Прошу прощения за рекламу на сайте. Я постарался сделать это максимально ненавязчиво и по минимуму. При чтении заинтересовавших вас статей она не будет вам мешать.
И если есть возможность поставить мой сайт в исключения у блокировщика рекламы, я буду очень признателен вам.

Ниже приведена небольшая инструкция об изменении политики паролей в Microsoft Windows Server 2012 R2.
По умолчанию политика паролей определена таким образом, что все пароли учетных записей пользователей должны удовлетворять следующим требованиям:
1. Не содержать имени учетной записи пользователя или частей полного имени пользователя длиной более двух рядом стоящих знаков.
2. Иметь длину не менее 6 знаков.
3. Содержать знаки трех из четырех перечисленных ниже категорий:
4. Латинские заглавные буквы (от A до Z)
5. Латинские строчные буквы (от a до z)
6. Цифры (от 0 до 9)
7. Отличающиеся от букв и цифр знаки (например, !, $, #, %)
Все параметры политики паролей задаются в локальных групповых политиках.
Для запуска Редактора Локальных Групповых Политик (Local Group Policy Editor) необходим выполнить команду gpedit.msc (для этого необходимо нажать комбинацию клавиш Win + R, в окне «Выполнить» (Run) в поле «Открыть:» (Open:) ввести имя команды и нажать «ОК»)
В запустившейся оснастке в дереве групповых политик последовательно раскрываем группы:
_ «Конфигурация компьютера» (Computer Configuration)
__ «Конфигурация Windows» (Windows Settings)
___ «Параметры безопасности» (Security Settings)
____ «Политики учетных записей» (Account Policies)
_____ «Политика паролей» (Password Policy)
Здесь мы можем изменить необходимую нам политику.
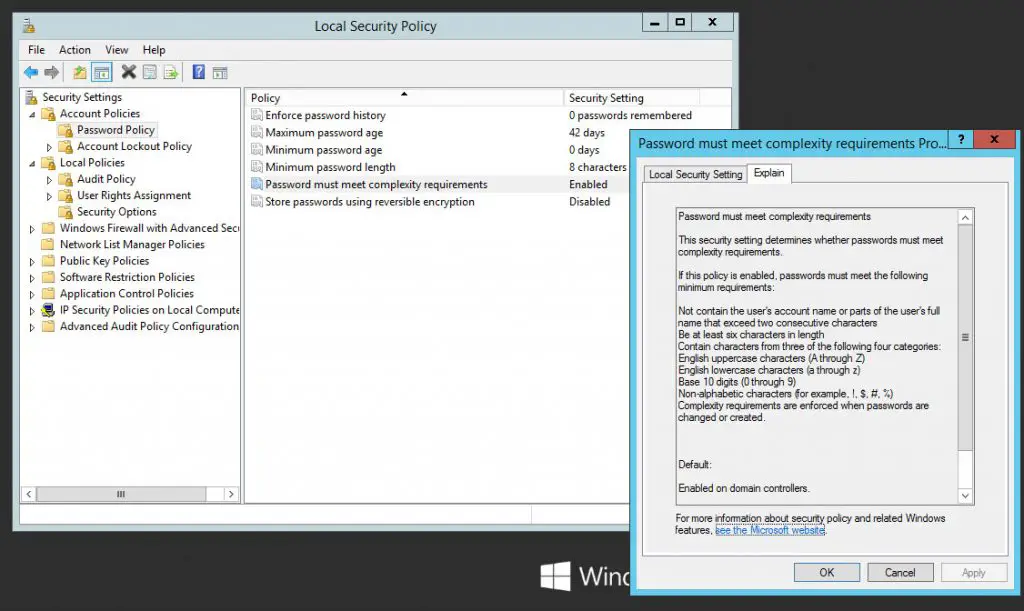
В частности, политику сложности паролей. Для этого два раза кликаем по строке «Пароль должен отвечать требованиям сложности» (Password must meet complexity requirements) и в окне свойства политики устанавливаем переключатель в «Отключен» (Disabled)
Для всех политик доступно довольно подробное описание, для доступа к которому необходимо перейти на вкладку «Объяснение» (Explain).
Изменив необходимые параметры, сохраняем настройки и закрываем окна, нажав «ОК» .
В этой же ветке можно изменить Политику блокировки учетных записей (Account Lockout Policy) в случае неверного ввода паролей.
Все политики редактируются аналогичным образом.
Необходимо понимать, что изменение политики паролей может сильно снизить безопасность сервера.
Вот и всё упрощение политики.
