Содержание
Просмотр системного журнала
Если в работе Windows 2012 появляется какая-то нестабильность, или появляются ошибки запуска\установки приложений, то это может быть связано с появлениями ошибок в самой операционной системе.
Все системные ошибки и предупреждения можно найти в «Журнале системы«.
В нем сохраняется информация о событиях, записываемых системными компонентами Windows.
Для просмотра и сохранения системного журнала нужно выполнить шаги:
Открыть «Пуск«:
Открыть «Панель управления«:

В «Панели управления» выбрать «Просмотр журналов событий«

В открывшемся окне выбрать «Просмотр событий» -> «Журналы Windows» -> «Система«

Экспорт журнала
Системный журнал в полном объеме можно выгрузить путем нажатия на ссылку «Сохранить все события как…«

После нажатия ссылки «Сохранить все события как…» нужно выбрать путь и имя файла для сохраняемого журнала.
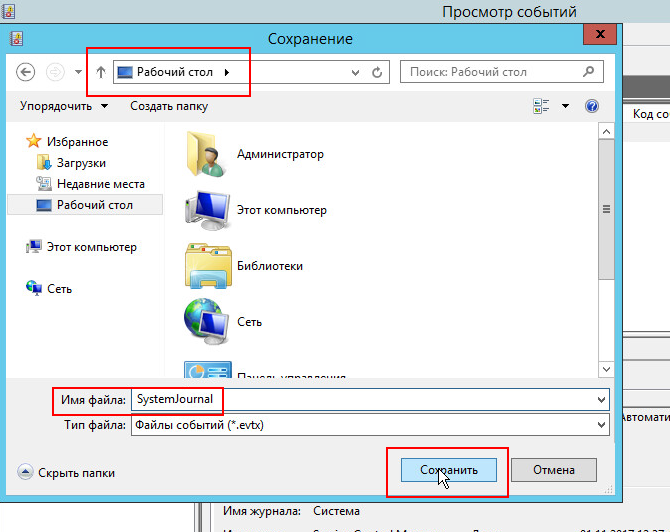
При сохранении файла возможно появление окна «Отображение сведений«.
В данном окне нужно выбрать пункт «Отображать сведения для следуюших языков: Русский«

Готово
The Event Log is a powerful tool in Windows Server 2012 R2 that allows you to track and analyze system events and troubleshoot issues. It records information about various system events such as system startup/shutdown, hardware and software failures, security issues, and more. In this tutorial, we will guide you through the steps to check the Event Log on Windows Server 2012 R2.
Step 1: Open the Event Viewer
– Click on the Start button or press the Windows key.
– In the search bar, type «Event Viewer» and click on the «Event Viewer» app.
Step 2: Navigate to the Event Log
– In the Event Viewer window, you will see a tree-like structure on the left side.
– Expand the «Windows Logs» node to view the various event logs available.
– The commonly used event logs are:
– Application: Contains events logged by installed applications.
– Security: Records security-related events such as login attempts, user account changes, etc.
– System: Logs events related to system components, drivers, and services.
– Setup: Stores events related to Windows setup and installation.
Step 3: Check Event Log Details
– Click on the desired event log, for example, «Application.«
– You will see a list of events in the middle pane, with detailed information such as the date, time, event ID, source, and description.
– You can double-click on an event to view its specific details and additional information.
Step 4: Filter Events (optional)
– If you want to narrow down the events based on specific criteria, you can use the filtering option.
– In the right pane, click on «Filter Current Log» under «Actions.«
– Specify the desired filter criteria such as event sources, event IDs, keywords, etc.
– Click OK to apply the filter and view the filtered events.
Step 5: Clear Event Log (optional)
– If you want to clear the events from a specific event log, you can do so by right-clicking on the log and selecting «Clear Log.«
– A confirmation dialog box will appear, asking if you want to save the log before clearing. Choose the desired option.
Step 6: Export Event Log (optional)
– If you need to save a copy of the event log or share it with others, you can export it to a file.
– Right-click on the desired event log and select «Save All Events As.«
– Choose the file format (e.g., CSV, EVT, XML) and specify the location to save the file.
Pros Cons
1. Efficient troubleshooting tool 1. Overwhelming amount of data
2. Helps identify underlying issues 2. Requires understanding of event codes and descriptions
3. Provides detailed information 3. May not always provide clear solutions
By following these steps, you can easily check the Event Log on Windows Server 2012 R2 and leverage its valuable insights for system analysis and troubleshooting.
