Download Windows Speedup Tool to fix errors and make PC run faster
A Security Identifier (SID) is a unique value of variable length used to identify a security principal or security group in Windows operating systems. Well-known SIDs are a group of SIDs that identify generic users or groups. Their values remain constant across all operating systems.
Windows grants or denies access and privileges to resources based on access control lists (ACLs), which use these SIDs to identify users and their group memberships uniquely. When a user logs into a computer, an access token contains user and group SIDs and user privilege levels. When a user requests access to a resource, the access token is checked against the ACL to permit or deny a particular action on a particular object.
SIDs are useful for troubleshooting issues with security audits, Windows server, and domain migrations.
What does an SID look like?
An SID (Security Identifier) starts with the letter “S” and comprises individual components separated by hyphens. It is stored as binary data and then converted to a human-readable string format. This structure helps identify users and groups uniquely within a system.
SID has the format as follows:
S-1-5-21-7623811015-3361044348-030300820-1013
S – The string is a SID.
1 – The revision level (the version of the SID specification).
5 – The identifier authority value.
21-7623811015-3361044348-030300820 – domain or local computer identifier
1013 – a Relative ID (RID). Any group or user that is not created by default will have a Relative ID of 1000 or greater.
Possible identifier authority values are:
0 – Null Authority
1 – World Authority
2 – Local Authority
3 – Creator Authority
4 – Non-unique Authority
5 – NT Authority
9 – Resource Manager Authority
Windows SID Resolver from wingeek.com is a free utility that allows you to resolve a Windows SID.
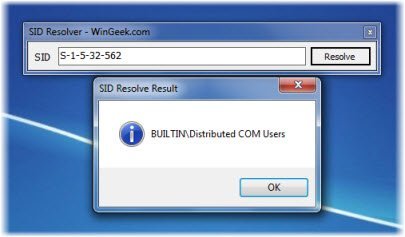
Simply enter the SID you want to resolve, and the utility will identify what account the SID is from.
Additional information is available on KB243330.
How do I find my Windows Security information?
To find your Windows security information, go to Start > Settings > Update & Security > Windows Security. From there, select Virus & threat protection and then Manage settings. This will show you your Windows device’s relevant security details and options.
Read: How to find Security Identifier (SID) of any User in Windows
What is the Security Identifier (SID) for the network service account on Windows OS?
The security identifier (SID) for the Network Service account on Windows OS is S-1-5-20. This SID is used internally by the operating system to represent this built-in account, which is used to run services with minimal privileges.
How do I change my Windows Security ID?
To change your Windows security ID (SID), use the Sysprep (System Preparation Tool) utility provided by Microsoft. This is the only supported method. For detailed instructions on using Sysprep, refer to the official Microsoft documentation.
Anand Khanse is the Admin of TheWindowsClub.com, a 10-year Microsoft MVP (2006-16) & a Windows Insider MVP (2016-2022). Please read the entire post & the comments first, create a System Restore Point before making any changes to your system & be careful about any 3rd-party offers while installing freeware.

Люди, как правило, существа очень забывчивые. Для того чтобы не заставлять пользователей запоминать новый пароль при регистрации в вашем приложении UWP, можно использовать аккаунты сторонних платформ. При этом, можно не заставляя заполнять длиннющие анкеты получить доступ к какой-либо полезной информации и характеристикам пользователя. О том, что публикация контента в социальных сетях повышает конверсию даже и упоминать не буду, это и так понятно. Если хотите разобраться, как работать с самой пока что популярной сетью в мире из C#/XAML приложений UWP, не куря мануалы, то добро пожаловать под кат.
Создание связи приложения Facebook с приложением UWP
Для того, чтобы приложение UWP могло работать с Facevook API нужно создать приложение Facebook. Это делается через портал https://developers.facebook.com/apps/ нажатием кнопки «+ Добавьте новое приложение»
Заполняем поля названия приложения и контактного адреса, а также классифицируем приложение, выбрав категорию.
Далее нам необходима функция входа через facebook
Выстраиваем переключатели таким образом, чтобы как минимум клиентская авторизация OAuth, веб-авторизация OAuth и авторизация OAuth, встроенная в браузер были включены
и выбираем платформу, нажав на platform settings
Получаем окошко:
в котором выбираем Приложение для Windows
Теперь можно сделать какие-то настройки, но они не критичные. Зато впоследствии понадобится идентификатор приложения facebook.
То, что нам действительно нужно заполнить, находится немного ниже:
Значение идентификатора безопасности магазина Windows (SID) можно получить разными способами.
Более простой способ это из кода с помощью:
WebAuthenticationBroker.GetCurrentApplicationCallbackUri().ToString();
Эта строка вернет нам ms-app://SID (ms-app:// необходимо будет удалить)
Второй способ требует, чтобы приложение было связано с Store. В таком случае можно зайти в панель управления, далее в App management приложения и выбрать App identity. Значение PackageSID это и есть то, что нужно.
