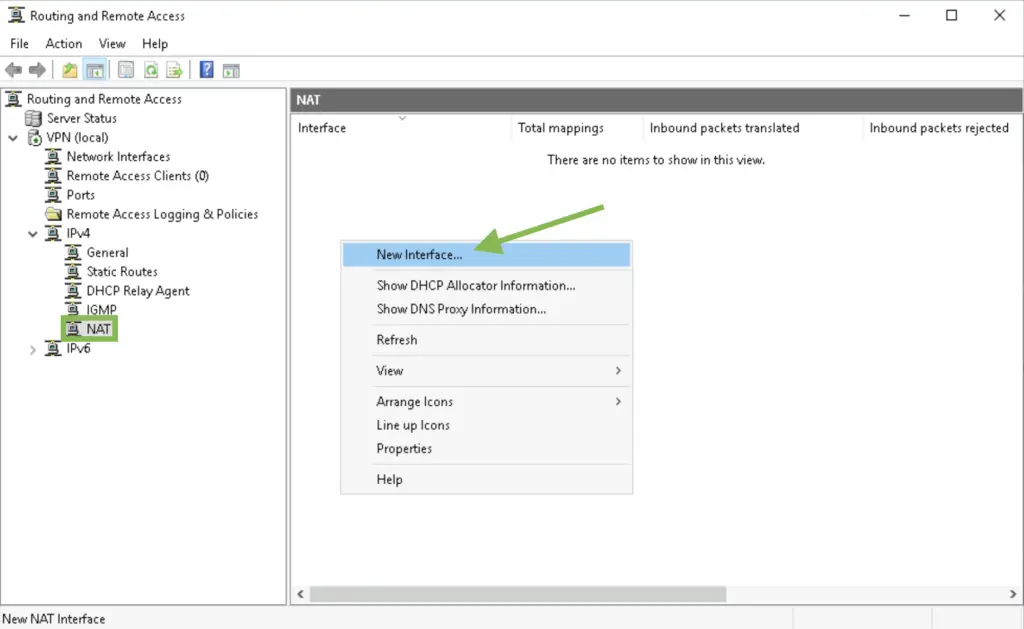
2. Highlight the NAT option in the left-side menu, and create two new interfaces as follows
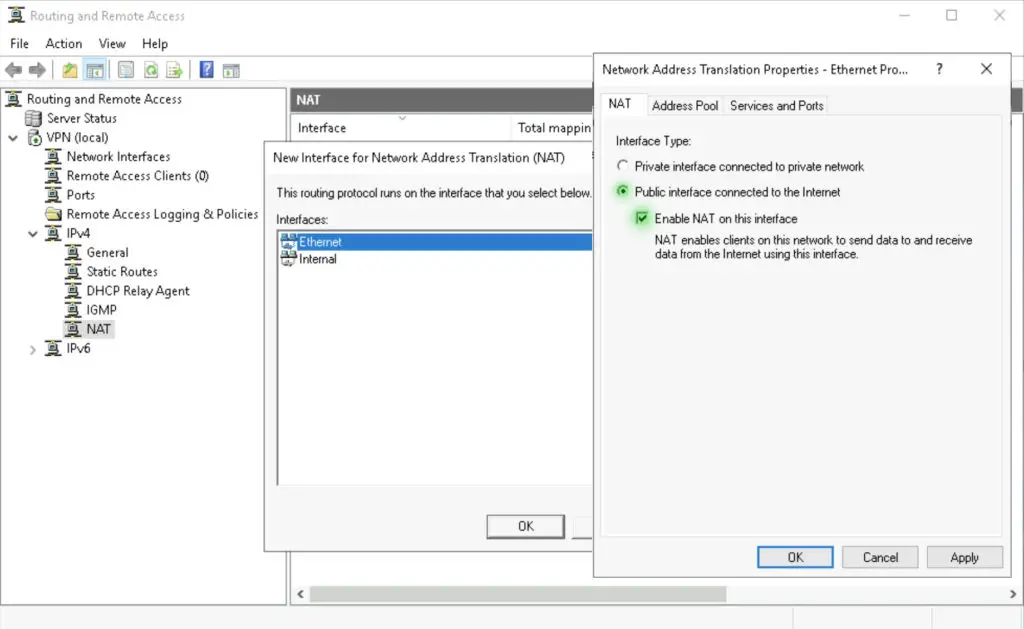
3. Add «Ethernet» as the public interface and enable NAT on it. This interface will be the our local outside interface.
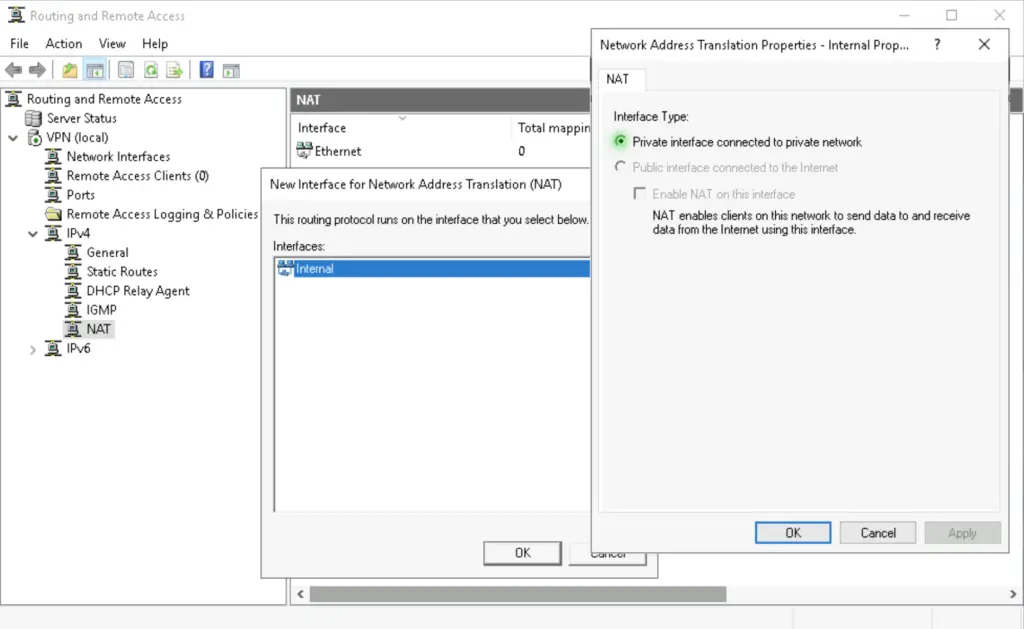
4. Add the «Internal» interface as a private interface. This means it becomes our local inside interface.
Set the Network Policies
Network policies are controlling who can use the VPN service and when. You can declare if only machines running Windows operating systems are allowed, or if any kind of devices are accepted. You can lock down the service so only a member of a certain security group will be able to authenticate to the server. You can even specify a certain time period when the service is accepting incoming VPN connections.
1. Open the Network Policy Server console in the Admin Tools, or use the nps.msc command.
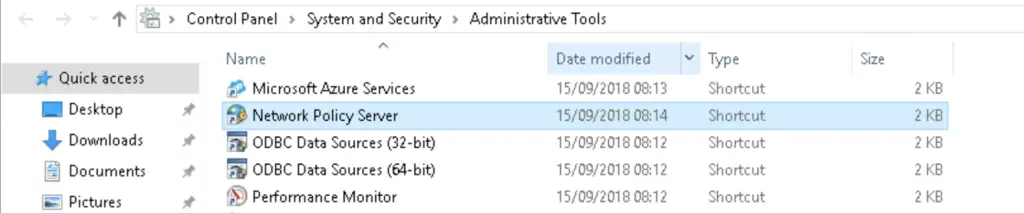
2. Under Network Policies double-click on the «Connections to Microsoft Routing and Remote Access server«
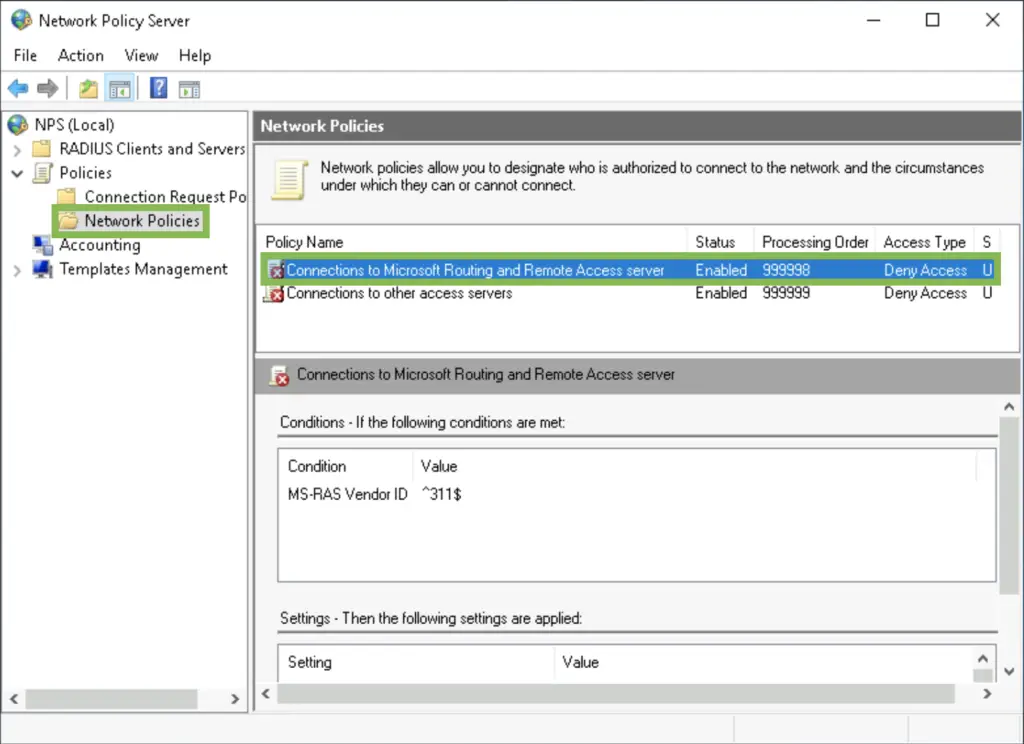
3. Select «Grant access» to specify this policy is for allowing users to connect. In the following tabs you can specify the requirements the client needs to meet in order to be allowed in.
