При возникновении синих экранов BSoD Windows 11, 10 и другие версии системы создают дамп (снимок состояния) оперативной памяти, содержащий отладочную информацию, которую можно использовать для диагностики и определения причин сбоя. Функция обычно включена по умолчанию, но если дампы памяти не создаются, их можно включить: Как включить создание дампов памяти в Windows.
Подробным анализом дампов памяти занимаются разработчики, но и для рядового пользователя, столкнувшегося с синими экранами в Windows это может оказаться полезным: адреса в памяти ему ничего не дадут, но часто можно обнаружить имя файла приложения или драйвера, вызывающее сбой. Здесь помогут специальные программы для анализа дампов памяти, о которых и пойдёт речь далее.
WinDbg

У Майкрософт имеется собственный инструмент отладки и анализа дампов памяти — WinDbg (пока Preview). Скачать его для Windows 11 и Windows 10 можно из Microsoft Store, используя поиск в магазине приложений или прямую ссылку.
Пример простого анализа дампа памяти для обычного пользователя с целью выявления процесса, вызвавшего BSoD с помощью WinDbg:
- Запустите WinDbg от имени Администратора (правый клик по ярлыку в меню «Пуск» — «Запуск от имени администратора»).
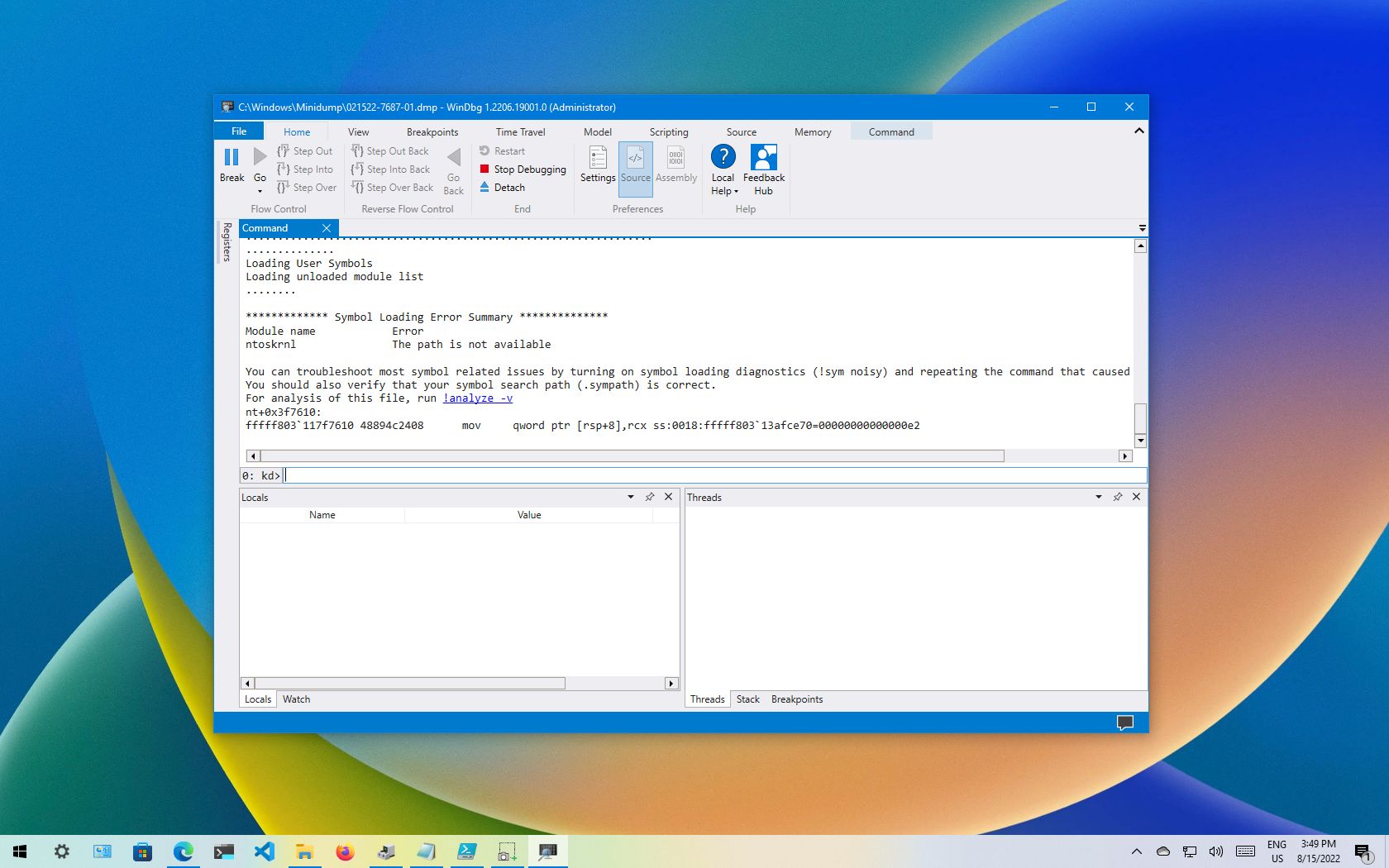
- В главном меню программы выберите «Файл» — «Open dump File» и укажите путь к нужному мини-дампу, обычно находящемуся в папке C:\Windows\Minidump, нажмите кнопку «Open».
- Введите команду
!analyze -v
в поле ввода команд (либо нажмите по ссылке с командой в верхней панели WinDbg) и дождитесь завершения анализа.
- В панели «Command» в верхней части окна программы будет отображен результат анализа, где, при удаче, вы сможете найти информацию о том, каким процессом был инициирован сбой (PROCESS_NAME).
- Может быть информация о файле драйвера (.sys) в поле IMAGE_NAME и другая информация, позволяющая найти источник проблемы.
Далее полученную информацию можно использовать для того, чтобы найти, каким устройствам соответствуют драйверы в Интернете, выяснить назначение процессов вызвавших сбой, предпринять те или иные действия с целью их устранения.
BlueScreenView
BlueScreenView — очень простая утилита, которая позволяет выбрать файла дампа памяти в списке и посмотреть, какие файлы драйвера и процессы привели к сбою: в окне программы они будут выделены красным цветом.

Скачать BlueScreenView можно с официального сайта разработчика https://www.nirsoft.net/utils/blue_screen_view.html
WhoCrashed
Ещё одна программа для анализа дампов памяти — WhoCrashed. В бесплатной версии предоставляет не так много информации.
После нажатия кнопки «Analyze» имеющиеся дампы памяти анализируются, и на вкладке «Report» выводятся коды ошибок, а также текстовое описание на английском языке о том, что означает этот код и о возможных причинах сбоя.

Официальный сайт WhoCrashed https://www.resplendence.com/whocrashed, судя по всему, не открывается из РФ, но утилиту легко найти и скачать из сторонних источников.
When it comes to troubleshooting computer issues, reading minidump files can provide valuable insights. These files, generated by Windows 10 when a system crash occurs, contain crucial information about the crash. Did you know that minidump files can reveal the cause of the crash, helping you identify problematic drivers or hardware? By understanding how to read these files, you can effectively diagnose and resolve system issues.