Video Tutorial: How do I find event logs in Windows Server?
Where are the event logs stored in Windows 2012?
In Windows 2012, event logs are stored in specific locations on the file system. Here are the default storage locations for event logs:
1. Application and Service Logs: The event logs for various applications and services are stored in the «C:\Windows\System32\winevt\Logs» directory. Each application or service has its folder within this directory, and the corresponding log files are stored there.
2. Windows Logs: The built-in Windows logs, such as Application, Security, System, Setup, and Forwarded Events, are located in the «C:\Windows\System32\winevt\Logs» directory as well. Each log file for these categories is stored in their respective folder within this directory.
To access the event logs in Windows 2012, you can follow these steps:
1. Open the Event Viewer: Press the Windows key + R to open the Run dialog box, then type «eventvwr.msc» and hit Enter. Alternatively, you can search for «Event Viewer» in the Start menu and select the corresponding result.
2. Navigate to the desired log: In the Event Viewer window, you will find a list of event logs on the left-hand side. Expand the «Windows Logs» folder and click on the specific log you want to view, such as «Application» or «Security.«
3. View log entries: Once you have selected a log, the central pane will display the log entries chronologically. You can scroll through the entries to examine the details, including event ID, source, date, and time.
Remember, the above instructions are specific to Windows 2012. Please note that the file paths or steps may vary slightly in different Windows versions, and depending on any system modifications or customizations made.
How do I view event logs?
To view event logs on various devices, you can follow these general steps:
1. Windows PC:
– Press the Windows key + R to open the Run dialog box.
– Type «eventvwr.msc» and hit Enter.
– In the Event Viewer window, you can browse different logs like Application, Security, and System. Expand the desired log to view events.
2. macOS:
– Click on the Spotlight search icon (magnifying glass) in the menu bar.
– Type «Console» and press Enter.
– The Console app will open, displaying logs from different categories on the left. Click on the desired log type to view events.
3. Linux (Ubuntu/Debian-based):
– Open the Terminal by pressing Ctrl + Alt + T.
– Type «sudo less /var/log/syslog» and press Enter.
– You can replace «syslog» with other log filenames like «auth.log» or «kern.log» to view specific event logs.
4. Android:
– Open the Settings app on your Android device.
– Look for the «About phone» or «About device» option and tap on it.
– Find «Build number» and tap on it multiple times until it enables developer options.
– Go back to the main Settings screen and find «Developer options» or «Developer settings.«
– Open «Developer options» and look for «Enable USB debugging» or a similar option.
– Connect your Android device to your computer via USB and use tools like Android Debug Bridge (ADB) to view logs.
5. iOS (iPhone/iPad):
– Connect your iPhone or iPad to a computer with iTunes or Finder installed.
– Open iTunes or Finder and select your device.
– Choose the «Summary» or «General» tab and look for the «View logs» or «Console» option.
– Click on it to view the event logs related to your iOS device.
Remember, the specific steps may vary depending on the operating system version and device, but these general guidelines should help you in viewing event logs across various platforms.
How do I export event logs from Windows Server 2012 r2?
To export event logs from Windows Server 2012 R2, follow these steps:
1. Launch the Event Viewer: Press the Windows key + X on your keyboard, then select «Event Viewer» from the menu that appears.
2. In the Event Viewer window, navigate to the specific event log you want to export. For example, if you want to export the System event log, expand the «Windows Logs» folder and select «System.«
3. Right-click on the event log you’ve selected and choose «Save All Events As.«
4. In the «Save As» dialog box, choose a destination folder where you want to save the exported event log. Provide a filename and select a file format, such as «CSV» (Comma Separated Value) or «EVTX» (Event Log Format). CSV is a widely used format that allows for easy analysis using spreadsheet programs like Microsoft Excel.
5. Click the «Save» button to begin the export process. A progress bar will indicate the status of the export.
6. Once the export is complete, you can find the exported event log file in the destination folder you selected earlier.
By following these steps, you will be able to export event logs from Windows Server 2012 R2. Remember to choose an appropriate file format that suits your needs for analysis or sharing purposes.
How to check user login history in Windows Server 2012 r2 Powershell?