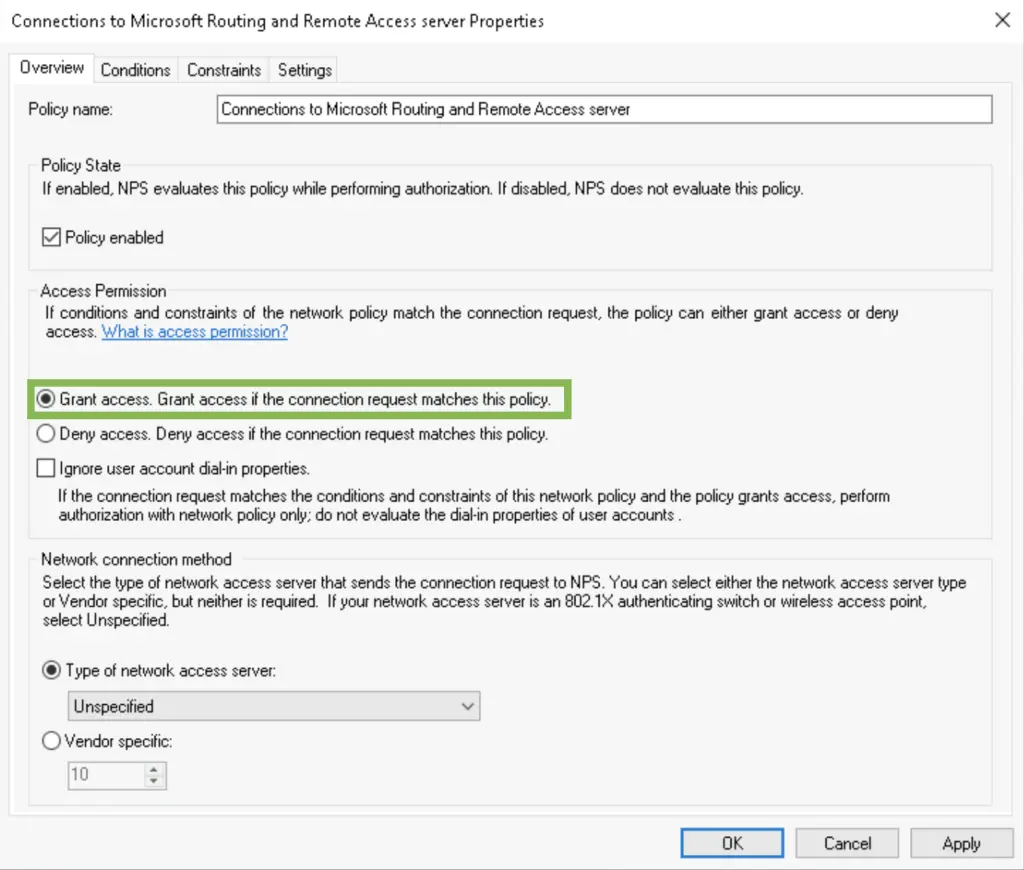
4. We want only the ALWAYSHOTCAFE.COM domain users to be remote access enabled, so we add the «Domain Users» group in the Conditions list. Ideally you can have a separate security group that only contains the remote workers. This is great for tighter security and it makes adding or removing users to a group really easy.
5. We leave the default settings in the Constraints and Settings tab.
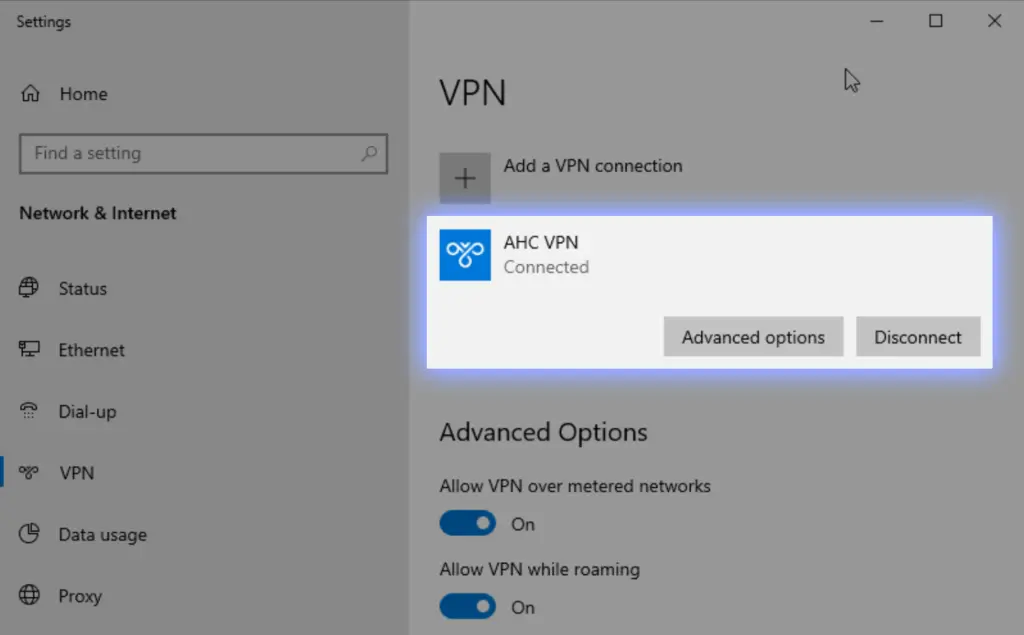
Alice is now ready to connect!
Client Connection Test
To verify that our service is up and running, create the connection for Alice. Use the vpn.alwayshotcafe.com server address, with her SamAccountName (alice) as username. Select the protocol: SSTP.
Make sure to select an authentication method, otherwise the client will throw an error message!
Reader Interactions
- RRAS on WIndows Server 2019 with DHCP
- RRAS on WIndows Server 2019 with DHCP
- RRAS on WIndows Server 2019 with DHCP
- RRAS on WIndows Server 2019 with DHCP
- RRAS on WIndows Server 2019 with DHCP
RRAS on WIndows Server 2019 with DHCP
-
Pay Microsoft for a support call and see how that goes. (Good luck) 2)
Install server 2016 and revisit the issue in about 6 months after microsoft
fixes the problems with server 2019. You can also monitor the Update History
Website and see if they say something about RRAS in the release notes.reg add «HKLM\SYSTEM\CurrentControlSet\Services\Dhcp» /v RequiredPrivileges /d «SeChangeNotifyPrivilege»\0″SeCreateGlobalPrivilege»\0″SeImpersonatePrivilege»\0 /t REG_MULTI_SZ /f
RRAS on WIndows Server 2019 with DHCP
Hmm, I have Winsrv 2019 running ALOVPN service (RRAS) and IP’s are gathered
from remote DHCP which is DC also. DHCP relay agent pointing to that DHCP was
the key here. Also, RRAS’s server internal NIC …
PPP adapter AO:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : AO
Physical Address. . . . . . . . . :
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 10.0.16.7(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . :
Primary WINS Server . . . . . . . : 10.0.0.22
NetBIOS over Tcpip. . . . . . . . : Enabled
PPP adapter AO:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : AO
Physical Address. . . . . . . . . :
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 10.0.16.7(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . :
Primary WINS Server . . . . . . . : 10.0.0.22
NetBIOS over Tcpip. . . . . . . . : EnabledRRAS on WIndows Server 2019 with DHCP
Solution 1: Can you try the work around to change below registry key value and
restart DHCP Client service? Path:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dhcp. Value:
(change from) SeChangeNotifyPrivilege SeCreateGlobalPrivilege. (to)
SeChangeNotifyPrivilege …
reg add "HKLM\SYSTEM\CurrentControlSet\Services\Dhcp" /v RequiredPrivileges /d "SeChangeNotifyPrivilege"\0"SeCreateGlobalPrivilege"\0"SeImpersonatePrivilege"\0 /t REG_MULTI_SZ /fRRAS on WIndows Server 2019 with DHCP
Exactly as the one here My setup is dead simple, internal network 10.0.0.0/16
One RRAS interface in DMZ, another in LAN (so it is not full DMZ setup , but
like left picture here) DHCP gives out 10.0.10.0-10.0.15.254 As I can not get
VPN clients to obtain IP from DHCP, I used static pool of 10.0 · Hello, As far
as I’m concern, with RRAS service if
PPP adapter AO:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : AO
Physical Address. . . . . . . . . :
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 10.0.16.7(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . :
Primary WINS Server . . . . . . . : 10.0.0.22
NetBIOS over Tcpip. . . . . . . . : Enabled
PPP adapter AO:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : AO
Physical Address. . . . . . . . . :
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 10.0.16.7(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . :
Primary WINS Server . . . . . . . : 10.0.0.22
NetBIOS over Tcpip. . . . . . . . : EnabledRRAS on WIndows Server 2019 with DHCP
Boldar Asks: RRAS on WIndows Server 2019 with DHCP I have the following setup:
A Windows Server 2019 VM, which is also the AD Domain Controller. It has a
public IP. I want to set up a VPN (RRAS) where the users can connect to so
they are in the local network. I made a new private Virtual
services.AddMemoryCache();
sealed class Course(
val type: Type
) {
data class ProgrammingCourse(val name: String, val detail: String) : Course(Type.PROGRAMMING)
object LanguageCourse: Course(Type.LANGUAGE)
.....
}
fun getCourse(): Course {
if(...)
return Course.ProgrammingCourse("test", "test")
else
return Course.LanguageCourse
}
fun workWithCourse(course: Course.ProgrammingCourse) {
// here some logic
}
fun main() {
val course = getCourse()
workWithCourse(course)
}
Type mismatch.
