,
If you cannot connect to your L2TP/IPsec VPN server from Windows 10, continue reading below to solve the problem.
VPN connection errors can be caused by a variety of causes, but are usually due to incorrect settings of the VPN connection (e.g. incorrect server name/address, authentication method, username or password). So the first step to troubleshoot VPN connection problems, is to verify that all the VPN settings are correct.
This tutorial contains instructions to solve the following errors, while trying to connect to L2TP/IPsec VPN server in Windows 10 or Windows Server 2012/2016:
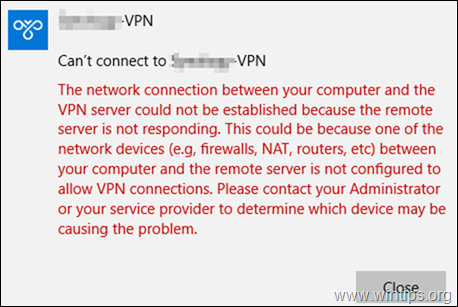
- The network connection between your computer and the VPN server could not be established because the remote server is not responding. This could be because one of the network devices (e.g. firewalls, NAT, routers, etc) between your computer and the remote server is not configured to allow VPN connections. Please contact your Administrator or your service provider to determine which device may be causing the problem.
-
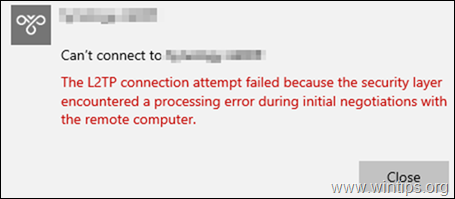
The L2TP connection attempt failed because the security layer encountered a processing error during the initial negotiations with the remote computer.
How to FIX: Can’t connect to VPN. L2TP connection between your computer and the VPN server could not be established on Windows 10.
Before continue to the instructions below, apply the following actions: *
* Important: If the problem started in January 2022, see the following article first:
- Related Article: FIX: The L2TP connection attempt failed because the security layer encountered a processing error during initial negotiations with the remote computer.
1. Ensure that the Required L2TP/IPsec Ports are enabled on VPN Server’s side.
Login to the Router on VPN Server’s side, and forward the following UDP ports to VPN Server’s IP address: 1701, 50, 500 & 4500
2. Connect to VPN via another device or network.
Try connecting to L2TP VPN from another device (e.g. your mobile), or network (e.g. your Mobile’s phone network).
3. Delete and recreate the VPN connection.
Sometimes VPN connection problems, are resolved after removing and re-adding the VPN Connection.
If, after the above steps, you are still unable to connect to your l2tp/IPsec VPN server from your Windows 10 computer, apply the following modifications to the registry and the VPN connection.
STEP 1. ALLOW L2TP CONNECTIONS BEHIND NAT.
By default, Windows do not support L2TP/IPsec connections if the computer or the VPN server are located behind a NAT. To bypass this problem modify registry as follows:
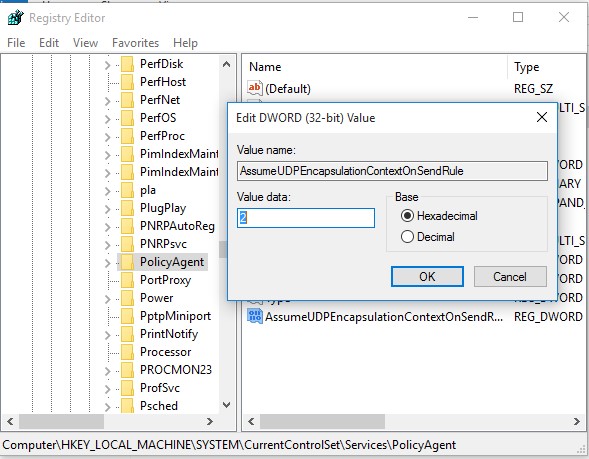
1. Open Registry Editor. To do that:
1. Simultaneously press the Win + R keys to open the run command box.
2. Type regedit and press Enter to open Registry Editor.
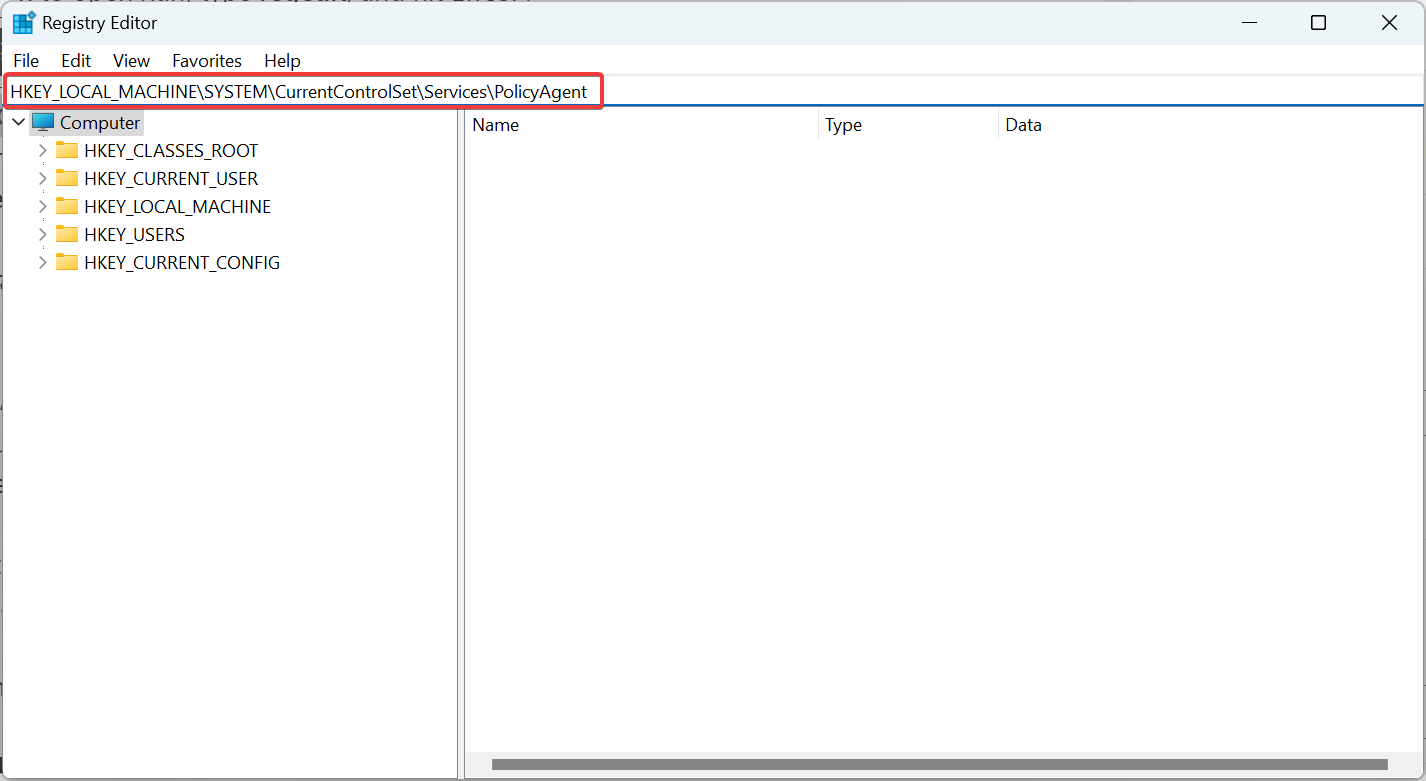
2. At the left pane, navigate to this key:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Sevices\PolicyAgent
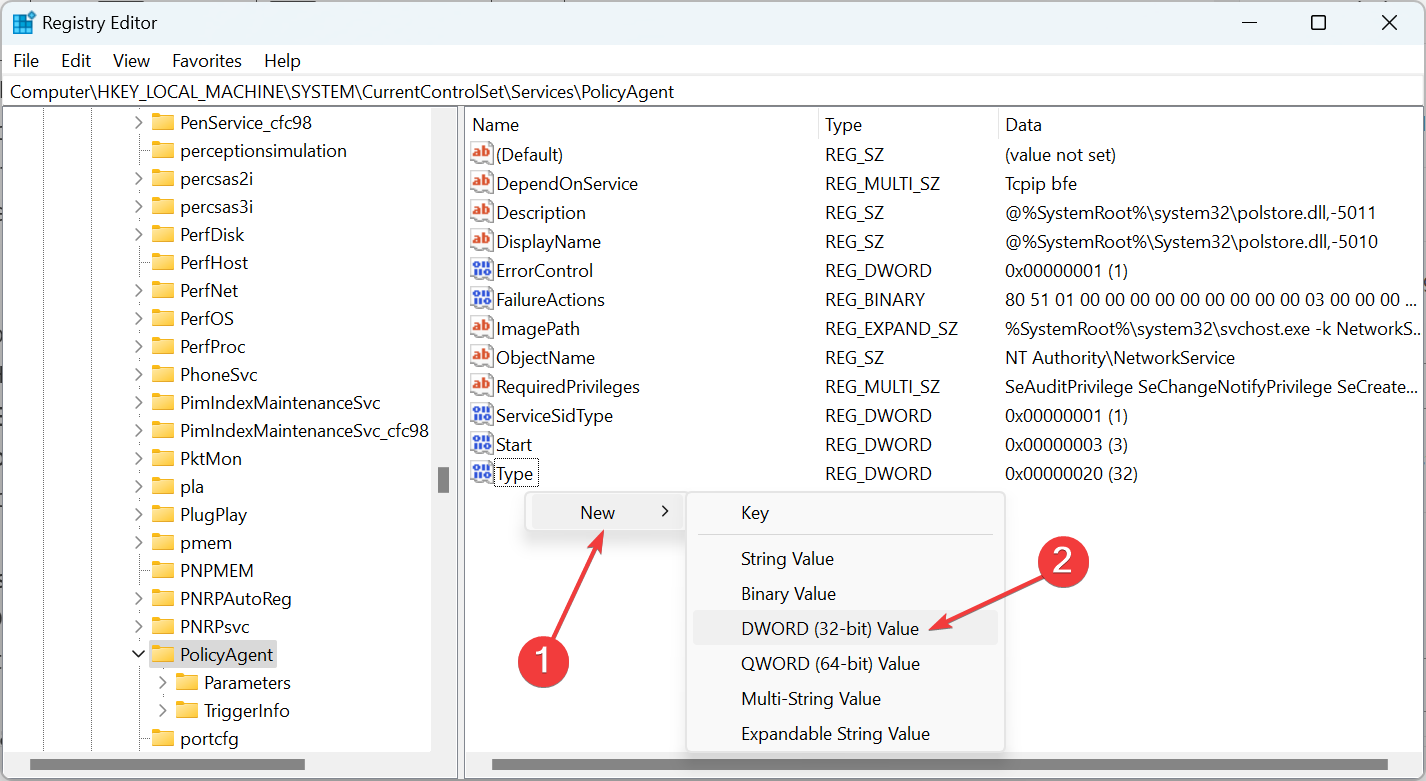
3. Right click at an empty space at the right pane and select New –> DWORD (32 bit) Value.
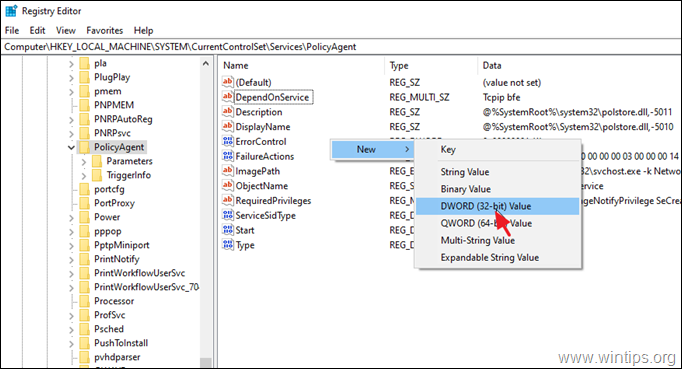
4. For the new key name type: AssumeUDPEncapsulationContextOnSendRule and press Enter.
* Note: The value must be entered as shown above and with no space at the end.
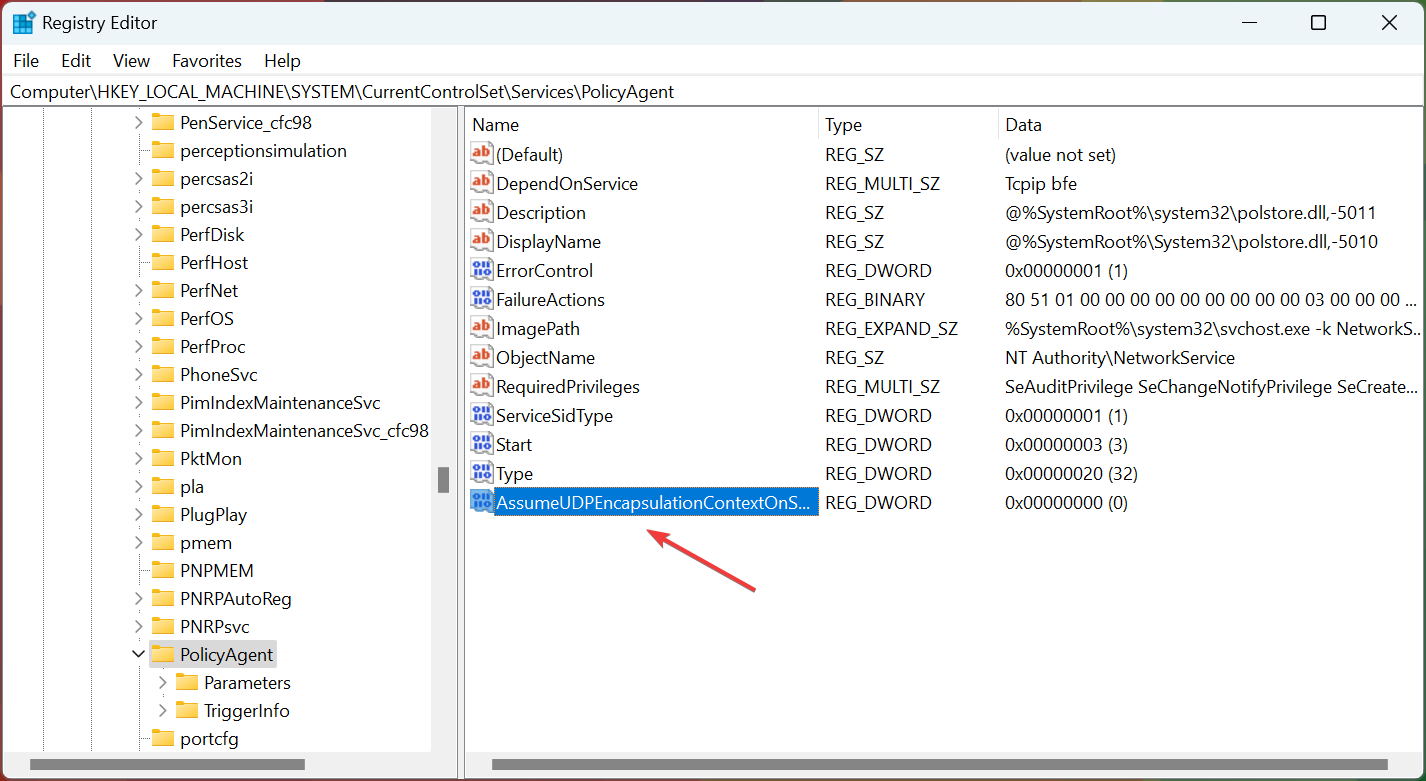
5. Double click at AssumeUDPEncapsulationContextOnSendRule value, type 2 at Value data and click OK.
6. Close Registry Editor and reboot the machine.
Step 2. Modify Security Settings on VPN Connection.