Работа с Facebook API с помощью Windows SDK for Facebook
Используем библиотеку от Microsoft с труднопроизносимым сокращенным названием winsdkfb. Полное название выговорить гораздо проще — Windows SDK for Facebook. Это самый удобный способ использовать API фейсбука из приложений UWP. Скачать и установить ее можно с NuGet
В C# код страницы XAML добавим пространство имен
using winsdkfb;
Код аутентификации такой:
string[] requested_permissions = {"public_profile", "email", "user_friends"};
FBSession session = FBSession.ActiveSession;
session.WinAppId = WebAuthenticationBroker.GetCurrentApplicationCallbackUri().ToString();
session.FBAppId = "229583744102151";
FBPermissions permissions = new FBPermissions(requested_permissions);
FBResult result = await session.LoginAsync(permissions);
if (result.Succeeded)
{
// здесь мы можем что-то полезное сделать
}
else
{
// не получилось получить доступ к аккаунту facebook
}
Первая строка задает разрешения, доступ к которым получит приложение. В примере упомянуто 3 разрешения, на которые facebook не запрашивает дополнительных подтверждений пользователя.
Полный список находится по ссылке Справка по разрешениям: «Вход через Facebook»
Два параметра, которые необходимо задать для подключения, это уже упомянутый SID и идентификатор созданного приложения facebook.
В результате получим следующее встроенное окно:
Зная как войти, нужно знать, как выйти. Это можно сделать с помощью подобного кода:
FBSession sess = FBSession.ActiveSession;
await sess.LogoutAsync();
Простые данные пользователя можно получить из объекта session.User
string username = session.User.Name; // имя пользователя
string locale = session.User.Locale; // локаль пользователя
Что можно сделать полезное? Например, можно добавить в свое приложение возможность размещения в ленту сообщения с результатом/рекордом игры или приглашением присоединиться
PropertySet parameters = new PropertySet();
parameters.Add("title", "Угадай MP3");
parameters.Add("link", "https://www.microsoft.com/ru-ru/store/p/Угадай-mp3/9wzdncrdkwgv");
parameters.Add("description", "Прикольная игра а-ля угадай мелодию для компании");
parameters.Add("message", "Попробуй тоже эту прикольную игру");
string path = "/" + session.User.Id + "/feed";
var factory = new FBJsonClassFactory(s =>
{
return JsonConvert.DeserializeObject<FBReturnObject>(s);
});
var singleValue = new FBSingleValue(path, parameters, factory);
var fbresult = await singleValue.PostAsync();
if (fbresult.Succeeded)
{
var response = fbresult.Object as FBReturnObject;
}
else
{
// Попытка запостить оказалась неудачной
}
Данный сниппет выполняется в случае, если if (result.Succeeded) возвращает true (то есть после успешной аутентификации). Он использует популярный парсер JSON под названием NewtonSoft.JSON, который нужно установить из NuGet.
Кроме того, необходимо чтобы в проекте присутствовал следующий класс, который характеризует результат совершения операции:
public class FBReturnObject
{
public string Id { get; set; }
public string Post_Id { get; set; }
}
Есть вариант разместить сообщение в ленте, при этом отобразив диалоговое окно, в котором пользователь сможет добавить комментарий. Код немного проще:
PropertySet parameters = new PropertySet();
parameters.Add("title", "ТесТ");
parameters.Add("link", "https://www.microsoft.com/ru-RU/store/p/take-a-test/9wzdncrdkwgx");
parameters.Add("description", "Нескучная программа для проведения тестирований");
parameters.Add("message", "Я прошел тест с отличным результатом");
FBResult fbresult = await session.ShowFeedDialogAsync(parameters);
if (fbresult.Succeeded)
{
var response = fbresult.Object as FBReturnObject;
}
else
{
// Попытка запостить оказалась неудачной
}
С помощью следующего небольшого сниппета, пользователь может отправить ссылку кому-нибудь из друзей и добавить к ней какое-либо сообщение:
PropertySet parameters = new PropertySet();
parameters.Add("link", "http://www.habrahabr.ru");
FBResult fbresult = await session.ShowSendDialogAsync(parameters);
Примеры приложений, использующих winsdkfb, находятся на GitHub, но для C# пока что пример только один и то не особо понятный.
Более-менее нормальная документация находится по ссылке
В частности кроме уже рассмотренных способов взаимодействия с fb рассматриваются следующие возможности: загрузка фото/видео, отправка приглашения друзьям (только для игр), лайк какого-либо объекта или ссылки.
From Wikipedia, the free encyclopedia
Security Identifier (SID) is a unique, immutable identifier of a user account, user group, or other security principal in the Windows NT family of operating systems. A security principal has a single SID for life (in a given Windows domain), and all properties of the principal, including its name, are associated with the SID. This design allows a principal to be renamed (for example, from «Jane Smith» to «Jane Jones») without affecting the security attributes of objects that refer to the principal.