Reading minidump files in Windows 10 requires some technical knowledge, but it can be a powerful tool for troubleshooting. Minidump files serve as a record of the system state at the time of the crash, including information about the processes running, memory usage, and any error codes. By analyzing these files, you can identify patterns, find potential software conflicts, and take necessary steps to prevent future crashes. Learning how to read minidump files is a valuable skill that can save you time and frustration when it comes to diagnosing and resolving system issues in Windows 10.
If you’re experiencing a crash or system error on your Windows 10 computer, analyzing minidump files can provide valuable information. To read minidump files in Windows 10, follow these steps:
- First, make sure you have the debugging tools for Windows installed on your computer.
- Open the minidump file in the WinDbg tool, which is part of the debugging tools.
- Analyze the crash dump by examining the call stack, loaded modules, and other information.
- Look for error codes or warnings that can help identify the cause of the crash.
- Search for solutions or consult with technical forums if you need assistance interpreting the analysis.

Understanding Minidump Files in Windows 10
Minidump files are essential diagnostic files generated by the Windows operating system when a system crash, also known as a Blue Screen of Death (BSOD), occurs. These files contain vital information about the crash, including the memory contents at the time of the crash, which can be invaluable in diagnosing and troubleshooting the issue. However, reading and interpreting minidump files requires a deep understanding of the internal structure and context of the operating system.
Locating Minidump Files in Windows 10
Before diving into reading minidump files, it’s essential to know where to find them. By default, Windows 10 is configured to create minidump files whenever a system crash occurs. These files are typically stored in the %SystemRoot%\Minidump folder, where %SystemRoot% represents the installation directory of Windows.
To locate the minidump files, follow these steps:
- Open File Explorer.
- Navigate to the
C:drive (or the drive where Windows is installed). - Open the
Windowsfolder. - Find and open the
Minidumpfolder.
Inside the Minidump folder, you will find the minidump files with the extension .dmp. These files are binary files that contain valuable information about the crash that occurred.
Using WinDbg to Read Minidump Files
WinDbg is a powerful debugging tool provided by Microsoft that can be used to read and analyze minidump files in Windows 10. It offers advanced features and commands that help in understanding the cause of the crash and identifying the faulty components.
To use WinDbg to read minidump files, follow these steps:
- Download and install the Windows Software Development Kit (SDK) for Windows 10 from the official Microsoft website.
- Launch WinDbg once the SDK is installed.
- From the File menu, click on «Open Crash Dump» or press Ctrl + D.
- Navigate to the location of the minidump file and select it.
- Click «Open» to load the minidump file into WinDbg.
Once the minidump file is loaded, you can use various commands and analyze the output to gain insights into the crash. WinDbg provides access to the system’s memory, registers, stack trace, and other relevant information that can help identify the root cause of the crash.
Analyzing the Stack Trace
One of the most crucial aspects of reading minidump files is analyzing the stack trace. The stack trace provides information about the sequence of function calls leading up to the crash, helping developers pinpoint the exact location where the error occurred.
To analyze the stack trace in WinDbg:
- Use the
kbcommand to display the stack trace. - Examine the function names, memory addresses, and module names in the stack trace to identify any patterns or abnormal behavior.
- Look for function names or module names that are related to your application or drivers to identify potential culprits.
By carefully analyzing the stack trace, you can narrow down the potential causes of the crash and focus on troubleshooting those specific areas.
Using Symbols for Better Analysis
Symbols play a crucial role in the analysis of minidump files. They provide human-readable names for memory addresses, functions, and modules, making it easier to understand the crash context.
To configure symbol settings in WinDbg:
- From the File menu, click on «Symbol File Path» or press Ctrl + S.
- Add the symbol server path provided by Microsoft:
srv*https://msdl.microsoft.com/download/symbols. - Click «OK» to save the settings.
Once the symbol server path is set, WinDbg will automatically download the necessary symbol files for better analysis.
A notable command for symbol analysis is !analyze -v. This command provides a verbose analysis of the minidump file and helps identify potential causes based on various factors, such as exception codes, faulting modules, and more.
Extending Analysis with Extensions
WinDbg allows users to extend its functionality through various extensions. These extensions provide additional commands, scripts, and features for specialized analysis scenarios.
Some popular extensions for minidump analysis include:
- NTSD extension: Offers advanced commands for analyzing both user-mode and kernel-mode crashes.
- SOS extension: Designed for debugging managed .NET applications and provides powerful commands for analyzing the managed code stack and objects.
- Common WinDbg extensions: Includes a collection of extensions that provide additional functionality and information for various analysis scenarios.
Using extensions can significantly enhance the analysis capabilities of WinDbg and help uncover critical details about the crash.
Analyzing Minidump Files Using Visual Studio
Another powerful tool for reading and analyzing minidump files in Windows 10 is Visual Studio. It provides a rich debugging experience and integrates seamlessly with the development environment.
To analyze minidump files using Visual Studio, follow these steps:
- Open Visual Studio.
- From the «Debug» menu, select «Open Dump File» or press Ctrl + Alt + D.
- Navigate to the location of the minidump file and select it.
- Click «Open» to load the minidump file into Visual Studio.
Once the minidump file is loaded, Visual Studio provides a comprehensive set of tools for analyzing the crash. You can examine the call stack, view memory contents, evaluate expressions, and even step through the code to understand the flow of execution.
Using the Call Stack Window
The Call Stack window in Visual Studio displays the sequence of function calls leading up to the crash, similar to the stack trace in WinDbg. However, Visual Studio provides more advanced features and a user-friendly interface for analyzing the call stack.
To use the Call Stack window:
- From the «Debug» menu, select «Windows» and then «Call Stack» or press Ctrl + Alt + C.
- Examine the function names, file paths, and line numbers in the call stack to identify any potential issues.
- You can double-click on a function in the call stack to navigate directly to its source code for further analysis.
The Call Stack window in Visual Studio helps developers quickly identify the origin of the crash and navigate to relevant code sections for debugging and troubleshooting.
Inspecting Variable Values with the Watch Window
The Watch window in Visual Studio allows developers to inspect the values of variables and expressions at different points during the crash. This enables a deeper understanding of the state of the program and can reveal valuable insights into the cause of the crash.
To use the Watch window:
- From the «Debug» menu, select «Windows» and then «Watch» or press Ctrl + Alt + W.
- Add variables or expressions of interest to the Watch window.
- As you step through the code using breakpoints or the debugger, the values in the Watch window will update dynamically.
By observing the variable values, developers can identify any anomalies or unexpected changes that might be contributing to the crash.
Mining Valuable Information from Minidump Files
Minidump files contain a wealth of information that can shed light on the cause of a system crash. However, to extract the most value from these files, it is crucial to know what specific details to look for and how to interpret them.
Some key information that can be obtained from minidump files includes:
- Exception codes: These codes provide insight into the type of exception that occurred during the crash, such as access violations or illegal instructions.
- Faulting modules: The minidump file identifies the modules or drivers that were active at the time of the crash, helping to pinpoint potential problem areas.
- Register values: The values of CPU registers (e.g., EAX, EBX, EIP) provide information about the state of the system at the time of the crash and can aid in understanding the flow of execution.
- Memory contents: By analyzing the memory contents, it is possible to determine the values of variables, function return addresses, and other critical data that might be relevant to the crash.