Пароли в Windows Server 2012 R2, упрощение пароля
18 октября 2017, 10:59
Александр
Windows
0
1479
0
Из этой категории
-
Windows не грузится после переноса на RAID
WINDOWS SERVER 2012/2016/2019: Изменение размера шрифта при подключении по RDP
Mukeydrv не работает. Обнаружена обновленная политика цифровых подписей
Проблемы с печатью из RDP
Разрешаем этому приложению вносить изменения на вашем устройстве
Очистка RDP подключения
Перенос папки пользователя и администратора на другой диск windows server
Показать скрытые устройства в диспетчере устройств Windows 7
Этому файлу не сопоставлена программа для выполнения этого действия
Исчезла служба Диспетчер печати в Windows Server 2012
In this second post dedicated to System Administrators who have to deal with a Risk Assessment, Security Assessment, Due Diligence or Compliance Questionnaire: if you lost the first one, you can read it here. This time we’ll talk about how to enforce a password policy by altering the default settings — in terms of password complexity and password minimum length — in Windows Server 2012.
This is a task that often needs to be done to comply with the security requirements asked by most modern regulations and standards — such as the ISO/IEC 27001:2013, ISO/IEC 27002:2013, ISO/IEC 20000:2011, NIST CyberSecurity Framework, SSAE/SOC2, ITIL, PCI-DSS and so on — but it can also be useful for those who just want to protect their system in a better way — or do the exact opposite by relaxing these controls (which is not something you should normally do — read here to understand why).
Here’s how we can take a look at the current system settings in terms of password strength and change them as we please:
Networks without Active Directory
In case you need to configure clients and/or servers not connected to an Active Directory Domain, use the following:
- Open the Control Panel.
- Navigate to Administrative Tools > Local Security Policy.
- In the modal window that will open, expand the Security Settings > Account Policies > Password Policy node.
From there, you can view and/or edit the various options available in Windows Server 2012. For example, you can choose to enable or disable the password complexity requirements, which means the following:
If this policy is enabled, passwords must meet the following minimum requirements:
- Not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters
- Be at least six characters in length
- Contain characters from three of the following four categories:
- English uppercase characters (A through Z)
- English lowercase characters (a through z)
- Base 10 digits (0 through 9)
- Non-alphabetic characters (for example, !, $, #, %)
- Complexity requirements are enforced when passwords are changed or created.
This standard complexity profile can be toggled altering the Password must meet complexity requirements policy.
These are quite good settings, except for the minimum password length: six characters would’ve been arguably viable for 2012, but are definitely not enough in 2017. Luckily enough, you can override that single option by altering the Minimum password length policy, which should be put to (at least) 8 to fend off most brute-force attacks.
Networks with Active Directory
If your client or server is part of an Active Directory domain, you won’t be able to use the Local Security Policy console: if that’s the case, use the Group Policy Management console from Control Panel > Administrative Settings of your AD domain controller and edit the GPO settings there.
Conclusion
That’s it: we hope that these hints will help other System Administrator to make their system compliant with the latest security standards.
If you’re looking for a way to set a idle timeout for Remote Desktop sessions, read this other post.
Microsoft introduced Fine-Grained Password Policy for the first time in Windows Server 2008 and the policy has been part of every Windows Server since then. Fine-Grained Password Policy allows overcoming the limitations of only one password policy for a single domain. A brief example is that we apply different password and account lockout policies to different users in a domain with the help of Fine-Grained Password Policies.
This article discusses the Fine-Grained Password Policy as applicable to Windows Server 2012, and the different ways of configuring this policy. Windows Server 2012 allows two methods of configuring the Fine-Grained Password Policy:
1. Using the Windows PowerShell
2. Using the Active Directory Administrative Center or ADAC
In earlier Windows Server editions, it was possible to configure Fine-Grained Password Policy only through the command line interface (CLI). However with Windows Server 2012 a graphical user interface has been added, allowing the configuration of the Fine-Grained Password Policy via the Active Directory Administrative Center. We will discuss both the methods.
Before you begin to implement the Fine-Grained Password Policy, you must make sure the domain functional level must be Windows Server 2008 or higher. Refer to relevant Windows 2012 articles on our website Firewall.cx.
Backup your Windows Server 2012 R2 host using Altaro’s Free Hyper-V & VMware Backup solution. Download Now!
Configuring Fine-Grained Password Policy From Windows PowerShell
Use your administrative credentials to login to your Windows Server 2012 domain controller. Invoke the PowerShell console by Right clicking on the third icon from the left in the taskbar on the Windows Server desktop and then clicking on Run as Administrator.
Figure 1. Executing Windows PowerShell as Administrator
Clicking on Yes to the UAC confirmation will open up an Administrator: Windows PowerShell console.
