Strengthen your Zero Trust posture—a new, unified approach to security is here.
Read the blog
Establish Zero Trust access controls, prevent identity attacks, and manage access to resources.
Create your trust fabric in four stages
Accelerate your Zero Trust journey for identity and access with generative AI.
Manage and protect with Microsoft Entra ID
Safeguard your organization with a market-leading cloud identity and access management solution.
Secure adaptive access
Protect access to resources and data using strong authentication and risk-based conditional access policies without compromising user experience.
Seamless user experiences
Provide a fast, easy sign-in experience across your multicloud environment to reduce time managing passwords, and increase productivity.
Unified identity management
Manage all your identities and access to all your applications in a central location, whether they’re in the cloud or on-premises, to improve visibility and control.
Comprehensive capabilities
App integrations and single sign-on (SSO)
Connect your workforce to all your apps, from any location, using any device. Simplify app access from anywhere with SSO.
Passwordless and multifactor authentication (MFA)
Help safeguard access to data and apps and keep it simple for users. Provide ease of use without the inherent risk of passwords.
Conditional Access
Apply the right access controls to strengthen your organization’s security.
Identity protection
Protect identities and block identity attacks in real time.
Privileged identity management
Strengthen the security of your privileged accounts.
End-user self-service
Help your employees securely manage their own identity with self-service portals including My Apps, My Access, My Account, and My Groups.
Unified admin center
Confidently manage all Microsoft Entra multicloud identity and network access solutions in one place.
Back to tabs
Multicloud identity and access management
Secure access for your employees to apps and resources in any cloud or on-premises with Microsoft Entra ID.
Consistently recognized as a Leader by industry analysts
Microsoft recognized for eighth year
Microsoft is an eight-time Leader in the Gartner® Magic Quadrant™ for Access Management.1, 2
A leader in access management
Learn why KuppingerCole rates Microsoft a strong positive across all product and leadership dimensions in access management.3
See why more than 720,000 organizations use Microsoft Entra ID
Get started with Microsoft Entra ID
Microsoft Entra ID P2
Get comprehensive identity and access management capabilities including identity protection, privileged identity management, and self-service entitlement management for users.
Microsoft Entra ID P1
Get the fundamentals of identity and access management, including single sign-on, multifactor authentication, passwordless, conditional access, and other features.
Establish Zero Trust
Secure workforce access
Secure customer and partner access
Secure access in any cloud
Additional resources for Microsoft Entra ID
Azure AD is now Microsoft Entra ID
Microsoft Entra ID is the new name for Azure AD. All licensing and functionality remain the same. No action is required from you.
Microsoft Entra blog
Stay up to date with the latest news about our identity and network access product family.
The Total Economic Impact™ of Microsoft Entra
Learn how a composite organization achieved a positive three-year, ROI with Microsoft Entra in this 2023 commissioned Forrester Consulting study.4
Technical documentation
Explore all the features in Microsoft Entra ID, and view how-to guides, tutorials, and quickstart guides.
Frequently asked questions
-
Microsoft Entra ID, formerly known as Azure Active Directory (Azure AD), is an identity and access management solution from Microsoft that helps organizations secure and manage identities in cloud and on-premises environments.
Learn more
-
Microsoft Entra ID has a free edition that provides user and group management, on-premises directory synchronization, basic reports, self-service password change for cloud users, and single sign-on (SSO) across Azure, Microsoft 365, and many popular SaaS apps. The free edition is included with a subscription of a commercial online service such as Azure, Microsoft 365, Dynamics 365, Intune, or Power Platform.
Learn more
-
In 2023, Azure Active Directory (Azure AD) was renamed Microsoft Entra ID.
Learn more
-
The name changed. Microsoft offers and supports the capabilities and service level agreements of Azure AD under the new name of Microsoft Entra ID.
Learn more
Get started
Safeguard your organization with a seamless identity and access management solution.
Время на прочтение8 мин
Количество просмотров55K
Традиционно, для управления корпоративной сетью используется Active Directory. Но все чаще организации внедряют в свою работу различные облачные службы, которые требуют создания своих учетных записей. Инструментом для создания и управления учетными записями пользователей, применыемых в различных облачных службах Microsoft, которые приобретает организация, является Azure Active Directory. В этой статье мы поговорим о некоторых отличиях между Active Directory и Azure Active Directory, а также рассмотрим основные сценарии их синхронизации.
Я уверена, что подавляющее большинство тех, кто читает эту статью, знакомы с Active Directory, которая является частью операционных систем Windows Server и представляет собой службу каталогов, предлагаемую компанией Microsoft. Имея учетную запись AD, пользователь аутентифицируется в системе и получает доступ к приложениям, файловым службам, принтерам и другим локальным ресурсам.
Так же, как и локальная Active Directory, Azure Active Directory аутентифицирует пользователей и предоставляет им доступ к приложениям. Однако, Azure Active Directory предназначена для работы пользователь не в локальной инфраструктуре, а при работе со сторонними облачными приложениями, такими как Office365 и Windows Intune.
