-
Home
-
Help -
Common tasks with certificates -
How to create an PFX file
A PFX file indicates a certificate in PKCS#12 format; it contains the certificate, the intermediate authority certificate necessary for the trustworthiness of the certificate, and the private key to the certificate. Think of it as an archive that stores everything you need to deploy a certificate.
When do you need to create a PFX? Most common scenarios
- You will install the certificate on Windows Server (IIS), but the CSR request was not created in IIS.
- You need a certificate for Windows Server, but you do not have IIS to generate the CSR.
- You created the CSR in SSLmarket and saved your private key. You now need to deploy the certificate to Windows Server.
Here is a guide for these (and other) situations.
Creating PFX using OpenSSL
OpenSSL is a library (program) available on any Unix operating system. If you have a Linux server or work on Linux, then OpenSSL is definitely among the available programs (in repository).
In OpenSSL, separately stored keys must be used in a single PFX (PKCS#12) file. So join existing keys to PFX:
openssl pkcs12 -export -in linux_cert+ca.pem -inkey privateky.key -out output.pfx
When you enter the password protecting the certificate, the output.pfx file will be created in the directory (where you are located).
Creating PFX on Windows (server with IIS)
Create a PFX from an existing certificate
From a Windows operating system, an existing certificate can be exported from the certificate store as a PFX file using the MMC. You can also choose to do this on a Windows server if IIS stores them in the certificate store.
The IIS Web Server allows you to export an existing certificate to PFX directly from the server certificate store. The private key and CSR are created during the creation of a CSR request in IIS and the certificate is reimported when issued (both steps can be found in the video guide ).
Exporting is very simple — right-click on the certificate and select Export. After you choose a password to protect the PFX file, it is saved to disk.
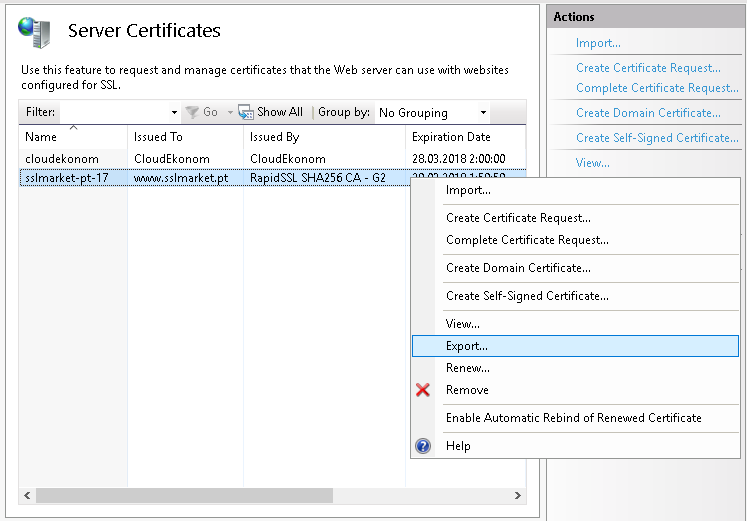
Import a new certificate and create a PFX
Unfortunately, this is not possible. The Windows certificate store does not allow you to import a separate private key from a file, so in MMC you do not merge keys to PFX as in OpenSSL. You can only import PFX into an IIS web server, so what is in the previous case.
If you need to import a new certificate into Windows Server and there is no private key on the server (you did not create a CSR request on the server), you can follow these steps:
- Create PFX elsewhere (OpenSSL or otherwise) and then import the certificate using PFX
- Create a new CSR request on the server and perform a reissue of the certificate.
Reissue means that the certificate will be reissued free of charge and you can import it to an existing private key. You can do this yourself in customer administration.
Create a PFX using a third-party application
You can create a .pfx file from separate keys in a graphics program to bypass the need to use OpenSSL in the terminal.
The best program for this purpose is opensource XCA. In this intuitive program you can manage all your certificates and keys. The main advantage is the automatic matching of the corresponding keys to each other; you do not have to look for which private key belongs to which certificate. Importing keys is easy and you can export to all known formats.
