
Понадобилось мне как-то раз настроить на IIS 7 прозрачное проксирование запросов из интернета на другой web-сервер, расположенный во внутренней сети. По сути, нужно было настроить IIS 7 как обратный прокси-сервер (reverse proxy). Потом сделал то же самое на IIS 10.
Обратный прокси-сервер (reverse proxy) — тип прокси-сервера, который ретранслирует запросы клиентов из внешней сети на один или несколько серверов, логически расположенных во внутренней сети. При этом для клиента это выглядит так, будто запрашиваемые ресурсы находятся непосредственно на прокси-сервере.
Из коробки эта штука не заработала. Будем настраивать. Нам понадобится модуль для IIS 7 под названием URL Rewrite. У меня он установлен, но этого, как показала практика, недостаточно.
На IIS 10 всё поставилось таким же образом, только проблем было меньше.
Ссылки
ARR — Application Request Routing:
https://www.iis.net/downloads/microsoft/application-request-routing
Настраиваем reverse proxy
Итак, задача. Есть сайт http://setpizza.com, кстати, он продаётся. Сайт делегирован на наш web-сервер IIS 7. Нужно настроить обратное проксирование на другой сервер в локальной сети с IP адресом 192.168.1.11 на 81 порт. Не важно что там крутится, IIS, apache, nginx — мы не знаем. Допустим, мы решили проблемы с доступами и прорубили дырку по 81 порту на этот сервер с нашего IIS.
Открываем IIS там, где будем настраивать проксирование, создаём там пустую директорию, C:\redirect_setpizza.com. Создаём сайт redirect_setpizza.com, который привязан к этой директории. Выбираем сайт мышкой.
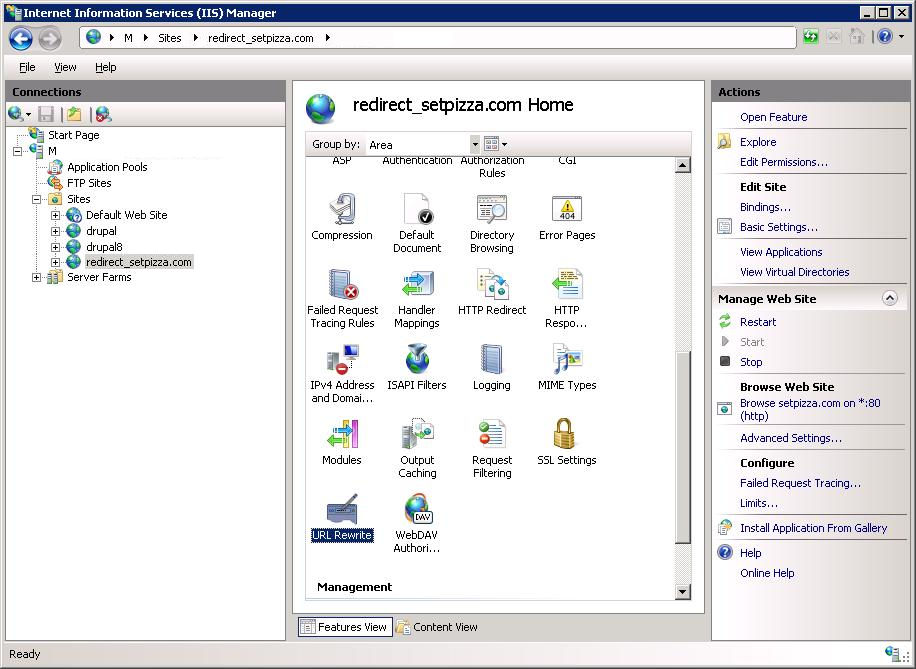
Находим URL Rewrite — тыкаем.
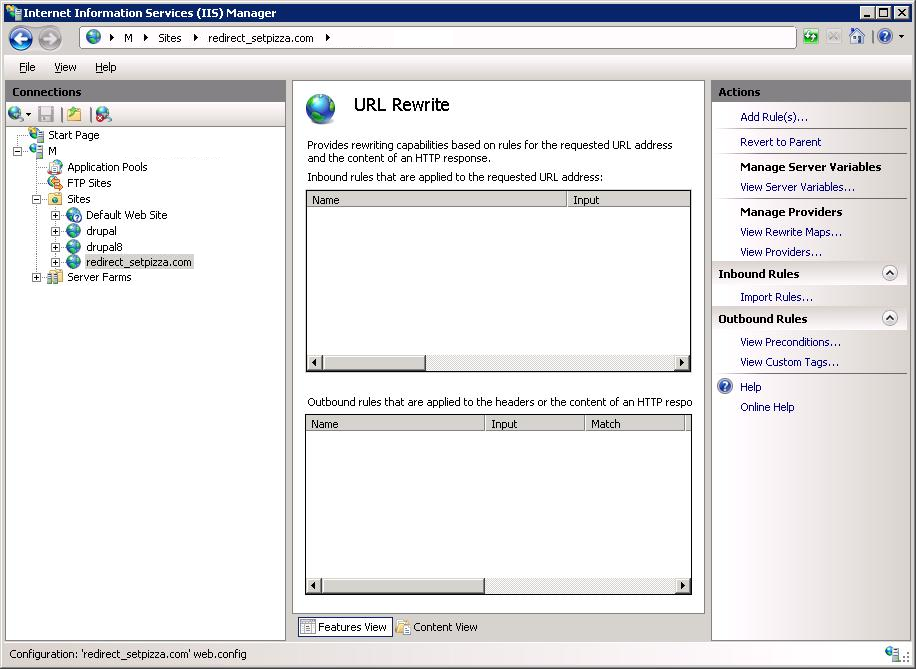
Добавляем правило — Add Rule(s)…
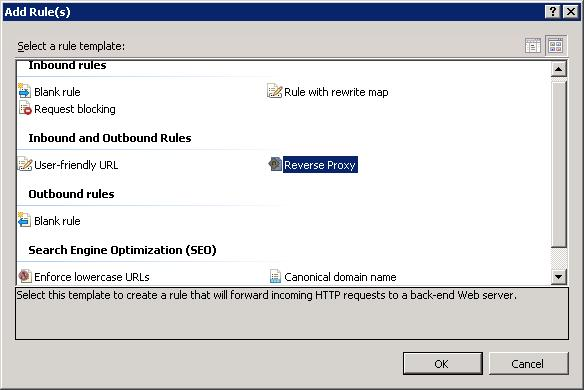
Выбираем правило Reverse Proxy. OK.
Первая проблема. О как, хочешь пирожок? А нету! Для Reverse Proxy требуется фича для IIS под названием Application Request Routing (ARR). Тыкаем OK. Открывается сайт:
https://www.iis.net/downloads/microsoft/application-request-routing
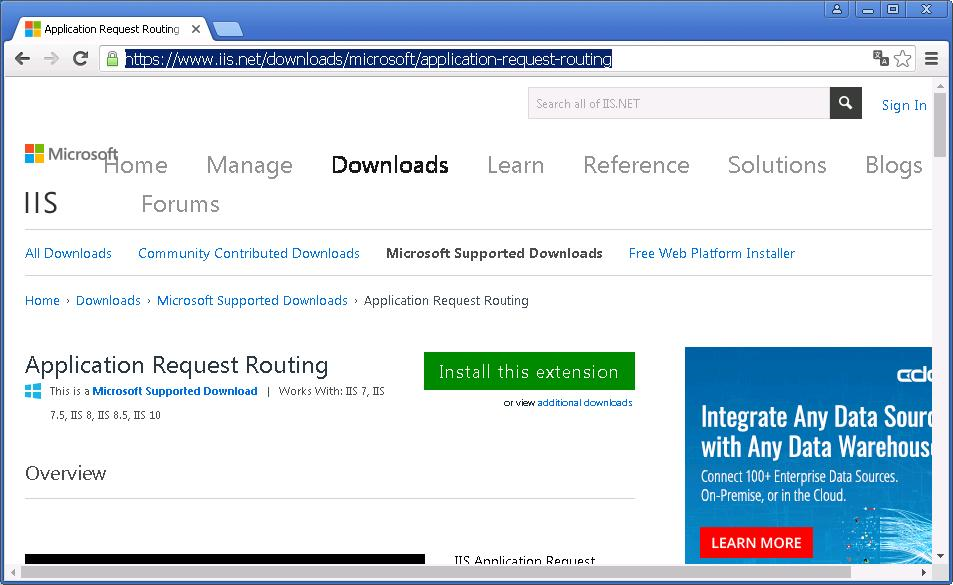
Install this extension. Качаем ARRv3_0.exe.