Windows grants privileges and access to resources based on access control lists (ACLs). Each entry on the list defines one SID and a set of permissions for that SID. When a user logs into a PC, Windows generates an access token that contains the user SID, the group SIDs to which the user account belongs, and the user privilege level. When a user requests access to a resource, its ACL is checked against the user’s access token to permit or deny particular action on a particular object.
The human-readable representation of a SID is a string that starts with «S-» and consists of several dash-separated numbers. For example, «S-1-5-21-3623811015-3361044348-30300820-1013» could be a user account’s SID. The following table explains the components of this example SID.
Anatomy of a SID
| Component | Example | Explanation |
|---|---|---|
| Header | S | Identifies the string as a SID |
| Revision level | 1 | The version number of the SID specification. As of 2025, «1» is the only valid number. |
| Authority | 5 | See below |
| Subauthorities | 21- |
In this example, «21» indicates a «domain» subauthority. The following 96-bit ID is a domain identifier. |
| Relative ID (RID) | 1013 | Uniquely identifies the principal within its subauthority group. In the context of domain accounts (which is the focus of our example), RIDs greater than 1000 indicate an admin-defined principal (as opposed to a predefined, built-in, or special-purpose generic principal). |
Originally, SIDs were supposed to allow arbitrarily deep nesting, with each level allowed to create sub-authorities underneath itself. However, that goal was abandoned early in Windows NT development, when it was decided that it would be too unmanageable in practice; by then, however, the SID format had already been finalized and was in heavy use in the Windows code.[1]
Identifier authority
[edit]
Identifier authorities are formally defined as six-byte (48-bit) quantities. The identifier authority is expressed in decimal if its value is less than 232, otherwise in hexadecimal.[2][3] However, while this is the behavior formally defined by Microsoft, and implemented by the relevant Windows APIs (e.g. RtlConvertSidToUnicodeString),[3] hexadecimal identifier authorities appear to have never been used in practice. All known values fit in the least significant byte, and the other 5 bytes are always zero. Identifier authorities are stored in big-endian format, even on little-endian CPU architectures.
Valid identifier authority values[4][5]
| Authority | Formal name | First introduced | Notes |
|---|---|---|---|
| 0 | Null Authority | e.g., «Nobody» (S-1-0-0) | |
| 1 | World Authority | e.g., well-known groups such as «Everyone». (S-1-1-0) | |
| 2 | Local Authority | e.g., flag SIDs like «CONSOLE LOGON» | |
| 3 | Creator Authority | ||
| 4 | Non-unique Authority | ||
| 5 | NT Authority | Managed by the NT security subsystem. There are many sub-authorities such as «BUILTIN» and every Active Directory Domain | |
| 6[6][7] | Site Server Authority | Windows XP | |
| 7[6][7] | Internet Site Authority | Windows XP | |
| 8[6][7][8] | Exchange Authority | Windows XP | |
| 9[7][9][10] | Resource Manager Authority | Windows Server 2003 | |
| 10[6] | Passport Authority | ||
| 11[11] | Microsoft Account Authority | Windows 8 | |
| 12 | Azure Active Directory | Windows 10 | |
| 15[12][13][14] | App Package Authority (Capability SIDs) | Windows Server 2012 | All capability SIDs begin at S-1-15-3. By design, a capability SID does not resolve to a friendly name. The most commonly used capability SID is S- |
| 16[15] | Mandatory Label Authority | Windows Vista | Used as part of Mandatory Integrity Control |
| 17[16] | Scoped Policy ID Authority | ||
| 18[16] | Authentication Authority | ||
| 19[17] | Process Trust Authority |
S-1-5 subauthority values[12][18][5]
| Decimal | Name | First introduced | Format and purpose |
|---|---|---|---|
| 8[5] | Proxy | Windows Server 2003 | S-1-5-8 is the SID of the «SECURITY_NT_AUTHORITY» proxy.[5]
|
| 18 | LocalSystem | Windows NT 3.1 | S-1-5-18 is the SID of the LocalSystem account on all Windows machines.
|
| 19 | LocalService | S-1-5-19 is the SID of the LocalService account on all Windows machines.
|
|
| 20 | NetworkService | S-1-5-20 is the SID of the NetworkService account on all Windows machines.
|
|
| 21 | Domain | S-1-5-21-<Domain ID>, where <Domain ID> is in the form of <32-bit>-<32-bit>-<32-bit>. See below for details.
|
|
| 32 | Users | Windows 7 | S-1-5-32-<RID>. Example: S-1-5-32-544 (the built-in Administrators group).
