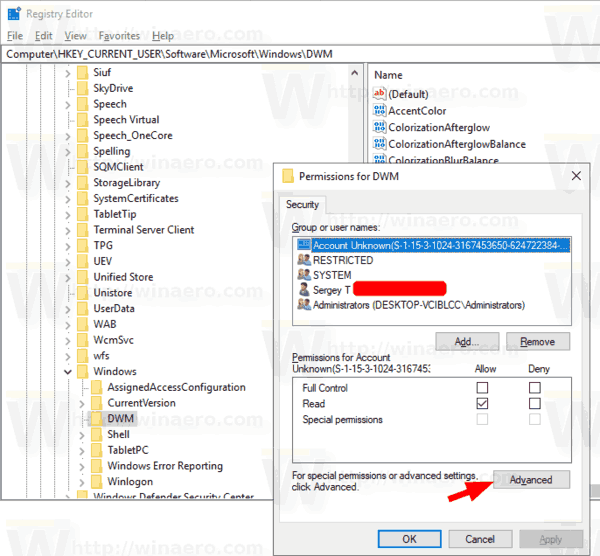
Today, we will see what Inherited Permissions are in Windows 10, and how they affect files, folders, and Registry keys. Also, we will learn how to disable and enable them for an object in Windows 10.
NTFS is the standard file system of the Windows NT operating system family. Starting with Windows NT 4.0 Service Pack 6, it supported the concept of permissions which can be configured to permit or restrict access to files, folders, and other objects locally and over a network.
By default, almost all system files, system folders and even Registry keys in Windows 10 are owned by a special built-in user account called «TrustedInstaller». Other user accounts are set to only read the files.
As a user accesses each file, folder, registry key, printer, or an Active Directory object, the system checks its permissions. It supports inheritance for an object, e.g. files can inherit permissions from their parent folder. Also every object has an Owner which is the user account that can set ownership and change permissions.
If you are interested in managing NTFS permissions, refer to the following article:
How to take ownership and get full access to files and folders in Windows 10
Permission types
In short, there are two types of permissions — explicit permissions and inherited permissions.
There are two types of permissions: explicit permissions and inherited permissions.
-
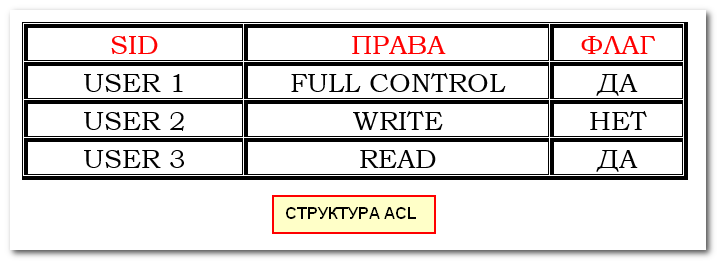
Explicit permissions are those that are set by default on non-child objects when the object is created, or by user action on non-child, parent, or child objects.
- Inherited permissions are those that are propagated to an object from a parent object. Inherited permissions ease the task of managing permissions and ensure consistency of permissions among all objects within a given container.
By default, objects within a container inherit the permissions from that container when the objects are created. For example, when you create a folder called MyFolder, all subfolders and files created within MyFolder automatically inherit the permissions from that folder. Therefore, MyFolder has explicit permissions, while all subfolders and files within it have inherited permissions.
Effective permissions are based on a local evaluation of the user’s group membership, user privileges, and permissions. The Effective Permissions tab of the Advanced Security Settings property page lists the permissions that would be granted to the selected group or user based solely on the permissions granted directly through group membership. For details, see the following articles:
- Quickly Reset NTFS Permissions in Windows 10
- Add Reset Permissions Context Menu in Windows 10
Let’s see how to enable and disable inherited permissions for files in Windows 10. You must be signed in with an administrative account to continue.
Disable Inherited Permissions for a File or Folder in Windows 10
- Open File Explorer.
- Locate the file or folder you want to take disable inherited permissions for.
- Right-click the file or folder, click Properties, and then click the Security tab.
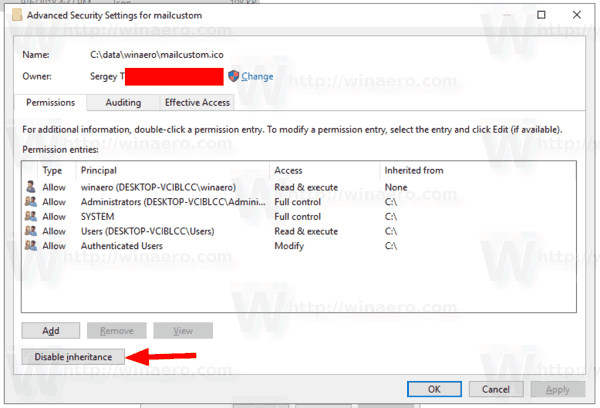
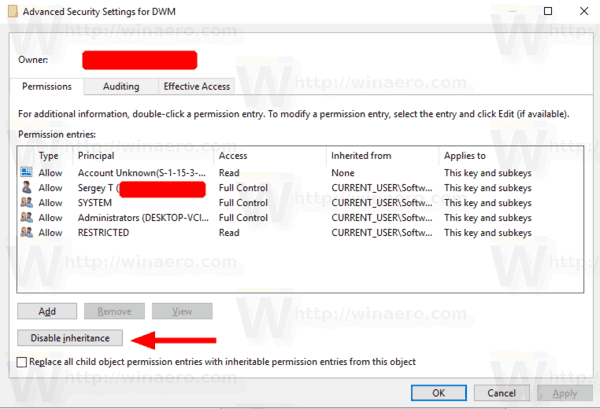
- Click on the Advanced button. The «Advanced Security Settings» window will appear.
- Click on the Disable inheritance button.