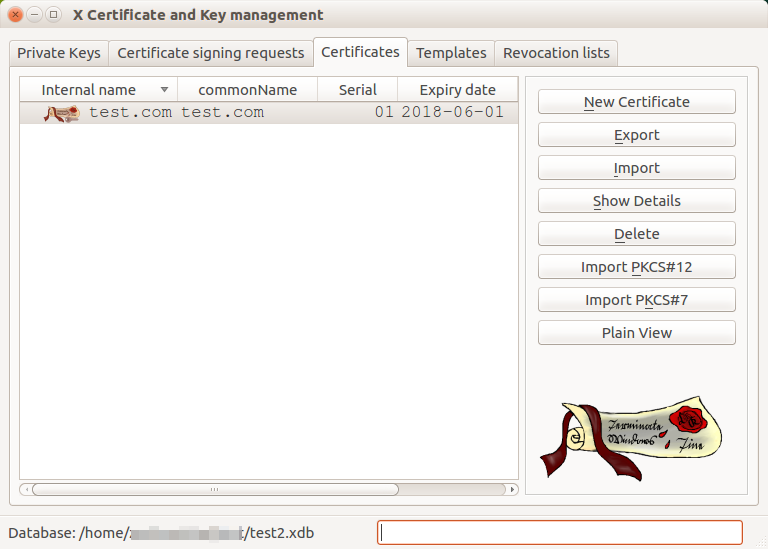
(In)security of the PFX file
The PFX file is always password protected because it contains a private key. When creating a PFX, choose a password responsibly, as it can protect you from misuse of the certificate. An attacker would be pleased if the password to the stolen PFX file was «12345»
— he could start using the certificate all the time immediately.
The danger of storing a Code Signing certificate in the PFX file was the main reason for the transition of all these certificates to token. Both the Code Signing OV and EV certificate must be stored on a token and its misuse in theft is virtually impossible; if the password is entered several times, the token is blocked.
Feel free to contact our Customer Support to help you choose certificate and ask any questions.
Has this article been useful?
Собрать SSL-сертификат в PFX-файл (также известный как PKCS#12) можно с помощью OpenSSL в linux и windows системах:
1. Убедитесь, что у вас есть все необходимые файлы:
— сертификат (.crt, .cer, .pem)
— приватный (закрытый) ключ (.key)
— опционально: цепочка промежуточных сертификатов ((.crt, .cer, .pem))
2. Используйте OpenSSL для создания PFX:
openssl pkcs12 -export -out certificate.pfx -inkey private.key -in certificate.crt -certfile fullchain.crt
где:
-out certificate.pfx — выходной PFX-файл;
-inkey private.key — Ваш приватный ключ;
-in certificate.crt — Ваш сертификат;
-certfile ca-bundle.crt — файл с промежуточными сертификатами (опционально, но рекомендуется для корректной работы цепочки доверия).
3. Введите пароль (если требуется):
OpenSSL запросит пароль для защиты PFX-файла. Этот пароль понадобится при импорте сертификата.
Примечание: старые версии Windows могут не поддерживать современные алгоритмы шифрования PFX (например, AES-256). Попробуйте создать PFX с -legacy:
openssl pkcs12 -legacy -export -out certificate.pfx -inkey private.key -in certificate.crt -certfile fullchain.crt
В windows SSL-сертификат в PFX-файл можно собрать с помощью CertUtil –MergePFX:
1. Установка промежуточного сертификата
Промежуточный сертификат импортируем в «Computer\Intermediate Certificate Authorities»
2. Сборка сертификата pfx
Для сборки понадобится ключ и сам сертификат. Файлы должны находиться в одной директории и имена файлов должны совпадать. Используем встроенную утилиту Windows «CertUtil.exe».
Выполняем команду: CertUtil –MergePFX <имя>.crt <имя>.pfx.
Вводим пароль два раза.
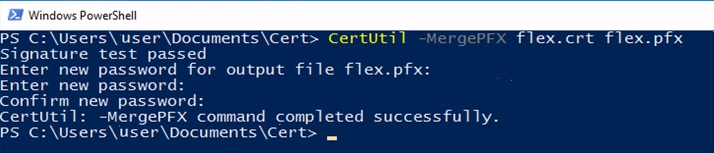
На выходе получим .pfx файл.
Для включения в .pfx файл промежуточных сертификатов и сертификата центра сертификации(CA) необходимо экспортировать сертификат с опциями «Yes, export private key» и «Include all certificates in the certification path if possible» в certlm.msc.
Вы уже работаете с сервисами Cloud4Y?
Перейти на вебсайт
Попробовать бесплатно

Другие заметки
Что такое машинное обучение?
Сегодня хочу поделиться небольшой заметкой про машинное обучение. Машинное обучение это будущее цифрового мира и подраздел искусственного интеллекта, который сосредоточен на использовании данных и алгоритмов для имитации способности человека учиться, постепенно повышая точность своих прогнозов
Linux для всех. Команды. Часть 1
В современной программной инженерии навык работы с командной строкой Linux не является просто “плюсом”, а часто необходимостью. Эффективное использование Linux-команд позволяет специалисту не только быстро и точно выполнять разнообразные задачи
Добро пожаловать!