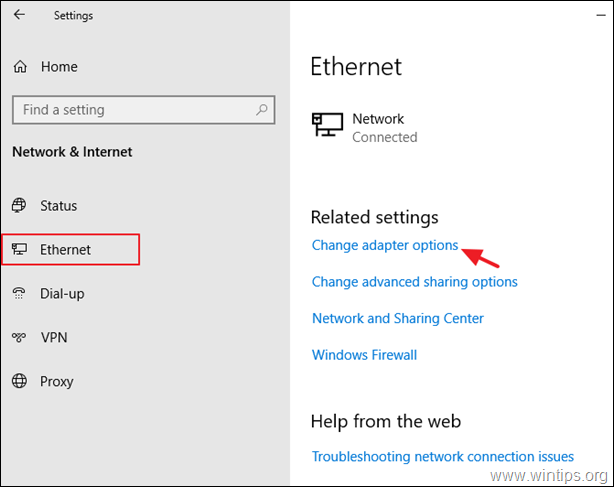
1. Right-click at the Network icon on the taskbar and choose Open Network & Internet settings.
* Note: Alternatively, go to Start > Settings click Network and Internet.
2. Select Ethernet on the left and then click Change adapter options on the right.
3. Right-click on the VPN connection and chose Properties.
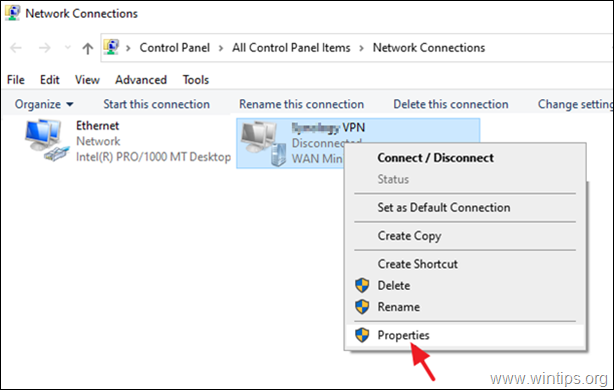
4a. At Options tab, click PPP Settings.
4b. Check Enable LCP extensions and click OK.
4c. At Security tab, check the following and click OK.
- Allow these protocols
- Challenge Handshake Authentication Protocol (CHAP)
- Microsoft CHAP Version 2 (MS-SHAP v2)
5. Try to connect to VPN. The connection should be established now without problems. *
ADDITIONAL HELP: If after applying the above steps you still have a problem, try the following:
1. Check that the following services are enabled (Startup type: Automatic)
-
- IKE and AuthIP IPsec Keying Modules
- IPsec Policy Agent
2. If you’re using a third-party firewall program, try to disable it or to completely uninstall it before connecting to VPN.
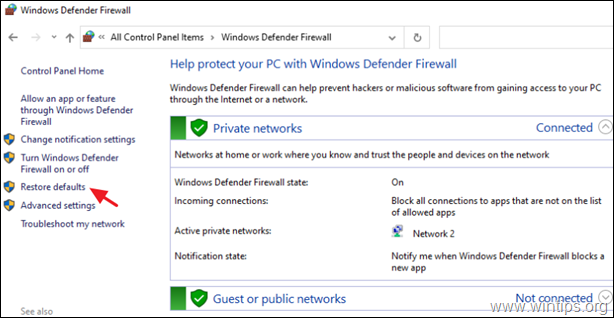
3. Try to reset the Windows Firewall settings to their default. To do that, go to Control Panel > Windows Defender Firewall and click Restore defaults.
4. Delete and recreate the VPN connection.
5. Reboot the router on VPN’s server side.
That’s it! Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:
- Author
- Recent Posts
Konstantinos is the founder and administrator of Wintips.org. Since 1995 he works and provides IT support as a computer and network expert to individuals and large companies. He is specialized in solving problems related to Windows or other Microsoft products (Windows Server, Office, Microsoft 365, etc.).
В этой статье мы рассмотрим типовые причины ошибок при подключении к L2TP/IPSec VPN серверу с клиентов Windows 10/11 и Windows Server 2019/2016. Если вы не можете установить L2TP VPN подключение к Windows, внимательно посмотрите на код и описание ошибки. Там часто указывается причина ошибки.
Содержание:
- Не удается установить связь между компьютером и VPN сервером L2TP/IPScec
- Разрешить подключение к L2TP/IPSec VPN серверу за NAT
- Подключение L2TP не удалось из-за ошибки согласования безопасности
Не удается установить связь между компьютером и VPN сервером L2TP/IPScec
При попытке установить соединение из клиента Windows к L2TP VPN серверу появляется ошибка:
Can’t connect to ваше_L2TP_IPSec_VPN_подключение The network connection between your computer and the VPN server could not be established because the remote server is not responding. This could be because one of the network devices (e.g. firewalls, NAT, routers, etc) between your computer and the remote server is not configured to allow VPN connections. Please contact your Administrator or your service provider to determine which device may be causing the problem.
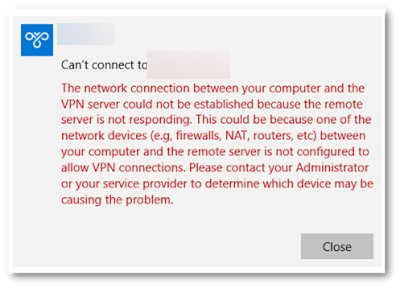
Не удалось установить связь по сети между компьютером и VPN-сервером, так как удаленный сервер не отвечает. Возможная причина: одно из сетевых устройств (таких как брандмауэры, NAT, маршрутизаторы и т.п.) между компьютером и удаленным сервером не настроено для разрешения VPN-подключений. Чтобы определить, какое устройство вызывает эту проблему, обратитесь к администратору или поставщику услуг.
Чаще всего при этом появляются следующие коды ошибок: 800, 794 или 809.
Если появилась такая ошибка, нужно проверить что вы указали правильный адрес VPN сервера, VPN сервер доступен и в файерволах открыты все необходимые порты.
Для доступа к L2TP/IPsec VPN сервере должны быть открыты следующие порты:
- UDP порт 1701 (Layer 2 Forwarding Protocol (L2F) & Layer 2 Tunneling Protocol (L2TP))
- UDP порт 500 (IKE, для управления ключами шифрования)
- Протокол ESP 50 (Encapsulating Security Payload) для IPSec
- Если VPN сервер находится за NAT, нужно дополнительно открыть UDP порт 4500 (протокол NAT-T, IPSec Network Address Translator Traversal)
Для подключения к L2TP VPN серверу можно использовать встроенный VPN клиент Windows. Проверьте настройки вашего VPN подключения. Убедитесь, что для VPN подключения используется туннель L2tp и pre-shared key (PSK)/сертификат для аутентификации. Настройки VPN подключения можно вывести с помощью PowerShell:
Get-VpnConnection
Разрешить подключение к L2TP/IPSec VPN серверу за NAT
Если целевой L2TP VPN сервер находится за NAT, то с настройками по-умолчанию вы не сможете установить подключение к нему с компьютера Windows. Дело в том, что протокол IPsec не поддерживает NAT. Для обхода этого ограничения используется протокол NAT-T, который инкапсулирует пакеты IPsec в UDP/4500.
IPSec использует протокол ESP (Encapsulating Security Payload) для шифрования пакетов, а протокол ESP не поддерживает PAT/ Port Address Translation.
NAT-T включен по-умолчанию почти во всех операционных системах (iOS, Android, Linux), кроме Windows.
Если VPN сервер L2TP/IPsec находится за NAT, то для корректного подключения внешних клиентов через NAT необходимо как на сервере, так и на клиенте Windows внести изменение в реестр, разрешающее UDP инкапсуляцию пакетов для L2TP и поддержку (NAT-T) для IPsec.
- Откройте редактор реестра
regedit.exe
и перейдите в ветку:- Для Windows 10,8.1,7 и Windows Server 2016,2012R2,2008R2 — HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent
- Для Windows XP/Windows Server 2003 — HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\IPSec
- Создайте DWORD параметр с именем AssumeUDPEncapsulationContextOnSendRule и значением 2;
Примечание. Возможные значения параметра AssumeUDPEncapsulationContextOnSendRule:
- 0 – (значение по-умолчанию), предполагается, что VPN сервер подключен к интернету без NAT;
- 1 – VPN сервер находится за NAT;
- 2 — и VPN сервер и клиент находятся за NAT.
- Осталось перезагрузить компьютер и убедиться, что VPN туннель успешно создается.
Если и Windows VPN сервер и клиент находятся за NAT, нужно изменить это параметре на обоих системах.
Можно использовать командлет PowerShell для внесения изменений в реестр:
Set-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Services\PolicyAgent" -Name "AssumeUDPEncapsulationContextOnSendRule" -Type DWORD -Value 2 –Force
После включения поддержки NAT-T, вы сможете успешно подключаться к VPN серверу с клиента через NAT (в том числе двойной NAT). В этом случае при установлении L2TP/IPsec подключения сначала создается зашифрованный IPsec-канал (используется протокол IKE: UDP/500 и NAT-T: UDP/4500). После этого уже внутри IPsec поднимается туннель L2TP на порт 1701 UDP. Это означает, что, если VPN сервер находится за NAT, вам не нужно пробрасывать на него порт 1701 UDP с внешнего роутера/маршрутизатора.
Подключение L2TP не удалось из-за ошибки согласования безопасности
Есть еще один интересный баг. Если в вашей локальной сети несколько Windows компьютеров, вы не сможете установить более одного одновременного подключения к внешнему L2TP/IPSec VPN серверу. Если при наличии активного VPN туннеля с одного клиента, вы попытаетесь подключиться к тому же самому VPN серверу с другого компьютера, появится ошибка с кодом 809 или 789:
Error 789: The L2TP connection attempt failed because the security layer encountered a processing error during initial negotiations with the remove computer.
Попытка L2TP-подключения не удалась из-за ошибки, произошедшей на уровне безопасности во время согласований с удаленным компьютером. (Ошибка 789)
Что интересно, эта проблема наблюдется только с Windows-устройствами. На устройствах с Linux/MacOS/Android в этой же локальной сети таких проблем нет. Можно без проблем одновременно подключиться к VPN L2TP серверу с нескольких устройств.
По информации на TechNet проблема связана с некорректной реализацией клиента L2TP/IPSec клиента в Windows (не исправляется уже много лет).
Для исправления этого бага нужно изменить два параметра реестра в ветке HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasMan\Parameters и перезагрузите компьютре:
- AllowL2TPWeakCrypto – изменить на 00000001 (ослабляет уровень шифрования, для L2TP/IPSec используются алгоритмы MD5 и DES)
- ProhibitIPSec – изменить на 00000000 (включает шифрование IPsec, которое часто отключается некоторыми VPN клиентами или утилитами)
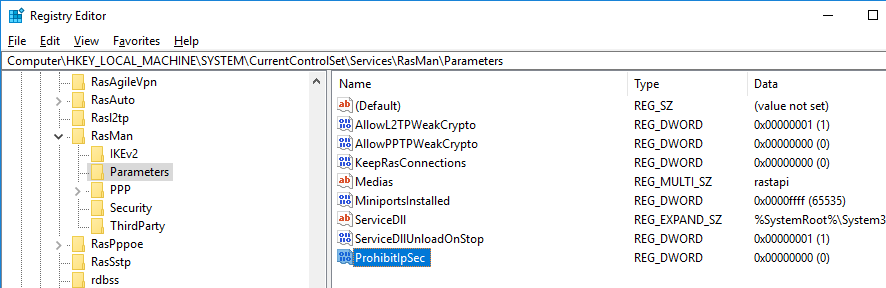
Для изменения этих параметров реестра достаточно выполнить команды:
reg add "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters" /v AllowL2TPWeakCrypto /t REG_DWORD /d 1 /f
reg add "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters" /v ProhibitIpSec /t REG_DWORD /d 0 /f
Это включает поддержку нескольких одновременных L2TP/IPSec-подключений в Windows через общий внешний IP адрес (работает на всех версиях, начиная с Windows XP и заканчивая Windows 10/11).
Еще несколько советов, которые помогут вам исправить проблему с L2TP VPN подключением в Windows
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
VPNs have, of late, gained tremendous importance in day-to-work, and are used by several users. But many of them report that they cannot connect to L2TP VPN in Windows 10.