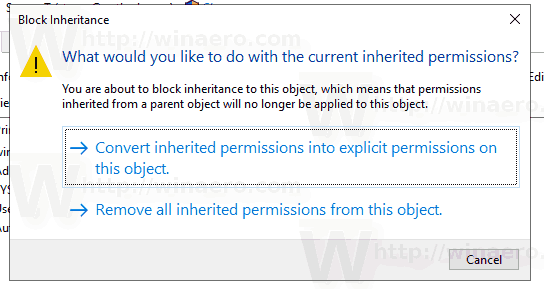
- You will be asked either to convert inherited permissions into explicit permissions or to remove all inherited permissions. If you are not sure, choose to convert them.
The following screenshot shows what happens when you choose to remove the inherited permissions. Only explicit permissions are left.
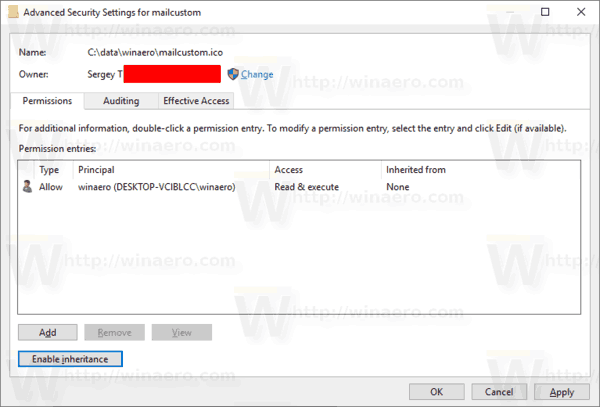
You are done. Click OK to close the dialog.
Enable Inherited Permissions for a File or Folder in Windows 10
- Open File Explorer.
- Locate the file or folder with disabled inherited NTFS permissions.
- Right-click the file or folder, click Properties, and then click the Security tab.
- Click on the Advanced button. The «Advanced Security Settings» window will appear.
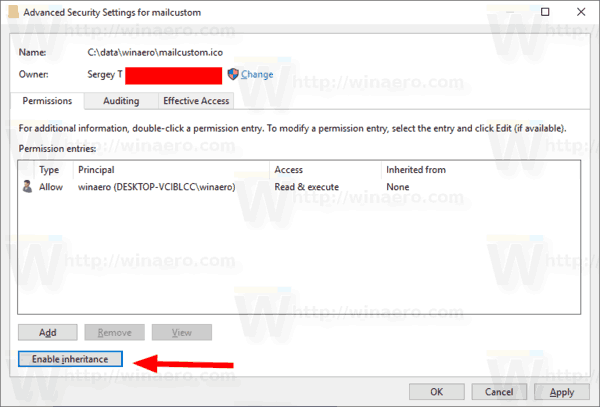
- If you see the Change permissions button, click on it.
- Click on the button Enable inheritance.
You are done. The inherited permissions will be added to the list of current permissions.
Note: If you are enabling or disabling permission for a folder, you can turn on the option Replace all child object permissions entries with inheritable permission entries from this object to update permissions for all child objects.
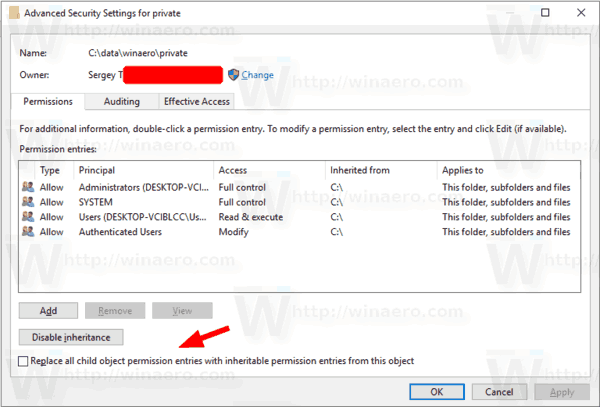
Enable or Disable Inherited Permissions for a Registry Key
Subkeys can have inherited permissions from their parent key. Or, subkeys can also have explicit permissions, separate from the parent key. In the first case, that is, if the permissions are inherited from the parent key, you have to disable inheritance and copy permissions to the current key.
To change the inherited permissions for a Registry key,
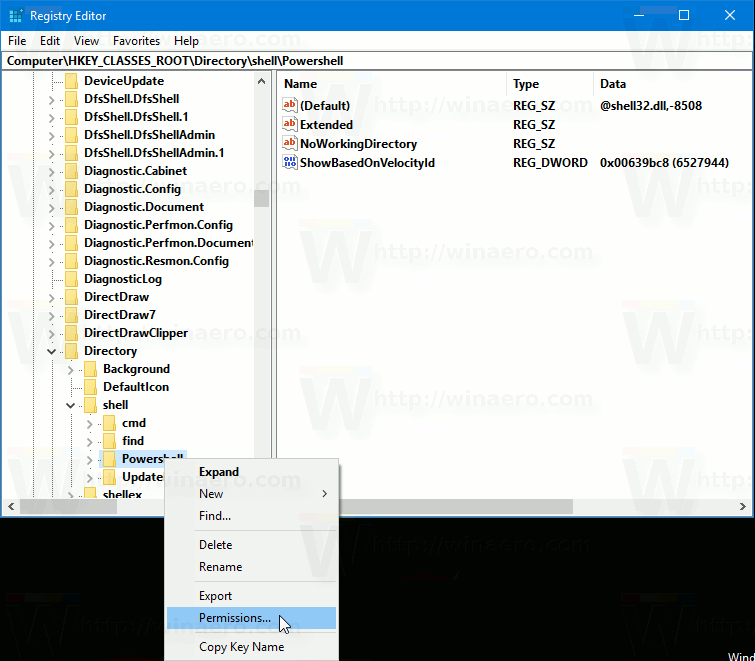
- Open the Registry Editor app.
