Enable or Disable Domain Users Sign in to Windows 10 Using Biometrics: Although Windows 10 is pretty secure as it gives you the option to sign into Windows using a PIN, Password, or Picture Password but you can always add an extra layer of security by enabling the built-in fingerprint reader. But your PC must have come with the fingerprint reader in order for you to take the benefit of this extra layer of security. The benefit of using Biometrics is that your fingerprints are unique so no chance of brute force attack, it’s easier than remembering password etc.

You can use any Biometrics such as your face, iris, or fingerprint to sign in to your device, apps, online services etc provided your device comes with these features built-in by the manufacturer of your device. Anyway, without wasting any time let’s see How to Enable or Disable Domain Users to Sign in to Windows 10 using Biometrics.
Table of Contents
Make sure to create a restore point just in case something goes wrong.
Method 1: Enable or Disable Domain Users Sign in to Windows 10 Using Biometrics in Local Group Policy
Note: This method will not work for Windows 10 Home Edition Users, this method is only for Windows 10 Pro, Education, and Enterprise Edition Users.
1.Press Windows Key + R then type gpedit.msc and hit Enter to open Local Group Policy.
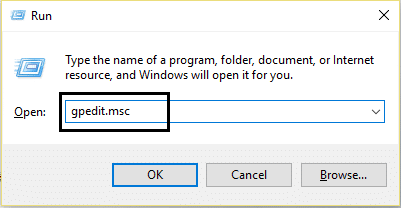
2.Navigate to the following path from the left-hand side pane:
Computer Configuration > Administrative Templates > Windows Components > Biometrics
3.Make sure to select Biometrics then in right window pane double-click on “Allow domain users to log on using biometrics” policy.

4.Now to change the above policy settings according to your choice:
Enable Domain Users Sign in to Windows 10 Using Biometrics: Not Configured or Enabled
Disable Domain Users Sign in to Windows 10 Using Biometrics: Disabled

Note: Not Configured is the default setting.
5.Click Apply followed by OK.
6.Once finished, close everything then reboot your PC to save changes.
Method 2: Enable or Disable Domain Users Sign in to Windows 10 Using Biometrics in Registry Editor
1.Press Windows Key + R then type regedit and hit Enter to open Registry Editor.
2.Navigate to the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Biometrics\Credential Provider
3.Right-click on Credential Provider then select New > DWORD (32-bit) Value.

4.Name this newly created DWORD as Domain Accounts and hit Enter.

5.Double-click on Domain Accounts DWORD and change its value according to:
0 = Disable Domain Users Sign in to Windows 10 Using Biometrics
1 = Enable Domain Users Sign in to Windows 10 Using Biometrics
6.Once finished, click OK to close the above dialog box then restart your PC.
Recommended:
- Enable or Disable Write Protection for Disk in Windows 10
- How to Change Monitor Refresh Rate in Windows 10
- Enable or Disable Disk Write Caching in Windows 10
- Prevent Hard Disk from going to Sleep in Windows 10
That’s it you have successfully learned How to Enable or Disable Domain Users Sign in to Windows 10 Using Biometrics but if you still have any queries regarding this tutorial then feel free to ask them in the comment’s section.
So your company bought brand new Surface Pro devices. Are users complaining that they can’t setup “Windows Hello” features?
This is a common issue with these new devices with biometric authentication features (or when you want a PIN login), for which the configuration panel is presented greyed out, accompanied by a status message that “Some settings are managed by your Organisation“.
Note that you need the latest Administrative Templates (.admx) for Windows 10 and Windows Server 2016 revision both on your server and client for these group policies to be available (get them from Microsot here). Do check if there’s a new revision at the time of reading, though.
There are plenty of posts on the web with tricks for this, but none actually solved the issue entirely. Here are the Group Policy Settings I have implemented to successfully on Windows Server 2012 Essentials to allow access to these features (ignore “Allow deployment operations in special profiles“):