Запускаем.
Ждём.
Начинается запуск инсталлятора Microsoft Web Platform Installer 5.1.
Ждём.
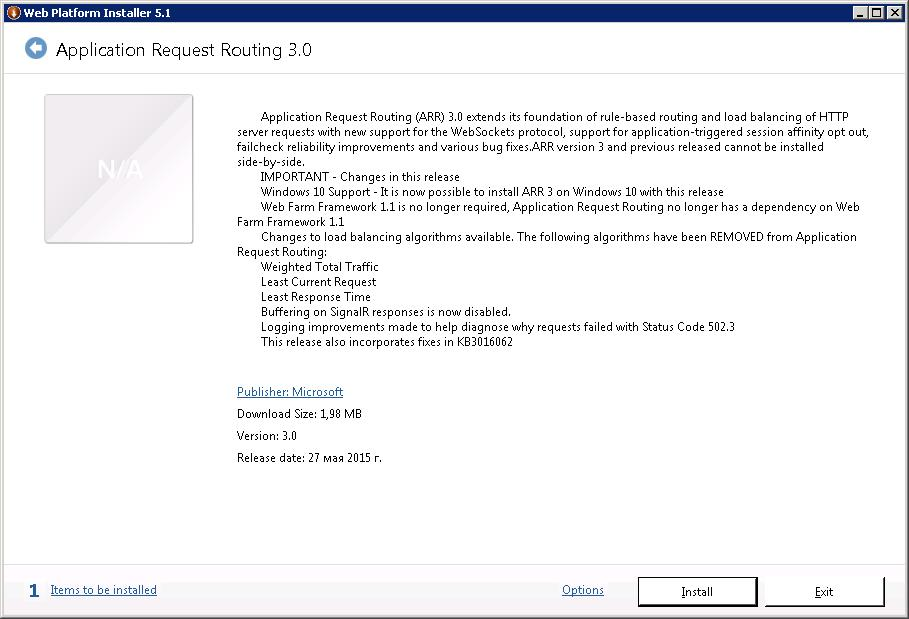
Читаем описание того, что мы ставим. На самом деле ARR позволяет не только делать обратное проксирование на один сервер. С помощью ARR можно настраивать фермы веб-серверов и выступать в качестве балансировщика, но в моей задаче всё проще. Install.
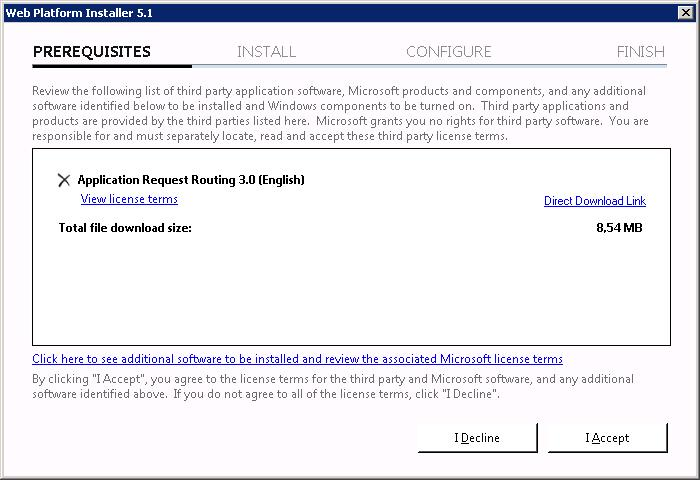
Нам говорят, что надо скачать файлы на 8,54 мегабайт. I Accept.
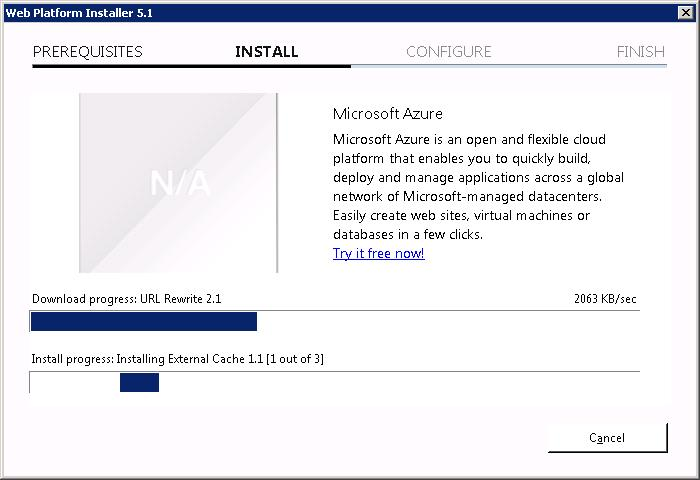
ARR состоит из нескольких модулей, в него входит External Cache 1.1, URL Rewrite 2.1, сам ARR 3.0.
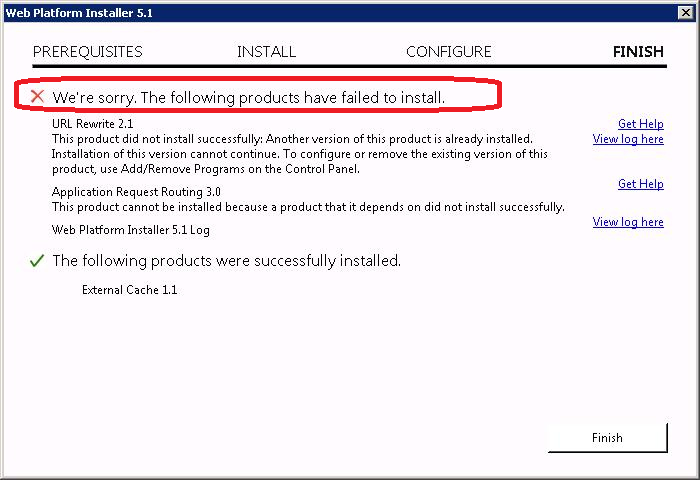
Вторая проблема. URL Rewrite 2.1 не установился — установка прервалась. Говорят. что URL Rewrite уже установлен более старой версии. Требуется сначала его удалить вручную.
Тысяча чертей! Находим установленный старый URL Rewrite Module 2 и удаляем его. Он с 2011 года тут болтается.
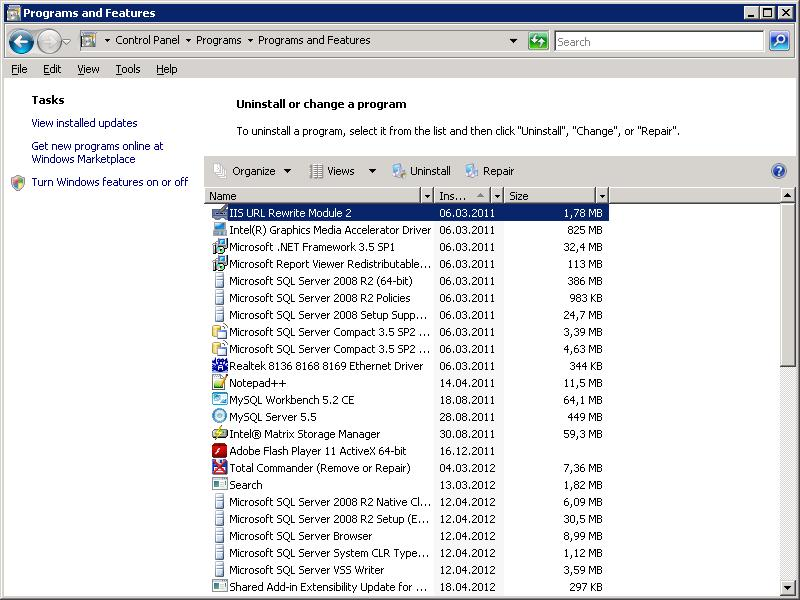
Запускаем инсталлятор ARR заново.