The resulting SID pertains a predefined, special-purpose user group, and is valid on all Windows machines. RID could only be one the predefined ones. |
| 64 | Authentication | S-1-5-64-<RID>, where <RID> is one of the following:
|
|
| 80 | NT Service | Windows Vista | S-1-5-80-<RID>, where <RID> is a service identifier. «0» (zero) is reserved for the ALL SERVICES group (hence, S-1-5-80-0’s fully qualified name is NT SERVICE\ALL SERVICES).
|
| 82 | IIS AppPool | Windows 7 | |
| 83-0 | Virtual Machines | Windows 7 | S-1-5-83-0 is the SID of the «NT VIRTUAL MACHINE\Virtual Machines» group, which maintains a list of all Hyper-V virtual machines.
|
| 83-1 | Virtual machine | Windows 7 | S-1-5-83-1-<ID1>-<ID2>-<ID3>-<ID4>.
The resulting SID pertains a Hyper-V virtual machine. |
| 90[5] | Windows Manager | Windows 7 | S-1-5-90-0 is the SID of the «Windows Manager Group», a built-in group that maintains all virtual accounts of the Desktop Windows Manager (DWM).
|
| 96 | User-Mode Driver Framework | Windows 7 | S-1-5-96-0-<RID>, where <RID> is a number, is the SID format of a User-Mode Driver Framework (UMDF) virtual account. For example, S-1-5-96-0-1 pertains UMDF-1. The User-mode Font Driver Host (fontdrvhost.exe) runs in the context of a UMDF account.
|
SIDs that start with «S-1-5-21» are noticeably longer than most other SIDs (with the notable exception of service SIDs). Their general format is: S-1-5-21-<Domain ID>, where <Domain ID> is in the form of <32-bit>-<32-bit>-<32-bit>.
The Domain ID uniquely identifies a Windows domain. The RID specifies a principal (user account, group account, or computer account) within that domain.
If the RID portion is greater than 1000, the resulting SID pertains an admin-defined user account, user group, or computer account, e.g., S-1-5-21-Domain.local\JaneDoe.
If the RID portion is smaller than 1000, the resulting SID pertains a predefined (built-in) user account or user group. For example, RID 500 identifies the controversial «Administrator» user account while RID 512 pertains the «Domain Admins» group.
Machine SIDs are variety of domain SIDs (S-1-5-21) with a 96-bit domain ID (a machine is considered its own local domain) but no RID. Their general format is: S-1-5-21-<Machine ID>, where <Machine ID> is in the form of <32-bit>-<32-bit>-<32-bit>.
The machine SID is stored in the SECURITY hive of the Windows Registry, more specifically at HKEY_LOCAL_MACHINE\SECURITY\SAM\Domains\Account. This key has two values: F and V. The latter is a raw binary value that has the machine SID embedded within it at the end of its data (last 96 bits).[19] (Some sources[example needed] state that it is stored in the SAM hive instead.) A backup is located at SECURITY\Policy\PolAcDmS\@.[citation needed]
NewSID ensures that this SID is in a standard NT 4.0 format (3 32-bit subauthorities preceded by three 32-bit authority fields). Next, NewSID generates a new random SID for the computer. NewSID’s generation takes great pains to create a truly random 96-bit value, which replaces the 96-bits of the 3 subauthority values that make up a computer SID.
— NewSID readme[20]
The machine SID is stored in a raw-bytes form in the registry. To convert it into the more common numeric form, one interprets it as three, little endian, 32-bit integers, converts them to decimal, and add hyphens between them.
Service SIDs are a feature of service isolation, introduced in Windows Vista and Windows Server 2008.[21] Any service with the «unrestricted» SID-type property will have a service-specific SID added to the access token of the service host process, allowing permissions for a single service to be managed without necessitating the creation of service accounts.
Each service SID is a local, machine-level SID that has the general form of S-1-5-80-<Service ID>. To generate <Service ID>, Windows copies the service name (in UTF-16 encoding), converts all characters to uppercase, and calculates the SHA-1 digest of said uppercase name. This digest becomes the <Service ID>. The sc.exe command can be used to generate this special SID value; for example, given the «dnscache» service:
C:\>sc query NAME: dnscache SERVICE SID: S-1-5-80-859482183-879914841-863379149-1145462774-2388618682
Therefore, the «dnscache» service can be referred to as either NT SERVICE\dnscache or S-1-5-80-859482183-879914841-863379149-1145462774-2388618682. Since a Service SID is determined exclusively by the service name, the value of the SID for a given service is always the same across all machines wherever the service runs.
A common method of mass-producing Windows PCs is to install Windows on a template machine, and duplicate its disk sector by sector to other identical machines. As a result, these mass-produced machines are identical in every respect, including their SIDs.[20]
Microsoft engineer Mark Russinovich is the creator of a utility called NewSID, the purpose of which is to solve «The SID Duplication Problem.»[20] Microsoft has retired the utility on November 2, 2009, because, Mark and the Windows security team have concluded that duplicate SIDs do not pose any problem whatsoever.[22]
- Access control
- Access Control Matrix
- Discretionary Access Control (DAC)
- Globally Unique Identifier (GUID)
- Mandatory Access Control (MAC)
- Role-Based Access Control (RBAC)
- Capability-based security
- Post-cloning operations
- ^ «[MS-AZOD]: Security Identifiers (SIDs)». learn.microsoft.com. 2022-06-14. Retrieved 2024-12-29.