L2TP is one of the most secure VPN protocols. It supports 256-bit encryption, which privacy experts highly recommend. Besides, the speed remains largely unaffected, and users get a stable connection. So, let’s find out all about the issue.
Why is my L2TP VPN not working?
Here are a few reasons you cannot connect to L2TP VPN in Windows 10:
- Incorrect username or password: The most likely reason you face issues with the connection is inaccurate authentication details.
- Misconfigured settings: Even misconfigured network or VPN settings can trigger issues and prevent the VPN from working effectively.
- Wrong server address: Some users found out that they had input an incorrect server address and were, as a result, unable to connect to L2TP VPN in Windows 10.
- Connection blocked by the firewall: A built-in or third-party firewall can often block connections it deems risky, and you need to modify the rules for things to work out.
Quick Tip:
Use a premium VPN instead. If you keep having problems with your current configuration, consider using a dedicated VPN app that’s way easier to configure.
ExpressVPN is a great alternative that supports L2TP/IPsec. The only thing you have to do is to install it and select the protocol in one click from settings.
ExpressVPN
Connect to ExpressVPN using its L2TP/IPsec protocol and get high-speed connections without errors!
What can I do if I cannot connect to L2TP VPN in Windows 10?
Before we head to the slightly complex solutions, try these quick ones first:
- Restart the computer and then try connecting to the VPN.
- Check the user name and password for the VPN connection. Also, verify with the administrator if these were recently changed, and use the new ones.
- Ensure you entered the correct server address and the Pre-shared key (if applicable).
- Check for updates and install any pending ones for Windows 10.
If none of these work, move to the fixes listed below.
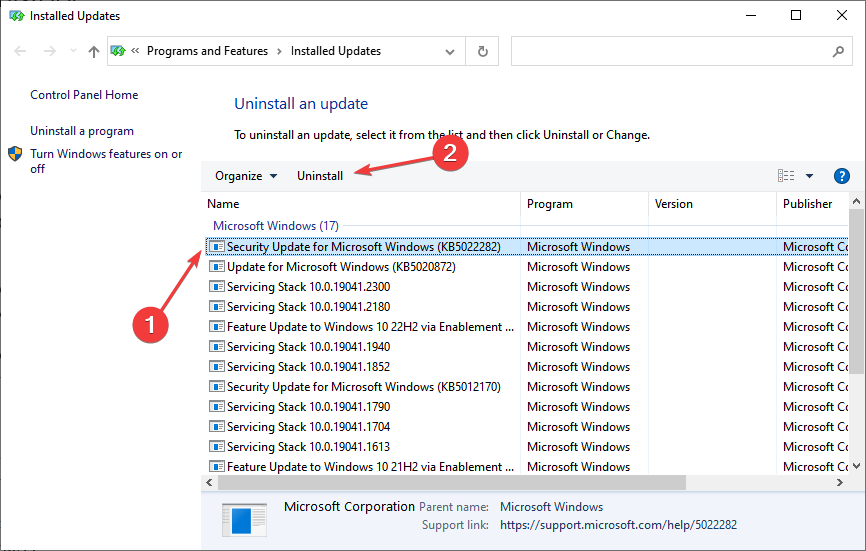
1. Uninstall recent Windows Update
- Press Windows + I to open Settings, and then click on Update & Security.
- Click on View update history.
- Now, click on Uninstall updates.
- Choose the update installed around the same time the issue first appeared, and click on Uninstall.
- Click on Yes in the confirmation prompt to proceed.
When you cannot connect to L2TP VPN in Windows 10, the first to check for is a buggy update since this has happened in the past. Verify whether others, too, are facing the same problem, and if that’s the case, uninstall the update.
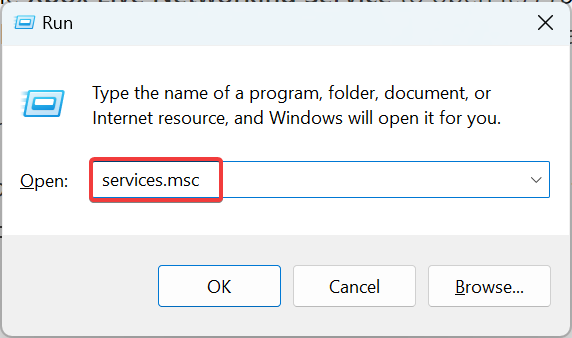
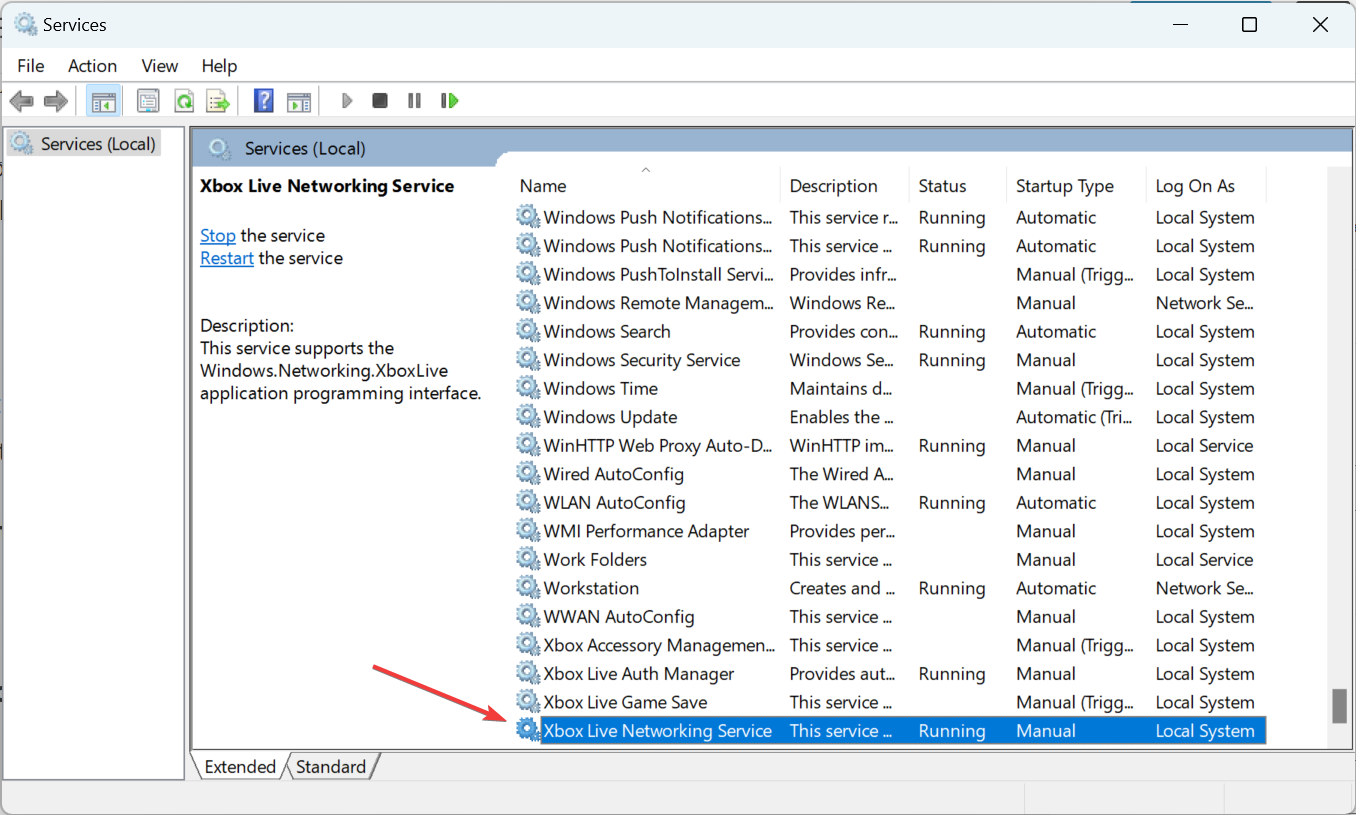
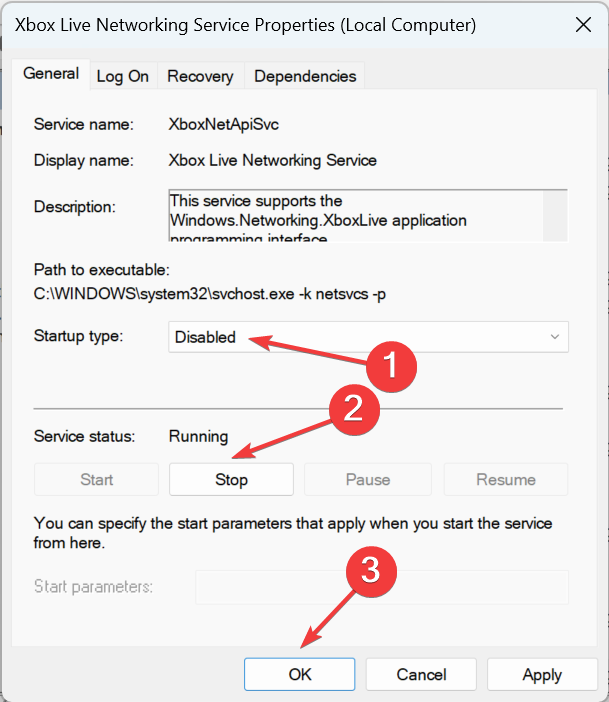
2. Disable Xbox Live Networking Service
- Press Windows + R to open Run, type services.msc, and then hit Enter.
- Locate and double-click on the Xbox Live Networking Service to open its Properties
.
- Now, choose Disabled from the Startup type dropdown menu, click on Stop, and then on OK to save the changes.
- Once done, restart the computer.
Many users found out that the Xbox Live Networking Service, for some reason, created conflicts and, as a result, they cannot connect to L2TP VPN in Windows 10.
3. Change the VPN settings
- Press Windows + R to open Run, type ncpa.cpl, and click OK.
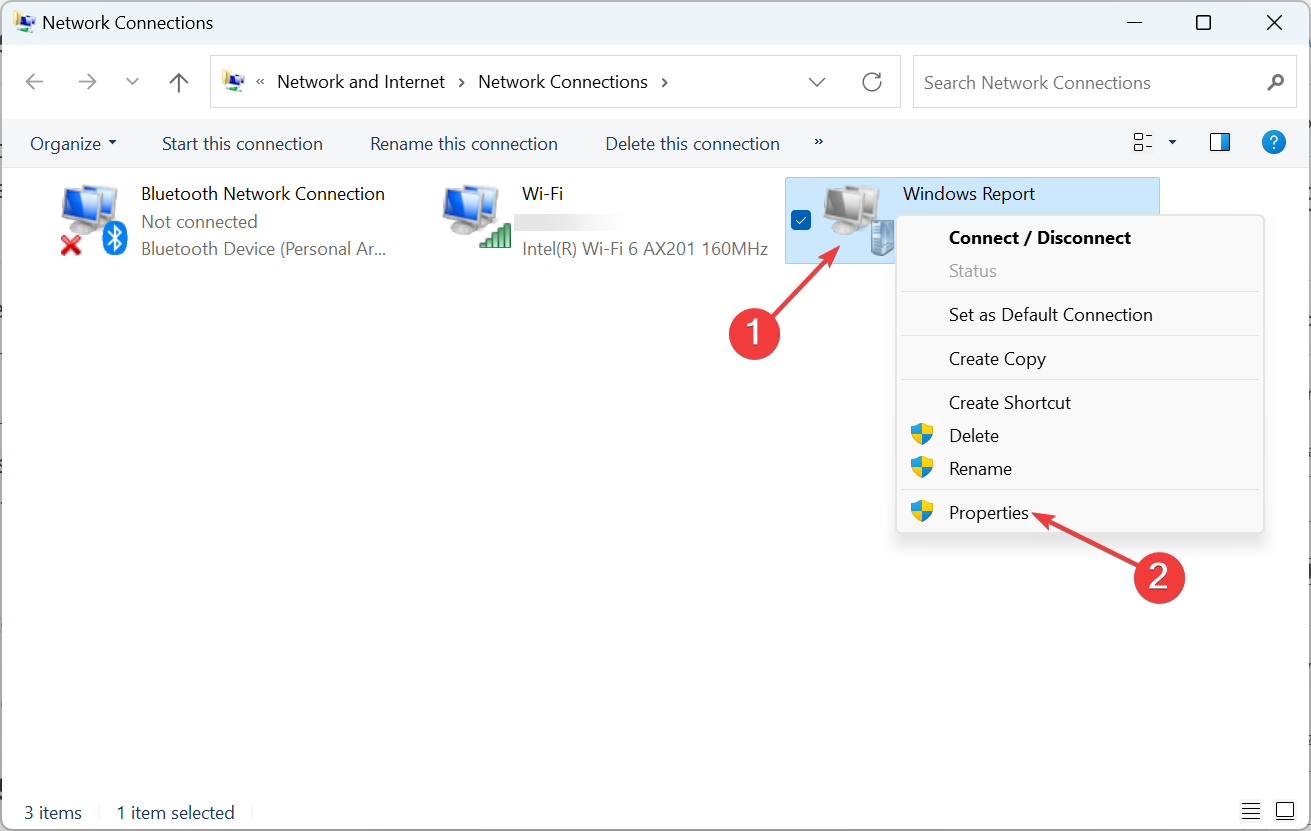
- Right-click on the VPN, and choose Properties.
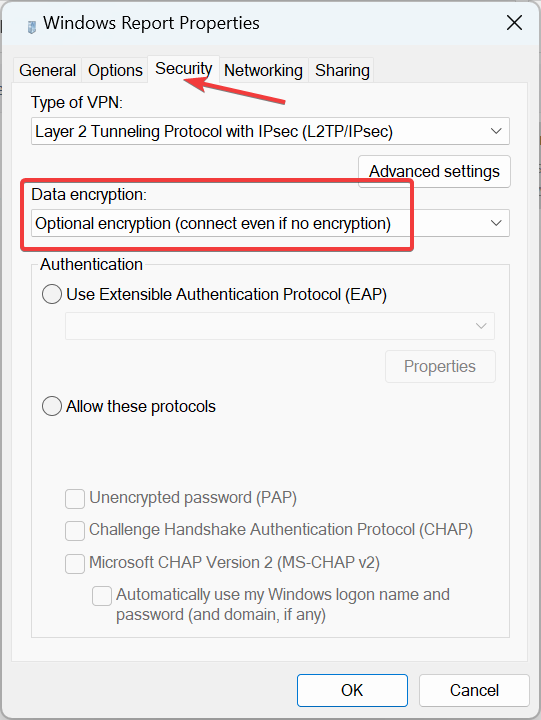
- Navigate to the Security tab, and then choose Optional encryption (connect even if no encryption) from the Data encryption dropdown menu.