Required:
Course.ProgrammingCourse
Found:
Course
if(course is Course.ProgrammingCourse) {
workWithCourse(course)
}
Cursor c = getContentResolver().query(Uri.parse("content://sms/inbox"), new String[] { "_id", "thread_id", "address", "person", "date","body", "type" }, "address=?", phoneNumber, null);
if(c.moveToFirst())
{
String msg_body = c.getString(c.getColumnIndexOrThrow("body")).toString();
//String sender_number = c.getString(c.getColumnIndexOrThrow("address")).toString();
txtMsg.setText(msg_body);
Log.d("Recent Message",""+msg_body);
}
c.close();
displayPaymentSheet(OrderProvider orderProvider) async {
try {
await Stripe.instance
.presentPaymentSheet(
parameters: PresentPaymentSheetParameters(
clientSecret: paymentIntentData!['client_secret'],
confirmPayment: true,
))
.then((newValue) {
print('payment intent ${paymentIntentData!['id']}');
print('payment intent ${paymentIntentData!['client_secret']}');
print('payment intent ${paymentIntentData!['amount']}');
print('payment intent $paymentIntentData');
//orderPlaceApi(paymentIntentData!['id'].toString());
ScaffoldMessenger.of(context)
.showSnackBar(SnackBar(content: const Text("Paid successfully")));
orderProvider.success = true;
Navigator.pop(context);
setState(() {
paymentIntentData = null;
});
}).onError((error, stackTrace) {
print('Exception/DISPLAYPAYMENTSHEET==> $error $stackTrace');
});
} on StripeException catch (e) {
print('Exception/DISPLAYPAYMENTSHEET==> $e');
showDialog(
context: context,
builder: (_) => AlertDialog(
content: Text("Cancelled "),
));
} catch (e) {
print('$e');
}
}A Virtual Private Network (VPN) connection is a private network that connects multiple devices remotely through the Internet. Traffic over the VPN network is sent encrypted. With a VPN connection, you add an extra layer of security to your (company) network. For a more detailed explanation of VPN networks, see our in-depth blog post «What is a VPN connection?».
In this tutorial, we show you how to install a VPN server in Windows Server 2019 and make a VPN connection from another computer, for example, your computer at home.
The steps in this tutorial require an SSL certificate via IIS on your VPN server.
Installing a VPN server
Step 1
Connect to your Windows Server via Remote Desktop or the VPS console.
Step 2
Open the ‘Server Manager‘ via the Windows Start button > Server Manager.
Step 3
Click on ‘Add roles and features‘ in the dashboard of the Server Manager.
Step 4
You will now see the ‘Before You Begin‘ page. You can select not to see this page again when you add roles & features in the future. Click on ‘Next‘ after you have read the points under ‘before you continue‘.
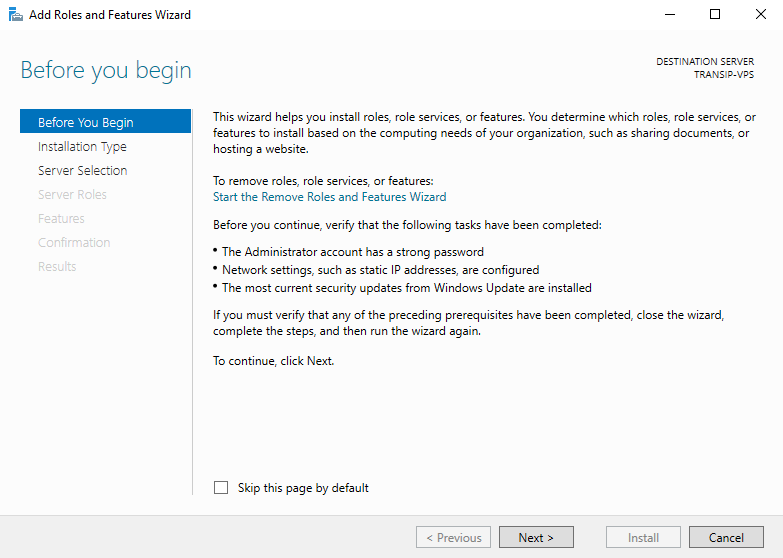
Step 5
Under ‘Installation Type‘ you can choose between ‘Role-based or feature-based‘ and ‘Remote Desktop Services installation‘. Choose ‘Role-based or feature-based‘ and continue to the next step.
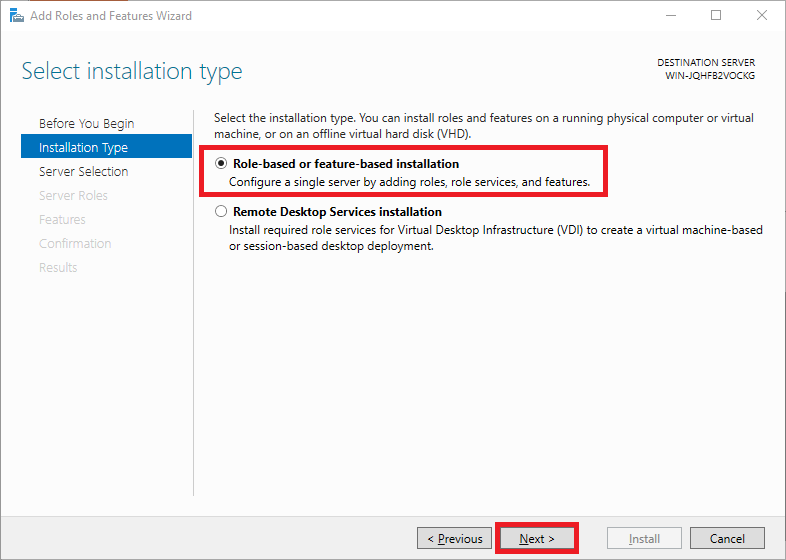
Step 6
Select the desired VPS on which you want to perform the installation. If you use an Active Directory and it contains several VPSs, these are listed in this overview. If you do not use Active Directory, you will see the VPS on which you go through this tutorial.
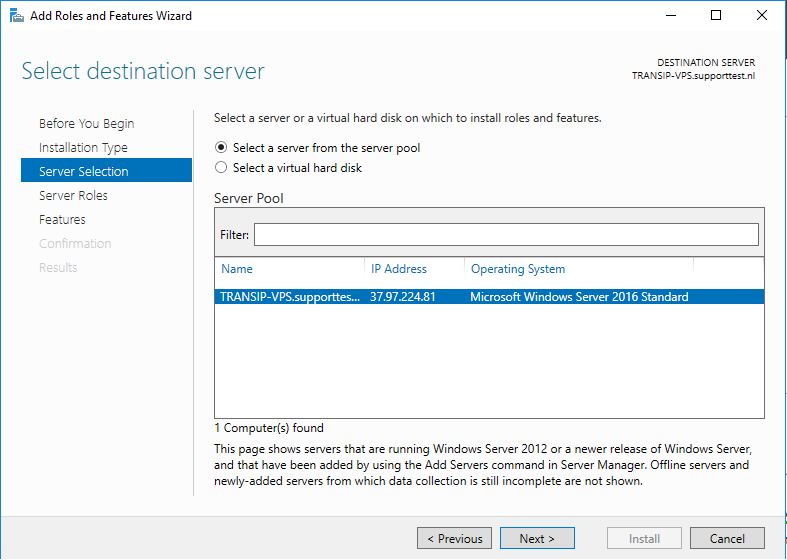
Step 7
On the next page, you can select a ‘Server Role‘. Select ‘Remote Access‘ (including responsible for VPN) and click on ‘Next‘. You do not have to adjust any other options already checked.
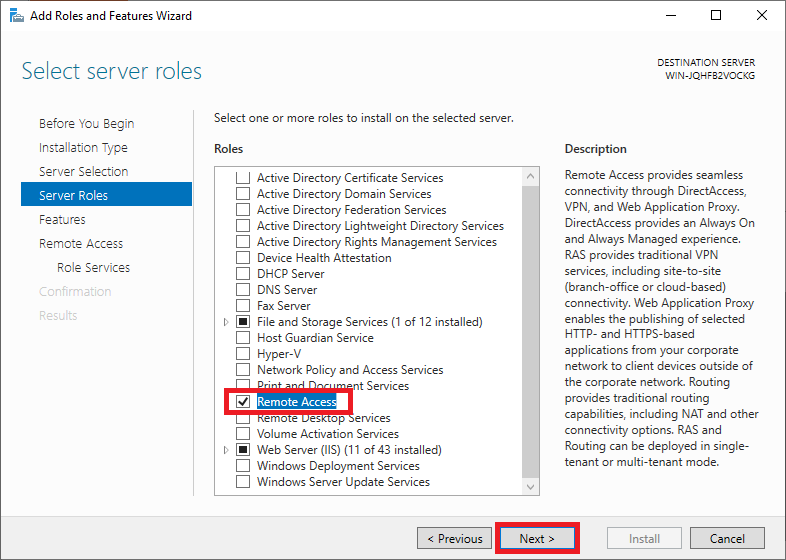
Step 8
You do not have to select or adjust features. Click immediately on ‘Next‘ to continue.
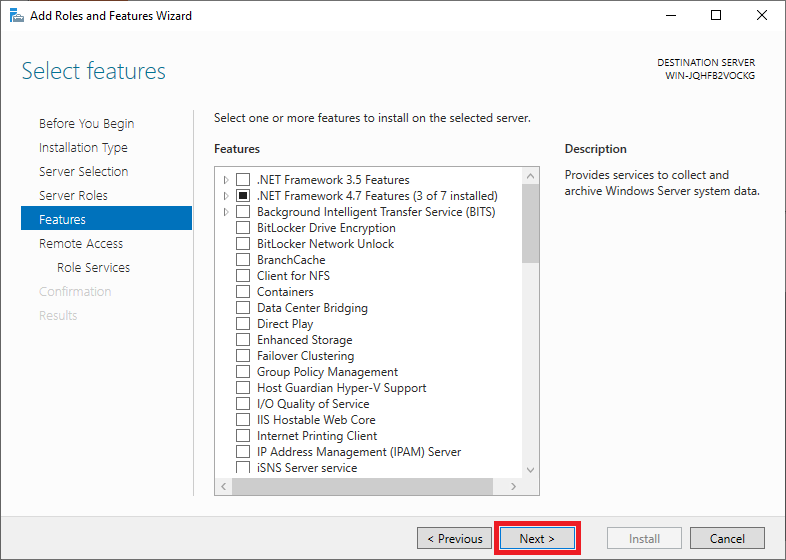
Step 9
You will see a description of the Remote Access role. Click on ‘Next‘ to continue.
