Contents
- YouTube video
- Important info
- Objectives
- Disclaimer
- Requirements
- Help out devs
- Alternatives
- Credits
- FAQ (Frequently Asked Questions)
- Can I run this in Virtualbox or similar?
- Will I be able to install Windows on real computers?
- Proxmox or XCP-ng?
- Docker, really?
- Which Linux distro should I use?
- Docker swarm?
- (CAVEAT) Do I need secure boot?
- BIOS or UEFI?
- Boot file type differences?
- Can I use the SAMBA server for other stuff?
- I already have a SAMBA server running, can I use that?
- Linux server deployment
- Configure sudo access
- Install docker
- Get VM IP address
- Deploy containers with docker compose
- Clone GitHub repo where containers are
- Deploy netboot.xyz container
- Deploy samba container
- Generate new password for samba user
- Deploy container
- Configure samba permissions
- Add DNS entries
- Configure router after setting up container
- Configure Mikrotik router
- Download additional menus
- Configure netboot.xyz to use local assets
- Download an asset locally and test
- Boot a machine to test a local asset
- Create Windows 11 installation media
- Download and extract the Windows ISO to samba drive
- Create Windows WinPE ISO
- Download and install WinPE
- Create Bootable WinPE media
- Mount the Windows PE boot image
- Copy boot files back to the Windows PE add-on installation
- Unmount the WinPE image, committing changes
- Create working files
- (OPTIONAL) Customize Windows PE
- Create bootable media (WinPE ISO)
- Copy the WinPE ISO files to the samba server
- Configure netboot to point to the WinPE files
- Configure custom options in windows.ipxe
- Configure samba server and password in winpe files
- Configure autoattend.xml file
- Disable secure boot
- Install windows via netboot.xyz
- If you like my content, and want to support me
- Discord server
- Follow me on social media
- All links in the video description
- How do you manage your passwords?
YouTube video
Important info
Objectives
- Be able to install Windows 11 (or a lot of different OSs or tools available) via the network, instead of having to store them in a flash drive and install from there
- To see the list of OSs and tools available on netboot.xyz go to this page
- By the end of this tutorial, you will have learned how to:
- Install docker on Linux
- Deploy the
netboot.xyzandsambacontainers - Create winpe images
- Install Windows 11 over the network
- And much more
Disclaimer
- This tutorial is designed purely for educational objectives.
- Microsoft activation keys are not included at any stage of this tutorial. Also, refrain from sharing any Windows activation keys in the comment section.
- You can use generic Microsoft keys to install a specific windows version but these keys will not activate Windows, you will need to provide your own purchased license key to activate Windows later on.
- So this guide is meant for use with a Windows activation key that you have legally acquired.
Requirements
- You will need a
windows computer, that’s where we will create the WinPE image which will help install Windows over the network, you will understand what this means later- I will use a windows VM, that works too, as long as it can reach other devices in your local network
- You will need a Linux VM because that’s where we will install docker
- You can virtualize it in VirtualBox (or whatever you chose), I havent’ tested this in virtualization software, but it should work
- If you run a hypervisor already (Proxmox, XCP-ng, VMware) just run the VM there
Help out devs
- If you like the netboot.xyz project, please donate to their devs, if possible at least one time
https://github.com/sponsors/netbootxyz- I don’t know the developers, nor had I had any contact with them
Alternatives
- If you don’t want to boot over network, there’s Ventoy, that allows you to store multile ISOs in a flash drive and boot from those
https://github.com/ventoy/Ventoy- That’s not the purpose of this guide, this is specifically to avoid USB drives, and boot from the network instead
- There’s another PXE server alternative called
iVentoy
Credits
- This guide was built on Techno Tim’s YouTube video, I didn’t know about netboot.xyz before this
https://youtu.be/4btW5x_clpg?si=G7_bLA6axCvOIx53
- I was having issues with the Windows installation part, but with a comment from user @jaromirrivera on Techno Tim’s blogpost I was able to figure it out and go from there
https://technotim.live/posts/netbootxyz-tutorial/
- Yeah, my blog looks like Techno Tim’s, guess how I set it up :shhhhh:
FAQ (Frequently Asked Questions)
Can I run this in Virtualbox or similar?
- This guide’s setup, including the deployment of Docker containers and network booting services, is designed to be compatible with virtualization environments like VirtualBox, VMware, and others. Running the setup in a virtual machine (VM) should work, in theory, as long as the VM is correctly configured and reachable over the network by other devices. Here are some key points to ensure compatibility:
- Network Configuration: Ensure your VM’s network adapter is set to a mode that allows it to communicate with other devices on your network. Bridged Adapter or Host-only Networking (with additional configuration) are commonly used modes. Bridged Adapter mode is recommended for easier accessibility from other devices on the network.
- Resource Allocation: Allocate sufficient resources (CPU, RAM, and disk space) to your VM to handle the workload. This setup is not particularly resource-intensive, but ensuring your VM has enough resources to run Docker and the contained services smoothly is crucial.
- Port Accessibility: Make sure any ports required by the deployed containers (e.g., port 69 for TFTP, port 8083 for the NGINX server, etc.) are not blocked by the host machine’s firewall or by the virtualization software’s network settings.
- VM Reachability: Test the VM’s IP address from another device on the same network to confirm that it’s reachable. This step is crucial for network booting to work, as other devices need to communicate with the services running inside the VM.
- I haven’t used virtualization environments in years, so that’s as far as I can go, but if you know what you’re doing, you should be good.
- If you have questions go to the comments section below on the website and hopefully other kind, open source loving souls, will be able to assist.
Will I be able to install Windows on real computers?
- Yes, once everything is setup, you will be able to install Windows 11 over the network on regular computers, I installed windows on my laptop that way and it worked fine
Proxmox or XCP-ng?
- If you don’t know what I’m talking about, just skip this section.
- Most people use proxmox these days, I use XCP-ng, but what won’t make a difference or affect you in any way, just deploy your VM as you regularly do in proxmox
Docker, really?
- We will deploy the tools that we need as docker containers because it’s easier to install and configure them, it doesn’t matter what distro you’re on, once you have docker installed, the containers will run the same
- I hate docker, I prefer installing things like back in the day, do I need to use it?
- No, but this guide does, so if you want to install the stuff needed, manually on your own, or you already have it installed, skip those parts and go to the relevant sections
- This is not a docker course, so if you want to learn more about docker there’s plenty of youtube videos out there, if you want me to create some videos that teach docker with practical examples, like the ones seen in this guide, let me know in the youtube comments.
Which Linux distro should I use?
- My distro of choice is always Debian, so this guide is only tested in Debian you could try a Debian based distro, like Ubuntu and it should work, but there are no guarantees. If you’re using another distro, just translate the logic to that distro but it shouldn’t vary much as we will install the required packages as docker containers. So once you have docker installed, you should be ready to go.
- I’m running a regular Debian server, no GUI as you won’t use it anyway because all of the work will be done via SSH
- As of Feb 2024, I’m running Debian 12 bookworm
Docker swarm?
- I wasn’t able to get the
netboot.xyzcontainer to run in docker swarm, probably due to the VIP shared by keepalived between the 3 docker hosts - Not 100% sure, don’t have the time to figure it out right now , so instead I just deployed it in a single host with docker compose. Which is what we’ll do in this guide
- Will probably migrate the container to Kubernetes in the future anyway, so will be skipping swarm altogether. Or maybe I’ll just leave it running in a single docker host, Who knows.
(CAVEAT) Do I need secure boot?
https://support.microsoft.com/en-gb/windows/windows-11-system-requirements-86c11283-ea52-4782-9efd-7674389a7ba3- The link above describes that Windows 11 requires that your machine is running
secure boot, see the requirements below from that page: - System Firmware: UEFI (for Unified Extensible Firmware Interface, a modern version of the PC BIOS) and Secure Boot capable. If your device does not meet the minimum requirements because it is not Secure Boot capable
- The link above describes that Windows 11 requires that your machine is running
- Does netboot.xyz support Secure Boot?
- netboot.xyz doesn’t support Secure Boot, I found this on the netboot.xyz FAQ:
https://netboot.xyz/docs/faq/#does-netbootxyz-support-secure-boot- iPXE and hence netboot.xyz does not support Secure Boot because its binaries are not signed by Microsoft. You must disable Secure Boot mode in your computers firmware configuration menu before you can boot netboot.xyz.
- So we have a dilemma, windows requires
Secure bootbut netboot.xyz does NOT supportSecure boot - We’ll fix this by configuring the windows installer to bypass the secure boot, and TPM checks later on
- This means you can proceed with the installation regardless of whether Secure Boot is enabled or not
BIOS or UEFI?
- BIOS and UEFI are firmware types, and they serve as an interface between the computer’s operating system and its hardware, performing initial hardware checks and booting the operating system
- BIOS (Basic Input/Output System)
- Legacy firmware interface for PCs, initializing and testing hardware at startup.
- Supports MBR (Master Boot Record) partition tables, limiting drives to 2TB.
- Does not support native secure boot.
- Interface is typically text-based, with limited mouse support.
- UEFI (Unified Extensible Firmware Interface)
- Modern firmware interface designed to replace BIOS, providing faster boot times.
- Supports GPT (GUID Partition Table) for larger drives (over 2TB) and more partitions.
- Native support for secure boot, ensuring that only signed bootloaders run.
- Graphical interface with support for mouse and network functionality in the pre-boot environment.
Personally, I'll handle everything with UEFI- If your machine is kind of old, and the only option it has available is BIOS then set your boot file type, on your router, to a BIOS one, see below how to do this
- I tested running windows 11 in both UEFI and BIOS and it worked fine in both
Boot file type differences?
- Whatever firmware you decide to go with (BIOS or UEFI) will determine the type of boot file you will configure on your router, you’ll understand this later but for now, all you need to know is that there are different boot file types:
netboot.xyz.efiis used for devices that boot using UEFI firmware. The .efi extension is a file format for UEFI applications, including bootloaders.netboot.xyz-snp.efiUEFI w/ Simple Network Protocol, attempts to boot all net devices- This is the only one that worked for my case, you will see why below
netboot.xyz.kpxeis used for devices that boot using legacy BIOS firmware The .kpxe extension indicates that it’s a PXE (Preboot Execution Environment) kernel, which allows computers to load and boot an operating system from a network server instead of local storage.
Can I use the SAMBA server for other stuff?
- Yes, we will be deploying a samba server running in a docker container, you can create other users, samba shares, groups, etc. I even store my time machine backups in my samba container.
- So it’s a normal SAMBA server that you can use for anything you want, we’re just using it for a specific purpose in the video
- If you’d like to to go over how I set up my samba, let me know in the video comments
I already have a SAMBA server running, can I use that?
- Yes, you can use your existing samba server, you don’t need to deploy this other one
Linux server deployment
Configure sudo access
- If you can run the command below, without being asked for your password, skip this section
- I have to log in as root to do be able to add my user to the sudoers file
- Remember that I’m on Debian, may be different for your distro
1 2 3 4 5 |
# Saving the name of my current user to a temp file because will need it whoami > /tmp/current_user # Log in as root su - |
- If you already have the packages below installed, and run the install commands again, the packages will just be updated, so no worries
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
# Update package lists and install common Linux tools apt-get update apt-get install -y vim curl wget git htop net-tools sudo # Create a sudoers file for the current user in the correct directory # This command allows you to enter sudo commands without being asked for the password # The name of the file doesnt have to match the user, but its good for consistency my_current_user=$(cat /tmp/current_user) echo "$my_current_user ALL=(ALL) NOPASSWD:ALL" > /etc/sudoers.d/$my_current_user # Set the file permissions to 440 for security chmod 440 /etc/sudoers.d/$my_current_user # Cleanup the temporary file rm /tmp/current_user # Exit the root shell and go back to our regular user exit |
- Here’s the contents of the file
1 |
sudo cat /etc/sudoers.d/$(whoami) |
- Now my user can run sudo commands without being asked for the password
In case you want to remove what we just did, just delete the file we created
1 |
sudo rm /etc/sudoers.d/krishna
|
Install docker
- If you already have docker installed, skip this section
- If you’re following this guide, you should have docker installed, but in case you don’t here’s a script that installs it on
debian - If you want to understand what the script does, go and check out my other article
- Install docker using the convenience script
1 2 3 4 5 6 7 8 |
# Download docker official install script curl -fsSL https://get.docker.com -o install-docker.sh # Run installation as root sudo sh install-docker.sh # Add your current user to the docker group sudo usermod -aG docker $(whoami) |
- Once this is done, exit your shell and log in again
- You will now be able to run docker commands without sudo
- If you see the headers below, it means you’re good
1 2 |
krishna@docker4:~$ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
Get VM IP address
- We need the IP address of the VM where the docker container is running, so that we can configure our router to point to it
- Both commands below do the same thing, they will show you the IP of the interface being used to connect to the internet, which is likely your local IP
1 |
ip route get 8.8.8.8 | awk '{print $7}' | head -n 1 |
- Notice that in my case, the machine IP is
192.168.88.135
1 2 3 4 5 |
krishna.@.linkarzu-docker~ [24/02/11 13:13:56] ❯ ip route get 8.8.8.8 | awk '{print $7}' | head -n 1 192.168.88.135 |
Deploy containers with docker compose
- If you’re new to docker, there are several ways of deploying containers, in our case, we will use docker compose, which allows us to deploy a docker container from a yaml file
Clone GitHub repo where containers are
- First we will clone the repo where my docker compose files are
- If you installed git above, or already have it installed, you can run the install command below again and nothing happens
1 2 3 4 5 6 7 8 9 10 |
# Install git to be able to clone the repo sudo apt-get update sudo apt-get install git # Clone my repo where the docker compose file is and change to that dir echo echo "Cloning github repo" mkdir -p ~/github/ cd ~/github/ git clone https://github.com/linkarzu/containerdata-public.git |
Deploy netboot.xyz container
- This container deploys a few things:
Web Interface (Port 3029): This allows you to download images, see the menus, download boot menus and other things in a graphical interfaceTFTP Port (Port 69/UDP): This is used to serve boot files for PXE booting. This is done so that PXE-enabled clients can download boot filesNGINX Server for Hosting Assets (Port 8083): Maps port 8083 to NGINX’s port 80 inside the container for hosting boot assets like OS images.