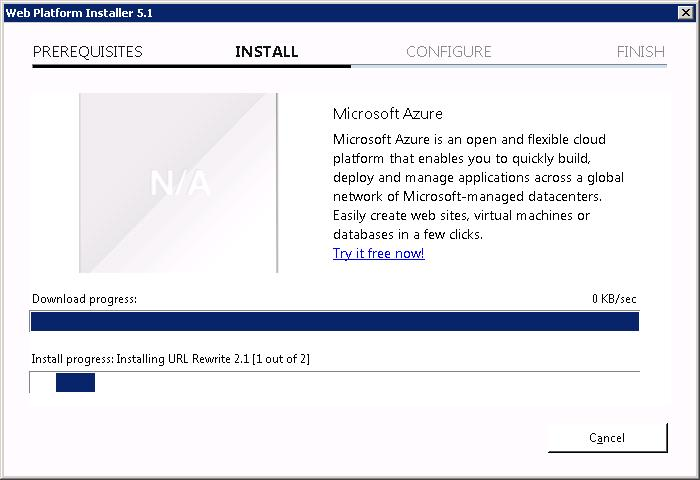
Теперь URL Rewrite 2.1 устанавливается.
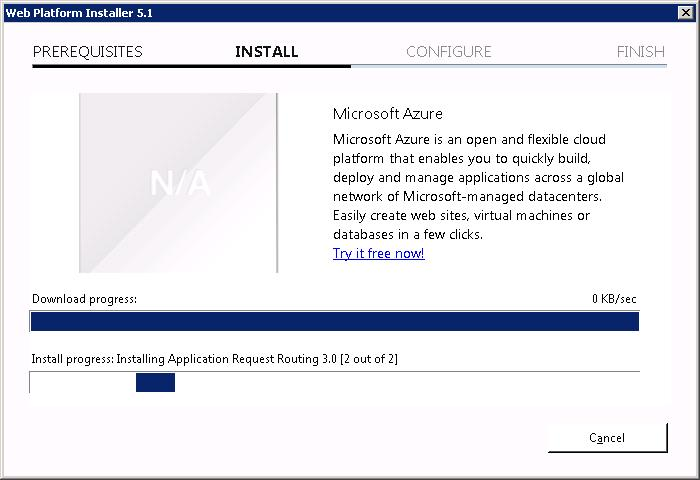
За ним ставится Application Request Routing 3.0.
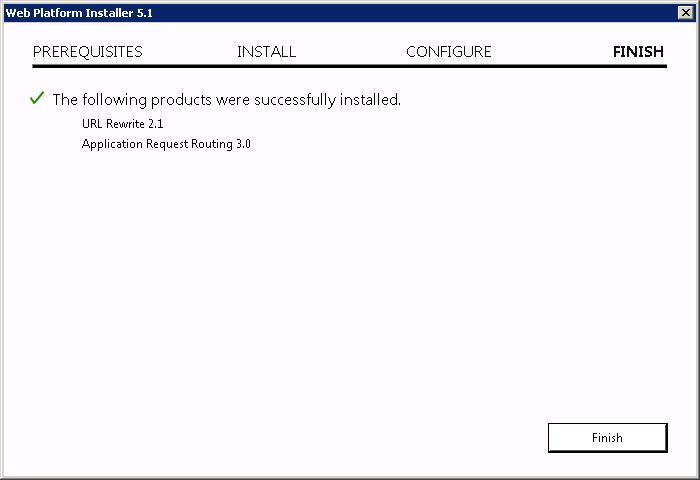
ARR установлен. Возвращаемся к нашему IIS. Добавляем правило — Add Rule(s)… Выбираем правило Reverse Proxy. OK.
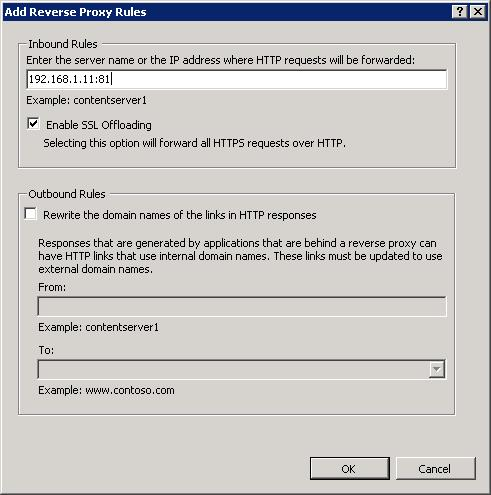
На этот раз правило создаётся. Пишем. «192.168.1.11:81». Ставим галку Enable SSL Offloading — терминируем SSL на этом прокси-сервере. OK.
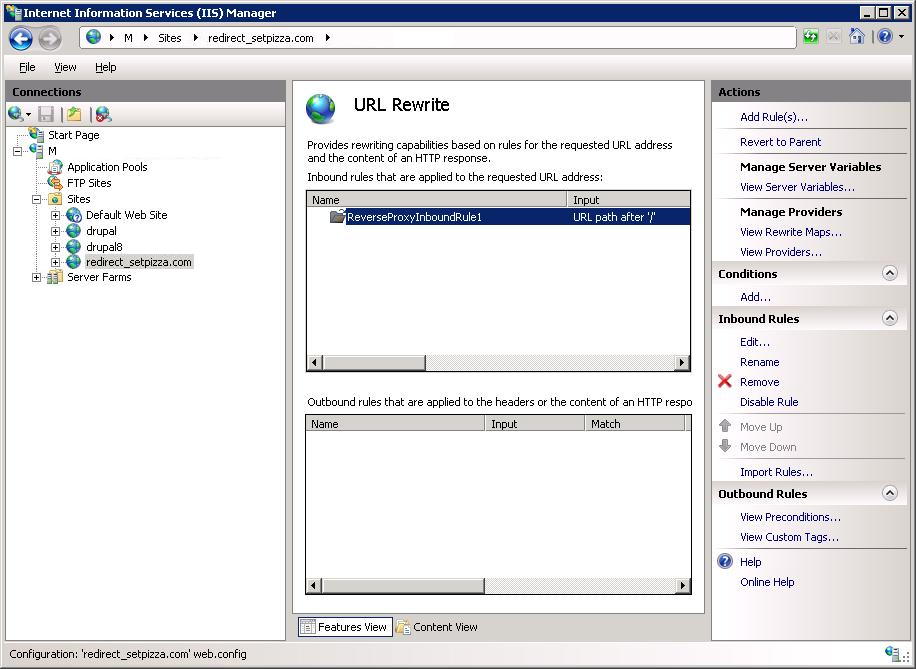
Всё, собственно. В пустой папке сайта создался файлик web.config. В нём:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<rewrite>
<rules>
<rule name="ReverseProxyInboundRule1" stopProcessing="true">
<match url="(.*)" />
<action type="Rewrite" url="http://192.168.1.11:81/{R:1}" />
</rule>
</rules>
</rewrite>
</system.webServer>
</configuration>«http://» и {R:1} дописываются автоматически. Проверяем работу сайта — всё отлично.
Caddy представляет собой обратный прокси-сервер (обратный прокси-сервер). Написанный на языке Go, это полностью бесплатный проект с открытым исходным кодом с лицензией Apache 2.0.