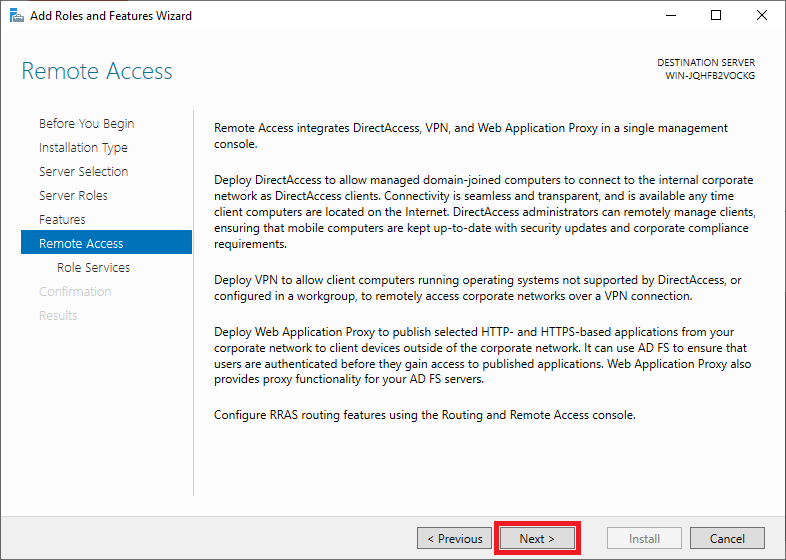
Step 10
Then select the ‘role services‘ of the Remote Access role you want to use. Click here on ‘DirectAccess and VPN (RAS)‘.
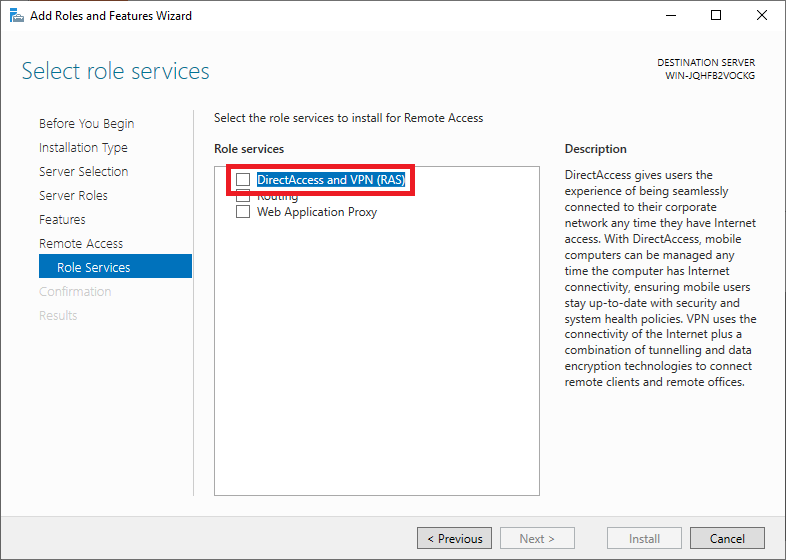
You should probably see a pop-up with an overview of role services and features that need to be added to use the DirectAccess and VPN (RAS). Click on ‘Add Features‘ to have it added automatically.
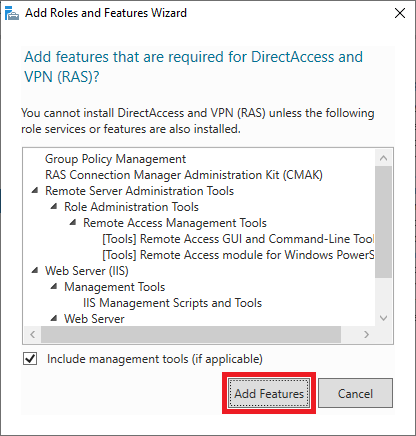
After this, you return to the ‘Role Services‘ screen and the option ‘DirectAccess and VPN (RAS)‘ is checked. Also, check the ‘Routing’ option and click ‘Next‘ to proceed to the next step.
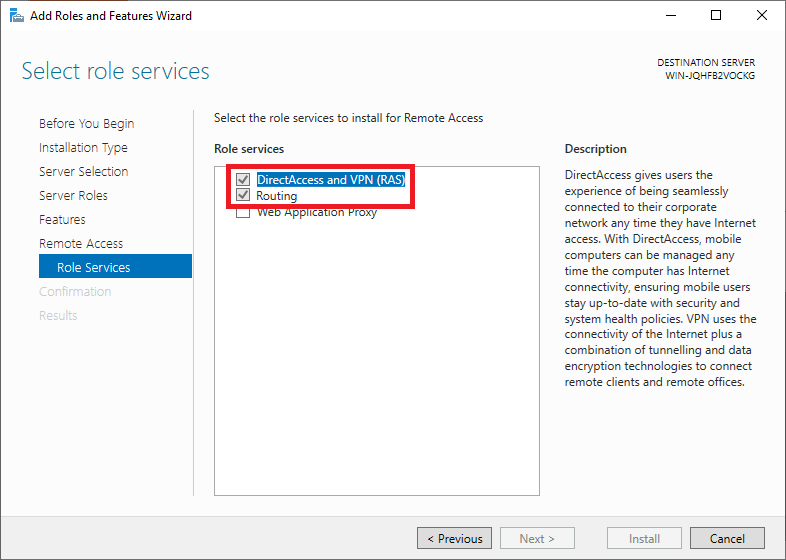
Step 11
Before the installation starts, you will see a confirmation of the options you selected in the previous steps.
Check ‘Restart the destination server automatically if required‘: it is always important (if an installation requires it) to restart your server to ensure the proper functioning of the role/feature.
Finally, click on ‘Install‘. The installation itself takes a few minutes, so feel free to grab a cup of coffee before proceeding to the next step.
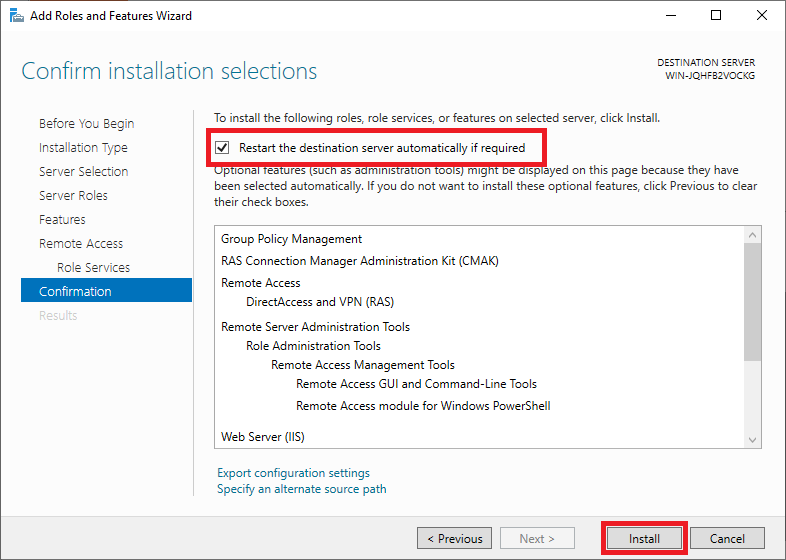
Step 12
Do not close the confirmation screen after installation, but click on ‘Open the Getting Started Wizard‘. It may take a minute to open. If not, click in the Server Manager on ‘Tools‘> ‘Remote Access Management‘.
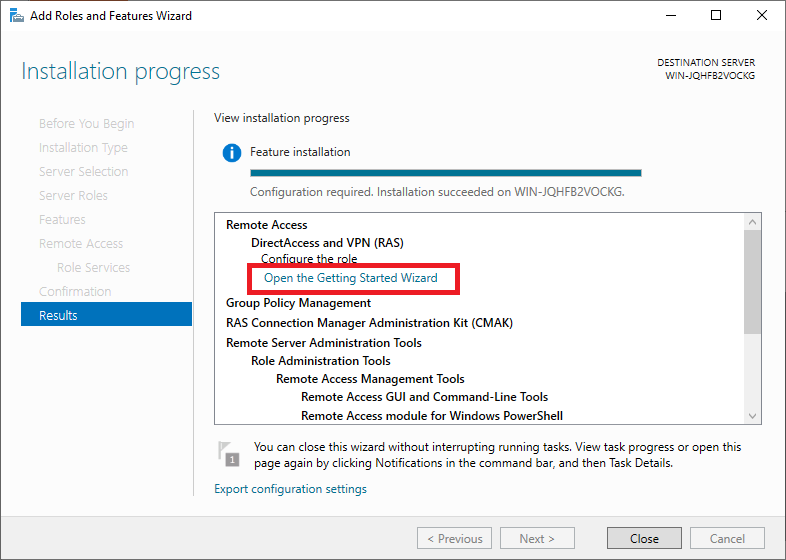
Step 13
You are greeted by the screen below. Before proceeding with the wizard, it is useful to first open the necessary ports in your firewall; otherwise, you will get an error after going through this wizard.