Within the PowerShell console, type the following command in order to begin the creation of a new fine grained password policy and press Enter:
C:\Windows\system32> New-ADFineGrainedPasswordPolicy
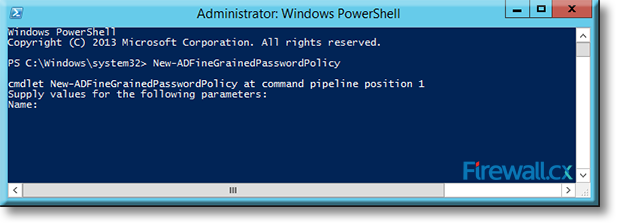
Figure 2. Creating a new Fine Grained Password Policy via PowerShell
Type a name for the new policy at the Name: prompt and press Enter. In our example, we named our policy FGPP:
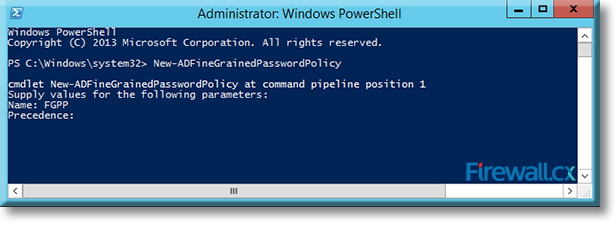
Figure 3. Naming our Fine Grained Password Policy
Type a precedence index number at the Precedence: prompt and press Enter. Note that policies that have a lower precedence number have a higher priority over those with higher precedence numbers. We’ve set our new policy with a precedence of 15:
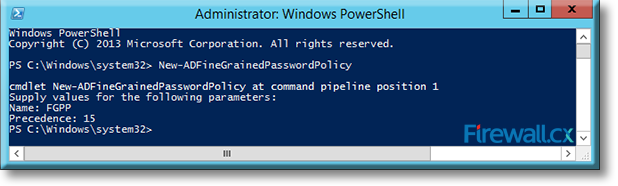
Figure 4. Setting the Precedence index number of our Fine Grained Password Policy
Now the policy is configured, but has all default values. If there is need to add specific parameters to the policy, you can do that by typing the following at the Windows PowerShell command prompt and press Enter:
C:\Windows\system32> New-ADFineGrainedPasswordPolicy -Name FGPP -DisplayName FGPP -Precedence 15 -ComplexityEnabled $true -ReversibleEncryptionEnabled $false -PasswordHistoryCount 20 -MinPasswordLength 10 -MinPasswordAge 3.00:30:00 -MaxPasswordAge 30.00:30:00 -LockoutThreshold 4 -LockoutObservationWindow 0.00:30:00 -LockoutDuration 0.00:45:00
In the above command, replace the name FGPP with the name of your password policy, which in our example is FGPP.
The parameters used in the above are mandatory and pretty much self-explanatory:
Attributes for Password Settings above include:
- Enforce password history
- Maximum password age
- Minimum password age
- Minimum password length
- Passwords must meet complexity requirements
- Store passwords using reversible encryption
Attributes involving account lockout settings include:
- Account lockout duration
- Account lockout threshold
- Reset account lockout after
To apply the policy to a user/group or users/groups, use the following command at the PowerShell command prompt:
C:\Windows\system32> Add-ADFineGrainedPasswordPolicySubject -Identity FGPP -Subjects “Chris_Partsenidis”
For confirming whether the policy has indeed been applied to the groups/users correctly, type the following command at the PowerShell command prompt and press Enter:
C:\Windows\system32> Get-ADFineGrainedPasswordPolicy -Filter { name -like “FGPP” }
Remember, it is necessary to replace FGPP in the above with the name of your password policy. Also replace Chris_Partsenidis with the name of the group or user to whom you want to apply the policy.
The screenshot below shows the execution of the commands and output:
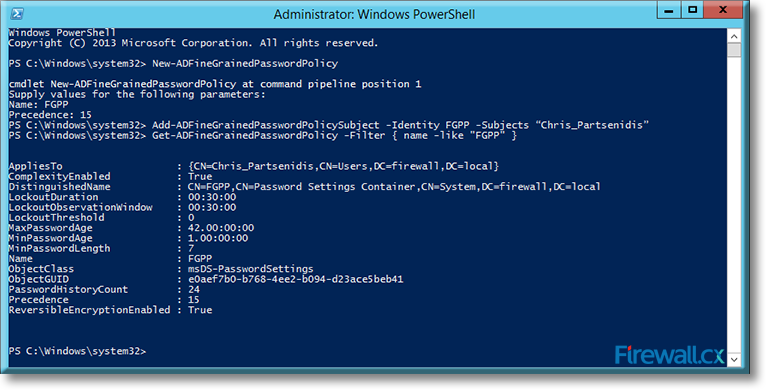
Figure 5. Applying and verifying a Fine Grained Password Policy to a User or Group
Check the AppliesTo section from the output to verify if the policy is applied to the intended user or group.