Например, ваша организация приобретает подписку на Windows Intune. При этом вы, как администратор, получаете доступ к порталу управления Windows Intune и должны предоставить доступ другим пользователям в вашей сети (всем или нескольким – это уже детали). Windows Intune – это облачная служба Microsoft, которая не работает с локальной Active Directory. Для того, чтобы создать учетные записи пользователей для доступа к облачным службам, которые внедряет и использует организация, необходимо использовать Azure Active Directory.
C технической точки зрения, нужно отметить, что для доступа к данным в локальной службе Active Directory бизнес-приложения могут использовать LDAP, а сторонние облачные приложения могут взаимодействовать с данными с помощью API Graph. Для аутентификации в AD DS используется протокол Kerberos, а в Azure Active Directory – OAuth 2.0. На схеме далее показано, как приложения, размещенные либо локально, либо в облаке, используют похожие методологии для доступа к данными удостоверений, которые хранятся в наиболее подходящей для них службе удостоверений.
Но вернемся к нашему примеру. Компания приобрела подписку на Windows Intune, и теперь системный администратор должен создать в Azure AD учетные записи для пользователей. Сделать он это может конечно ручками через графический интерфейс или даже использовать командлеты и скрипты PowerShell. Но, используя этот вариант добавления пользователей, вы создаете абсолютно самостоятельных пользователей, никак не связанных с теми, что давно уже существуют в вашей локальной сетке. Да, логины могут совпадать, но могут и отличаться; пароли – тем более. Все это – огромный источник потенциальной головной боли для админа и регулярных обращений от пользователей в службу поддержки. Для того, чтобы эти проблемы минимизировать предлагается три сценария синхронизации AD и Azure AD, о которых мы поговорим далее.
Синхронизация Active Directory и Azure Active Directory
Выделяют три основных сценария синхронизации каталогов Active Directory и Azure Active Directory:
- Сценарий синхронизации каталога позволяет автоматически синхронизировать с облаком новые учетные записи пользователей и групп, обновления к существующим учетным записям в локальной Active Directory, настроить клиент для работы в комбинированных сценариях с использованием Office 365 и включить решения многофакторной проверки подлинности в облаке.
- Синхронизация Active Directory с помощью сценария синхронизации паролей в дополнение к возможностям синхронизации каталога дает возможность пользователям задействовать пароль от локальной учетной записи для доступа к облачным приложениям и службам, что, в свою очередь, сокращает расходы на администрирование паролей и позволяет управлять политиками паролей из локального каталога Active Directory.
- Синхронизация Active Directory с помощью сценария единого входа, в отличие от первых двух сценариев, не поддерживает возможность включения решения многофакторной аутентификации в облаке, но зато поддерживает эту возможность в локальной среде, а также обеспечивает проверку подлинности пользователей в локальном каталоге Active Directory и позволяет реализовать сценарии единого входа с использованием корпоративных учетных данных, настроить страницу для единого входа и ограничить доступ к облачным службам и приложениям по местоположению, типу клиента или конечной точке Exchange клиента.
Все это, кончено, замечательно звучит, но более интересно посмотреть, как каждый из сценариев синхронизации работает и в чем заключается его принципиальная особенность.
1 Сценарий синхронизации каталога
Сценарий синхронизации каталогов используется для синхронизации локальных объектов доменной сети в облако. При реализации этого сценария в итоге вы получите учетную запись пользователя в Azure Active Directory, которая будет совпадать с локальной учетной записью во всем, кроме пароля. Пароли при реализации сценария синхронизации каталога НЕ синхронизируются. Поэтому теперь вы говорите вашим пользователям, что для доступа, например, к Windows Intune можно использовать свой обычный логин, а вот пароль нужно будет придумать другой. В этом случае, пользователь при доступе к облачной службе будет аутентифицирован с помощью именно Azure Active Directory. Примерная схема того, как работает этот процесс, представлена ниже.
После того, как настройка выполнена, администраторы могут управлять объектами каталога, используя локальную Active Directory, и эти изменения будут синхронизированы с клиентскими компьютерами. Синхронизация службы каталогов выполняется по расписанию и синхронизируются с Azure AD.
Среди преимуществ сценария синхронизации каталога можно выделить:
- Сокращение затрат на администрирование. При использовании уже существующих локальных учетных записей пользователей и групп нет необходимости управлять ими вручную в Azure AD, что экономит бюджет и время.
- Повышение продуктивности. Автоматическая синхронизация учетных записей пользователей и групп сокращает время, необходимое для обеспечения пользователя доступом к облачным службам и приложениям.
- Повышение безопасности. Предоставление доступа и его отзыв для учетных записей пользователей и групп происходит автоматически, что позволяет гарантировать доступ к ресурсам корпоративной сети только тем, кому он действительно нужен, а также указывать срок, на который доступ предоставлен.
2 Синхронизация Active Directory с помощью сценария синхронизации паролей
Все-таки больным местом учетных записей пользователей являются не логины, а пароли. Логин обычно запомнить не сложно, а вот иметь разные пароли для доступа к разным ресурсам – испытание для пользователя.
Поэтому он либо придумывает простые пароли, либо пишет их на стикерах и клеит на монитор, либо догадывается использовать везде один и тот же пароль.