Understanding the significance of these details and correlating them with the application or system state can help identify the root cause of the crash and guide the troubleshooting process.
Analyzing Minidump Files with WinDbg Preview
In addition to the traditional WinDbg, Microsoft has introduced a new WinDbg Preview tool, specifically designed for Windows 10. It provides an improved user interface and introduces new features to enhance the analysis of minidump files.
To use WinDbg Preview:
- Download and install WinDbg Preview from the Microsoft Store or the official Windows Dev Center.
- Launch WinDbg Preview.
- From the «File» menu, click on «Open Dump File» or press Ctrl + D.
- Navigate to the location of the minidump file and select it.
- Click «Open» to load the minidump file into WinDbg Preview.
WinDbg Preview offers a refreshed and modernized interface, making it easier to navigate and explore the contents of a minidump file. It also introduces several new commands and features, such as a command-line interface, JavaScript scripting, and integration with the Windows Debugger extension gallery.
Developers familiar with the original WinDbg will find the transition to WinDbg Preview smooth, while benefiting from the additional functionality and improvements offered by the new tool.
Leveraging Symbol Servers in WinDbg Preview
Similar to traditional WinDbg, WinDbg Preview also relies on symbols for better analysis of minidump files. Setting up symbol servers in WinDbg Preview offers the same advantages as in the traditional tool, including the ability to resolve memory addresses and provide meaningful names for modules and functions.
To configure symbol settings in WinDbg Preview:
- From the «File» menu, click on «Symbol File Path» or press Ctrl + S.
- Add the symbol server path provided by Microsoft:
srv*https://msdl.microsoft.com/download/symbols. - Click «OK» to save the settings.
With the symbol server path properly configured, WinDbg Preview will automatically download and load the necessary symbol files, improving the analysis experience.
Scripting and Automation with JavaScript
An exciting feature introduced in WinDbg Preview is the ability to automate analysis tasks using JavaScript scripting. This enables developers to write scripts that can perform complex analysis operations, inspect variables, apply breakpoints, and extract valuable information from minidump files.
WinDbg Preview provides an integrated JavaScript console where scripts can be executed, eliminating the need to switch between the debugger and external scripting environments.
By leveraging the power of JavaScript

Understanding Minidump Files in Windows 10
Minidump files are small memory dump files that are created when Windows encounters a critical error. These files contain important information that can help in diagnosing the cause of the error. If you are experiencing frequent crashes or blue screens in Windows 10, learning how to read minidump files can provide valuable insights into the underlying issues.
To read minidump files in Windows 10, you need to analyze them using specialized tools. One such tool is WinDbg, which is part of the Windows Software Development Kit (SDK). WinDbg allows you to load and examine minidump files, analyze the stack trace, identify the faulty driver or module, and interpret error codes.
When analyzing minidump files, it is important to have knowledge of Windows internals and debugging techniques. The process can be complex and requires expertise in troubleshooting Windows issues. However, with proper guidance and resources, even non-experts can learn how to interpret minidump files and find clues to resolve system crashes.
Reading minidump files is a valuable skill for IT professionals, system administrators, and software developers. By understanding the information stored in these files, you can effectively troubleshoot and fix Windows 10 crashes, ensuring a stable and reliable computing experience.
Key Takeaways — How to Read Minidump Files Windows 10:
- Understanding minidump files can help diagnose and troubleshoot Windows 10 crashes.
- Minidump files contain important information such as error codes and memory addresses.
- Using the Windows Debugger tool, you can analyze minidump files and identify the cause of the crash.
- Learning to read the stack trace in a minidump file can provide insights into the sequence of events leading to the crash.
- Knowledge of common error codes and their meanings can help interpret minidump files more effectively.
Frequently Asked Questions
Reading minidump files in Windows 10 can be a valuable skill when troubleshooting system crashes. Here are some common questions and answers that can help you understand how to read minidump files in Windows 10.
1. Why are minidump files important for analyzing system crashes in Windows 10?
Minidump files are essential for analyzing system crashes in Windows 10 because they contain valuable information about the state of the system at the time of the crash. These files provide a snapshot of the memory, processes, and threads that were active when the crash occurred. Analyzing minidump files can help identify the root cause of the crash, such as a driver issue or hardware problem.
Analyzing minidump files can help system administrators and technicians troubleshoot and resolve the underlying issues that caused the system crash. It can also provide valuable insights into the stability and reliability of the system, enabling proactive maintenance and preventive measures to avoid future crashes.
2. How can I locate and open minidump files in Windows 10?
To locate and open minidump files in Windows 10, follow these steps:
1. Open File Explorer by pressing Windows Key + E.
2. Navigate to the following location: C:\Windows\Minidump (or the location where your minidump files are stored).
3. Look for files with the .dmp extension.
4. Double-click on a minidump file to open it in the default minidump analysis tool in Windows.
By following these steps, you will be able to locate and open minidump files, allowing you to begin the analysis process.
3. What tools can I use to read minidump files in Windows 10?
There are several tools available that can help you read and analyze minidump files in Windows 10. The most commonly used tools include:
1. WinDbg: A powerful debugging tool provided by Microsoft, primarily used by developers and advanced users to analyze minidump files.
2. BlueScreenView: A user-friendly tool that provides a simple interface to view and analyze minidump files. It highlights important information such as the crash address, the driver responsible for the crash, and the crash stack.
3. Visual Studio: If you are a developer using Visual Studio, you can use its built-in debugging and analysis capabilities to read and analyze minidump files.
4. WhoCrashed: Another user-friendly tool that automatically analyzes minidump files and provides information about the cause of the crash.
By using these tools, you can effectively read and analyze minidump files to diagnose system crashes in Windows 10.
4. What information can I find in a minidump file?
Minidump files contain valuable information that can help diagnose system crashes in Windows 10. Some of the key information you can find in a minidump file includes:
1. Crash address: The memory address where the crash occurred.
2. Stack trace: The sequence of function calls leading up to the crash, providing insights into the code execution flow.
3. Module information: Information about the loaded modules and drivers at the time of the crash.
4. Process and thread information: Details about the active processes and threads at the time of the crash.
5. Exception code: The specific code that caused the crash, such as an access violation or an invalid handle.
Analyzing this information can help identify the specific cause of the crash and guide the troubleshooting and resolution process.
5. What are some common causes of system crashes indicated by minidump files in Windows 10?
Minidump files can provide insights into the common causes of system crashes in Windows 10. Some of the common causes indicated by minidump files include:
1. Faulty hardware drivers: Outdated or incompatible drivers can cause system crashes. Minidump files can identify the specific driver responsible for the crash.
2. Memory issues: Problems with system memory, such as faulty RAM modules, can cause crashes. Minidump files can help identify memory-related issues.
3. Software conflicts: Conflicts between different software applications or between software and hardware can lead to crashes. Minidump files can reveal the software components involved in the crash.
4. Overheating: Excessive heat can cause system instability and crashes. Minidump files can provide information about the temperature at the time of the crash.
5. Malware or security threats: Certain types of malware or security threats can cause system crashes. Minidump files can provide insights into any suspicious processes or modules.
By analyzing minidump files, you can identify the underlying causes of system crashes and take appropriate action to resolve them.