Рад видеть каждого из вас здесь, на страницах моего блога, который будет целиком и полностью посвящен миру системного администрирования. Сегодня отличная дата, чтобы начать вести данный блог. В эпоху технологий и быстро меняющихся инноваций, считаю важным поделиться своим опытом, знаниями и наблюдениями
Report
You have already reported this .
Note: This article does not apply to SSL.com code signing and document signing certificates. These types of certificates cannot be generated as .pfx files and their private keys cannot be exported. SSL.com code signing and document signing certificates and their private keys can only be generated and stored in the eSigner cloud signing environment, a Yubikey device, or a supported Cloud HSM.
In cryptography, the PKCS#12 or PFX format is a binary format often used to store all elements of the chain of trust, such as the server certificate, any intermediate certificates, and the private key into a single encryptable file. PFX files are usually found with the extensions .pfx and .p12. PFX files are typically used on Windows and macOS machines to import and export certificates and private keys.
Requirements
- The original private key used for the certificate
- A PEM (.pem, .crt, .cer) or PKCS#7/P7B (.p7b, .p7c) File
- OpenSSL (included with Linux/Unix and macOS, and easily installed on Windows with Cygwin)
The commands below demonstrate examples of how to create a .pfx/.p12 file in the command line using OpenSSL:
PEM (.pem, .crt, .cer) to PFX
openssl pkcs12 -export -out certificate.pfx -inkey privateKey.key -in certificate.crt -certfile more.crt
Breaking down the command:
openssl– the command for executing OpenSSLpkcs12– the file utility for PKCS#12 files in OpenSSL-export -out certificate.pfx– export and save the PFX file as certificate.pfx-inkey privateKey.key– use the private key file privateKey.key as the private key to combine with the certificate.-in certificate.crt– use certificate.crt as the certificate the private key will be combined with.-certfile more.crt– This is optional, this is if you have any additional certificates you would like to include in the PFX file.
After entering the command, you will be prompted to enter and verify an export password to protect the PFX file. Remember this password! You will need it when you wish to export the certificates and key.
If you are creating a PFX to install on Azure Web Apps, or another service requiring a PFX file for SSL/TLS installation, it is recommended to include a full chain of trust in your PFX. You can do this by downloading the Apache download link from your SSL.com account, and including both your website certificate and the file named ca-bundle-client.crt in your PFX file. For example:
openssl pkcs12 -export -out certificate.pfx -inkey privateKey.key -in certificate.crt -certfile ca-bundle-client.crt
PKCS#7/P7B (.p7b, .p7c) to PFX
P7B files cannot be used to directly create a PFX file. P7B files must be converted to PEM. Once converted to PEM, follow the above steps to create a PFX file from a PEM file.
openssl pkcs7 -print_certs -in certificate.p7b -out certificate.crt
Breaking down the command:
openssl– the command for executing OpenSSLpkcs7– the file utility for PKCS#7 files in OpenSSL-print_certs -in certificate.p7b– prints out any certificates or CRLs contained in the file.-out certificate.crt– output the file as certificate.crt
Note: You can also use OpenSSL to extract the certificates and private key from a PKCS#12/PFX file.
Video
Thank you for choosing SSL.com! If you have any questions, please contact us by email at Support@SSL.com, call 1-877-SSL-SECURE, or just click the chat link at the bottom right of this page. You can also find answers to many common support questions in our knowledgebase.
For more helpful how-tos and the latest cybersecurity news, subscribe to SSL.com’s newsletter here:
A while back I had a post where I talked about setting up .net core in docker using SSL and a HTTPS port you can read that here
To make a .net core project work on a HTTPS port you need to pass it the cert. One way to do this is to create a PFX cert and load it into the project during the compile. This then means Kestrel will be listening on the HTTPS port for you.
We would configure our .net core app as follows
.UseKestrel(options =>
options.Listen(IPAddress.Any, 8050, listenOptions =>
listenOptions.UseHttps("demowebapp.pfx", "XXXX")))The important part: There are a few ways to do this but this is the way I’m going to cover the way I do it not to say there aren’t other very valid ways of doing it.
Windows subsystem for Linux
In windows 10 they gave us a subsystem of Ubuntu on Windows. If you haven’t tried it check it out here
OpenSSL
I use openSSL inside the subsystem. OpenSSL is a powerful set of tools for creating certs on either linux or windows.
Once I install it
sudo apt-get install opensslCloudflare
I use cloudflare for alot of my DNS and caching, etc. One thing it can do is give me origin certificates.