Caddy поддерживает HTTP/2, HTTP и HTTPS, позволяет автоматически получать и обновлять сертификаты Let’s Encrypt. Обладает кроссплатформенностью: можно установить на любую ОС, а также поддерживает разные архитектуры процессоров. Также Caddy можно использовать просто в Docker-контейнере.
- Официальный сайт
- Страница на GitHub
- Документация
Альтернативы Кэдди:
- Nginx (ТОП-1 в мире, большое сообщество, множество инструкций, выдерживает большую нагрузку, огромное количество функций и тонких настроек).
- Traefik (интересный проект, много интересных фишек для удобства и автоматизаций).
Основные особенности Caddy, на мой взгляд:
- Самая простая и понятная настройка, легко читается и пишется конфигурационный файл, минималистичность.
- Автоматическое получение и обновление SSL-сертификатов.
- Использует HTTPS по умолчанию.
- Настройка по API. Принимаем меры по настройке Caddy с помощью REST API запросов в JSON-формате. Хорошо подходит для настроек автоматизации и дает дополнительные возможности в конфигурации.
- Плагины. Из коробки Caddy работает со звуковым набором, адаптером для работы прокси-сервера, но с помощью плагинов можно легко внедрить дополнительные функции. Например, авторизация страниц, интеграция с DNS-провайдерами (Cloudflare) и т.п.
cloud
Ознакомительный запуск
Для экспериментов я взял самый простой сервер на Timeweb Cloud c Ubuntu 22.04.
Установка по документации с официального сайта:
sudo apt install -y debian-keyring debian-archive-keyring apt-transport-httpscurl -1sLf 'https://dl.cloudsmith.io/public/caddy/stable/gpg.key' | sudo gpg --dearmor -o /usr/share/keyrings/caddy-stable-archive-keyring.gpgcurl -1sLf 'https://dl.cloudsmith.io/public/caddy/stable/debian.deb.txt' | sudo tee /etc/apt/sources.list.d/caddy-stable.listsudo apt updatesudo apt install caddyПроверяю активность сервиса:
systemctl status caddyПроверка версии:
caddy version> v2.7.4
Для проверки откройте в браузере страницу по IP-адресу хоста:
Далее пошагово выполним предложенные рекомендации Caddy по настройке.
Шаг 1. Создать доменное имя и направить на адрес сервера
Создаю в DNS доменное имя 2 уровня: caddy.akmalov.com.
Указываю ему «белый» IP-адрес созданного сервера.
Шаг 2. Изменить путь и использовать свои статические файлы для отображения
Для создания своего index.html по указанному пути /var/www/html/.
Добавляю картинку volk.jpg:
<!DOCTYPE html>
<head>
<meta charset="UTF-8">
<title>Шапка</title>
</head>
<body>
<header>
<h1>Самый простой index файл для демо</h1>
</header>
<main>
<h2>План чек-лист по Caddy</h2>
<p>Сам ничего не придумал, поэтому пойдем по документации:</p>
<ul>
<li>DNS сделать</li>
<li>Конфиг поменять</li>
<li>сервер перезапустить</li>
<li>пресс качат</li>
<li>анжумания вечером</li>
</ul>
<img src="volk.jpg" alt="volchara">
</main>
</body>
</html>Шаг 3. В конфигурации измените порт :80 на свое доменное имя
Открываю для редактирования структуру файла:
nano /etc/caddy/Caddyfile# The Caddyfile is an easy way to configure your Caddy web server.
#
# Unless the file starts with a global options block, the first
# uncommented line is always the address of your site.
#
# To use your own domain name (with automatic HTTPS), first make
# sure your domain's A/AAAA DNS records are properly pointed to
# this machine's public IP, then replace ":80" below with your
# domain name.
:80 {
# Set this path to your site's directory.
root * /usr/share/caddy # Enable the static file server.
file_server
# Another common task is to set up a reverse proxy:
# reverse_proxy localhost:8080
# Or serve a PHP site through php-fpm:
# php_fastcgi localhost:9000
}
# Refer to the Caddy docs for more information:
# https://caddyserver.com/docs/caddyfile
Удаляю все лишнее, чтобы конфиг выглядел следующим образом:
caddy.akmalov.com {
root * /var/www/html
file_server
}Шаг 4. Перезапустить Caddy
Перезапускаю с помощью команды:
systemctl reload caddyОткрываю браузер по доменному имени caddy.akmalov.com.
Страница сразу открывается по HTTPS с доверенным сертификатом — и все это в четырех строках схемы, в которых все минимально, красиво и понятно.
Запуск Caddy в docker-compose
Допустим, нам нужно выделить сервис и перенаправить трафик.
Мне очень нравится использовать все в контейнерах, без установки дополнительных пакетов, зависимостей и запускать одной кнопкой. Поэтому удаляю сервис Caddy и устанавливаю Docker:
systemctl stop caddy
apt remove caddy
apt install docker.io docker-composeДля начала повторяю то же самое, что было выше, но уже использовалось в контейнере.
Создаю директорию по пути /srv/caddy и копирую туда статические файлы и конфигурацию файлов.
mkdir -p /srv/caddy/site
cp -r /var/www/html /srv/caddy/site
cp /etc/caddy/Caddyfile /srv/caddy/CaddyfileСоздаю docker-compose.yml с такой конфигурацией:
version: '3.8'
services:
caddy:
image: caddy:2.7.4
restart: always
ports:
- 80:80
- 443:443
volumes:
- ./Caddyfile:/etc/caddy/Caddyfile
- ./site:/var/www/htmlЗдесь я с помощью томов перекидываю файлы в те же знакомые каталоги, чтобы ничего не сохранить в конфигурации.
После этого запускаю и проверяю:
docker-compose up -dТакже хочу показать, как еще можно защитить страницу, используя BasicAuth и пару строк конфигурации.
Для этого отредактируем Caddyfile следующим образом, добавив Basicauth * {логин-пароль}:
caddy.akmalov.com {
basicauth * {
volk $2y$10$v8t9CqkLFEon3UTYKUsRs.8zhMMLFX5.9WyDERzd7ESRT75PICkiW
}
root * /var/www/html
file_server}
Логин и пароль пользователя можно сгенерировать в консоли или воспользоваться онлайн-генераторами .htpasswd (алгоритм по умолчанию: bcrypt).
docker-compose restartТеперь при открытии страницы появляются окна аутентификации.
Теперь в docker-compose подниму какой-нибудь сервис с веб-интерфейсом, например, Grafana.
version: '3.8'
caddy:
image: caddy:2.7.4
restart: always ports:
- 80:80
- 443:443
volumes:
- ./Caddyfile:/etc/caddy/Caddyfile
- ./site:/var/www/html
grafana:
image: grafana/grafana:10.0.5-ubuntu
container_name: grafana
# ports:
# - 3000:3000
environment:
GF_SECURITY_ADMIN_USER: 'admin'
GF_SECURITY_ADMIN_PASSWORD: 'volk'
Порты закомментированы, т.к. Grafana и Caddy присоединяются к одной группе и могут общаться по имени сервисов, внешний проброс портов не нужен. Если необходимо обращаться не только по доменному имени, но и по локальному IP-хостеру и порту, то нужно раскомментировать эти строки.
Для сервиса Grafana создаю в DNS еще одно доменное имя второго уровня, например test.akmalov.com, и добавляю в конфигурацию Caddyfile:
caddy.akmalov.com {
root * /var/www/html
file_server
}
test.akmalov.com {
reverse_proxy grafana:3000
}Чтобы не запутаться, еще раз покажу структуру того, что получилось:
В директории сайта два файла:
- index.html (главная страница сайта).
- volk.jpg (картинка).
В docker-compose.yml поднимается два сервиса:
- Кэдди для проксирования и получения сертификатов.
- Grafana как отдельное веб-приложение.
Caddyfile (файл с конфигурацией) — через тома продаем внутренний контейнер по пути /etc/caddy/Caddyfile.