The following registry key and GPO information settings below may be helpful/required as well; I haven’t been able to verify it is actually required or not, as it was one of the first things I tried (applicable from Windows 10 rev 1607):
Advertisement
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System] "AllowDomainPINLogon"=dword:00000001
1. “Turn on Convenience PIN sign-in” policy (as above) must be enabled
2. All 3 Policies under Computer Configuration\Administrative Templates\Windows Components\Windows Hello for Business\ must be in the state “Not configured”. This was the piece that was missing, and not documented properly on Technet.
Advertisement
- Related Content by Tag
- fix
- how to
- Microsoft
- repair
- Windows
- Windows 10
- Windows Server
- Windows Server 2012
Столкнулся с проблемой при настройке входа в систему Windows 10 под доменной учетной записью по отпечатку пальца.
На ноутбуке Lenovo Thinkpad X220 была установлена операционная система Windows 10 Enterprise.
Драйвер Fingerprint Reader установился автоматически.
На всякий случай, установил еще ThinkVantage Fingerprint Software.
Записал при помощи этой программы несколько отпечатков. Отпечатки считались без проблем, но после перезагрузки вход в систему все также происходил только по паролю.
Открыл «Параметры/Система/Параметры входа», а там раздел «Отпечаток пальца» не активен, т.е. кнопка «Изменить» бледно серая и недоступна.
Исправить удалось, как ни странно, добавлением в реестр параметра «AllowDomainPINLogon»:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System]
"AllowDomainPINLogon"=dword:00000001
После добавления этого параметра стали доступны для настройки разделы «Отпечаток пальца» и «ПИН-код». Установка ThinkVantage Fingerprint Software при этом не требуется, хотя работа с отпечатками в этой программе мне понравилась больше, чем штатными средствами Windows 10.
Запись опубликована в рубрике Компьютеры и Интернет. Добавьте в закладки постоянную ссылку.
Last Updated on January 3, 2025 by Deepanshu Sharma