Существует расширение сценария синхронизации каталога – сценарий синхронизации паролей. Если на компьютере с уже реализованной синхронизацией каталогов включить синхронизацию паролей, то сотрудники вашей организации смогут подключаться к облачными службам Microsoft (например, Office 365, Dynamics CRM, Windows InTune), используя пароль от локальной учетной записи. Изменение пароля в локальной корпоративной сети будут синхронизированы с облаком, причем пароли синхронизируются чаще, чем другие данные каталогов.
Ниже приведена схема синхронизации Active Directory с помощью сценария синхронизации паролей. Чтобы пароль был синхронизирован, средство синхронизации каталогов извлекает хэш пароля пользователя из локальной службы Active Directory и синхронизирует его с Azure Active Directory.

Теперь со спокойной душой говорим пользователям, что мы используем новую облачную службу, доступ к которой можно получить со своим обычным логином и паролем. Все довольны, все счастливы.
При использовании данного сценария синхронизации среди преимуществ нужно отметить:
- Сокращение эксплуатационных затрат. Сокращение количества паролей, которые необходимы пользователю для работы в корпоративной сети, влечет за собой уменьшение числа запросов на смену пароля к службе поддержки.
- Повышение продуктивности. Сокращение числа паролей, которые нужны пользователю для доступа к тем или иным корпоративным ресурсам, увеличивает время, в течение которого эти ресурсы доступны.
Тем не менее, при реализации сценария синхронизации паролей, пользователь все равно проходит процесс аутентификации с помощью учетной записи Azure Active Directory, а мы хотим пойти дальше, и использовать для аутентификации именно локальную Active Directory. Для того, чтобы нашу задумку осуществить, необходимо использовать сценарий синхронизации Active Directory с помощью единого входа.
3 Синхронизация Active Directory с помощью сценария единого входа
Для реализации единого входа должен быть реализован сценарий синхронизации каталога и построена инфраструктура службы токенов безопасности (STS). Azure AD поддерживает сценарии единого входа, которые используют одну из следующих служб токенов безопасности: Active Directory Federation Services, поставщик удостоверений Shibboleth, а также сторонние поставщики удостоверений.
Процесс работы сценария единого входа представлен на следующей схеме.
При реализации сценария единого входа настраиваются федеративные отношения между службой STS (Security Token Service) и системой проверки подлинности Azure Active Directory. Пользователь при попытке подключения к облачной службе будет перенаправлен на сервер службы STS. Например, при использовании службы ADFS, пользователь будет перенаправлен на ADFS сервер, что можно будет увидеть по изменению адреса в браузере:
После успешной аутентификации, пользователь с учетной записью локального каталога Active Directory получит токен проверки подлинности от локальной службы STS и с помощью которого получит доступ к облачной службе. Принципиальным отличием от первых двух сценариев является то, что в сценарии единого входа пользователь аутентифицируется с помощью Windows Server Active Directory.
Применение сценария единого входа предлагает главное преимущество: сотрудник использует свои учетные данные для доступа к облачным приложениям и службам. Системные администраторы также получают ряд новых возможностей:
- Управление политиками. Администратору не нужно выполнять какие-либо дополнительные задачи в облаке для того, чтобы контролировать политики учетных записей Active Directory.
- Управление доступом. Администратор может ограничить доступ к облачным службам так, чтобы доступ можно было получить только через среду организации или через интернет-сервер.
- Снижение количества обращений за поддержкой. Тут все тоже: меньше паролей запоминать – меньше обращений от пользователей.
- Безопасность. Так как все серверы и службы, используемые в рамках реализации сценария единого входа, управляются и контролируются локально, то удостоверения пользователей и информация о них защищены.
- Поддержка строгой проверки подлинности. Сценарий единого входа позволяет реализовать многофакторную проверку подлинности для доступа к облачной службе или приложению.
Надеюсь, данная статья дала вам представление о разнице между Active Directory и Azure Active Directory и сценариях их синхронизации.
Подробные инструкции о том, как реализовать каждый из описанных здесь сценариев, вы можете посмотреть на портале TechnNet:
- Сценарий синхронизации каталога
- Синхронизация Active Directory с помощью сценария синхронизации паролей
- Синхронизация Active Directory с помощью сценария единого входа
Спасибо!
Полезные ссылки
- Попробовать Azure бесплатно на 30 дней!
- Изучить курсы виртуальной академии Microsoft по облачным и другим технологиям
- Загрузить бесплатную или пробную Visual Studio
- Центр разработки Microsoft Azure (azurehub.ru) – сценарии, руководства, примеры, рекомендации по разработке
- Twitter.com/windowsazure_ru — последние новости Microsoft Azure
- Сообществе Microsoft Azure на Facebook – эксперты, вопросы
- Стать разработчиком универсальных приложений Windows
Microsoft Windows Azure Active Directory (Windows Azure AD or Azure AD) is a cloud service that provides administrators with the ability to manage end-user identities and access privileges. Its services include core directory, access management and identity protection. As the name implies, Azure AD is part of the Microsoft Azure public cloud computing platform.
The service gives administrators the freedom to choose which information will stay in the cloud, who can manage or use the information, which services or applications can access the information, and which end users can have access. Azure AD can help to provide single sign-on (SSO), so end users don’t have to enter passwords multiple times to access cloud applications.