В формулировке таких правил:
- caddy.akmalov.com — выдаем статические файлы из директории сайта.
- test.akmalov.com — перенаправляем в Grafana.
Для проверки того, что новое доменное имя ведет на данном хосте, проверяем DNS-записи:
nslookup test.akmalov.comЕсли всё получится, можно проверить в браузере.
Проверка в браузере по доменному имени test.akmalov.com — открывается страница входа в панель Grafana).
Заключение
В этой статье я привел простейшие схемы для ознакомления, но в документации также можно почитать, например, про балансировку нагрузки для распределения трафика по разным хостам, а также добавление проверки работоспособности для проверки работоспособности хостов, как обрезать, добавить или изменить заголовки (заголовок) . ) в запросах и т.д.
Я не погружаюсь в конфигурацию слишком глубоко, так как для меня Кэдди — это в первую очередь про простоту. Конфигурации, показанные в статье, — очень удобные и понятные, и, казалось бы, куда проще. Но оказывается, есть куда.
Например , если на этой же облачной машине сервису мне потребовалось бы поднять только Grafana , сертификат получить и закрыть за прокси-сервером, тогда файл конфигурации Caddyfile выглядел бы так:
test.akmalov.comreverse_proxy grafana:3000
За две строки в источнике мы получаем полноценный прокси-сервер, с перенаправлением HTTP на HTTPS и автоматической генерацией SSL-сертификатов. Вот за это мне и нравится Кэдди.
И напоследок — интересные и полезные материалы:
- Тест производительности Traefik и Caddy 2 (2023 г.)
- Примеры github caddy (примеры конфигураций для разных случаев)
Top 10 Best Reverse Proxy for Linux / Windows / Docker. Firstly, a reverse proxy is a type of server that sits in between a private network to direct client requests to the appropriate application’s back end server. Primarily, it receives requests and forwards them to the server to provide a smooth network traffic flow between clients and servers. Basically, this type of server is implemented to increase web performance, reliability, and security.
Secondly, A reverse proxy in your network receives HTTP connection requests and serves as a gateway between users and the web application’s backend server. Ideally, businesses with intricate backend servers use reverse proxies to serve data to clients in a seamless manner.
This article dives deep into what a reverse proxy is, how it works, and some of the best reverse proxy servers available in the market.
Shall we start our article about Top 10 Best Reverse Proxy for Linux / Windows / Docker. Please read on!
How Do Reverse Proxies Work?

All in all, a reverse proxy acts as an intermediary server by taking a client request and passing it to backend servers. Subsequently, it conveys the response from the server back to the client. After that, the backend server processes the request, which the reverse proxy returns to the client. These proxies work in split seconds to reduce latency.
Basically, a reverse proxy server is best be described as an internal facing proxy employed as a “frontend” to run and secure access to backend servers on a private network. Besides, this proxy is normally situated behind the network firewall. Certainly, also it enables backend servers to achieve anonymity and enhance their security. Moreover, reverse proxy also serves as an application firewall, web accelerator, TLS terminator, and much more.
Benefits of Using a Reverse Proxy
Below are some benefits of using a reverse proxy:
Load Balancing
Popular websites that get millions of users daily might find it difficult to handle their incoming site traffic using a single origin server. Therefore, to solve this, the site chooses to be distributed data among a pool of other servers, all of them handling requests from that particular site.
In such a case, the reverse proxy provides a load balancing solution by distributing the incoming site traffic proportionately among different servers to avoid overloading any single server. Even, if a server does happen to fail, the remaining operational servers steps up to manage the traffic.
Security
Consequently, reverse proxy eliminates the need for a website or service to reveal its origin server’s IP address. Masking the origin server IP address makes it very difficult for attackers to coordinate a targeted attack against the site. Instead, all attacks are only directed at the reverse proxy, which is better equipped to fight off a cyber attack. For extra protection against bots and hackers, you can put in place a web application firewall on your reverse proxies.
Caching
Equally, reverse proxies help in improving performance by caching content.
Encryption
Encrypting and decrypting TLS (or SSL) communication for individual clients can be very expensive for an origin server. However, a reverse proxy can be configured to encrypt all outgoing responses and decrypt all incoming requests, thus freeing up important resources on the origin server.
Testing
Further, a reverse proxy performs multivariate and A/B testing without JavaScript coding or tags.
Top 10 Best Reverse Proxy for Linux / Windows / Docker
In this article, we review the top 10 reverse proxies that are available for Linux, Windows, and Docker:
1. HAProxy

First on the list of Top 10 Best Reverse Proxy for Linux / Windows / Docker is HAProxy. Well, it stands for High Availability Proxy. Fast, free, open source reverse proxy with top-notch load balancing and proxying capabilities for HTTP and TCP based applications. Also, acts as a TCP proxy and normalizer, HTTP reverse proxy, HTTP compression off loader, and content based switch. Furthermore, it acts as an SSL/TLS off-loader/terminator/initiator, a caching proxy, and much more. In turn, this enables it to provide low latency while providing protection against DDoS attacks.
HAProxy is powered by a non blocking, event driven engine that combines a priority based, multi threaded scheduler with a first I/O layer. This engine enables it to deal with thousands of concurrent connections easily. So, in HAProxy, the proxy protocol forwards the client’s connection information to the application servers.
The basic features of HAProxy include SSL support, load balancing, monitoring of both server states plus its state, proxying, HTTP rewriting, server protection, statistics, stickiness, logging, and more.
Pros of HAProxy
- Supports multiple network segments and virtual hosting (layers 4 & 7).
- Well detailed and user friendly status page.
- Easy and smooth integration with third party monitoring tools and services.
- Supports cookie guidance and session retention.
- High load balancing speeds.
Cons of HAProxy
- Does not support web server capabilities.
- Does not support SPDY and POP/SMTP protocol.
- No support the HTTP cache function.
- Poor support for multi process mode.
2. NGINX

NGINX is a popular, free, open source server and reverse proxy that also works as an IMAP/POP3 proxy server. For instance, this reverse protocol is best known for its stability, high performance, low resource consumption, and rich feature set.
Similar to HAProxy, NGINX is powered by an event driven architecture. This means it handles thousands of concurrent connections, since it uses its powerful proxy protocol. Supports accelerated reverse proxying using the ngx_http_proxy_module module, which allows passing requests to another server over protocols such as Memcached, FastCGI, SCGI, and UWSGI.
Likewise, NGINX supports fault tolerance and load balancing, which are important elements of large scale computing systems. The ngx_http_upstream_module allows the defining of backend server groups to distribute incoming requests from clients. For that reason, this makes applications more reliable, available, and robust. Additionally, NGINX supports security features such as SSL/TLS termination.
Pros of NGINX
- NGINX has one of the most consistently written code bases.
- User friendly configuration format.
- With NGINX, the user handles several connections since it supports context switching.
- Enhances the website’s performance.
- Supports various web applications like Joomla, Python, and Ruby.
- Allows the simultaneous handling of multiple concurrent connections.
- It is not highly dependent on network stability.
- The port features allow for the detection of any internal failures.
Cons of NGINX
- Smaller community support when compared to other reverse proxies.
- Only provides support for HTTPS, HTTP, and email protocols.
- URL detection is not covered by the back-end server health check.
3. Varnish HTTP Cache
Varnish HTTP Cache is a free and open source caching reverse proxy that also doubles up as a web application accelerator. Built to enhance HTTP functionality by using server-side caching.
Typically deployed between an HTTP web server/application and a client. Each time a client makes a request for resources or information from a web server, a copy of the information is stored by Varnish, so when the client requests the same information, Varnish serves it without passing a request to the web server. For this reason, this reduces the load on the server and speeds up the process of delivering web content.
Varnish Configuration Language (VLC) is a flexible configuration language that allows system administrators to configure how incoming requests are processed, what content is served, and how the requests/responses are altered.