- So after downloading the repo to the local computer, we will deploy the docker container
-f— specifies the path to the .yml fileup— up is used to create and start the container-d— will start the container in detached mode, which will allow you to keep using your terminal- Previously command was
docker-composebut it changed todocker compose
1 |
docker compose -f ~/github/containerdata-public/docker/netbootxyz/docker-compose.yml up -d |
- NOTE:
- If you receive a message that says something like:
Bind for 0.0.0.0:8083 failed: port is already allocated- It means that other service on the host is already using port 8083
- So I’d recommend you deploy these containers in a freshly deployed VM
- Otherwise, I assume you know what you’re doing and you’ll be able to fix the port warnings
- If you receive a message that says something like:
- After deploying, make sure the container is running
- You should see something like this
- Notice the status has been up for 2 minutes
1 2 3 |
❯ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
7a0ae35a4842 linuxserver/netbootxyz:0.7.1 "/init" 29 seconds ago Up 23 seconds 0.0.0.0:69->69/udp, :::69->69/udp, 0.0.0.0:8083->80/tcp, :::8083->80/tcp, 0.0.0.0:3029->3000/tcp, :::3029->3000/tcp netbootxyz
|
Deploy samba container
- Samba is an open-source tool that provides file and print services to SMB/CIFS clients, allowing Windows, Linux, and macOS systems to share files, printers, and other resources over a network.
- This container will be used to store the WinPE ISO, also the Windows installation ISO, and other configuration files from our Windows machine to the Linux machine, over the network .
Generate new password for samba user
- In the docker-compose.yml file, there are instructions to change the samba password for the
isosuser - I highly recommend you change the password, instead of using the default one I configured
- I’ll set mine to
- Password —
passpass
- Password —
- But you set your password to something that just you know
- If you change the samba password in the future, redeploy the container to apply the changes
1 |
docker compose -f ~/github/containerdata-public/docker/samba/docker-compose.yml up -d |
Deploy container
- Then deploy the samba container
1 |
docker compose -f ~/github/containerdata-public/docker/samba/docker-compose.yml up -d |
- After deploying, you should see 2 containers running
- You should see something like this
- Notice the status is
upfor both containers
- Notice the status is
1 2 3 4 5 |
❯ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7dae3bd7844e ghcr.io/servercontainers/samba:a3.19.0-s4.18.9-r0 "/container/scripts/…" About a minute ago Up About a minute (healthy) samba 7a0ae35a4842 linuxserver/netbootxyz:0.7.1 "/init" 3 minutes ago Up 3 minutes 0.0.0.0:69->69/udp, :::69->69/udp, 0.0.0.0:8083->80/tcp, :::8083->80/tcp, 0.0.0.0:3029->3000/tcp, :::3029->3000/tcp netbootxyz |
Configure samba permissions
- We need to fix permissions on the
isosdirectory in the samba container - Our samba user
isoshas UID8225and is part of the8598group because we configured it that way in the docker container - So we will give write access on the
isosdirectory to the8225user - That way, when we connect to the samba server from our windows machine, we can add and modify files
- We’re giving it
775permissions - I’m running these commands in the machine where the containers are running
- I’m giving it 775 permissions, so that you can still edit the files from your Linux VM if needed, and the group 8598 also has write permissions 8598 is the group that the samba user is part of.
1 2 |
sudo chown -R $(whoami):8598 ~/github/containerdata-public/docker/samba/mnt/isos sudo chmod -R 775 ~/github/containerdata-public/docker/samba/mnt/isos |
Add DNS entries
- If you don’t have DNS servers on your network, skip this step and just use IP addresses instead of DNS names (FQDNs)
- If you have a DNS servers, add a DNS entry for this server where the containers are running, for example:
netbootxyz A 192.168.88.135samba A 192.168.88.135
Configure router after setting up container
- If you have an existing DHCP server, usually you will need to make some small adjustments to make your DHCP server forward requests to the netboot.xyz container. You will need to typically set your
next-serverandboot-file-nameparameters in the DHCP configuration. This tells DHCP to forward requests to the TFTP server and then select a boot file from the TFTP server. - I found this in the official documentation
- In my local network my Mikrotik router #mikrotikForTheWin is my DHCP server as of Feb 2024, so I’ll configure it to forward requests to netboot.xyz
- For instructions on how to set up your router, go to the site below
https://github.com/linuxserver/docker-netbootxyz?tab=readme-ov-file#router-setup-examples- This is from the LinuxServer.io team, which is the docker image I’m using
- If your router is not listed there, you’ll have to Google it or figure it on your own, I had to figure out how to configure Mikrotik, but it was not complicated at all
- If you want to add the steps for your router on this guide, so others can see leave them in a comment and I’ll add them to this section
Configure Mikrotik router
- In Winbox go to
ip - dhcp server - networks - 192.168.88.0/24- Then set the
Next Server, just enter the VM IP we got earlier- If you enter the VM DNS name
192.168.88.135for example, it will automatically change it to the IP address192.168.88.135
- If you enter the VM DNS name
- Then for the
Boot File NameI tried these optionsnetboot.xyz-snp.efi— worked with UEFI VMsnetboot.xyz.kpxe— worked with BIOS VMsnetboot.xyz.efi— didn’t work- not sure why
netboot.xyz.efididn’t work with my VMs and omen laptop. Not sure if it’s a docker thing or what. The list of boot file types I used above, I found it on the docker section of the documentationhttps://netboot.xyz/docs/docker#netbootxyz-boot-file-types
- Mikrotik, unlike other routers, doesn’t allow me to set multiple
Boot File Nameoptions (sad)- This means that I can only use a single boot file name at a time, for either UEFI or BIOS
- Then set the
- If you notice above, the menu that worked for me is
netboot.xyz-snp.efiso we will check if that configuration file is downloaded - Go to the web GUI
http://192.168.88.135:3029 - Go to
Menuson the top- Click on
Menuson the top again
- Click on
- You should see
netboot.xyz-snp.efiin the list on the left hand side - If you don’t see this file:
- Click on
Menu Development Versions - Click on Download the latest release
- Click on
- Now you should see the file on the left
Configure netboot.xyz to use local assets
- With the default configuration, netboot.xyz will be pointing to the
https://github.com/netbootxyzrepo, it will work, but every time you install an OS, for example the tool gparted, it will download it again. I tried to use gparted in the same VM twice, and it went to download it each time. Images won’t be saved in your assets directory. What I’ll do instead is switch tolocal assets - You don’t need to do this, if you leave the config pointing at github it will also work, you don’t have to pre-pull images, but they will be downloaded from the internet every time, if your connection is fast enough I guess you would be fine
- In the same web GUI
http://192.168.88.135:3029 - Go to
Menuson the top - Click on the
boot.cfgfile- We will change this line:
set live_endpoint https://github.com/netbootxyz- To this:
set live_endpoint http://192.168.88.135:8083- We’re using the IP address of the VM where the container is running
- If you have DNS configured, instead of the IP use a DNS name
- Notice I’m pointing it to the port (8083) that’s running Nginx, which hosts the assets
- After this click
Save Configon the top right corner
Download an asset locally and test
- Now that we have pointed netboot.xyz to use local assets, we’ll download a test image to make sure it’s working as expected
- Go to the web GUI
http://192.168.88.135:3029 - Click on
Local Assetsat the top - Search for the image you need
gpartedin this example - You need to download the
3 filesto run any OSvmlinuz— This is the compressed Linux kernel.initrd— Temporary file system used during the initial boot process. It contains the necessary drivers and scripts to mount the real filesystem. In the context of a live environment like GParted, initrd helps to boot the system before the actual filesystem (contained in the filesystem.squashfs file) is mounted.filesystem.squashfs— Compressed file system image. It contains the actual file system with all the necessary files, applications (including GParted), and settings to run the environment. Once the kernel is loaded and the initrd has prepared the system, filesystem.squashfs is mounted to provide the full GParted environment.
- Select the 3 files and click
Pull Selected - Since we changed the config to ‘Local Assets’, you need to make sure to pre-pull the images you want to use ahead of time
- Below are the files that it downloaded for gparted
1 2 |
cd ~/github/containerdata-public/docker/samba/mnt/isos/netbootxyz-assets
tree
|
1 2 3 4 5 6 7 8 9 10 |
❯ cd ~/github/containerdata-public/docker/samba/mnt/isos/netbootxyz-assets tree . ├── debian-squash │ └── releases │ └── download │ └── 1.5.0-6-521af9dc │ ├── filesystem.squashfs │ ├── initrd │ └── vmlinuz |
- Notice that above, you cannot tell which distro these files belong to, so to know that
- Grab the release number
1.5.0-6-521af9dcand go to the web gui192.168.88.135:3029- In the
Local Assetstab, you will see the asset name and also release name gparted-stable 1.5.0-6-521af9dc/filesystem.squashfs- That way you can tell this asset is related to gparted
- In the
Boot a machine to test a local asset
- You can skip this section, but just in case you want to test it’s working
- After downloading the asset locally, we will boot up a new VM to test
- In my hypervisor (XCP-ng) I just selected a
Debiantemplate and changed it toPXEinstead of selecting an ISO - You will notice that nothing happens if you try a tool or OS that you didn’t pre pulled
- Change it to
UEFIbecause I’m usingnetboot.xyz-snp.efias the boot file name on my router
- Windows PE (WinPE) is a small operating system used to install, deploy, and repair Windows desktop editions, Windows Server, and other Windows operating systems. From Windows PE, you can:
- Set up your hard drive before installing Windows.
- Install Windows by using apps or scripts from a network or a local drive.
- Capture and apply Windows images.
- Modify the Windows operating system while it’s not running.
- Set up automatic recovery tools.
- Recover data from unbootable devices.
- Add your own custom shell or GUI to automate these kinds of tasks.
- So we will need to create a WinPE bootable drive, which is what will allow us to install Windows 11 on our machines from the network
Download and extract the Windows ISO to samba drive
- During the network boot windows installation phase, the winpe image will need to point to a dir where this windows ISO is stored
- That’s why we use the samba drive, to store this ISO so that we can reach it
- This is the regular Windows installation ISO that you download from the official Microsoft page
https://www.microsoft.com/software-download/windows11
- So go and download that ISO as we will store all the files that are in the iso in the samba directory
- In my Windows vm:
- First install 7zip as I’ll use it to extract the ISO files
- From the windows machine go to
This PCandmap a network drivefrom the file explorer \\192.168.88.135\isos, enter theisosusername and password- User —
isos - Password —
passpass
- User —
- Right click the windows ISO
show more options - 7zip - extract files - Now in the 7zip extraction menu navigate to the win11 dir
windows\win-os\win11- After selecting the directory I unchecked the option below
Win11_23H2_English_x64v2\so it doesn’t create a new dir, but it instead just extracts the files
- With this we will have the windows ISO, but extracted in our samba drive
Create Windows WinPE ISO
https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/winpe-intro?view=windows-11- In this page, the 2 sections that follow are
Download WinPECreate Bootable WinPE media
- Which is what we will do below
Download and install WinPE
- WinPE is an add-on to the Windows Assessment and Deployment Kit (ADK). You can download the ADK and WinPE add-on from Download and install the ADK. Install the ADK and the WinPE add-ons to start working with WinPE.
- In the same page shown above, right below there’s the link to
Download WinPE - On my
win11-xcpVM, download the windows 11 ADK, link on the microsoft page- Download both:
Windows ADKPE add-on for the Windows ADK
- Install first the
Windows ADK- I installed it with all the defaults
- Then install the
PE add-on for the Windows ADK- I installed it with all the defaults
- Both files are a bit big, so it will take some time to download/install
- Download both:
Create Bootable WinPE media
- In this section, we will also be following the steps that are on the Microsoft guide, all the commands come from there
- The Windows ADK deployment tools and ADK Windows PE Add-ons, include command-line utilities that make it easy to create bootable WinPE media
- Run the
Deployment and Imaging Tools Environmentas administrator - Navigate to the “Windows Preinstallation Environment” folder and the processor architecture folder of your choice. See sample command for the amd64 folder:
1 |
cd "..\Windows Preinstallation Environment\amd64" |
- Sample output
1 2 3 |
C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Deployment Tools>cd "..\Windows Preinstallation Environment\amd64" C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64> |
Mount the Windows PE boot image
- md command creates a directory where the WinPE image will be mounted
- Dism command mounts the image to that directory using the DISM tool
1 2 |
md C:\WinPE_amd64\mount Dism /Mount-Image /ImageFile:"en-us\winpe.wim" /index:1 /MountDir:"C:\WinPE_amd64\mount" |
- Sample output
1 2 3 4 5 6 7 8 9 10 |
C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64>md C:\WinPE_amd64\mount C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64>Dism /Mount-Image /ImageFile:"en-us\winpe.wim" /index:1 /MountDir:"C:\WinPE_amd64\mount" Deployment Image Servicing and Management tool Version: 10.0.25398.1 Mounting image [==========================100.0%==========================] The operation completed successfully. |
- DO NOT RUN THE COMMANDS BELOW, just notice that hese directores were created
- The overall
mountdirectory created has 16,000 files, around 50Mb
- The overall
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64>cd \WinPE_amd64\mount C:\WinPE_amd64\mount>dir Volume in drive C has no label. Volume Serial Number is 60FF-CDC6 Directory of C:\WinPE_amd64\mount 06/10/2023 09:49 PM <DIR> . 02/13/2024 02:13 AM <DIR> .. 06/10/2023 09:49 PM <DIR> Program Files 06/10/2023 09:49 PM <DIR> Program Files (x86) 06/10/2023 09:49 PM <DIR> Users 06/10/2023 09:55 PM <DIR> Windows |
Copy boot files back to the Windows PE add-on installation
- Copies the file
bootmgr.efifrom the source to the destination (Media\) - Copies
bootmgfw.efifrom the source to the destination, renaming it tobootx64.efi- This will copy the files in the
amd64\Media\ - In case you get asked if it’s a file or directory, type F, as it’s a file
- This will copy the files in the
1 2 |
Xcopy "C:\WinPE_amd64\mount\Windows\Boot\EFI\bootmgr.efi" "Media\bootmgr.efi" /Y Xcopy "C:\WinPE_amd64\mount\Windows\Boot\EFI\bootmgfw.efi" "Media\EFI\Boot\bootx64.efi" /Y |
- Sample output
- Notice I got asked if it’s a file or directory and I chose F for file
1 2 3 4 5 6 7 8 9 10 |
C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64>Xcopy "C:\WinPE_amd64\mount\Windows\Boot\EFI\bootmgr.efi" "Media\bootmgr.efi" /Y C:\WinPE_amd64\mount\Windows\Boot\EFI\bootmgr.efi 1 File(s) copied C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64>Xcopy "C:\WinPE_amd64\mount\Windows\Boot\EFI\bootmgfw.efi" "Media\EFI\Boot\bootx64.efi" /Y Does Media\EFI\Boot\bootx64.efi specify a file name or directory name on the target (F = file, D = directory)? F C:\WinPE_amd64\mount\Windows\Boot\EFI\bootmgfw.efi 1 File(s) copied |
Unmount the WinPE image, committing changes
- This command unmounts the Windows image from the
C:\WinPE_amd64\mountdirectory and commits changes made to the image, making the changes permanent.