Understanding how to read minidump files in Windows 10 can be a valuable skill for troubleshooting system crashes. By analyzing these files, you can gain insights into the root cause of the crash and take appropriate measures to resolve the issue.
To read minidump files in Windows 10, you can start by using specialized tools like WinDbg, which can provide detailed information about the crash. By examining the stack trace, module information, and error codes within the minidump file, you can identify the faulty driver or hardware component causing the crash.
Learning how to read minidump files in Windows 10 might sound tricky, but it’s easier than you think. Minidump files are useful for diagnosing system crashes and are created automatically when Windows experiences a critical error. By following a few steps, you can open these files and understand what might be causing your computer woes.
This tutorial will guide you through the process of downloading the right tools, opening minidump files, and interpreting the data they contain. Let’s get started!
Step 1: Download and Install the Windows Debugging Tools
First, you need to download and install the Windows Debugging Tools, which are part of the Windows Software Development Kit (SDK).
The Windows Debugging Tools are necessary to open and read minidump files. You can find the Windows SDK on the official Microsoft website. During installation, make sure to select the Debugging Tools for Windows option.
Step 2: Open WinDbg (Windows Debugger)
After installing the debugging tools, launch WinDbg from your Start menu.
WinDbg is the program you’ll use to read the minidump files. When you open it for the first time, you might feel a bit overwhelmed by its interface, but don’t worry—the steps are straightforward.
Step 3: Set the Symbol Path
Next, set the symbol path in WinDbg by entering a specific command in the command line.
Symbols help interpret the minidump files accurately. Type the following into the command line: SRV*c:symbols*http://msdl.microsoft.com/download/symbols. This command sets the path for the symbols needed to debug the files properly.
Step 4: Open the Minidump Files
Now, open your minidump file in WinDbg by navigating to File > Open Crash Dump.
Select your minidump file, usually located in C:WindowsMinidump. After selecting the file, WinDbg will load it and provide a summary of the crash.
Step 5: Analyze the Minidump File
Finally, use the !analyze -v command in the WinDbg command line to get a detailed analysis.
This command will give you a comprehensive report, including the probable cause of the crash, which can help you troubleshoot the issue effectively.
Once you’ve completed these steps, you’ll have a detailed report from the minidump file. This report can help you pinpoint the cause of your system crashes and take appropriate actions to fix them.
Tips for How to Read Minidump Files Windows 10
- Always keep your debugging tools updated: Regular updates can ensure that you have the latest features and bug fixes.
- Store symbols locally: Storing symbols on your local drive can speed up the debugging process.
- Practice makes perfect: The more you read minidump files, the easier it becomes to understand them.
- Consult online forums: Communities like Stack Overflow can be invaluable when you’re stuck.
- Document your findings: Keeping a log of your debugging sessions can help you spot patterns and recurring issues.
Frequently Asked Questions
What is a minidump file?
A minidump file is a smaller, more manageable version of a full crash dump and includes important data about why a system crash occurred.
Where can I find minidump files on my computer?
Minidump files are typically located in the C:WindowsMinidump directory.
Do I need to be a programmer to read minidump files?
Not necessarily. While it helps to have some technical knowledge, following step-by-step guides can make the process manageable for most users.
Can I delete minidump files?
Yes, but it’s advisable to keep them until you’ve resolved the issue causing the crashes.
Is WinDbg the only tool to read minidump files?
No, there are other tools like BlueScreenView, but WinDbg is the most comprehensive and widely used.
Summary
- Download and install the Windows Debugging Tools.
- Open WinDbg.
- Set the symbol path.
- Open the minidump file.
- Analyze the file with
!analyze -v.
Conclusion
And there you have it—how to read minidump files Windows 10 style! By following these steps, you can dig deep into the causes of those pesky system crashes. This newfound knowledge not only helps you troubleshoot issues efficiently but also empowers you to take control of your PC’s health.
Whether you’re a tech enthusiast or just someone who wants to keep their computer running smoothly, understanding minidump files is a valuable skill. Happy debugging, and here’s to fewer blue screens in your future! If you’re eager to dive deeper, consider exploring advanced WinDbg commands and additional resources for a more thorough understanding.
Matt Jacobs has been working as an IT consultant for small businesses since receiving his Master’s degree in 2003. While he still does some consulting work, his primary focus now is on creating technology support content for SupportYourTech.com.
His work can be found on many websites and focuses on topics such as Microsoft Office, Apple devices, Android devices, Photoshop, and more.
On Windows 10, when there is a crash, the system creates a «dump» file containing the memory information at the time of the error, which can help determine the reason for the problem.
The «.dmp» file includes the stop error message, a list of the drivers loaded at the time of the problem, kernel, processor, and process details, as well as other information depending on the type of dump file you have.
Although Windows 10 automatically creates dump files, the only problem is that you won’t find any built-in tools to open this type of file, and this is when the Microsoft Windows Debugging (WinDbg) tool can help. WinDbg is an advanced tool designed for debugging kernel-mode and user-mode code, reviewing processor registries, and analyzing crash dumps.
This guide will walk you through the steps to open a dump file to determine what caused the crash to resolve the problem on your computer.
How to open dump file with WinDbg on Windows 10
On Windows 10, you may find multiple ways to open and review a dump error file, but the easiest way is to use the WinDbg tool available through the Microsoft Store.
Install WinDbg
To install the WinDbg tool on Windows 10, use these steps:
All the latest news, reviews, and guides for Windows and Xbox diehards.
- Open the WinDbg download page.
- Click the Install button.
- Click the Open button.
- Click the Install button.
Once you complete the steps, the application will install, and it will be available through the Start menu.
Analyze dump file
To open and analyze a dump file created by a crash on Windows 10, use these steps:
- Open Start.
- Search for WinDbg, right-click the top result, and select the Run as administrator option.
- Click the File menu.
- Click on Start debugging.
- Select the Open sump file option.
- Select the dump file from the folder location — for example, %SystemRoot%\Minidump.
- Click the Open button.
- Click the Open button again.
- Check the progress bar until it loads the dump file (this may take a while).
- Type the following command in the run command and press Enter: !analyze -v
- Quick tip: You can also click the !analyze -v link if available from the main area if available after loading the dump file.