Configuring Fine-Grained Password Policy Using The Active Directory Administrative Center (ADAC)
Use your administrative credentials to login to your Windows Server 2012 domain controller. Invoke the Server Manager Dashboard by left-clicking on the second icon in the taskbar on the Windows Server desktop:
Figure 6. Opening Server Manager Dashboard
In the Server Manager Dashboard, go to the top right hand corner, click on Tools and then click on Active Directory Administrative Center:
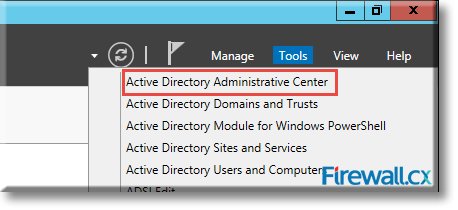
Figure 7. Launching Active Directory Administrative Center
Once the Active Directory Administrative Center screen is open, from the left panel, select the Active Directory (local) to expand.
In our example, the active directory is firewall (local). Locate Systems, expand it and click on Password Settings Container:
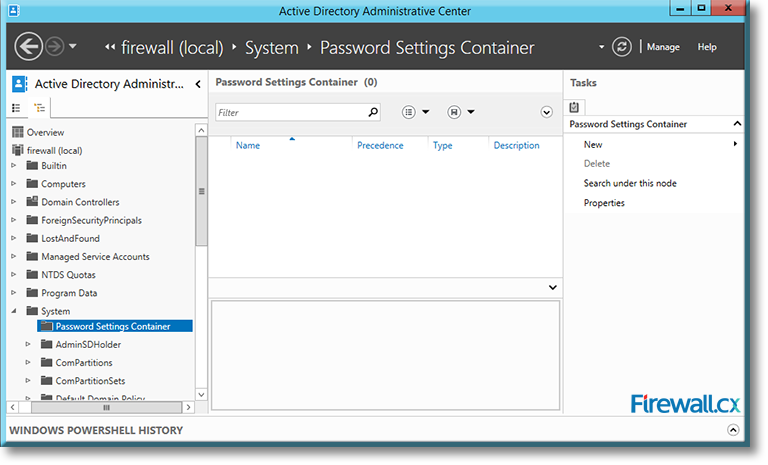
Figure 8. Locating the Password Settings Container
On the right panel, under Tasks and Password Settings Container, click on New:
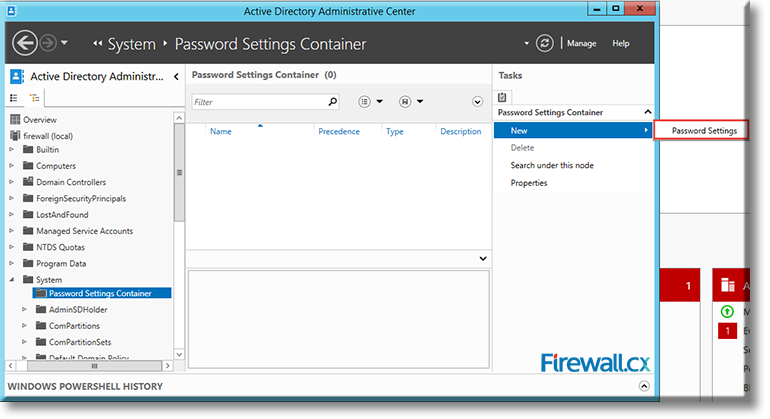
Figure 9. Accessing Password Settings Container
Now click on Settings, which will open up the Create Password Settings screen. Enter a name for the Fine-Grained Password Policy and a number for its precedence.
For our example, we are using the name FGPP or Firewall Group Password Policy with a precedence index of 15. Also, configure the remainder of the policy settings as required:
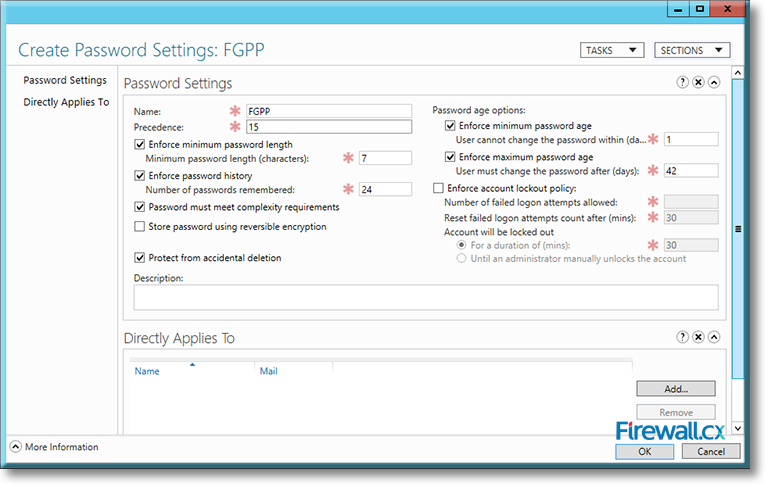
Figure 10. Configuring settings for our FGPP Policy
Once satisfied with the settings, click on Add at the bottom right hand corner. This will open up the Select Users or Groups dialog.