1 |
Dism /Unmount-Image /MountDir:"C:\WinPE_amd64\mount" /commit |
- Sample output
1 2 3 4 5 6 7 8 9 10 |
C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64>Dism /Unmount-Image /MountDir:"C:\WinPE_amd64\mount" /commit Deployment Image Servicing and Management tool Version: 10.0.25398.1 Saving image [==========================100.0%==========================] Unmounting image [==========================100.0%==========================] The operation completed successfully. |
- After this, if we navigate back to the
C:\WinPE_amd64\mountin the file explorer, we will see it’s empty
Create working files
- The purpose of this command is to create a new set of WinPE files, including bootable media files, specifically for the 64-bit architecture. It prepares the environment for further customization, like adding drivers, applications, or other components necessary for deployment tasks.
- Notice I’m creating this files in a new dir with lowercase letters
C:\winpe-amd64- You can create it anywhere, but stick to this guide if you don’t want to have issues
1 |
copype amd64 C:\winpe-amd64
|
- Sample output
- Notice the
successmessage at the bottom
- Notice the
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64>copype amd64 C:\winpe-amd64 =================================================== Creating Windows PE customization working directory C:\winpe-amd64 =================================================== C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\bootmgr C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\bg-bg\bootmgr.efi.mui C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\Boot\BCD C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\Boot\BCDTemplate C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\Boot\boot.sdi C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\Boot\bootfix.bin C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\Boot\memtest.exe C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\Boot\bg-bg\bootmgr.exe.mui C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\Media\zh-tw\bootmgr.efi.mui 189 File(s) copied 1 file(s) copied. 1 file(s) copied. 1 file(s) copied. Success |
- These were the files created, you can see them in your file explorer
1 2 3 4 5 6 7 8 9 10 11 |
PS C:\winpe-amd64> dir Directory: C:\winpe-amd64 Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 1/12/2024 1:29 PM fwfiles d----- 1/12/2024 1:29 PM media d----- 1/12/2024 1:29 PM mount |
(OPTIONAL) Customize Windows PE
- In this section, you can add programs and stuff to the WinPE image, these are usually tools used for deployment and recovery scenarios. These tools will be available only within the WinPE environment and will not be part of the Windows installation
- If you want to learn more about Windows PE, go and check this
ThioJoevideohttps://youtu.be/HBFukw1hkKY?si=u2lZTlO24R21eN5G
Create bootable media (WinPE ISO)
- The purpose of this command is to take the WinPE files located in the
C:\winpe-amd64directory and compile them into a single ISO file, which can then be used to create bootable media for system deployment, recovery, or troubleshooting tasks.
1 |
MakeWinPEMedia /ISO C:\winpe-amd64 C:\winpe-amd64\winpe-amd64.iso |
- Sample output
1 2 3 4 5 6 |
C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64>MakeWinPEMedia /ISO C:\winpe-amd64 C:\winpe-amd64\winpe-amd64.iso Creating C:\winpe-amd64\winpe-amd64.iso... 100% complete Success |
- Here’s the ISO file that was created, you can see it in the file explorer
1 2 3 4 5 6 7 8 9 10 11 12 |
PS C:\winpe-amd64> dir Directory: C:\winpe-amd64 Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 1/12/2024 1:29 PM fwfiles d----- 1/12/2024 1:29 PM media d----- 1/12/2024 1:29 PM mount -a---- 1/12/2024 1:47 PM 369459200 winpe-amd64.iso |
Copy the WinPE ISO files to the samba server
- Now we need to extract all the files in the
winpe-amd64.isowe just created to the netboot.xyz container’s x64 directory- This is the samba dir
netbootxyz-assets/win-pe/x64 - The bootloader will look for the files in the x64 dir, so save the files there. I learned this the hard way. See below how to do it.
- This is the samba dir
- Go to the
C:\winpe-amd64directory - Right click the
winpe-amd64.isoand clickshow more options - 7zip - extract files - Now in the 7zip extraction menu navigate to the samba dir
netbootxyz-assets/win-pe/x64- In case it’s checked, unchecked the checkbox below so it doesn’t create a new dir, but it instead just extracts the files
- With this we will have the ISO files, but extracted in our samba drive
- If you want to, you can create a backup of the
winpe-amd64.isoin the samba directoryiso-files
Configure netboot to point to the WinPE files
- In the netboot.xyz web GUI
http://192.168.88.135:3029 - Go to
Menuson the top - Update
boot.cfgunder Media Locations for Licensed Distrosset win_base_url http://192.168.88.135:8083/win-pe- This is the IP of our linux VM, notice port used is 8083
- Hit
Save Configon the top right
Configure custom options in windows.ipxe
- Now we need to configure the windows.ipxe file, this will instruct the installation to connect to the samba server to get the Windows installation ISO and will also disable the secure boot check
- If we don’t disable secure boot, windows cannot be installed over using netboot.xyz
- To understand why, go and see (CAVEAT) Do I need secure boot?
- Click on the
windows.ipxefile- We will change this section right below the line
kernel http://${boot_domain}/wimboot
- We will change this section right below the line
1 2 3 4 5 6 7 |
# Custom configs start initrd ${win_base_url}/configs/auto.bat auto.bat initrd ${win_base_url}/configs/winpeshl.ini winpeshl.ini initrd ${win_base_url}/configs/config.ini config.ini # Custom config ends |
Configure samba server and password in winpe files
- During the network install, WinPE will need access to the samba directory we configured, so we need to configure our samba
serverandpasswordin the file below - You can edit this file from within the samba server itself, as it has the right permissions, but I prefer to do it via Linux, as its way faster and I don’t have to deal with notepad or whatever text editor is on Windows
- If you’re editing it on windows, do it in the samba drive
netbootxyz-assets/win-pe/configs/config
- If you’re doing it from the Linux VM, edit this file
~/github/containerdata-public/docker/samba/mnt/isos/netbootxyz-assets/win-pe/configs/config.ini
Configure autoattend.xml file
- I use this file to perform an unattended installation, what does this mean?
- I configured mine to just ask you for the partition in which you want to install windows, although, you can automate that as well
- But besides that, it also:
- Skips the End User License Agreement (EULA) page.
- Omits the OEM registration screen during setup.
- Prevents display of prompts to log in with or create an online account.
- Skips the wireless network setup in the Out-of-Box Experience (OOBE).
- Sets the network location to ‘Home’
- Skips user-specific Out-of-Box Experience settings.
- Skips machine-specific Out-of-Box Experience settings.
- Sets Windows Update to automatically download and install updates.
- I generated the file on this website
https://www.windowsafg.com- You can generate your there with your desired options
- Or you can use the file that I included, just make whatever changes you need
- I’ll use the file I included, but will make the following changes:
linkarzu— replace with the desired user nameLinkarzu-org— replace with desired organization nameLINKARZU-PC— replace with desired computer name<ProductKey>— I’m using a generic windows key here- This key WILL NOT ACTIVATE WINDOWS, it’s just used so you can install it, but once installed, you will need to enter your original purchased, and legally obtained Windows activation key.
- In this file, you could also include custom scripts or installation commands to install apps or configure Windows to your liking, but that’s out of the scope of this video
Disable secure boot
- Since we disabled the secure boot checks in the WinPE image, we don’t have to disable secure boot on our machine, for windows to boot properly. At least that worked in my case, but if it does not work in your case, disable
secure boot- Secure boot is disabled in the BIOS/UEFI menu, google how to do it
- In my case, I didn’t have to disable secure boot when installing on a VM running on XCP-ng
Install windows via netboot.xyz
- Before starting the installation process, I’ll restart my samba container I was having an issue in which the samba password was right, but it was not connecting, it fixed until I restarted the samba container
- Run this on your linux VM where the container is running
- We already configured the router, but remember that it is set to use the
netboot.xyz-snp.efiboot file type - The
netboot.xyz.efiboot file didn’t work for me on my laptop nor VMs when using UEFI, but it may work for you, so try and see which one works - NOTE: If you’re on a physical computer, make sure you have it connected with an ethernet cable, as the network install happens via ethernet
- If on a computer, at least on my case, I had to press f9 and select the
boot from the networkoption- This will initiate the network boot process, otherwise your HDD/SDD/USB will be used as the boot option
- In the netboot.xyz menu, select
Windowsunder DistributionsLoad Microsoft Windows Installer
- After copying the windows files the computer will reboot for the first time
- So when the VM reboots after the installation and is on the PXE menu again turn it off
- Then disable network boot
- If you’re working with a physical computer, same thing, change the boot order so it starts with the drive
- If you don’t do this, it will keep trying to boot from the network, but since the files are already copied to the HDD/SSD, we need to start from the drive instead of the network
- After you change it to start from the drive instead of the network, it will finish the installation process, if you used my
autoattend.xmlfile it will ask you to change the password when - Add a password for the user and that’s it, you successfully installed Windows 11 over the network
If you like my content, and want to support me
- If you want to share a tip, you can donate here
- I recently was laid off, so if you know about any SRE related roles, please let me know
Discord server
- My discord server is now open to the public, feel free to join and hang out with others
- join the discord server in this link
- Twitter (or “X”)
- TikTok
- GitHub
- Threads
- OnlyFans 🍆
- YouTube (subscribe MF, subscribe)
- Ko-Fi
All links in the video description
- The following links will be in the YouTube video description:
- Each one of the videos shown
- A link to this blogpost
How do you manage your passwords?
- I’ve tried many different password managers in the past, I’ve switched from
LastPasstoDashlaneand finally ended up in1password - You want to find out why? More info in my article:
- How I use 1password to keep all my accounts safe
- If you want to support me in keeping this blogpost ad free, start your 1password 14 day free trial by clicking the image below
Варианты загрузки компьютера
Для низкоуровневого обслуживания компьютеров (работа с разделами и образами жесткого диска, восстановление данных, борьба с вирусами и кибератаками и т.п.), а также для установки операционной системы можно использовать загрузочные USB флешки, например: Ubuntu Live, Clonezilla, SergeyStrelec.
Однако, у этого решения есть недостатки:
- инструментов и дистрибутивов разных много, поэтому приходится хранить много флешек или постоянно их перезаписывать, в том числе при обновлении версии утилиты;
- компьютер может не поддерживать загрузку с флешки или она может быть запрещена;
- можно элементарно забыть взять флешку в командировку;
- большой парк компьютеров обслуживать флешкой намного медленнее, чем по сети.
Кроме того, при использовании Gigabit Ethernet, загрузка по сети быстрее.
Под Windows для загрузки по сети я обычно использовал tftpd32 — удобная портабельная маленькая, но достаточно мощная программа с открытыми исходниками. Однако я в последнее время стараюсь уходить от Windows, поэтому решил разобраться, как решить эту задачу под Linux.
Поиск выдает довольно много вариантов, но можно выделить netboot.xyz как зрелое решение с хорошей поддержкой. Уникальным преимуществом этого проекта является то, что там собраны и обновляются образы многих дистрибутивов ОС и утилит, которые можно загружать прямо из интернета или выкачать для кеширования на локальный диск. Есть загрузочное меню, которое можно редактировать и наращивать, в том числе через Git. Можно загружать ISO образы, однако не все: например, SergeyStrelec не пошел.
Самый удобный способ установки netboot.xyz — с помощью контейнера Docker. Это дает такие преимущества:
- быстрая и удобная установка и конфигурация;
- можно быстро запустить/остановить и удалить ПО;
- высокая надежность и безопасность — изоляция от основной ОС, благодаря виртуализации, при этом используемые ресурсы (место на диске, память, процессор) намного меньше, чем при использовании виртуальной машины.
Docker контейнеров для netboot.xyz также существует несколько, наиболее зрелым представляется этот. Также вот его дополнительное описание.
Особенность этого контейнера — отсутствие своего DHCP сервера. Если DHCP уже есть в сети, например, в роутере, то следует использовать его во избежание конфликтов. Если же роутера нет, или не получается его настроить, то можно установить DHCP сервер на компьютере также с помощью Docker контейнера, например этого. Либо использовать другой контейнер c netbootxyz со встроенным DHCP, например этот. Либо использовать контейнер, в котором реализован PXE и DHCP без netboot.xyz, например этот.
Установка и настройка netbootxyz
Однако мы рассмотрим тут контейнер linuxserver/netbootxyz. Здесь приведены основные выжимки из официальной документации, а также кое-что, чего там не хватало.