Biometrics technology, which uses biological features for user authentication, is gaining popularity and becoming an essential part of security technology. Methods such as facial recognition and fingerprint recognition are widely used in various industries including healthcare, banking, and hospitality to secure digital transactions and provide a seamless user experience. The global biometrics market is projected to reach $136.18 billion by 2031, with Asia and North America experiencing the highest adoption rates. The increasing use of biometrics can be attributed to factors such as the popularity of facial recognition, the convenience of voice biometrics, advancements in artificial intelligence, the need for multi-factor authentication due to terrorism and cybercrime, and the need for contactless methods of authentication during the COVID-19 pandemic. As technology continues to advance, barriers to adoption will decrease, leading to further growth and usage of biometrics.
How to Implement Biometric Authentication in Active Directory
Below are some of the easiest ways to get started with biometric authentication in Active Directory and Azure AD.
Use Windows Hello
Using Windows Hello is the most widely recommended method for implementing Biometric Authentication in Active Directory. It allows for fingerprint authentication across Windows devices and eliminates the need for users to remember pins or passwords. By requiring users to log in with facial recognition or a fingerprint scanner, the risk of unauthorized access is reduced. Windows Hello enrolls user credentials in Microsoft Passport, which allows for authentication into Microsoft accounts, Active Directory, and other services that support the Fast ID Online (FIDO) standard. This system can use mobile device cameras and fingerprint readers, as well as laptops with fingerprint readers.
Use Public Key Infrastructure
Public Key Infrastructure (PKI) serves as the foundation for all strong authentication factors, including biometric authentication. Azure AD users can now access their accounts without passwords by using FIDO2 security keys, which can be generated by the Microsoft Authenticator app, or Windows Hello. These keys help verify the user and the device to the services within your Active Directory environment. Additionally, the combined registration portal in Microsoft Entra has been updated to enable users to create and manage FIDO2 security keys. FIDO2 security keys can also be used to authenticate across Azure AD-joined Windows 10 devices on the latest versions of Edge and Firefox browsers.
Prepare Devices Accordingly
During the setup process for a new Windows 10 device, the user is asked whether the device belongs to the organization or if it is a personal device. If it belongs to the organization, the user is prompted to select a preferred method of connecting to enterprise resources. They can choose between joining using Azure Active Directory or setting up a local account and manually joining a domain later. Once the user makes a successful selection, they are then asked to verify their identity. This can be done by receiving a phone call or a text message and entering a code. Sometimes, an authentication app is also used for this purpose. In certain cases, organizations may enable a Group Policy setting that allows for biometric authentication, such as fingerprint, iris, or facial recognition through Windows Hello. However, biometric authentication can only be used if the device is equipped with the necessary hardware.
Enable Microsoft Passport
Microsoft makes it easy to implement Microsoft Passport in the workplace using Group Policy. The integration of Microsoft Passport depends on the type of device being used, whether it’s domain-joined or a user-owned device. The ‘Use Biometrics’ setting in the Group Policy Object Editor allows the use of biometric devices, such as retina scanners and fingerprint readers, instead of a PIN. Biometric device use is enabled by default, but it can be disabled to only accept a PIN. If an organization chooses to allow biometric authentication, there are additional Group Policy settings specifically related to biometrics located in:
Computer Configuration > Policies > Administrative Templates > Windows Components > Biometrics.
Use The Expiration Setting