Given these points, varnish extends using Varnish Modules (VMODs), allowing users to write their custom modules or use community-provided modules. However, varnish does not support SSL/TLS. In addition, to enable HTTPS, the user has to deploy an SSL/TLS off-loader or terminator in front of it.
Pros of Varnish HTTP Server
- One time installation ensures that no further checks or updates are required after installation.
- Enhanced user experience with fast search results.
- Supports customization to software which in turn increases performance.
- Reliability and affordability.
Cons of Varnish HTTP Server
- Does not support Standard integrated SSL.
- The cache does not update in real time.
4. Traefik

Traefik is a fast load balancer and HTTP reverse proxy for deploying microservices with support for multiple load balancing algorithms. Interfaces with a wide range of providers, such as Docker, Etcd, Swarm, Zookeeper, Mesos/Marathon, Rest API, and Kubernetes.
Major strength of Traefik is its ability to dynamically and automatically manage its configuration. Significantly, it achieves this by scanning the infrastructure for relevant information and locating which service serves which request from the outside. Providers then inform Traefik, where your microservices or applications are located.
Simultaneously, Traefik supports HTTP/2 and GRPC, WebSockets, HTTPS using Let’s Encrypt certificates, and a REST API. Provides metrics ( Statsd, Datadog, Rest, InfluxDB, Prometheus). In essence, Traefik comes with a HTML based web user interface to monitor events. Supports rate limiting, basic authentication, and retry requests.
Pros of Traefik
- Seamless Kubernetes integration.
- A simple and clean user interface.
- Supports multiple load balancing algorithms.
- Has Letsencrypt support
Cons of Traefix
- Not very beginner friendly, and has a steep learning curve.
- Poor documentation, especially in the earlier versions.
5. Apache HTTP server

Following choice of Top 10 Best Reverse Proxy is Apache HTTP Server. Arguably the most popular web server in the world. In fact, it be configured to act as a reverse proxy. Surely, Apache web server comes with modules that increase the software’s functions.
In like manner, Apache processes requests and serves the web via HTTP. Distributes traffic across web servers that handle HTTP(s) requests and application servers. Thereafter, Apache HTTP Server is a feature rich tool. Some of its top features include:
- FTP connections.
- URL rewriting
- .ht access.
- PHP, Perl, and Lua scripts.
- Bandwidth throttling.
- Gzip compression and decompression.
Use apache HTTP Server for a wide variety of protocols, with HTTP(s) being the primary protocol. In short, the server is configured via config files whereby modules control its behaviour.
Pros of Apache HTTP Server
- Updates security patches frequently.
- The software is open source and free, even for commercial users.
- The module based structure increases flexibility.
- Beginner friendly and easy to use.
- Cross platform as both Windows and Unix servers.
- Large community and readily available support.
- Out-of-the-box functionality for WordPress sites.
- Compatibility with all programming languages.
Cons of Apache HTTP Server
- Difficulty in handling multiple concurrent requests on websites with extremely heavy traffic.
- Too many configuration options increase security vulnerabilities.
6. Squid Proxy Server
Next choice on our list is Squid Proxy Server. Open source caching proxy that supports FTP, HTTP, and HTTPS among other protocols. Acts as an intermediary proxy that aids in enhancing response times and reducing bandwidth usage by caching and serving the frequently requested web pages. Generally, squid is a great accelerator that also provides access control capabilities.
Thus, squid proxy works as a proxy cache and has a reverse proxy mode feature that caches incoming requests for outbound data. Access control, traffic optimization options as well as authorization are supported. Undoubtedly, Squid Proxy server also integrates easily with a lot of third-party software solutions.
Pros of Squid Proxy Server
- Provides improved network security.
- Offers SSL encryption.
- Aids in distributing requests to multiple origin servers.
- Generates reports that you can utilize as input for resource planning, security, and scaling.
Cons of Squid Proxy Server
- Relatively fewer functionalities compared to other reverse proxies.
- The data center contains only shared or private proxies
- Has no live support.
7. Lighttpd

Lighttpd which is pronounced as “Lighty” is a web server software that is built for flexibility, speed, and security. Ideal for diverse applications, dynamic websites, or environments with minimal resources. In truth, Lighttpd provides support for SCGI, FastCGI, and CGI. Meaning you can use this server software in conjunction with applications written in any programming language.
Pros of Lighttpd
- Supports all programming languages.
- Handles all requests asynchronously.
- The software is open-source and free to use.
- Low RAM usage even when serving thousands of users.
Cons of Lighttpd
- Lacks most advanced features present in other server software.
- Limited performance for larger websites as it uses a single CPU thread.
8. Microsoft IIS

Another of Top 10 Best Reverse Proxy is Microsoft IIS. Of course, a web server software developed by Microsoft for the Windows system. In addition, Microsoft IIS is a secure and flexible server thatis used to host web applications and services. Unlike other reverse proxies, Microsoft IIS has a unique design. Server features are managed as standalone points. On balance, this means you can easily add, remove, or replace them as you want.
Since you choose a certain set of server features, it’s possible to create a custom reverse proxy unique to your business needs. This type of architecture provides multiple benefits as it addresses specific business needs. Removing unnecessary features reduces memory usage and enhances server performance.
Pros of Microsoft IIS
- Highly extensible web server.
- Seamless integration with other Microsoft products.
- Leverages the full power of ASP.NET.
- Has a great developer experience.
- Low memory footprint and improves performance.
- Secures the server by reducing the surface area of attacks.
Cons of Microsoft IIS
- Configuring IIS reverse proxy requires advanced Microsoft development skills.
- You can only use with Windows OS.
9. Apache Tomcat

Apache Tomcat is an open source implementation of Java Server Pages, Java Servlet, Java WebSocket technologies, and Java Expression language. Well, it acts as a matured Java servlet container. Container helps install various Java enterprise specifications such as JavaServer Pages (JSP).
Pros of Apache Tomcat
- Free and open source.
- Regular updates to patch any vulnerabilities.
- Runs several web applications on different ports.
- Use Apache Tomcat use on multiple operating systems.
Cons of Apache Tomcat
- Low speeds when working with static pages.
- Problems with installations.
- Has a poor user interface
10. HashiCorp Consul

Last on the list of Top 10 Best Reverse Proxy for Linux / Windows / Docker is HashiCorp Consul. To illustrate it is a data center aware solution designed to connect and configure applications across distributed and dynamic infrastructure. Basically, it acts as a reverse proxy for Docker applications.
Consuls’ main features include:
- Service Mesh- This feature allows secure service-to-service communication with identity-based authorization and automatic TLS encryption.
- Multi Data Center– Consul supports multiple regions without complicated configurations.
- Health Checking– This enables the Consul to warn operators about any issues present in a cluster.
Pros of Hashicorp Consul
- Allows for easy and quick viewing of the status of your services.
- Consul offers convenient APIs that enable you to automate tasks.
- Seamless integration with other HashiCorp tools.
- Consul has service mesh capabilities that simplify the process of connecting and managing microservices.
Cons of Hashicorp Consul
- Relatively expensive.
- Complex with steep learning features.
- Limited features compared to popular proxies like NGINX.
Thank you for reading this article about Top 10 Best Reverse Proxy for Linux / Windows / Docker. We shall conclude.
Top 10 Best Reverse Proxy for Linux / Windows /Docker Conclusion
These are just a few of the best reverse proxies for Windows, Linux, or Docker. With any of these tools, you are sure of fast server requests as they deliver high performance and low latency. Therefore, you should choose a proxy server that works best for your websites or web applications. Keep in mind that the choice of reverse proxy affects most components of your network.
Client’s with a need to secure legacy servers behind a reverse proxy server have an option to use Microsoft IIS. While we typically recommend using a Linux server that has NGINX installed, we understand the need for such a use case and feel it’s important to demonstrate this basic technique.
We’ll be using a VM running Windows Server 2019 with IIS 10 installed. The IIS extension we’ll use is called URL Rewrite and has been around since IIS 7, so this technique should work well with older versions of IIS.