- Go to a Registry key you want to disable or enable the inherited permissions. See how to go to a Registry key with one click.
- Right click on that key and select the Permissions… option from the context menu.
- In the next dialog, click on the Advanced button.
- Click on the button Disable inheritance to disable the inherited permissions.
- Click on the button Enable inheritance to enable the inherited permissions for a key with disabled inherited permissions.
Also, see the following guide:
Windows Registry Editor for dummies
Enable or Disable Inherited Permissions in the Command Prompt
- Open an elevated command prompt.
- Run the following command to disable the inherited permissions for a file or folder and convert them into explicit permissions:
icacls "full path to your file" /inheritance:d. - Disable the inherited permissions for a file or folder and remove them:
icacls "full path to your file" /inheritance:r. - Enable the inherited permissions for a file or folder:
icacls "full path to the folder" /inheritance:e.
That’s it.
Related articles:
- Add Take Ownership Context Menu in Windows 10
- Backup Permissions For Files and Folders in Windows 10
- Add View Permissions Context Menu in Windows 10
- Add View Owner Context Menu in Windows 10
- How to restore the TrustedInstaller ownership in Windows 10
- How to take ownership and get full access to files and folders in Windows 10
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won’t take a lot from you, but it will help us grow. Thanks for your support!
To turn off the option for inheriting permissions in Windows 10, follow these steps:
1. Right-click on the folder or file for which you want to disable permission inheritance and select “Properties” from the context menu.
2. In the Properties window, navigate to the “Security” tab.
3. Click on the “Advanced” button located at the bottom.
4. In the Advanced Security Settings window, click on the “Disable inheritance” button.
5. A pop-up window will appear, asking if you want to convert inherited permissions into explicit permissions. Choose the option that suits your requirements. Keep in mind that converting inherited permissions to explicit permissions can be a complex process, so proceed with caution.
6. After making your selection, click on the “Remove all inherited permissions from this object” checkbox and click “Apply”.
7. You will receive another warning about the potential consequences of removing inherited permissions. Review the information provided and click “OK” if you are certain about your decision.
8. Finally, click “OK” in the Advanced Security Settings window and “OK” again in the Properties window to save the changes.
By following these steps, you can effectively turn off the option for inheriting permissions for a specific folder or file in Windows 10, granting you more control over access and security settings.
Video Tutorial:How to disable inheritance in command line?
How do you block inheritance?
In object-oriented programming, inheritance is a fundamental concept that allows classes to inherit properties and methods from a parent class. However, there may be scenarios where you want to prevent a class from being inherited.
To block inheritance in most programming languages, you can use specific keywords or mechanisms depending on the language you’re working with. Let’s consider an example using the Java programming language.
In Java, the `final` keyword can be used to block inheritance. By declaring a class as `final`, you indicate that it cannot be subclassed. Here’s an example:
“`java
final class MyClass {
// Class implementation here
}
“`
In this case, the `MyClass` is marked as `final`, preventing other classes from inheriting from it.
Similarly, some languages provide alternative mechanisms to block inheritance. For instance, in C++, the `final` keyword can be used to prevent a class from being derived:
“`cpp
class MyBaseClass final {
// Class implementation here
};
“`
By marking `MyBaseClass` as `final`, you indicate that it cannot be used as a base class for any other class.
Understanding and applying the right mechanism to block inheritance will depend on the programming language you are using. It is important to consult the documentation and guidelines specific to the language you are working with to ensure you are using the correct approach.
What does enable inheritance mean in Windows 10?
In the context of Windows 10, enabling inheritance refers to the process of allowing permissions to be inherited by subfolders or files within a parent folder. When inheritance is enabled, the security settings applied to the parent folder automatically propagate to its subfolders and files. This means that any permissions set on the parent folder will be passed down to all its contained objects, ensuring consistent access control across the hierarchy.
Enabling inheritance can be useful in scenarios where you want to apply uniform security settings to multiple files or folders within a directory structure. By enabling inheritance, you can avoid the need to manually set individual permissions for each subfolder or file, streamlining the management of access controls.
However, it’s important to note that enabling inheritance should be done with caution, as it can potentially lead to unintended exposure of sensitive data or unauthorized access. Before enabling inheritance, it is advisable to carefully review and understand the existing permissions on the parent folder, ensuring that they align with your security requirements.
In summary, enabling inheritance in Windows 10 allows permissions set on a parent folder to be automatically passed down to its subfolders and files, ensuring consistent access control throughout the directory structure. Careful consideration and review of existing permissions are essential to prevent unintended security vulnerabilities.
What is inherited permissions in Windows 10?
In Windows 10, inherited permissions refer to the concept of granting access rights or permissions to a file or folder based on its position within the directory structure. When permissions are inherited, it means that a file or folder inherits the permissions of its parent directory. This allows for easier management and consistency of access control throughout the system.
Inherited permissions work by propagating the permissions down the directory tree. By default, when a new file or folder is created within a directory, it inherits the permissions of that directory. If the permissions on the parent directory change, the changes are also applied to the child objects within it.
Inherited permissions can be useful in situations where you want to apply consistent access control to multiple files or folders without having to set individual permissions on each one. It simplifies the administration of permissions and ensures that changes made at the parent level are automatically reflected in the child objects.
However, it’s important to note that inherited permissions can sometimes lead to unintended consequences. For example, if a user has permissions to a parent directory, all the files and subfolders within it will also inherit those permissions. This means that it’s crucial to carefully manage permissions at the parent level to avoid granting excessive access to unintended users or groups.
Overall, understanding and properly managing inherited permissions in Windows 10 is essential for maintaining a secure and organized file system while ensuring appropriate access control for different users and groups.
What is disable inheritance Windows 10?