In Windows Server 2012 R2, you can utilize PowerShell to check user login history by performing the following steps:
1. Open PowerShell: Click on the Start button, search for «PowerShell,» and select the PowerShell application.
2. Run PowerShell as an Administrator: Right-click on the PowerShell icon and choose «Run as Administrator» to ensure you have the necessary privileges to access the required information.
3. Enter PowerShell command: Once the PowerShell window opens, enter the following command:
«`powershell
Get-WinEvent -FilterHashtable @{Logname=’Security’; ID=’4624′} | Select-Object -Property TimeCreated, Message | Format-List
«`
This command utilizes the `Get-WinEvent` cmdlet to retrieve security events with Event ID 4624, which represents successful logins. The `Select-Object` cmdlet is used to display only the TimeCreated and Message properties, and `Format-List` formats the output for better readability.
4. View the login history: After entering the command, press Enter to execute it. PowerShell will list the login history with details such as the time of login and related messages.
Please note that this method assumes the default configuration of Windows Server 2012 R2. If any modifications have been made to the event log settings or security policies, the command may need to be adjusted accordingly.
Remember, it’s crucial to run PowerShell as an administrator to obtain the necessary permissions to access user login history.
Where is event log in Windows Server 2012 R2?
In Windows Server 2012 R2, the Event Viewer is the tool to access event logs. Here are the steps to find the Event Viewer:
1. Click on the «Start» button located at the bottom-left corner of the screen.
2. In the search bar, type «Event Viewer» and click on the corresponding result.
3. The Event Viewer window will open, providing you access to various logs categorized by different event types.
4. Expand the «Windows Logs» section, which contains the event logs related to Windows system components.
5. Here, you will find different categories such as Application, Security, Setup, System, and Forwarded Events.
6. Click on any of these categories to see the corresponding event logs.
7. For example, if you’re troubleshooting an application-related issue, go ahead and select the «Application» event log.
8. Within each category, you can see a list of events with details like event type, date, time, source, and event ID.
By utilizing the Event Viewer in Windows Server 2012 R2, you can monitor and analyze various events occurring on your system for troubleshooting, security audits, and system health analysis without relying solely on error messages.
Please note that the specific steps to access the Event Viewer may vary slightly depending on the server’s configuration and any customizations made.
How to check user login history Windows Server 2012?
To check user login history on Windows Server 2012, you can follow these steps:
1. Open the Event Viewer: Press the Windows key + R on your keyboard to open the Run dialog box. Type «eventvwr.msc» and hit Enter. This will launch the Event Viewer.
2. Navigate to the Security Event Log: In the Event Viewer, expand the «Windows Logs» folder on the left-hand side. Then, click on «Security» to open the Security Event Log.
3. Filter the Event Log: In the middle pane of the Event Viewer, click on the «Filter Current Log» option. This will open the Filter Current Log dialog box.
4. Define the Filter Criteria: In the Filter Current Log dialog box, specify the filter criteria to view user login history. Under the «Event sources» section, select «Security» from the drop-down menu. Then, in the «Logged» section, enter the desired time frame or leave it blank to retrieve all login records. Finally, click on the «OK» button.
5. View User Login Events: The Event Viewer will now display the filtered user login events in the middle pane. You can review the events to see user logins, including their usernames, login timestamps, and other relevant details.
Note: The ability to view user login history may require administrative privileges or elevated access on the Windows Server 2012 system.
Windows Server 2012 features a robust logging system using the Event Viewer, which records detailed information about system activities, application behavior, and security events. Understanding how to leverage Event Logs is crucial for system administrators to troubleshoot issues, monitor server performance, and enhance security.
Windows Server 2012 maintains several types of event logs:
- Application Logs – Track events related to installed software.
- System Logs – Record system-level events, such as hardware issues and driver problems.
- Security Logs – Monitor security-related events, such as user logins, failed attempts, and permission changes.
This guide covers how to access, configure, and analyze event logs on Windows Server 2012 to improve server management and troubleshooting.
Log & Configuration File Locations
Before diving into details, it’s essential to know where Windows Server 2012 stores its logs:
| Log Type | Location |
|---|---|
| Application Logs | Event Viewer > Windows Logs > Application |
| System Logs | Event Viewer > Windows Logs > System |
| Security Logs | Event Viewer > Windows Logs > Security |
| Setup Logs | Event Viewer > Windows Logs > Setup |
| Custom Logs | Event Viewer > Applications and Services Logs |
All logs are stored in binary format files located at:
C:\Windows\System32\winevt\Logs\Understanding Windows Server 2012 Application Logs
What Are Application Logs?