Click on Object Types to select either Users or Groups or both. Click on Locations to select the domain, which in our case is firewall.local.
Under the object names to select, type the name of the group or user on whom you want to apply the password policy. In our example, this is Chris_Partsenidis as shown below:
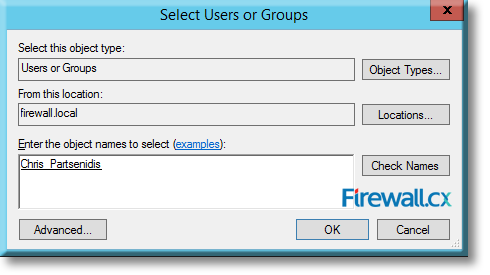
Figure 11. Selecting the Active Directory object to which the Fine Grained Password Policy will be applied to
Click on OK, and you will return to the Create Password Settings screen, which will now have the new name FGPP on top and the name of the user (to whom the policy will apply) at the bottom:
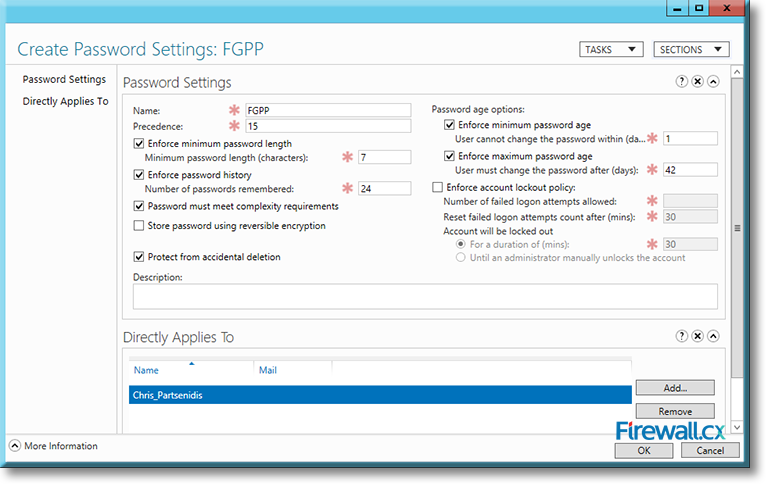
Figure 12. Our Fine Grained Password Policy
Click on OK to complete the process and go back to the Active Directory Administrative Center, which will now show the new Password Settings Container with the name FGPP and the precedence index in the center panel:
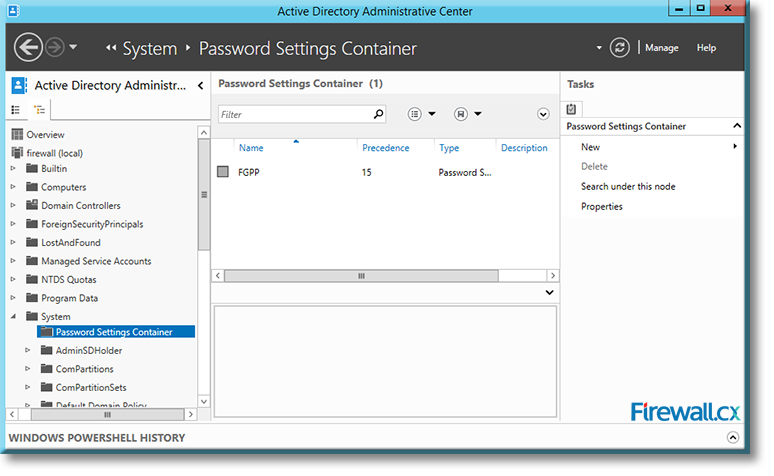
Figure 13. Our Fine Grained Password Policy appearing in the Password Settings Container
To modify any parameter, double click on the Password Settings Container in the central panel. Finally, when you are done, close the Active Directory Administrative Center window.
This article covered the installation and configuration of Fine-Grained Password Policies for Windows Server 2012. We explained how Fine-Grained Password Policies can be installed via PowerShell and the Active Directory Administrative Center. Our step-by-step guide shows all the necessary details to ensure a successful installation and configuration. More high-quality articles can be found in visit our Windows 2012 Section.