Disable inheritance in Windows 10 is a security feature that allows users to prevent permissions and settings from being inherited by files, folders, and subfolders within a specific location. When inheritance is enabled, permissions from parent folders are automatically applied to child objects, which can simplify access control management. However, in certain cases, it may be necessary to disable inheritance to restrict access or permissions to specific folders or files independently.
By disabling inheritance, administrators can take full control of access control settings and tailor them to meet specific security requirements. This feature is particularly useful when dealing with sensitive data or when implementing custom permission settings that differ from parent folders.
To disable inheritance in Windows 10, follow these steps:
1. Navigate to the folder or file for which you want to disable inheritance.
2. Right-click on the folder or file and select “Properties.”
3. In the Properties window, go to the “Security” tab.
4. Click on the “Advanced” button.
5. In the Advanced Security Settings window, uncheck the option that says “Include inheritable permissions from this object’s parent.”
6. Select “Remove” when prompted to either copy or remove the inherited permissions.
7. Click “OK” to save the changes.
Once inheritance is disabled, the folder or file will no longer inherit permissions from its parent, and you can customize access control settings as needed. However, it’s important to note that managing permissions manually can be more complex and requires careful consideration to avoid unintended consequences or security vulnerabilities.
To turn off the option for inheriting permissions on a device running iOS 16, such as an iPhone 14, iPhone 14 Pro, or iPhone 14 Plus, you can follow these steps:
1. Open the “Settings” app on your iPhone and scroll down to find the “Privacy” section. Tap on it.
2. In the “Privacy” section, you’ll see various categories listed. Look for the category that relates to the permissions you want to manage. For example, if you want to adjust permissions for camera access, tap on the “Camera” option.
3. Inside the camera settings, you’ll find a toggle switch for “Inherit Permissions” or “Inherit Access.” Toggle this switch off to disable the option for inheriting permissions.
4. After turning off the inherit permissions option for a specific category, you can customize the permissions individually for each app or service listed below.
By disabling the inherit permissions option, you gain more control over which apps or services can access certain features or data on your device. This can be useful in ensuring your privacy and optimizing your device’s security. Keep in mind that some app functionalities may be affected if you restrict their access to specific permissions, so make sure to review and adjust the permissions according to your preferences and needs.
How do I stop inheriting permissions in powershell?
To stop inheriting permissions in PowerShell, you can use the Set-Acl cmdlet to modify the Access Control List (ACL) of a file or folder. Here’s how you can do it:
1. Open PowerShell by searching for it in the Start menu and running it as an administrator.
2. Use the Get-Acl cmdlet to retrieve the current ACL of the file or folder you want to stop inheriting permissions from. For example, if you want to modify the permissions of a folder named “MyFolder,” you would run the following command:
“`
$acl = Get-Acl -Path “C:PathToMyFolder”
“`
3. Use the Set-Acl cmdlet to modify the ACL and disable permission inheritance. You can achieve this by specifying the “Access” parameter and setting it to the desired permissions. Additionally, use the “NoPropagateInherit” flag to prevent inherited permissions from applying. For example:
“`
Set-Acl -Path “C:PathToMyFolder” -AclObject $acl -Access “$env:username”,”FullControl” -NoPropagateInherit
“`
In this command, “$env:username” represents your username, and “FullControl” is the permission level you want to set. You can adjust these values as per your specific requirements.
4. After executing the command, the ACL for the specified file or folder will be updated, and it will no longer inherit permissions from its parent directory.
Please note that modifying ACLs can have serious security implications, so exercise caution and ensure that you understand the consequences before making any changes.
{“@context”:”https://schema.org”,”@type”:”FAQPage”,”mainEntity”:[{“@type”:”Question”,”name”:”How do you block inheritance?”,”acceptedAnswer”:{“@type”:”Answer”,”text”:”In object-oriented programming, inheritance is a fundamental concept that allows classes to inherit properties and methods from a parent class. However, there may be scenarios where you want to prevent a class from being inherited. nnTo block inheritance in most programming languages, you can use specific keywords or mechanisms depending on the language you’re working with. Let’s consider an example using the Java programming language.nnIn Java, the `final` keyword can be used to block inheritance. By declaring a class as `final`, you indicate that it cannot be subclassed. Here’s an example:nn“`javanfinal class MyClass {n // Class implementation heren}n“`nnIn this case, the `MyClass` is marked as `final`, preventing other classes from inheriting from it.nnSimilarly, some languages provide alternative mechanisms to block inheritance. For instance, in C++, the `final` keyword can be used to prevent a class from being derived:nn“`cppnclass MyBaseClass final {n // Class implementation heren};n“`nnBy marking `MyBaseClass` as `final`, you indicate that it cannot be used as a base class for any other class.nnUnderstanding and applying the right mechanism to block inheritance will depend on the programming language you are using. It is important to consult the documentation and guidelines specific to the language you are working with to ensure you are using the correct approach.”}},{“@type”:”Question”,”name”:”What does enable inheritance mean in Windows 10?”,”acceptedAnswer”:{“@type”:”Answer”,”text”:”In the context of Windows 10, enabling inheritance refers to the process of allowing permissions to be inherited by subfolders or files within a parent folder. When inheritance is enabled, the security settings applied to the parent folder automatically propagate to its subfolders and files. This means that any permissions set on the parent folder will be passed down to all its contained objects, ensuring consistent access control across the hierarchy.nnEnabling inheritance can be useful in scenarios where you want to apply uniform security settings to multiple files or folders within a directory structure. By enabling inheritance, you can avoid the need to manually set individual permissions for each subfolder or file, streamlining the management of access controls.nnHowever, it’s important to note that enabling inheritance should be done with caution, as it can potentially lead to unintended exposure of sensitive data or unauthorized access. Before enabling inheritance, it is advisable to carefully review and understand the existing permissions on the parent folder, ensuring that they align with your security requirements.nnIn summary, enabling inheritance in Windows 10 allows permissions set on a parent folder to be automatically passed down to its subfolders and files, ensuring consistent access control throughout the directory structure. Careful consideration and review of existing permissions are essential to prevent unintended security vulnerabilities.”