Assumptions
We won’t cover the basics of spinning up a VM running Windows Server on Microsoft Azure in this article. For more information on that topic, check out this great Microsoft Quickstart Tutorial on setting up a VM and installing IIS.
This article assumes you have the following items setup prior to starting this tutorial:
- Azure Portal — you will need a Microsoft Azure account.
- Azure Windows VM — we will be running Windows Server 2019 for this tutorial.
- IIS — we have installed IIS 10.
- Domain Name — you will need access to a domain or use a dynamic DNS service.
- DNS — we have setup azure-test.tevpro.com to point to the public IP of our VM.
Step 1: Install URL Rewrite
We have installed IIS 10 using a simple PowerShell command.
Doing so will setup and configure IIS using all the basic defaults that come with IIS.
Install-WindowsFeature -name Web-Server -IncludeManagementTools
The first thing we need to do is install an IIS extension called URL Rewrite. This will allow us to configure IIS to act as a reverse proxy server.
On the server you choose as your reverse proxy, download and install the URL Rewrite extension taking all the defaults when installing.
Step 2: Setup a Website
To begin, open up IIS manager and create a new website to use as your reverse proxy end-point. It should look like this:
Right click on Sites, then select Add Website.
Next, fill in some details about the website. For our example, we will create a new sub-domain for our Tevpro.com website.
Note: Even though we aren’t setting up an actual website, we still need to create a folder somewhere for our dummy site. Here, we created a test folder under our websites folder.
Once you have completed the form, click OK.
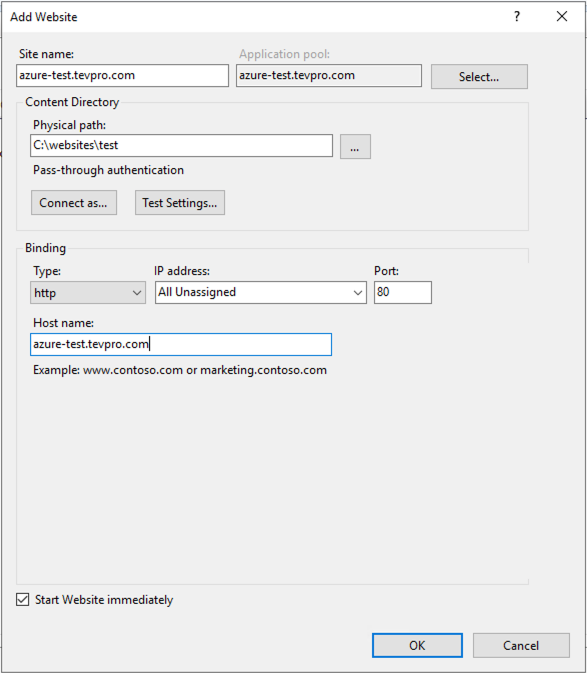
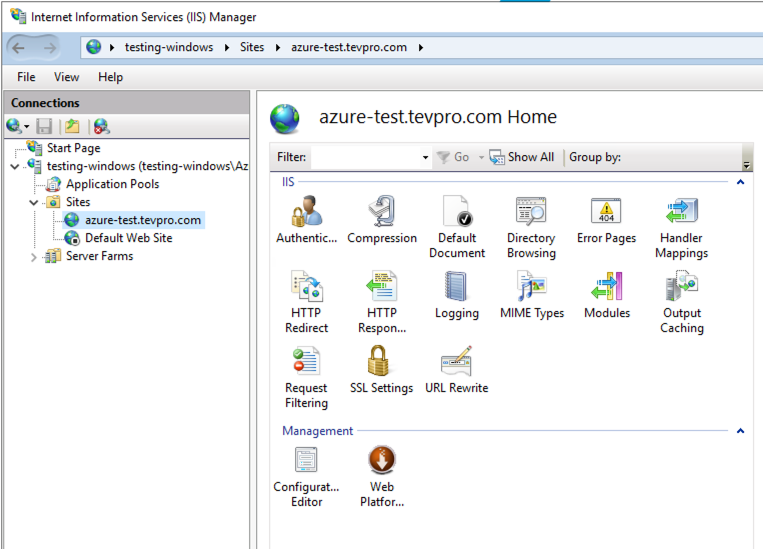
After clicking OK, we should see our website.
When selected, we should see the following options. Notice the URL Rewrite option that shows up after we successfully installed the extension. This is what we will use to configure our reverse proxy.
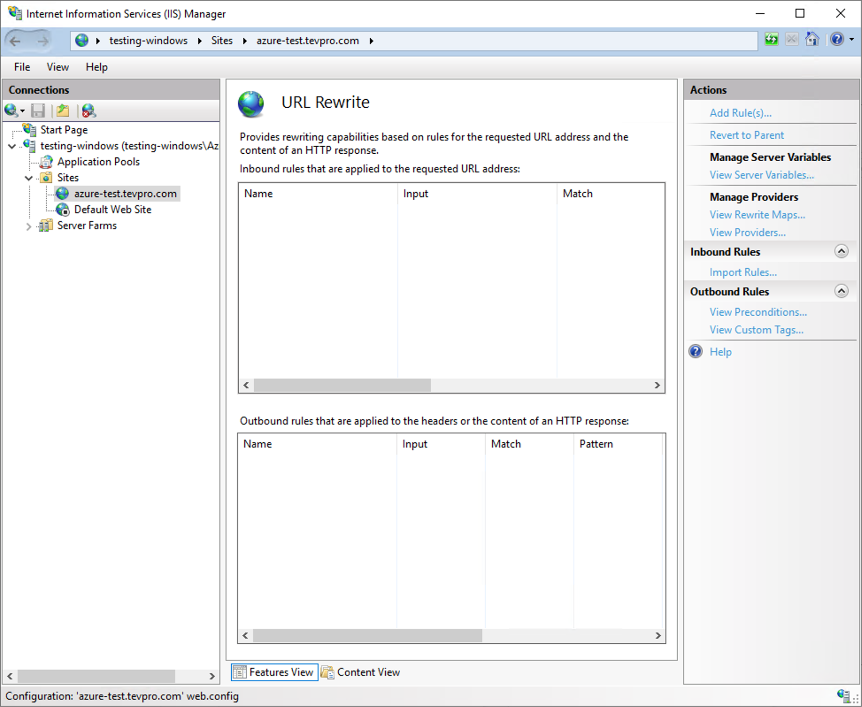
Step 3: Configure URL Rewrite
After we have setup our new website, that will act as our public end-point, we need to configure it as our reverse proxy.
To do this, double click on the URL Rewrite option under our website (shown in Figure 3).
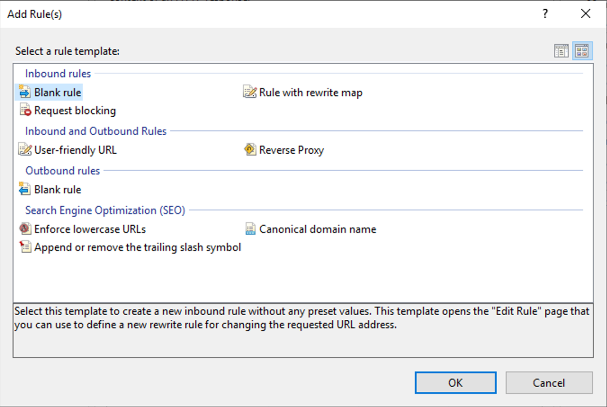
Next, click the Add Rule(s) item from the Actions section on the far right.
This will bring up the following dialog, under Inbound rules. Select Blank rule and click OK.
For our example, the configuration is pretty straightforward. It’s outside of the scope of this article, but know you can get more complex in the pattern matching and route handling.
First, we need to provide a name for our rule, add a pattern for how we want to match incoming request, and set the rewrite URL.