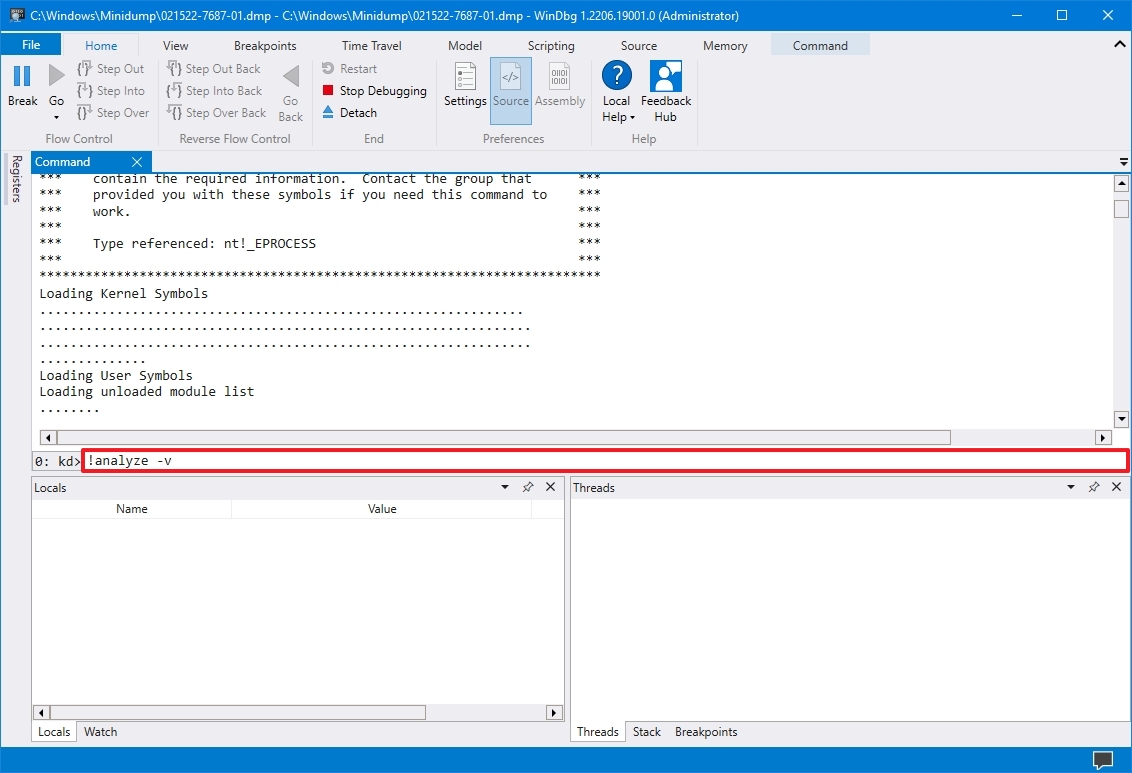
- Check the progress bar until the analysis is complete (this may take a long time depending on the data size).
After you complete the steps, the application will return the dump file analyses, which you can then review to determine the reason for the problem to help you resolve the issue.
The information will be different depending on the problem. For example, this result points out that this was a manually initiated crash with an «e2» error code, which is correct since, for this guide, we use these instructions to force a dump file. The WinDbg even makes an excellent job describing the crash in a language anyone can understand («The user manually initiated this crash dump»).
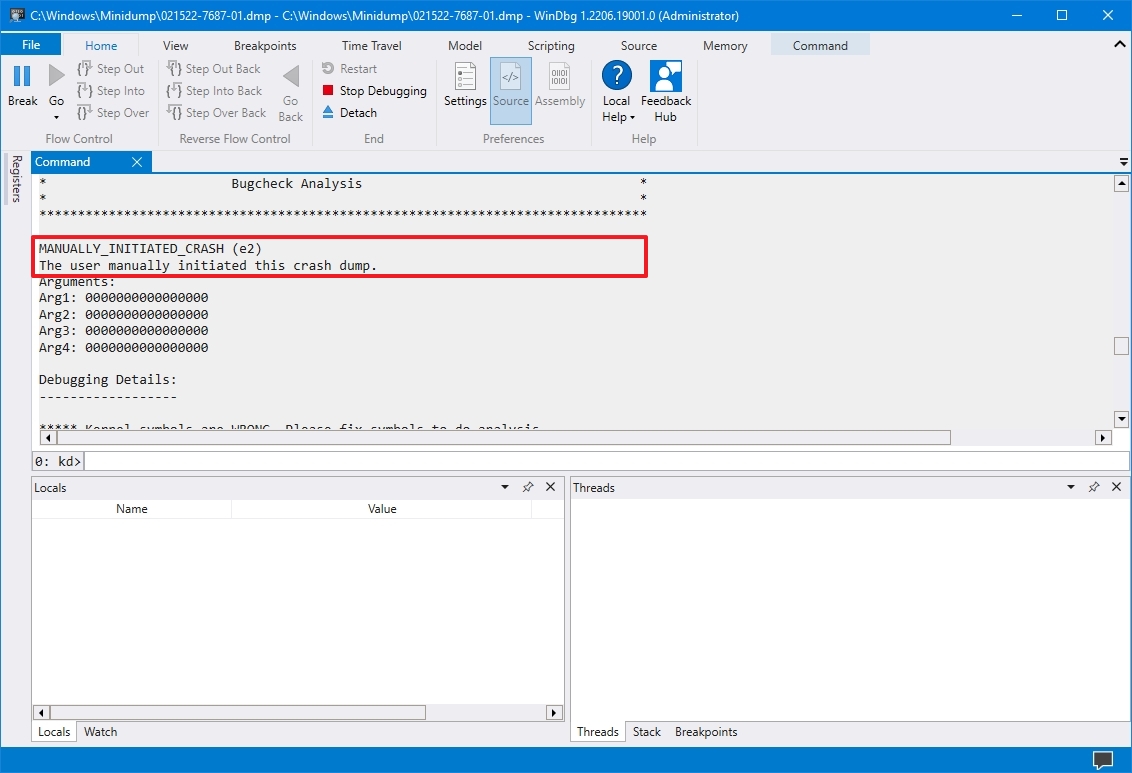
As you continue reviewing the dump file, you will also find more information, such as «FAILURE_BUCKET_ID» and «MODULE_NAME,» which could indicate what is causing the problem.
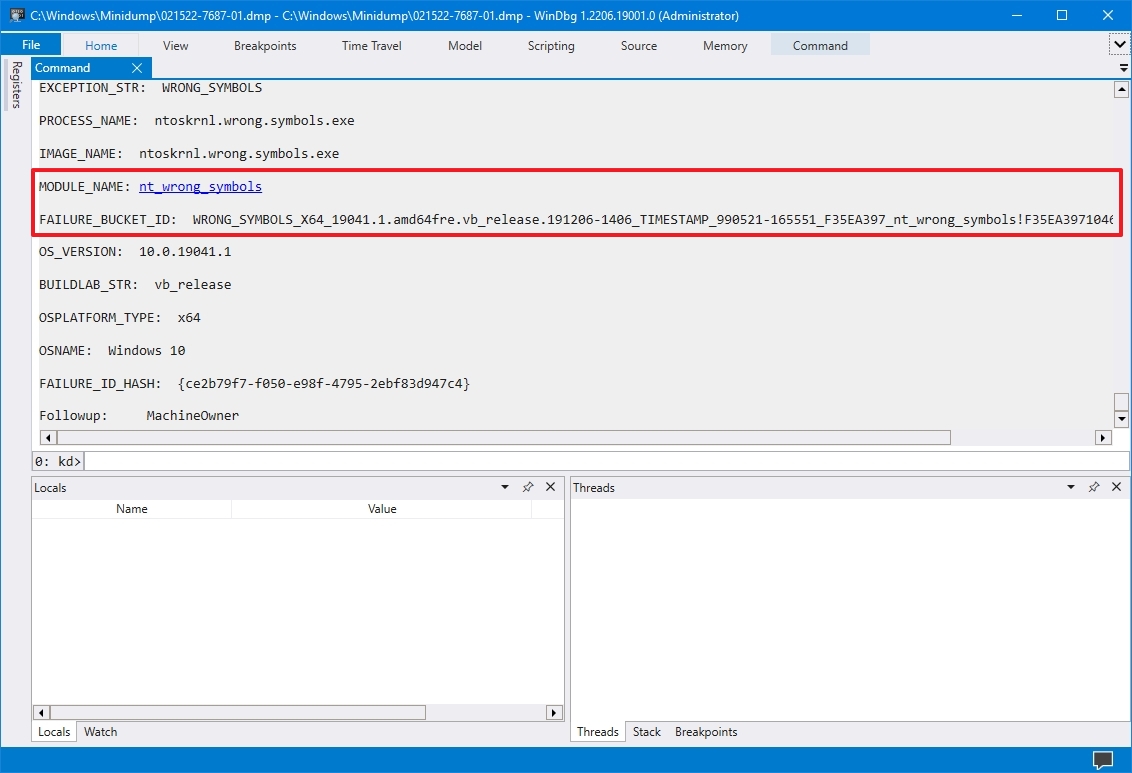
The information can be overwhelming since it is not meant for regular users. If your computer keeps crashing, you can use this tool to get an idea of the problem. If you cannot figure it out, you can use the hints in the report to search online for more information.