Azure AD is used by IT admins, app developers and Microsoft cloud service subscribers. IT admins use Azure AD to manage role permissions and control access to specific applications and resources for individual users. App developers may use Azure AD to add single sign-on to apps that work with preexisting user credentials. Azure AD also provides app developers with application program interfaces (APIs) that use existing data within the organization. Subscribers to Microsoft cloud services, such as Office 365, Dynamics CRM Online or Azure, are, by default, tenants of Azure AD.
Azure AD comes in four distinct tiers of service and pricing. Basic features, with limitations, can be accessed at no cost. Subscribers to Microsoft 365 Office apps obtain more functionality than the basic features. Azure AD Premium requires an additional extra monthly subscription, and it comes in two tiers: P1 and P2 (highest tier).
Despite the similar name, Azure AD is not the same as Windows Active Directory (Windows AD), another Microsoft product.
How does Windows Azure Active Directory work?
Azure AD is a cloud-based service for identity and access management (IAM). It is a secure online authentication store for individual user profiles and groups of user profiles, and it falls into the identity as a service (IDaaS) category. Azure AD is intended for managing access to cloud-based applications and servers that use modern authentication protocols such as SAML 2.0, OpenID Connect, OAuth 2.0 and WS-Federation.
Azure AD manages access through user accounts, which carry a username and a password. Users can be organized into different groups, which can be granted different access privileges for individual applications. Identities can also be created for cloud applications, which may be from Microsoft or third-party software as a service (SaaS), to grant user access through.
Azure AD uses SSO to connect users to SaaS applications. This allows each user to access the full suite of applications they have permission for, without having to repeatedly log in each time. Azure AD creates access tokens which are stored locally on employee devices; these tokens may be created with expiration dates. For important business resources, Azure AD can require multifactor authentication (MFA).
Security in Azure AD
Azure AD contains a number of features to secure and protect organizational data. Azure AD’s security features include MFA, SSO for cloud-based SaaS applications, context-based adaptive policies, Identity governance, an application proxy to secure remote access and protective machine learning (to guard against stolen credentials and suspicious log-on attempts).
A feature called Security Defaults in Azure AD was released recently, which, when turned on, will block legacy authentication protocols, require MFA for administrators and users and require MFA for valuable organizational resources. The purpose of security defaults is to better secure digital assets, as baseline access policies in Azure AD are designed to accommodate organizations with legacy clients and added on third-party security features. Security defaults are designed against common types of attacks such as phishing, password spray and session replay. If not disabled, malicious attacks can use legacy protocols to authenticate, whilst bypassing multifactor authentication.
Azure AD is not to be confused with Windows Active Directory, another Microsoft service with a similar name. Active Directory consists of several services that run on Windows Server, managing user access to networked resources, such as printers. Though Azure AD and Windows AD both manage user accounts, they use completely different authentication protocols and code bases. Therefore, Azure AD is not simply the cloud-based counterpart of Windows AD.
Key differences include the following:
- Unlike Windows AD, Azure AD is designed for web-based services. Azure AD supports services that use REST (Representational State Transfer) APIs for online cloud-based apps such as Office 365.
- Azure AD uses different protocols from Windows AD. Azure AD uses protocols such as SAML and OAuth.2.0. It does not support NTLM, Kerberos or LDAP (Lightweight Directory Access Protocol).
- Azure AD uses Azure Policy, as opposed to Group Policy in Windows AD.
- Azure AD does not use OUs (organizational units) or forests. It has a flat directory structure.
- Azure AD Join, which links to PCs (personal computers), can only be used with Windows 10.
Azure AD features and licensing
Azure AD comes in four different licensing tiers: free (lowest), Office 365 Apps, Premium P1 and Premium P2 (highest).
The free licensing tier has a 500,000-object limit for directory objects. It contains all of the business-to-business, core identity and access management features. It does not include IAM for Office 365, premium features, hybrid identities, conditional access, identity protection, identity governance or advanced group access management. According to Microsoft, features included in the free tier are:
- Unlimited single sign-on
- User provisioning
- Federated Authentication (Active Directory Federation Services or third-party identity provider)
- Users and group management
- Device registration
- Cloud authentication (Pass-Through Authentication, Password Hash synchronization, Seamless SSO)
- Azure AD Connect sync, which extends an organization’s on-premises directories to Azure AD
- Self-service password change
- Azure AD Join (desktop SSO and administrator BitLocker recovery)
- Password protection
- Multifactor authentication
- Basic reporting for security and usage
- Azure AD features for guest users
The second-lowest tier of Azure AD services is accessible for subscribers to Office 365 apps. It is accessible for subscribers of the E1, E3, E5, F1 and F3 levels. This tier has no directory object limit. It includes all of the features offered in the free tier, plus identity and access management for Office 365 apps, such as:
- Customized company branding of access panels and logon/logout pages
- Service-level agreement (SLA)
- Self-service password reset for cloud users
- Two-way synchronization of device objects between Azure AD and on-premises directories
The Premium P1 tier grants the second-highest level of access to Azure AD. Premium P1 access costs $6 per month, per user. It includes full functionality of Azure AD, except for identity protection and identity governance. Specific features in Premium P1 include everything offered in the Office 365 tier, plus:
- Premium password protection, self-service password reset with on-premises write-back
- Advanced group access management
- Azure AD Join with mobile device management (MDM) auto enrollment, local admin policy customization, self-service BitLocker recovery, enterprise state roaming
- Advanced security and usage reports
- Hybrid identities
- Conditional access
The Premium P2 tier costs $9 per month, per user and includes the full suite of Azure AD functionality. It includes everything offered in P1, as well as identity protection and identity governance features.