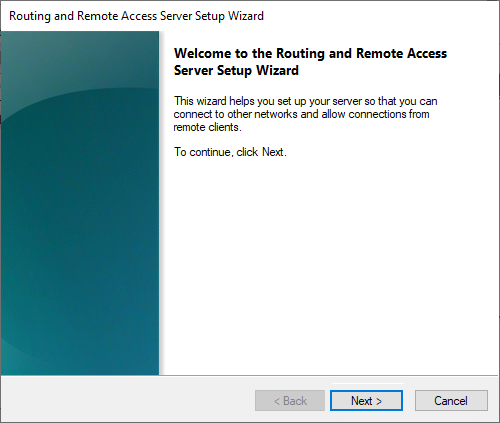
Do not close the wizard and click the Windows Start button, type ‘firewall‘ and click ‘Windows Defender Firewall with Advanced Security‘ in the search results.
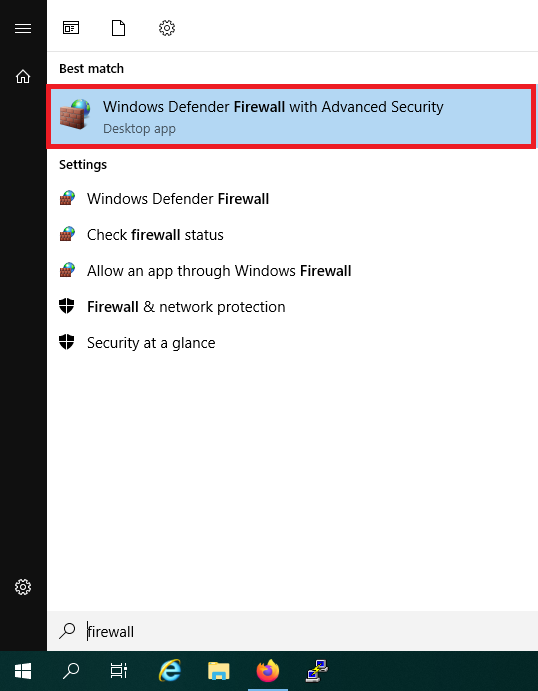
Step 14
Click on ‘Inbound rules‘ and scroll down to the ‘Secure Socket Tunneling Protocol (SSTP-in)‘. This rule is probably already on. If not, right-click on the line and select ‘Enable rule‘.
There are several protocols you can use for a VPN server. For this tutorial, we choose the best of all worlds: a combination of security (256-bit encryption), stability and speed. The SSTP protocol using the HTTPS port 443 is the best fit, see this page for more information.
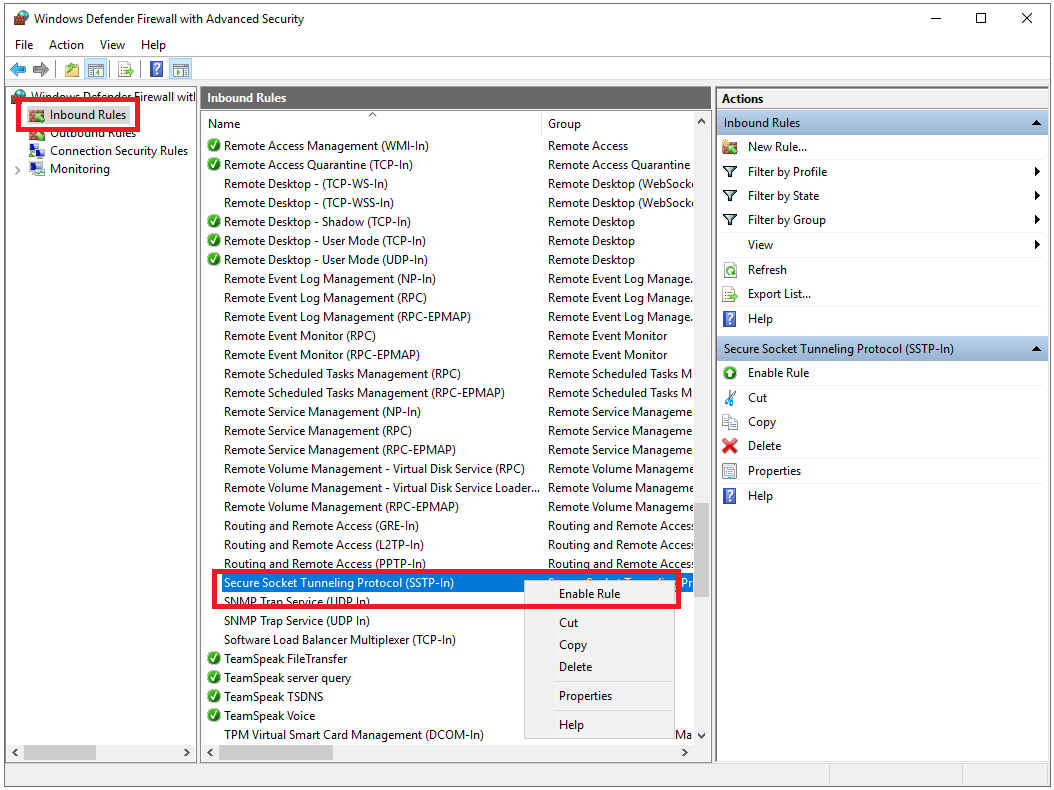
Step 15
Then close Windows Defender Firewall with Advanced Security and return to the ‘Remote Access Server Setup Wizard‘ and click ‘Next‘.
Step 16
Click on ‘Deploy VPN only‘.
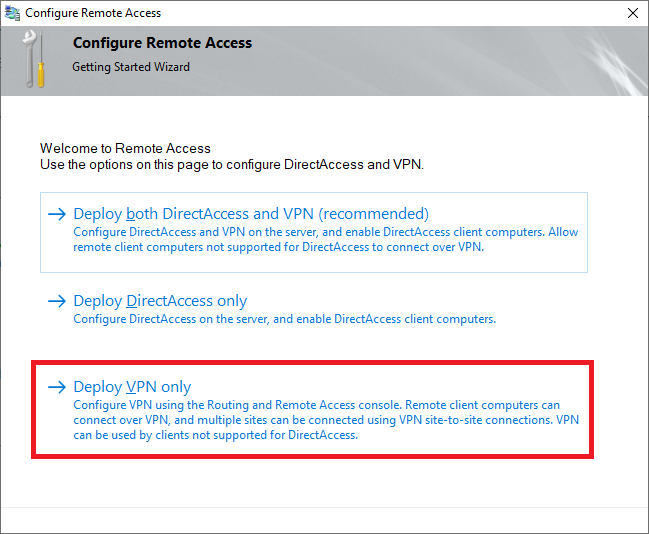
Step 17
The ‘Routing and Remote Access Management Console‘ now opens. Right-click on the name of your VPS and click on ‘Configure and Enable Routing and Remote Access‘.
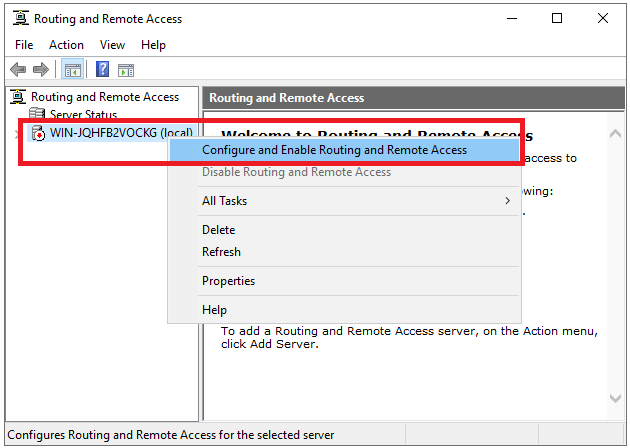
Step 18
Click on ‘Custom configuration‘> ‘Next‘ in the Configuration screen. This gives you the option to specifically configure a VPN server instead of installing services that you don’t need.
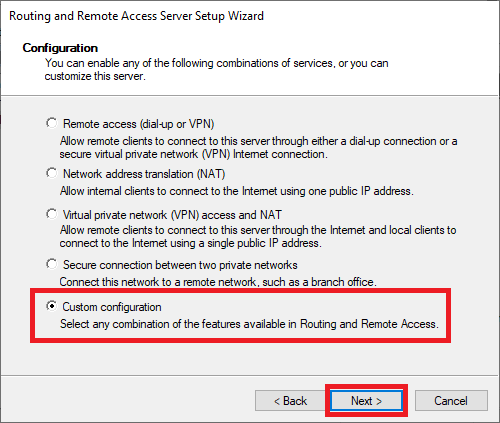
Step 19
Select ‘VPN Access‘ and ‘NAT‘ and click ‘Next‘.
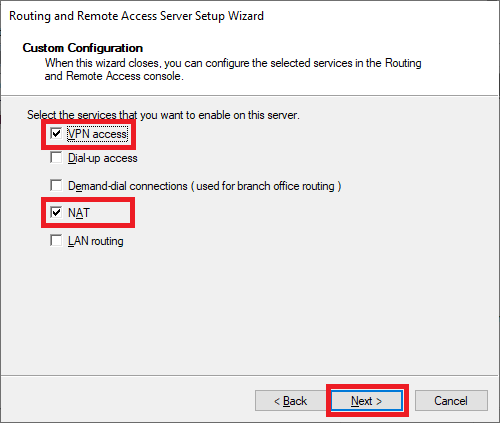
Step 20
That brings you to the end of the configuration wizard. Click on ‘Finish‘ to complete the configuration.
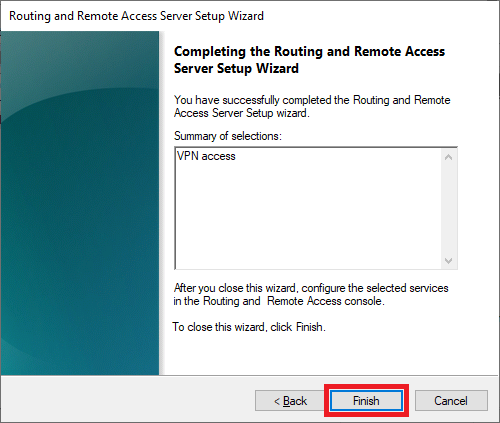
Finally, you will be given the option to start your VPN server. Click here on ‘Start service‘.
