My Windows 10 is 1809. Recently I saw the warning in the Event Viewer.
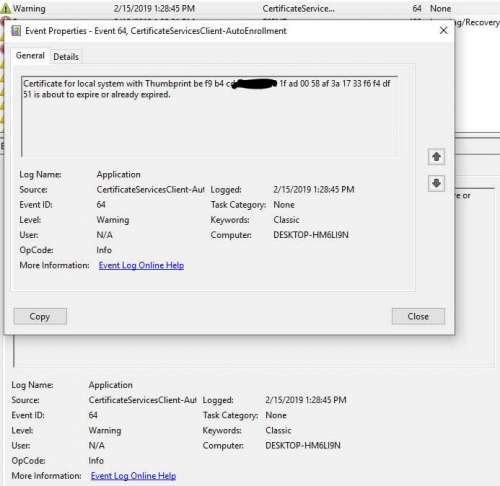
Event 64, CertificateServicesClient-AutoEnrollment
Certificate for local system with Thumbprint be f9 b4 cd 1xxxxxxxx f4 df 51 is about to expire or already expired.
I did the search and find the way to solve this problem.
Before to do the following, I would like to make an announcement. It is just a warning. It will not affect your Windows System.
Right Click Start > Run > type mmc > press ENTER
On the File Menu > Click Add/Remove Snap-in > Click Certificates > Click Add
Click Computer Account > click Next
Click Finish > Click OK
In the console tree, Expand Certificates > Personal > Certificates
You should see the XBL Client IPsec Issuing CA
Right Click on it > All tasks > Export
Follow the Export Wizard > Export it as a x509 (.cer) > Give it a name (example: xbl-client-ipsec.cer)
Right Click on it > Delete > Confirm Delete
Close the mmc > Say NO when asked if you want to save Console
Now, the certificate is removed. This warning should not appear in the Event Viewer.
Exchange 2010 Certificate Renewal
In this article we cover the following:
- Exchange Certificate that is about to expire.
- Renew Exchange Certificate.
Exchange Certificate that is expiring or has expired:
On Exchange 2010 you might see the following warning to say that a certificate is about to expire or has already expired.
We can check which certificate this is in Exchange by running the following command from the Exchange Management Shell on the server that is logging this warning:
- Get-ExchangeCertificate
- Or
- Get-ExchangeCertificate | fl Thumbprint,Subject
In this case this certificate handled the following services: IIS, IMAP, POP and SMTP
Renew Certificate
To renew the certificate you can use the EMC or the EMS. You can use the Exchange Management Shell and run the following command:
- Get-ExchangeCertificate -thumbprint “<ThumbPrint as above>” | New-ExchangeCertificate
- Once the command has run confirm the prompts by typing in “y” and then pressing enter.
Assign Services to the new Certificate
Once the new certificate installation has completed we can now assign services to it. In the same EMS window run the following command:
- Enable-ExchangeCertificate -thumbprint “<ThumbPrint as above>” -services IIS,POP,IMAP,SMTP
Once you are happy with the new certificate then you can open the MMC and add the snap-in for your certificates and remove the expiring one.
Hope it helps.
To totally unlock this section you need to Log-in
Login
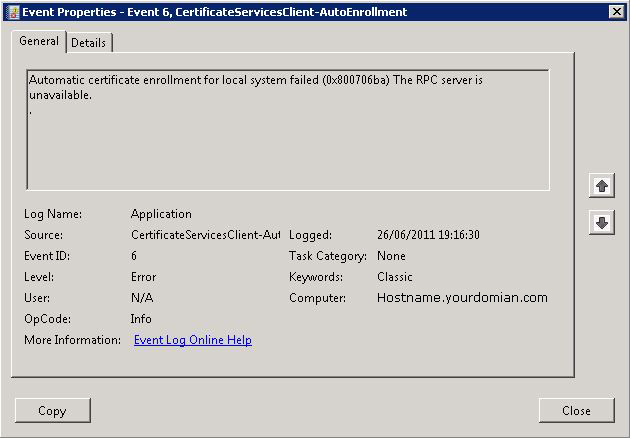
In a domain environment, that could be a common issue about certificates auto-enrollment, with common events error like 6 and 13. Let’s see how to fix them.