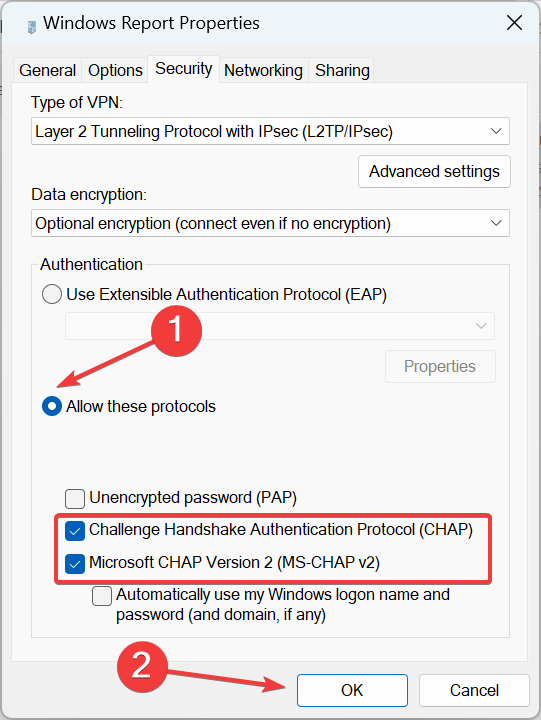
- Now, select Allow these protocols, tick the checkboxes for Challenge Handshake Authentication Protocol (CHAP) and Microsoft CHAP Version 2 (MS-CHAP v2), and then click OK to save the changes.
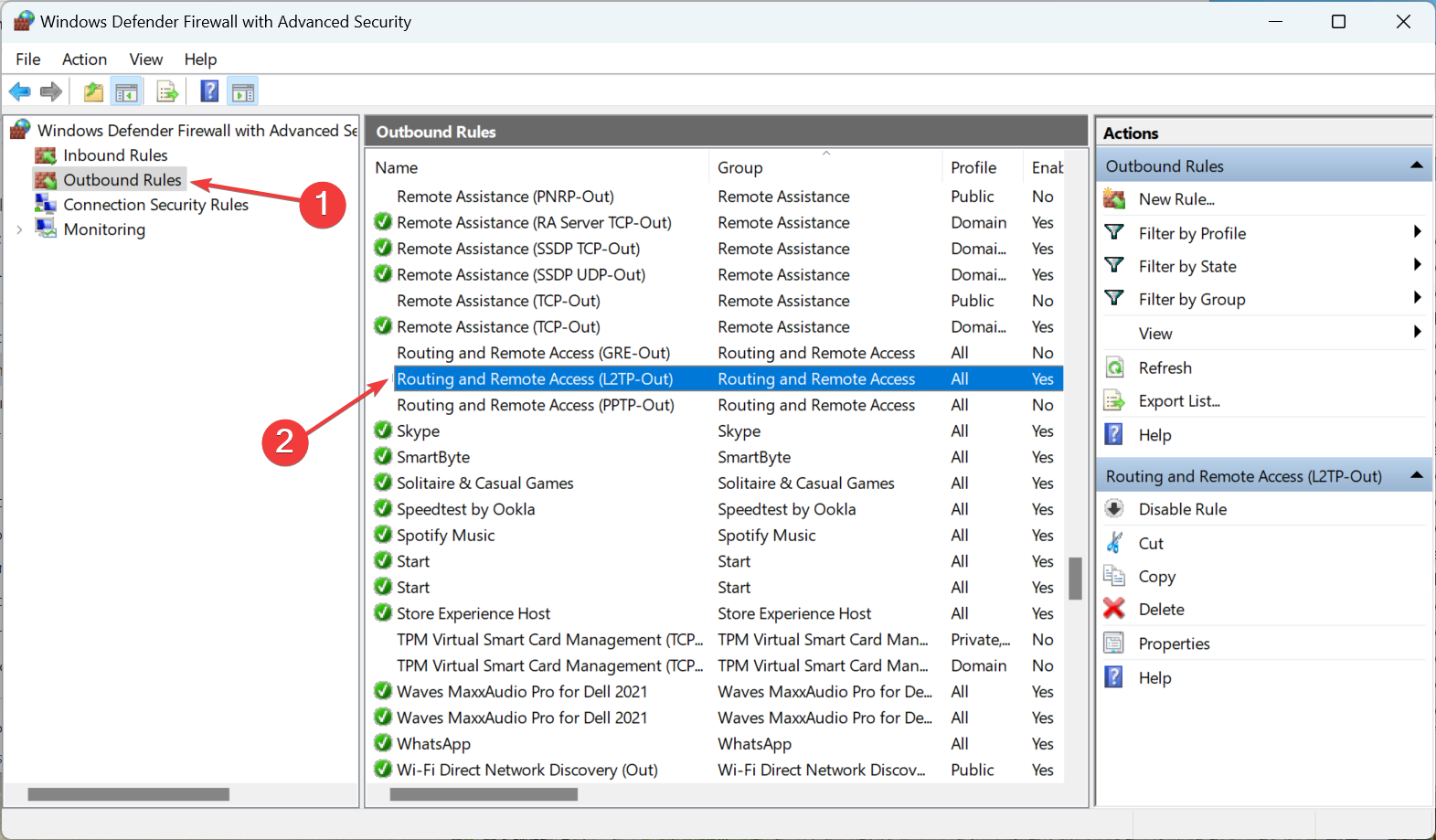
4. Change the firewall rules
- Press Windows + S to open Search, type Windows Defender Firewall in the text field, and click on the relevant search result.
- Click on Advanced settings on the left.
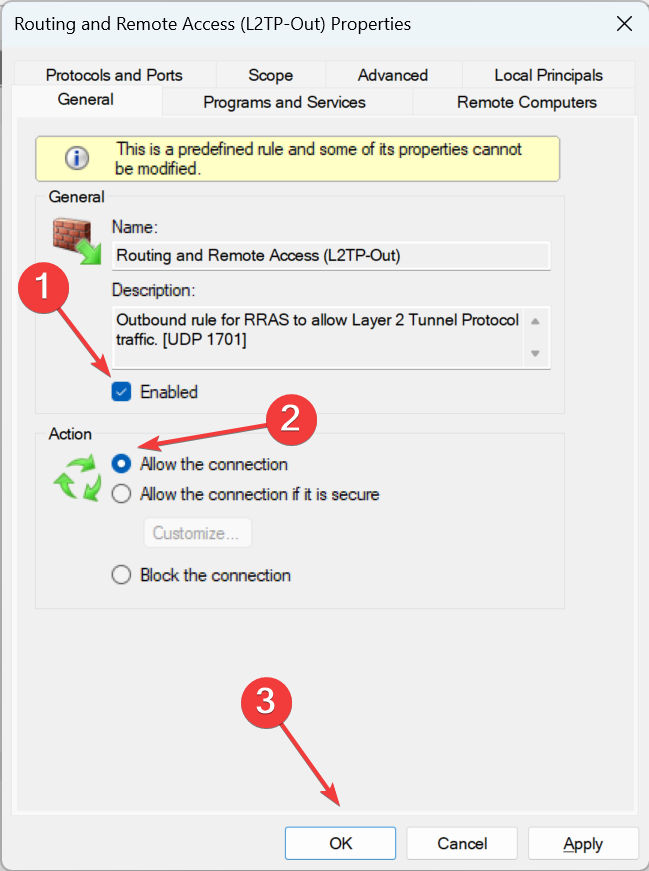
- Choose Outbound Rules from the navigation pane, and double-click on Routing and Remote Access (L2TP-Out).
- Tick the checkbox for Enabled, then under Action, enable Allow the connection, and click OK to save the changes.
In many cases, the firewall is the underlying cause when you cannot connect to L2TP VPN in Windows 10, and simply changing the rules should do the trick.
5. Modify the Registry
- Press Windows + R to open Run, type regedit, and hit Enter.
- Click Yes in the UAC prompt.
- Paste the following path in the address bar and hit Enter:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent - Right-click on the empty portion, hover the cursor over New, select DWORD (32-bit) Value, and name it AssumeUDPEncapsulationContextOnSendRule.
- Double-click on the newly created DWORD.
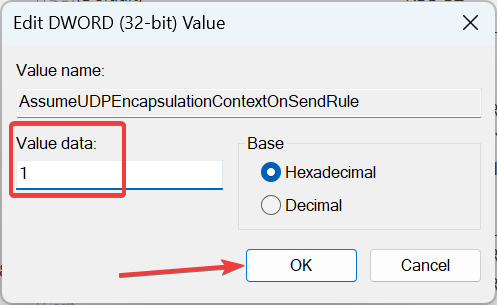
- Enter 1 under Value data, and click on OK.
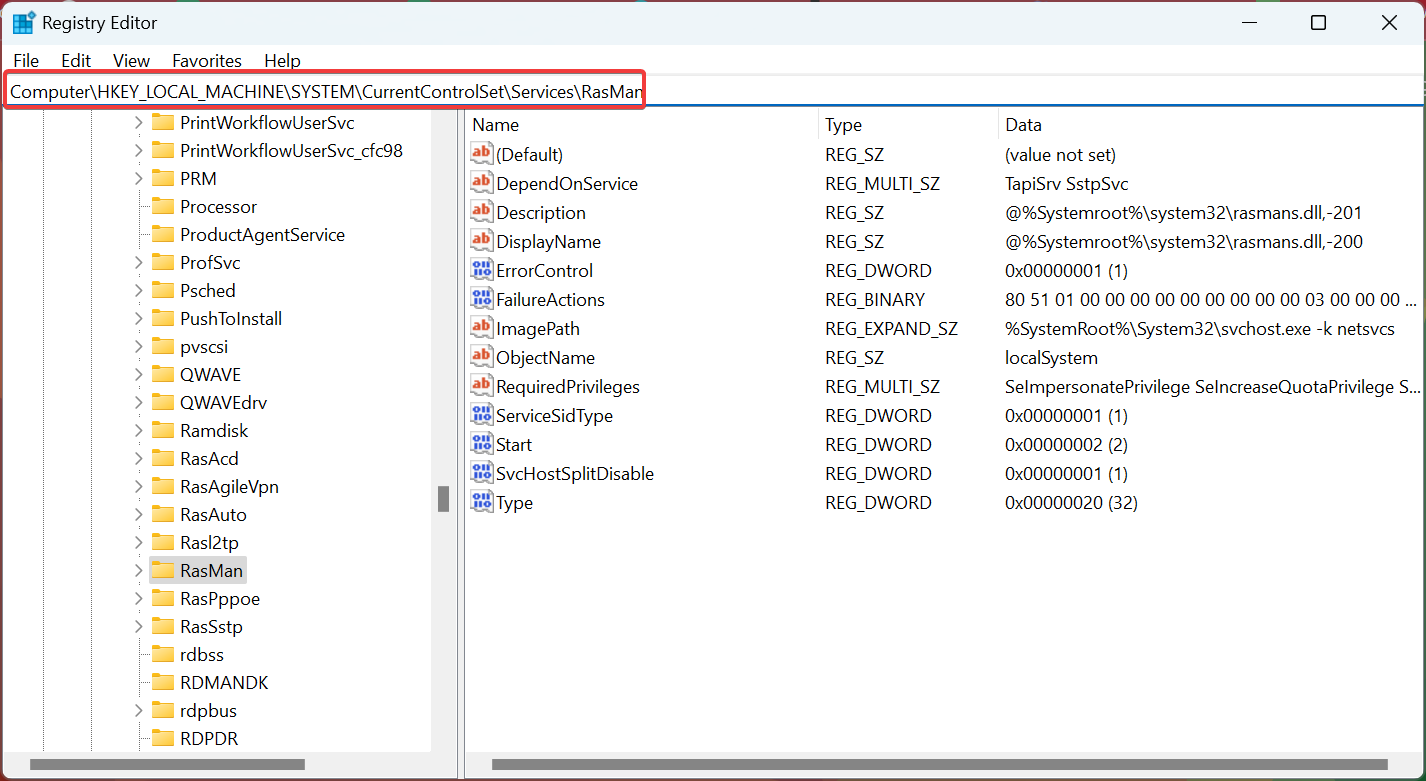
- Next, paste the following path and hit Enter:
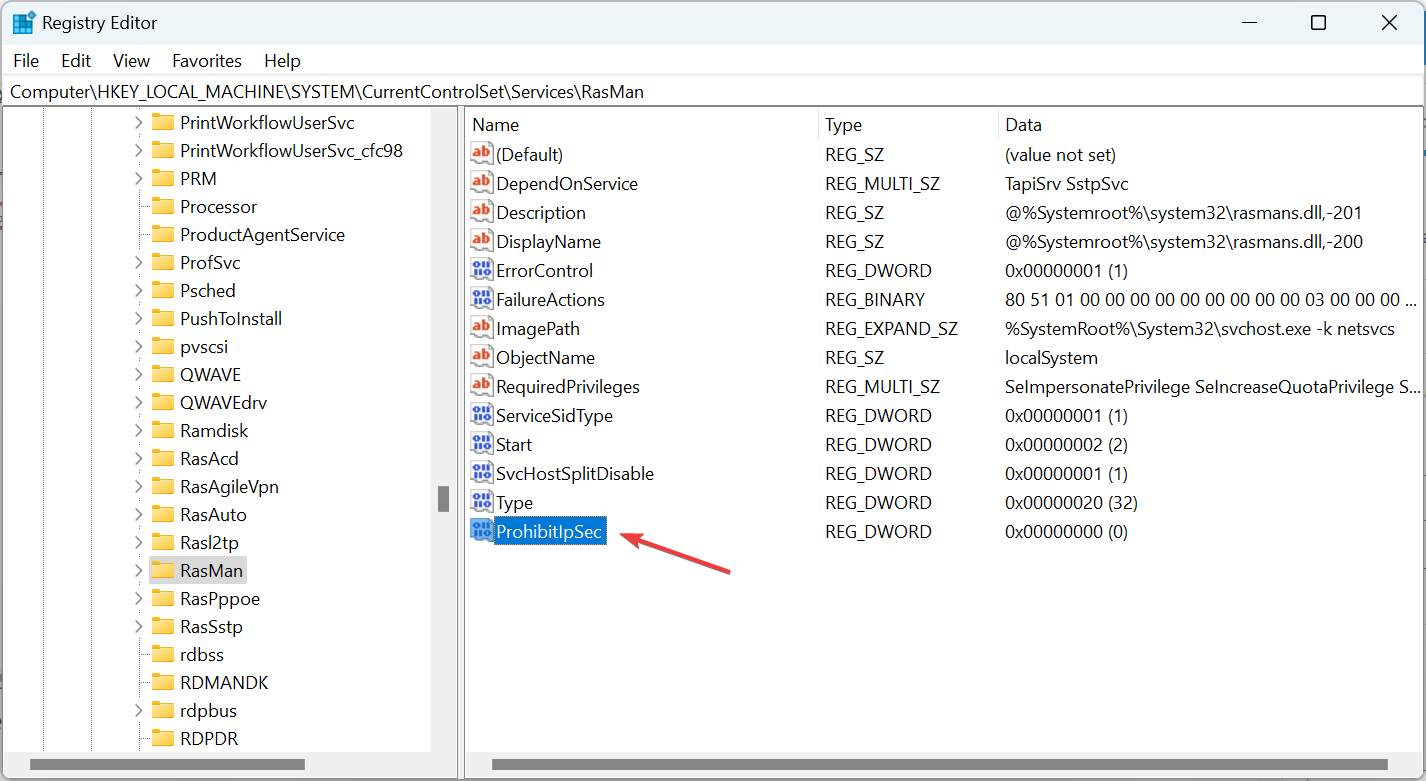
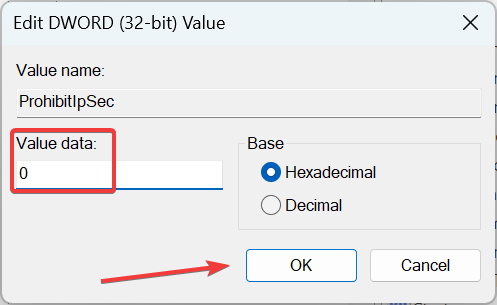
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasMan - Create a new DWORD (32-bit) Value, name it ProhibitIpSec as the value name, and then double-click on it.