Under the SSL / TLS option
When you create a certificate you can set how long it is valid. Because this is my origin and not my edge I can set it to a longer life than a few months. I’ve explained part of this in my Lets talk about HTTPS post.
So once you do that you can generate a PEM Key Format, it will look something like this
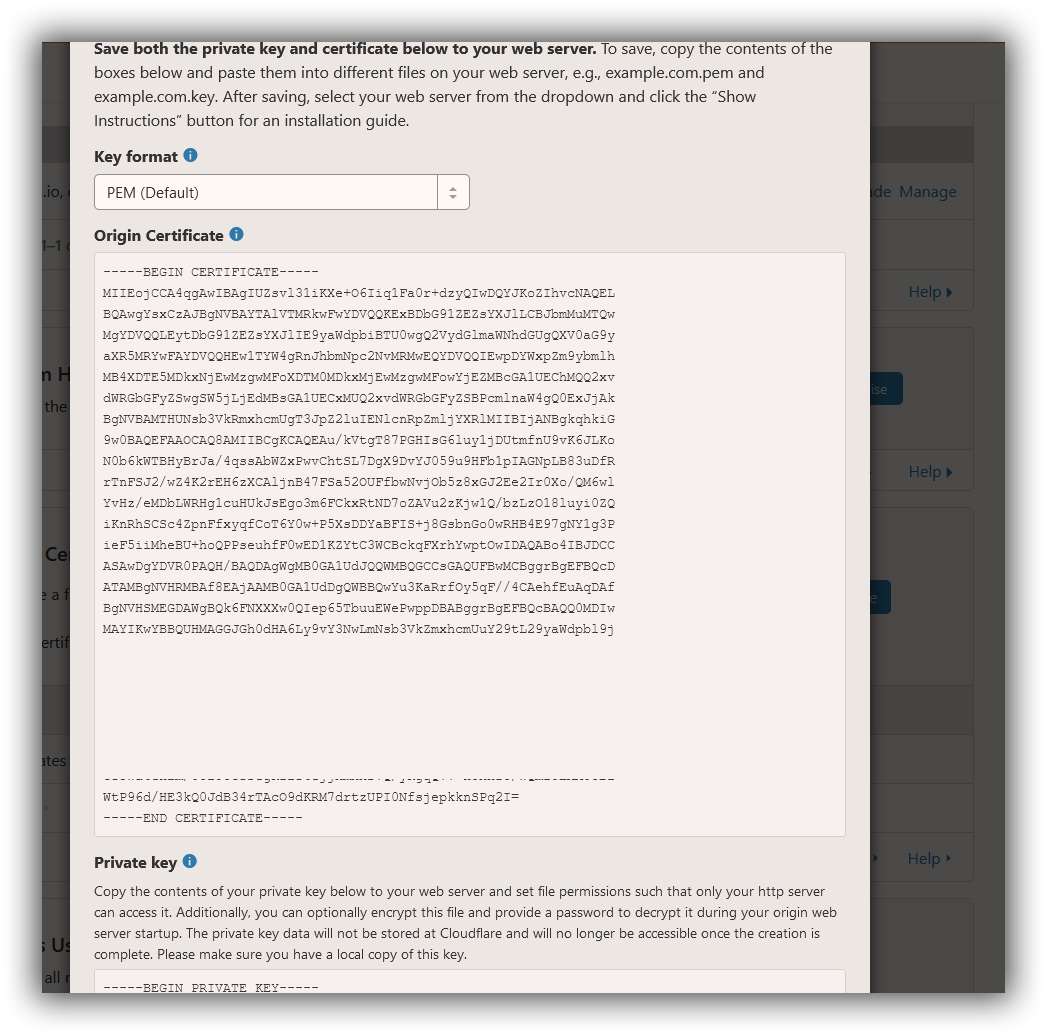
Copy text between the «Begin and End Certificate» including those lines and you can create two files
- mynewcert.pem
- mynewcert.key
In the end these are just text files you need to save onto your computer.
Create PFX Certificate
Now the big bit. In our Linux subsystem we need to mount our drive and find the folder containing our .key and .pem files.
To mount the C: just do the following
cd /mnt/cYou can then move to the folder you saved the .key and .pem file.
Now the bit to generate the .pfx certificate.
openssl pkcs12 -export -inkey mynewcert.key -in mynewcert.pem -name myCert -out mynewcert.pfxThis will generate a .pfx file and save it to the same folder and adds the password when it’s generated.
And that’s it, you have a .pfx file now, you can copy that into the .net core app and set the password.