Установка Docker для Ubuntu. Ставим вариант docker.io из официального репозитория Ubuntu — ранее он считался устаревшим, но недавно возобновилась его поддержка. Соответственно, другие варианты удаляем (если они не были установлены, не важно):
sudo apt-get update sudo apt-get remove docker docker-engine docker.io docker-ce docker-ce-cli containerd.io sudo apt install docker.io docker-compose sudo groupadd docker sudo usermod -aG docker $USER newgrp docker
Существует несколько способов запуска этого контейнера, самый удобный — с помощью docker-compose. Следует создать файл docker-compose.yml:
version: "2"
services:
netbootxyz:
image: linuxserver/netbootxyz
container_name: netbootxyz
environment:
- PUID=1000
- PGID=1000
volumes:
- ./netbootxyz-config:/config
- /media/d1/Dist/OS/netbootxyz:/assets # put here the path for the local downloaded distributives
ports:
- 3000:3000
- 69:69/udp
- 8080:80
restart: unless-stopped
Далее отредактируйте в docker-compose.yml путь /media/d1/Dist/OS/netbootxyz — там будут храниться скачанные образы. Для удобства запуска можно еще создать файл start.sh в той же директории (закомментированные строки — для установки Windows 10):
#!/bin/bash #mkdir /media/d1/Dist/OS/netbootxyz/win #sudo mount -o loop /media/d1/Dist/OS/Windows10_orig/WIN10_64_En.ISO /media/d1/Dist/OS/netbootxyz/win docker-compose up --build #sudo umount /media/d1/Dist/OS/netbootxyz/win
Для запуска контейнера — sh start.sh в терминале, для остановки — Ctrl-C.
Далее следует настроить DHCP сервер в роутере. Например, для OpenWRT (в нашем примере адрес компьютера с запущенным контейнером — 192.168.1.2):
Network -> DHCP and DNS -> TFTP Settings -> Enable -> Network boot image:
для Legacy BIOS:
netboot.xyz.kpxe,,192.168.1.2
для UEFI:
netboot.xyz.efi,,192.168.1.2
Уже можно пробовать загружаться по сети. Образы будут выкачиваться из интернета каждый раз при загрузке.
Для убыстрения загрузки, а также для работы без интернета (что часто бывает на промышленных объектах) следует закешировать образы на локальном диске. Для этого нужно открыть в браузере веб-интерфейс программы (http://localhost:3000/) и перейти по ссылке Local Assets в верхнем меню.
Я себе решил выкачать следующие утилиты (заняло 7.3 Гб):
Kali Live KDE Ubuntu 19.10 Gnome/Default Kaspersky Rescue Disk DBAN 4MLinux Breakin Rescatux GParted Live GRML Clonezilla Debian stable
Также нужно отредактировать файлы меню, которые находятся в поддиректории ./netbootxyz-config/menus :
4mlinux.ipxe clonezilla.ipxe dban.ipxe gparted.ipxe kaspersky.ipxe live-kali.ipxe live-ubuntu.ipxe utils-efi.ipxe utils-pcbios.ipxe
В этих файлах нужно добавить такую строку после заголовка #!ipxe :
set live_endpoint http://192.168.1.2:8080
Установка Windows
Хотя такая опция и предусмотрена в netboot.xyz, но из коробки она не работает. Получилось допилить только для Windows 10 (возможно Windows 8.1 тоже заработает, не пробовал; но Windows 7 не заработал).
Итак, нужно отредактировать файл windows.ipxe:
- добавить после заголовка строку:
set win_base_url http://192.168.1.2:8080/win
- заменить везде по тексту строку “${win_base_url}/${win_arch}” на “${win_base_url}” — в моих дистрибутивах Windows не оказалось подпапки x86/x64.
- заменить строку “kernel http://${boot_domain}/wimboot” на “kernel http://192.168.1.2:8080/wimboot”, а также скопировать файл wimboot из ./netbootxyz-config/menus/ в /media/d1/Dist/OS/netbootxyz/ — это нужно, чтобы было можно загружаться без интернета.
Далее нужно расшарить по сети (Samba) директорию /media/d1/Dist/OS/netbootxyz/win , в которую должен быть распакован или замонтирован (до запуска контейнера) образ ISO.
Далее, когда откроется первый экран установщика Windows (там где выбирается язык, формат времени и клавиатура), следует нажать Shift+F10 и выполнить следующие команды (взято отсюда):
wpeinit net use S: \\192.168.1.2\Dist /user:guest password S:\OS\netbootxyz\win\sources\setup.exe
Загрузка ISO образов
В меню netboot.xyz есть пункт “Test Distribution ISO”. Чтобы эта функция работала без интернета, нужно скопировать файл memdisk из ./netbootxyz-config/menus/ в /media/d1/Dist/OS/netbootxyz/ и отредактировать файл ./netbootxyz-config/menus/boot.cfg :
заменить
set memdisk http://${boot_domain}/memdisk
на
set memdisk http://192.168.1.2:8080/memdisk
netboot.xyz
Your favorite operating systems in one place!
Bootloader Downloads
Combined Legacy and UEFI iPXE Bootloaders
| Type | Bootloader | Description |
|---|---|---|
| ISO | netboot.xyz.iso | Used for CD/DVD, Virtual CDs, DRAC/iLO, VMware, Virtual Box |
| USB | netboot.xyz.img | Used for creation of USB Keys |
Legacy (PCBIOS) iPXE Bootloaders
| Type | Bootloader | Description |
|---|---|---|
| Kernel | netboot.xyz.lkrn | Used for booting from GRUB/EXTLINUX |
| Floppy | netboot.xyz.dsk | Virtual floppy disk for DRAC/iLO, VMware, Virtual Box, etc |
| Padded Floppy | netboot.xyz.pdsk | Padded Virtual floppy disk for DRAC/iLO, VMware, Virtual Box, etc |
| DHCP | netboot.xyz.kpxe | DHCP boot image file, uses built-in iPXE NIC drivers |
| DHCP-undionly | netboot.xyz-undionly.kpxe | DHCP boot image file, use if you have NIC issues |
UEFI iPXE Bootloaders
| Type | Bootloader | Description |
|---|---|---|
| DHCP | netboot.xyz.efi | DHCP boot image file, uses built-in iPXE NIC drivers |
| DHCP-snp | netboot.xyz-snp.efi | EFI w/ Simple Network Protocol, attempts to boot all net devices |
| DHCP-snponly | netboot.xyz-snponly.efi | EFI w/ Simple Network Protocol, only boots from device chained from |
ARM64 iPXE Bootloaders
| Type | Bootloader | Description |
|---|---|---|
| DHCP | netboot.xyz-arm64.efi | DHCP boot image file, uses built-in iPXE NIC drivers |
| DHCP-snp | netboot.xyz-arm64-snp.efi | EFI w/ Simple Network Protocol, attempts to boot all net devices |
| DHCP-snponly | netboot.xyz-arm64-snponly.efi | EFI w/ Simple Network Protocol, only boots from device chained from |
Raspberry Pi iPXE Bootloaders
| Type | Bootloader | Description |
|---|---|---|
| USB/SD Card | netboot.xyz-rpi4-sdcard.img | Raspberry Pi 4 — USB/SD Card Image |
| DHCP-snp | netboot.xyz-rpi4-snp.efi | Raspberry Pi 4 — EFI Image |
SHA256 checksums are generated during each build of iPXE and are located here. You can also view the scripts that are embedded into the images here.
What is netboot.xyz?
netboot.xyz is a convenient place to boot into any type of operating system or utility disk without the need of having to go spend time retrieving the ISO just to run it. iPXE is used to provide a user friendly menu from within the BIOS that lets you easily choose the operating system you want along with any specific types of versions or bootable flags.
If you already have iPXE up and running on the network, you can hit netboot.xyz at anytime by typing for Legacy (PCBIOS) mode:
chain --autofree http://boot.netboot.xyz/ipxe/netboot.xyz.lkrn
or when in UEFI mode:
chain --autofree http://boot.netboot.xyz/ipxe/netboot.xyz.efi
You can also load using HTTPS, but by default builds of iPXE do not have HTTPS support compiled in. This will load the appropriate netboot.xyz kernel with all of the proper options enabled.
Documentation
See netboot.xyz for all documentation. Some links to get started with are:
- Downloads
- Self Hosting
- Booting Methods
- FAQ
- Blog
If you’d like to contribute to the documentation, the netboot.xyz documentation is located at netboot.xyz-docs.
Self Hosting netboot.xyz
For those users who want to deploy their own netboot.xyz environment, you can leverage the same scripts that are used to deploy the hosted environment. The source scripts are all Ansible templates and can be generated and customized to your preference.
Please see the self-hosting docs for more information but in short:
Deploying using Ansible
To generate, run:
ansible-playbook site.yml
The build output will be located in /var/www/html by default.
Deploying with Docker
docker build -t localbuild --platform=linux/amd64 -f Dockerfile .
docker run --rm -it --platform=linux/amd64 -v $(pwd):/buildout localbuild
The build output will be in the generated folder buildout
Local Overrides
Ansible will handle source generation as well as iPXE disk generation with your settings. It will generate Legacy (PCBIOS) and UEFI iPXE disks that can be used to load into your netboot.xyz environment. If you want to override the defaults, you can put overrides in user_overrides.yml. See user_overrides.yml for examples.
Using the overrides file, you can override all of the settings from the defaults/main.yml so that you can easily change the boot mirror URLs when the menus are rendered. If you prefer to do this after the fact, you can also edit the boot.cfg to make changes, but keep in mind those changes will not be saved when you redeploy the menu.
Self Hosted Custom Options
In addition to being able to host netboot.xyz locally, you can also create your own custom templates for custom menus within netboot.xyz. Please see Custom User Menus for more information.
What Operating Systems are currently available on netboot.xyz?
Operating Systems
| Name | URL | Installer Kernel | Live OS |
|---|---|---|---|
| AlmaLinux | https://almalinux.org/ | Yes | No |
| Alpine Linux | https://alpinelinux.org | Yes | No |
| Arch Linux | https://www.archlinux.org | Yes | No |
| Backbox | https://www.backbox.org | No | Yes |
| BlackArch Linux | https://blackarch.org | Yes | Yes |
| Bluestar Linux | https://sourceforge.net/projects/bluestarlinux | No | Yes |
| Bodhi Linux | https://www.bodhilinux.com | No | Yes |
| CentOS | https://centos.org | Yes | No |
| Fedora CoreOS | https://getfedora.org/en/coreos?stream=stable | Yes | No |
| Debian | https://debian.org | Yes | Yes |
| Deepin | https://www.deepin.org | No | Yes |
| Devuan | https://devuan.org | Yes | No |
| Elementary OS | https://elementary.io | No | Yes |
| EndeavourOS | https://endeavouros.com | No | Yes |
| Fatdog64 | https://distro.ibiblio.org/fatdog/web/ | No | Yes |
| Fedora | https://fedoraproject.org | Yes | Yes |
| Feren OS | https://ferenos.weebly.com/ | Yes | No |
| Flatcar Container Linux | https://www.flatcar.org | Yes | No |
| FreeBSD | https://freebsd.org | Yes, disk image | No |
| FreeDOS | https://www.freedos.org | ISO — Memdisk | No |
| Garuda Linux | https://garudalinux.org/ | No | Yes |
| Gentoo | https://gentoo.org | Yes | Yes |
| Harvester | https://harvesterhci.io | Yes | No |
| hrmpf | https://github.com/leahneukirchen/hrmpf/ | No | Yes |
| IPFire | https://www.ipfire.org | Yes | No |
| K3OS | https://k3os.io/ | Yes | Yes |
| Kairos | https://kairos.io/ | Yes | No |
| Kali Linux | https://www.kali.org | Yes | Yes |
| KDE Neon | https://neon.kde.org | No | Yes |
| Kodachi | https://www.digi77.com/linux-kodachi/ | No | Yes |
| Linux Lite | https://www.linuxliteos.com | No | Yes |
| LXLE | https://lxle.net/ | No | Yes |
| Mageia | https://www.mageia.org | Yes | No |
| Manjaro | https://manjaro.org | No | Yes |
| Mint | https://linuxmint.com | No | Yes |
| Microsoft Windows | https://www.microsoft.com | User supplied media | No |
| MirOS | http://www.mirbsd.org | Yes | No |
| Nitrux | https://nxos.org/ | No | Yes |
| NixOS | https://nixos.org | Yes | No |
| OpenBSD | https://openbsd.org | Yes | No |
| openEuler | https://openeuler.org | Yes | No |
| openSUSE | https://opensuse.org | Yes | No |
| Oracle Linux | https://www.oracle.com/linux/ | Yes | Installer |
| Parrot Security | https://www.parrotsec.org | No | Yes |
| Peppermint | https://peppermintos.com | No | Yes |
| Pop OS | https://system76.com/pop | No | Yes |
| Proxmox Open Source Products | https://www.proxmox.com/ | Yes | No |
| Q4OS | https://q4os.org | No | Yes |
| Raizo | https://sourceforge.net/projects/live-raizo/ | No | Yes |
| Red Hat Enterprise Linux | https://www.redhat.com | User supplied media | No |
| Regolith | https://regolith-linux.org | No | Yes |
| Rocky Linux | https://rockylinux.org/ | Yes | No |
| Septor | https://septor.sourceforge.io | No | Yes |
| Slackware | https://www.slackware.com | Yes | No |
| SmartOS | https://www.smartos.org/ | Yes | No |
| SparkyLinux | https://sparkylinux.org/ | No | Yes |
| Tails | https://tails.net | No | Yes |
| Talos | https://www.talos.dev/ | Yes | No |
| Tiny Core Linux | https://tinycorelinux.net | Yes | Yes |
| Ubuntu | https://www.ubuntu.com | Yes | Yes |
| VMware | https://www.vmware.com | User supplied media | No |
| VMware Photon | https://vmware.github.io/photon/ | Yes | No |
| Vanilla OS | https://vanillaos.org | No | Yes |
| Voyager | https://voyagerlive.org | No | Yes |
| VyOS | https://vyos.io | Yes | No |
| Zen Installer | https://sourceforge.net/projects/revenge-installer | Yes | No |
| Zorin OS | https://zorin.com | No | Yes |
Utilities
| Name | URL | Type |
|---|---|---|
| 4MLinux | https://4mlinux.com/ | Kernel/Initrd |
| Boot Repair CD | https://sourceforge.net/projects/boot-repair-cd/ | LiveCD |
| Breakin | https://www.advancedclustering.com/products/software/breakin/ | Kernel/Initrd |
| CAINE | https://www.caine-live.net/ | LiveCD |
| Clonezilla | https://www.clonezilla.org/ | LiveCD |
| DBAN | https://www.dban.org/ | Kernel |
| GParted | https://gparted.org | LiveCD |
| Grml | https://grml.org | LiveCD |
| Kaspersky Rescue Disk | https://support.kaspersky.com/krd18 | LiveCD |
| Memtest | https://www.memtest.org/ | Kernel |
| MemTest86 Free | https://www.memtest86.com | USB Img |
| Redo Rescue | http://redorescue.com/ | LiveCD |
| Rescatux | https://www.supergrubdisk.org/rescatux/ | LiveCD |
| Rescuezilla | https://rescuezilla.com/ | LiveCD |
| ShredOS | https://github.com/PartialVolume/shredos.x86_64 | Kernel |
| Super Grub2 Disk | https://www.supergrubdisk.org | ISO — Memdisk |
| System Rescue | https://system-rescue.org/ | LiveCD |
| Ultimate Boot CD | https://www.ultimatebootcd.com | ISO — Memdisk |
| ZFSBootMenu | https://docs.zfsbootmenu.org/ | Kernel |
Stargazers over time
Feedback
Feel free to open up an issue on Github or ping us on Discord. Follow us on Twitter and like us on Facebook!