Source: Microsoft-Windows-CertificateServicesClient-AutoEnrollment
Description: Automatic certificate enrollment for local system failed (0x800706ba) The RPC server is unavailable.
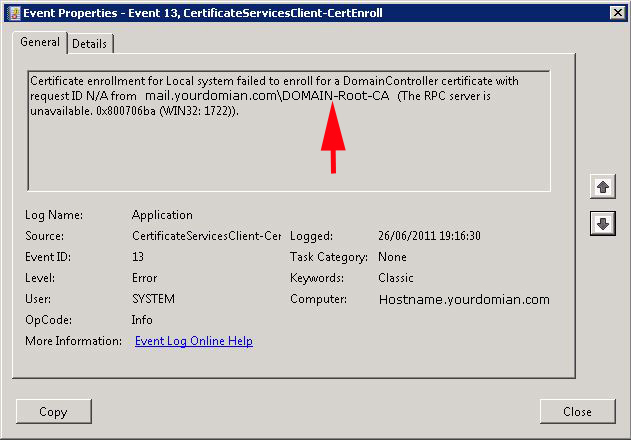
Event ID 13
Source: Microsoft-Windows-CertificateServicesClient-CertEnroll
Description: Certificate enrollment for Local system failed to enroll for a DomainController certificate with request ID N/A from {hostname}{name of CA}(The RPC server is unavailable. 0x800706ba (WIN32: 1722)).
Solution
Note: The pertinent information in the Event ID 13 above is 0x800706ba there are Other causes of this Event ID make sure yours is the same.
In a sample case we could have an Exchange server that was using a certificate that had been «self signed«. And the Root CA that signed the certificate had been ungracefully removed from the domain. Take a note of the Root CA name from the Event ID error shown arrowed).
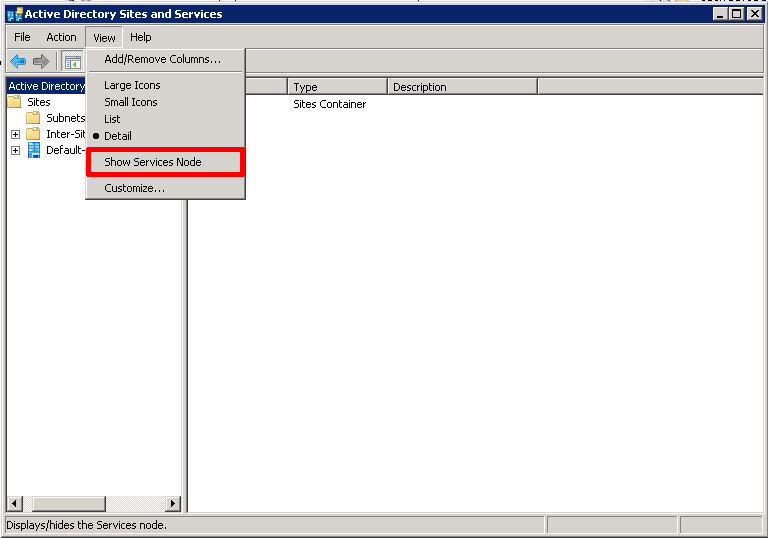
Launch Active Directory Sites and Services» > Select the top level object > View > Show Services Node.
Expand Services > Public Key Services > AIA > Delete the «Problem CA«.
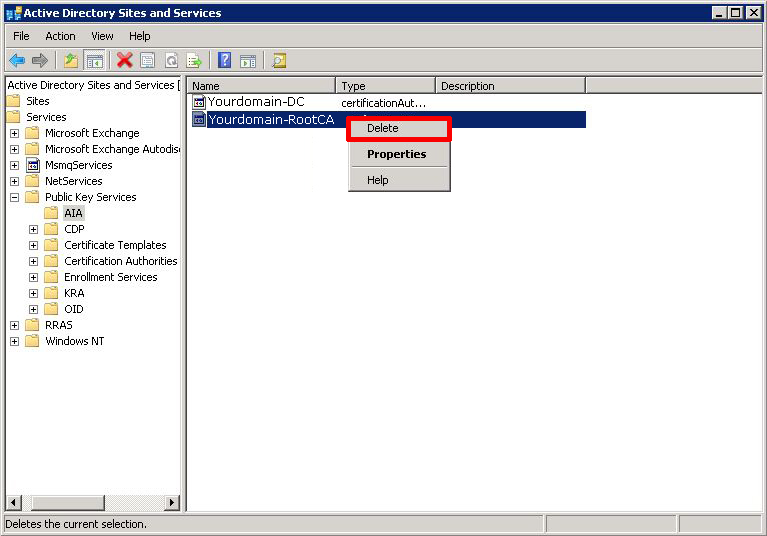
Then select «Enrollment Services» > Delete the «Problem CA«.