Application logs capture events generated by software applications installed on the server. These logs are essential for:
- Troubleshooting application errors and crashes
- Monitoring software performance
- Analyzing application behavior
Accessing Application Logs
To access application logs:
- Open Event Viewer:
- Press
Win + X, then select Event Viewer. - Alternatively, press
Win + R, typeeventvwr, and press Enter.
- Press
- Expand Windows Logs.
- Click on Application to view a list of application events.
Sample Application Log Entry
Level: Error
Source: Application Error
Event ID: 1000
Task Category: (100)
Message: Faulting application name: w3wp.exe, version: 7.5.7601.17514, faulting module name: ntdll.dll, exception code: 0xc0000374.
| Field | Description |
|---|---|
| Level | Severity of the event (Information, Warning, Error) |
| Source | The application or service that generated the event |
| Event ID | Numeric code identifying the event |
| Message | Description of the event |
Understanding Windows Server 2012 System Logs
What Are System Logs?
System logs capture system-related events, such as hardware changes, driver updates, and operating system errors. These logs are crucial for:
- Diagnosing server crashes and failures
- Troubleshooting hardware and driver issues
- Monitoring system performance
Accessing System Logs
To access system logs:
- Open Event Viewer.
- Expand Windows Logs.
- Click on System to view system events.
Sample System Log Entry
Level: Warning
Source: Microsoft-Windows-Kernel-Power
Event ID: 41
Message: The system has rebooted without cleanly shutting down first. This error could be caused if the system stopped responding, crashed, or lost power unexpectedly.
Explanation: This log entry indicates that the system was improperly shut down, which could be due to a power failure or crash.
Understanding Windows Server 2012 Security Logs
What Are Security Logs?
Security logs track security-related events, such as user logins, failed access attempts, and changes to system permissions. These logs are essential for:
- Auditing user activity
- Monitoring unauthorized access attempts
- Detecting potential security breaches
Accessing Security Logs
To access security logs:
- Open Event Viewer.
- Expand Windows Logs.
- Click on Security to view security events.
Sample Security Log Entry
Level: Information
Source: Microsoft-Windows-Security-Auditing
Event ID: 4624
Task Category: Logon
Message: An account was successfully logged on. Subject: Security ID: S-1-5-18 Account Name: SERVER\Administrator
| Field | Description |
|---|---|
| Level | Severity (Information, Success Audit, Failure Audit) |
| Source | Service or application that generated the event |
| Event ID | Unique identifier for the event |
| Task Category | Context of the event (e.g., Logon) |
| Message | Detailed information about the event |
Common Security Event IDs
| Event ID | Description |
|---|---|
| 4624 | Successful logon |
| 4625 | Failed logon attempt |
| 4672 | Special privileges assigned to a new logon |
| 4688 | A new process has been created |
| 4719 | System audit policy was changed |
Using PowerShell to Access Event Logs
PowerShell provides a powerful way to query and filter event logs on Windows Server 2012:
Get a list of available logs:
Get-EventLog -ListView the most recent entries in the System log:
Get-EventLog -LogName System -Newest 10Filter logs by Event ID:
Get-EventLog -LogName Security -InstanceId 4624Export logs to a CSV file:
Get-EventLog -LogName Application -Newest 100 | Export-Csv -Path "C:\logs\application_logs.csv" -NoTypeInformationConfiguring Event Log Size and Retention
To prevent event logs from consuming disk space, adjust their size and retention policies:
- Open Event Viewer.
- Right-click on a log (e.g., Application) and select Properties.
- Adjust the Maximum log size and set Overwrite events as needed.
Best Practice: Set logs to “Overwrite as needed” to avoid filling up disk space.
Using Task Scheduler to Automate Log Monitoring
Windows Server 2012 allows you to create automated tasks based on event logs:
- Open Task Scheduler.
- Create a new task and select Begin the task: “On an event”.
- Specify the log, source, and event ID to trigger the task.
- Configure the task to send an email, run a script, or display a message.
This is useful for monitoring critical events like failed logins or application errors.
Mastering Windows Server 2012 Event Logs is essential for maintaining server performance, security, and stability. By using tools like Event Viewer and PowerShell, you can gain deep insights into your server’s operations, quickly identify issues, and optimize system performance.