}},{“@type”:”Question”,”name”:”What is inherited permissions in Windows 10?”,”acceptedAnswer”:{“@type”:”Answer”,”text”:”In Windows 10, inherited permissions refer to the concept of granting access rights or permissions to a file or folder based on its position within the directory structure. When permissions are inherited, it means that a file or folder inherits the permissions of its parent directory. This allows for easier management and consistency of access control throughout the system.nnInherited permissions work by propagating the permissions down the directory tree. By default, when a new file or folder is created within a directory, it inherits the permissions of that directory. If the permissions on the parent directory change, the changes are also applied to the child objects within it.nnInherited permissions can be useful in situations where you want to apply consistent access control to multiple files or folders without having to set individual permissions on each one. It simplifies the administration of permissions and ensures that changes made at the parent level are automatically reflected in the child objects.nnHowever, it’s important to note that inherited permissions can sometimes lead to unintended consequences. For example, if a user has permissions to a parent directory, all the files and subfolders within it will also inherit those permissions. This means that it’s crucial to carefully manage permissions at the parent level to avoid granting excessive access to unintended users or groups.nnOverall, understanding and properly managing inherited permissions in Windows 10 is essential for maintaining a secure and organized file system while ensuring appropriate access control for different users and groups.”}},{“@type”:”Question”,”name”:”What is disable inheritance Windows 10?”,”acceptedAnswer”:{“@type”:”Answer”,”text”:”Disable inheritance in Windows 10 is a security feature that allows users to prevent permissions and settings from being inherited by files, folders, and subfolders within a specific location. When inheritance is enabled, permissions from parent folders are automatically applied to child objects, which can simplify access control management. However, in certain cases, it may be necessary to disable inheritance to restrict access or permissions to specific folders or files independently.nnBy disabling inheritance, administrators can take full control of access control settings and tailor them to meet specific security requirements. This feature is particularly useful when dealing with sensitive data or when implementing custom permission settings that differ from parent folders.nnTo disable inheritance in Windows 10, follow these steps:n1. Navigate to the folder or file for which you want to disable inheritance.n2. Right-click on the folder or file and select “Properties.”n3. In the Properties window, go to the “Security” tab.n4. Click on the “Advanced” button.n5. In the Advanced Security Settings window, uncheck the option that says “Include inheritable permissions from this object’s parent.”n6. Select “Remove” when prompted to either copy or remove the inherited permissions.n7. Click “OK” to save the changes.nnOnce inheritance is disabled, the folder or file will no longer inherit permissions from its parent, and you can customize access control settings as needed. However, it’s important to note that managing permissions manually can be more complex and requires careful consideration to avoid unintended consequences or security vulnerabilities.”}},{“@type”:”Question”,”name”:”How do I turn off the option for inheriting permissions?”,”acceptedAnswer”:{“@type”:”Answer”,”text”:”To turn off the option for inheriting permissions on a device running iOS 16, such as an iPhone 14, iPhone 14 Pro, or iPhone 14 Plus, you can follow these steps:nn1. Open the “Settings” app on your iPhone and scroll down to find the “Privacy” section. Tap on it.n2. In the “Privacy” section, you’ll see various categories listed. Look for the category that relates to the permissions you want to manage. For example, if you want to adjust permissions for camera access, tap on the “Camera” option.n3. Inside the camera settings, you’ll find a toggle switch for “Inherit Permissions” or “Inherit Access.” Toggle this switch off to disable the option for inheriting permissions.n4. After turning off the inherit permissions option for a specific category, you can customize the permissions individually for each app or service listed below.nnBy disabling the inherit permissions option, you gain more control over which apps or services can access certain features or data on your device. This can be useful in ensuring your privacy and optimizing your device’s security. Keep in mind that some app functionalities may be affected if you restrict their access to specific permissions, so make sure to review and adjust the permissions according to your preferences and needs.”}},{“@type”:”Question”,”name”:”How do I stop inheriting permissions in powershell?”,”acceptedAnswer”:{“@type”:”Answer”,”text”:”To stop inheriting permissions in PowerShell, you can use the Set-Acl cmdlet to modify the Access Control List (ACL) of a file or folder. Here’s how you can do it:nn1. Open PowerShell by searching for it in the Start menu and running it as an administrator.nn2. Use the Get-Acl cmdlet to retrieve the current ACL of the file or folder you want to stop inheriting permissions from. For example, if you want to modify the permissions of a folder named “MyFolder,” you would run the following command:n “`n $acl = Get-Acl -Path “C:PathToMyFolder”n “`nn3. Use the Set-Acl cmdlet to modify the ACL and disable permission inheritance. You can achieve this by specifying the “Access” parameter and setting it to the desired permissions. Additionally, use the “NoPropagateInherit” flag to prevent inherited permissions from applying. For example:n “`n Set-Acl -Path “C:PathToMyFolder” -AclObject $acl -Access “$env:username”,”FullControl” -NoPropagateInheritn “`nn In this command, “$env:username” represents your username, and “FullControl” is the permission level you want to set. You can adjust these values as per your specific requirements.nn4. After executing the command, the ACL for the specified file or folder will be updated, and it will no longer inherit permissions from its parent directory.nnPlease note that modifying ACLs can have serious security implications, so exercise caution and ensure that you understand the consequences before making any changes.”}}]}
Эффективные методы удаления параметра наследования разрешений
На этой странице представлены полезные советы о том, как правильно и эффективно удалить параметр наследования разрешений, чтобы обеспечить безопасность и контроль доступа к вашим данным.