- Set 0 as the Value data, and click on OK.
- Finally, restart your computer for the changes to apply.
The Registry fix is found to be highly effective when you cannot connect to L2TP VPN in Windows 10 and worked for many.
Also, if 1 does not work as the Value data for AssumeUDPEncapsulationContextOnSendRule, enter 2 the next time, and the error should be gone.
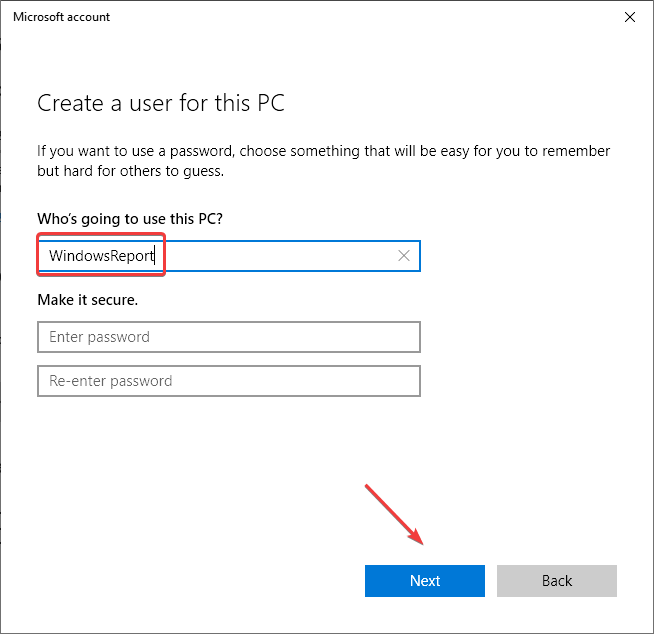
6. Create a new user account
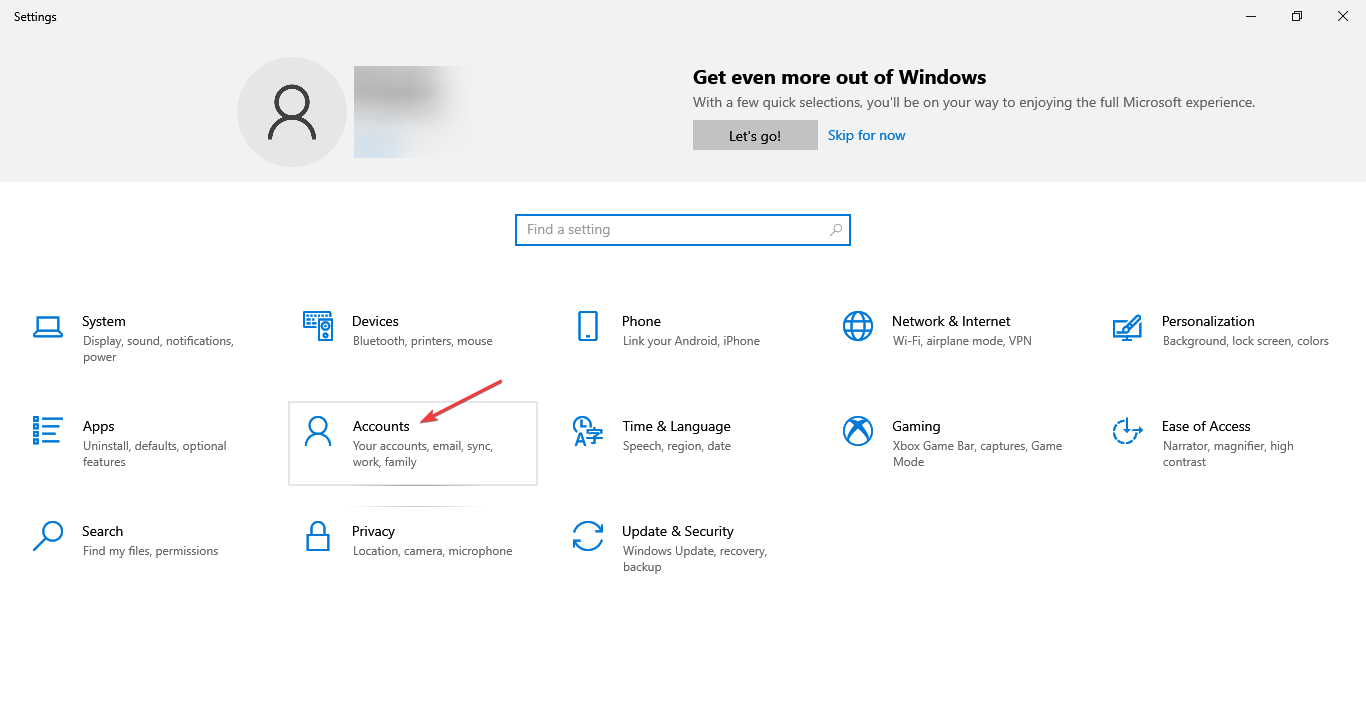
- Press Windows + I to open Settings, and click on Accounts.
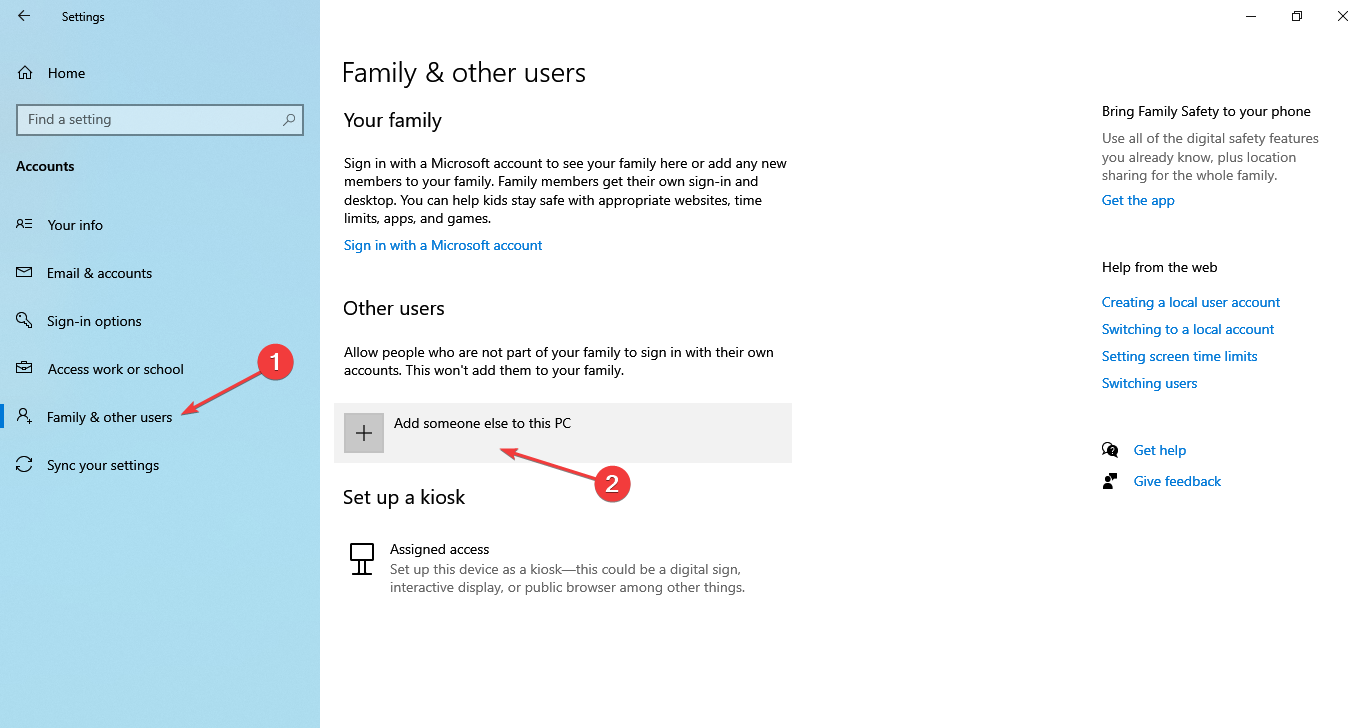
- Go to the Family & other users tab, and click on Add someone else to this PC.
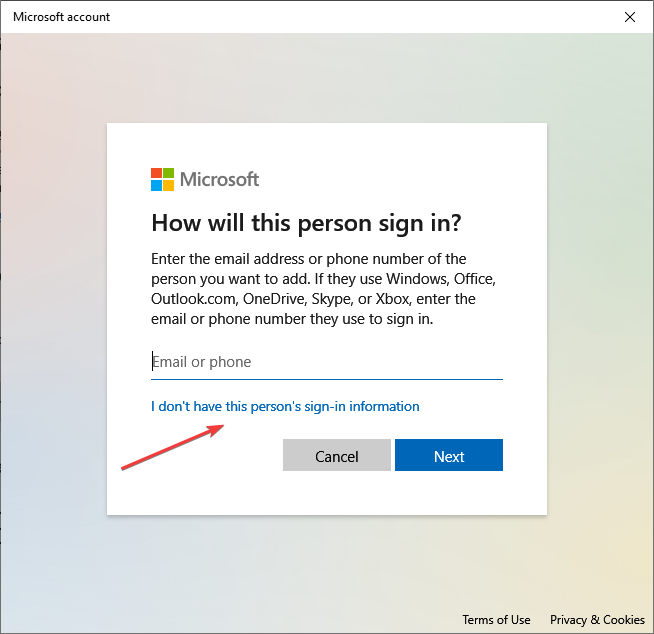
- Choose the I don’t have this person’s sign-in information option.
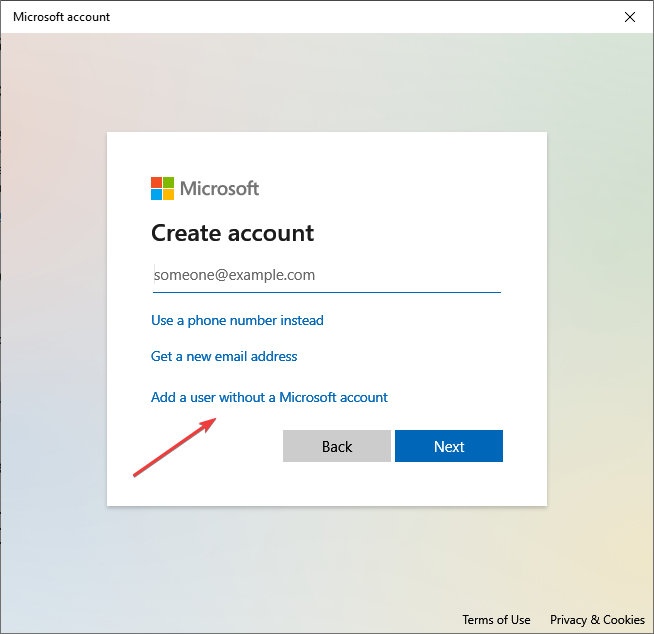
- Next, click on Add a user without a Microsoft account.
- Enter a username (mandatory) and a password (optional), and then click on Next to create an account.
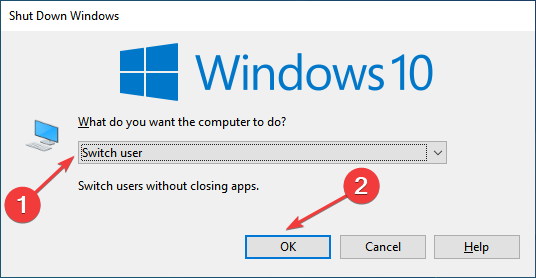
- Once done, press Alt + F4, select Switch user from the dropdown menu, and click OK
.