This was last updated in August 2020
Continue Reading About Microsoft Windows Azure Active Directory (Windows Azure AD)
- Prepare for the cloud by updating your AD services
- A look at the new and improved Windows Azure AD
- What admins should know about Azure services
- Single-sign on with cloud apps possible with Windows Azure AD
- An introduction to Windows Azure AD
Dig Deeper on IT operations and infrastructure management
-
How to copy files from source to destination in PowerShell
By: Anthony Howell
-
How to secure on-prem apps with Entra Application Proxy
By: Adam Fowler
-
How to use a Microsoft Entra ID emergency access account
By: Liam Cleary
-
What should admins know about Microsoft Entra features?
By: Brien Posey
What is Azure Active Directory?
Azure Active Directory (Azure AD) is Microsoft’s cloud service that provides identity and access management (IAM). It is part of the Office 365 system, it is compatible with an on-premise active directory, and is useful to provide authentication to multiple cloud-based services via various cloud protocols such as SAML, OAuth2, and WS Security. It provides the ability to manage user identities and access rights. Azure AD combines core directory services, access management, and identity protection into a single solution.
Azure AD allows your users to sign in and access the resources which are in external resources such as Office 365 and thousands of other Software as a service (SaaS) applications. It also allows your users to gain access to internal resources such as applications on your company network and intranet. Azure AD uses Representational State Transfer (REST) APIs to connect with other web-based applications. In this directory, the admin has the capability to create groups and add accounts to those groups. Group access to resources can then be assigned to them. Mobile devices and Windows desktops can connect to Azure AD using Microsoft Intune.
How does Azure Active Directory work?
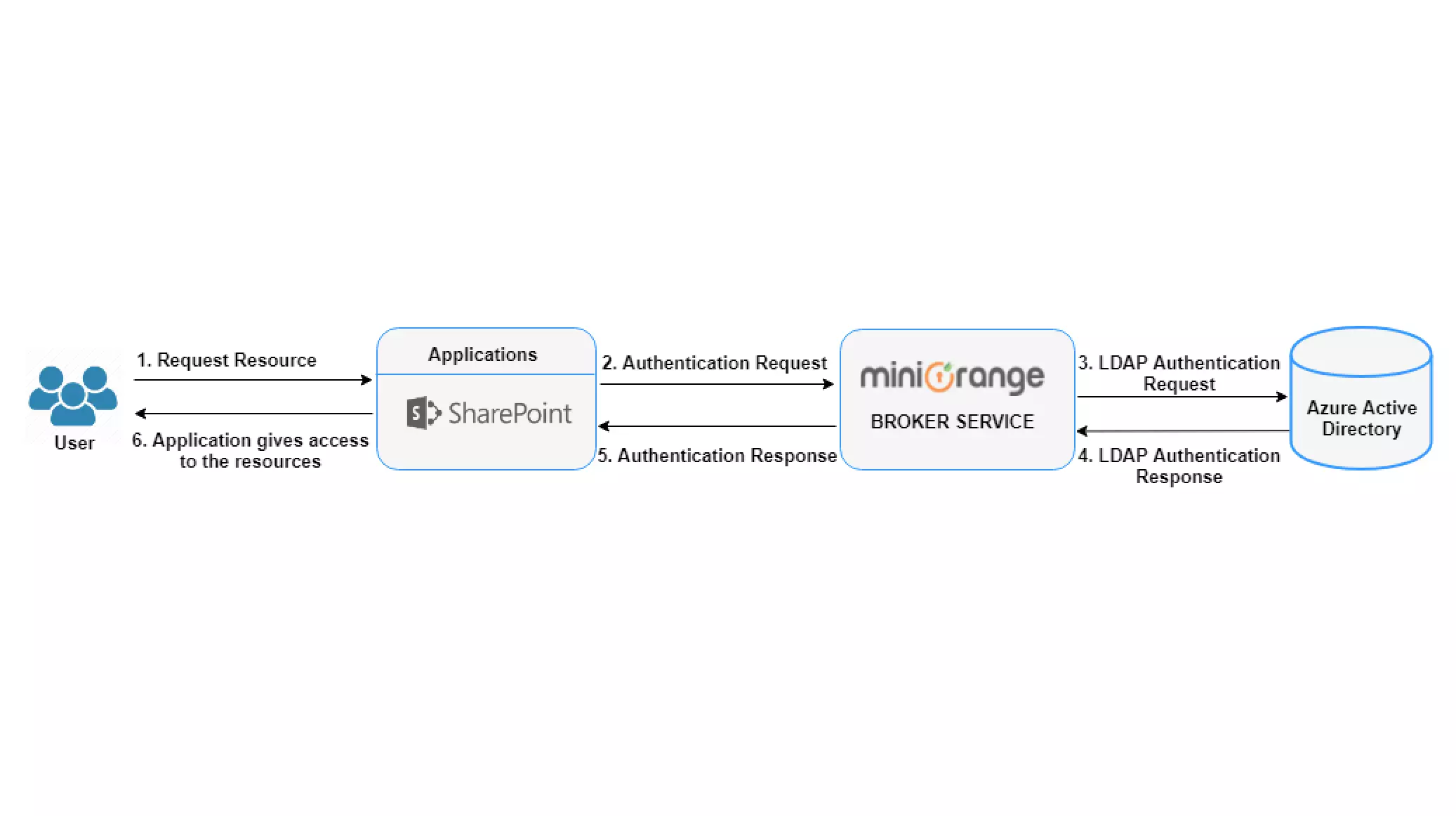
The Azure Active Directory Authentication takes place in the following steps:
- The user navigates to the application and requests access.