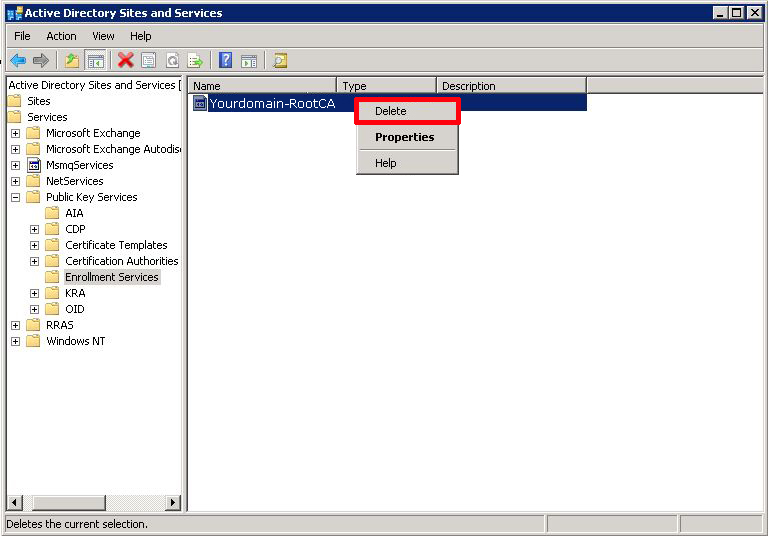
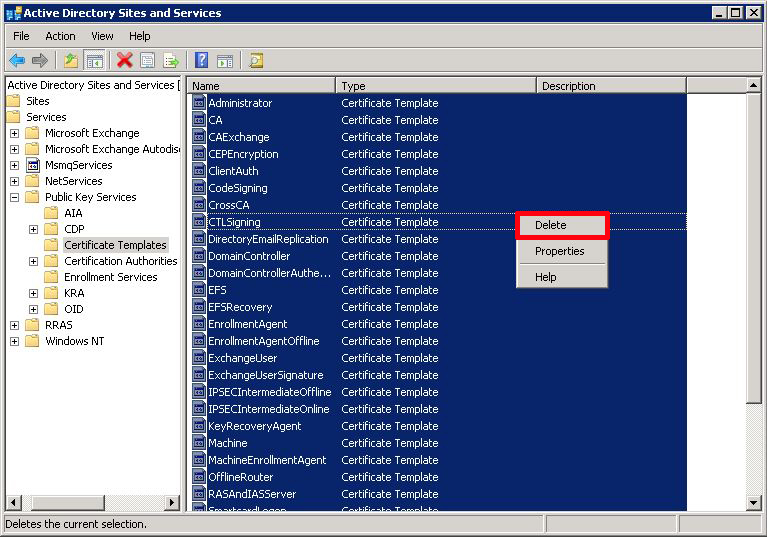
IMPORTANT: If you have a New CA, then DO NOT perform the next two steps!!!
Providing you DON’T have a CA now, select «Certificate Templates» and delete them all.
Providing you DON’T have a CA now, select «Public Key Services» and delete the NTAuthCertificates item.