Install server using netboot.xyz
Last updated on
July 2, 2024
ℹ️
This method of installing your server is for people with enough technical knowledge about servers and operating systems. You can always use our automated installer.
Also, IPMI rights are required. If not present, please request it by opening a support ticket with our team.
What is Netboot.xyz?
netboot.xyz is a powerful tool that allows you to PXE boot various operating system installers or utilities from a single interface over the network. This means you can use one media source for many types of operating systems or tools. The iPXE project is used to provide a user-friendly menu within the BIOS, enabling you to easily choose the operating system you want, including specific versions or bootable flags.
With netboot.xyz, you can:
- Remotely attach the ISO to servers
- Set it up as a rescue option in GRUB
- Configure your home network to boot from it by default
How netboot.xyz Works
netboot.xyz operates by leveraging iPXE, which is an open-source implementation of the PXE network booting protocol. iPXE extends the capabilities of standard PXE by allowing you to:
- Boot from a variety of sources including HTTP, iSCSI, and FTP.
- Use scripts to automate booting processes.
- Boot into a user-friendly menu system that simplifies the selection and booting of various operating systems and tools.
What Operating Systems and Utilities does it offer?
Linux Network Installs
The Linux Network Installs Menu provides a lightweight method for installing operating systems that offer network bootable installers. This method retrieves a minimal set of installer kernels and installs packages as needed, making it a faster installation process since only the necessary packages are downloaded.
Live CD/Distro
The Live CD/Distro Menu includes operating systems that are available as ISO images or Live CD/DVDs. These images boot into memory without modifying the machine’s storage and typically offer an installation option from the live system. netboot.xyz makes these images iPXE friendly by monitoring new version updates, retrieving releases, and modifying the initrd to ensure a consistent boot experience.
Utilities
The Utilities Menu provides access to various tools for tasks like disk cloning, drive wiping, or other rescue operations. It also includes endpoints for testing menus that may be in development.
How to Install Your Bare Metal Server Using netboot.xyz
- Log in to the Bare Metal Management by going to your service in our client area and then clicking
Log in to panel.
- Select your server from the Servers list and click on
Rescue.
- Select Netboot.xyz from the option list and click
Start Rescue. The system will now reboot your server and boot the Netboot.xyz ISO file.

- Open the IPMI console by clicking
Consoleon the top right. If this option is not available, please request it by opening a support ticket with our team.

- In the IPMI Console window, in the Netboot.xyz screen that has been booted, select the desired operating system or utility that you want to install or use. For example, you might select a Linux distribution or a disk cloning tool.
- Follow the on-screen instructions to complete the installation or run the selected tool. This may involve selecting specific installation options or configurations.
- Once the installation is complete, the server will reboot. You can now configure the installed operating system as needed.
⚠️
Possibly, you need to cancel the Rescue boot from the Bare Metal Manager.
Did this answer your question?
Обновлено 05.05.2025
Приветствую!
Недавно я запостил опрос в телеграм и пользователи моего канала проголосовали за)
Сегодня создадим мультизагрузочную флешку для: установки Linux/Windows локально, установки Linux по интернету + обычный раздел под файлы и + шифрованный раздел для чувствительной информации (подключается нативно в Linux и в Windows). И так, поехали.
Присоединяйтесь к нашему каналу: t.me/r4ven_me и чату: t.me/r4ven_me_chat в Telegram .
Предисловие
В чем суть. На usb-флешке будет 4 раздела:
- Загрузочный раздел Ventoy (утилита запуска установочных ISO образов). Почитать, что это такое можно здесь;
- Обычный раздел для хранения ISO образов и обычных файлов;
- Загрузочный раздел netboot.xyz для запуска и установки Linux через интернет. У меня была по данной утилите отдельная статья: netboot.xyz – Установка Linux онлайн с USB флешки;
- Шифрованный раздел bitlocker (работает в Linux и Windows) для хранения конфиденциальной информации. Подробно про Bitlocker тут.
В результате мы получаем флешку на все случаи жизни. Чем больше объем флешки, тем лучше. В данном руководстве будет рассмотрен вариант настройки съемного носителя размером в 32GB.
Сразу предупреждаю, что тестировалось все на системах с UEFI. Настройку в режиме BIOS Lagacy boot не проводил, ввиду отсутствия у меня такой необходимости.
И да, в процессе настройки usb флешки все данные с неё БУДУТ СТЁРТЫ! Поэтому предварительно сохраните с неё все важные файлы, если они там есть. Я вас предупредил:)
Все действия в статье проводились в среде дистрибутива Linux Mint 21.
Подготовка
Для начала скачаем все необходимые утилиты.
Скачивание Ventoy
Переходим на официальный сайт, в раздел загрузок Ventoy, скачиваем версию для Linux:
Нас перекинет на SourceForge, тоже выбираем Linux:
Скачивание netboot.xyz
Также идём на оф. сайт в раздел загрузок netboot.xyz и качаем .img образ:
Скачивание BitLocker Anywhere For Linux
Пару слов прежде чем продолжить.
Bitlocker — это проприетарная технология шифрования дисков от Microsoft. В Linux также существует своя замечательная открытая подсистема для шифрования дисков — Luks. Но т.к. цель статьи — получить универсальное устройство под различные задачи. Чтобы шифрованный раздел нативно работал в файловом менеджере Linux и в проводнике Windows, я принял решение зашифровать этот раздел с помощью Bitlocker. Как это часто бывает, Linux из коробки прекрасно поддерживает открытие шифрованных с помощью Bitlocker разделов. Windows же в свою очередь, поддерживает только свой закрытый Bitlocker, игнорируя Linux.
Крч, ради универсальности пришлось пойти на компромисс)
Продолжим. Bitlocker доступен из коробки только в Pro версии Windows, но есть альтернативный вариант, использовать ПО стороннего разработчика, у которого есть порт для Linux — это BitLocker Anywhere. Программа платная, но с пробным периодом (чего нам достаточно). Ох уж эта проприетарщина..
Скачиваем BitLocker Anywhere с официального сайта:
Теперь все нужные утилиты скачаны, осталось проверить и определить блочное устройство самой usb флешки в нашей системе Linux Mint.
Проверка съёмного носителя
Открываем терминал и выполняем команду вывода списка блочных устройств:
lsblk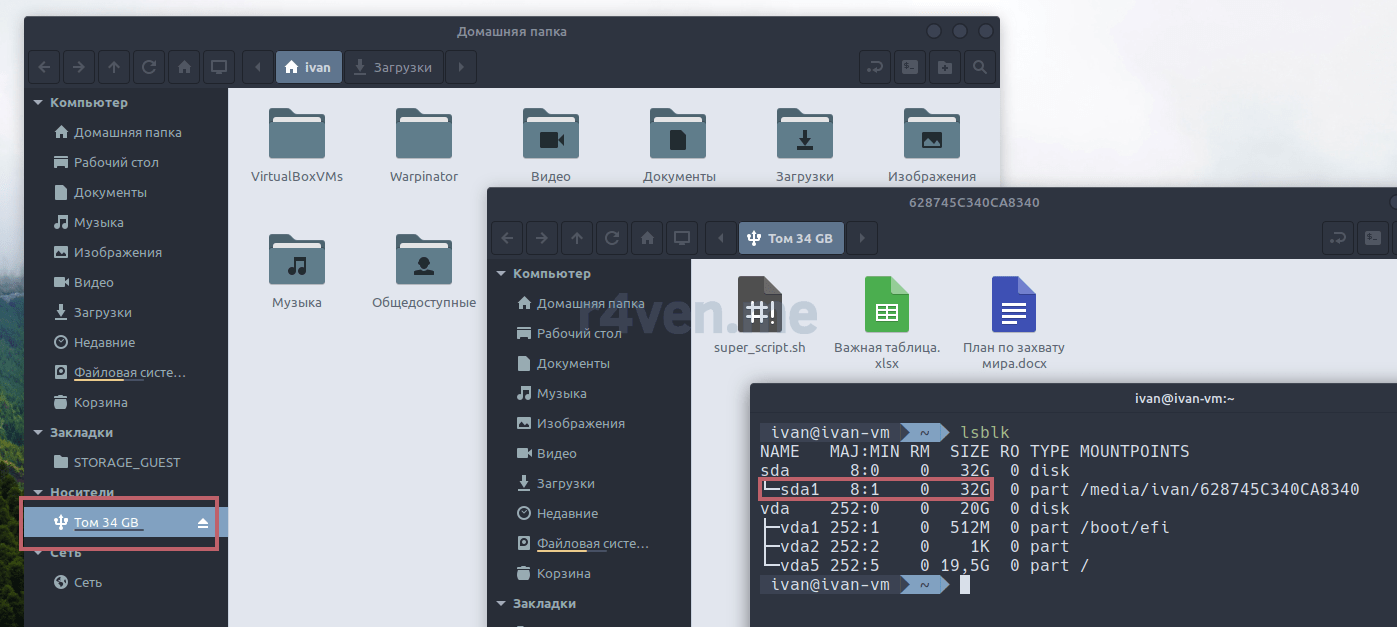
В моём примере это /dev/sda1. У вас скорее всего будет другое имя. Сравниваем с подключенным устройством в файловом менеджере.
Подробную информацию об устройстве можно вывести с помощью утилиты udisksctl. Например, так:
udisksctl info -b /dev/sdaДля справки, udisksctl — консольная утилита управления съемными накопителями в пространстве пользователя.
Приступаем к установке.
Распаковываем архив с Ventoy:
Переходим в распакованный каталог, кликаем ПКМ — открыть терминал. И вводим команду установки:
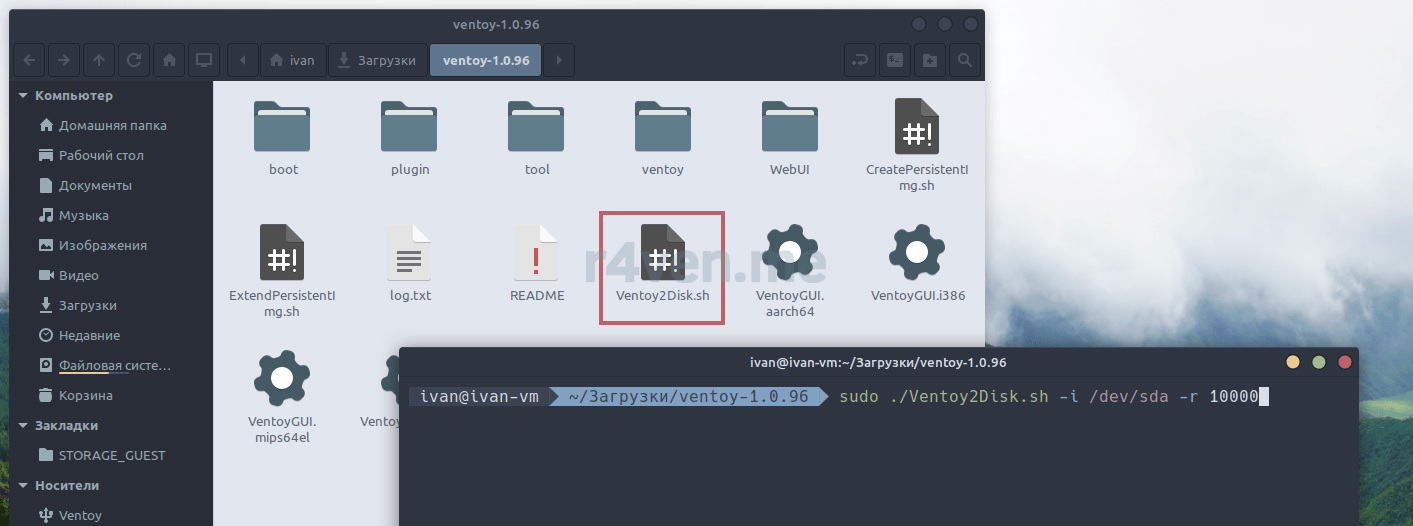
ВНИМАНИЕ!
Команда ниже удалить все данные с указанного устройства. Будьте внимательны, верно укажите имя вашей флешки. Все действия вы выполняете на свой страх и риск.
sudo ./Ventoy2Disk.sh -i /dev/sda -r 10000-i— выполнить установку;-r— объем пространства в мегабайтах, которое будет зарезервировано (не размечено) после форматирования флешки. Это пространство будет использовано для netboot и шифрованного раздела.