More resources
For more helpful articles, coverage, and answers to common questions about Windows 10 and Windows 11, visit the following resources:
- Windows 11 on Windows Central — All you need to know
- Windows 10 on Windows Central — All you need to know
Mauro Huculak has been a Windows How-To Expert contributor for WindowsCentral.com for nearly a decade and has over 15 years of experience writing comprehensive guides. He also has an IT background and has achieved different professional certifications from Microsoft, Cisco, VMware, and CompTIA. He has been recognized as a Microsoft MVP for many years.
В момент критического сбоя операционная система Windows прерывает работу и показывает синий экран смерти (BSOD). Содержимое оперативной памяти и вся информация о возникшей ошибке записывается в файл подкачки. При следующей загрузке Windows создается аварийный дамп c отладочной информацией на основе сохраненных данных. В системном журнале событий создается запись о критической ошибке.
Внимание! Аварийный дамп не создается, если отказала дисковая подсистема или критическая ошибка возникла на начальной стадии загрузки Windows.
Содержание:
- Типы аварийных дампов памяти Windows
- Как включить создание дампа памяти в Windows?
- Установка WinDBG в Windows
- Настройка ассоциации .dmp файлов с WinDBG
- Настройка сервера отладочных символов в WinDBG
- Анализ аварийного дампа памяти в WinDBG
Типы аварийных дампов памяти Windows
На примере актуальной операционной системы Windows 10 (Windows Server 2016) рассмотрим основные типы дампов памяти, которые может создавать система:
- Мини дамп памяти (Small memory dump) (256 КБ). Этот тип файла включает минимальный объем информации. Он содержит только сообщение об ошибке BSOD, информацию о драйверах, процессах, которые были активны в момент сбоя, а также какой процесс или поток ядра вызвал сбой.
- Дамп памяти ядра (Kernel memory dump). Как правило, небольшой по размеру — одна треть объема физической памяти. Дамп памяти ядра является более подробным, чем мини дамп. Он содержит информацию о драйверах и программах в режиме ядра, включает память, выделенную ядру Windows и аппаратному уровню абстракции (HAL), а также память, выделенную драйверам и другим программам в режиме ядра.
- Полный дамп памяти (Complete memory dump). Самый большой по объему и требует памяти, равной оперативной памяти вашей системы плюс 1MB, необходимый Windows для создания этого файла.
- Автоматический дамп памяти (Automatic memory dump). Соответствует дампу памяти ядра с точки зрения информации. Отличается только тем, сколько места он использует для создания файла дампа. Этот тип файлов не существовал в Windows 7. Он был добавлен в Windows 8.
- Активный дамп памяти (Active memory dump). Этот тип отсеивает элементы, которые не могут определить причину сбоя системы. Это было добавлено в Windows 10 и особенно полезно, если вы используете виртуальную машину, или если ваша система является хостом Hyper-V.
Как включить создание дампа памяти в Windows?
С помощью Win+Pause откройте окно с параметрами системы, выберите «Дополнительные параметры системы» (Advanced system settings). Во вкладке «Дополнительно» (Advanced), раздел «Загрузка и восстановление» (Startup and Recovery) нажмите кнопку «Параметры» (Settings). В открывшемся окне настройте действия при отказе системы. Поставьте галку в чек-боксе «Записать события в системный журнал» (Write an event to the system log), выберите тип дампа, который должен создаваться при сбое системы. Если в чек-боксе «Заменять существующий файл дампа» (Overwrite any existing file) поставить галку, то файл будет перезаписываться при каждом сбое. Лучше эту галку снять, тогда у вас будет больше информации для анализа. Отключите также автоматическую перезагрузку системы (Automatically restart).
В большинстве случаев для анализа причины BSOD вам будет достаточно малого дампа памяти.
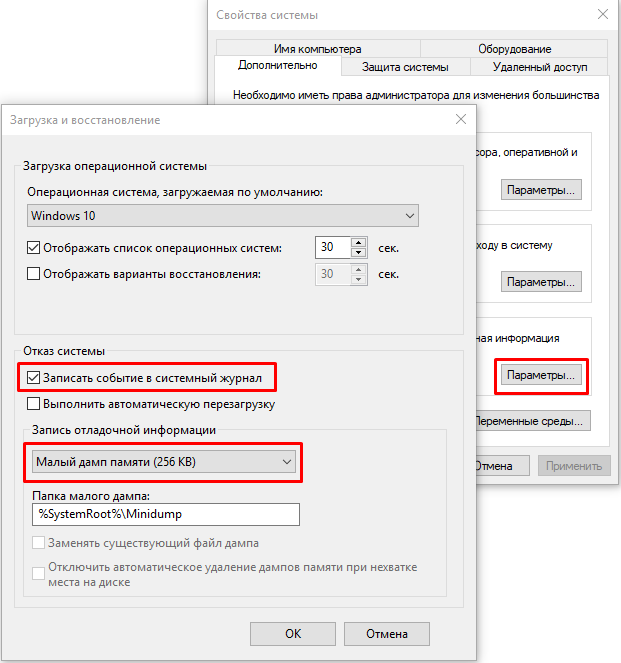
Теперь при возникновении BSOD вы сможете проанализировать файл дампа и найти причину сбоев. Мини дамп по умолчанию сохраняется в папке %systemroot%\minidump. Для анализа файла дампа рекомендую воспользоваться программой WinDBG (Microsoft Kernel Debugger).
Установка WinDBG в Windows
Утилита WinDBG входит в «Пакет SDK для Windows 10» (Windows 10 SDK). Скачать можно здесь.
Файл называется winsdksetup.exe, размер 1,3 МБ.
WinDBG для Windows7 и более ранних систем включен в состав пакета «Microsoft Windows SDK for Windows 7 and .NET Framework 4». Скачать можно здесь.
Запустите установку и выберите, что именно нужно сделать – установить пакет на этот компьютер или загрузить для установки на другие компьютеры. Установим пакет на локальный компьютер.