- ^ «[MS-DTYP]: SID String Format Syntax». learn.microsoft.com. 2023-12-12. Retrieved 2024-12-29.
- ^ a b «RtlConvertSidToUnicodeString function (ntifs.h) — Windows drivers». learn.microsoft.com. 2022-11-04. Retrieved 2024-12-29.
- ^ «Well-known security identifiers in Windows operating systems». support.microsoft.com. Retrieved 12 December 2019.
- ^ a b c d e openspecs-office. «[MS-DTYP]: Well-Known SID Structures». docs.microsoft.com. Retrieved 2020-09-03.
- ^ a b c d «[MS-PAC]: SID Filtering and Claims Transformation». learn.microsoft.com. 2023-06-28. Retrieved 2024-12-29.
- ^ a b c d Honeycutt, Jerry (2005). Microsoft Windows Registry Guide. Microsoft Press. p. 11. ISBN 978-0-7356-2218-0.
- ^ «Outlook2007CodeSamples/SampleWrappedPSTStoreProvider/WrapPST/EdkMdb.h at 10edfa1ce7e6895a4788ad7c766b9120bec0128d · microsoft/Outlook2007CodeSamples». GitHub. Retrieved 2024-12-29.
- ^ See «Custom Principals» section on https://msdn.microsoft.com/en-us/library/aa480244.aspx
- ^ «Larry Osterman’s WebLog». 17 July 2020.
- ^ «Example impact of Microsoft Accounts on Windows APIs in Windows 8/8.1 – Windows SDK Support Team Blog». blogs.msdn.microsoft.com. 12 December 2014.
- ^ a b «Security identifiers». support.microsoft.com. 28 August 2021. Retrieved 2020-09-02.
- ^ «Some SIDs do not resolve into friendly names». support.microsoft.com. 24 September 2021. Retrieved 2020-09-02.
- ^ «Capability SID Constants (Winnt.h) — Win32 apps». docs.microsoft.com. Retrieved 2020-09-02.
- ^ «SYSTEM_MANDATORY_LABEL_ACE (winnt.h) — Win32 apps». learn.microsoft.com. 2024-02-22. Retrieved 2024-12-29.
- ^ a b «[MS-DTYP]: SID_IDENTIFIER_AUTHORITY». learn.microsoft.com. 2020-10-30. Retrieved 2024-12-29.
- ^ «Sandboxing Antimalware Products for Fun and Profit — Elastic Security Labs». www.elastic.co. 2023-02-21. Retrieved 2024-12-29.
- ^ «IIS AppPool Identity SIDs». winterdom. 2020-09-02.
- ^ «MS TechNet NewSID Utility — How It Works». Knowledge Base. Microsoft. November 1, 2006. Retrieved 2008-08-05.
- ^ a b c «NewSID v4.10». Windows Sysinternals. Microsoft. 2006-11-01.
- ^ «Windows Service Isolation Feature». Article. Windows IT Pro. June 6, 2012. Retrieved December 7, 2012.
- ^ Russinovich, Mark (2009-11-03). «The Machine SID Duplication Myth». Mark’s Blog. Microsoft – via Microsoft Learn’s blog archive.
- Official
- ObjectSID and Active Directory
- Microsoft TechNet: Server 2003: Security Identifiers Technical Reference
- MSKB154599: How to Associate a Username with a Security Identifier
- MSKB243330: Well-known security identifiers in Windows operating systems
- Support tools for Windows Server 2003 and Windows XP
- Security Identifiers — Windows Security docs
- Other
- Why Understanding SIDs is Important
- Microsoft Security Descriptor (SID) Attributes : Tutorial Article about SID handling / converting in scripts
When you need to find the security identifier (SID) of a user in Windows environments, understanding the right tools and methods becomes essential. While Microsoft has refined this identification system since Windows NT, administrators need reliable methods to locate and verify these identifiers for effective system management and troubleshooting.
Core methods to find a Windows user’s Security Identifier (SID)
There are several ways to retrieve a SID, depending on your access level and Windows version. Let’s look at the most effective methods.
Command prompt techniques
The command prompt provides straightforward, reliable methods to retrieve SID information across all Windows versions. These commands work efficiently in both standalone and domain-joined environments.
- Open Command Prompt as an administrator.