- Now, log in to the new account, and connect to the VPN.
If nothing helps and you still cannot connect to L2TP VPN in Windows 10, the last option is to create a new user account. It should, in all likelihood, fix the problem.
However, if you don’t want to worry about such problems anymore, we suggest using ExpessVPN instead. It’s also the best VPN for Google Chrome.
Tell us which fix worked for you in the comments section below.
Elena Constantinescu
Windows Software Expert
Elena started writing professionally in 2010 and hasn’t stopped exploring the tech world since. With a firm grasp of software reviewing and content editing, she is always trying new things to improve her skill set.
Once in a blue moon, she steps aside from the desk to play with her bunny and to water her probably dead plants.
L2TP/IPsec is a popular VPN protocol built-in to most modern platforms including Microsoft Windows 10. Using a built-in protocol can be a good choice as you do not have to install any extra applications or worry if they are written securely and bug free. Depending on your provider’s software they can be a little trickier to set up as you need to manually enter in your VPN configuration.
The following tutorial with plenty of screenshots will show you how to set up a L2TP/IPsec VPN on Windows 10 using the built-in capabilities of the operating system.
Step 1: Open Network settings
Click on the Network icon on the taskbar and then click on Network settings.
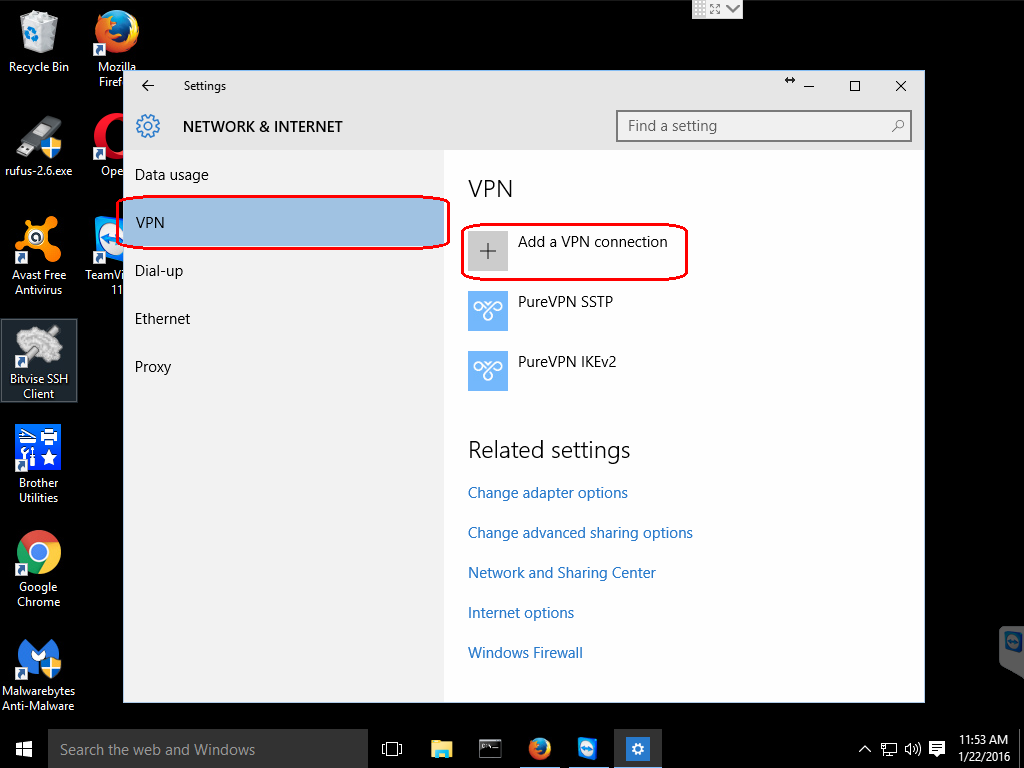
Step 2: Add a VPN connection
Click on the VPN option and then click on the Add a VPN connection.
Step 3: Configure VPN connection
- Left-click the VPN provider drop down menu and select Windows (built-in).
- Click on the Connection name box and enter a name for your connection.
- Click the Server name or address box and enter a FQDN or IP address for your VPN server. Your VPN provider should have a list of their servers available on their website.
- Click the VPN type drop down menu and select Layer 2 Tunneling Protocol with IPsec (L2TP/IPsec).
- Click the Type of sign-in info drop down menu and select User name and password.
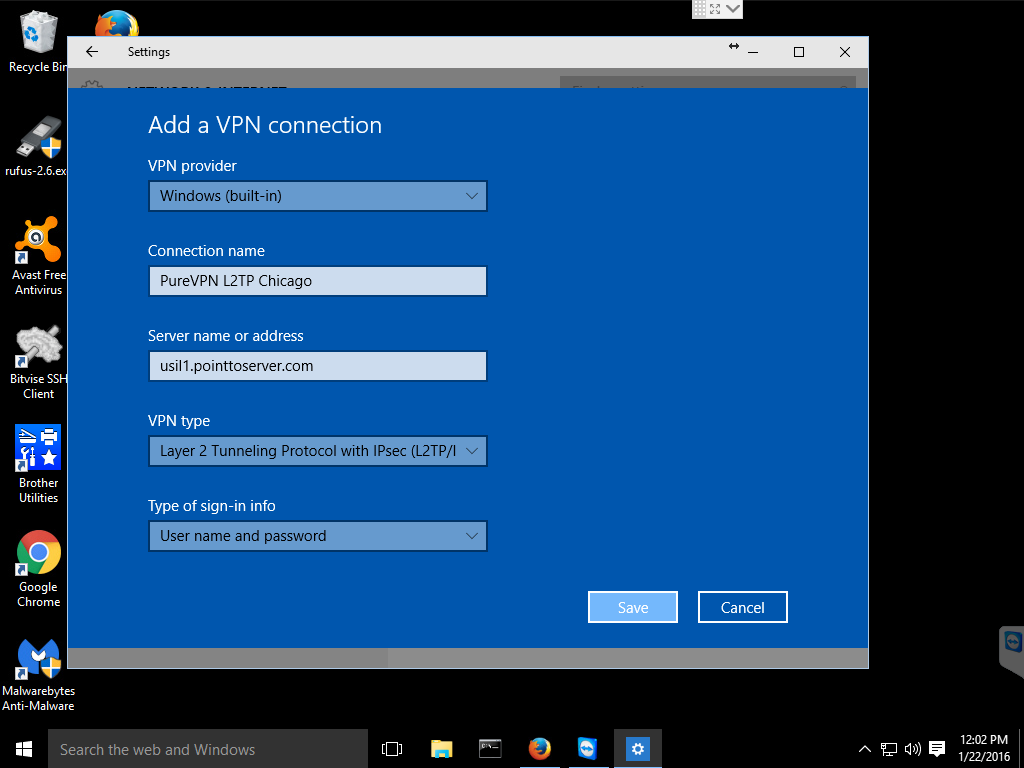
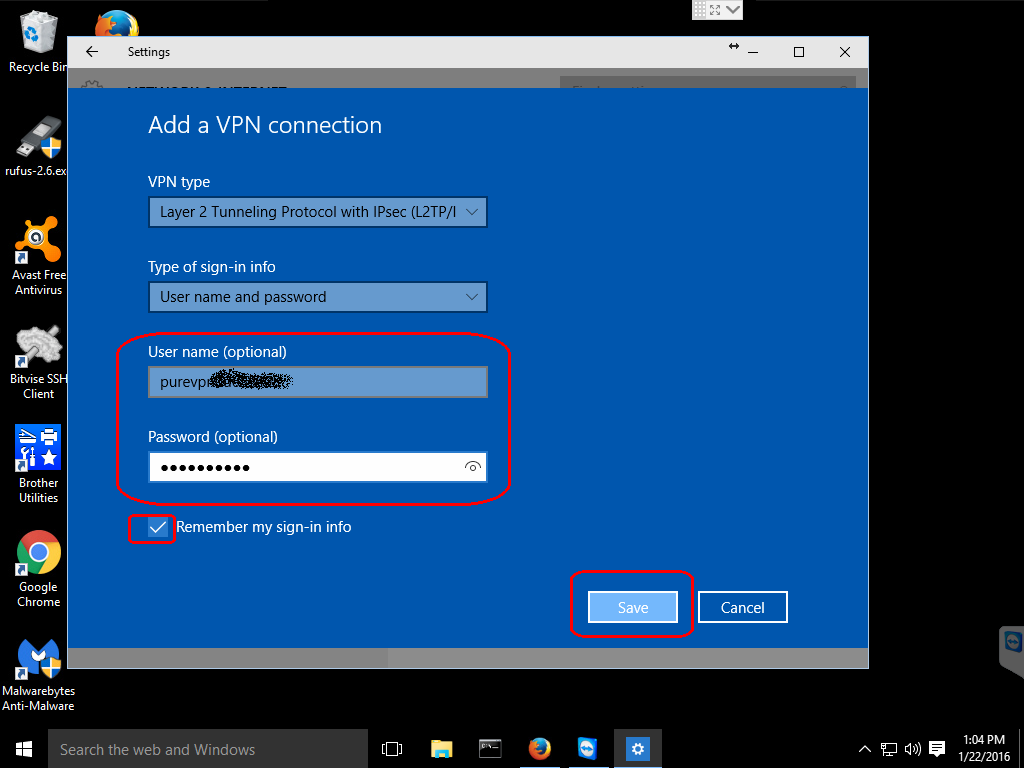
Step 4: Enter username and password (optional)
You may need to scroll down in the VPN configuration window to see the rest of the options, depending on the size of your Settings window.
If you desire, you can enter your VPN username and password in the appropriate fields and check the Remember my sign-in info and then you will not be asked for this information every time you activate your VPN connection.
When you are done entering all your information, click on the Save button to save your new VPN connection.
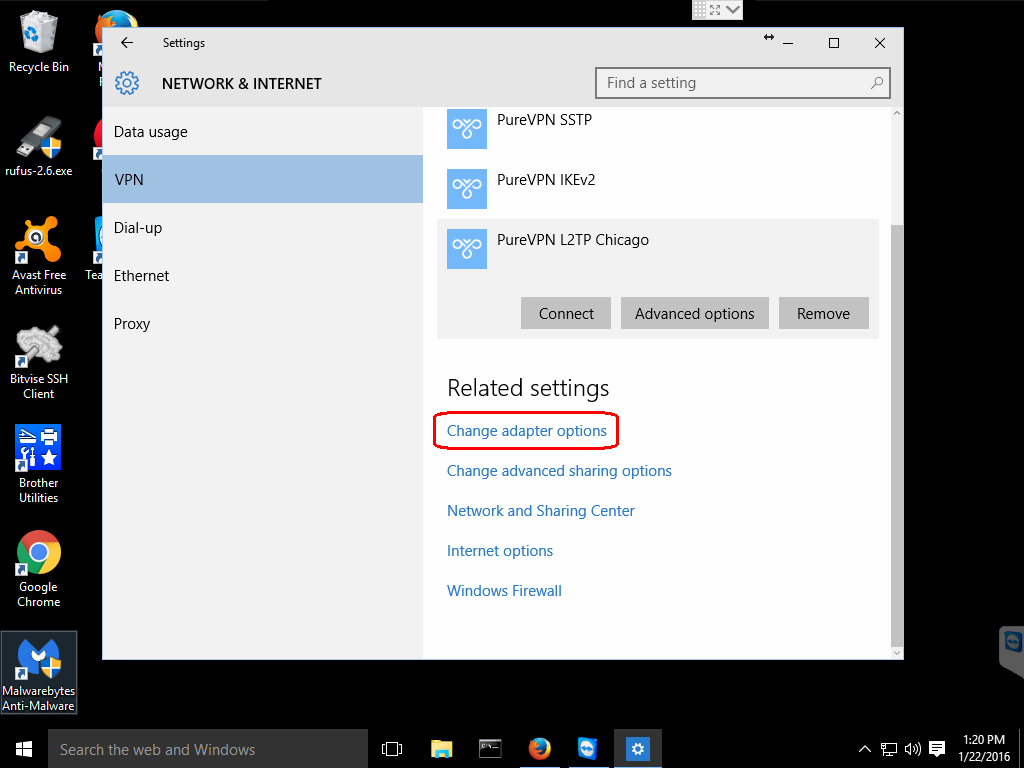
Step 5: Configure advanced settings
Under Related settings click on the Change adapter options choice.
This will open a new window titled Network Connections. Right-click on your newly created connection and this will bring up another menu. Click on the Properties option in this menu.
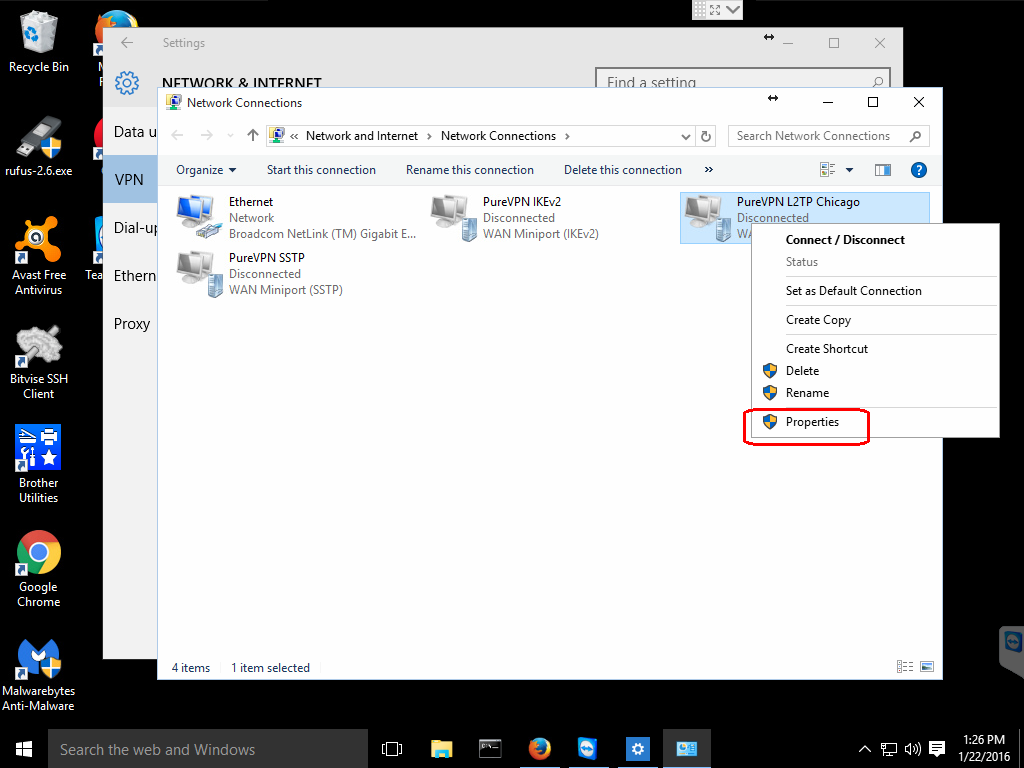
This will open a Properties window for the connection. Select the Security tab in this window.