Step 21
You are now back in the ‘Routing and Remote Access Management Console‘, see step 17. Right-click on your VPN server and then ‘Properties‘.
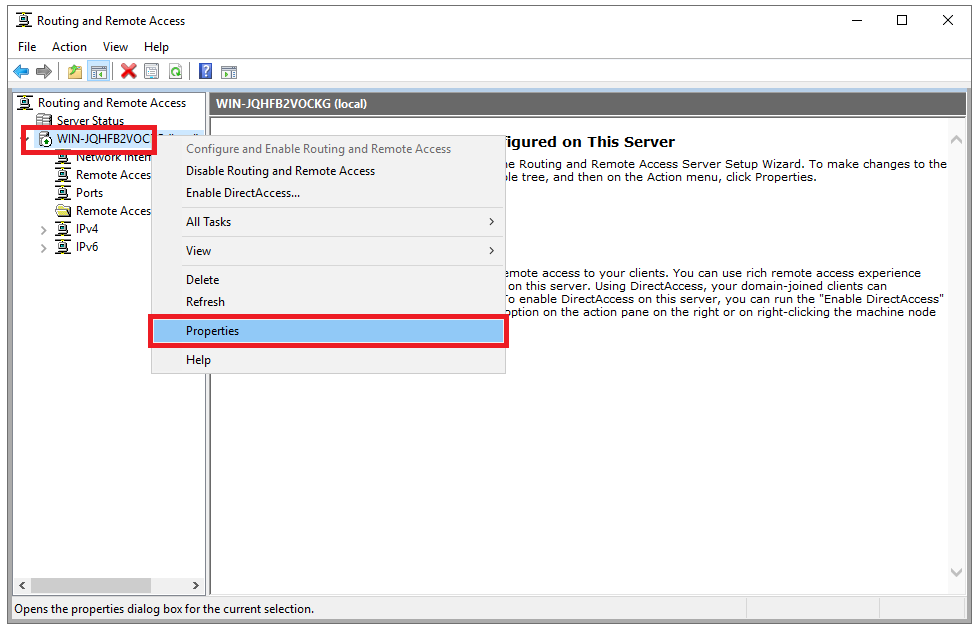
Step 22
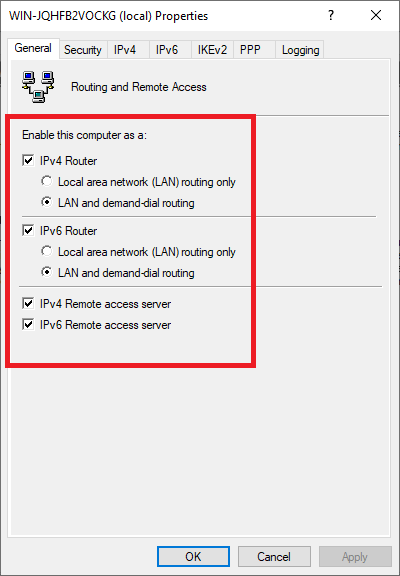
Check both ‘IPv4 Router’ and ‘IPv6 Router‘ with both the option ‘LAN and demand-dial routing‘ and the options ‘IPv4 Remote access server‘ and ‘IPv6 Remote access server‘.
Then, click on the ‘IPv4‘ tab and select ‘Static address pool‘ > ‘Add‘.
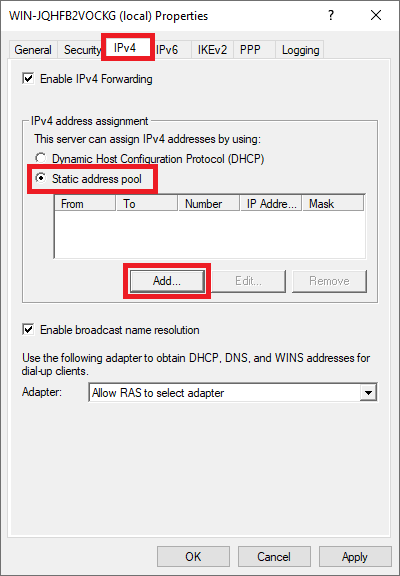
Step 23
Enter the IP range for your VPN network, for example from 10.10.0.0 to 10.10.255.255 and click ‘OK‘ (a smaller range is of course also possible, such as 10.10.10.0 to 10.10.10.255).
Step 24
You will now return to the screen from the previous step. Now click on the ‘IPv6‘ tab and enter an IPv6 prefix assignment, for example, fe80: 7c8: 7c8: f866::
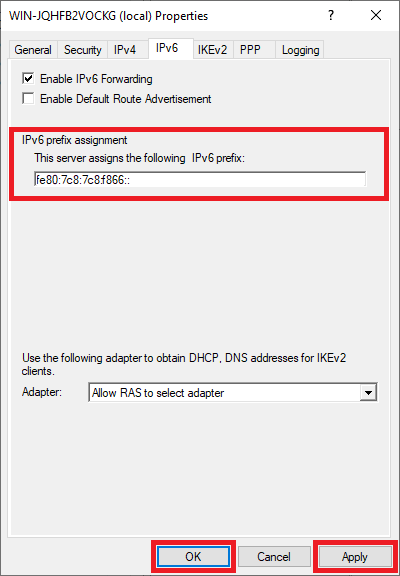
Then click ‘Apply‘ and ‘OK‘ to apply the changes.
You will probably now receive a message that RRAS (Routing and Remote Access) must restart. Allow this and after restarting proceed to the next step.
Step 25
Expand ‘IPv4‘ and select ‘NAT‘. Then right-click on an empty spot on the right side of the screen and select ‘New Interface …‘
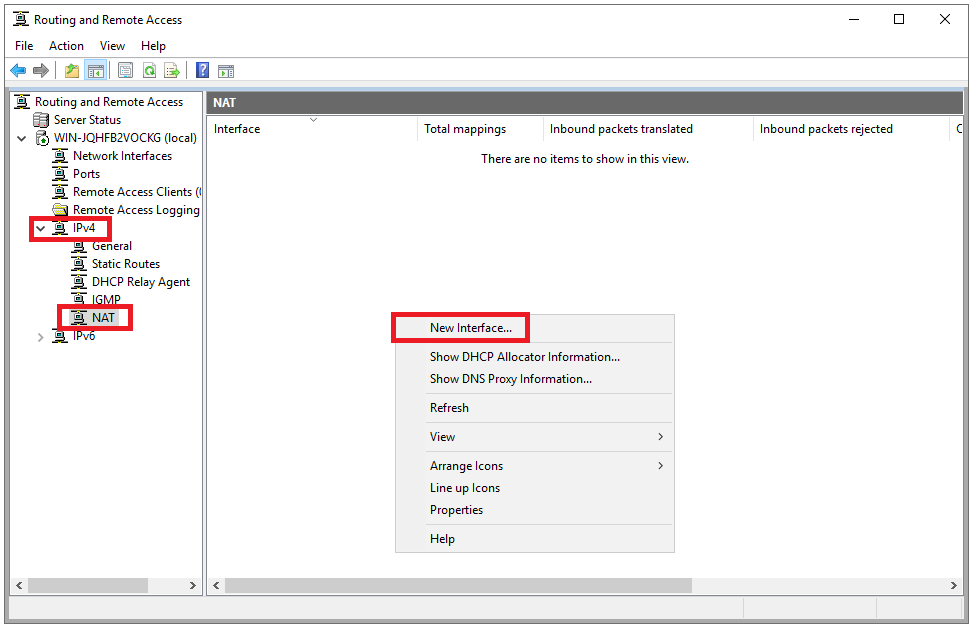
Step 26
Select ‘Ethernet‘ as the interface for the routing protocol and click ‘OK‘.
Step 27
Double click on ‘Ethernet‘ and check ‘Enable NAT on this interface‘.
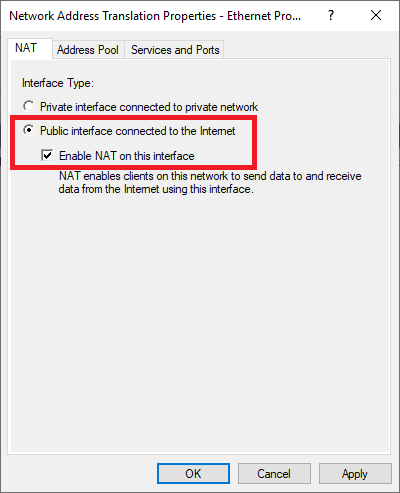
Step 28
Click on the ‘Services and Ports‘ tab and check the options below one by one. When you click on them, a pop-up will appear with information about the service. Adjust the ‘Private Address‘ value to 127.0.0.1 for:
- IP Security (IKE)
- IP Security (IKE NAT traversal)
- Remote Desktop
- Secure Web Server (HTTPS)
- VPN Gateway (L2TP / IPsec — running on this server)
- VPN Gateway (PPTP)
- Web Server (HTTP)
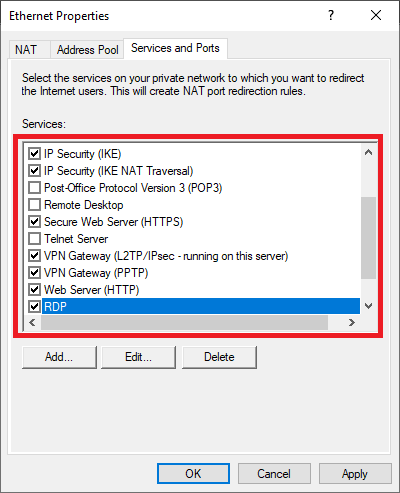
Do you use a custom port for Remote Desktop? Click on ‘Add‘ and add a TCP line for the correct port and also use 127.0.0.1 as a Private address.
Finally, click on ‘Apply‘ and ‘OK‘.
Step 29
You should now be prompted to restart RRAS. If not, right-click on your VPN server > ‘all tasks‘ > ‘restart‘ in the ‘Routing and Remote Access console‘ to process the changes.