- An authentication request is sent to the miniOrange Broker Service.
miniOrange Broker identifies the Azure AD and sends authentication requests to Azure AD. - Azure Active Directory authenticates the user and generates the SAML token, LDAP authentication Response is sent to the broker.
- miniOrange broker posts the SAML response to the Service provider (Application) via the user’s browser.
- The service provider (Application) verifies the SAML response and access is granted to the user.
Windows Active Directory vs Azure Active Directory
Windows Active Directory, launched by Microsoft in 2000, is the predecessor to the Azure Active Directory, which has become the standard for enterprise identity management since its launch. Unlike Azure Active Directory, the Windows Active Directory uses Lightweight Directory Access Protocol (LDAP) to connect with other web-based applications. It also does not manage mobile devices. Group Policies (GPOs) are usually used to govern desktops and servers connected to Windows Active Directory. Finally, Kerberos and NTLM protocols are used to validate user credentials.
Because of the limitations of Windows Active Directory in cloud contexts, Microsoft created Azure Active Directory. Users may use Azure AD to manage all of their cloud apps and servers, including Office 365, SharePoint Online, and Exchange Online.
The key distinction between the two platforms is that Azure AD uses Representational State Transfer (REST) API interfaces to provide web-based applications. As previously indicated, it accomplishes this through the use of unique protocols and code bases. You will instantly become an Azure AD Tenant after you register with one of Microsoft’s cloud apps. This means you can manage all users, permissions, passwords, and more from a single location.
Benefits of azure active directory
Simple Integration:
Because Azure AD supports a wide range of identity providers, users may log in using their Microsoft, Google, Facebook, or GitHub accounts. Azure AD may also be integrated with a variety of apps, including Salesforce, Office 365, and others.
Strong Azure AD Security:
Microsoft, as you might assume, takes security very seriously. Multi-factor authentication, conditional access, and Privileged Identity Management (PIM) are just a few of the security features available in Azure AD.
High Availability:
Microsoft promises a 99.9% availability guarantee. Azure AD is highly available thanks to a distributed architecture that spans 28 data centers throughout the globe. All data is written to the Active Primary partition first, then duplicated to the Passive Primary, and finally read from the Secondary Replica partitions.
Collaboration:
By granting access to the internal project site or material, Azure AD aids collaboration outside the business, such as with partners. Azure AD B2B (business-to-business) and Azure AD B2C (business-to-consumer) are the two major external collaboration functions. You may invite business colleagues to your application or service using the B2B functionality, and they can sign in using their current Azure identity. The B2C functionality is similar, except your clients may sign in to your app or service using their preferred identity provider (Facebook, Google, GitHub, etc.). MFA and Conditional Access rules can be used to control access to resources in both circumstances.
Single sign-on:
This allows onboarding new workers, terminating access for outgoing employees, and implementing access to new cloud services easier and faster, allowing users to get up and running faster. Single sign-on also promotes commitment to security and identification rules.
Multi-Factor Authentication:
This adds an extra degree of protection to accounts by requiring another form of verification. Microsoft Authenticator app, OATH Hardware token, OATH Software token, SMS, Voice call, and other MFA verification methods are available in Azure AD.
Limitations of Azure Active Directory Authentication
- Limited MFA methods: Azure Active Directory Authentication supports limited Multi-Factor Authentication (MFA) methods.
- No Group policy: It has few policy tools like conditional access, but it is more focused on granting access.
- No support for NTLM or Kerberos: Azure AD Authentication supports only modern authentication protocols like OAuth, SAML & OpenID Connect.
- Limited OAuth support: It does not have support for all OAuth grants.
- No support to extend or customize existing protocols with custom apps.
- Limited support for Device, location, and time-based access policies.
Azure Active Directory Authentication Components
- Service Provider — Service providers are responsible for communications between the user, an identity provider that maintains a user directory. In this case, Azure Active Directory is an identity provider and the application could be a Service provider.
- Identity Provider — Here Azure AD is an identity provider. So As an Identity Provider, it authenticates the user and provides an authentication token (that is, information that verifies the authenticity of the user) to the service provider.
Click here to learn more about Azure Active Directory.