The ‘Expiration’ setting in Windows Server determines whether a user’s PIN will expire or not. If disabled or not configured, the PIN will never expire. Enabling this setting allows the administrator to specify the number of days after which the PIN will expire, with a minimum value of zero and a maximum of 730 days. The ‘History’ setting determines how many previous PINs are stored and prohibited for reuse. By default, Windows does not store PIN histories. Enabling this setting allows the administrator to specify the number of PINs to be stored, including the current PIN as one of the history items. The ‘Require Special Characters’ setting determines whether special characters can be used in a user’s PIN. By default, Windows does not allow special characters. Enabling this setting requires users to include at least one special character in their PIN.
How Lepide Helps
The Lepide Data Security Platform can provide an extra level of security to Active Directory by monitoring all authentication-related activities, and also covers a wide range of cloud platforms, including Azure AD. Lepide provides a centralized dashboard where administrators can easily view and manage all biometric events, configurations and policies. Lepide also has the ability to automatically rotate passwords on managed endpoints, bolstering the security of your authentication process. Lepide records all relevant events and provides real-time alerts for any suspicious or unauthorized access attempts. Additionally, Lepide simplifies privileged account management by enabling the definition of roles and assigning permissions to different users within the organization. This ensures that only authorized personnel can access and modify biometric configurations and PINs, further enhancing security and control.
If you’d like to see how the Lepide Data Security Platform can provide added security to your AD authentication process, schedule a demo with one of our engineers.
- Active Directory
Апрельское обновление Windows 10, привело к тому, что у отдельных пользователей, устройства с динамической блокировкой перестали работать. Пользователи Windows 10, которые подключены к домену, сообщают, что вход с помощью отпечатка пальца или ПИН кода перестали работать. В приложении «Параметры», нет возможности включить опцию идентификации по отпечатку пальца и PIN-кода, параметры не активны, и выделены серым цветом. Чтобы исправить это, есть довольно простое решение, но оно связано с редактированием реестра Windows.
Windows 10, не работает Вход с помощью отпечатка пальца или ПИН кода.
Примечание: Чтобы редактировать реестр Windows, вы должны иметь права администратора.
- Откройте реестр, введя regedit в поле поиска или с помощью диалогового окна «Выполнить» ( см. как).
- Перейдите по следующему пути.
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System
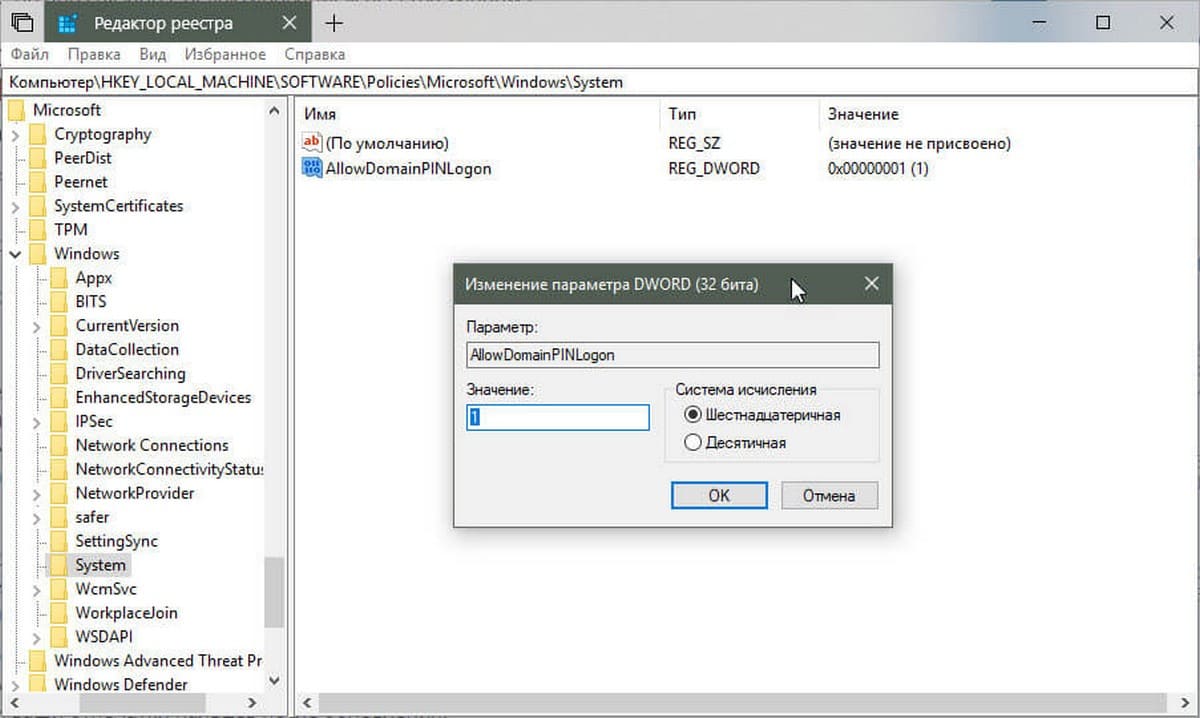
- Здесь найдите параметр DWORD с именем AllowDomainPINLogon. Если параметр отсутствует, кликните правой кнопкой мыши на раздел «System» и выберите в контекстном меню «Создать» → «Новый параметр DWORD (32-бита)». Назовите его AllowDomainPINLogon и установите значение равным 00000001.
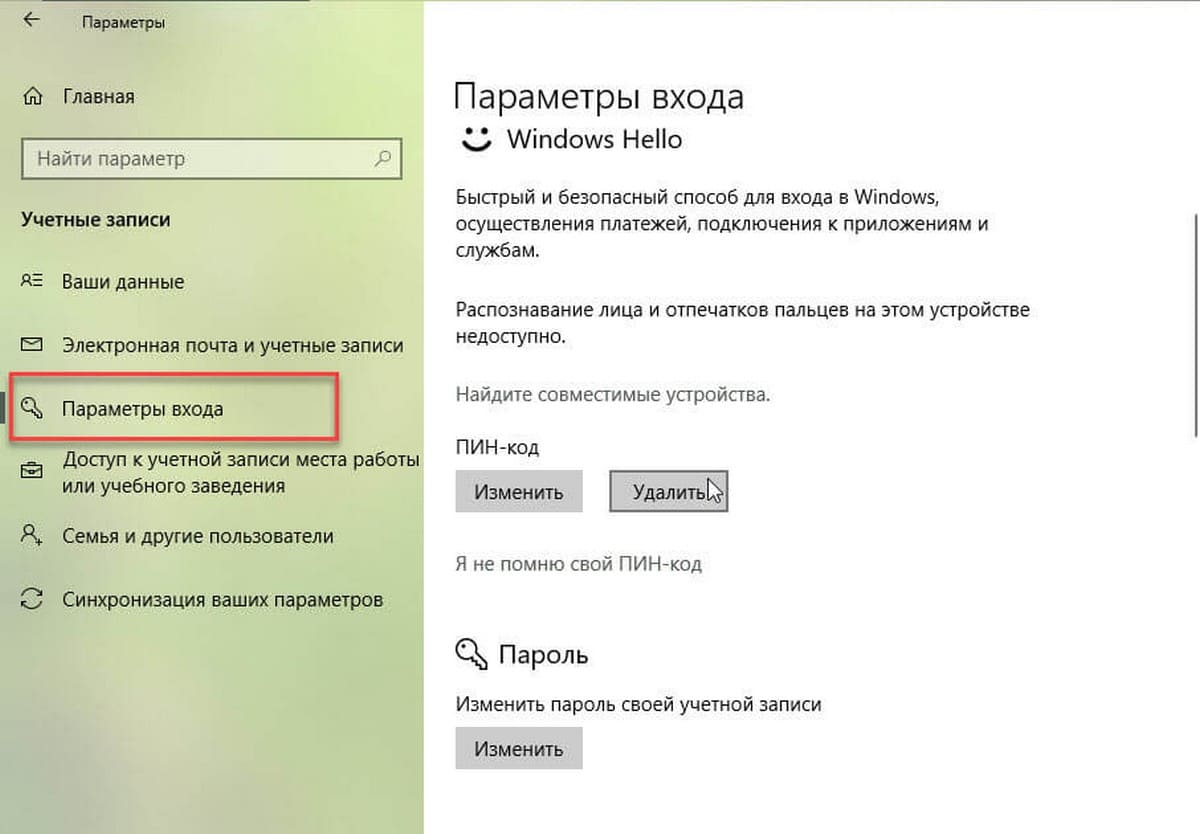
- Перезагрузите систему и откройте приложение «Параметры». Перейдите в группу настроек учетных записей. На вкладку «Параметры входа» и задействуйте опцию Входа с помощью отпечатка пальца или ПИН кода.
Это похоже на ошибку, но это было сделано намеренно. В идеале, добавление параметра DWORD в реестр Windows должно решить проблему. Windows 10 в большинстве случаев, будет помнить ваш PIN-код и ваши отпечатки пальцев после обновления.
Если после добавления значения AllowDomainPINLogon, Windows 10 не распознает ваш ПИН или отпечатки пальцев, удалите их все и добавьте снова. Это немного похоже на проблему с динамической блокировкой, которая может быть исправлена — путем удаления устройств, используемых для блокировки / разблокировки, а затем добавления их заново. Это решение работает для всех пользователей, подключенных к домену. Если вы не подключены к домену, но испытываете эту же проблему, вы можете попробовать это исправление, но нет никаких гарантий, что он будет работать.
Если вы все еще не можете использовать PIN-код или отпечаток пальца для разблокировки системы, обратитесь к администратору сети. Если ваше оборудование, то есть сканер отпечатков пальцев, устарел, возможно, новое обновление несовместимо с ним. Нет простого способа определить совместимость устройства. Попробуйте вернуться к более старому драйверу сканера отпечатков пальцев, и он может снова работать. Если это не так, вам, возможно, потребуется обновить систему.