Fine-Grained Password Policies (FGPP) allow you to create multiple password policies for specific users or groups. Multiple password policies are available starting with the Windows Server 2008 version of Active Directory. In previous versions of AD, you could create only one password policy per domain (using the Default Domain Policy).
In this article, we’ll show how to create and configure multiple Password Setting Objects in an Active Directory domain.
Contents:
- Fine-Grained Password Policies Concepts
- How to Create Password Setting Policy (PSO) in Active Directory?
- Configuring Fine-Grained Password Policies (PSOs) Using PowerShell
Fine-Grained Password Policies Concepts
Fine-Grained Password Policies allow an administrator to create multiple custom Password Setting Objects (PSO) in an AD domain. In PSOs, you can set the password requirements (length, complexity, history) and account lockout options. PSO policies can be assigned to specific users or groups, but not to Active Directory containers (OUs). If a PSO is assigned to a user, then the password policy settings from the Default Domain Policy GPO are no longer applied to the user.
For example, using FGPP policies you can increase the requirements to the length and complexity of passwords for the administrator accounts, service accounts, or users having external access to the domain resources (via VPN or DirectAccess).
Basic requirements for using multiple FGPP password policies in a domain:
- Domain functional level of Windows Server 2008 domain or newer;
- Password policies can be assigned to users or Global (!) security groups;
- FGPP is applied entirely (you cannot set some of the password settings in the GPO, and some of them in FGPP)
How to Create Password Setting Policy (PSO) in Active Directory?
On Windows Server 2012 and newer, you can create and edit Fine-Grained Password Policies from the graphical interface of the Active Directory Administration Center (ADAC) console.
In this example, we’ll show how to create and assign a separate password policy for the Domain Admins group.
Start the Active Directory Administrative Center (dsac.msc), switch to the tree view and expand the System container. Find the Password Settings Container, right-click it, and select New -> Password Settings.
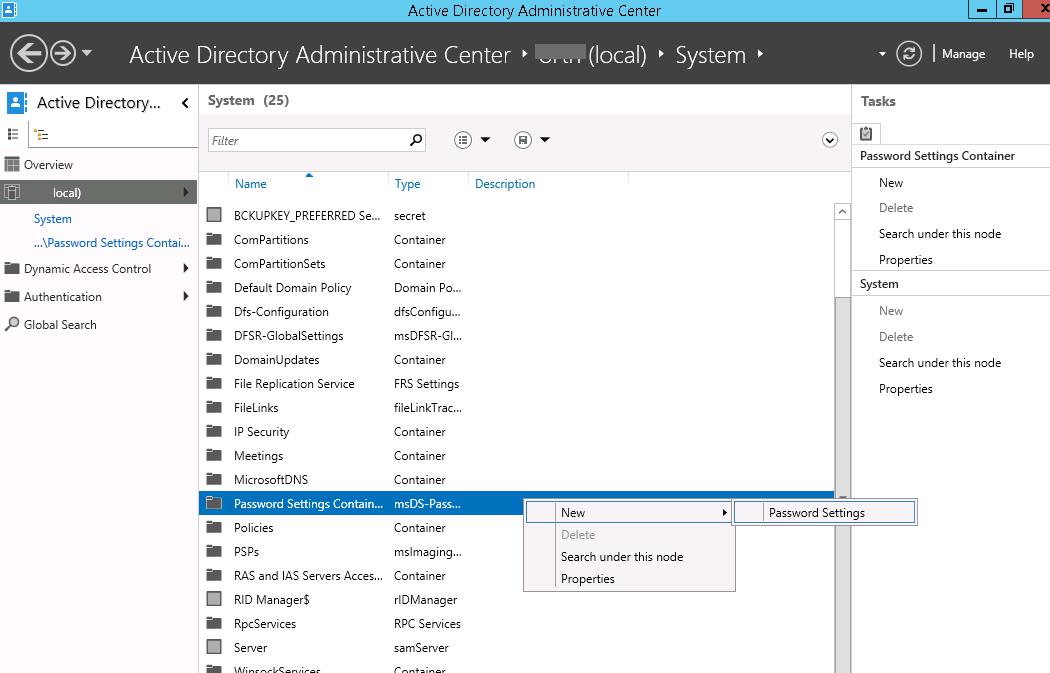
Specify the name of the password policy (in our example it is Password Policy for Domain Admins) and configure its settings (minimal length and complexity of a password, the number of passwords stored in the history, lockout settings, how often to change password, etc.).