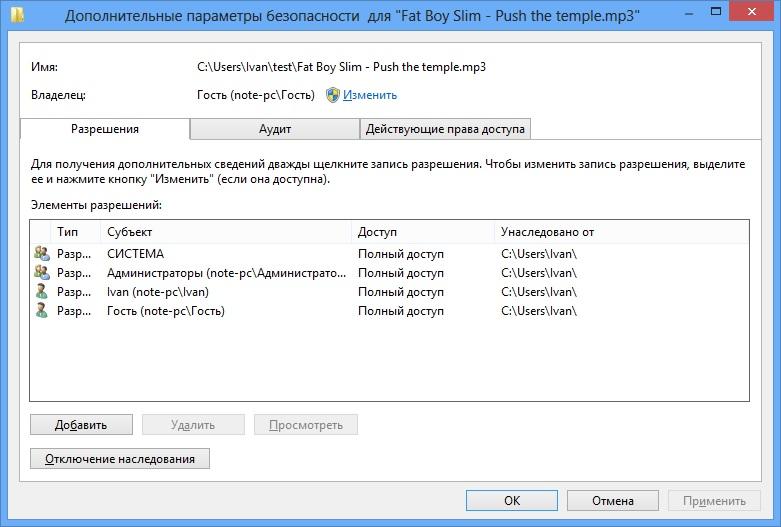

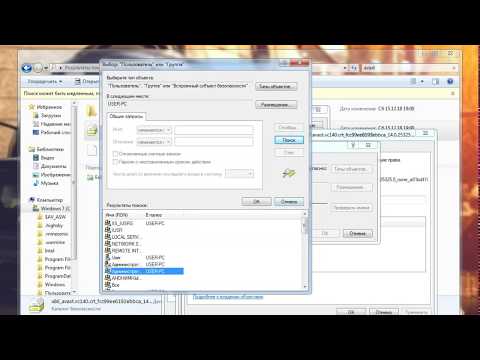
Откройте свойства нужной папки или файла и перейдите на вкладку Безопасность.

Запросите разрешение от TrustedInstaller
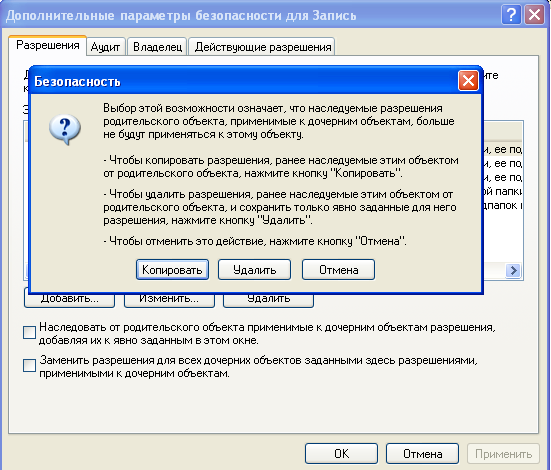
Нажмите на кнопку Дополнительно, чтобы открыть дополнительные параметры безопасности.

Сингапур’24 Итоги пятницы
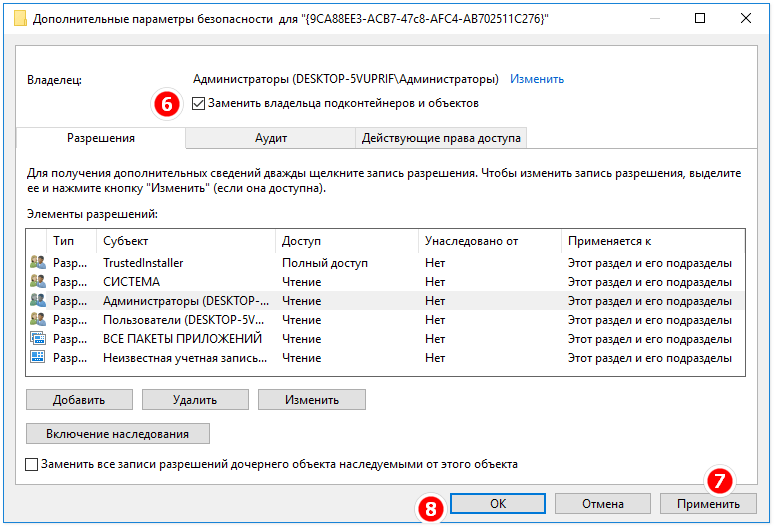
В открывшемся окне найдите раздел Наследование и нажмите на кнопку Отключить наследование.
У вас нет разрешения на доступ к этой папке. Windows 11
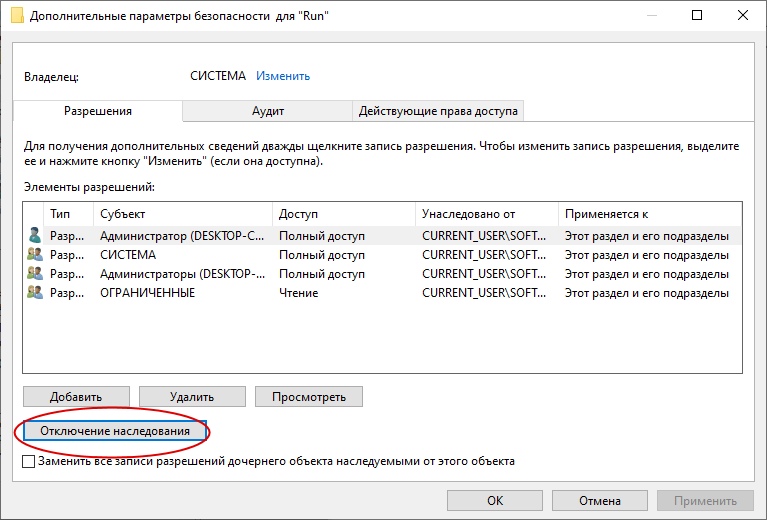
Выберите вариант Удалить все унаследованные разрешения от этого объекта, чтобы полностью удалить наследуемые разрешения.

Как удалить права Администратора на Windows 10 без другого активного Администратора?