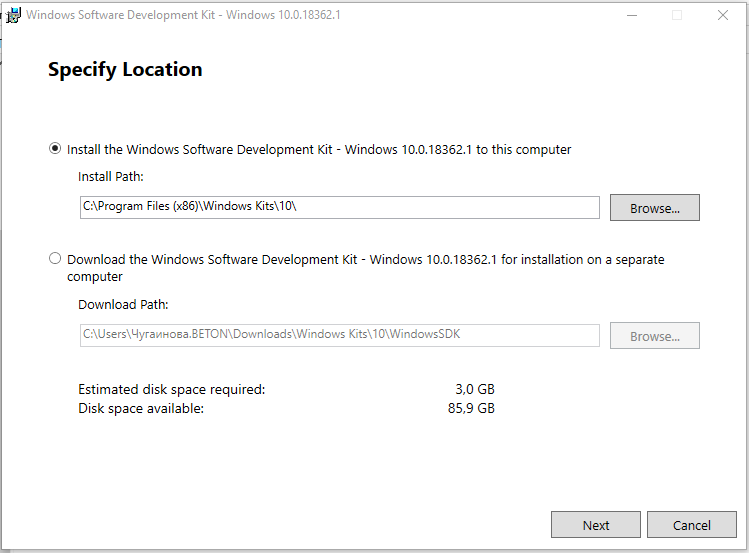
Можете установить весь пакет, но для установки только инструмента отладки выберите Debugging Tools for Windows.
После установки ярлыки WinDBG можно найти в стартовом меню.
Настройка ассоциации .dmp файлов с WinDBG
Для того, чтобы открывать файлы дампов простым кликом, сопоставьте расширение .dmp с утилитой WinDBG.
- Откройте командную строку от имени администратора и выполните команды для 64-разрядной системы:
cd C:\Program Files (x86)\Windows Kits\10\Debuggers\x64
windbg.exe –IA
для 32-разрядной системы:
C:\Program Files (x86)\Windows Kits\10\Debuggers\x86
windbg.exe –IA - В результате типы файлов: .DMP, .HDMP, .MDMP, .KDMP, .WEW – будут сопоставлены с WinDBG.
Настройка сервера отладочных символов в WinDBG
Отладочные символы (debug-символы или symbol files) – это блоки данных, генерируемые в процессе компиляции программы совместно с исполняемым файлом. В таких блоках данных содержится информация о именах переменных, вызываемых функциях, библиотеках и т.д. Эти данные не нужны при выполнении программы, но полезные при ее отладке. Компоненты Microsoft компилируются с символами, распространяемыми через Microsoft Symbol Server.
Настройте WinDBG на использование Microsoft Symbol Server:
- Откройте WinDBG;
- Перейдите в меню File –> Symbol File Path;
- Пропишите строку, содержащую URL для загрузки символов отладки с сайта Microsoft и папку для сохранения кэша:
SRV*E:\Sym_WinDBG*http://msdl.microsoft.com/download/symbols
В примере кэш загружается в папку E:\Sym_WinDBG, можете указать любую. - Не забывайте сохранить изменения в меню File –> Save WorkSpace;
WinDBG произведет поиск символов в локальной папке и, если не обнаружит в ней необходимых символов, то самостоятельно загрузит символы с указанного сайта. Если вы хотите добавить собственную папку с символами, то можно сделать это так:
SRV*E:\Sym_WinDBG*http://msdl.microsoft.com/download/symbols;c:\Symbols
Если подключение к интернету отсутствует, то загрузите предварительно пакет символов с ресурса Windows Symbol Packages.
Анализ аварийного дампа памяти в WinDBG
Отладчик WinDBG открывает файл дампа и загружает необходимые символы для отладки из локальной папки или из интернета. Во время этого процесса вы не можете использовать WinDBG. Внизу окна (в командной строке отладчика) появляется надпись Debugee not connected.
Команды вводятся в командную строку, расположенную внизу окна.
Самое главное, на что нужно обратить внимание – это код ошибки, который всегда указывается в шестнадцатеричном значении и имеет вид 0xXXXXXXXX (указываются в одном из вариантов — STOP: 0x0000007B, 02.07.2019 0008F, 0x8F). В нашем примере код ошибки 0х139.
Полный справочник ошибок можно посмотреть здесь.
Отладчик предлагает выполнить команду !analyze -v, достаточно навести указатель мыши на ссылку и кликнуть. Для чего нужна эта команда?
- Она выполняет предварительный анализ дампа памяти и предоставляет подробную информацию для начала анализа.
- Эта команда отобразит STOP-код и символическое имя ошибки.
- Она показывает стек вызовов команд, которые привели к аварийному завершению.
- Кроме того, здесь отображаются неисправности IP-адреса, процессов и регистров.
- Команда может предоставить готовые рекомендации по решению проблемы.
Основные моменты, на которые вы должны обратить внимание при анализе после выполнения команды !analyze –v (листинг неполный).
1: kd>
!analyze -v
*****************************************************************************
* *
* Bugcheck Analysis *
* *
*****************************************************************************
Символическое имя STOP-ошибки (BugCheck)
KERNEL_SECURITY_CHECK_FAILURE (139)
Описание ошибки (Компонент ядра повредил критическую структуру данных. Это повреждение потенциально может позволить злоумышленнику получить контроль над этой машиной):
A kernel component has corrupted a critical data structure. The corruption could potentially allow a malicious user to gain control of this machine.
Аргументы ошибки:
Arguments:
Arg1: 0000000000000003, A LIST_ENTRY has been corrupted (i.e. double remove).
Arg2: ffffd0003a20d5d0, Address of the trap frame for the exception that caused the bugcheck
Arg3: ffffd0003a20d528, Address of the exception record for the exception that caused the bugcheck
Arg4: 0000000000000000, Reserved
Debugging Details:
------------------
Счетчик показывает сколько раз система упала с аналогичной ошибкой:
CUSTOMER_CRASH_COUNT: 1
Основная категория текущего сбоя:
DEFAULT_BUCKET_ID: FAIL_FAST_CORRUPT_LIST_ENTRY
Код STOP-ошибки в сокращенном формате:
BUGCHECK_STR: 0x139
Процесс, во время исполнения которого произошел сбой (не обязательно причина ошибки, просто в момент сбоя в памяти выполнялся этот процесс):
PROCESS_NAME: sqlservr.exe
CURRENT_IRQL: 2
Расшифровка кода ошибки: В этом приложении система обнаружила переполнение буфера стека, что может позволить злоумышленнику получить контроль над этим приложением.
ERROR_CODE: (NTSTATUS) 0xc0000409 - The system detected an overrun of a stack-based buffer in this application. This overrun could potentially allow a malicious user to gain control of this application.
EXCEPTION_CODE: (NTSTATUS) 0xc0000409 - The system detected an overrun of a stack-based buffer in this application. This overrun could potentially allow a malicious user to gain control of this application.