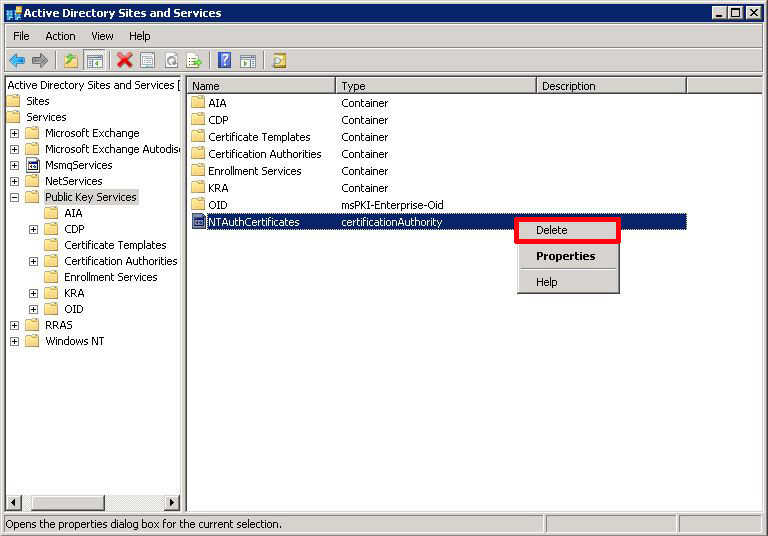
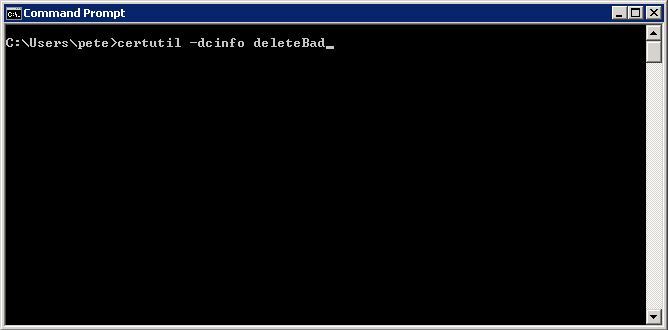
To tidy up, (on the server logging the error) run the following command:
certutil -dcinfo deleteBad
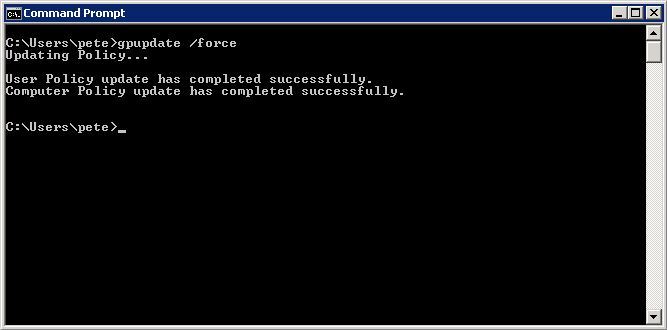
Finally on the server logging the error run the following command to update the policies:
gpupdate /force
Resolve
Renew a CA certificate
A computer certificate on a managed computer, not a certification authority (CA), must be renewed when it passes 90 percent of its validity period or has expired. Because a successful renewal will generally be initiated before the certificate reaches 90 percent of its lifetime, this error indicates that there may be a problem automatically obtaining a new certificate via autoenrollment.
To perform this procedure, you must have membership in local Administrators or Users on the computer that logged the error, or you must have been delegated the appropriate authority.
To renew a CA certificate:
* Click Start, type mmc, and then press ENTER.
*If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue.
* On the File menu, click Add/Remove Snap-in, click Certificates, and then click Add.
* Select the user or computer account that logged the error, and click Next.
* Click Finish, and then click OK.
* In the console tree, click Certificates — Current User or Certificates (Local Computer), and then click Personal.
In the console tree, double-click Certificates, double-click Personal, and then click Certificates.
* Locate the certificate with the thumbprint listed in the event log message.
* Right-click the certificate, and select one of the Renew Certificate options to start the Certificate Renewal Wizard and renew the CA certificate.
- Event Log providers
- Microsoft-Windows-CertificateServicesClient-AutoEnrollment
- View page source
Seen on:
-
Windows Vista
-
Windows 2008
-
Windows 7
-
Windows 2012
-
Windows 8.0
-
Windows 8.1
-
Windows 10 (1511, 1607, 1703, 1709, 1803, 1809, 1903, 1909, 2004, 20H2)
-
Windows 2016
-
Windows 2019
-
Windows 11 (21H2)
| Name: | Microsoft-Windows-CertificateServicesClient-AutoEnrollment |
| Identifier: | {f0db7ef8-b6f3-4005-9937-feb77b9e1b43} |
| Log type(s): | Application |
| Log source(s): | AutoEnrollment |
| Microsoft-Windows-CertificateServicesClient-AutoEnrollment | |
| Event message file(s): | %SystemRoot%\system32\pautoenr.dll |