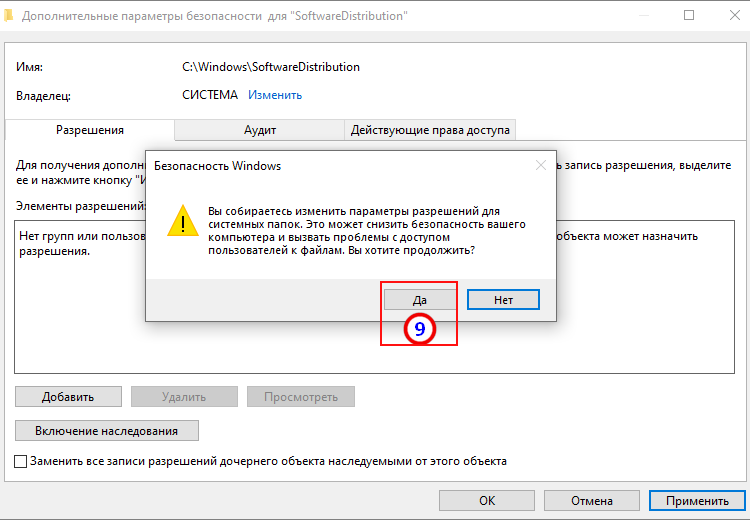
Если необходимо сохранить текущие разрешения, но отключить их наследование, выберите Преобразовать унаследованные разрешения в явные для этого объекта.

Запросите разрешение от Администраторы при удалении папки
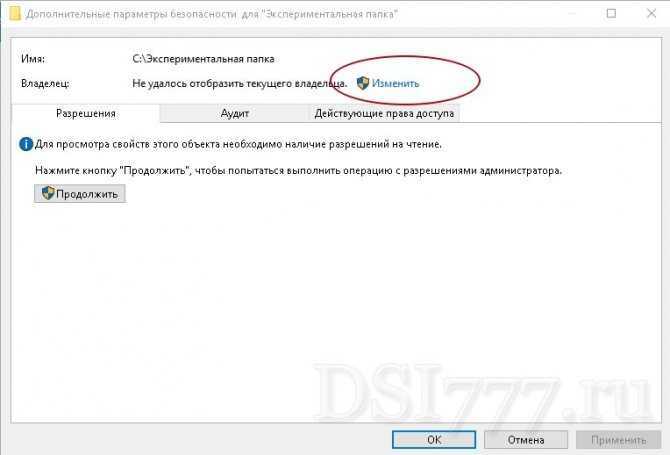
Убедитесь, что у вас есть достаточные права доступа для внесения изменений в разрешения.
После внесения изменений нажмите ОК для сохранения настроек и закрытия окна.
Проверьте текущие разрешения, чтобы убедиться, что они установлены корректно.
Вам отказано в доступе к этой папке Решение

Регулярно проверяйте и обновляйте разрешения, чтобы поддерживать высокий уровень безопасности.
Как удалить неудаляемый файл/папку ? Запросить разрешение от trustedinstaller.
Используйте встроенные инструменты аудита, чтобы отслеживать изменения в разрешениях и предотвращать несанкционированный доступ.
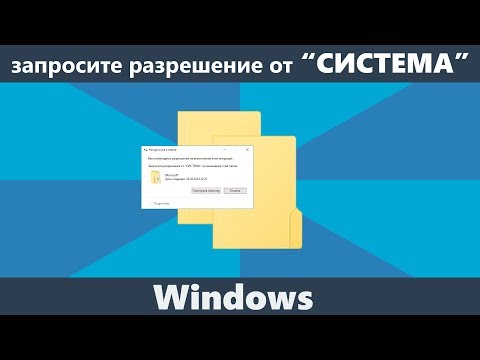
Запросите разрешение от «Система» на изменение этой папки при удалении
|
|
|
Супер-модератор 8811 / 4712 / 571 Регистрация: 13.03.2013 Сообщений: 16,755 Записей в блоге: 16 |
|
Отключить функцию наследования прав в свойствах папки30.12.2018, 08:26. Показов 13140. Ответов 9 Приветствую Вас, уважаемые коллеги и участники форума.
0 |
|
Модератор 9794 / 6342 / 2446 Регистрация: 21.01.2014 Сообщений: 27,019 Записей в блоге: 3 |
|
|
30.12.2018, 15:17 |
|
|
Maks, насколько мне известно, такие вирусы работают от имени системы: им пофигу все локальные админы и их наличие/отсутствие… Этот способ вряд ли сработает…
0 |
|
Супер-модератор 8811 / 4712 / 571 Регистрация: 13.03.2013 Сообщений: 16,755 Записей в блоге: 16 |
|
|
30.12.2018, 16:06 [ТС] |
|
|
Сообщение от D1973 такие вирусы работают от имени системы У системной учетной записи также спокойно отбираются права на папку, как и у администратора, вопрос в том, как отключить возможность повторного наследования.
0 |
|
15903 / 7926 / 755 Регистрация: 03.01.2012 Сообщений: 32,863 |
|
|
30.12.2018, 16:47 |
|
|
Maks, А как будет происходить создание бэкапа?
0 |
|
Супер-модератор 8811 / 4712 / 571 Регистрация: 13.03.2013 Сообщений: 16,755 Записей в блоге: 16 |
|
|
31.12.2018, 06:24 [ТС] |
|
|
Сообщение от gecata А как будет происходить создание бэкапа? Очень просто: от имени пользователя, у которого есть права на папку, создается задание в планировщике, куда подгружается скрипт на архивирование определенных файлов и папок.
0 |
|
6664 / 2825 / 1087 Регистрация: 06.06.2017 Сообщений: 9,585 |
|
|
31.12.2018, 08:56 |
|
|
Сообщение от Maks на ПК пользователей создается некая папка А зачем на локальном ПК? Профили сетевыми должны быть, хранимыми на сервере. Там же (или на другой удалёнке, в облаке) бэкап логично создавать.