Нас дважды попросят подтвердить. Вводим y:
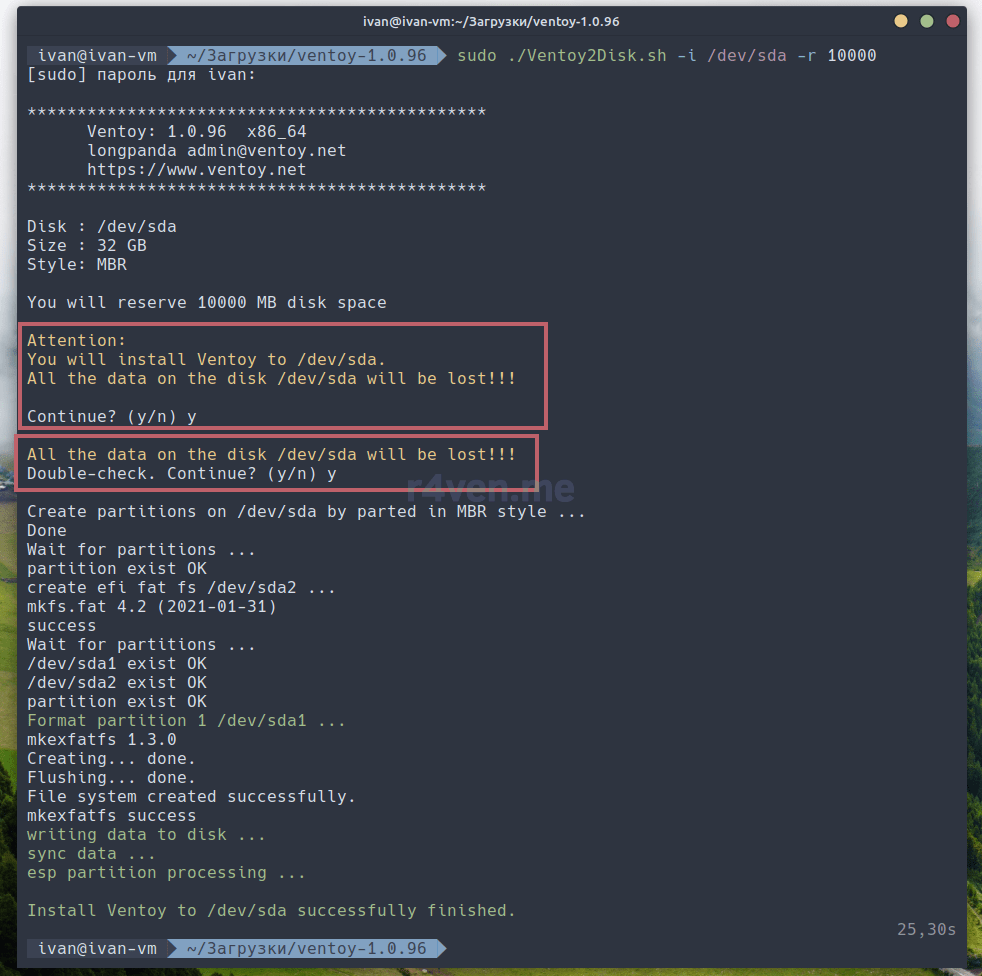
Если результат завершения команды, как на моём скрине, поздравляю. Загрузочный раздел Ventoy и обычный раздел под файлы создан. Если нет, поговорим об этом потом.
Проверяем:
lsblk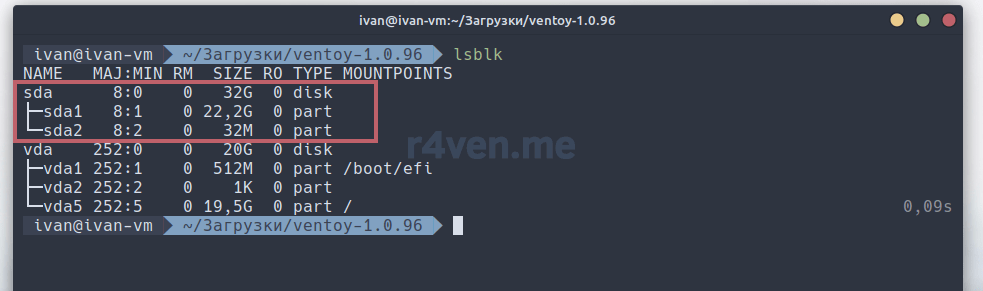
Видим тут 2 раздела: 32МБ и 22ГБ. Оставшееся, неразмеченное место не отображается. Давайте его разметим.
Дополнительная разметка usb диска
Разметку выполним с помощью удобной консольной утилиты cfdisk. Она интерактивная и проста в использовании. Выполняем команду от имени суперпользователя:
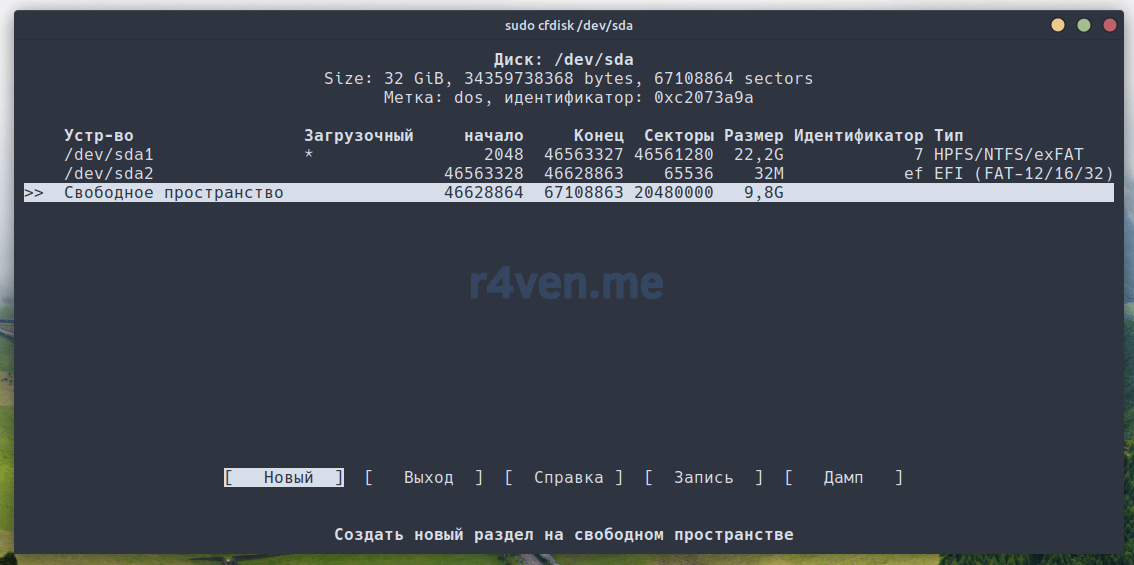
sudo cfdisk /dev/sdaОчень прошу, будьте внимательны указывая имя устройства. Ошибетесь буквой и случайно сотрёте не те данные. Восстановить их будет скорее всего возможно, но гарантий никто не даст.
Стрелкой вниз перемещаем курсор на строку: «Свободное пространство». Это то пространство, которое мы зарезервировали с помощью ключа -r 10000:
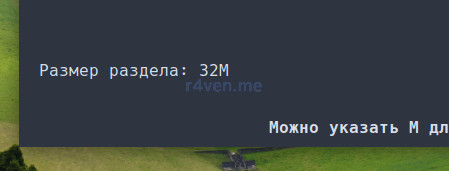
Теперь стрелкой влево выбираем «Новый», нажимаем Enter и вводим размер. Я установил объем, как и у загрузочного раздела Ventoy — 32МБ. Вводим с клавиатуры 32M (M — мегабайты, G — гигабайты):
Вновь Enter. Выбираем «основной» и Enter:
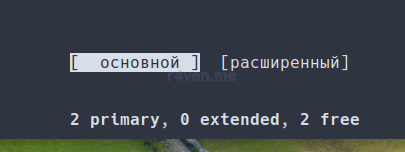
Появится 3-й раздел. Теперь вновь выбираем «Свободное пространство» и аналогично создаем раздел на оставшееся место (выставляется автоматически). Жмём Enter и также выбираем «Основной»:
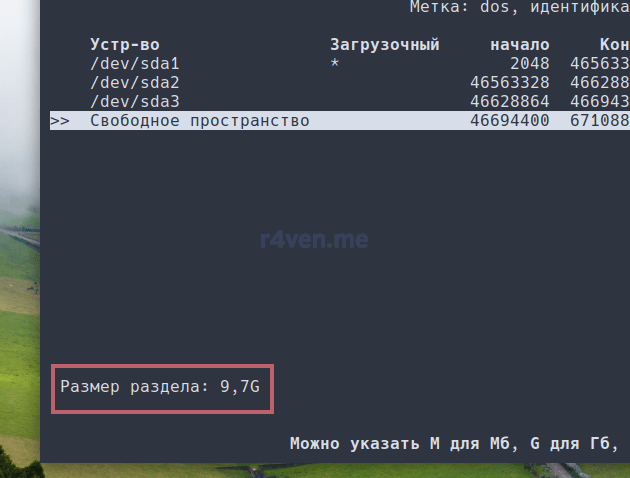
Видим 4 раздела. Теперь необходимо изменить «Тип» последнего, 4-го раздела, чтобы Windows автоматически определяла его в проводнике.
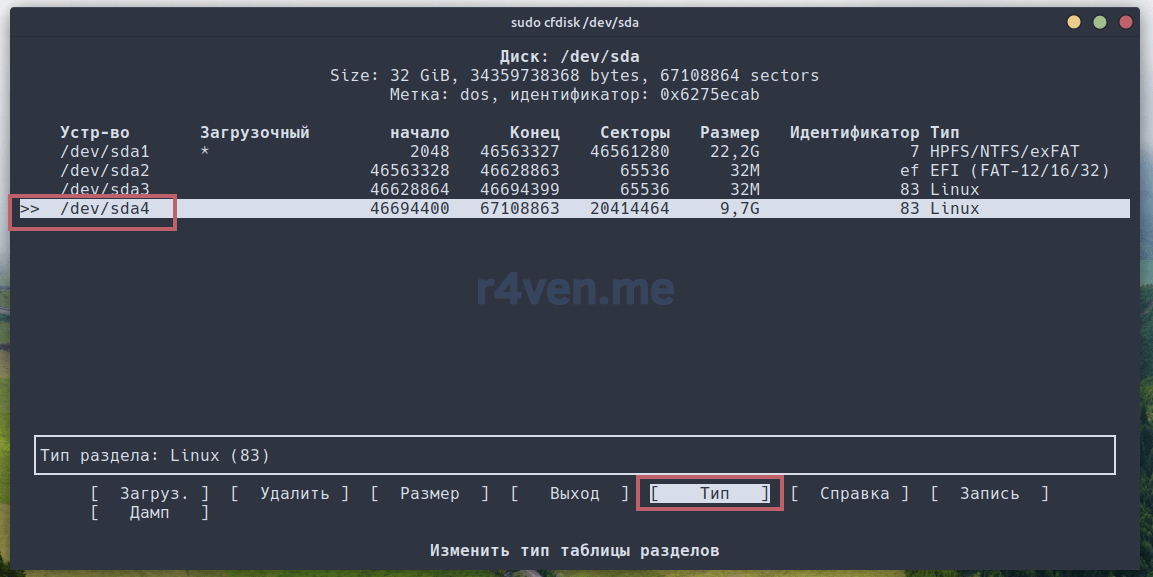
Перемещаем курсор на «Тип» и Enter:
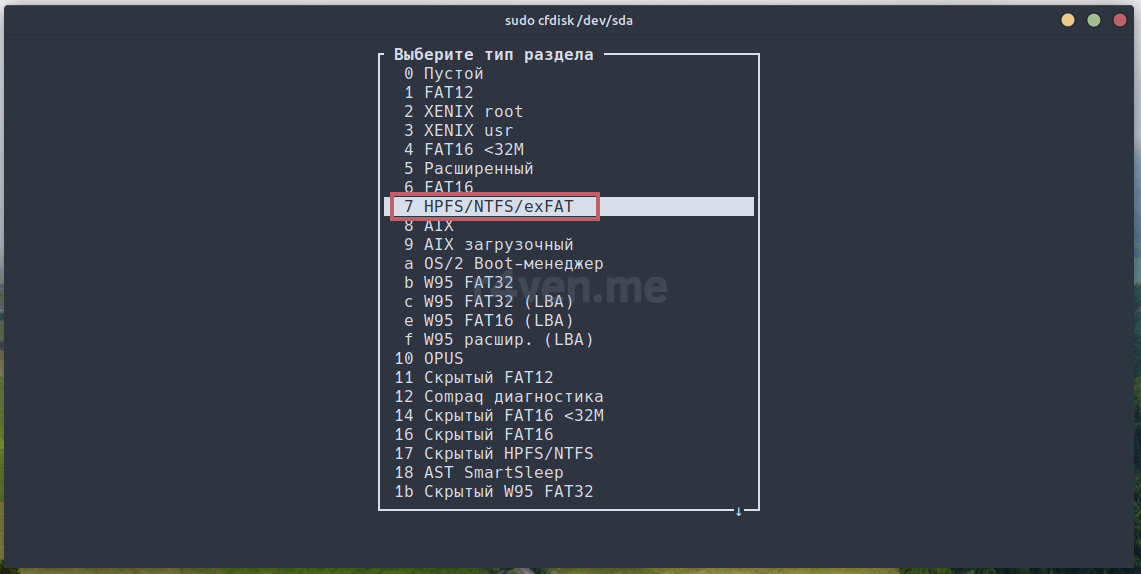
Стрелкой вверх пролистываем до строки 7 HPFS/NTFS/exFAT и Enter:
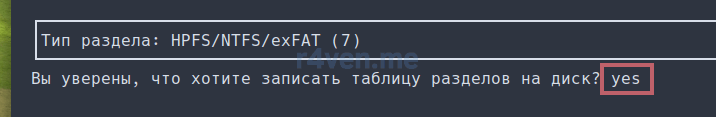
В основном меню видим наши изменения. Картина должна быть примерно, как у меня. Теперь нужно записать изменения на диск. Для этого перемещаем курсор на «Запись» и жмём Enter:
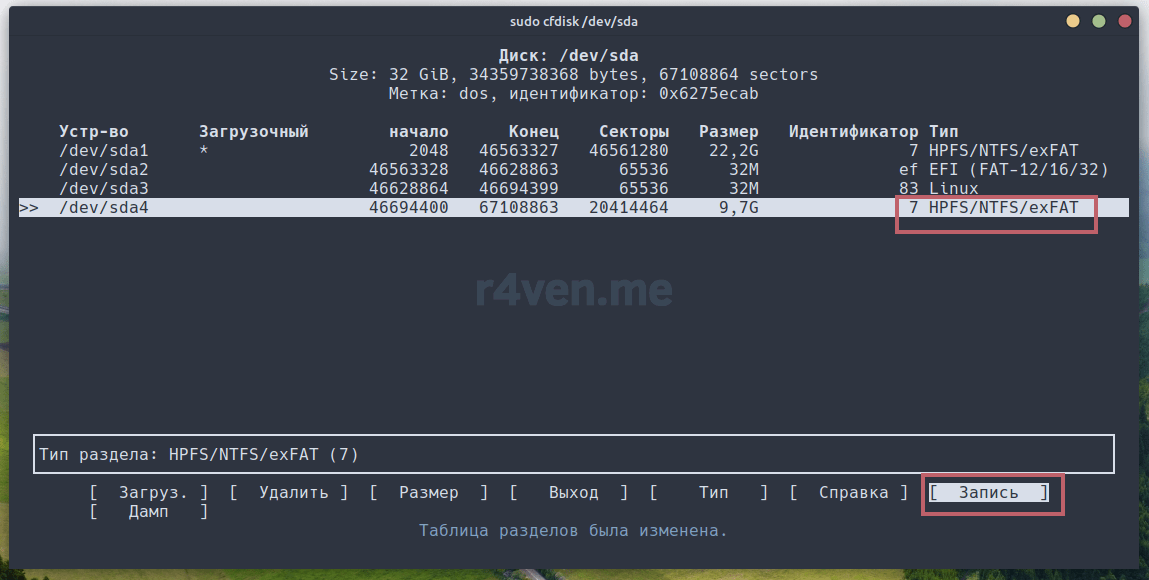
Нас попросят подтвердить вносимые изменения. Вводим yes и Enter:
Обратите внимание, что пока вы не выполните «Запись», изменения на устройство не вносятся. Т.е. до этого момента можно спокойно выйти нажатием клавиши q, если вы что-то разметили не так.