Use this guide to enhance your event log management and improve your Windows Server troubleshooting capabilities.
Время на прочтение3 мин
Количество просмотров43K
Не так давно, для успешного прохождения аудита на соответствие стандартам PCI DSS, потребовалось включить аудит событий Windows серверов и что самое главное — настроить отправку уведомлений о критичных событиях на E-mail. Для Linux серверов вопрос решается установкой и настройкой OSSEC (ну еще могут понадобиться syslog ws loganalyzer и auditd), для Windows Server 2012 R2 да еще и русской версии он не подошел (в последствии нам таки удалось его адекватно настроить, если будет интересно — смогу описать как). Так что решили искать другие способы…
Первым дело следует включить аудит всех необходимых операций (управление учетными записями и контроль целостности файлов) в доменной политике. И если с аудитом операций над объектами Active Directory все просто, то вот с аудитом файловых операций придется повозиться. Тут, как нельзя кстати, компания Netwrix (не сочтите за рекламу, — компания автор коммерческого софта для аудита) подготовила замечательную статью: «Настройка аудита файловых серверов: подробная инструкция и шпаргалка» (.pdf).
Но вернемся к нашим «костылям». После успешной активации аудита всех необходимых операций и обнаружения в журналах Windows интересующих нас событий, встал вопрос об их отправке на сервер мониторинга… Логично было бы воспользоваться встроенными инструментами («Attach Task To This Event» не самый информативный инструмент, зато «родной» для Windows), но тут всплывает первый любопытный и не приятный момент от Microsoft — «Send an email and Display a message are deprecated for from Windows Server 2012 and Windows 8».
Send an e-mail (deprecated)

…
Согласно рекомендациям от Microsoft, как замену встроенному «deprecated» функционалу решили использовать скрипты PowerShell для фильтрации журналов и отправки по E-mail, благо есть подробные инструкции:
«Аудит Active Directory средствами Powershell с оповещением об изменениях».
«Аудит удаления и доступа к файлам и запись событий в лог-файл средствами Powershell»
Но тут возникла сложность другого характера: приведенные выше скрипты отсылали на E-mail только заголовки (темы) событий, тело письма было пустым 
пример скрипта отправки уведомления о событии ‘Заблокирован аккаунт’ — Event ID 4725:
$time = (get-date) - (new-timespan -min 60)
$Subject = “Заблокирован аккаунт"
$Theme = “Только что был заблокирован аккаунт”
$Server = “smtp.server.local”
$From = “AD@domain.local”
$To = “support@domain.local”
$encoding = [System.Text.Encoding]::UTF8
#Выбирается последнее произошедшее событие с таким ID.
$TimeSpan = new-TimeSpan -sec 1
foreach($event in $events)
{
$PrevEvent = $Event.Запись
$PrevEvent = $PrevEvent - 1
$TimeEvent = $Event.TimeCreated
$TimeEventEnd = $TimeEvent+$TimeSpan
$TimeEventStart = $TimeEvent- (new-timespan -sec 1)
$Body=Get-WinEvent -maxevents 1 -FilterHashtable @{LogName=”Security”;ID=4725;StartTime=$TimeEventStart;} | Select TimeCreated,@{n=”Account Name”;e={([xml]$_.ToXml()).Event.EventData.Data | ? {$_.Name -eq “TargetUserName”} |%{$_.’#text’}}},@{n=”Computer”;e={([xml]$_.ToXml()).Event.EventData.Data | ? {$_.Name -eq “TargetDomainName”}| %{$_.’#text’}}}
$body = $body -replace "@{" -replace "}" -replace "=", ": " -replace ";","`n" -replace "TimeCreated","Время события" -replace "^","`n"
$BodyM = $Body
}
Send-MailMessage -From $From -To $To -SmtpServer $server -Body “$BodyM `n$Theme” -Subject $Subject -Encoding $encoding
В общем, если у вас есть реально рабочие скрипты для такого случая — милости прошу в комментарии.
Мы же перешли к другому способу (вдохновила вот эта статья: «Мониторинг и оповещение о событиях в журналах Windows: триггеры событий» и выручила эта утилита: sendEmail):
- Добавляем в Task Scheduler задание по интересующему нас событию (прямо из журнала «Security» -> «Attach Task To This Event…«
- В Actions указываем запуск скрипта, в котором с помощью утилиты wevtutil делаем выборку из журнала и сохраняем результат в файл.