Azure Active Directory VS miniOrange IdP
| Features | Azure Active Directory | miniOrange IdP |
|---|---|---|
| Multi-Protocol support | Supports only a few modern authentication protocols (OAuth, SAML & OpenID Connect) | Fully supports all protocols for Authentication. |
| Multi-Factor Authentication | Supports limited Multi-Factor Authentication methods. | Supports 15+ Multi-Factor Authentication methods. |
| Pricing Plans | A fixed annual subscription. (No quote-based pricing plan). | A flexible monthly & quote-based pricing plan for all size organizations. |
| Security | Doesn’t support. | It supports fraud prevention, social login, and cloud security. |
| Adaptive Authentication | Doesn’t support. | It supports Adaptive Multi-Factor Authentication. |
Further Reading
- Directory Services
- Single Sign-On SSO
- Login Using Azure AD
Azure Active Directory (Azure AD) is a service for managing identities and access in the cloud. This solution facilitates access to thousands of additional SaaS applications, the Azure portal, and external resources like Microsoft 365 for your staff members. They can also access internal resources like apps on your business intranet network and any cloud apps created by your own company, thanks to Azure Active Directory. You can also maintain your on-premises Active Directory implementation with the assistance of Azure AD. Simply explained, Azure AD enables users to sign up for various services and access them from any location via the cloud using a single username and password.
Why Azure Active Directory?
Suppose you have a large organization with a lot of developers. Some Azure services must be available to all developers for them to perform their responsibilities. When the administrator gives them a unique username and password for each service, they can access services like databases, virtual machines, or Azure storage services. It might be challenging for administrators and employees to manage many user logins at once.
Azure Active Directory (AD) enters the scene in this situation. Administrators can easily manage numerous user logins with Azure AD. To access each service, administrators must provide a single login and password in Microsoft Azure. You can also manage the permissions on Azure storage disks which contain important data of organizations.
Who uses Active Directory?
- IT administrators: Based on their organizational needs, administrators can utilize Azure AD to manage access to applications and Azure resources.
- Developers: With the help of Azure AD, developers may add functionality to the applications they create, such as SSO capability.
- Users: The ability to maintain identities and perform maintenance tasks like self-service password reset is provided to users.
- Online Service Subscribers: Azure AD is already being used by Microsoft 365 online subscribers to log into their accounts.
What is Windows Active Directory?
Windows Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. The primary purpose of Active Directory is to manage permissions and access to networked resources.
Components of Windows Active Directory
- Domain Controllers: Servers that host AD and manage the database, authentication, and directory services.
- Schema: Defines the objects and attributes stored in the directory.
- Global Catalog: A distributed data repository that contains a searchable, partial representation of every object in every domain within a multi-domain AD forest.
- DNS Integration: AD relies heavily on the Domain Name System (DNS) for locating domain controllers and other AD services.
How Does Azure Active Directory Work?
Azure Active Directory (Azure AD) simplifies identity and access management in the cloud. Users authenticate with Azure AD credentials, enabling secure access to applications and services. Single sign-on (SSO) streamlines user experience by allowing access to multiple resources with one login. Robust security features like multifactor authentication (MFA) and access policies ensure secure access control. Azure AD Connect facilitates seamless integration between on-premises and cloud environments for unified identity management.
How is Azure AD structured?
Azure Active Directory (Azure AD) is structured as a cloud-based directory and identity management service with a flat hierarchy. It organizes resources into tenants, where each tenant represents a dedicated and isolated instance of Azure AD. Within a tenant, users, groups, and applications are managed. Users are individual accounts, groups are collections of users, and applications are registered entities that Azure AD can authenticate. Additionally, administrators can set up roles and permissions to control access and enforce policies across these resources.

Steps to Configure Azure AD(Users, Roles, And Groups)
Step 1: Login into the Azure console and search for Azure Active Directory as shown in the image below.
.webp)
Step 2: On the left bar you can see the permissions you can manage by using Azure Active Directory in this article we are going to cover how to create a user with required permissions based on the requirements.
.webp)
Step 3: Click on create a new user.
.webp)
Step 4: Configure all the basics need to create a user like a user principal name password and etc.
.webp)
Step 5: In the assignments, we can assign the roles and if we want we can add that user to any group with our requirements roles play a major role in the assigning of permissions which is like assigning the required permissions.
.webp)
Step 6: Last and final step review all the details of the users including passwords and click on Review+Create.
Managing User Properties In Azure AD
If the user is already created and you want to make the changes to the users based on the requirements then you can use the edit properties tag to make the changes according to your requirements as shown in the steps below.
Step 1: Select the user to whom you want to change the properties.
.webp)
Step 2: After clicking on the edit properties option you can change the name, user Id, and contact information depending on your requirements.
.webp)
Users, Groups, and Roles
Users, Groups, And Roles are three features that play a major role while coming to Azure Active Directory by which you can create a user or add the users to the groups and assign the roles to groups, users, and services.
Users
By using the Azure AD of users feature you can create a new user with all the permissions required for the user like how many services he can access and the level of permissions he can have. The users can be employees of the same organization or they can be freelancers with very less amount permissions. And also manages the permission to users for certain permissions which they can perform on Virtual Machines, Azure functions, Azure Logic Apps and etc.