Выходим нажатием q и проверяем:
lsblk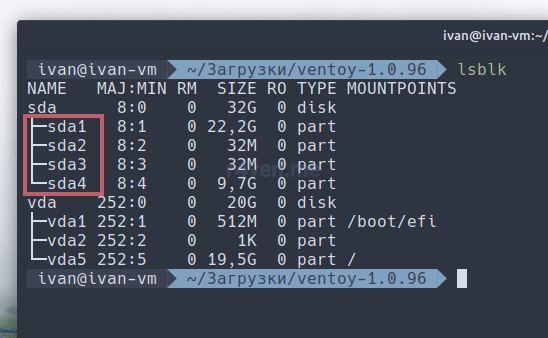
Вот такая картина у нас должна получиться.
Теперь установим netboot.
Создание раздела netboot.xyz
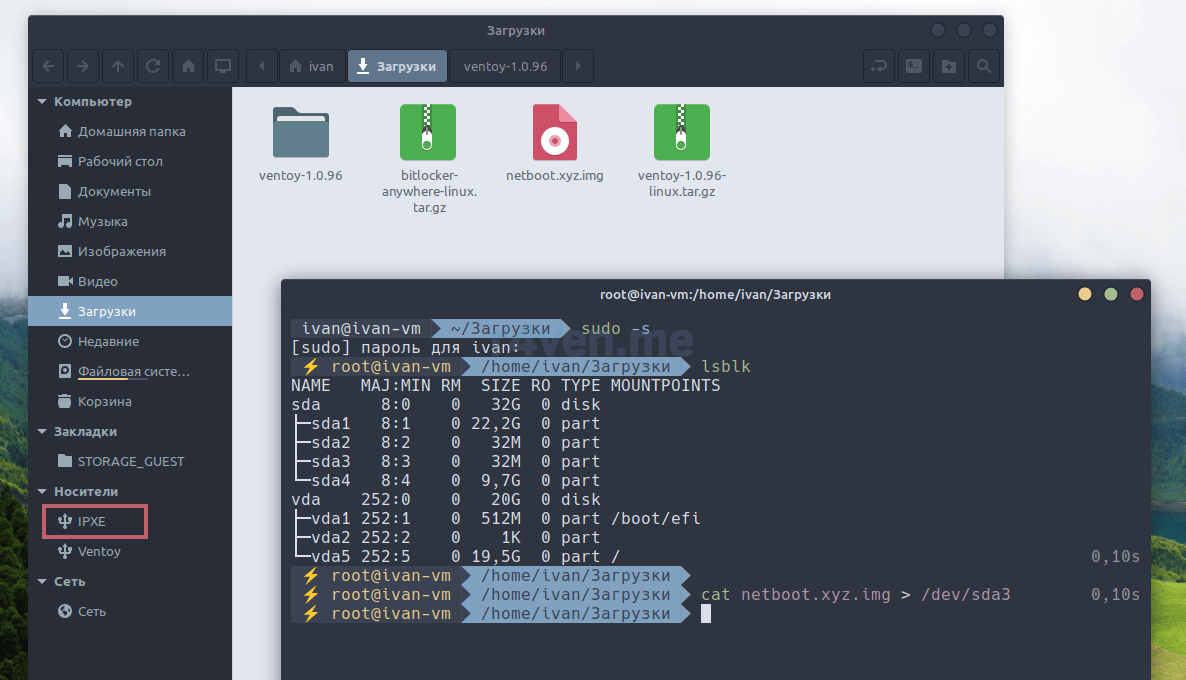
В папке с образом netboot.xyz.img открываем терминал, переходим на пользователя root и записываем образ на 3-й раздел (который 32МБ) командой:
sudo -s
cat netboot.xyz.img > /dev/sda3После выполнения в файловом менеджере должен появится раздел IPXE:
Осталось создать шифрованный раздел.
Создание шифрованного раздела Bitlocker в Linux
Для начала отформатируем наш 4-й раздел (у меня /dev/sda4) в файловой системе FAT утилитой mkfs:
sudo mkfs.vfat /dev/sda4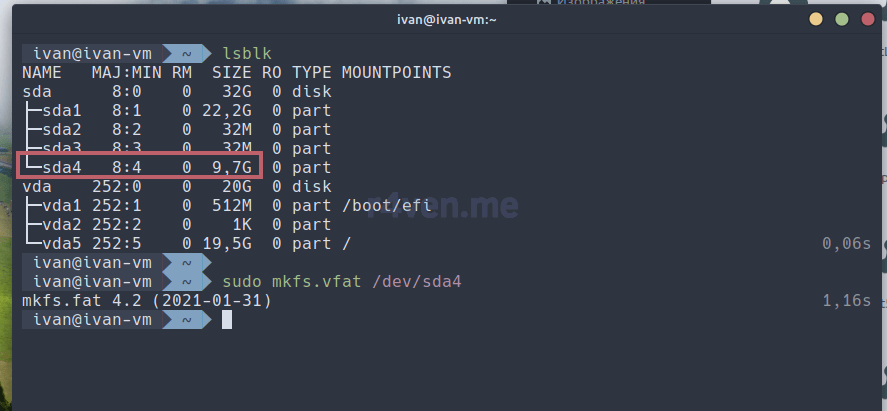
Теперь распаковываем архив с Bitlocker anywhere:
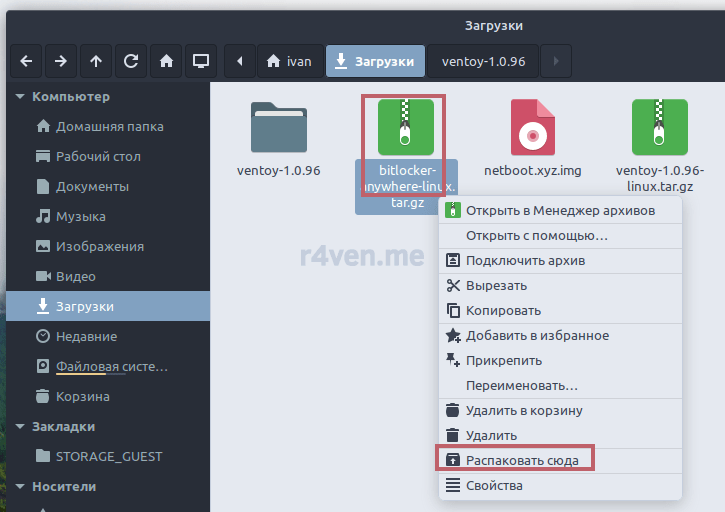
Переходим в каталог ~/Загрузки/bitlocker-anywhere/bin, открываем там терминал и запускаем run.sh
./run.sh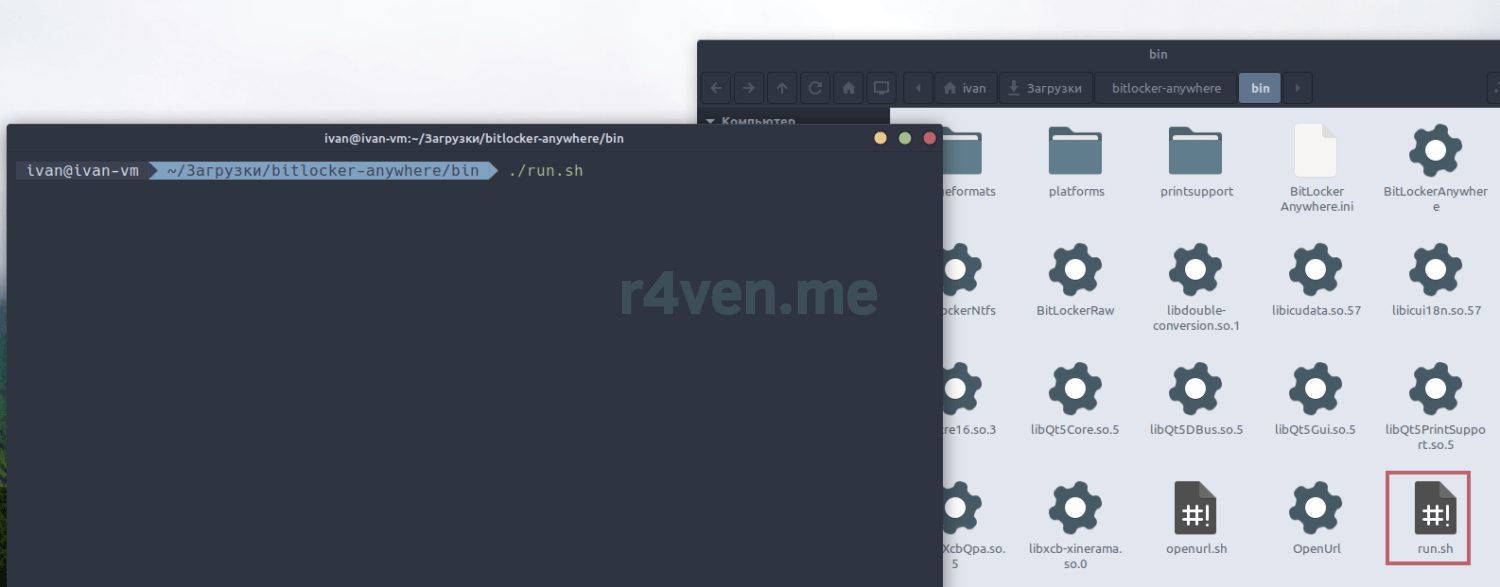
Команда попросит ввести пароль суперпользователя. После откроется графическое окно программы. Кликаем ПКМ по нашему 4-му разделу (у меня /dev/sda4) и нажимаем «Turn on Bitlocker»:
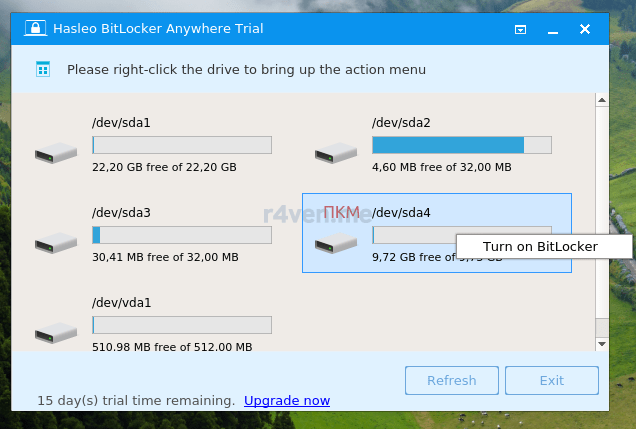
Далее вводим пароль, с помощью которого раздел будет зашифрован (галочки оставляем):
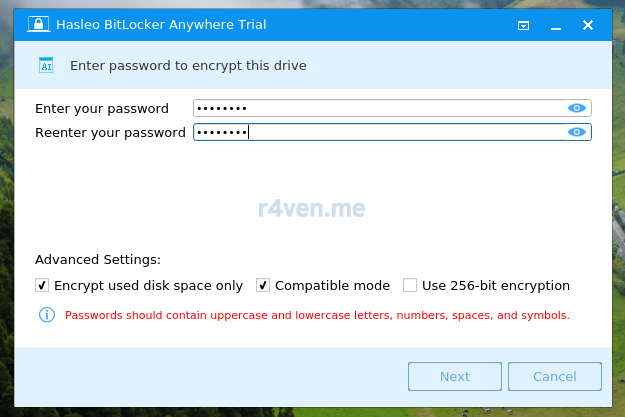
Обязательно запомните его или где-то запишите. Например, в менеджере паролей KeePass, про который у меня есть отдельная статья: Удобное и надёжное хранение паролей – KeePass.