пример скрипта — выборка событий с Event ID 4726
del c:\Audit\query_ID4726.txt wevtutil qe Security /q:"*[System[(EventID=4726)]]" /f:text /rd:true /c:1 > c:\Audit\query_ID4726.txt - Вторым действием, с помощью утилиты sendEmail отправляем сохраненный файл по назначению:
пример аргументов для команды запуска sendEmail:
-f audit_AD@domain.local -s smtp.domain.local:25 -t support@domain.local -m "AD User Account Management - Event ID 426 - Account was Deleted" -a C:\Audit\query_ID4726.txt
В результате должны получать что-то типа этого:

P.S. Спасибо всем авторам источников, указанных ранее!
Если эта публикация вас вдохновила и вы хотите поддержать автора — не стесняйтесь нажать на кнопку
Video Tutorial:
The Challenge of Checking the Event Log in Windows Server 2012
As an administrator handling a Windows Server 2012, it is essential to regularly monitor the Event Log. However, doing so can be quite challenging due to the sheer volume of events recorded and the complexity of the logs. Finding specific events, analyzing them, and extracting meaningful information from them can be time-consuming and overwhelming.
To overcome this challenge, we will discuss different methods to efficiently check the Event Log in Windows Server 2012. These methods will help you streamline your workflow, save time, and gain a better understanding of the system’s behavior.
Things You Should Prepare for
Before we dive into the methods, there are a few things you should prepare to make the Event Log checking process smoother and more effective.
1. Administrative Privileges: To access the Event Log, you need administrative privileges on the Windows Server 2012.
2. Familiarity with Event Viewer: Event Viewer is the built-in tool in Windows Server 2012 for managing and viewing Event Log data. Familiarize yourself with its interface and functionality to leverage its full potential.
3. Clear Understanding of Event Types: Event Log consists of different event types, such as Information, Warning, and Error. Understanding the significance and implications of each event type will help you pinpoint issues and take appropriate actions.
With these preparations in place, let’s explore the multiple methods to check the Event Log in Windows Server 2012.
Method 1: Using Event Viewer
Method 2: Using PowerShell
PowerShell is a powerful command-line tool in Windows Server 2012 that allows administrators to automate tasks and perform advanced system management operations. Here’s how you can check the Event Log using PowerShell:
Step 1: Open PowerShell by typing «PowerShell» in the Start menu search box and selecting «Windows PowerShell» from the results.
Step 2: In the PowerShell console, type the following command to view all available event logs:
Get-EventLog -List
Step 3: Identify the event log you want to check, and note its «LogName» attribute.
Step 4: Use the following command to view the events in the specified log:
Get-EventLog -LogName «LogName» | Select-Object -Property *
Step 5: The above command will display all events in the chosen log, along with their properties.
Pros:
– PowerShell provides automation capabilities for event log management, making it efficient for repetitive tasks.
– PowerShell commands can be used to fetch specific event types or filter events based on various attributes.
– PowerShell allows you to export event data in different formats, facilitating further analysis or reporting.
Cons:
– PowerShell commands may be challenging for users unfamiliar with the command-line interface.
– PowerShell’s advanced capabilities require a strong understanding of its syntax and functionalities.
– PowerShell doesn’t offer a graphical interface, which might hinder visual analysis of events.
Method 3: Using Third-Party Tools
While the built-in tools like Event Viewer and PowerShell provide sufficient functionalities to manage the Event Log, using third-party tools can enhance your experience and provide additional features. Consider the following steps to check the Event Log using a third-party tool like «EventLog Analyzer«:
Step 1: Download and install a third-party tool like «EventLog Analyzer» on your Windows Server 2012.
Step 2: Launch the tool and connect it to your server.
Step 3: Once connected, navigate to the Event Log section or a similar feature in the tool.
Step 4: Select the desired event log you want to check, and apply any necessary filters or search criteria.
Step 5: The tool will display the filtered events, allowing you to analyze them and take appropriate actions.
Pros:
– Third-party tools offer additional functionalities and features for event log management and analysis.
– Advanced reporting and visualization capabilities make it easier to interpret event data.
– Third-party tools often provide a more user-friendly interface than the built-in tools.
Cons:
– Third-party tools may come with a price tag, depending on the tool and its functionalities.