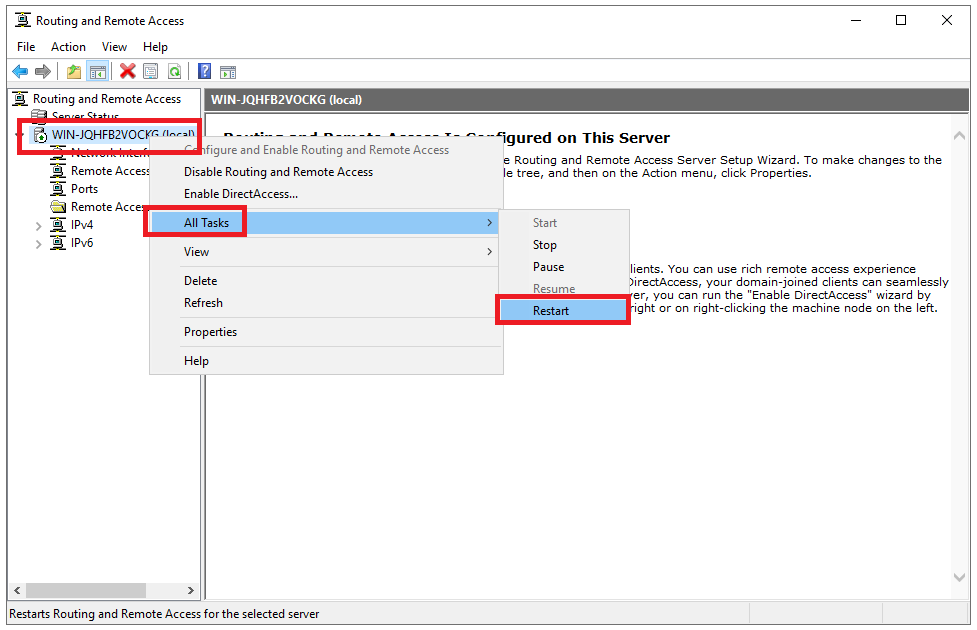
Your VPN server is now ready to accept VPN connections. Great! but what next? In the following sections, we explain how to authorize users, connect to your VPN server and what you can use it for.
Step 1
Before a user can connect to your VPN server, that user must be authorized for Remote Access.
Not using Active Directory? Then click on the Windows start button, search for ‘computer‘ and click on ‘Computer Management‘ in the results.
Do you use an Active Directory? Then click on the Windows start button, search for ‘group‘ and click on ‘Group Policy Management‘ in the results.
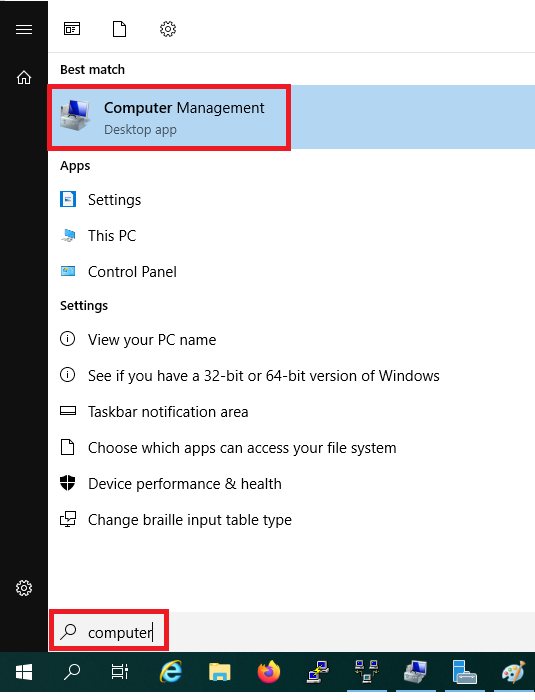
Step 2
You are free to create a new user for your VPN connection or use an existing one. Click on ‘Local Users and Groups‘ > ‘Users‘.
-
Existing user: Click on the name of the user
- New user: Right-click on an empty piece and then ‘New User‘. Enter the name of the new user, optionally disable ‘User must change password at next logon‘, and enter a password.
After creating the new user, close the ‘New User‘ screen and double click on the name of the account.
Step 3
Click on the ‘Dial-in‘ tab, under ‘Network Access Permission‘ check the option ‘Allow access‘ and finally click ‘Apply‘ and ‘OK‘ to confirm your changes.
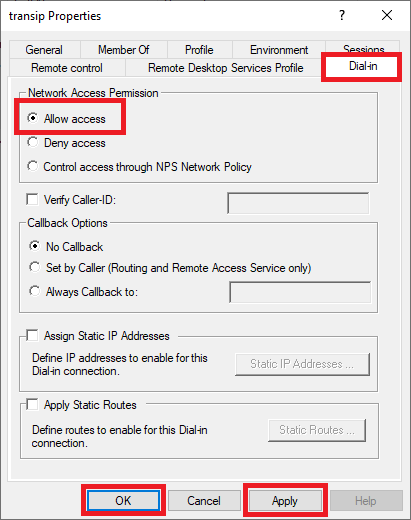
That’s it! You can now connect to your VPN server. We explain how this works in the next section.
Connect to your VPN network
- This tutorial assumes a Windows computer/laptop. For MacOS, you can use this guide from Apple. To connect to your VPN server, enter the IP address of your VPS and as VPN type ‘SSTP‘.
- You go through the steps once per computer. You only need the last step to connect to your VPN server from now on.
Step 1
Now that your VPN server is ready and your user is authorized, it’s time to connect to your VPN server. First, you need to add the VPN connection to your (client) computer/laptop once.
Click the Windows Start button and the Settings icon.
Step 2
Then click on ‘Network & Internet‘.
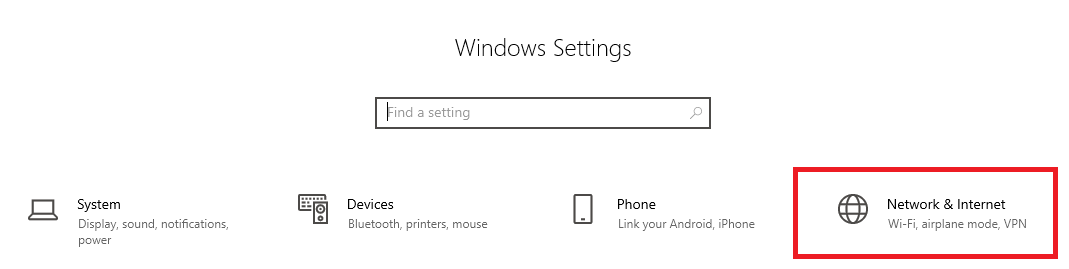
Step 3
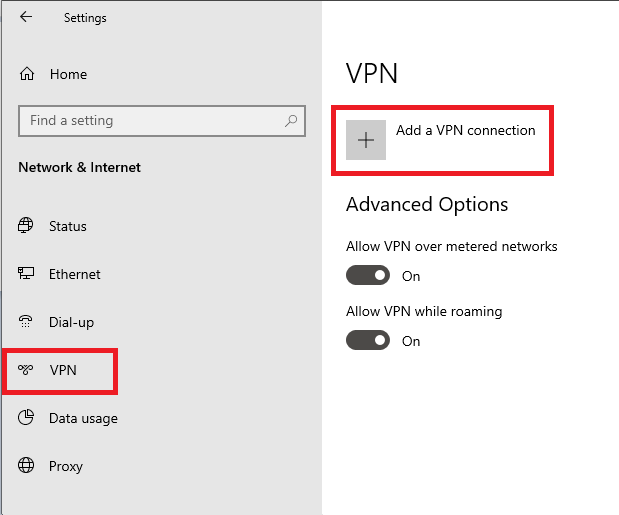
Click on ‘VPN‘ on the left and then on ‘Add a VPN connection‘.
Step 4
Enter the details on the ‘Add a VPN connection‘ screen that appears. Mind the following:
- Select ‘Windows (built-in)‘ as the VPN provider
- As ‘Server name or address‘, use the IPv4 address of your server, or a domain name that refers to your VPS.
- Choose as VPN type: ‘Secure Socket Tunneling Protocol (SSTP)‘.
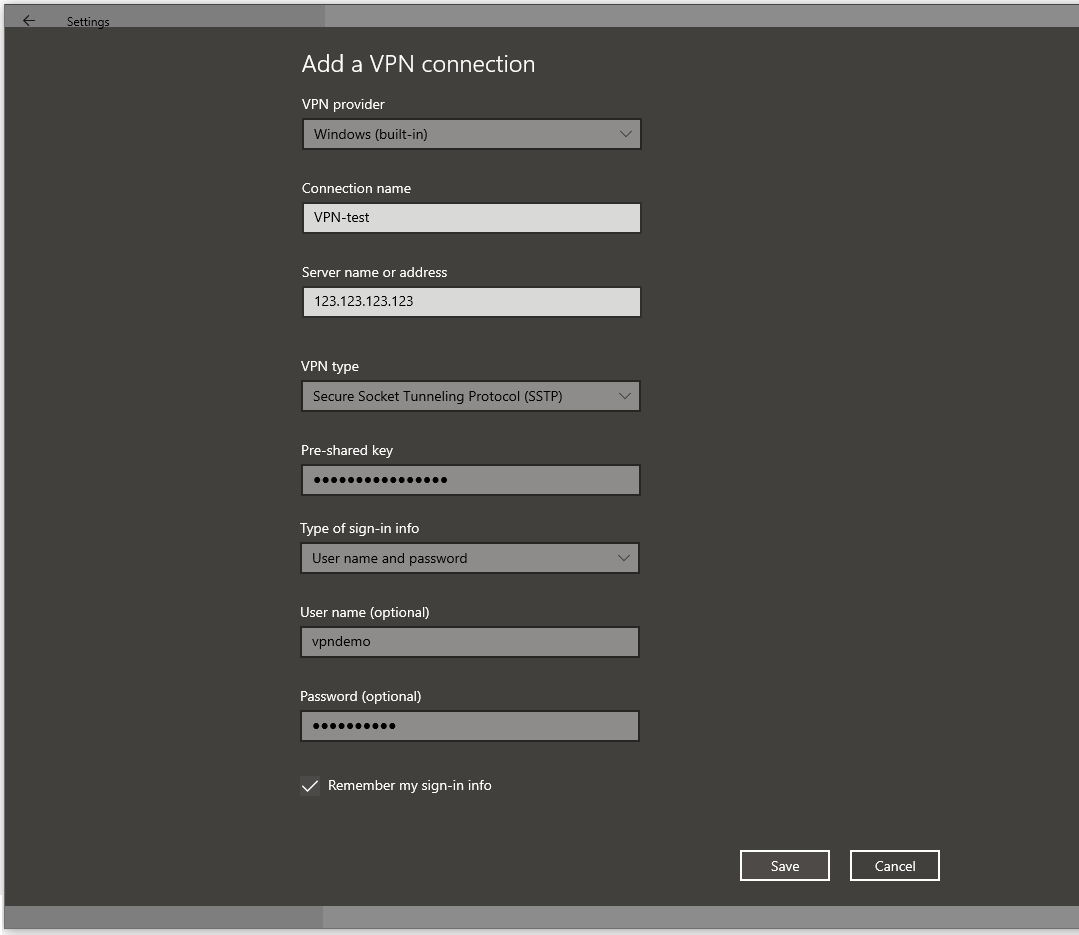
Step 5
All your internet traffic is standard over the VPN and uses the default gateway of the VPN server. This means that if you navigate on a client computer in a browser, you are using the connection of your VPS.