Each of the PSO parameters (msDS-PasswordSettings class) is described by a separate AD attribute:
- msDS-LockoutDuration
- msDS-LockoutObservationWindow
- msDS-LockoutThreshold
- msDS-MaximumPasswordAge
- msDS-MinimumPasswordAge
- msDS-MinimumPasswordLength
- msDS-PasswordComplexityEnabled
- msDS-PasswordHistoryLength
- msDS-PasswordReversibleEncryptionEnabled
- msDS-PasswordSettingsPrecedence
Pay attention to the Precedence attribute. This attribute determines the priority of the current password policy. If an object has several FGPP policies assigned to it, the policy with the lowest value in the Precedence field will be applied.
Note.
- If a user has two policies with the same Precedence value assigned, the policy with the lower GUID will be applied.
- If a user has several policies assigned, and one of them enabled through the AD security group, and another one assigned to the user account directly, then the policy assigned to the account will be applied.
Then add groups or users in the Direct Applies To section to apply the policy (in our case, it is Domain Admins). We recommend that you apply the PSO policy to groups rather than individual users. Save the policy.
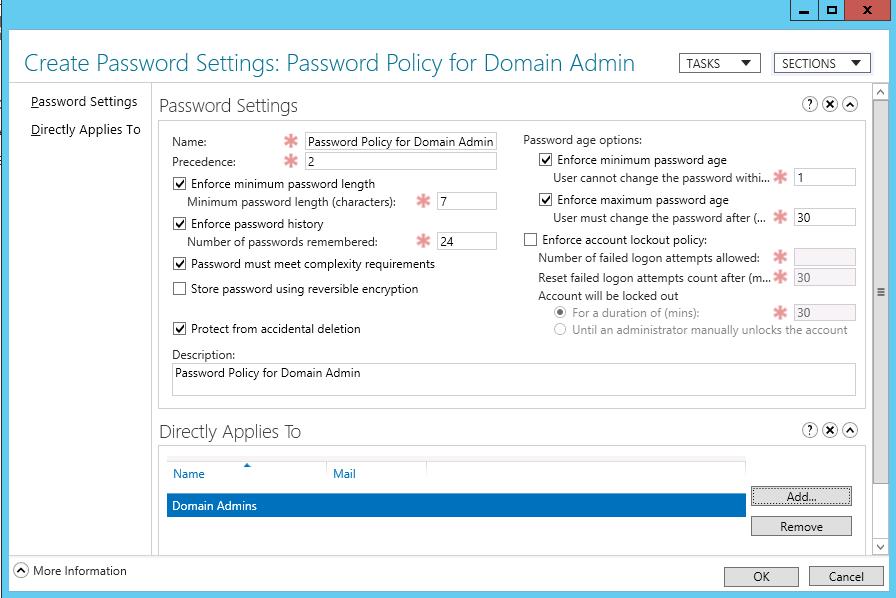
After that, this password policy will be applied to all members of the Domain Admins group.
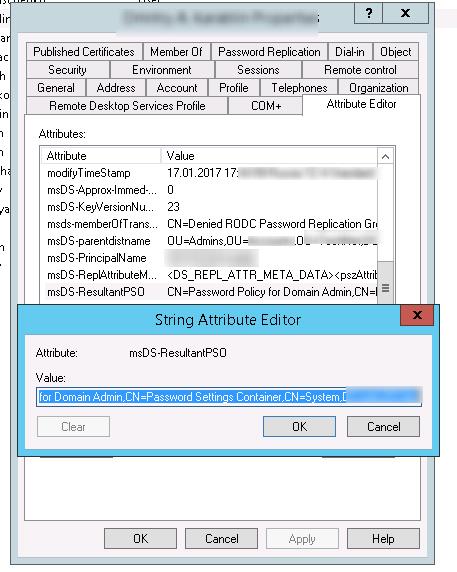
Start the Active Directory Users and Computers (dsa.msc) console (with the Advanced Features option enabled) and open the properties of any user from the Domain Admins group. Go to the Attribute Editor tab and select Constructed option in the Filter field.
Find the msDS-ResultantPSO user attribute. This attribute shows the password policy enabled for a user (CN=Password Policy for Domain Admin,CN=Password Settings Container,CN=System,DC=woshub,DC=com).
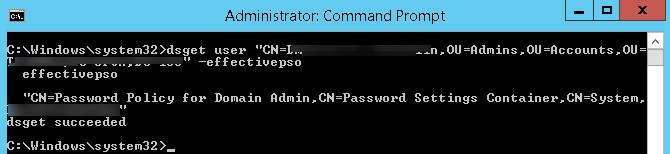
You can also get the current PSO policy for a user using the dsget tool:
dsget user "CN=Max,OU=Admins,DC=woshub,DC=com" –effectivepso
Configuring Fine-Grained Password Policies (PSOs) Using PowerShell
You can manage PSO password policies using PowerShell (the Active Directory PowerShell module must be installed on your computer).