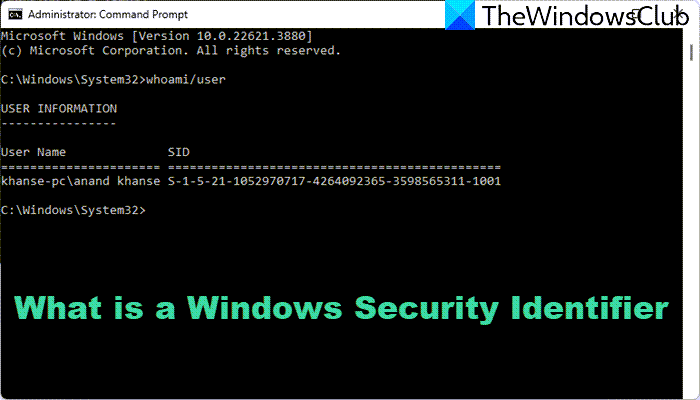
- Type “whoami /user” to see your current user SID.
- Use “wmic useraccount get name,sid” to list all user accounts and their SIDs.
- Enter “psexec -s cmd” to access system context if needed.
- Run “dir /q” in user directories to view SID ownership.
PowerShell get user SID
You can use PowerShell to get the user SID. These commands offer advanced flexibility and automation capabilities for SID retrieval, making them ideal for managing multiple systems or performing bulk operations.
- Execute “Get-WmiObject win32_useraccount” to retrieve a complete list of user accounts and their associated SIDs.
- Run “$objUser = New-Object System.Security.Principal.NTAccount($env:USERNAME)” for current user details.
- Use “Get-LocalUser | Select-Object Name,SID” to display local user accounts.
- Access Active Directory user SIDs with “Get-ADUser -Identity username -Properties SID.”
- Query remote computers using “Invoke-Command” with SID retrieval scripts.
GUI-based discovery
For those who prefer visual navigation, Windows provides built-in graphical tools to locate SID information. This method proves particularly useful during one-off queries or when training new team members.
- Access Computer Management through Windows Administrative Tools.
- Navigate to Local Users and Groups.
- Right-click the user account and select Properties.
- Choose the Security tab.
- Click Advanced to view the SID.
- Document the SID for future reference.
In Windows operating systems, security identifiers act as digital passports for every user and group, enabling precise access control and system management. For administrators tasked with maintaining security across enterprise environments, understanding these unique identifiers unlocks powerful capabilities for permission management and user tracking.
SID structure explained
The structure of a security identifier follows a precise format that Microsoft developed for the Windows NT architecture. Each SID contains multiple components: a revision level, an authority identifier, and a variable number of sub-authority values.
These components work together to create an identifier that remains unique across your entire domain infrastructure. You might see a typical SID displayed as S-1-5-21-3623811015-3361044348-30300820-1013.
Breaking it down:
- S: Stands for SID
- 1: The revision level
- 5: The identifier authority
- 21-3623811015-3361044348-30300820: A domain or computer-specific identifier
- 1013: The unique relative identifier (RID) assigned to a user or group
Why SIDs matter in Windows security?
Windows security relies on SIDs as the foundation of its access control system. Rather than depending on usernames or group names — which users can modify — the system tracks permissions and access rights through these unchangeable identifiers.
When a user attempts to access a resource, Windows examines the SID associated with their account against the access control list of the requested resource. This verification process occurs seamlessly in the background, maintaining security without disrupting user workflow.
The importance of a unique identifier
It is often necessary to find the SID of a user during security audits, access control updates, or troubleshooting scenarios. These permanent identifiers provide stability in user management, remaining unchanged even when usernames get modified.
Organizations operating across multiple domains or implementing complex security policies rely on these identifiers to maintain consistent access control and conduct thorough user activity audits.
Windows SID location map
Registry path navigation
The Windows Registry serves as a central database for storing critical system information, including SID data. Use these steps to safely navigate and locate the SID information you need.
- Launch the Registry Editor by typing “regedit” in the Run dialog.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList.
- Look for subkeys that start with S-1-5.
- Expand each key to view the ProfileImagePath value.
- Match the profile path to identify the correct user.
- Record the SID from the subkey name for reference.
Locating SIDs in system files
Windows stores SID information across various system files and directories, creating a complex web of security relationships. Your operating system maintains these identifiers in both the Security Accounts Manager database and the NTUSER.DAT files within user profiles.
When Windows creates a new user account, it generates a unique SID and stores this information in multiple locations to support various security functions. The system also maintains backup copies of this data through Volume Shadow Copy Service, providing redundancy for these mission-critical identifiers.
Access permission setup
Configuring proper access permissions requires precise SID mapping. Follow these steps to establish appropriate security controls.
- Open Windows Explorer and locate the target resource.
- Right-click and select Properties.
- Navigate to the Security tab.
- Click Advanced to view SID-based permissions.
- Select Add to include new permissions.
- Choose Principal to specify the user or group.
- Enter the SID in the object name field.
- Set appropriate permission levels.
- Apply changes and verify access.
Advanced SID management tools
Managing SIDs in enterprise environments requires sophisticated tools and methodologies. Whether you need to track user activities, implement domain-wide policies, or create security templates, choosing the right approach streamlines your administrative tasks.