We assume in this tutorial that for your regular internet traffic you would like to use your own connection. You can achieve this by setting your own connection as the default gateway for your VPN as follows:
Click on the Windows Start button, type ‘Internet Options‘ and click on the top result.
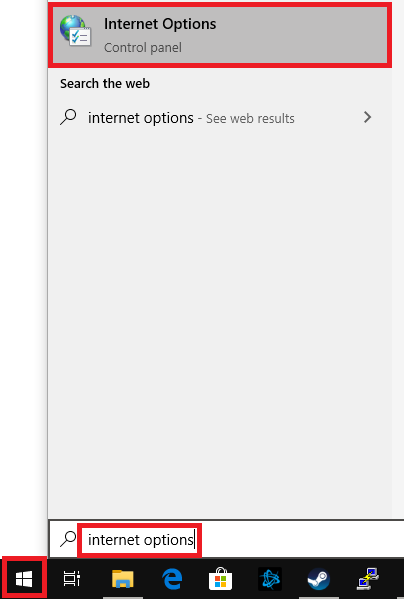
Step 6
Go to the ‘Connections‘ tab, select your VPN connection and click ‘Settings‘.
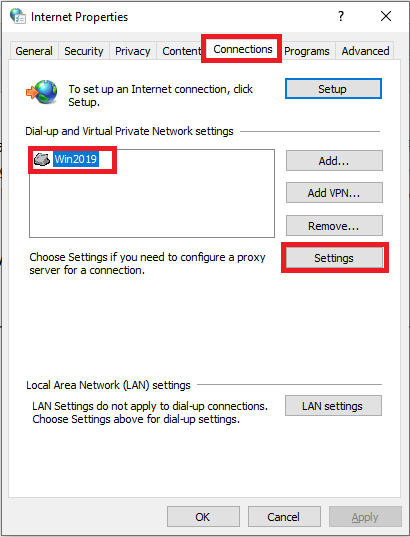
Step 7
In the window that appears, click on ‘Properties‘.
Step 8
Go to the ‘Networking‘ tab and select ‘Internet Protocol Version 4 (TCP / IPv4)‘ followed by ‘Properties‘.
Step 9
Click on ‘Advanced‘.
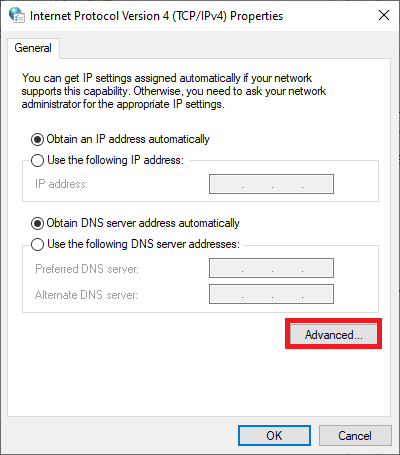
Step 10
Uncheck ‘Use default gateway on remote network‘ and click ‘OK‘.
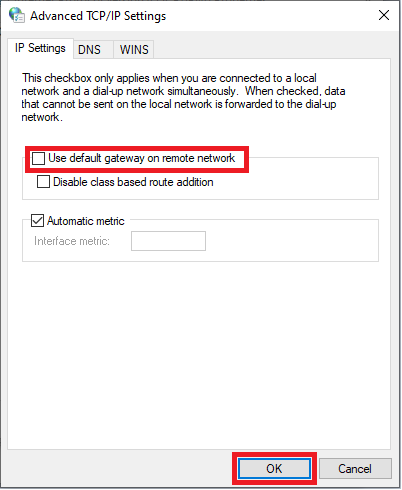
You will now return to the window from step 9. Click on ‘OK‘ there as well and repeat steps 8 to 10, but then for ‘Internet Protocol Version 6 (TCP / IPv6)‘.
Then click ‘OK‘ at each screen where you return until you return to the ‘Internet Properties‘ screen from step 6 and click ‘Apply‘ and ‘OK‘ there.
Step 11
Finally, click on the network icon at the bottom right of your screen and click on the name of your VPN connection, followed by ‘Connect‘. From now on, this is the only step you need to go through to reconnect to your VPN server.
Use Cases
Now that your VPN connection is working, you may be wondering what you can do with it. A VPN connection is powerful in combination with a firewall. You can set a scope for a rule in most firewall software, for example in Windows Defender Firewall with Advanced Security, see for example our tutorial on changing the Remote Desktop port.
By only allowing the range or specific addresses of your VPN connection as Remote IP address in the scope of your firewall rule, you limit access to the associated service to those IP addresses. Some examples of applications are:
- Restrict access to the Remote Desktop port to the IP range of your VPN network (10.10.0.0/24 for example).
- Restrict access to a website that you host on a server in your VPN network. This is useful, for example, for an internal administration system that can be reached via a web interface/website. You achieve this by limiting access to ports 80 and 443 on the server hosting your website to the IP range of your VPN network.
- Restrict access to an SMB server by restricting access to port 445 on the SMB server to the IP range of your VPN network.
That brings us to the end of this tutorial for setting up a VPN server in Windows Server 2019.
If you have any questions regarding this article, please do not hesitate to contact our support department. You can reach them via the button ‘Contact us‘ at the bottom of this page.
Routing And Remote Access Service Rras Network Encyclopedia This blog post is a step by step guide on how to install routing and remote access service on windows server 2019. overview: the remote access server role provides three network access technologies in windows server 2019. Routing and remote access services (rras) supports remote user or site to site connectivity by using virtual private network (vpn) or dial up connections. it accepts vpn connections based on protocols such as pptp, l2tp, sstp, and ikev2. these protocols are all enabled by default when the rras role is installed and setup with default configuration.

Install A Nat Router With Windows Server Routing And Remote Access Basic rras (routing and remote access service) installation process on windows server 2019. this is a brief guide only and a separate video will be uploaded later with an. With rras, windows server can function as a nat router, vpn server, or gateway for internal and vpn connected networks. this guide covers step by step instructions for configuring nat and enabling features like dhcp and dns proxy for seamless network management. Configure the server network settings on the remote access server. configure routing in the corporate network to make sure traffic is appropriately routed. configure additional firewalls, if required. configure a certification authority (ca), if required, and any other certificate templates required in the deployment. In this post, we will be configuring windows server 2019 as a nat (network address translation) router to route traffic between local lan and the internet. the windows server 2019 must have two network adapters, one configured for the internal local network (lan) and another one configured to access the internet (internet).
How To Install Remote Access Service On Windows Server 2019 Part 1 Configure the server network settings on the remote access server. configure routing in the corporate network to make sure traffic is appropriately routed. configure additional firewalls, if required. configure a certification authority (ca), if required, and any other certificate templates required in the deployment. In this post, we will be configuring windows server 2019 as a nat (network address translation) router to route traffic between local lan and the internet. the windows server 2019 must have two network adapters, one configured for the internal local network (lan) and another one configured to access the internet (internet). Install lan routing service on windows server 2019: the lan routing role service is part of the remote access server role. let’s install the remote access server role on the ws2k19 srv02 server. Rras supports remote user or site to site connectivity via using virtual private network (vpn) or dial up connections. you can read more in the official documentation page of the routing. This step by step guide describes how to set up a routing and remote access service on windows server 2003 standard edition or windows server 2003 enterprise edition to allow authenticated users to remotely connect to another network by way of the internet. In this post, i will be deploying rras (routing and remote access server). more specifically, i will utilize the ‘routing’ component of rras.
How To Install Remote Access Service On Windows Server 2019 Part 1 Install lan routing service on windows server 2019: the lan routing role service is part of the remote access server role. let’s install the remote access server role on the ws2k19 srv02 server. Rras supports remote user or site to site connectivity via using virtual private network (vpn) or dial up connections. you can read more in the official documentation page of the routing. This step by step guide describes how to set up a routing and remote access service on windows server 2003 standard edition or windows server 2003 enterprise edition to allow authenticated users to remotely connect to another network by way of the internet. In this post, i will be deploying rras (routing and remote access server). more specifically, i will utilize the ‘routing’ component of rras.
How To Install Remote Access Service On Windows Server 2019 Part 1 This step by step guide describes how to set up a routing and remote access service on windows server 2003 standard edition or windows server 2003 enterprise edition to allow authenticated users to remotely connect to another network by way of the internet. In this post, i will be deploying rras (routing and remote access server). more specifically, i will utilize the ‘routing’ component of rras.