The New-ADFineGrainedPasswordPolicy cmdlet is used to create a new PSO:
New-ADFineGrainedPasswordPolicy -Name “Admin PSO Policy” -Precedence 10 -ComplexityEnabled $true -Description “Domain password policy for admins”-DisplayName “Admin PSO Policy” -LockoutDuration “0.20:00:00” -LockoutObservationWindow “0.00:30:00” -LockoutThreshold 6 -MaxPasswordAge “12.00:00:00” -MinPasswordAge “1.00:00:00” -MinPasswordLength 8 -PasswordHistoryCount 12 -ReversibleEncryptionEnabled $false
Now you can assign a password policy to a user group:
Add-ADFineGrainedPasswordPolicySubject “Admin PSO Policy” -Subjects “Domain Admins”
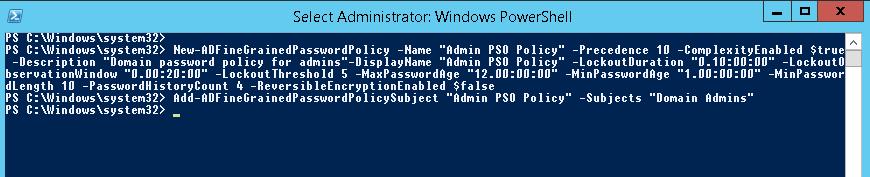
To change the PSO policy settings:
Set-ADFineGrainedPasswordPolicy "Admin PSO Policy" -PasswordHistoryCount:"12"
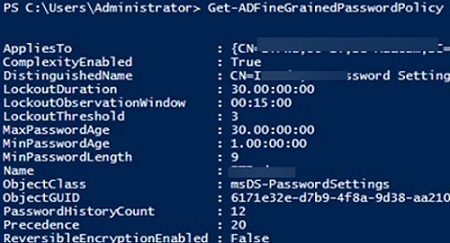
List all FGPP policies in a domain:
Get-ADFineGrainedPasswordPolicy -Filter *
Use the Get-ADUserResultantPasswordPolicy command to get the resulting password policy that applies to a specific user.
Get-ADUserResultantPasswordPolicy -Identity jsmith
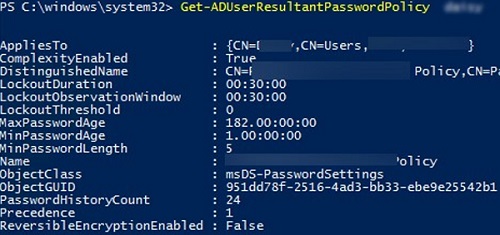
The name of the PSO that applies to the user is specified in the Name field.
You can display the list of PSO policies assigned to an Active Directory group using the Get-ADGroup cmdlet:
Get-ADGroup "Domain Admins" -properties * | Select-Object msDS-PSOApplied
To show the default password policy settings from the Default Domain Policy GPO, run the command:
Get-ADDefaultDomainPasswordPolicy
Despite using Fine-Grained Password policies, users can still use weak passwords, like P@ssw0rd, Pa$$w0rd, etc. We recommend that you periodically audit your domain for weak user passwords.
In Windows Server 2012 or Windows Server 2012 R2, fine-grained password policy management is made much easier than Windows Server 2008/2008 R2. Windows Administrators not have to use ADSI Edit and configure complicated settings to create the Password Settings Object (PSO) in the Password Settings Container. Instead we can configure fine-grained password policy directly in Active Directory Administrative Center (ADAC).
Before you can create fine-grained password policies for a domain, you must ensure that the domain functional level is Windows Server 2008 or newer. This can be done using either ADAC or Windows PowerShell . Note that Domain Admin credentials or greater are required to raise the domain functional level for a domain.
In order to configure fine-grained password policy, go to Windows Server 2012 Server Manager, select Active Directory Administrative Center (ADAC) from the Toolsmenu.

Navigate to System container then Password Settings Container

Click on New and then select Password Settings.

In the Create Password Settings windows, you can specify all the familiar password policy settings by using a user-friendly single screen interface.

Finally, click Add, and locate the group or groups you want the policy to apply to. Then click OK to create the new policy.
Note:
You can also use Windows PowerShell to create, modify, or delete fine-grained password policies for your domain. For example, you can use the New-ADFineGrainedPasswordPolicy cmdlet to create a new fine-grained password policy. You can also use the Set-ADFineGrainedPasswordPolicy cmdlet to modify an existing fine-grained password policy. And you can use the Remove-ADFineGrainedPasswordPolicy cmdlet to delete a fine-grained password policy that is no longer needed in your environment. Use the Get-Help cmdlet to display the syntax and examples for each of these cmdlets.