Последний вызов в стеке:
LAST_CONTROL_TRANSFER: from fffff8040117d6a9 to fffff8040116b0a0
Стек вызовов в момент сбоя:
STACK_TEXT:
ffffd000`3a20d2a8 fffff804`0117d6a9 : 00000000`00000139 00000000`00000003 ffffd000`3a20d5d0 ffffd000`3a20d528 : nt!KeBugCheckEx
ffffd000`3a20d2b0 fffff804`0117da50 : ffffe000`f3ab9080 ffffe000`fc37e001 ffffd000`3a20d5d0 fffff804`0116e2a2 : nt!KiBugCheckDispatch+0x69
ffffd000`3a20d3f0 fffff804`0117c150 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiFastFailDispatch+0xd0
ffffd000`3a20d5d0 fffff804`01199482 : ffffc000`701ba270 ffffc000`00000001 000000ea`73f68040 fffff804`000006f9 : nt!KiRaiseSecurityCheckFailure+0x3d0
ffffd000`3a20d760 fffff804`014a455d : 00000000`00000001 ffffd000`3a20d941 ffffe000`fcacb000 ffffd000`3a20d951 : nt! ?? ::FNODOBFM::`string'+0x17252
ffffd000`3a20d8c0 fffff804`013a34ac : 00000000`00000004 00000000`00000000 ffffd000`3a20d9d8 ffffe001`0a34c600 : nt!IopSynchronousServiceTail+0x379
ffffd000`3a20d990 fffff804`0117d313 : ffffffff`fffffffe 00000000`00000000 00000000`00000000 000000eb`a0cf1380 : nt!NtWriteFile+0x694
ffffd000`3a20da90 00007ffb`475307da : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
000000ee`f25ed2b8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffb`475307da
Участок кода, где возникла ошибка:
FOLLOWUP_IP:
nt!KiFastFailDispatch+d0
fffff804`0117da50 c644242000 mov byte ptr [rsp+20h],0
FAULT_INSTR_CODE: 202444c6
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: nt!KiFastFailDispatch+d0
FOLLOWUP_NAME: MachineOwner
Имя модуля в таблице объектов ядра. Если анализатору удалось обнаружить проблемный драйвер, имя отображается в полях MODULE_NAME и IMAGE_NAME:
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
Если кликнете по ссылке модуля (nt), то увидите подробную информацию о пути и других свойствах модуля. Находите указанный файл, и изучаете его свойства.
1: kd>
lmvm nt
Browse full module list
Loaded symbol image file: ntkrnlmp.exe
Mapped memory image file: C:\ProgramData\dbg\sym\ntoskrnl.exe\5A9A2147787000\ntoskrnl.exe
Image path: ntkrnlmp.exe
Image name: ntkrnlmp.exe
InternalName: ntkrnlmp.exe
OriginalFilename: ntkrnlmp.exe
ProductVersion: 6.3.9600.18946
FileVersion: 6.3.9600.18946 (winblue_ltsb_escrow.180302-1800)
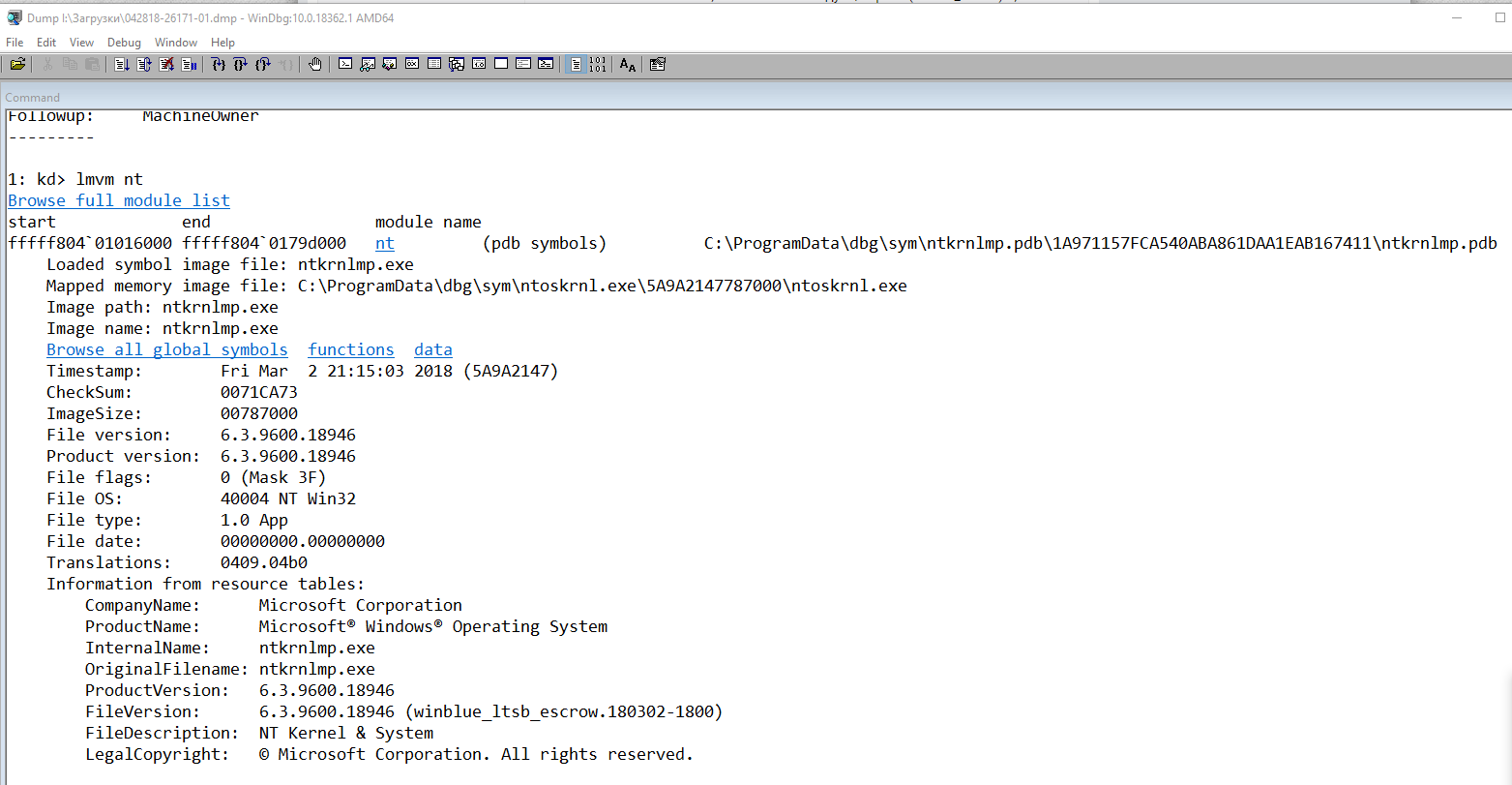
В приведенном примере анализ указал на файл ядра ntkrnlmp.exe. Когда анализ дампа памяти указывает на системный драйвер (например, win32k.sys) или файл ядра (как в нашем примере ntkrnlmp.exe), вероятнее всего данный файл не является причиной проблемы. Очень часто оказывается, что проблема кроется в драйвере устройства, настройках BIOS или в неисправности оборудования.
Если вы увидели, что BSOD возник из-за стороннего драйвера, его имя будет указано в значениях MODULE_NAME и IMAGE_NAME.
Например:
Image path: \SystemRoot\system32\drivers\cmudaxp.sys
Image name: cmudaxp.sys
Откройте свойсва файла драйвера и проверьте его версию. В большинстве случаев проблема с драйверами решается их обнвовлением.