Under the Data encryption: drop-down menu select Require encryption (disconnect if server declines).
Check the Allow these protocols radio button and ensure that only the Microsoft CHAP Version 2 (MS-CHAP v2) is checked.
There might be cases such as geo-unblocking streaming services where you might not want your connection encrypted. But you would probably be better served by using Smart DNS or some other proxy service for this.
MS-CHAP v2 is the only protocol that is still considered secure.
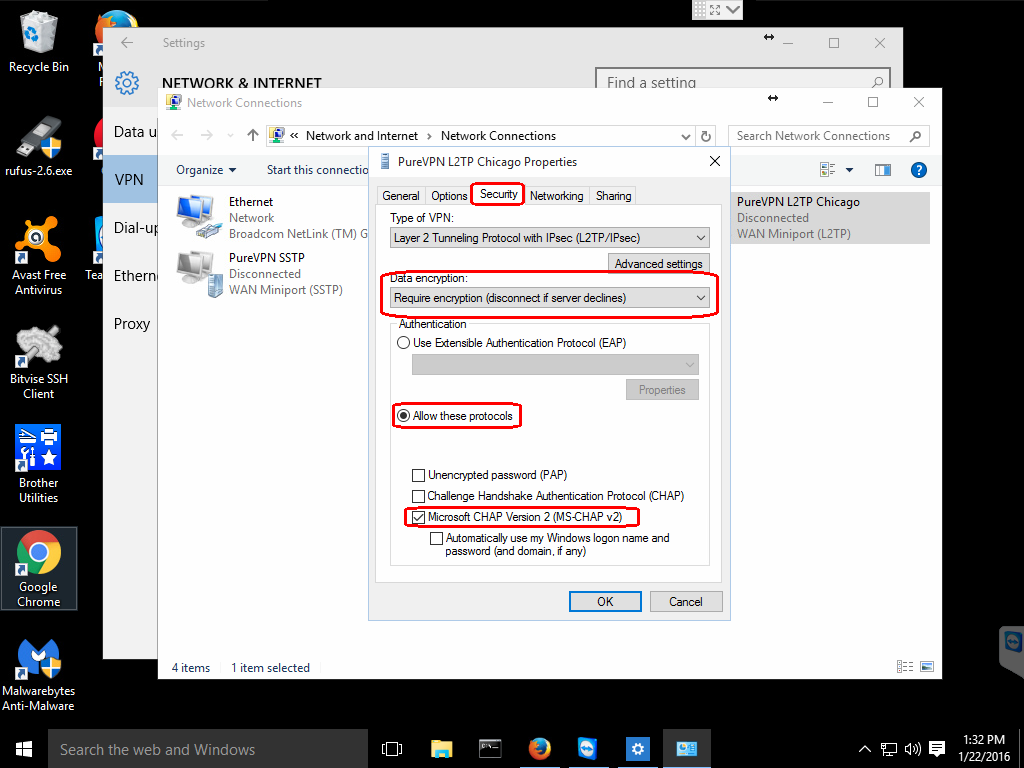
There is still one more setting that you will need to set for most providers. Stay on the Security tab and click the Advanced settings button.
Once you have the advanced settings open, click on the Use preshared key for authentication radio button and enter the key provided by your VPN provider.
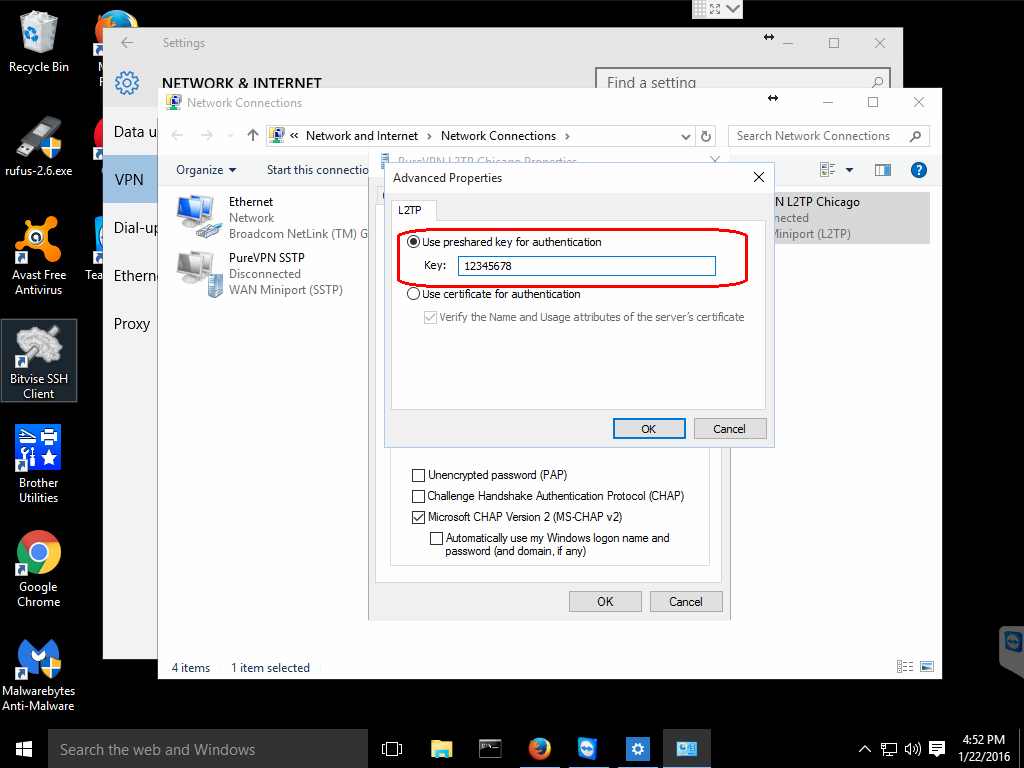
Most providers utilize a preshared key for authentication and this should be provided on their website, possibly in the client area or in the tutorials section.
Click the OK button on the Advanced properties. Then click the OK button on the Security tab.
Step 6: Connect to newly configured VPN
If you like, you can close any of the windows that you still have open from configuring your new VPN connection.
Click on the network icon on the taskbar and this will bring up a list of your configured connections.
Then, click on the name you gave your new configuration and this will bring up the NETWORK & INTERNET settings screen.
After that, click the name of your new configuration and this will reveal three buttons. Click the Connect button.
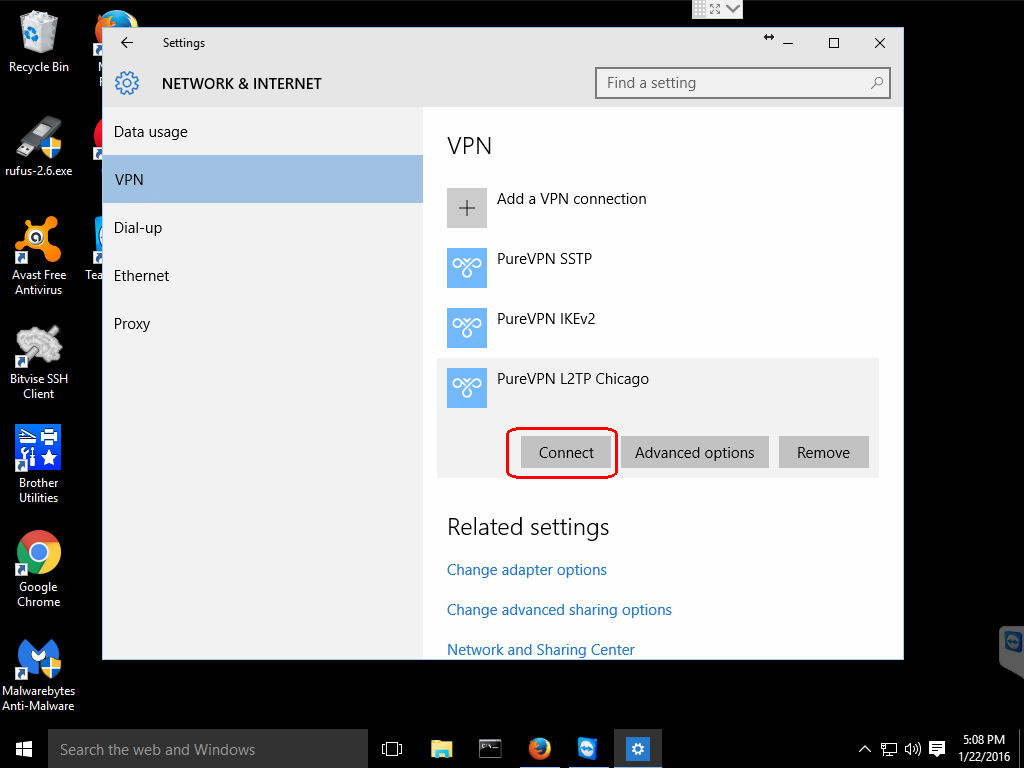
Once you click the Connect button, you will see the Windows 10 spinner and some informative messages and then it should say Connected, if all went well.
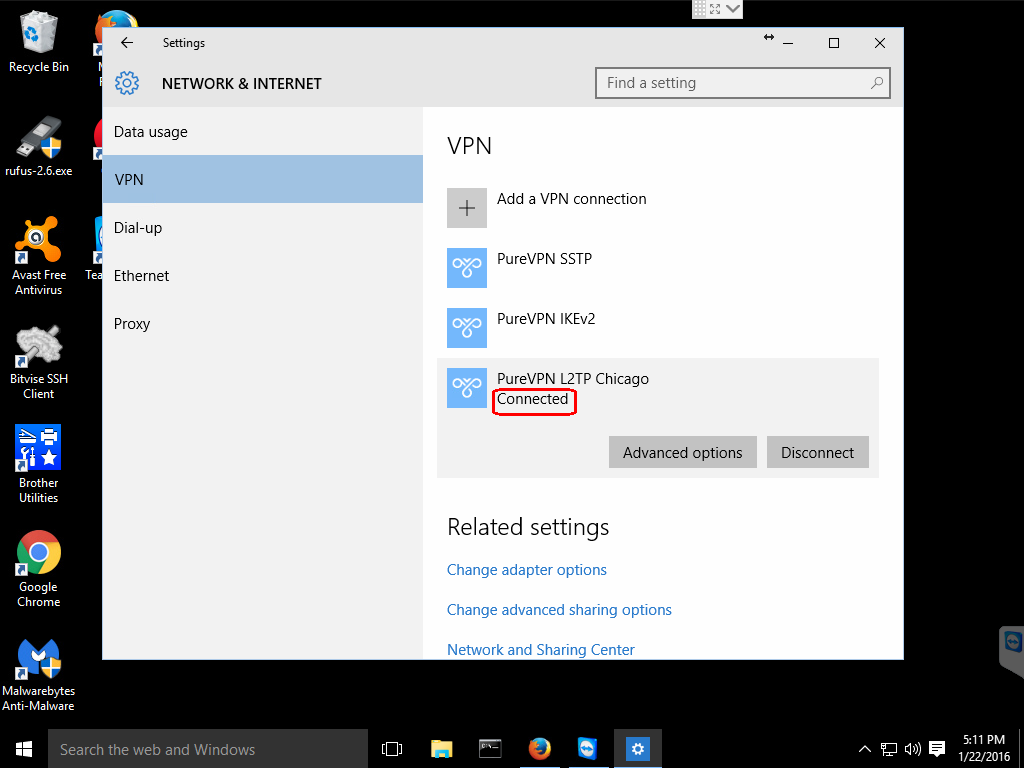
It is a good idea to use a tool to check what your IP is, it should now be reported as your VPN server;
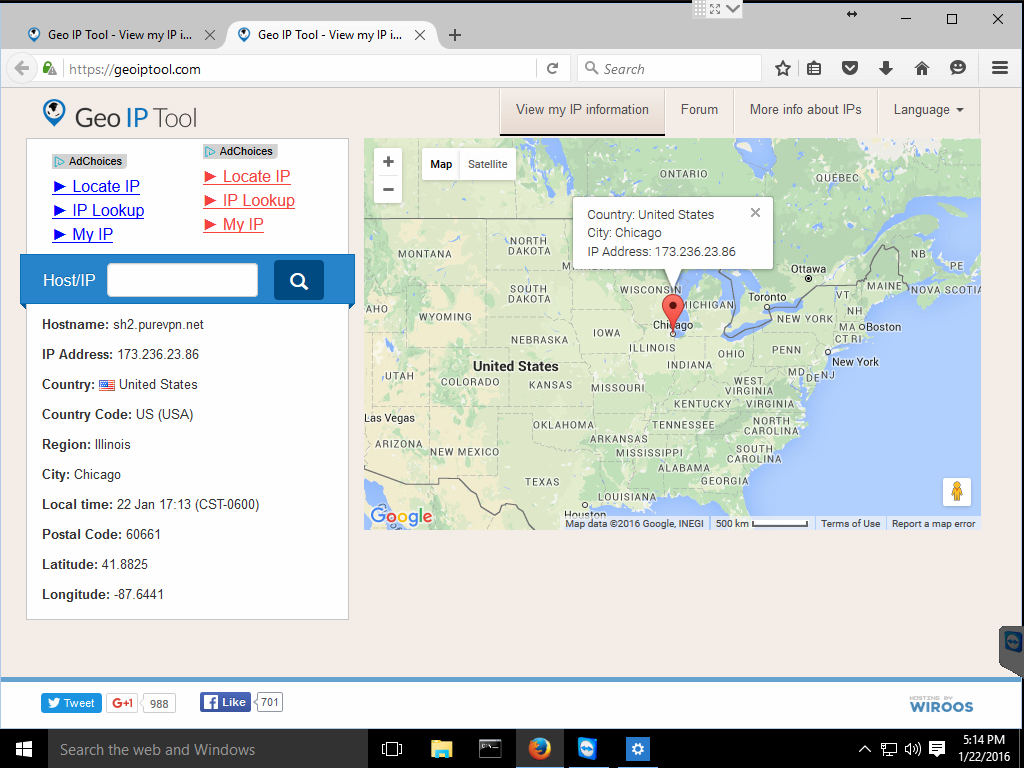
And that is it! I now appear to be coming from the VPN server located in Chicago.