Domain controller methods
If your system operates in an Active Directory (AD) environment, you can manage SIDs using these methods:
- Active Directory Users and Computers (ADUC): A centralized GUI for managing user accounts and their SIDs.
- NTDSUTIL: A command-line tool for database maintenance and SID history management.
- Group Policy Objects (GPOs): Helps enforce SID-based security policies across the domain.
- Replication Health Checks: Ensures SID synchronization across domain controllers.
- SID Filtering: Restricts cross-domain authentication to prevent unauthorized access.
Network user tracking
Continuous SID monitoring helps track user activity and detect anomalies or security threats. The tracking system maintains detailed logs of SID usage, providing valuable data for both real-time security monitoring and forensic analysis.
Security template options
Security templates provide structured approaches to implementing standardized SID management policies. These templates serve as the foundation for consistent security implementation across your organization.
Security templates provide structured frameworks for implementing consistent SID management policies throughout your organization. You can develop customized templates that align with your security requirements while maintaining compatibility with existing systems.
SID security best practices
Proper SID access control forms the foundation of your Windows security infrastructure. Regular audits of access patterns help identify potential vulnerabilities and opportunities to strengthen your security controls.
Your granular permission settings create trackable access paths throughout your network infrastructure. Setting up role-based access control with SIDs enables precise management of resource permissions across departments.
Backup documentation methods
Documentation serves as your security blueprint, providing records of SID configurations and changes. These records prove invaluable during audits, system recovery, and security investigations.
- Generate automated SID mapping reports on a scheduled basis.
- Store offline copies of SID assignments in secured locations.
- Document changes to SID configurations through version control systems.
- Maintain detailed logs of SID modifications and access pattern changes.
- Create standardized templates for SID backup procedures.
Managing SID security requires a strategic balance of documentation, access controls and troubleshooting protocols. Your organization’s security posture depends on implementing and maintaining these best practices effectively.
Case #
You need to change the security identifier SID in Windows operating systems. This KB article provides guidance on how to change the security identifier SID in Windows operating systems. There are many entities in the Windows operating system which have an associated SID, some of which are the following:
- Local users and groups
- Domain users and groups
- Computer objects
- Active Directory domains and forests
More specifically, changing the SID of a Windows computer may be required if you have used a misconfigured Windows OS image, which, if used to deploy new machines, may lead to a duplicate SID issue. The duplicate SID issue usually manifests with the following error when trying to join a machine to an Active Directory domain.
The following error occurred attempting to join the domain [domain name]. The domain join cannot be completed because the SID of the domain you attempted to join was identical to the SID of this machine. This is a symptom of an improperly cloned operating system install. You should run sysprep on this machine in order to generate a new machine SID.

Every security account, such as a user, group, or computer, has a unique SID. Access permissions are granted or denied to SIDs for resources, such as files, folders, printers, Microsoft Exchange mailboxes, Microsoft SQL Server databases, objects that are stored in Active Directory, and any data that is protected by the Windows Server security model. A SID contains header information and a set of relative identifiers that identify the domain and the security account. In a domain, each domain controller can create accounts and issue a unique SID to every account. It must be noted that there are both machine SIDs and domain SIDs (https://learn.microsoft.com/en-us/archive/blogs/aaron_margosis/machine-sids-and-domain-s).
This article provides guidance on how to change the security identifier SID in Windows operating systems, to resolve the duplicate SID issue.
Solution #
Before moving forward with any action, it is highly recommended to read a relevant article on Windows Security Identifiers (SID) to get a better grasp of how they work.
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-identifiers
AD Domain SID #
Run the following command to get the current AD domain SID. There is no supported way to change the AD domain SID.
Import-Module ActiveDirectory
#Get the SID of all domains in an AD forest
(Get-ADForest).Domains| %{Get-ADDomain -Server $_} | Select-Object name, domainsid
#Get the SID of a specific AD domain
Get-AdDomain | Select-Object name, domainsidUser or group SID #
Run the following command to get the current local user SID.
Get-LocalUser -Name "[username]" | Select-Object sidRun the following command to get the current domain user SID.
Import-Module ActiveDirectory
Get-AdUser -Identity [username-SaMAccount] | Select Name, SID, UserPrincipalNameRun the following command to get the current local group SID.
Get-LocalGroup "[groupname]" | select SIDRun the following command to get the current domain group SID.
Import-Module ActiveDirectory
Get-ADGroup -Identity "[groupname]" | Select-Object Name, SIDComputer SID #
To get the SID of a workgroup computer, you need to download and run the PsGetSID command line tool, which is part of the SysInternals suite.
To get the SID of a domain-joined machine, run the following Powershell cmdlet.
Get-ADComputer -Filter * | Select-Object Name, SID
Get-ADComputer "[computername]" | Select-Object Name, SIDTo change the computer SID of a Windows computer you can try the following methods.