– Installing and configuring a third-party tool adds an additional component to your server’s ecosystem.
– Not all third-party tools may be compatible with Windows Server 2012 or offer the desired features.
Method 4: Via Command Line
Windows Server 2012 provides command-line options to check the Event Log. Here’s how you can do it:
Step 1: Open Command Prompt by typing «cmd» in the Start menu search box and selecting «Command Prompt» from the results.
Step 2: In the Command Prompt window, type the following command to view all available event logs:
wevtutil el
Step 3: Identify the event log you want to check, and note its name.
Step 4: Use the following command to view events in the specified log:
wevtutil qe «LogName«
Step 5: The above command will display events from the chosen log.
Pros:
– Command-line options provide a lightweight and efficient way to check the Event Log.
– Command-line commands can be easily scripted and automated for recurring tasks.
– Command-line tools are accessible even on remote servers, making it possible to check Event Logs from a distance.
Cons:
– Command-line interface might not be as user-friendly as graphical interfaces.
– Advanced filtering and searching options may not be readily available in the command-line tools.
– Manual interpretation of events is still required.
Why Can’t I Check the Event Log in Windows Server 2012?
There can be several reasons why you might encounter difficulties when trying to check the Event Log in Windows Server 2012. Let’s explore some common issues and their solutions:
1. Lack of Administrative Privileges: To access the Event Log, you need administrative privileges on the Windows Server 2012. Make sure you are logged in with an account that has the required permissions.
2. Corrupt Event Log Files: If the Event Log files are corrupt or damaged, you may encounter errors or be unable to view the logs. To fix this, you can run the System File Checker (SFC) scan by following these steps:
– Open Command Prompt as an administrator.
– Type «sfc /scannow» and press Enter.
– Wait for the scan to complete, and then restart the server.
3. Insufficient Disk Space: If the server’s disk is low on free space, it can affect Event Log functionality and performance. Ensure that there is enough free disk space by removing unnecessary files or expanding the storage capacity.
4. Limited Event Log Retention: By default, Windows Server 2012 retains event log data for a specific period. If the log files reach their maximum size or the retention period is over, older events may get overwritten. Adjust the log settings to retain events for a longer duration or increase the maximum log size.
Additional Tips
To optimize your experience with checking the Event Log in Windows Server 2012, consider the following tips:
1. Regularly clear the Event Log to prevent log files from becoming too large and affecting performance.
2. Enable Event Log auto-backup to ensure you have a copy of the logs in case of system failures or crashes.
3. Customize event filters and views in Event Viewer to focus on specific event types or sources.
4. Familiarize yourself with common event IDs and their meanings to quickly identify and resolve issues.
5. Use event log aggregation and analysis tools to centralize log data from multiple servers and gain a broader perspective on system behavior.
5 FAQs about Checking the Event Log in Windows Server 2012
Q1: How can I filter events based on specific event types?
A: In Event Viewer, right-click on the desired event log, select «Filter Current Log,» and specify the necessary filter criteria, such as event levels or event sources.
Q2: Can I export event log data to a file for further analysis?
A: Yes, both Event Viewer and PowerShell allow you to export event log data in various formats, such as CSV or XML.
Q3: Can I check the Event Log remotely on a Windows Server 2012?
A: Yes, you can use PowerShell or command-line tools like «wevtutil» to check the Event Log on a remote Windows Server 2012.
Q4: How can I configure event log retention settings in Windows Server 2012?
A: Right-click on the desired event log in Event Viewer, select «Properties,» and navigate to the «Retention» tab. From there, you can adjust the maximum log size and retention method.
Q5: Are there any real-time monitoring options for the Event Log in Windows Server 2012?
A: Yes, various third-party tools provide real-time monitoring and alerting capabilities for the Event Log in Windows Server 2012. Consider exploring tools like «EventLog Analyzer» or «SolarWinds Event Log Manager.«
In Conclusion
Checking the Event Log in Windows Server 2012 is crucial for monitoring, troubleshooting, and ensuring the stability of the system. By following the methods discussed in this blog post, you can efficiently access and analyze the Event Log, saving time and improving your troubleshooting capabilities. Remember to prepare the necessary tools, familiarize yourself with Event Viewer, and consider using third-party tools to enhance your experience. With a clear understanding of the Event Log and effective management techniques, you can maintain the health and performance of your Windows Server 2012.