0 |
|
5335 / 2203 / 470 Регистрация: 17.10.2015 Сообщений: 9,355 |
|
|
31.12.2018, 09:29 |
|
|
Сообщение от FlasherX А зачем на локальном ПК? впринцепе это просто упрощает/ускоряет выполнение самого бекапа. Аналогичной задачей задался и я ранее. Сделал сл. образом.
0 |
|
Супер-модератор 8811 / 4712 / 571 Регистрация: 13.03.2013 Сообщений: 16,755 Записей в блоге: 16 |
|
|
31.12.2018, 10:39 [ТС] |
|
|
Сообщение от FlasherX А зачем на локальном ПК? Профили сетевыми должны быть, хранимыми на сервере. Там же (или на другой удалёнке, в облаке) бэкап логично создавать. В данном случае, у конторы нет файлопомойки, а делать бэкап в облако не позволяет скорость интернет-канала. Сообщение от romsan Потом это всё архивируется и….. внимание!…. архив переименовывается в расширение от балды. Дело в том, что шифровальщики используют фильтр общеизвестных расширений, в том числе и архивов. Поэтому я задаю архиву расширение типа *.t_8 (для себя знаю, что это *.rar) Тоже так думал, однако, совеременный троян-шифровальщик научился вычислять файлы по сигнатуре, т.е. он все равно доберется до файлов с измененным расширением и зашифрует их. Сообщение от romsan (в определённое время привязывается сетевой диск файлопомойки, делается синхронизация содержимого папки, отключается диск) Делаю также, еще локально создается один раздел диска, к которому на время бэкапа присваивается буква (дабы тот был доступен), а после создания бэкапа буква удаляется, тем самым делая диск недоступным ни для кого.
0 |
|
6664 / 2825 / 1087 Регистрация: 06.06.2017 Сообщений: 9,585 |
|
|
31.12.2018, 16:40 |
|
|
Maks, боюсь, запрашиваемое невозможно. Админ может банально удалить запрещающий элемент разрешений, если у него полностью отрезан доступ. Тут разве только сторонние локеры помогут.
0 |
|
5001 / 1029 / 144 Регистрация: 29.01.2013 Сообщений: 6,023 |
|
|
07.01.2019, 10:23 |
|
|
Можно зайти с другой стороны: Не по теме: Вообще, защитить NTFS от админа — полубесполезное занятие. Архитектура windows устроена так, что система может всё. Единственный вариант, который я вижу — перехитрить вредоноса.
1 |
|
BasicMan Эксперт 29316 / 5623 / 2384 Регистрация: 17.02.2009 Сообщений: 30,364 Блог |
07.01.2019, 10:23 |
|
10 |
|
Новые блоги и статьи
Все статьи Все блоги / |
||||
|
Разработка собственного фреймворка для тестирования в C#
UnmanagedCoder 04.05.2025 C# довольно богат готовыми решениями – NUnit, xUnit, MSTest уже давно стали своеобразными динозаврами индустрии. Однако, как и любой динозавр, они не всегда могут протиснуться в узкие коридоры. . . |
Распределенная трассировка в Java с помощью OpenTelemetry
Javaican 04.05.2025 Микросервисная архитектура стала краеугольным камнем современной разработки, но вместе с ней пришла и головная боль, знакомая многим — отслеживание прохождения запросов через лабиринт взаимосвязанных. . . |
Шаблоны обнаружения сервисов в Kubernetes
Mr. Docker 04.05.2025 Современные Kubernetes-инфраструктуры сталкиваются с серьёзными вызовами. Развертывание в нескольких регионах и облаках одновременно, необходимость обеспечения низкой задержки для глобально. . . |
Создаем SPA на C# и Blazor
stackOverflow 04.05.2025 Мир веб-разработки за последние десять лет претерпел коллосальные изменения. Переход от традиционных многостраничных сайтов к одностраничным приложениям (Single Page Applications, SPA) — это. . . |
Реализация шаблонов проектирования GoF на C++
NullReferenced 04.05.2025 «Банда четырёх» (Gang of Four или GoF) — Эрих Гамма, Ричард Хелм, Ральф Джонсон и Джон Влиссидес — в 1994 году сформировали канон шаблонов, который выдержал проверку временем. И хотя C++ претерпел. . . |
|
C# и сети: Сокеты, gRPC и SignalR
UnmanagedCoder 04.05.2025 Сетевые технологии не стоят на месте, а вместе с ними эволюционируют и инструменты разработки. В . NET появилось множество решений — от низкоуровневых сокетов, позволяющих управлять каждым байтом. . . |
Создание микросервисов с Domain-Driven Design
ArchitectMsa 04.05.2025 Архитектура микросервисов за последние годы превратилась в мощный архитектурный подход, который позволяет разрабатывать гибкие, масштабируемые и устойчивые системы. А если добавить сюда ещё и. . . |
Многопоточность в C++: Современные техники C++26
bytestream 04.05.2025 C++ долго жил по принципу «один поток — одна задача» — как старательный солдатик, выполняющий команды одну за другой. В то время, когда процессоры уже обзавелись несколькими ядрами, этот подход стал. . . |
Продвинутые List Comprehension в Python
py-thonny 04.05.2025 Когда я впервые столкнулся с list comprehension в Python, это было похоже на открытие тайной комнаты в знакомом доме. Вроде бы обычный цикл, но настолько элегантный, что заставляет переосмыслить. . . |
Confluent Kafka Go и потоковые приложения в реальном времени на Golang
golander 03.05.2025 Мир обработки данных перевернулся, когда в 2011 году LinkedIn открыл исходный код Kafka – распределённой системы передачи сообщений, разработанной для внутренних нужд компании. Изначально Кафка. . . |
Наверх