Groups
A group is a collection of users, and a single person can be a member of multiple groups. With the aid of groups, we can manage permissions for many users quickly and efficiently. Instead of managing the permissions individually, you can merge all the users into one group and maintain the permission in bulk.
Roles and Administrators
In Azure AD, access is granted for privileged actions via administrative roles. For allowing access to handle wide application configuration permissions without granting access to manage other areas of Azure AD unrelated to application configuration, we advise using these built-in roles.
Difference Between Windows and Azure AD
|
Active Directory |
Azure Active Directory |
|---|---|
|
Azure Directory is used to maintain the permissions and users’ other requirements on the on-premises by using a local network. |
Azure Active Directory is used to maintain the permissions to the users and applications within the cloud with the help of a cloud network. |
|
By using the group policies you can administrators can maintain the permissions across the network |
Azure Active Directory servers as an Identity Provider for the Azure Cloud. |
|
The Azure Directory will have more features than the Azure Active Directory |
Azure Active Directory will have fewer features when compared to the Azure Directory but it was highly available with more scalability. |
Azure Active Directory Considerations
Here are the top considerations for the Azure active directory.
- Identity Management: Understand user and group management, and consider synchronization with on-premises Active Directory using Azure AD Connect for hybrid identity solutions.
- Security: Enhance security with multifactor authentication (MFA) and conditional access policies to control access based on user location, device state, and application sensitivity.
- Integration: Ensure seamless integration with existing applications, including SaaS, on-premises, and custom applications, and implement single sign-on (SSO) for streamlined user access.
- Compliance and Governance: Ensure Azure AD meets regulatory compliance requirements relevant to your industry and leverage auditing and reporting capabilities to monitor user activities and policy compliance.
- Licensing and Costs: Evaluate different Azure AD licensing plans to determine which features and services align with your needs, and manage costs associated with Azure AD services effectively.
Features Of Azure Active Directory
Some features of Azure Active Directory are lisred below:
- Authentication: To access various services, identification verification is necessary. Including capabilities like multifactor authentication and self-service password reset is also part of Azure AD.
- Single sign-on: With single sign-on (SSO), you can log into various applications with just one login and password.
- Application management: Using Azure AD, you can manage both your on-premises and cloud-based apps.
- Device management: Azure AD provides the registration of devices in addition to accounts for specific individuals. It also enables device-based Conditional Access restrictions to limit access attempts to only those coming from known devices.
Security of Azure Active Directory
Azure Active Directory is like an IAM(Identity Access Management) which is used to manage the permissions of users and applications and services. Following are some securities that will be followed by Azure Active Directory.
- Maintains Logs: Azure Active Directory will maintain the logs of each and every activity performed on the Azure services which will allow you to verify the logs and can check the there is any unauthorized access are there or any password changes.
- Data Security: Microsoft Azure will invest around USD 1 billion annually in cybersecurity research and development. And also there are 3,500 security experts who are dedicated to data security and privacy.
- Multi-Factor Authentication: Microsoft Azure will allow you to configure multifactor authentication for users and the applications by which the unauthorized access will be reduced so much.
- Azure Key Vaults: The password which you are using for the applications or users will be strongly encrypted with the help of Azure Key Vaults.
- Data Encryption: Azure Active Directory will encrypt the data which is transferred between the Azure database and application by this it will ensure that the data is not at all misused or stolen.
Common Attacks Against Azure AD
Common attacks against Azure Active Directory (Azure AD) include phishing, brute force attacks, password spray attacks, token theft, and privilege escalation. These attacks aim to compromise user credentials, exploit vulnerabilities, or gain unauthorized access to sensitive data within Azure AD. Organizations must implement robust security measures such as multifactor authentication (MFA), strong password policies, regular security assessments, and monitoring to mitigate the risk of such attacks and safeguard their Azure AD environment.
Pricing Of Azure Active Directory
The Azure Active Directory will come with the plan you are going to purchase depending on the plan you are going to get the features access to use some of them.
- Free Plan: In the free plan, you will get basic features like SSO (single sign-on) by which you into log into various applications with just one login and password.
- Basic Plan: The basic plan will cost you around 5 USD/Month where you will get access to features like SSO, password management, conditional access, application management
- Standard Plan: The standard plan will cost you around 12 USD/Month which will include all the features in the basic plan and extra some other features like plus identity governance, and self-service password reset.
- premium Plan: The premium plan will cost you 20 USD/Month it consists of the features of Basic, Standard plans and with extra it will have the plus advanced auditing and reporting
Benefits Of Using Azure AD
- Data Protection: The protection of data will be increased by using Azure AD it will restrict the users, and services from accessing the resources which are available in Azure Cloud without permission.
- Remote Access: Once you created the user and give the credentials to the employee he can access Microsoft Azure from anywhere in the world without any threats.
- Easy Reset of Password: Azure AD will allow users to reset their password without any help from the IT desk by following some simple steps.
- Identity Protection and Grovence: Azure AD will protect unusual logins you can manage the user accounts of multiple employees from a single place.
- Cost: Azure AD will charge only for the service you are going to use you can purchase the subscription plan based on your organization’s needs.