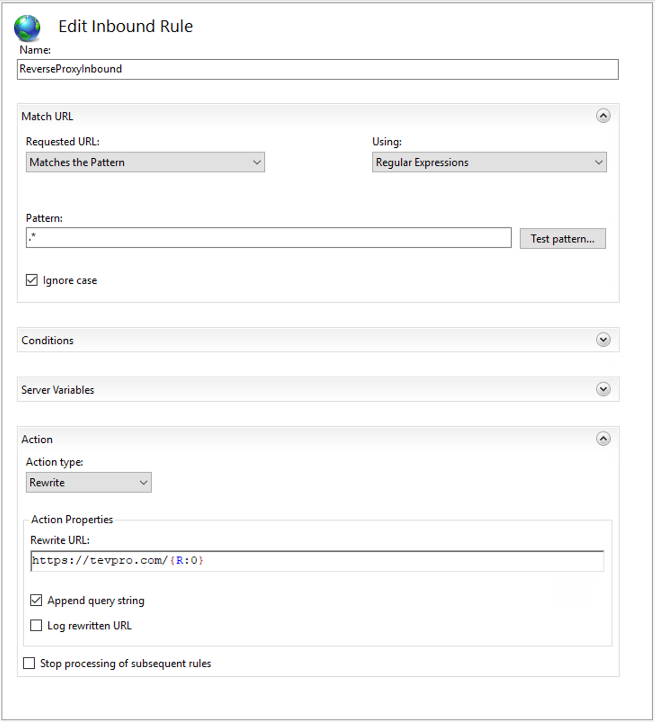
Breaking this step down a bit further, the pattern is how we want to handle capturing incoming request to the website we setup to act as our reverse proxy (azure-test.tevpro.com).
Since we want to be very broad and capture everything, our regex is quite simple. We want to match everything after the domain name, which is what «.*» will do for us.
Click the Test pattern… button and a tool dialog pops up that allows us to test our pattern. We want to make sure that anytime someone visits azure-test.tevpro.com/blog, we capture anything after the domain name. This way we ensure when we rewrite the URL, we can point to the right location.
Take note of the capture group {R:0}. We will use this to configure our rewrite URL.
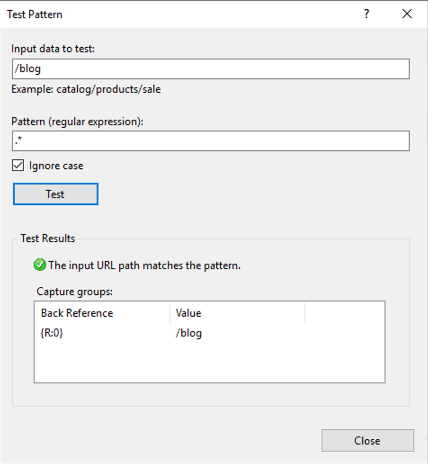
Taking a closer look at our action section, we see the Rewrite URL input field. This field indicates where we want our website to point. Since we want to route back to our website, we put in the URL and append the regex capture group {R:0} from the previous test pattern.
This will forward any request coming into our reverse proxy to the origin server tevpro.com keeping the URL fully intact.
Once you have finished setting up the new rule, click Apply.
And viola. We have configured our new website to act as a reverse proxy.
Note: Since we require SSL for our website, we configured SSL for our test server. That’s beyond the scope of this article, however we used Let’s Encrypt.
Step 4: Test the Reverse Proxy
Now that we have completed the reverse proxy configuration, we need to test our new website.
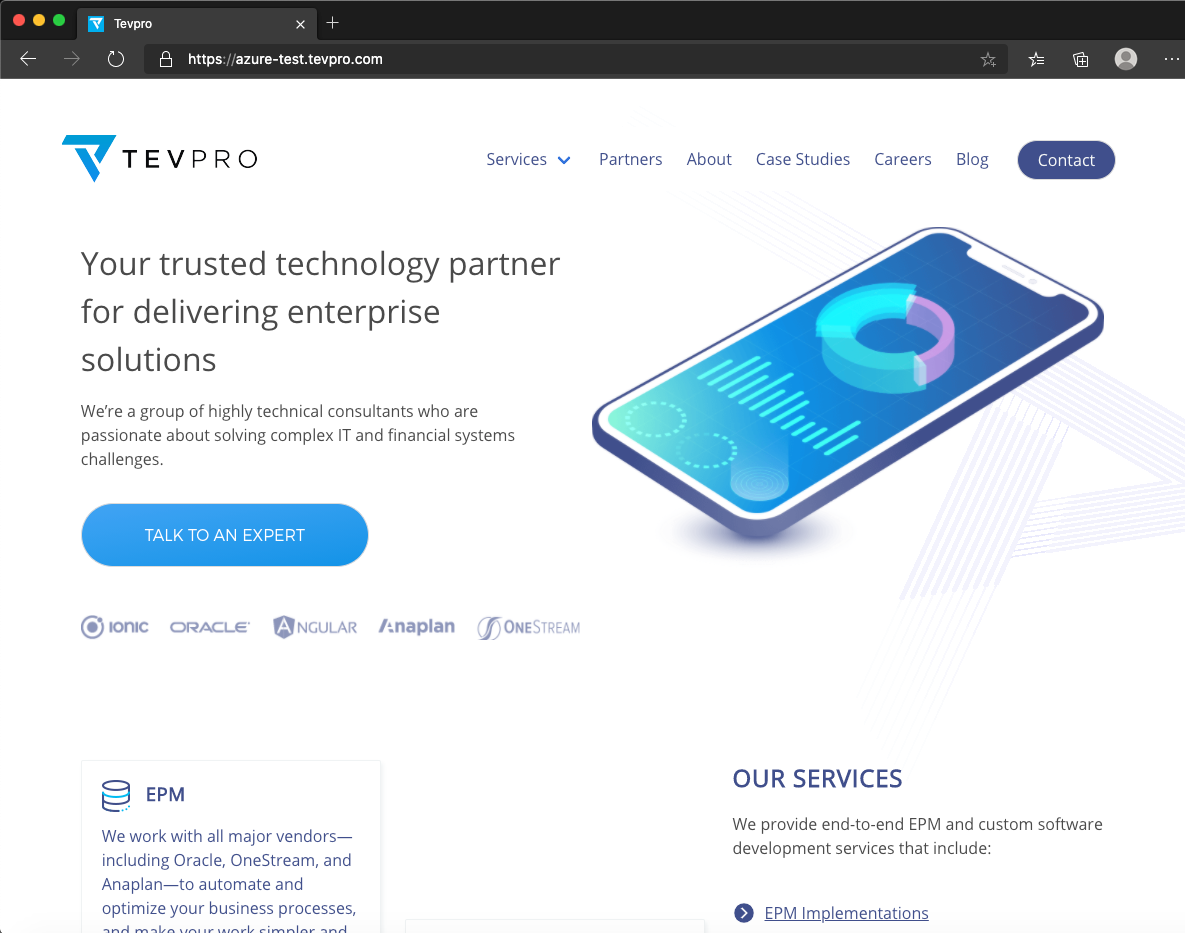
We expect that anytime a user visits the URL, azure-test.tevpro.com, we’ll automatically reroute the corresponding request to tevpro.com.
As you can see below, when we type the URL into our web browser, we see the Tevpro.com website. It is actually being masked behind our reverse proxy website. Pretty cool, right?
Conclusion
As you can see, it’s pretty simple technique to set up a reverse proxy server using IIS. The IIS extension does most of the heavy lifting and can be used for more complex routing when needed.
Whether you’re trying to protect a legacy system or add an extra layer in front of your existing website to make migrations easier, this approach has worked well over the years.
At Tevpro, we have helped countless clients improve their business with even the most basic techniques and technology solutions. We’re here to help clients discover their potential in a range of solutions, and weigh pros/cons, so that they are empowered to make the best decision for their business.
Feel free to reach out to us on Twitter or via email with any questions.
Photo by Science in HD