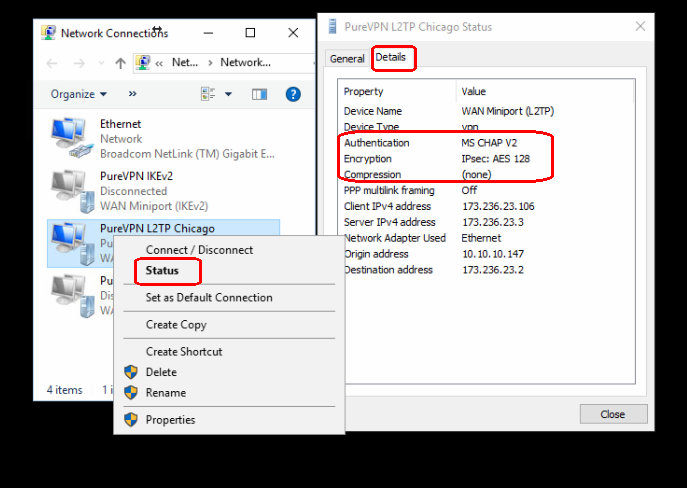
You can also check the network properties to get some information on your connection. Open the NETWORK & INTERNET window again by clicking on the network icon in the taskbar and selecting Network settings.
In the NETWORK & INTERNET window under Related settings select Change adapter options and this will bring up the Network Connections window. Right-click on the icon with the name of your VPN and select Status from that menu.
The General tab has some basic information but if you click on the Details tab you are provided with information about your VPN connection such as the cipher being used.
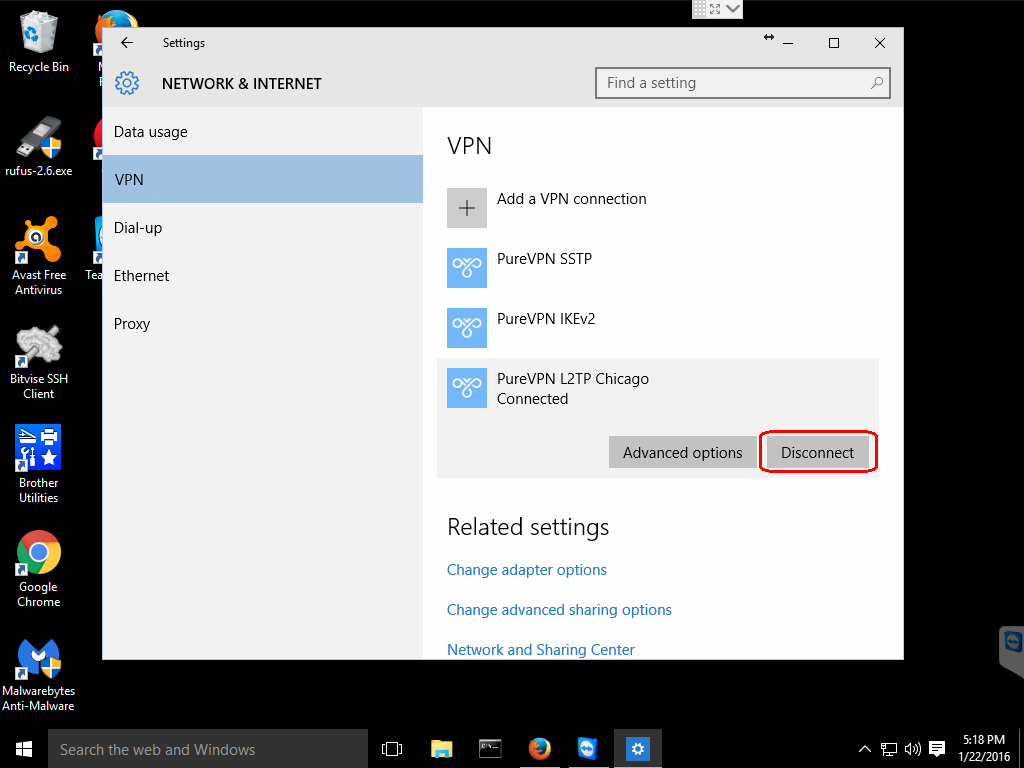
When you wish to disconnect from the VPN, you can click on the network icon and select your VPN connection profile which will bring up the NETWORK & INTERNET setting window again and click the Disconnect button.
That is all there is to setting up a L2TP/IPsec VPN using the built-in Microsoft Windows 10 functionality. I hope you found this tutorial to be useful and are enjoying your new VPN connection.
Добрый день.
Есть офисный Keenetic Ultra II, прошивка 3.5.10 (последняя). Поднят VPN-сервер L2TP/IPsec. Я со своего компьютера подключаюсь успешно. А вот у коллеги подключение не устанавливается, ошибка «Попытка L2TP-подключения не удалась из-за ошибки произошедшей на уровне безопасности во время согласований с удаленным компьютером.»
В логах: CoID={58CBDEBD-02F3-0002-C7EC-CB58F302D801}: Пользователь DESKTOP-OP9LD77\Наталья установил удаленное подключение Office, которое завершилось сбоем. Возвращен код ошибки 789.
Оба компьютера Windows 10 с последними обновлениями.
Лог успешного подключение с кинетика (1.1.1.1 офисный ip, публичный, 2.2.2.2 — ip моего домашнего роутера):
Скрытый текст
10[IKE] 2.2.2.2 is initiating a Main Mode IKE_SA
Янв 6 15:09:11 ipsec
10[CFG] received proposals: IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384, IKE:AES_CBC=128/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_256, IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Янв 6 15:09:11 ipsec
[truncated] 10[CFG] configured proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_768, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_256, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_768, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/ECP_384, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/ECP_256, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_768, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_256, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_768, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/ECP_384, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/ECP_256, IKE:DES_CBC/HMAC_MD5_96/PRF_HMA
Янв 6 15:09:11 ipsec
10[CFG] selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Янв 6 15:09:11 ipsec
10[IKE] sending DPD vendor ID
Янв 6 15:09:11 ipsec
10[IKE] sending FRAGMENTATION vendor ID
Янв 6 15:09:11 ipsec
10[IKE] sending NAT-T (RFC 3947) vendor ID
Янв 6 15:09:11 ipsec
07[IKE] remote host is behind NAT
Янв 6 15:09:11 ipsec
07[IKE] linked key for crypto map ‘(unnamed)’ is not found, still searching
Янв 6 15:09:11 ipsec
08[CFG] looking for pre-shared key peer configs matching 1.1.1.1…2.2.2.2[192.168.1.141]
Янв 6 15:09:11 ipsec
08[CFG] selected peer config «VPNL2TPServer»
Янв 6 15:09:11 ipsec
08[IKE] IKE_SA VPNL2TPServer[25108] established between 1.1.1.1[1.1.1.1]…2.2.2.2[192.168.1.141]
Янв 6 15:09:11 ipsec
08[IKE] scheduling reauthentication in 28777s
Янв 6 15:09:11 ipsec
08[IKE] maximum IKE_SA lifetime 28797s
Янв 6 15:09:11 ipsec
08[IKE] DPD not supported by peer, disabled
Янв 6 15:09:12 ipsec
12[CFG] received proposals: ESP:AES_CBC=256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC=128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:NULL/HMAC_SHA1_96/NO_EXT_SEQ
Янв 6 15:09:12 ipsec
12[CFG] configured proposals: ESP:AES_CBC=128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC=128/HMAC_MD5_96/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_MD5_96/NO_EXT_SEQ, ESP:DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:DES_CBC/HMAC_MD5_96/NO_EXT_SEQ
Янв 6 15:09:12 ipsec
12[CFG] selected proposal: ESP:AES_CBC=128/HMAC_SHA1_96/NO_EXT_SEQ
Янв 6 15:09:12 ipsec
12[IKE] received 3600s lifetime, configured 28800s
Янв 6 15:09:12 ipsec
12[IKE] received 250000000 lifebytes, configured 0
Янв 6 15:09:12 ipsec
14[IKE] CHILD_SA VPNL2TPServer{31235} established with SPIs c71c4a92_i 75eb5af8_o and TS 1.1.1.1/32[udp/l2tp] === 2.2.2.2/32[udp/l2tp]
Янв 6 15:09:12 ndm
IpSec::CryptoMapInfo: «VPNL2TPServer»: IPsec connection to L2TP/IPsec server from «2.2.2.2» is established.
Янв 6 15:09:12 ndm
IpSec::IpSecNetfilter: start reloading netfilter configuration…
Янв 6 15:09:12 ndm
IpSec::IpSecNetfilter: netfilter configuration reloading is done.
Янв 6 15:09:13 ppp-l2tp
l2tp: new tunnel 41037-3 created following reception of SCCRQ from 2.2.2.2:1701
Янв 6 15:09:13 ppp-l2tp
l2tp tunnel 41037-3 (2.2.2.2:1701): established at 1.1.1.1:1701
Янв 6 15:09:13 ppp-l2tp
l2tp tunnel 41037-3 (2.2.2.2:1701): new session 27123-1 created following reception of ICRQ
Янв 6 15:09:13 ppp-l2tp
ppp0:: connect: ppp0 <—> l2tp(2.2.2.2:1701 session 41037-3, 27123-1)
Янв 6 15:09:13 ppp-l2tp
ppp0:ivanov: ivanov: authentication succeeded
Янв 6 15:09:13 ppp-l2tp
ppp0:ivanov: CCP: discarding packet
Янв 6 15:09:13 kernel
l2tp0: renamed from ppp0
Янв 6 15:09:13 ppp-l2tp
l2tp0:ivanov: session started over l2tp session 41037-3, 27123-1
Янв 6 15:09:13 ndm
IpSec::CryptoMapInfo: «VPNL2TPServer»: L2TP/IPsec client «ivanov» connected from «2.2.2.2» with address «172.16.2.2».
Янв 6 15:09:14 ndhcps
DHCPINFORM received for 172.16.2.2 from 00:00:00:00:00:00.
Янв 6 15:09:14 ndhcps
sending INFORM to 00:00:00:00:00:00.
sending INFORM to 00:00:00:00:00:00.
Лог неудачного подключения (3.3.3.3 — ip домашнего роутера коллеги):
Скрытый текст
09[IKE] 3.3.3.3 is initiating a Main Mode IKE_SA
Янв 6 15:12:53 ipsec
09[CFG] received proposals: IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384, IKE:AES_CBC=128/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_256, IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Янв 6 15:12:53 ipsec
[truncated] 09[CFG] configured proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_768, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_256, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_768, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/ECP_384, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/ECP_256, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_768, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_256, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_768, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/ECP_384, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/ECP_256, IKE:DES_CBC/HMAC_MD5_96/PRF_HMA
Янв 6 15:12:53 ipsec
09[CFG] selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Янв 6 15:12:53 ipsec
09[IKE] sending DPD vendor ID
Янв 6 15:12:53 ipsec
09[IKE] sending FRAGMENTATION vendor ID
Янв 6 15:12:53 ipsec
09[IKE] sending NAT-T (RFC 3947) vendor ID
Янв 6 15:12:54 ipsec
14[IKE] remote host is behind NAT
Янв 6 15:12:54 ipsec
14[IKE] linked key for crypto map ‘(unnamed)’ is not found, still searching
Янв 6 15:12:54 ipsec
05[IKE] message parsing failed
Янв 6 15:12:54 ipsec
05[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:12:55 ipsec
07[IKE] message parsing failed
Янв 6 15:12:55 ipsec
07[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:12:56 ipsec
06[IKE] message parsing failed
Янв 6 15:12:56 ipsec
06[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:12:59 ipsec
11[IKE] message parsing failed
Янв 6 15:12:59 ipsec
11[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:02 ipsec
14[IKE] message parsing failed
Янв 6 15:13:02 ipsec
14[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:05 ipsec
15[IKE] message parsing failed
Янв 6 15:13:05 ipsec
15[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:08 ipsec
08[IKE] message parsing failed
Янв 6 15:13:08 ipsec
08[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:11 ipsec
09[IKE] message parsing failed
Янв 6 15:13:11 ipsec
09[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:14 ipsec
15[IKE] message parsing failed
Янв 6 15:13:14 ipsec
15[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:17 ipsec
06[IKE] message parsing failed
Янв 6 15:13:17 ipsec
06[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:20 ipsec
09[IKE] message parsing failed
Янв 6 15:13:20 ipsec
09[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:23 ipsec
15[IKE] message parsing failed
Янв 6 15:13:23 ipsec
15[IKE] ID_PROT request with message ID 0 processing failed
Янв 6 15:13:23 ipsec
10[JOB] deleting half open IKE_SA with 3.3.3.3 after timeout
Пробовал, но не помогло:
1) добавлять в реестр параметр:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent] «AssumeUDPEncapsulationContextOnSendRule»=dword:00000002
2) на домашнем роутере включить «Пропускать VPN IPSec»
3) на домашнем роутере добавить компьютер в DMZ
4) отключать брандмауэр на компьютере
Подскажите, куда дальше копать?