На следующем шаге нам предложат сохранить резервный ключ восстановления, на случай, если мы забудем пароль. Его можно сохранить в файл — так и поступим:
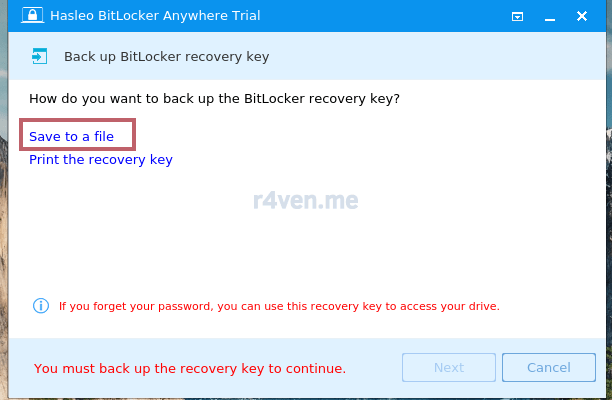
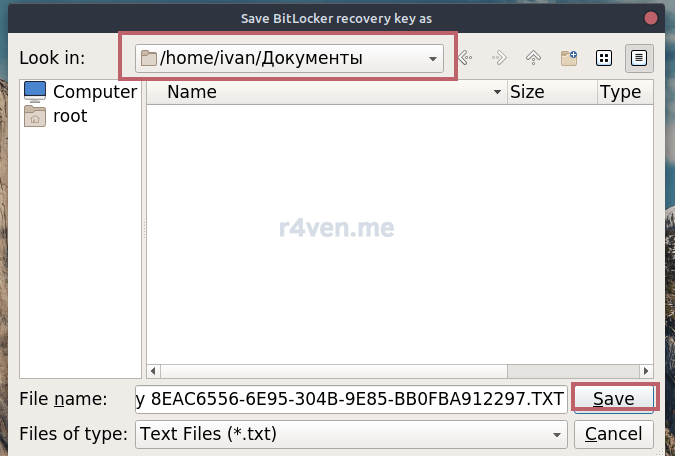
Кликаем «Next» и дожидаемся завершения:
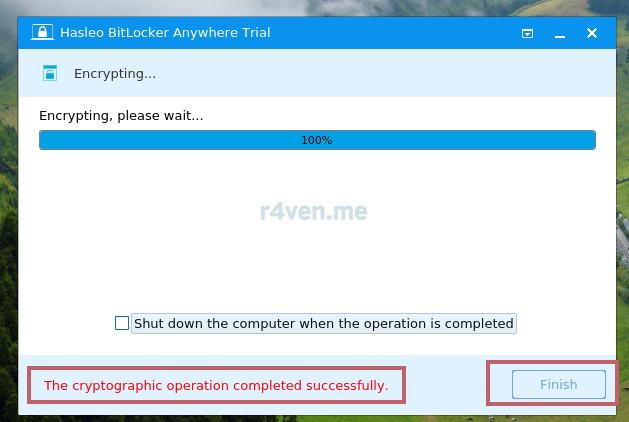
Готово. Слева в проводнике у нас отобразиться «Зашифрованный том». При нажатии на него, появится окно для ввода пароля разблокировки:
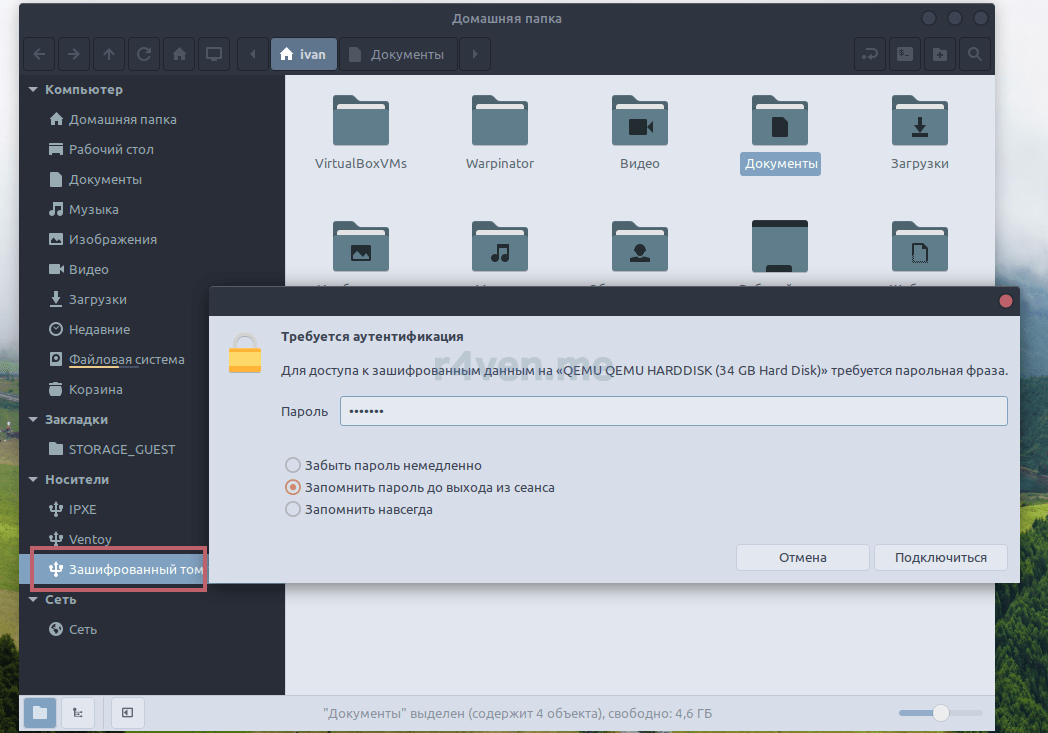
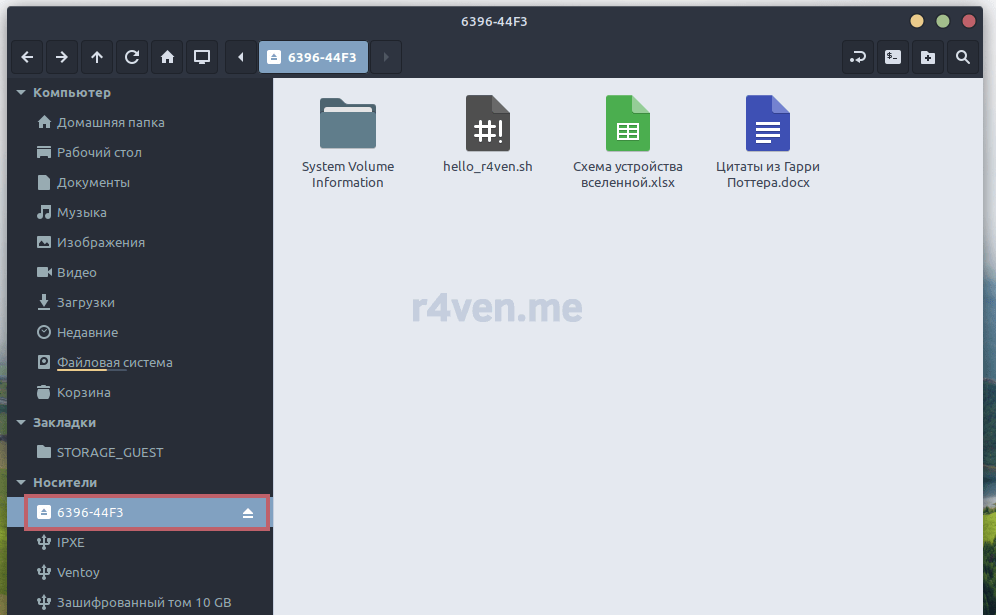
После ввода откроется обычный дисковый раздел, куда можно сохранить важные файлы:
Для безопасного выключения нажмите на разделе ПКМ и выберете один из пунктов:
При подключении флешки в системе Windows в проводнике зашифрованный раздел отобразится так:
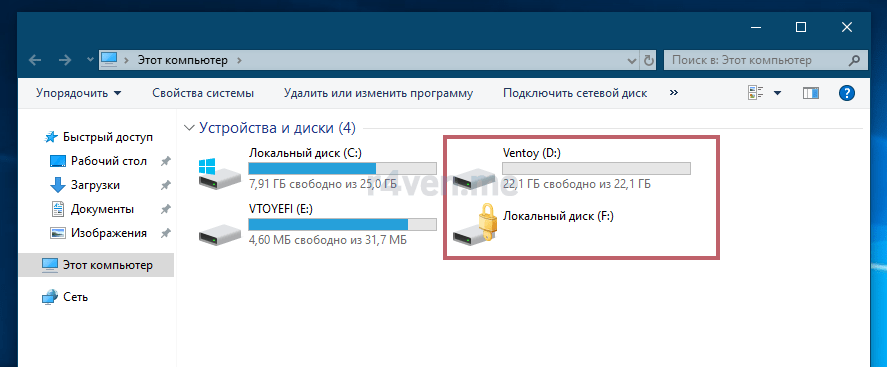
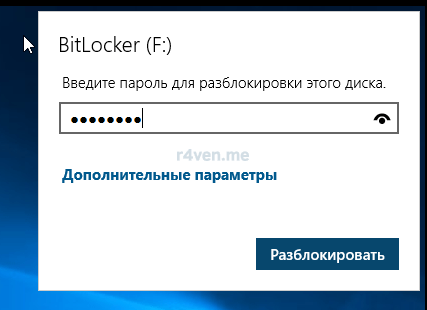
При попытке зайти на него, система запросить у нас пароль:
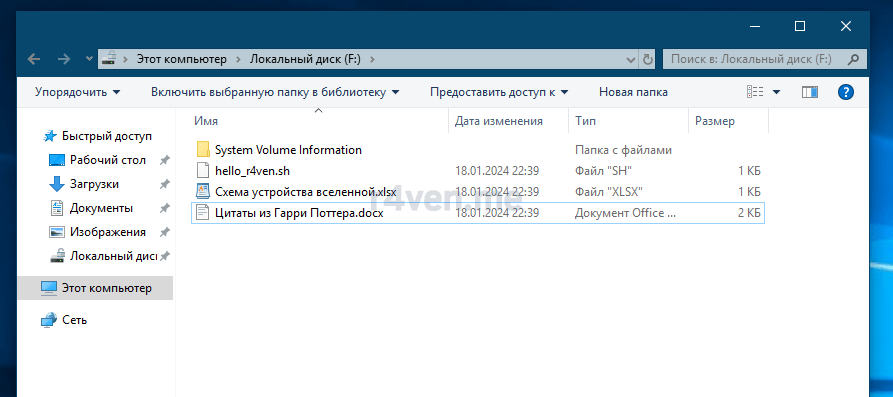
Также расскажу, как подключить шифрованный раздел через терминал Linux.
Для подключения раздел необходимо «открыть» (делается от root), т.е. разблокировать, а затем примонтировать (в данном примере в пространстве пользователя). Делается это двумя командами:
sudo cryptsetup open --type bitlk /dev/sda4 bitlocker
udisksctl mount -b /dev/mapper/bitlocker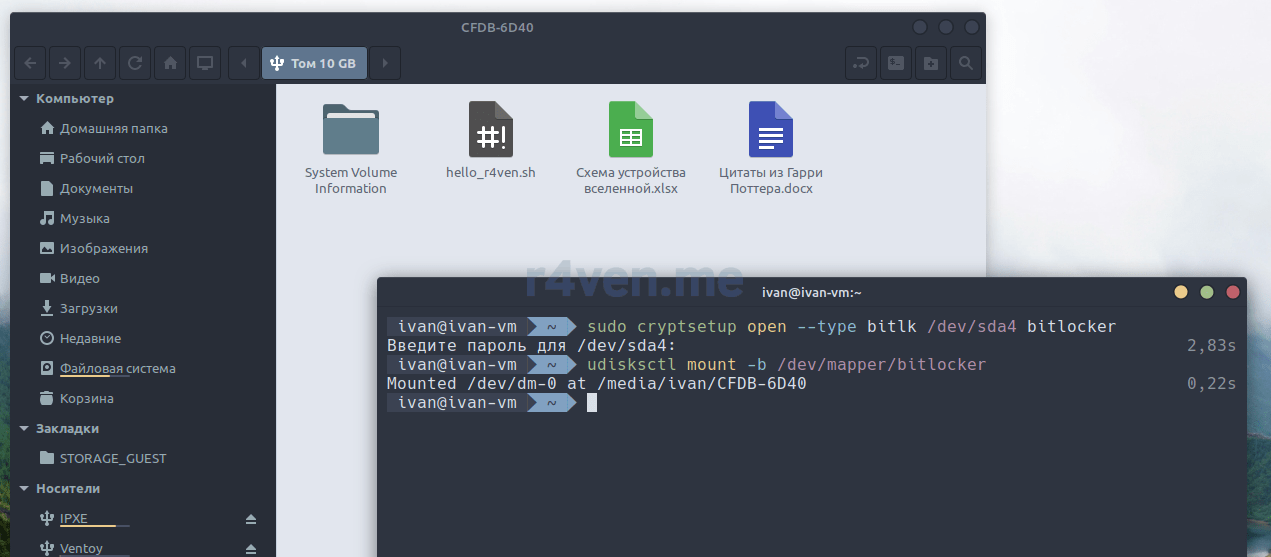
Где:
- cryptsetup — консольная утилита управления подсистемой Luks;
- —type bitlk — явное указание типа раздела виндового Bitlocker;
- bitlocker (в конце команды) — это метка шифрованного устройства, может быть произвольной.
Демонстрация загрузки с флешки-терминатора
Теперь проверим работу нашей мультизагрузочной флешки. Перезагружаем наш компьютер и загружаемся с usb флешки.
Как загрузится с usb носителя я рассказывал в своей статье Установка Linux рядом с Windows:Шаг 4. Загрузка системы с установочного носителя.
В загрузочном меню среди разделов нашего подключенного USB носителя будут доступны 2 пункта (обычно содержащие название/производителя флешки): первый это Ventoy, второй netboot.xyz.
На ноутбуке это может выглядеть так:
В случае с виртуальной машиной на базе QEMU/KVM это выглядит так:
Для демонстрации Ventoy я скачал малюсенький образ интересной ОС, написанной на ассемблере — CalibriOS. Весит образ всего 42.5 МБ. Скачать его можно со страницы загрузок на оф. сайте.
Качаем архив, распаковываем iso образ системы на обычный (ventoy) раздел флешки и загружаемся:

Отлично, всё работает. Теперь запустимся в Netboot.xyz. Также, всё отлично:
Послесловие
Сегодня мы свами создали T-1000 универсальную загрузочную флешку, позволяющую запускать как локальные iso образы, так и выполнять установку Linux по интернету. А также создали два раздела: обычный и шифрованный.
Если у вас возникли трудности, какие-либо вопросы или просто есть желание обсудить тему, то заглядывайте в наш чат в телеграм: @r4ven_me_chat.
Спасибо, что читаете. Удачи в ваших экспериментах!
Материалы по теме
- Ventoy — страница загрузок (EN)
- netboot.xyz — страница загрузок (EN)
- Bitlocker Anywhere — страница загрузок + инструкция (EN)
- Luks — Википедия
- CalibriOS — страница загрузок