- As the error message itself suggests, the most direct method of changing the machine SID is by running sysprep on it. Sysprep is a Windows utility which generalizes an OS image. Generalizing an image removes computer-specific information such as installed drivers and the computer security identifier (SID). You can either use Sysprep by itself or Sysprep with an unattend answer file to generalize your image and make it ready for deployment. Details about running sysprep can be found at https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/sysprep—generalize—a-windows-installation?view=windows-11. To run sysprep manually, run the following tasks:
- Open an elevated command prompt and run the following command:
C:\Windows\System32\Sysprep\sysprep.exeIn the pop-up form, select system cleanup action «Enter System OOBE», check the «Generalize» checkbox and select «reboot» or «shutdown» as the shutdown option and click OK.

- Since running sysprep is a quite intrusive action, which will most likely affect already installed applications and drivers, it is not recommended in machines already in production. An alternative for systems already in an Active Directory production environment is to first check for and cleanup any duplicate SID by running the ntdsutil utility. Details about ntdsutil can be found at: https://learn.microsoft.com/en-us/troubleshoot/windows-server/identity/ntdsutil-find-clean-duplicate-security-identifiers. Carry out the following steps to detect and cleanup duplicate SID from the SAM database.
- In an elevated command prompt, run ntdsutil.
- At the Ntdsutil command prompt, type security account management, and then press Enter.
- To connect to the server that stores your Security Account Maintenance (SAM) database, type
connect to serverDNSNameOfServerat the SAM command prompt, and then press Enter. - At the SAM command prompt, type check duplicate sid (or cleanup duplicate sid for cleaning up duplicate SID), and then press Enter.
- Microsoft used to provide the NewSID utility as part of the SysInternals suite but it was later determined that this tool would not provide a sufficient solution, hence it is no longer available for download. Microsoft does not support images that are prepared using NewSID, they only support images that are prepared using SysPrep. Microsoft has not tested NewSID for all deployment cloning options. You can still use the PsGetSID as part of the SysInternals suite, to identity SID property and map it to object names, for both workgroup and AD accounts.
- One viable option for changing a Windows computer SID in production environments is the SIDCHG command line tool, which comes in both 32-bit and 64-bit versions. This is a paid tool, which is licensed based on your usage scenario. SIDCHG (SIDCHG64 on 64-bit Windows) 3.0i is a command-line utility to modify local computer SID and computer name, for Windows 2022/11/2019/2016/10/8.1/2012 R2/8/2012/7/2008 R2. It replaces current computer SID with new random SID. In addition, it changes the WSUS ID for Windows Updates, the MachineGuid, the Machine ID, the Device Identifier for modern Windows apps, the MSDTC CID, the Dhcpv6 DUID, the SQL Server Master database, the encryption state to preserve encrypted files, Windows Action Center settings, Certificates and other encrypted stored information. Preservation of credentials stored in Windows Vault is possible with prior preparation of Vault backup. Optionally OneDrive can be reset. A reboot is needed after the SID change.
Run the following procedure to have the computer SID changed with the SIDCHG command line tool.
- Firstly, activate the SIDCHG software.
- Then run the command with any required parameters as per your scenario. Consult the software vendor’s documentation for each command parameter usage. In the example below the only parameter provided is the /R parameter for automatic system reboot after the SID change. Click Yes to continue.
- Click OK to continue and wait until the system is explicitly restarted or shutdown.
- After system reboot, login to the computer again to verify that the computer SID has been changed, by running the PsGetSID tool from SysInternals.
Bear in mind that before you change the machine SID you need to carry out the following actions:
- Take a full backup of the machine whose SID will be changed, whether that be a bear metal backup or operating system disk backup of a physical machine or a full backup of a virtual machine or container. A VM snapshot may also be handy but a full backup is always recommended. If you compare a snapshot with a backup, for example a Windows System State backup, the snapshots are dependent of the virtual machine, while the System State backup is not, it is independent.
- Audit the machine(s) in question to understand if operating system or application related functionality and features are dependent on the machine SID to operate. This can include application and SQL connection strings and application license files which may have dependencies on the machine SID. If this is the case, create a plan to make necessary changes to accommodate the change.
- Ensure that any real-time antivirus and antimalware software is turned off / disabled before you run the SID change application.
- Ensure that no users will be able to power off, shutdown or logon to the system whose SID is being changed, during the SID change procedure.
This article provided guidance on how to change the security identifier SID in Windows operating systems.
Sources #
- https://learn.microsoft.com/en-us/archive/blogs/deploymentguys/sysprep-machine-sids-and-other-myths
- https://learn.microsoft.com/en-us/archive/blogs/markrussinovich/the-machine-sid-duplication-myth-and-why-sysprep-matters
- https://learn.microsoft.com/en-us/archive/blogs/aaron_margosis/machine-sids-and-domain-sids
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-identifiers
